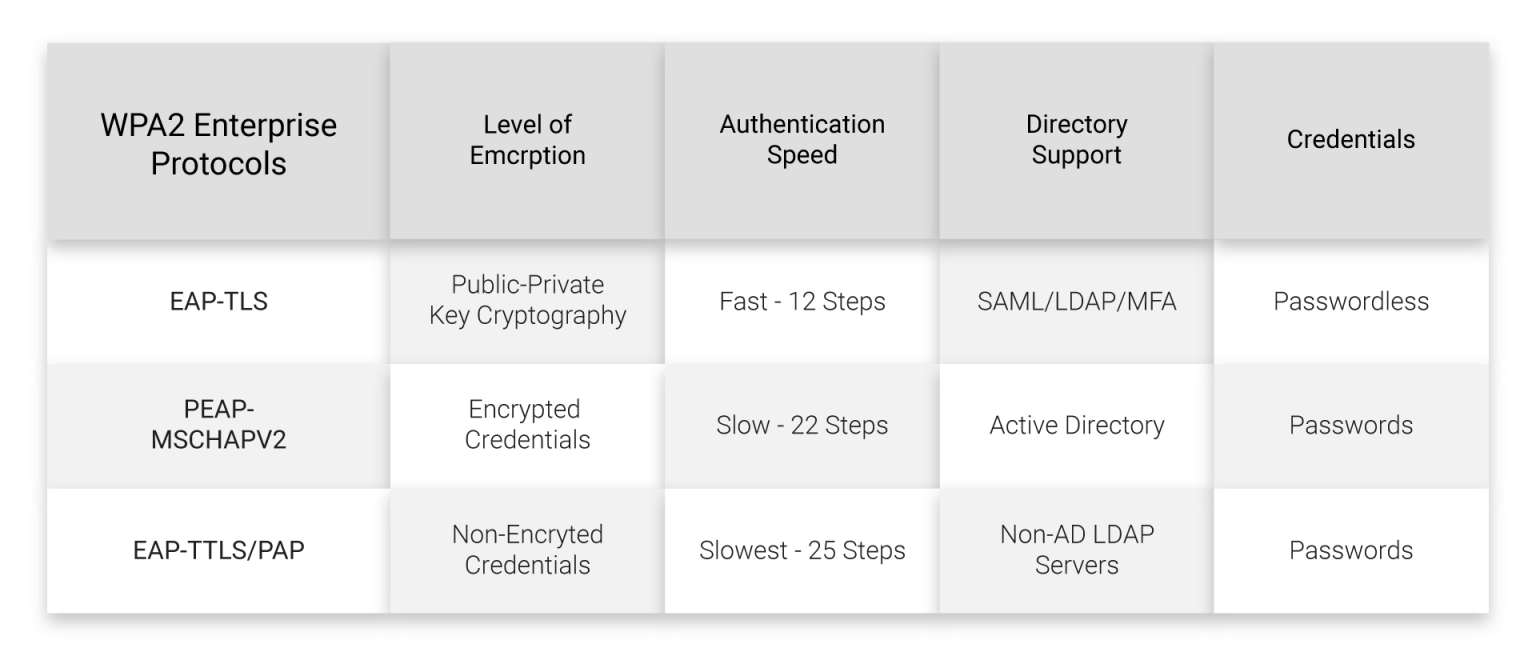
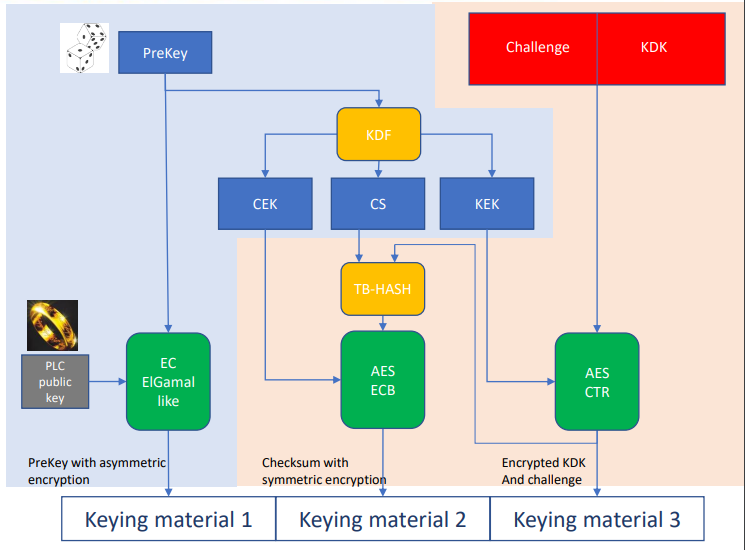
Embrace the aesthetic appeal of comparison of the isi of the authentication protocols. | download with our gallery of extensive collections of creative photographs. blending traditional techniques with contemporary artistic