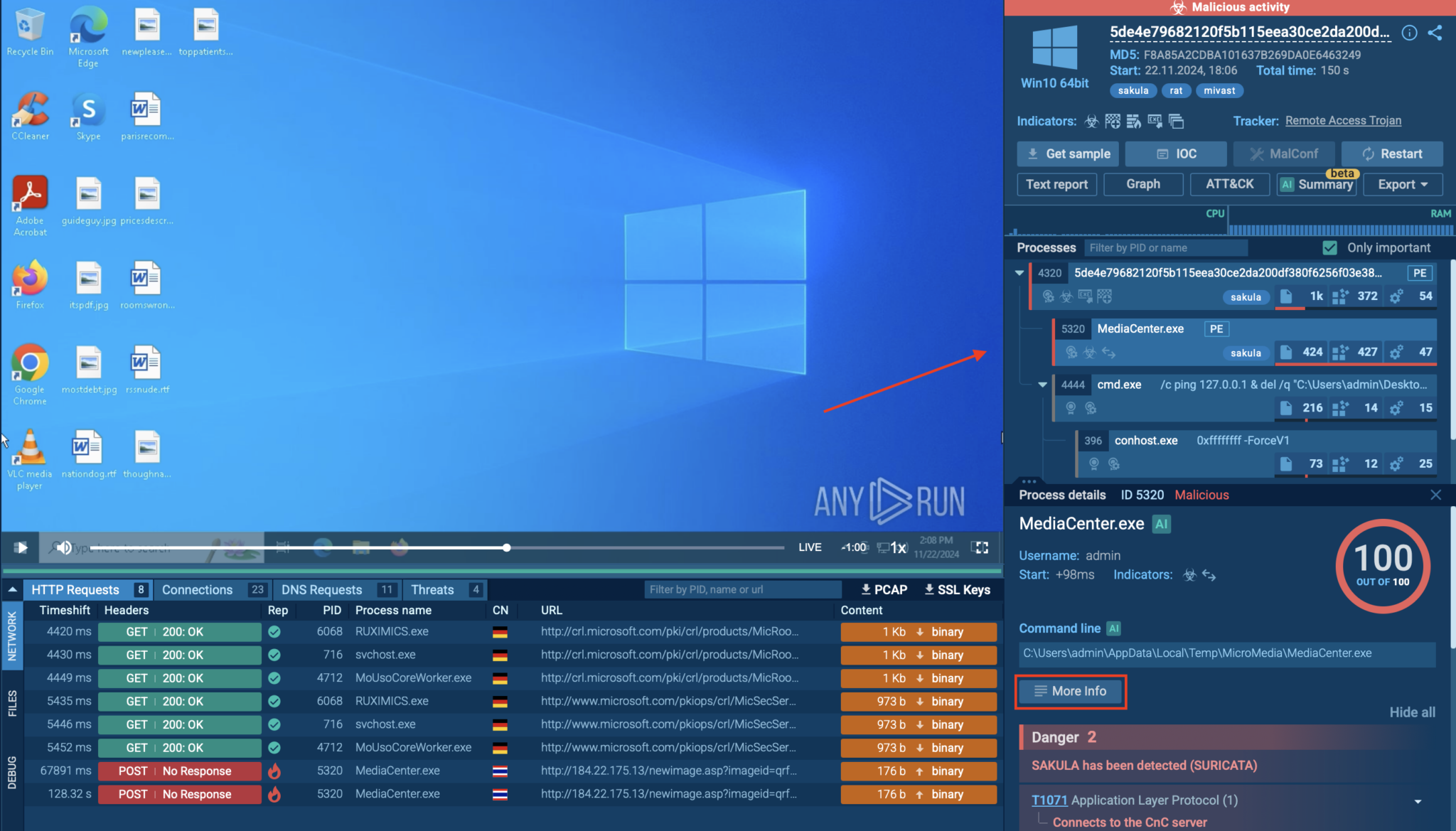
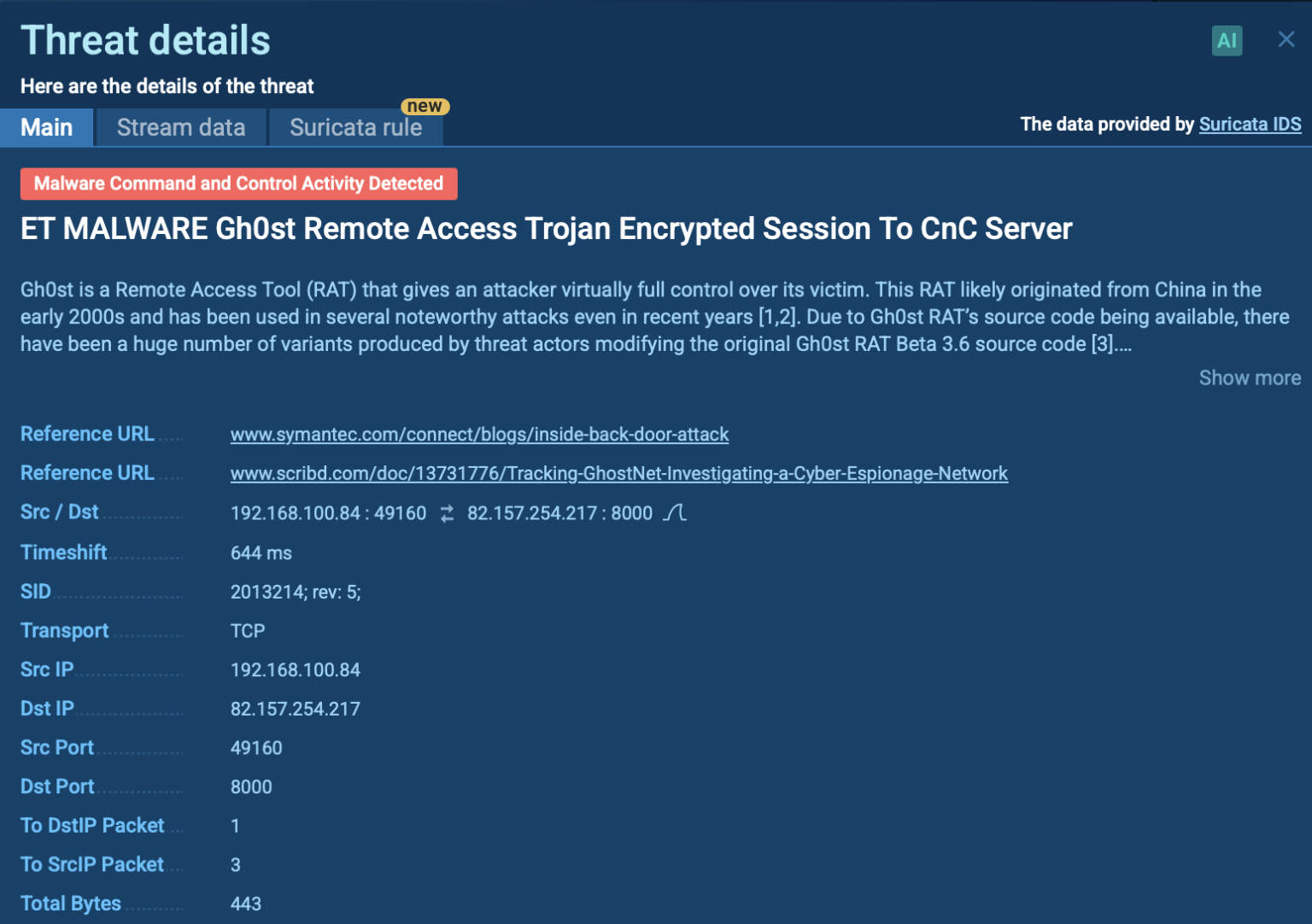
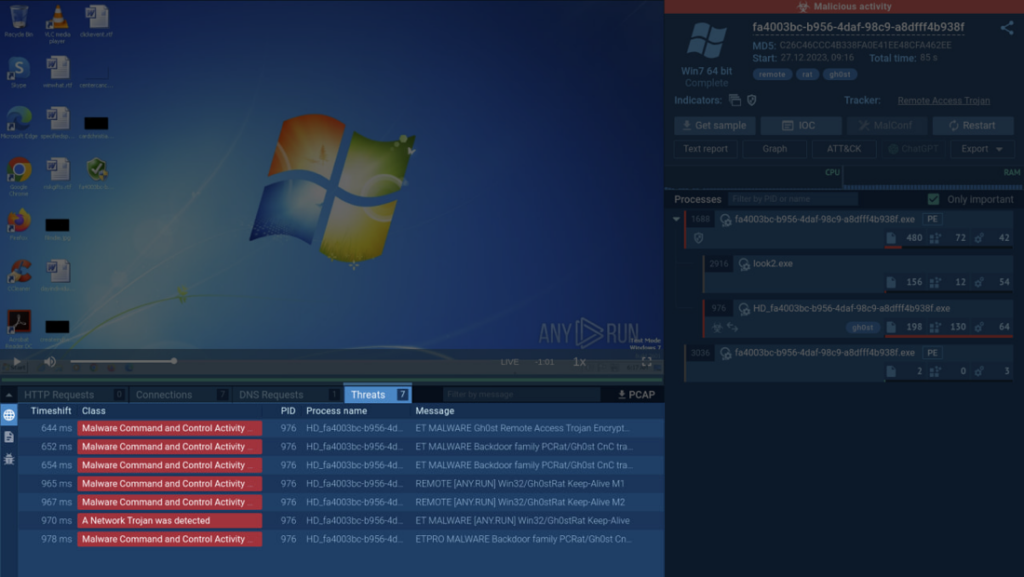
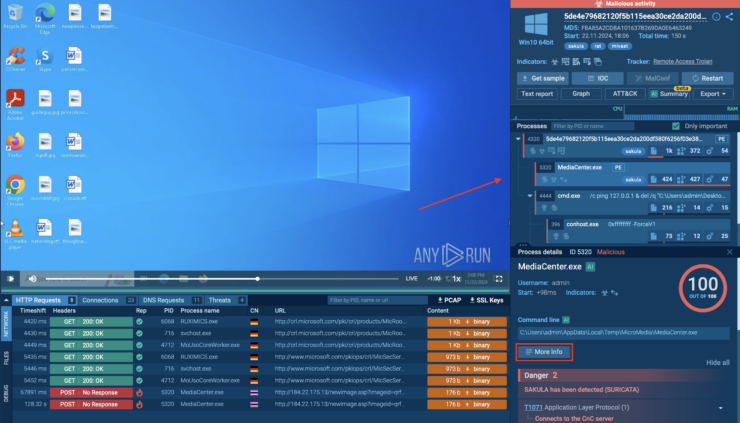
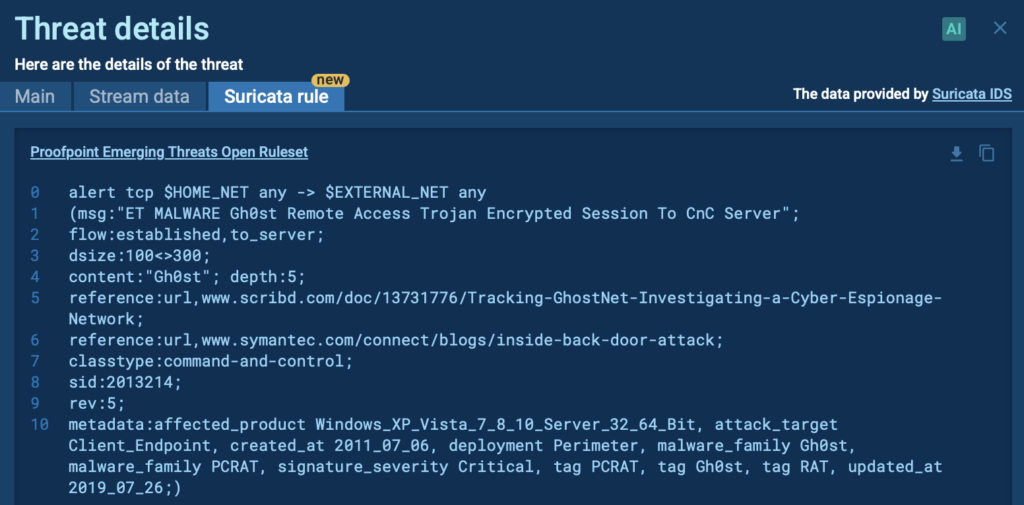
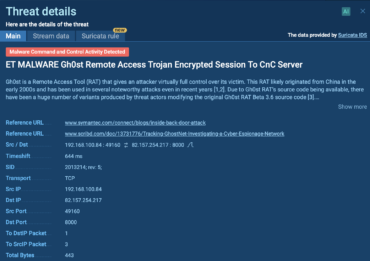
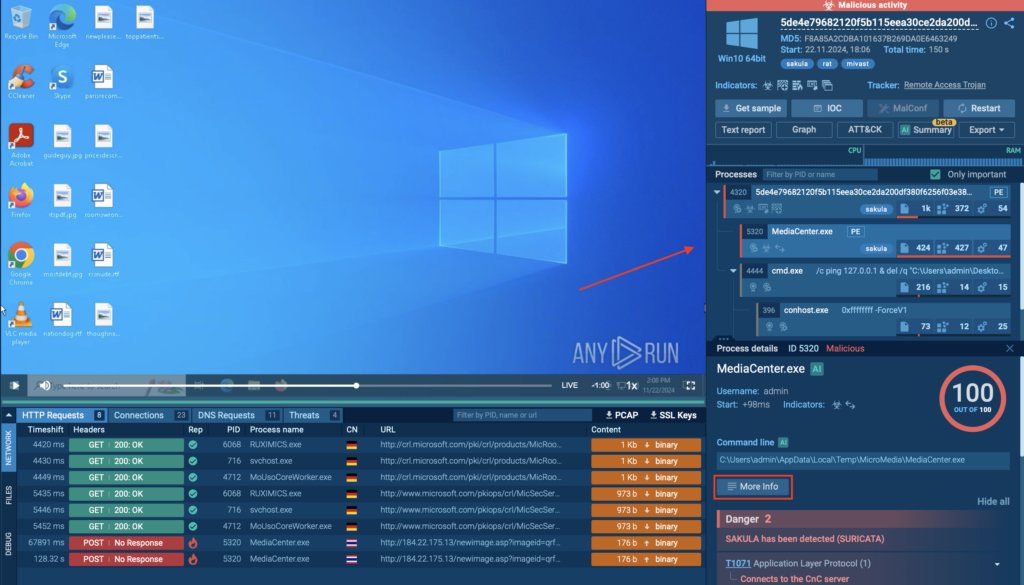
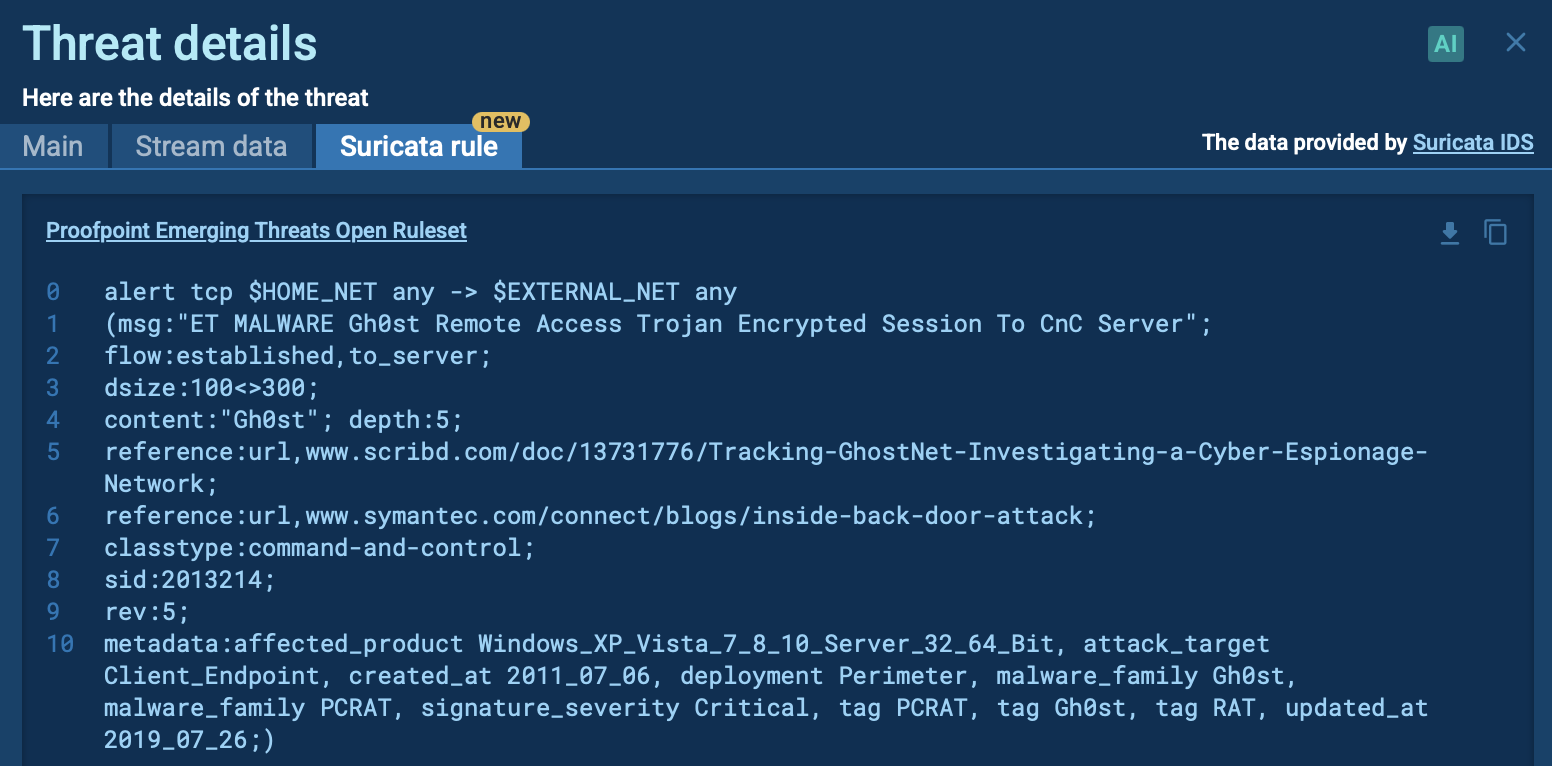
