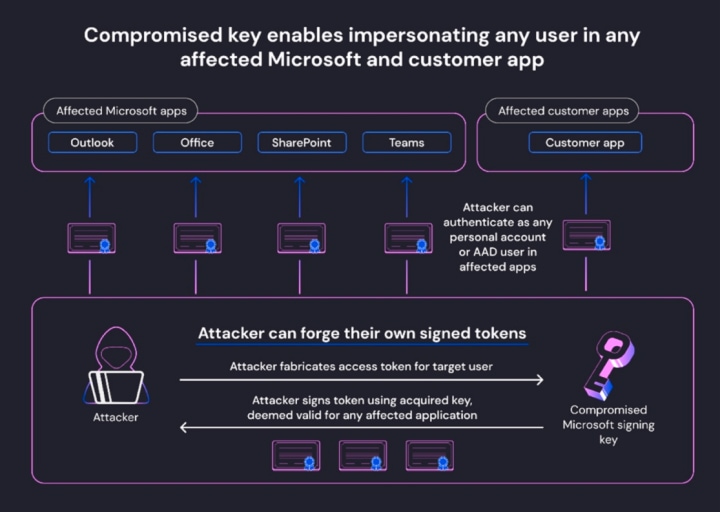
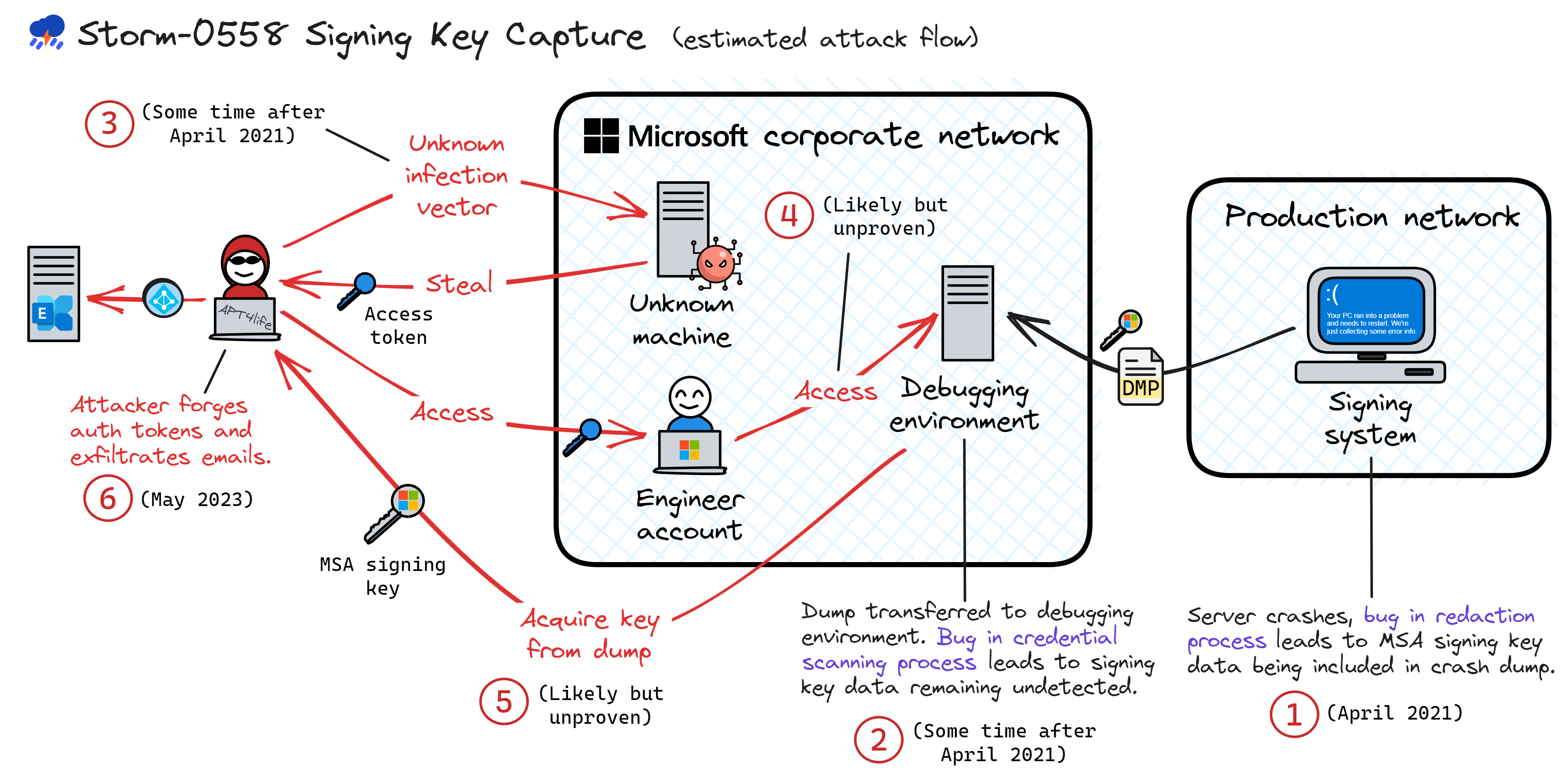
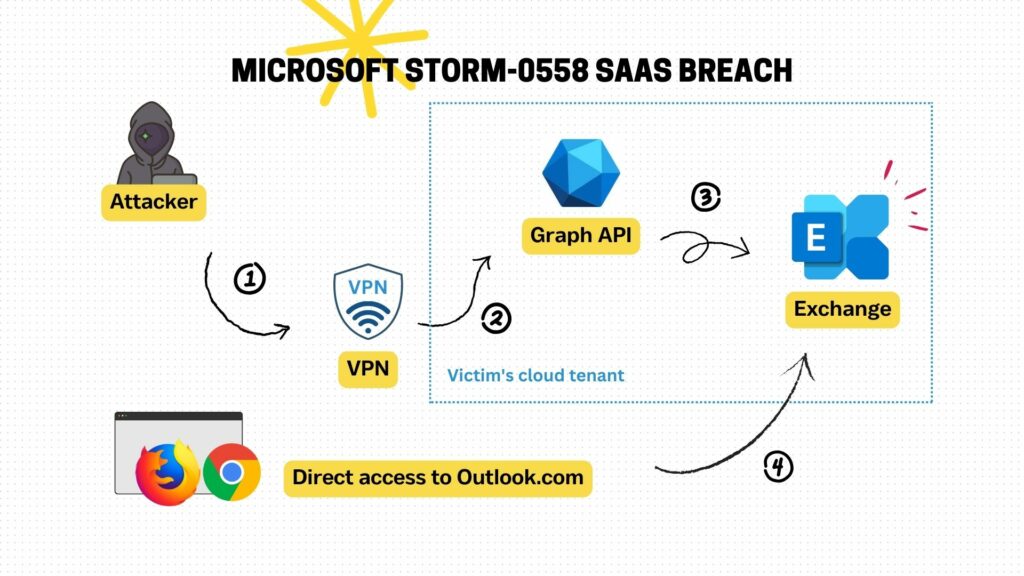
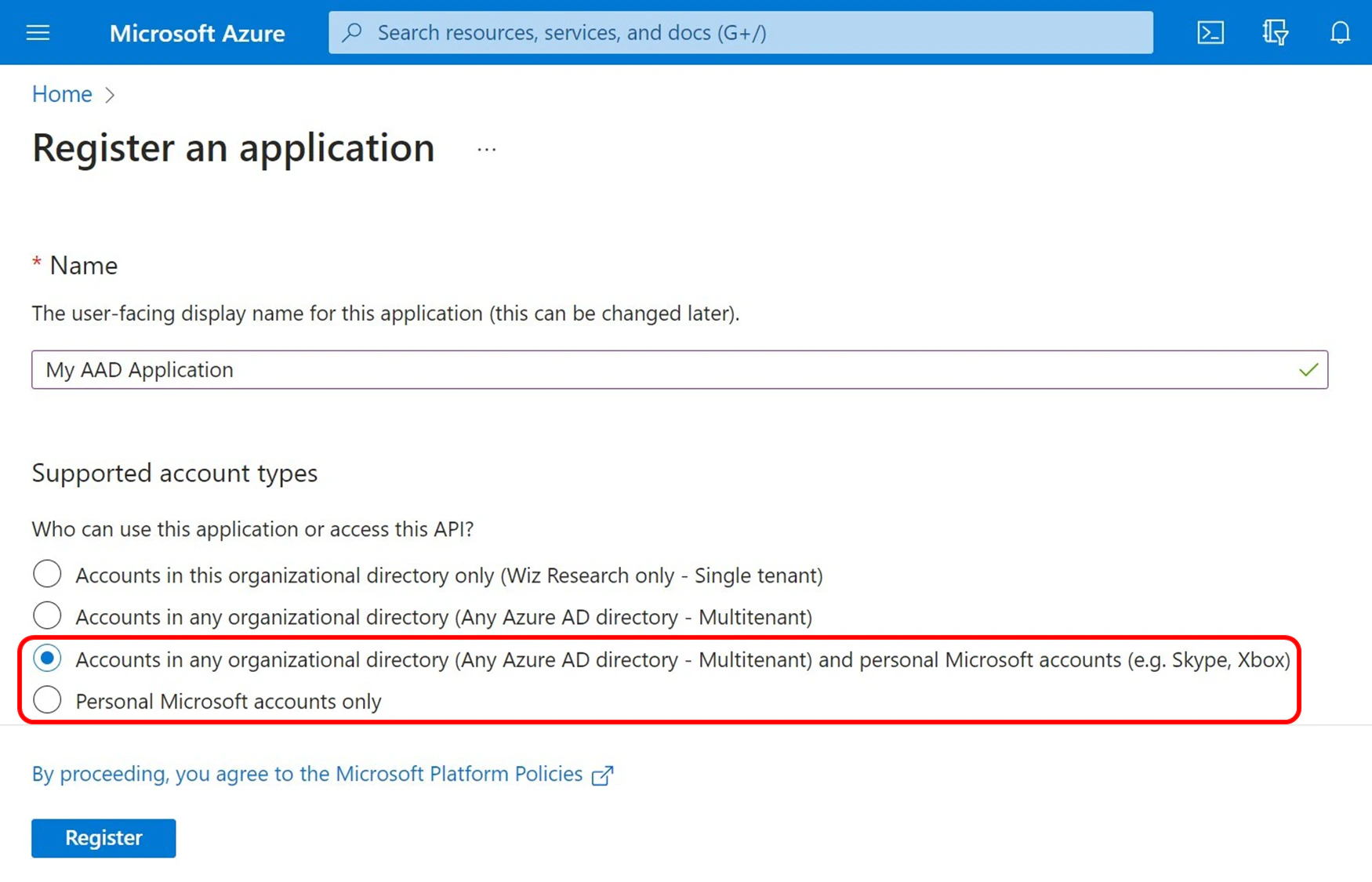
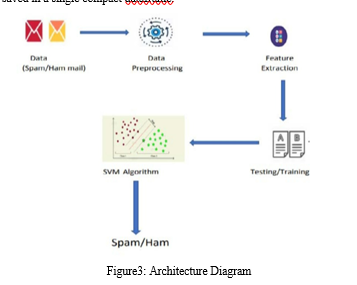
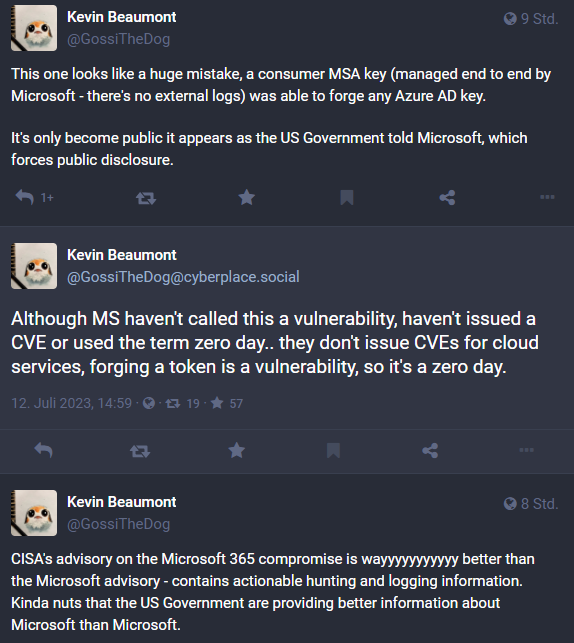
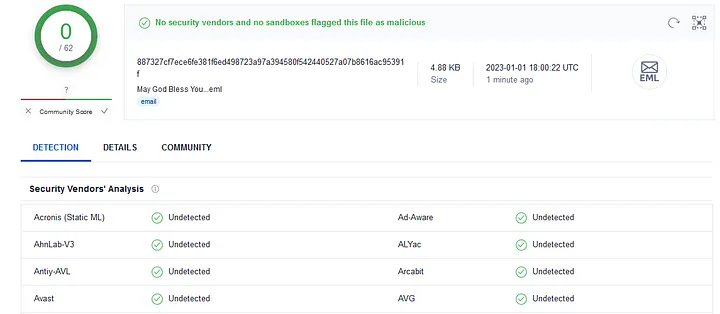
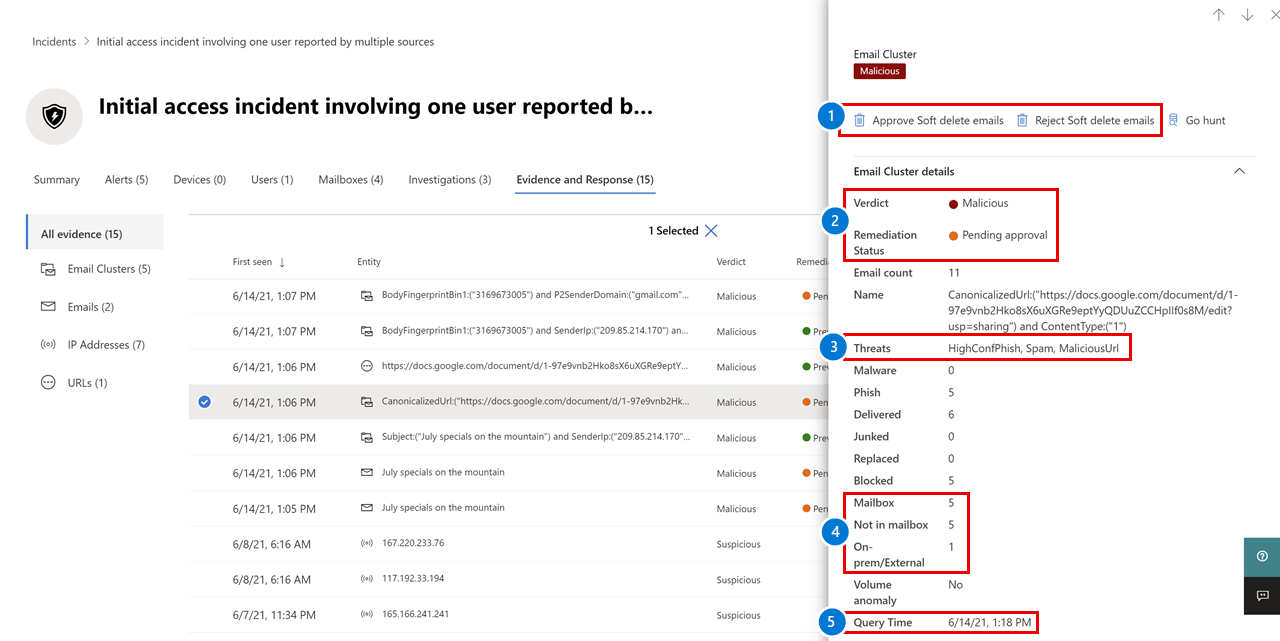
