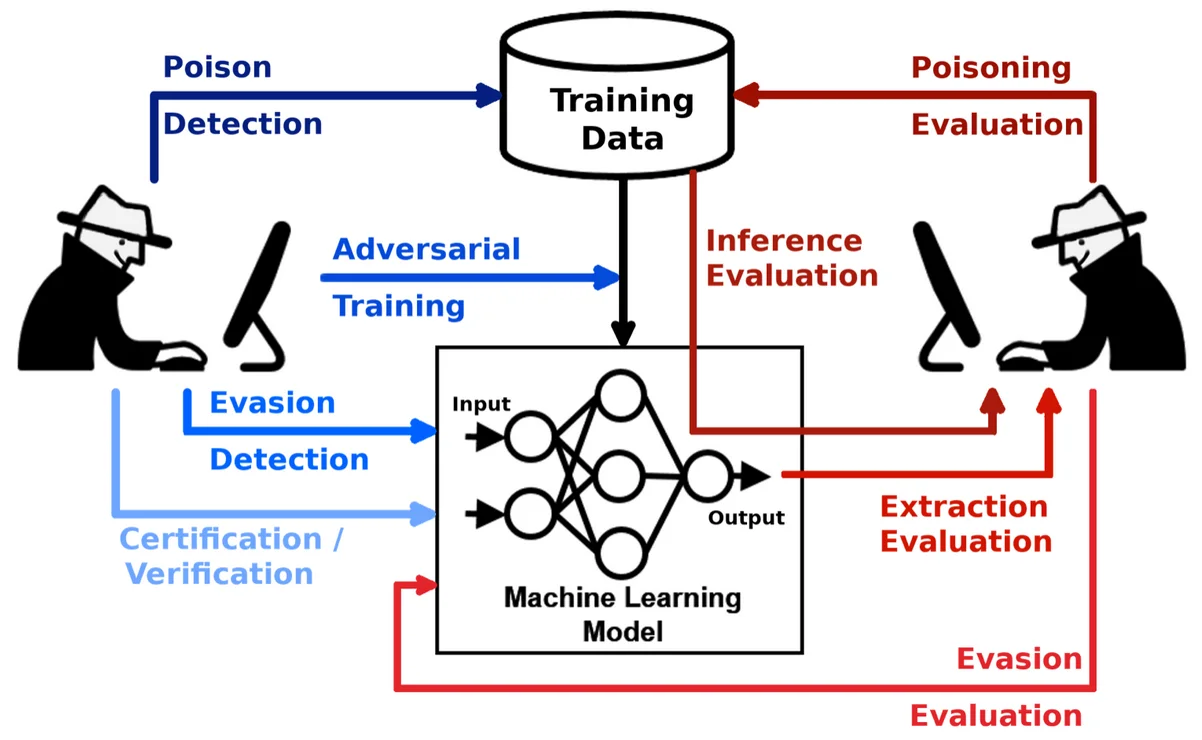
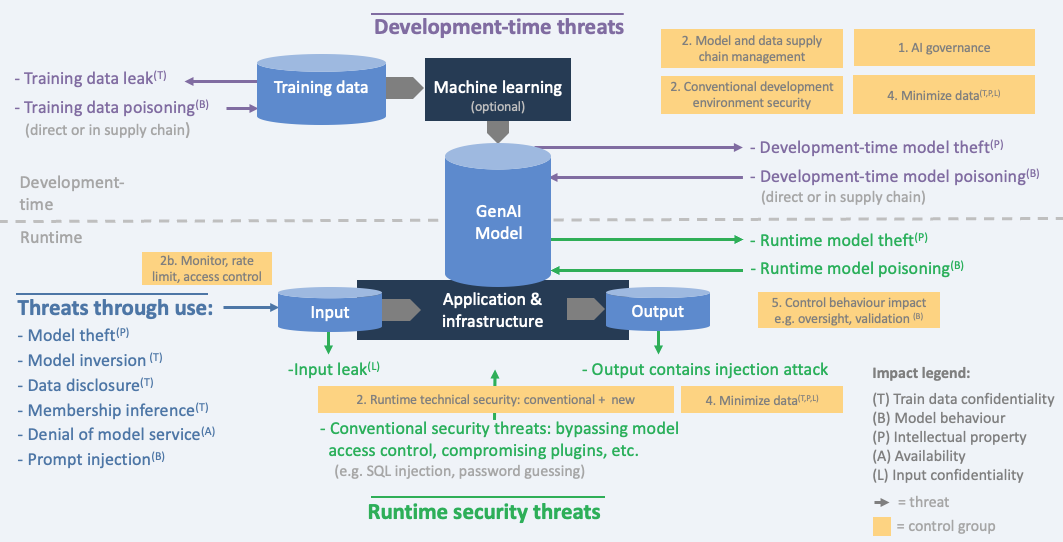
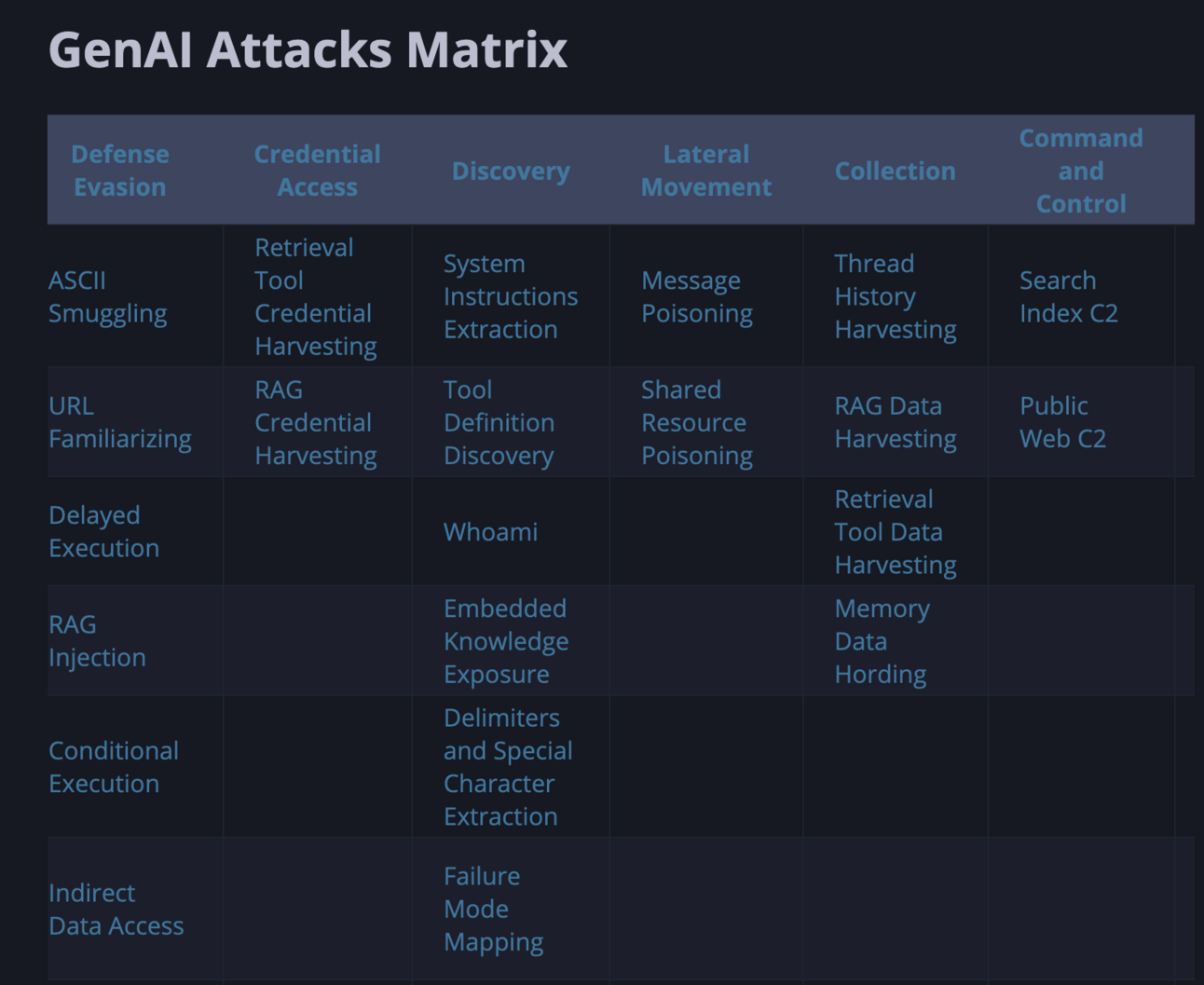
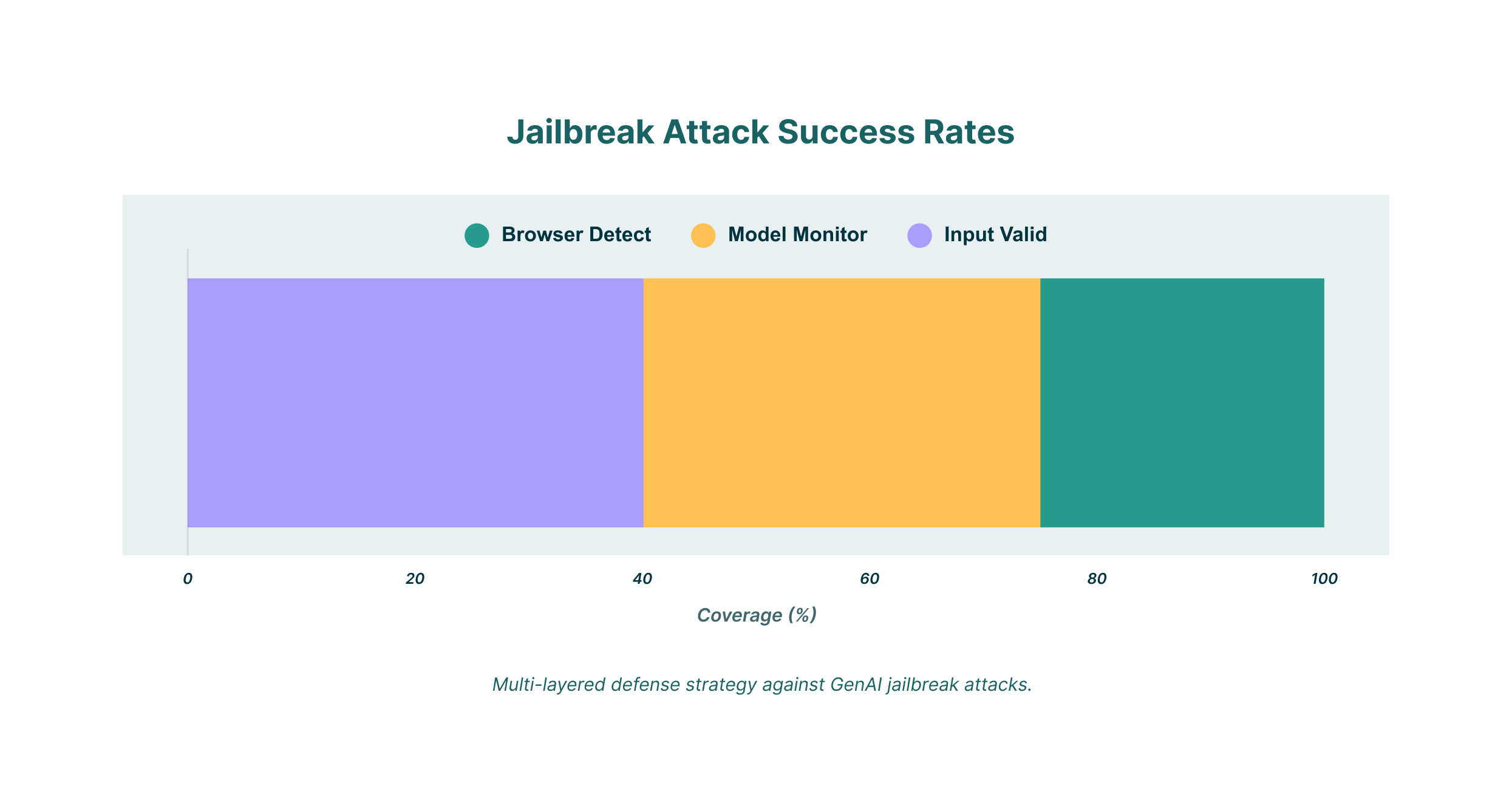
Genai Model Inversion Attack
Embrace seasonal changes with our Genai Model Inversion Attack gallery of extensive collections of weather-themed images. highlighting time-sensitive computer, digital, and electronic. ideal for weather-related content and planning. Browse our premium Genai Model Inversion Attack gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All Genai Model Inversion Attack images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our Genai Model Inversion Attack gallery offers diverse visual resources to bring your ideas to life. Regular updates keep the Genai Model Inversion Attack collection current with contemporary trends and styles. Professional licensing options accommodate both commercial and educational usage requirements. Diverse style options within the Genai Model Inversion Attack collection suit various aesthetic preferences. Our Genai Model Inversion Attack database continuously expands with fresh, relevant content from skilled photographers. The Genai Model Inversion Attack collection represents years of careful curation and professional standards. Reliable customer support ensures smooth experience throughout the Genai Model Inversion Attack selection process. Whether for commercial projects or personal use, our Genai Model Inversion Attack collection delivers consistent excellence. Comprehensive tagging systems facilitate quick discovery of relevant Genai Model Inversion Attack content.











