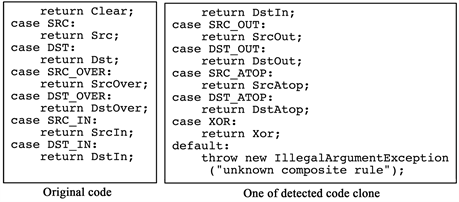
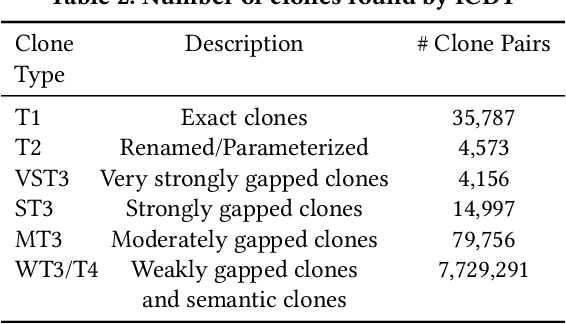
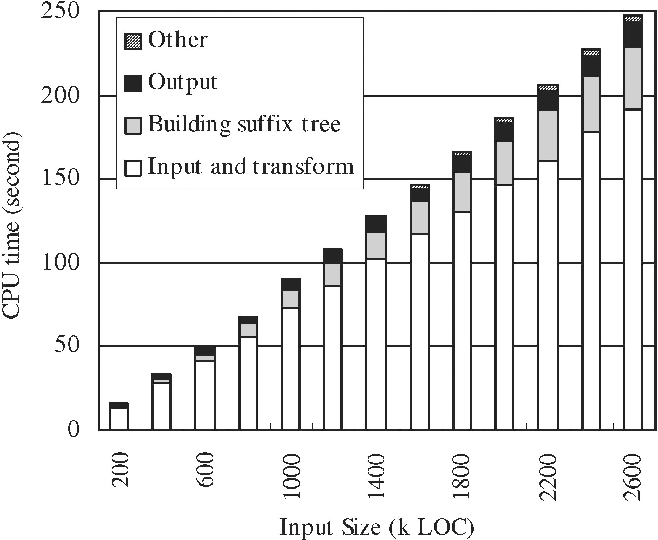
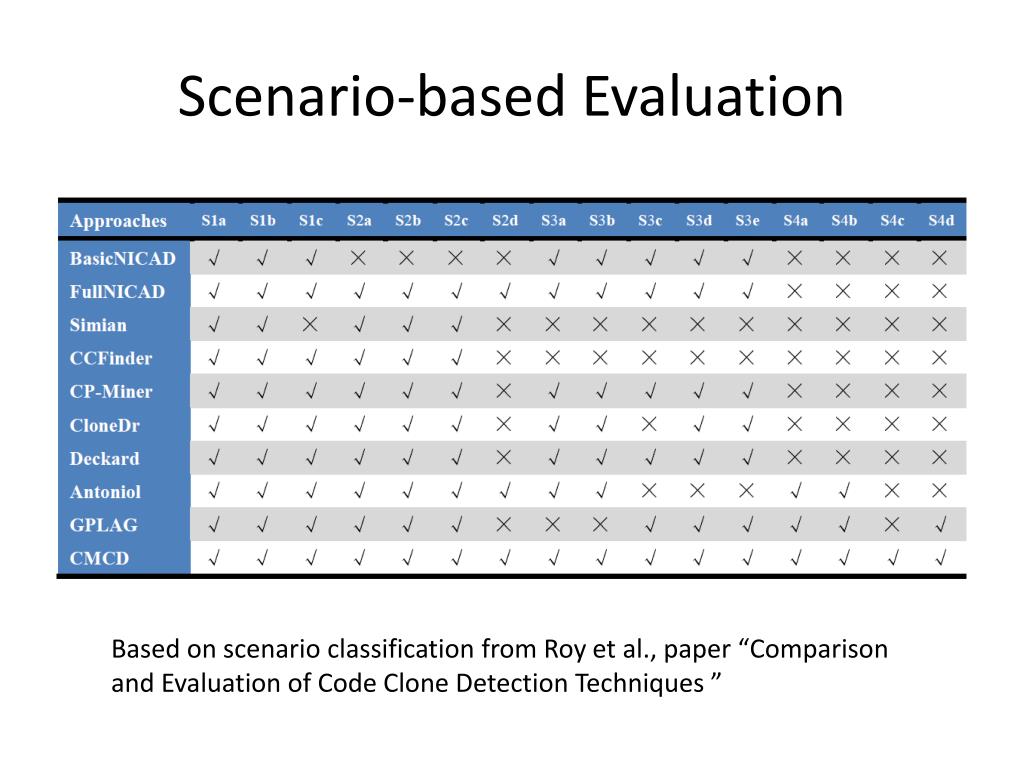
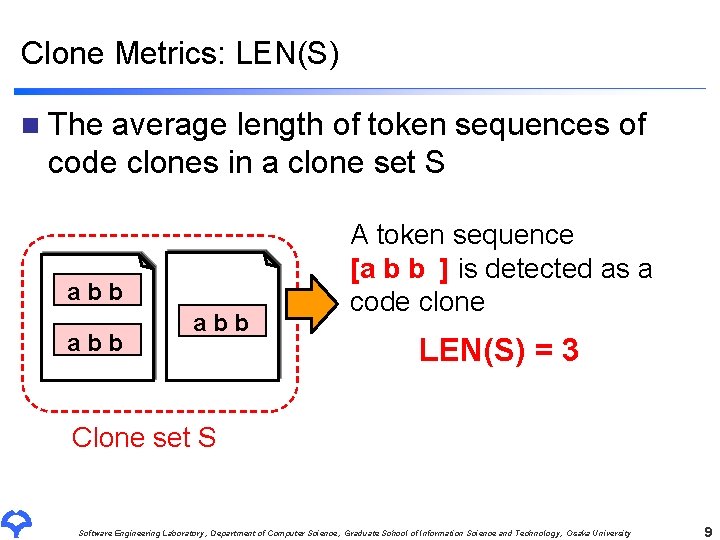
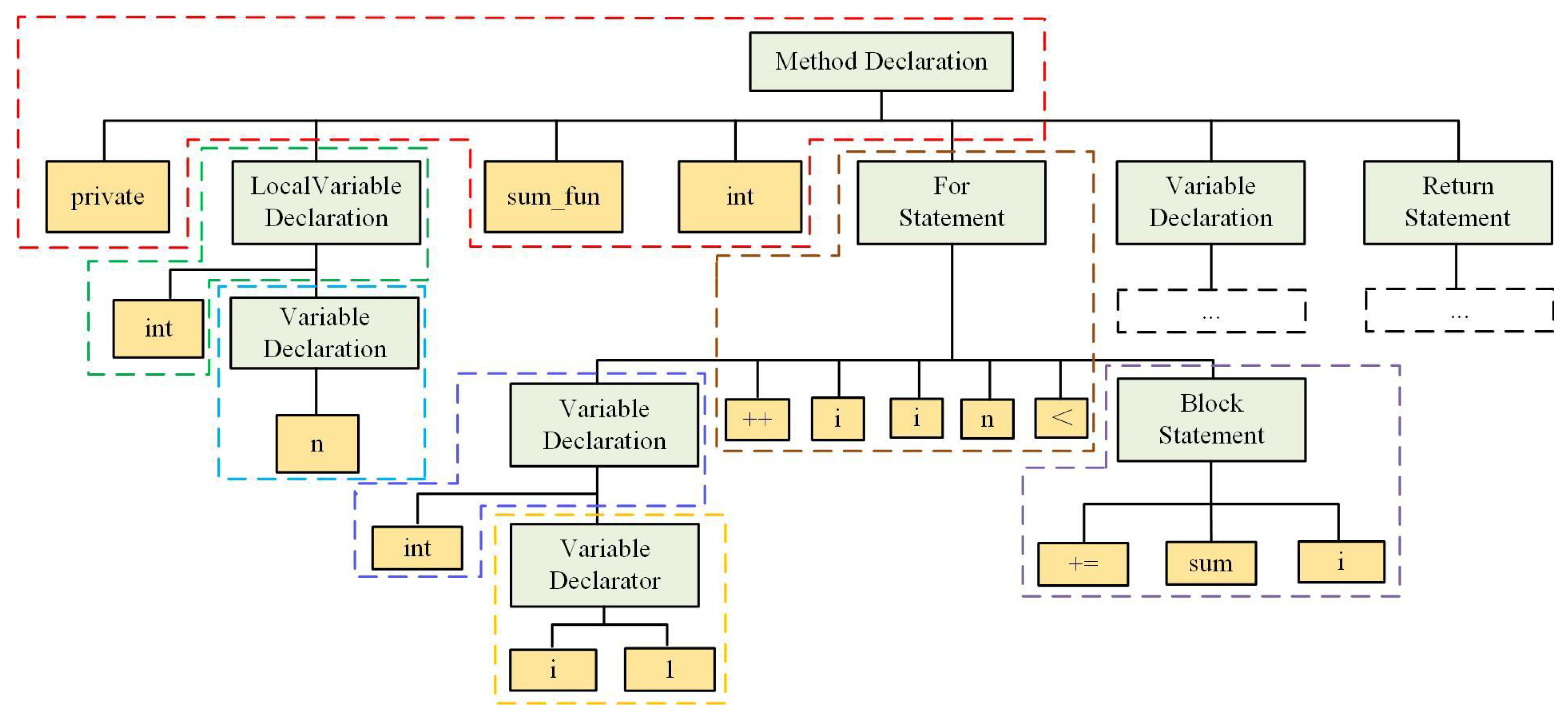
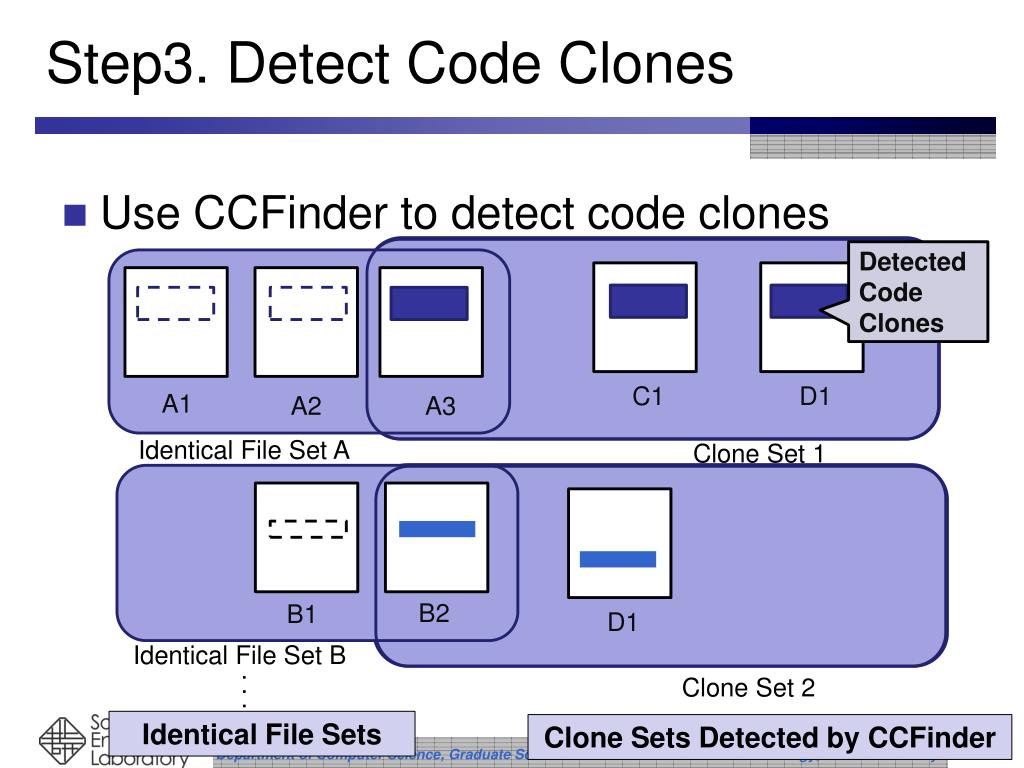
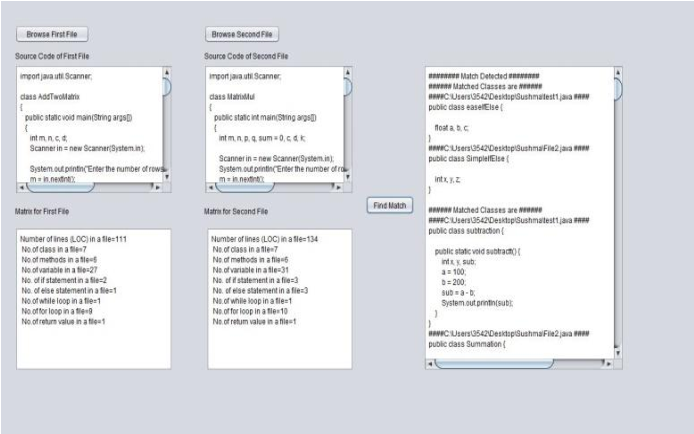
Explore the latest trends in (pdf) multi-threshold token-based code clone detection with our collection of substantial collections of contemporary images. highlighting modern interpretations of photography, images, and pictures. perfect for trend-focused marketing and design. Discover high-resolution (pdf) multi-threshold token-based code clone detection images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All (pdf) multi-threshold token-based code clone detection images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our (pdf) multi-threshold token-based code clone detection collection for various creative and professional projects. Cost-effective licensing makes professional (pdf) multi-threshold token-based code clone detection photography accessible to all budgets. Instant download capabilities enable immediate access to chosen (pdf) multi-threshold token-based code clone detection images. Advanced search capabilities make finding the perfect (pdf) multi-threshold token-based code clone detection image effortless and efficient. Reliable customer support ensures smooth experience throughout the (pdf) multi-threshold token-based code clone detection selection process. Whether for commercial projects or personal use, our (pdf) multi-threshold token-based code clone detection collection delivers consistent excellence. The (pdf) multi-threshold token-based code clone detection archive serves professionals, educators, and creatives across diverse industries.





