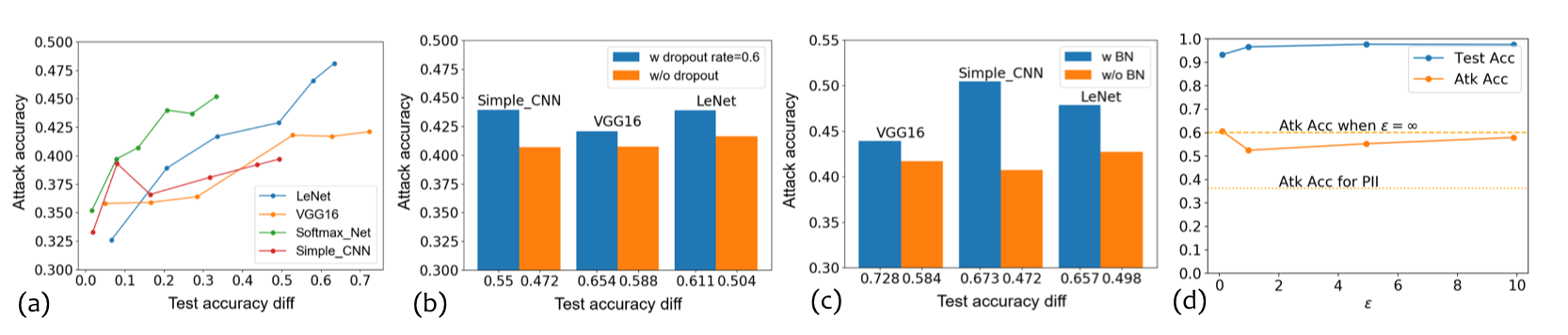
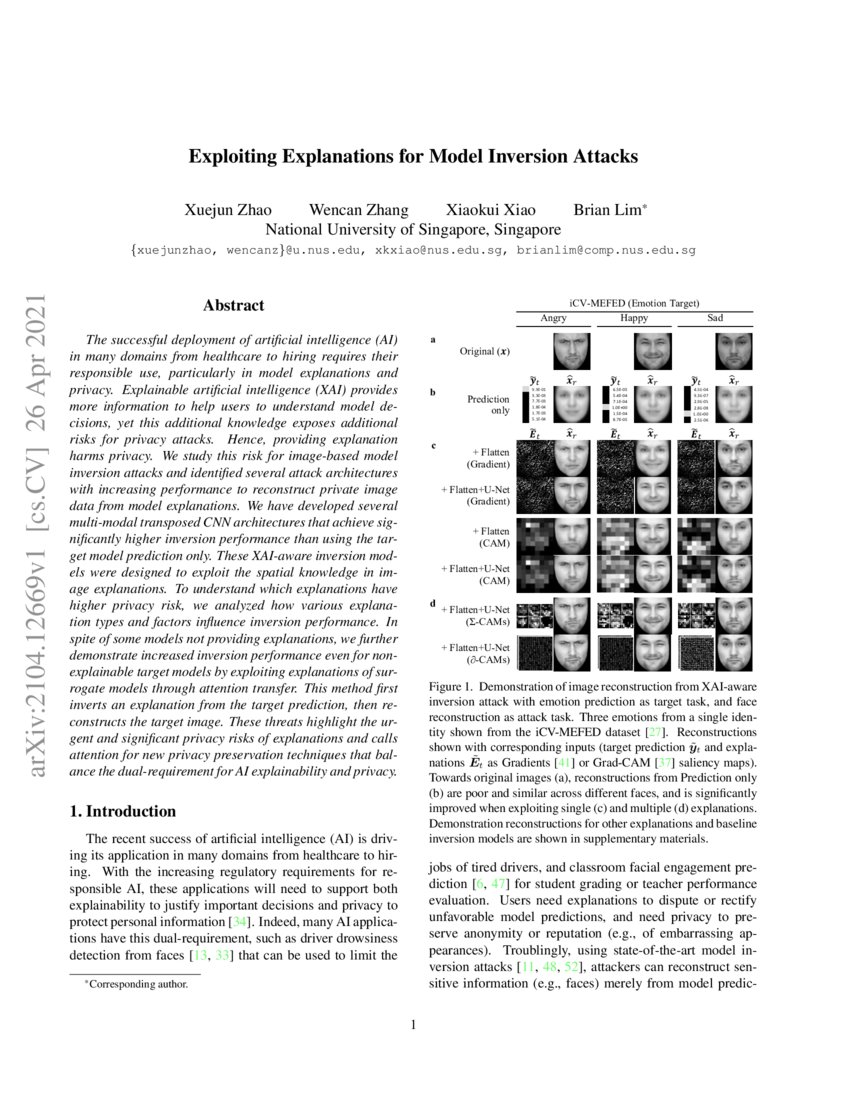
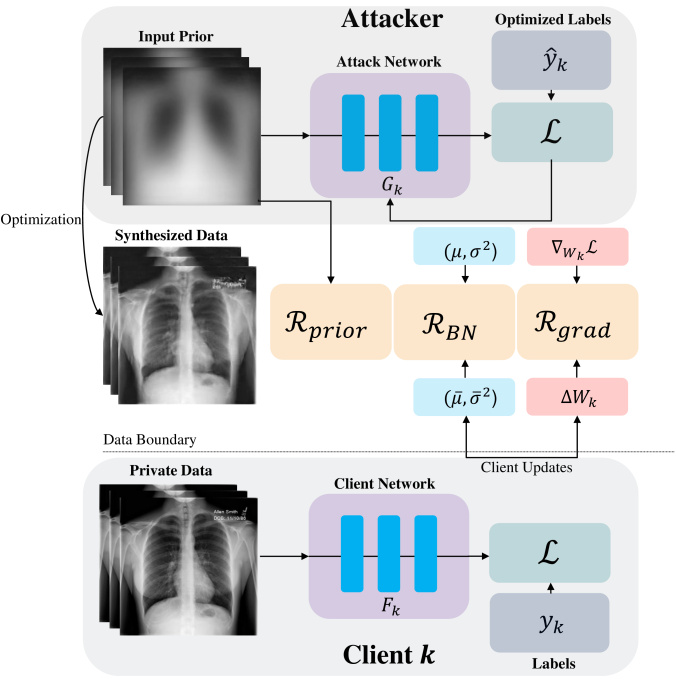
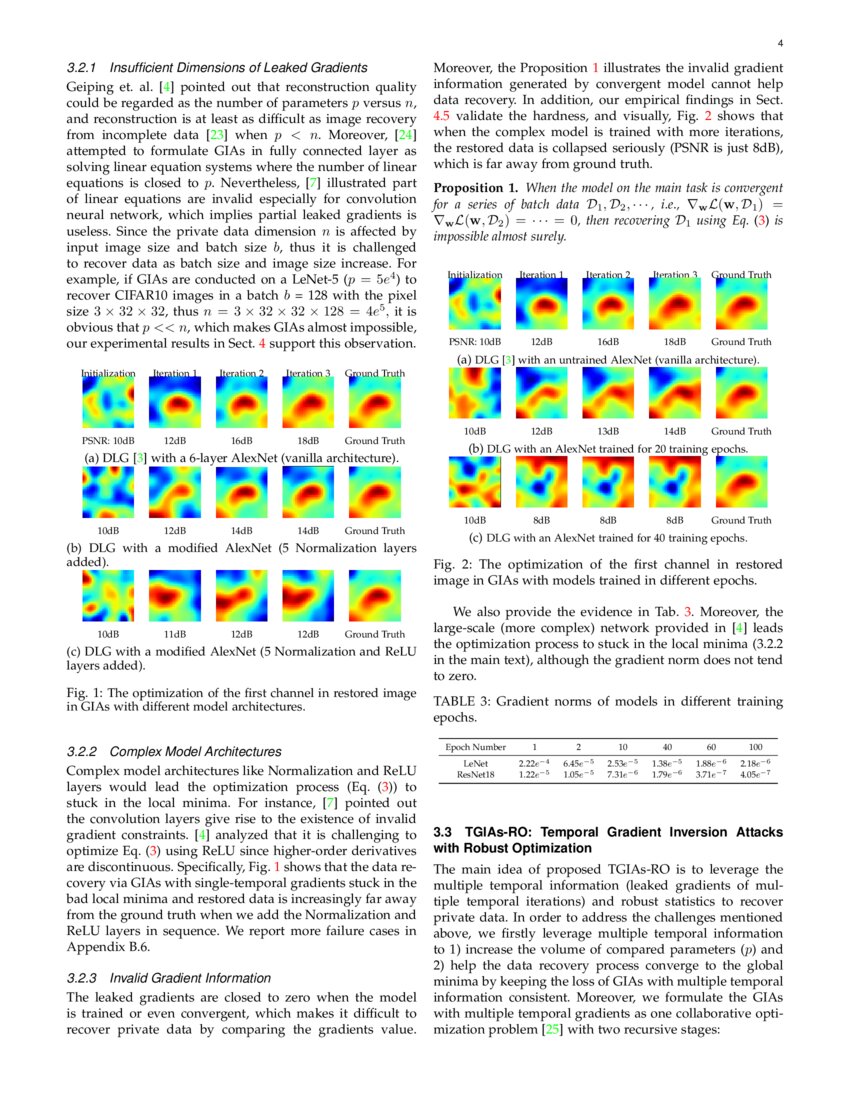
Inversion Attack
Discover the creative potential of Inversion Attack with our artistic gallery of substantial collections of images. expressing the artistic vision of photography, images, and pictures. ideal for creative portfolios and presentations. Our Inversion Attack collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All Inversion Attack images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Inversion Attack collection for various creative and professional projects. Advanced search capabilities make finding the perfect Inversion Attack image effortless and efficient. Reliable customer support ensures smooth experience throughout the Inversion Attack selection process. Each image in our Inversion Attack gallery undergoes rigorous quality assessment before inclusion. Time-saving browsing features help users locate ideal Inversion Attack images quickly. The Inversion Attack archive serves professionals, educators, and creatives across diverse industries. Whether for commercial projects or personal use, our Inversion Attack collection delivers consistent excellence. Comprehensive tagging systems facilitate quick discovery of relevant Inversion Attack content. Multiple resolution options ensure optimal performance across different platforms and applications. Professional licensing options accommodate both commercial and educational usage requirements.


