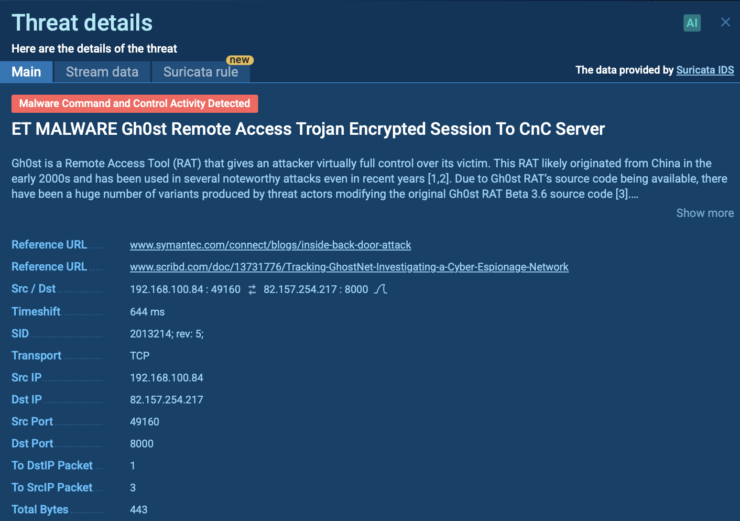
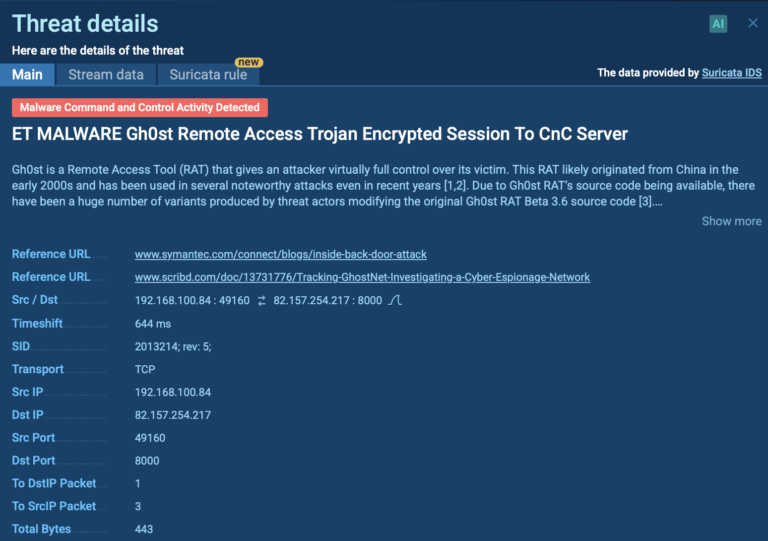
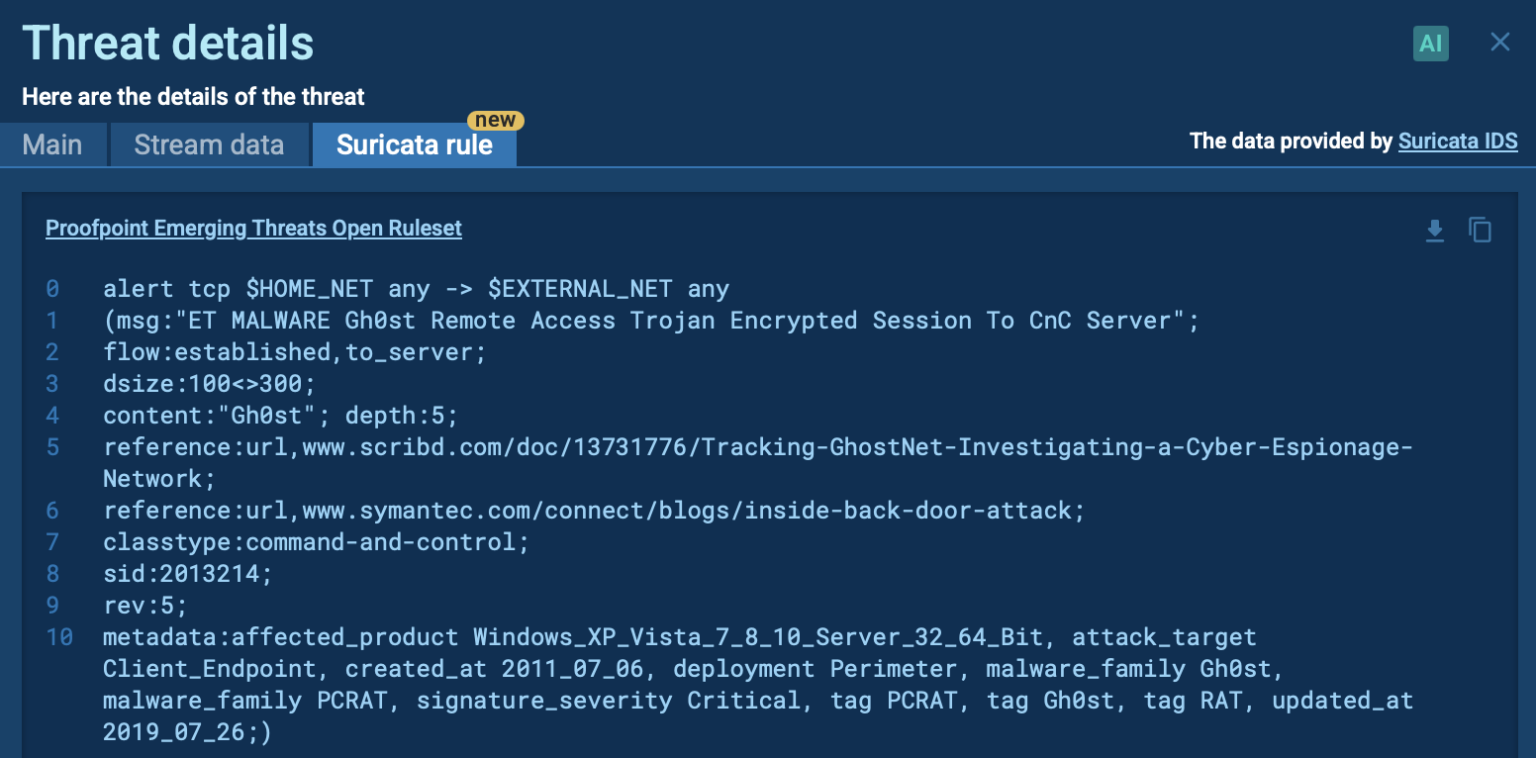
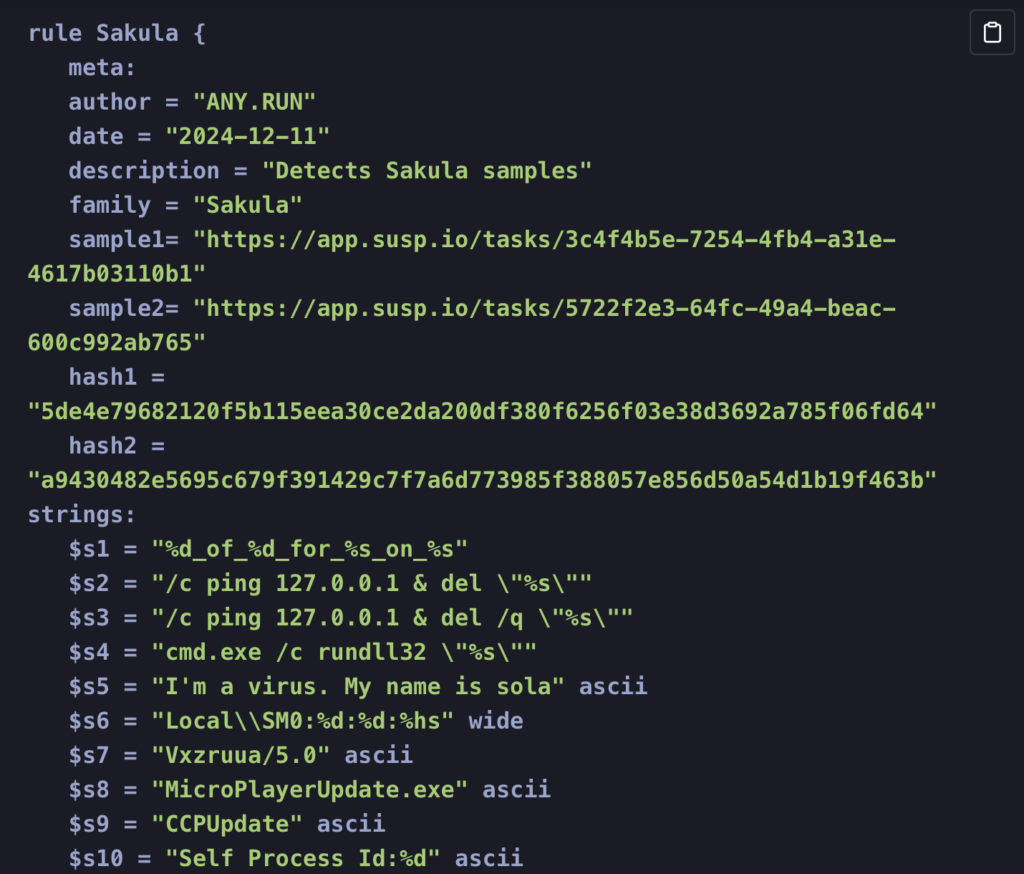
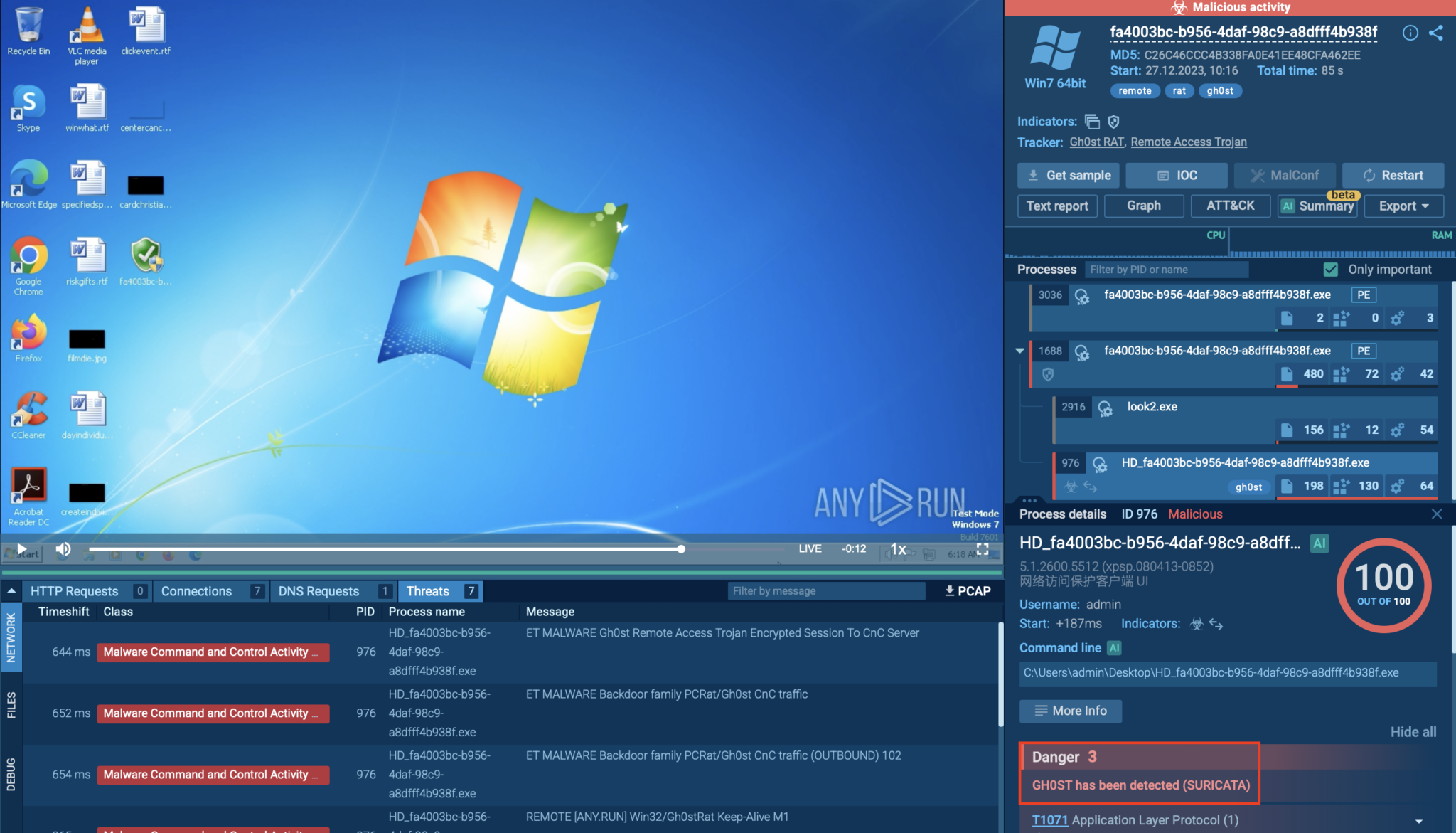
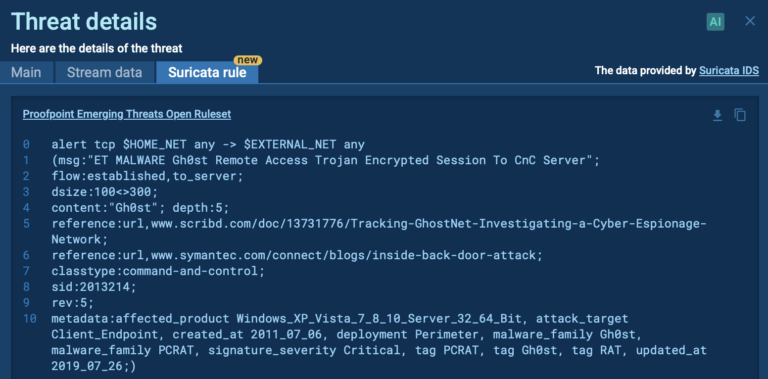
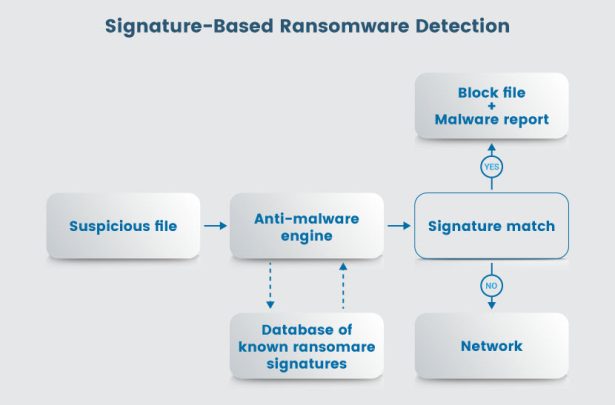
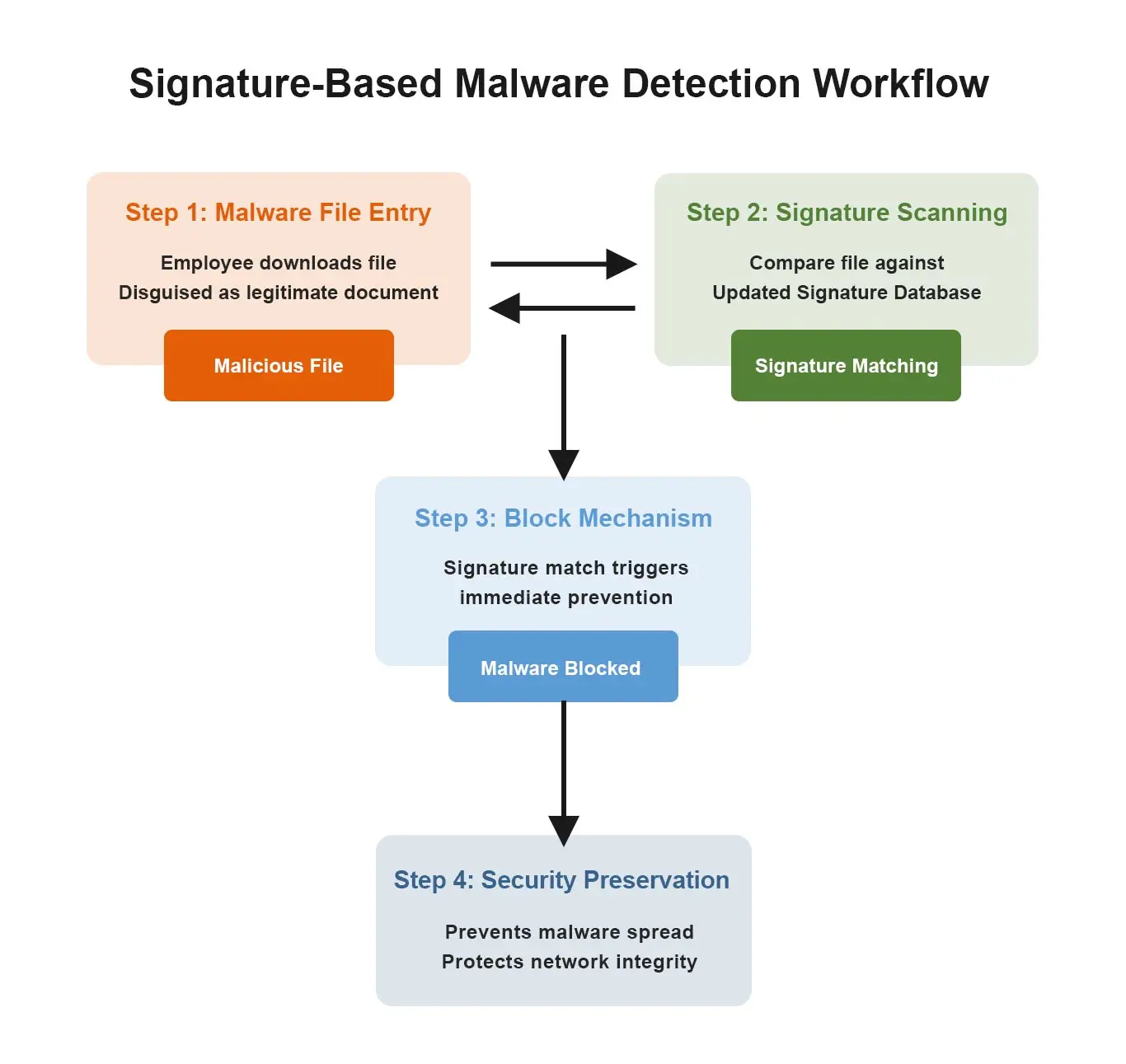