interpretation. inspiring creativity and emotional connection through visual excellence. Browse our premium comparison of the isi of the authentication protocols. | download gallery featuring professionally curated photographs. Ideal for artistic projects, creative designs, digital art, and innovative visual expressions All comparison of the isi of the authentication protocols. | download images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our comparison of the isi of the authentication protocols. | download collection inspires creativity through unique compositions and artistic perspectives. Our comparison of the isi of the authentication protocols. | download database continuously expands with fresh, relevant content from skilled photographers. Cost-effective licensing makes professional comparison of the isi of the authentication protocols. | download photography accessible to all budgets. Instant download capabilities enable immediate access to chosen comparison of the isi of the authentication protocols. | download images. The comparison of the isi of the authentication protocols. | download collection represents years of careful curation and professional standards. Comprehensive tagging systems facilitate quick discovery of relevant comparison of the isi of the authentication protocols. | download content.









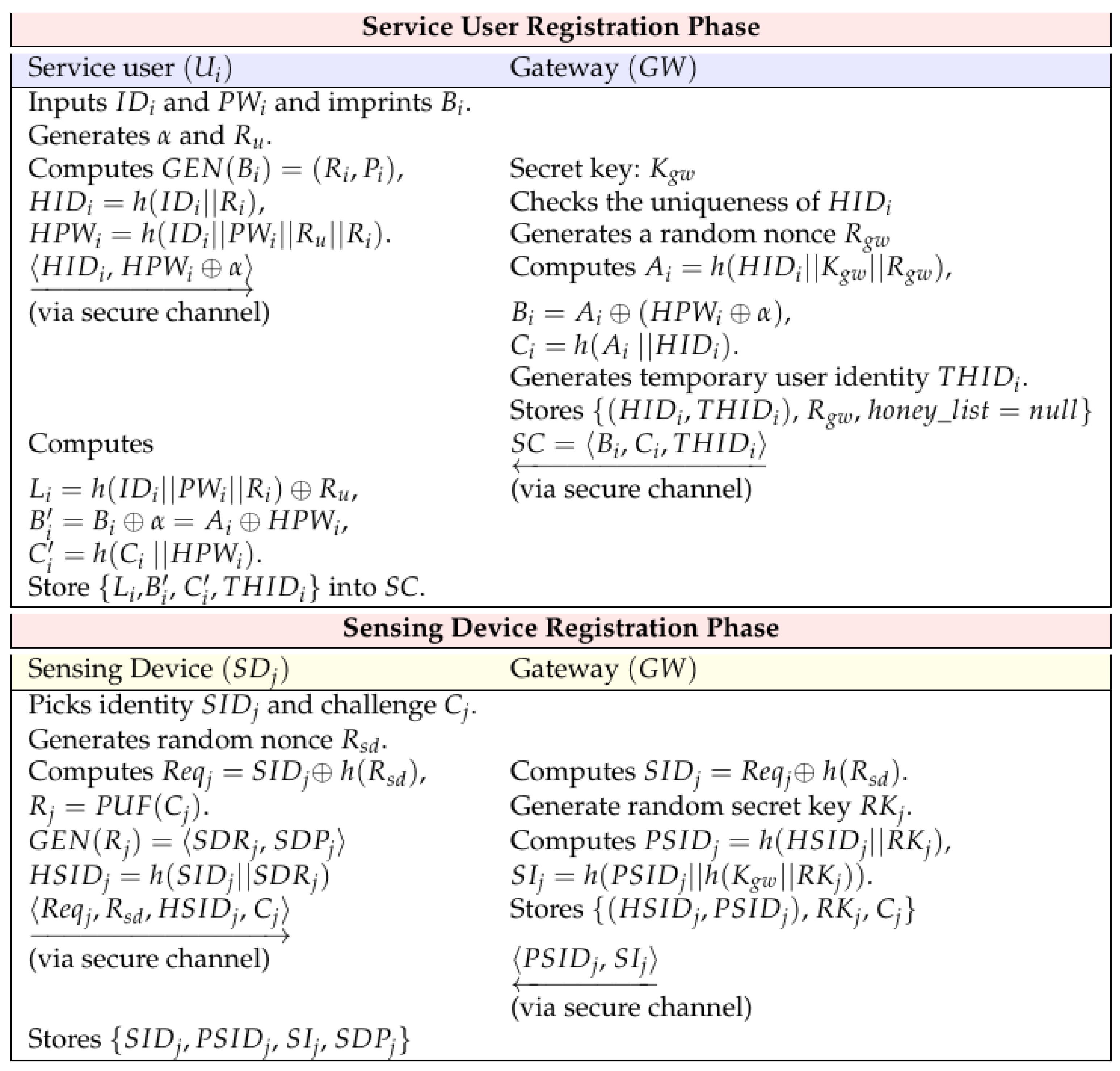
![[Article] Authentication Protocols Comparison and Analysis](https://wso2.com/files/Untitled.png)


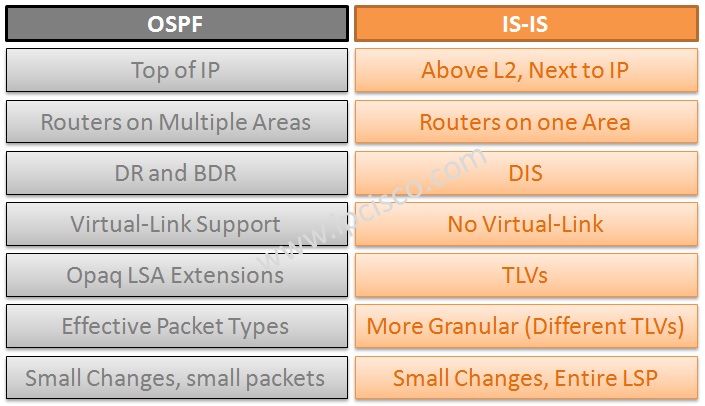