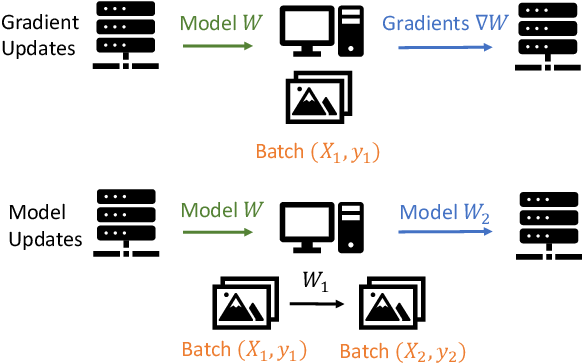




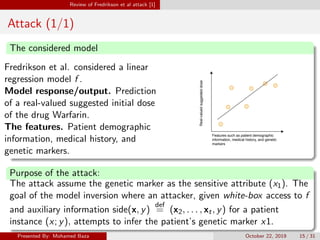


![[ICCV 2021] Exploiting Explanations for Model Inversion Attacks - YouTube](https://i.ytimg.com/vi/iAzB0Jo2Ek8/maxresdefault.jpg)




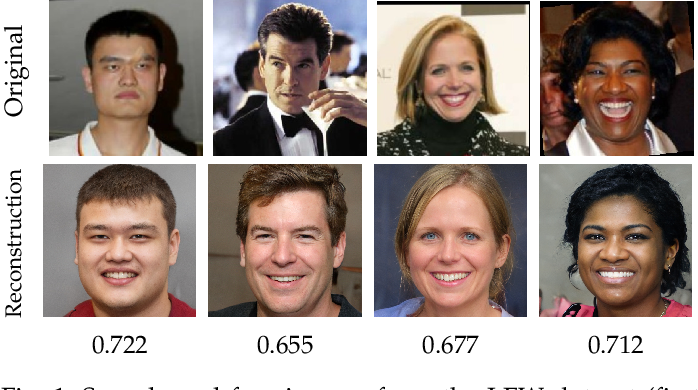
![[2501.18934] Deep Learning Model Inversion Attacks and Defenses: A ...](https://ar5iv.labs.arxiv.org/html/2501.18934/assets/Fig_MIA_example.jpg)































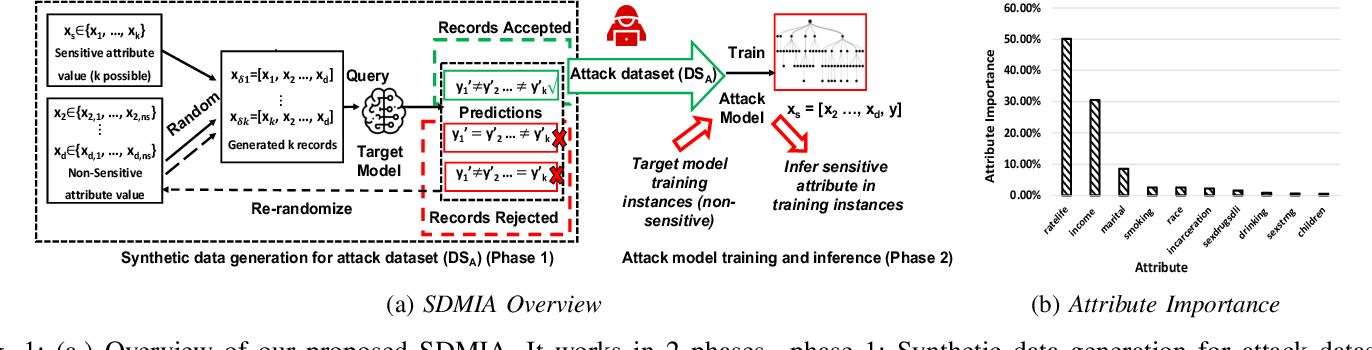
![[论文阅读系列2]Model Inversion Attacks that Exploit Confidence Information ...](https://pic2.zhimg.com/v2-2b8e2372d8408fd446e0263fa79b2565_r.jpg)