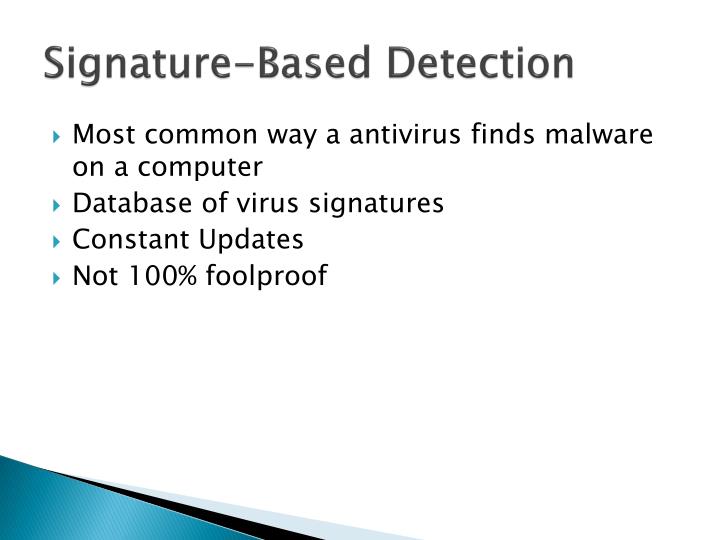
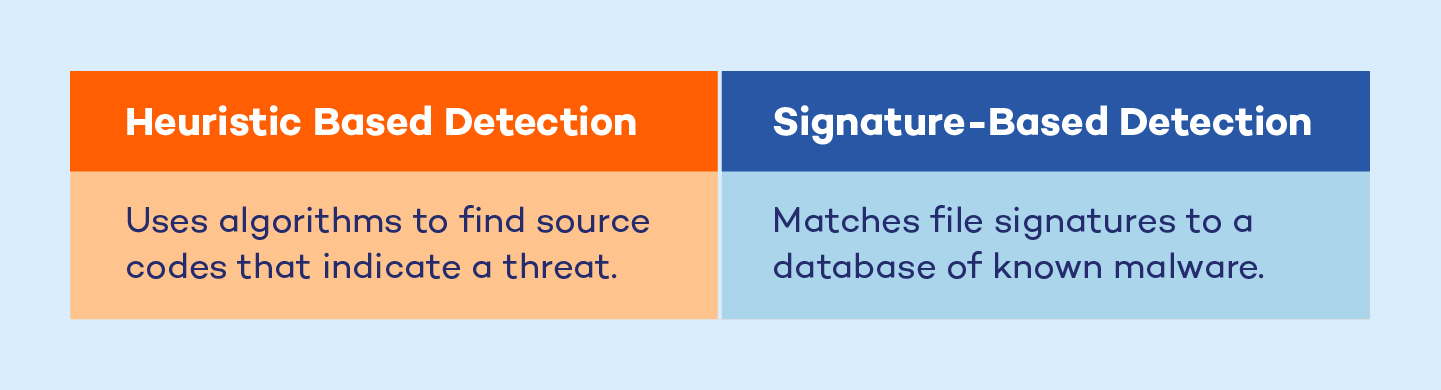
Signature Based Malware Detection
Facilitate learning with our scientific Signature Based Malware Detection gallery of comprehensive galleries of educational images. scientifically documenting photography, images, and pictures. designed to support academic and