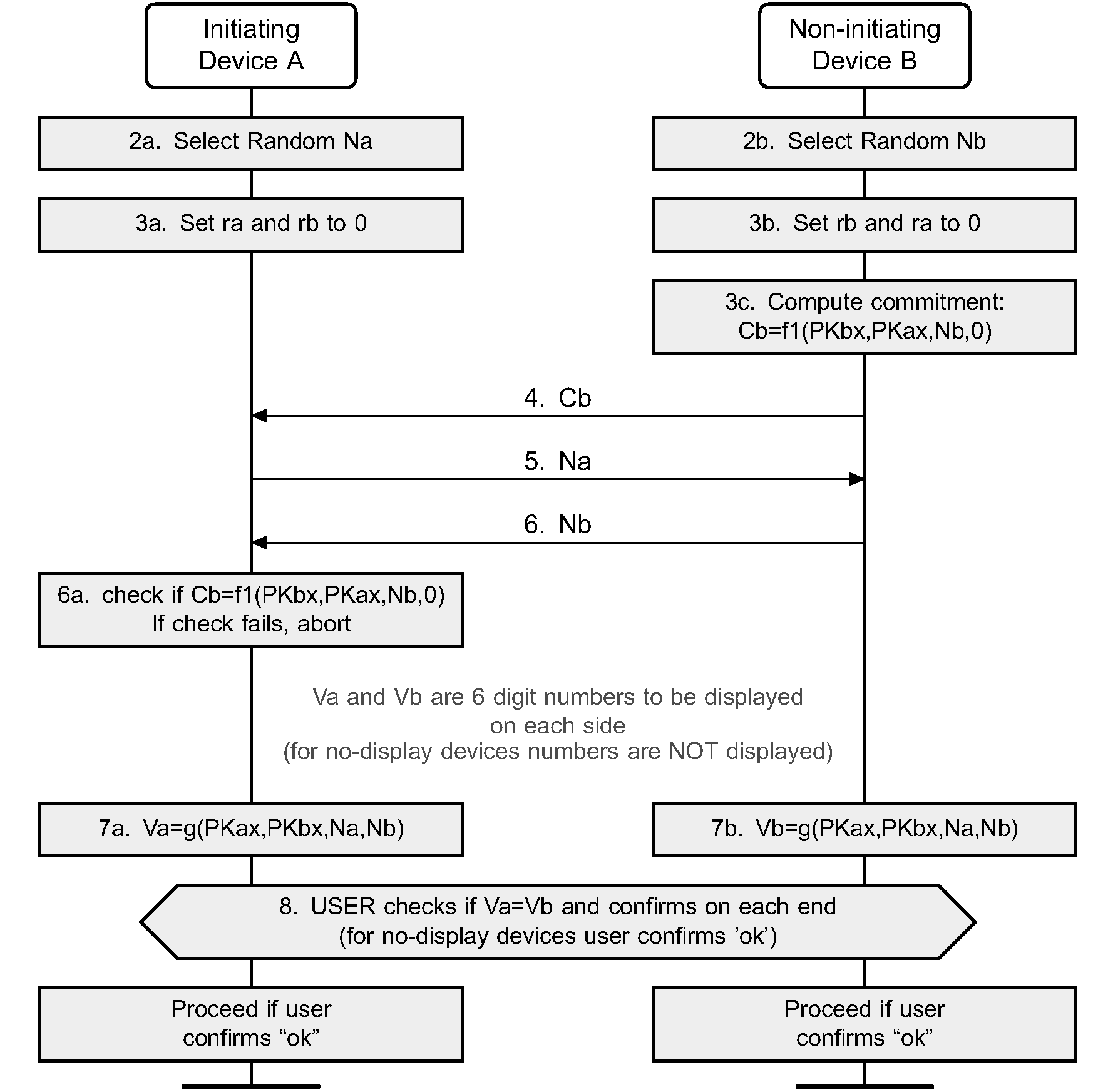


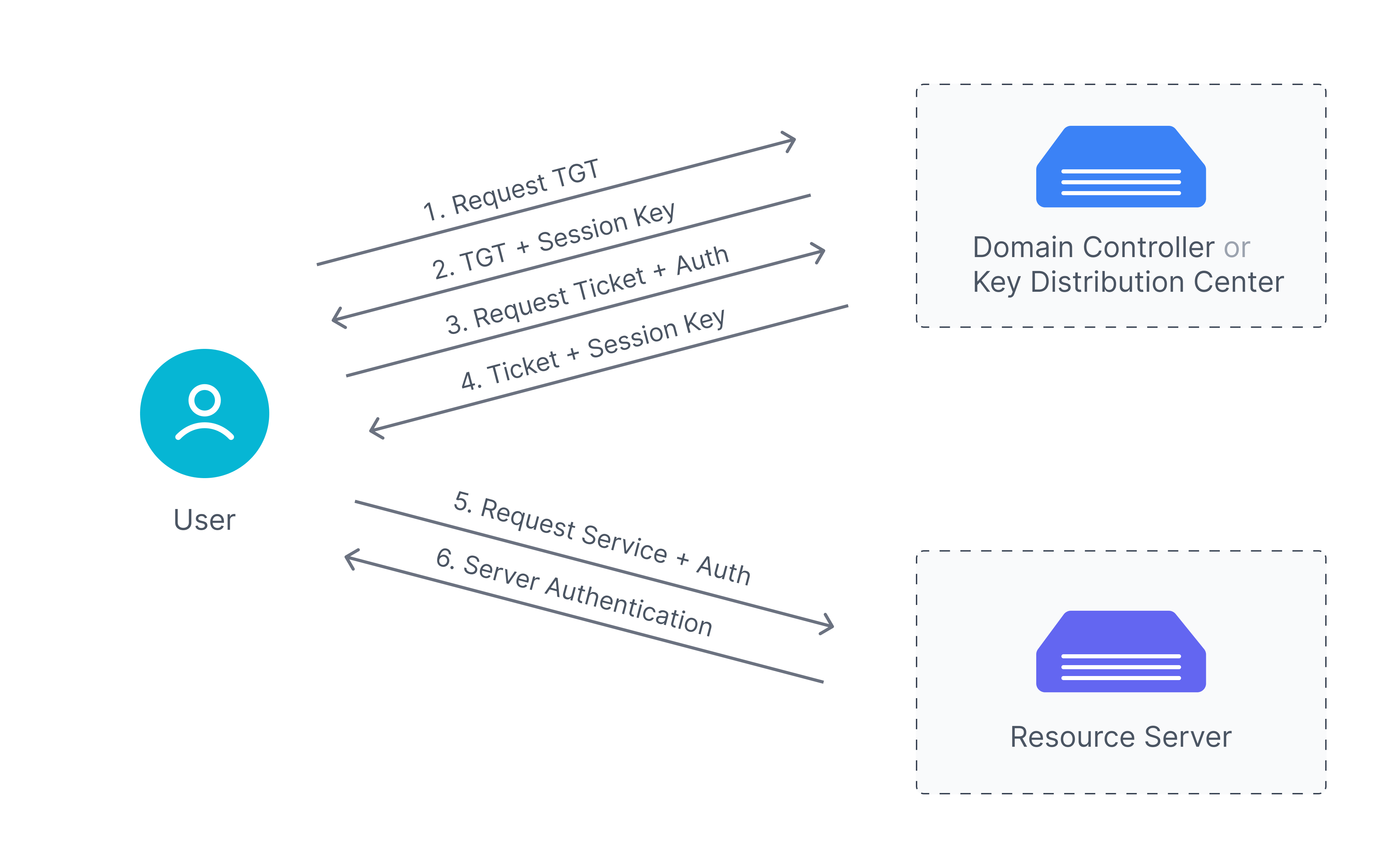

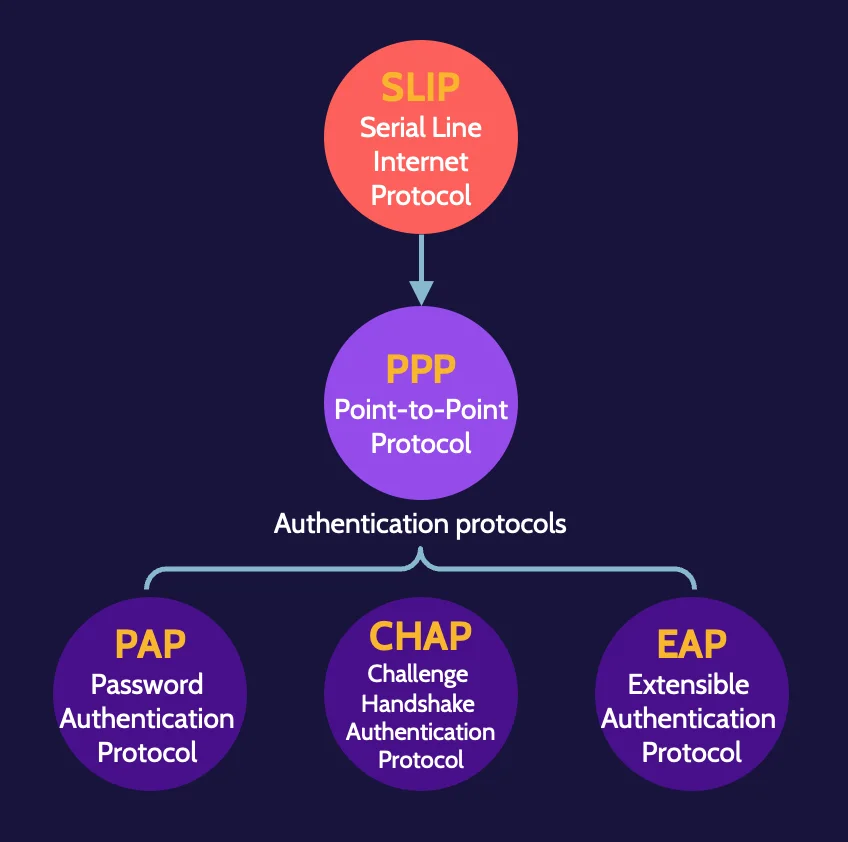
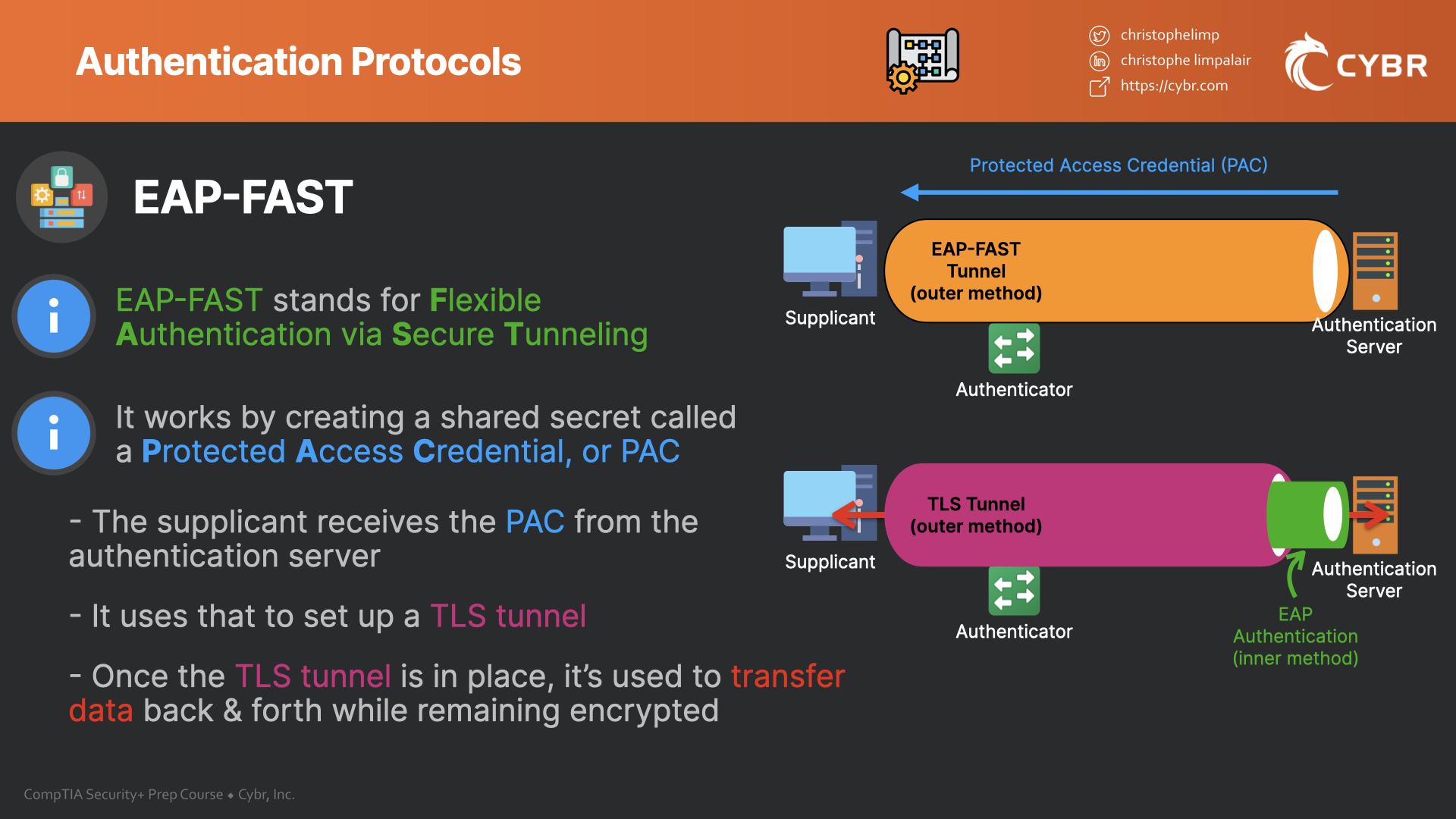






















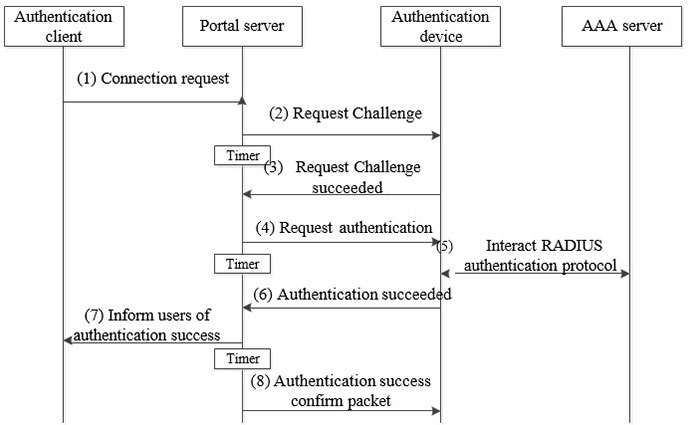
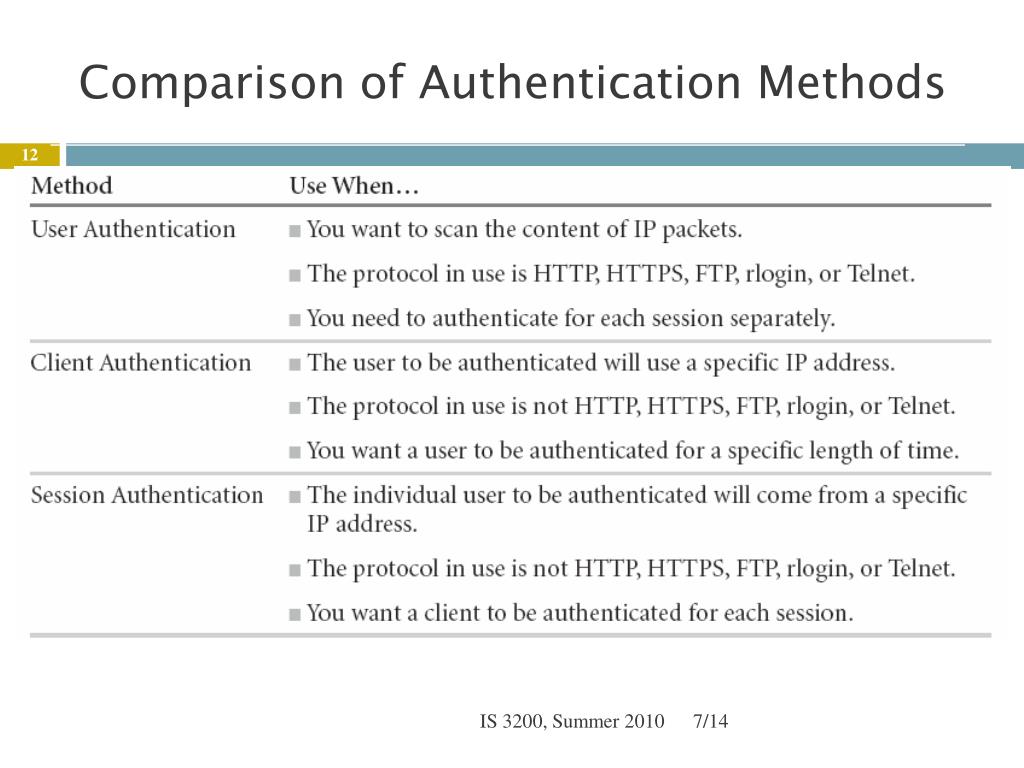








+protocol.jpg)