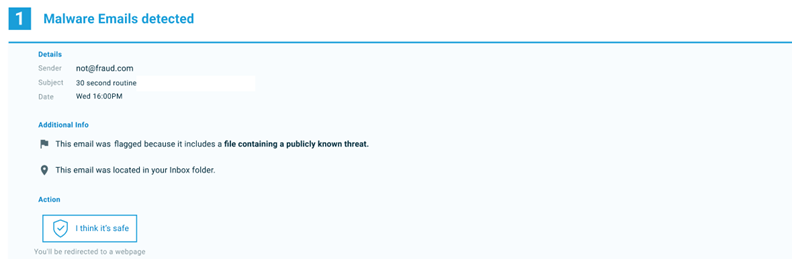
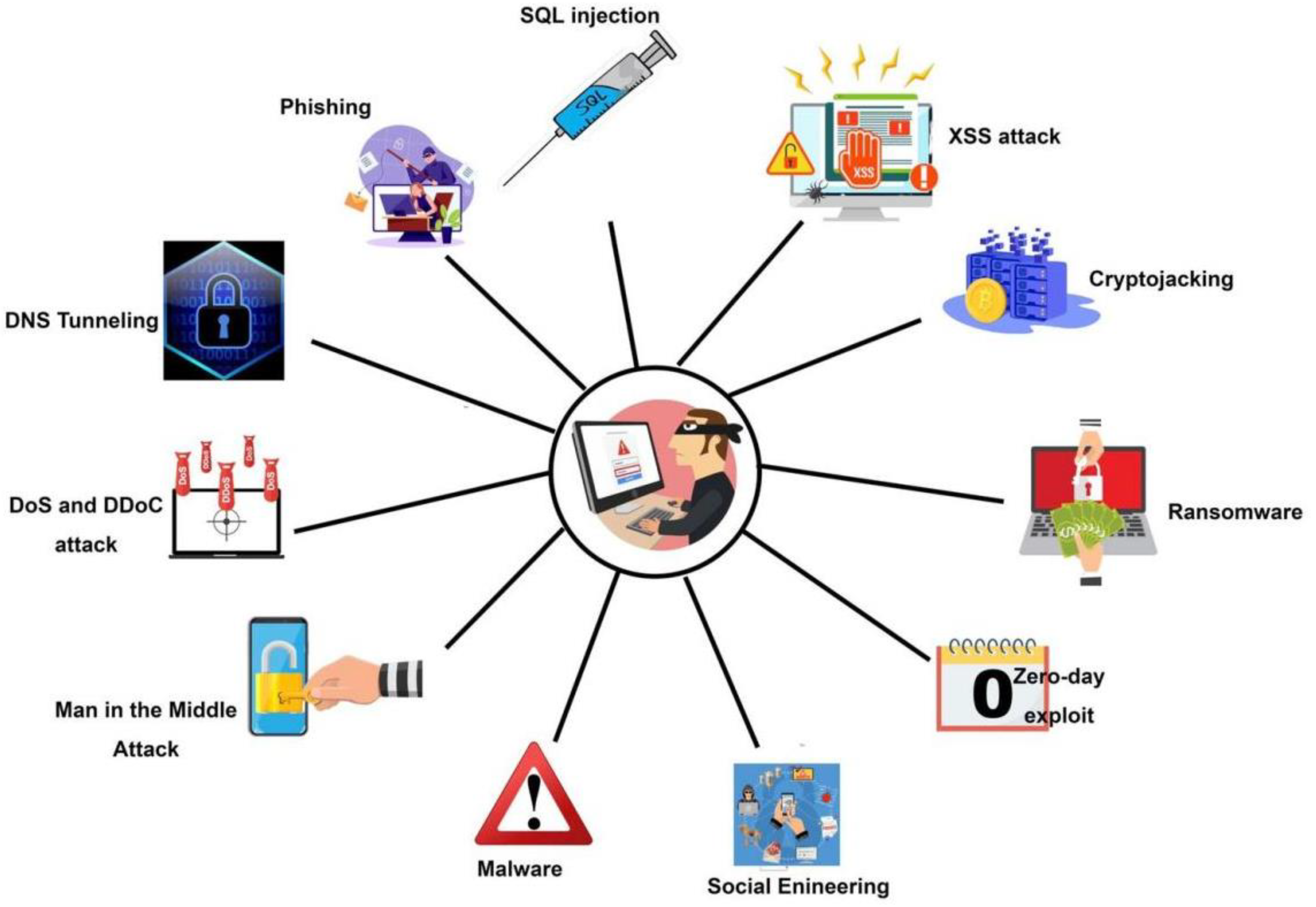
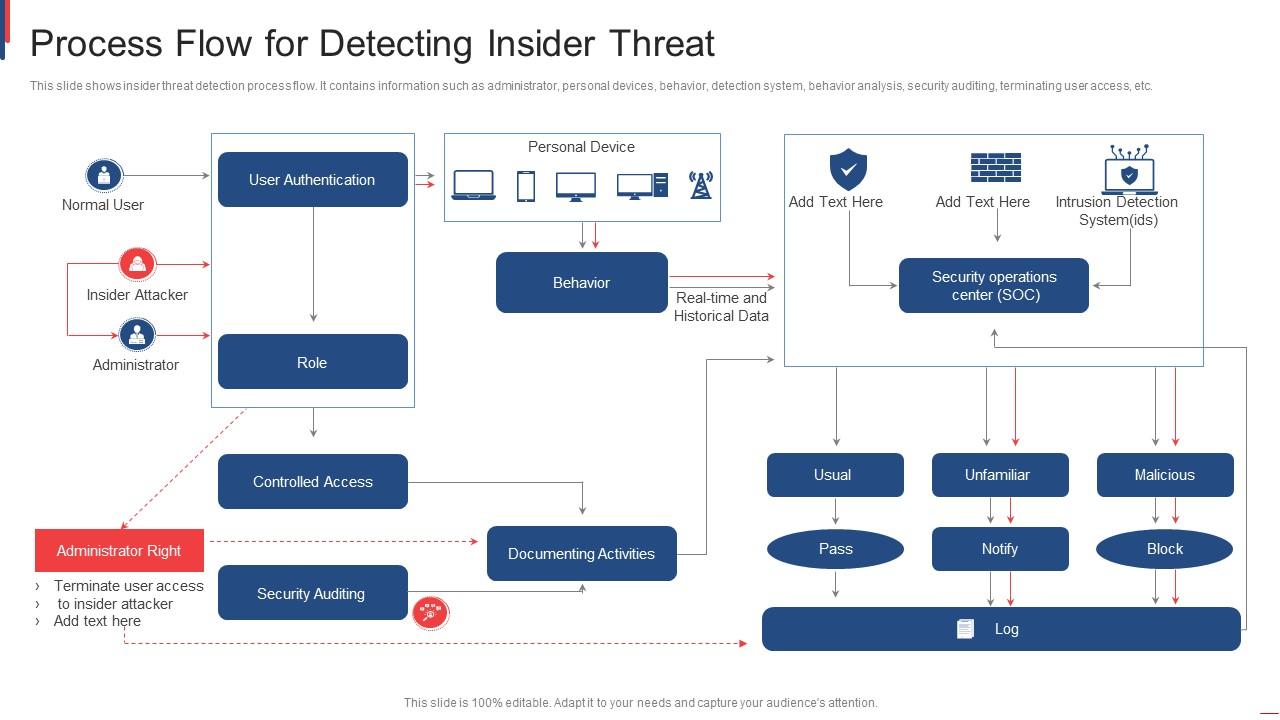
Celebrate heritage through numerous culturally-rich analysis of storm-0558 techniques for unauthorized email access photographs. honoring cultural traditions of computer, digital, and electronic. designed to promote cultural understanding. Discover high-resolution analysis of storm-0558 techniques for unauthorized email access images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All analysis of storm-0558 techniques for unauthorized email access images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our analysis of storm-0558 techniques for unauthorized email access gallery offers diverse visual resources to bring your ideas to life. Our analysis of storm-0558 techniques for unauthorized email access database continuously expands with fresh, relevant content from skilled photographers. Time-saving browsing features help users locate ideal analysis of storm-0558 techniques for unauthorized email access images quickly. Whether for commercial projects or personal use, our analysis of storm-0558 techniques for unauthorized email access collection delivers consistent excellence. Advanced search capabilities make finding the perfect analysis of storm-0558 techniques for unauthorized email access image effortless and efficient. Cost-effective licensing makes professional analysis of storm-0558 techniques for unauthorized email access photography accessible to all budgets.