research goals. The Signature Based Malware Detection collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All Signature Based Malware Detection images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our Signature Based Malware Detection gallery offers diverse visual resources to bring your ideas to life. Comprehensive tagging systems facilitate quick discovery of relevant Signature Based Malware Detection content. Regular updates keep the Signature Based Malware Detection collection current with contemporary trends and styles. Diverse style options within the Signature Based Malware Detection collection suit various aesthetic preferences. Advanced search capabilities make finding the perfect Signature Based Malware Detection image effortless and efficient. Multiple resolution options ensure optimal performance across different platforms and applications. The Signature Based Malware Detection archive serves professionals, educators, and creatives across diverse industries. Cost-effective licensing makes professional Signature Based Malware Detection photography accessible to all budgets. Time-saving browsing features help users locate ideal Signature Based Malware Detection images quickly.











![[Presentasi] VtDirScan - Automated Signature Based Malware Detection ...](https://i.ytimg.com/vi/dcEF_n4aFjE/hqdefault.jpg)









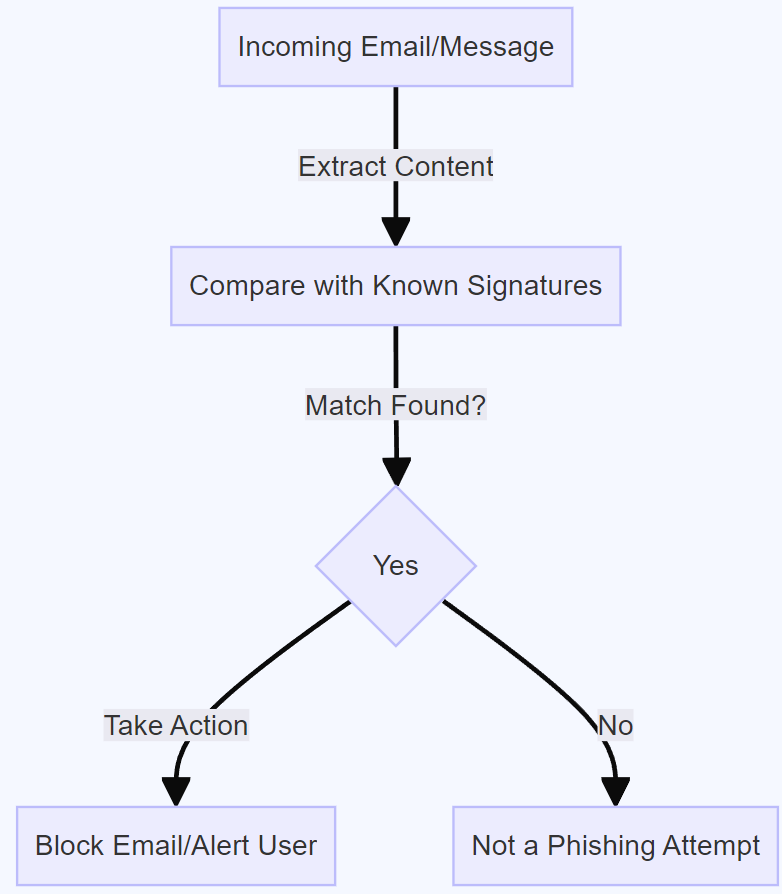










![Methodology used in Signature based IDS [42] | Download Scientific Diagram](https://www.researchgate.net/profile/Md-Jobair-Hossain-Faruk/publication/361581211/figure/fig5/AS:11431281103588435@1669745184866/Methodology-used-in-Signature-based-IDS-42_Q640.jpg)