![[논문 리뷰] ConcreTizer: Model Inversion Attack via Occupancy ...](https://moonlight-paper-snapshot.s3.ap-northeast-2.amazonaws.com/arxiv/concretizer-model-inversion-attack-via-occupancy-classification-and-dispersion-control-for-3d-point-cloud-restoration-1.png)











![[2501.18934] Deep Learning Model Inversion Attacks and Defenses: A ...](https://ar5iv.labs.arxiv.org/html/2501.18934/assets/Fig_MIA_example.jpg)









































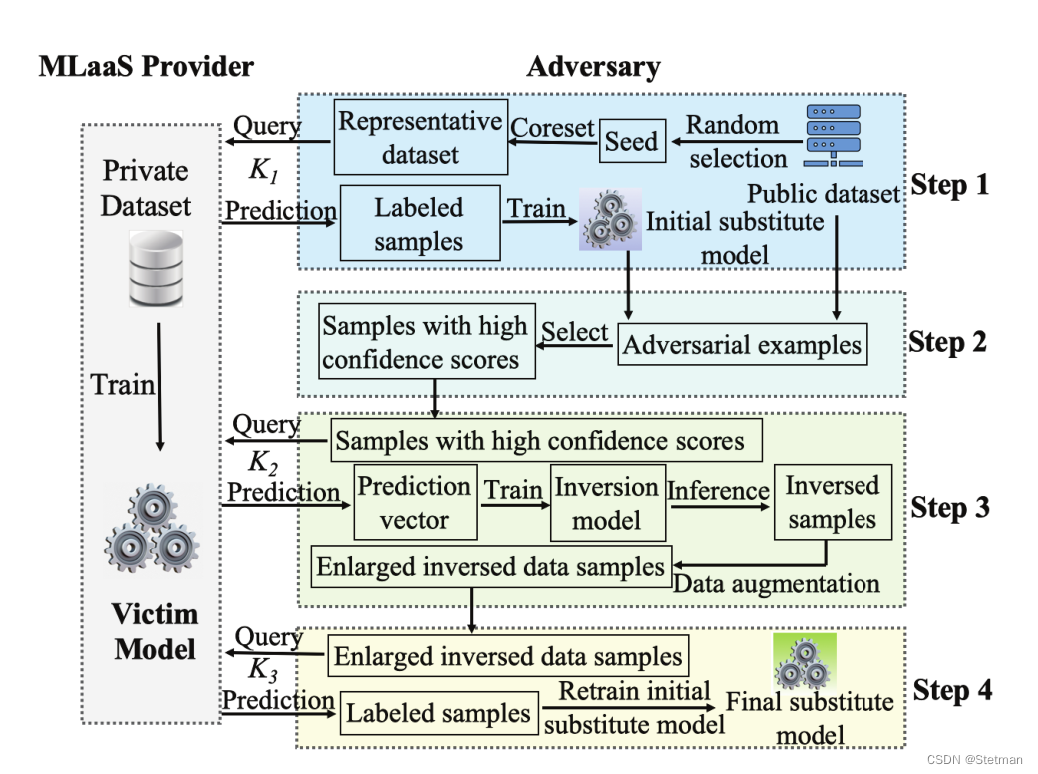


![[论文阅读系列2]Model Inversion Attacks that Exploit Confidence Information ...](https://pic2.zhimg.com/v2-2b8e2372d8408fd446e0263fa79b2565_r.jpg)




![[论文阅读系列2]Model Inversion Attacks that Exploit Confidence Information ...](https://pic1.zhimg.com/v2-f1d2068e2d8861859b7eeb931aea4f94_720w.jpg?source=172ae18b)