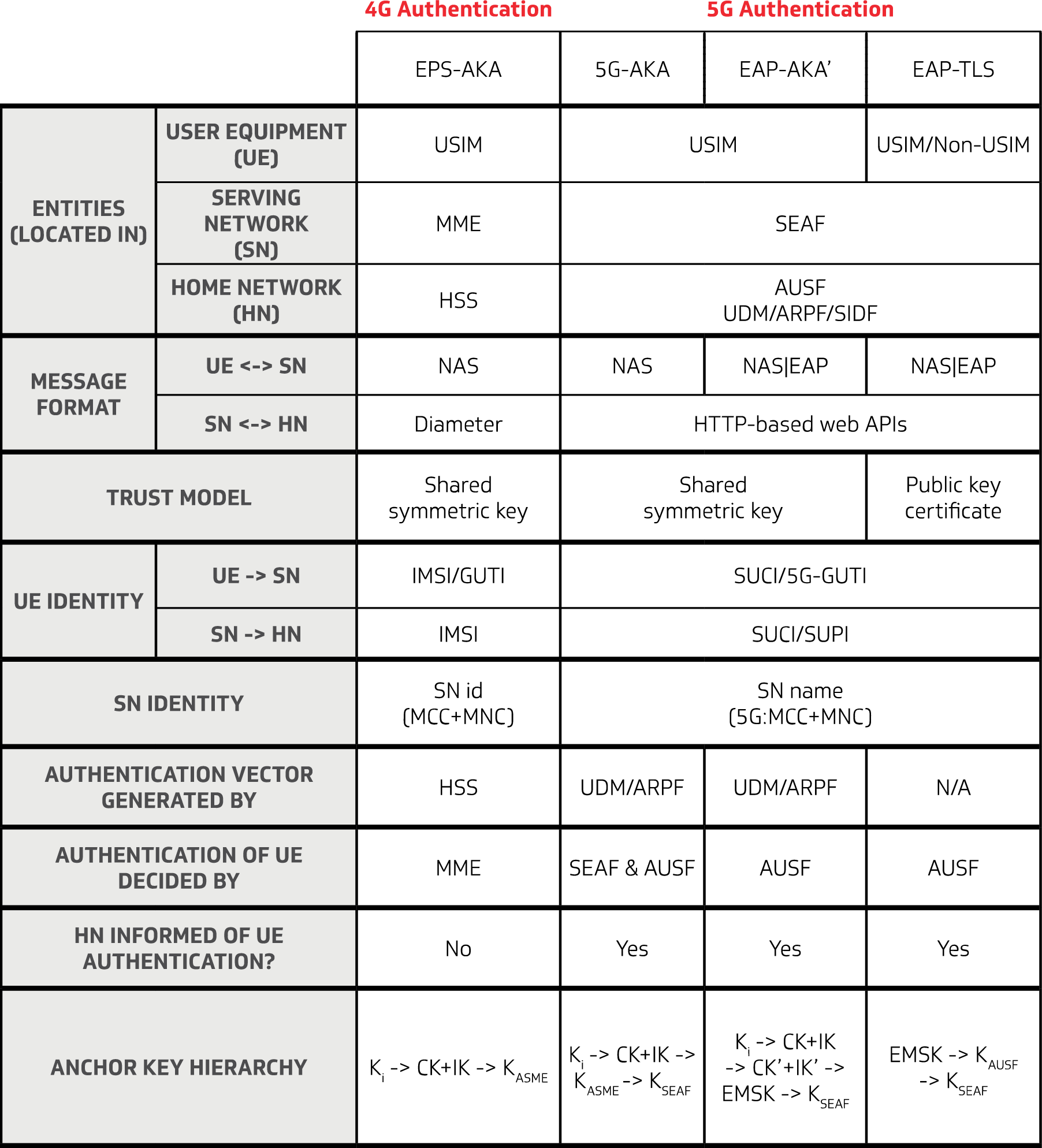
![Comparison of terminal authentication cost [7-10,12]. | Download ...](https://www.researchgate.net/publication/370617182/figure/fig1/AS:11431281156914776@1683646770204/Handover-authentication-protocol-5-Security-Analysis-51-Informal-Security-Analysis_Q320.jpg)