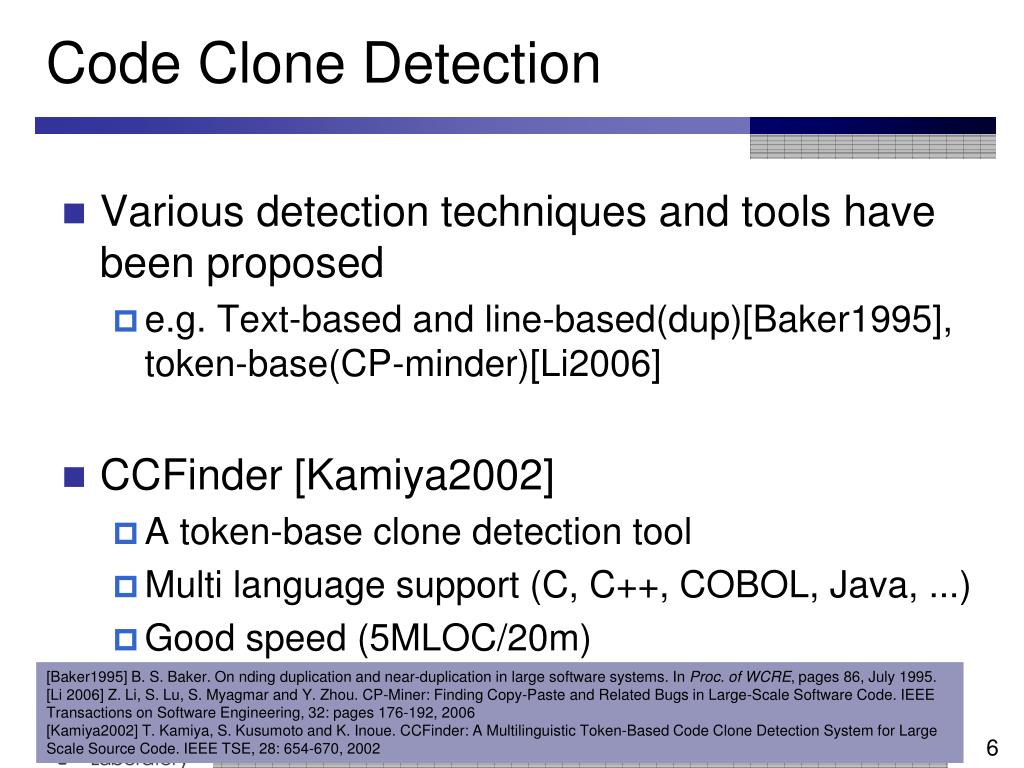

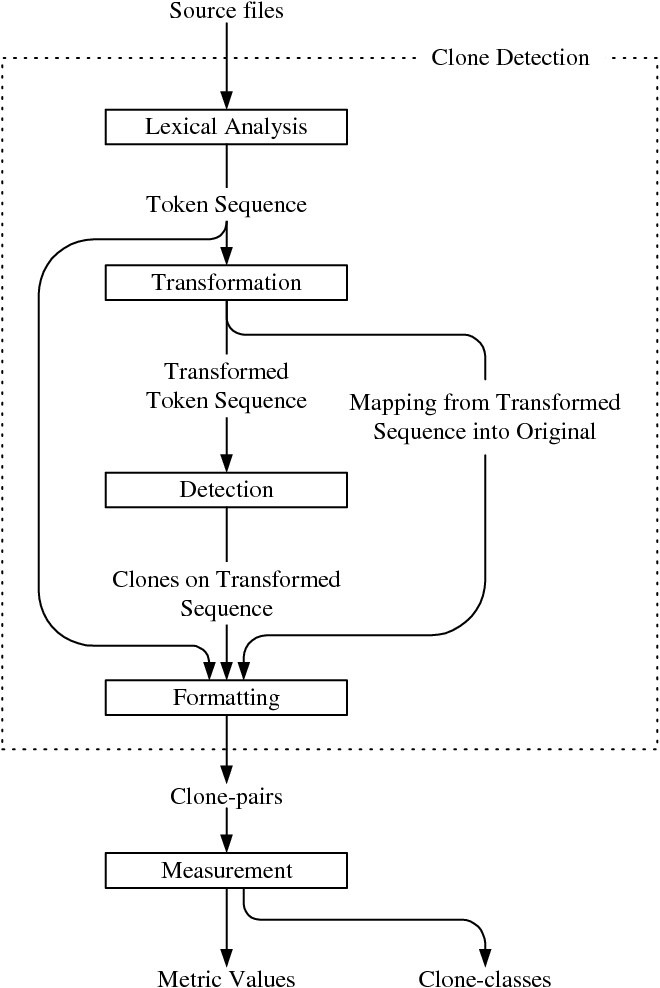





![Code clone detection process by Xue et al. [140]. | Download Scientific ...](https://www.researchgate.net/profile/Hongfa-Xue/publication/333118141/figure/fig8/AS:765081897934849@1559421147721/Code-clone-detection-process-by-Xue-et-al-140.png)
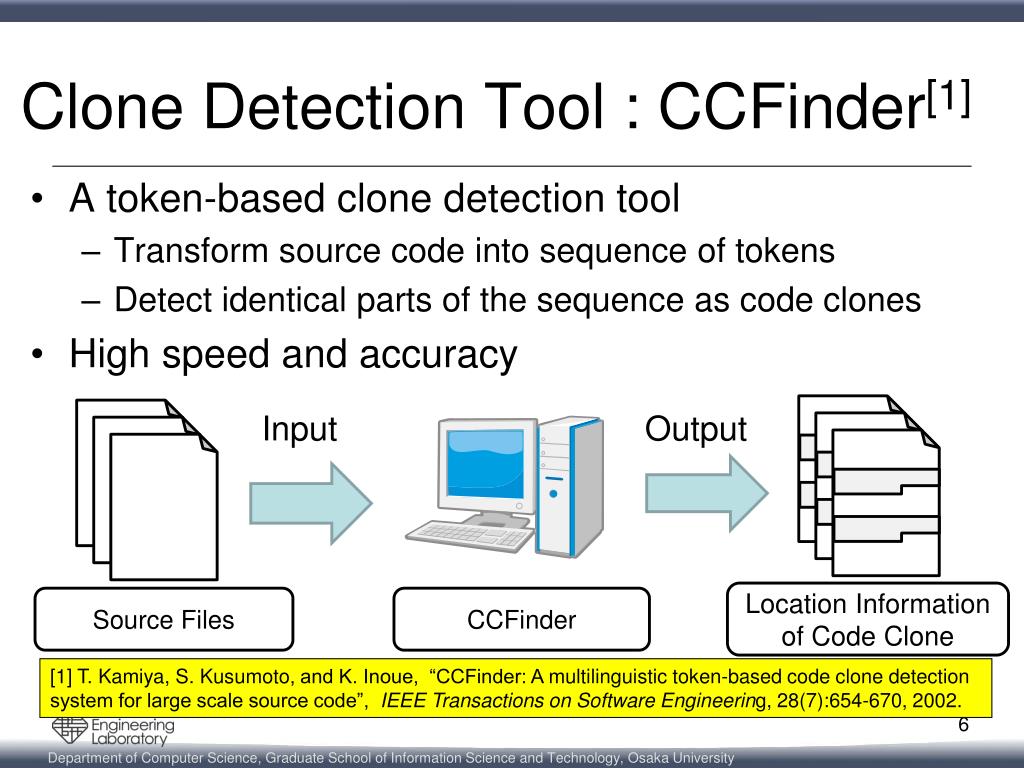

![Generic Code Clone Detection Process [8] | Download Scientific Diagram](https://www.researchgate.net/profile/Al-Fahim-Mubarak-Ali/publication/284593602/figure/fig1/AS:299563387768832@1448432885316/Generic-Code-Clone-Detection-Process-8.png)
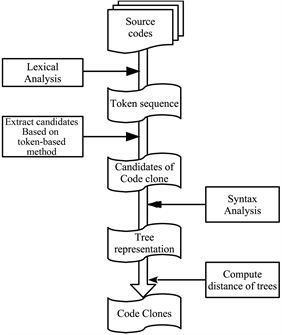









![[2405.00428] CC2Vec: Combining Typed Tokens with Contrastive Learning ...](https://ar5iv.labs.arxiv.org/html/2405.00428/assets/x2.png)