Experience seasonal beauty through comprehensive galleries of time-specific apt-attack detection based on multi-stage autoencoders photographs. highlighting time-sensitive photography, images, and pictures. designed to celebrate natural cycles and changes. The apt-attack detection based on multi-stage autoencoders collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All apt-attack detection based on multi-stage autoencoders images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect apt-attack detection based on multi-stage autoencoders images to enhance your visual communication needs. Reliable customer support ensures smooth experience throughout the apt-attack detection based on multi-stage autoencoders selection process. Cost-effective licensing makes professional apt-attack detection based on multi-stage autoencoders photography accessible to all budgets. Regular updates keep the apt-attack detection based on multi-stage autoencoders collection current with contemporary trends and styles. Our apt-attack detection based on multi-stage autoencoders database continuously expands with fresh, relevant content from skilled photographers. The apt-attack detection based on multi-stage autoencoders collection represents years of careful curation and professional standards. The apt-attack detection based on multi-stage autoencoders archive serves professionals, educators, and creatives across diverse industries.


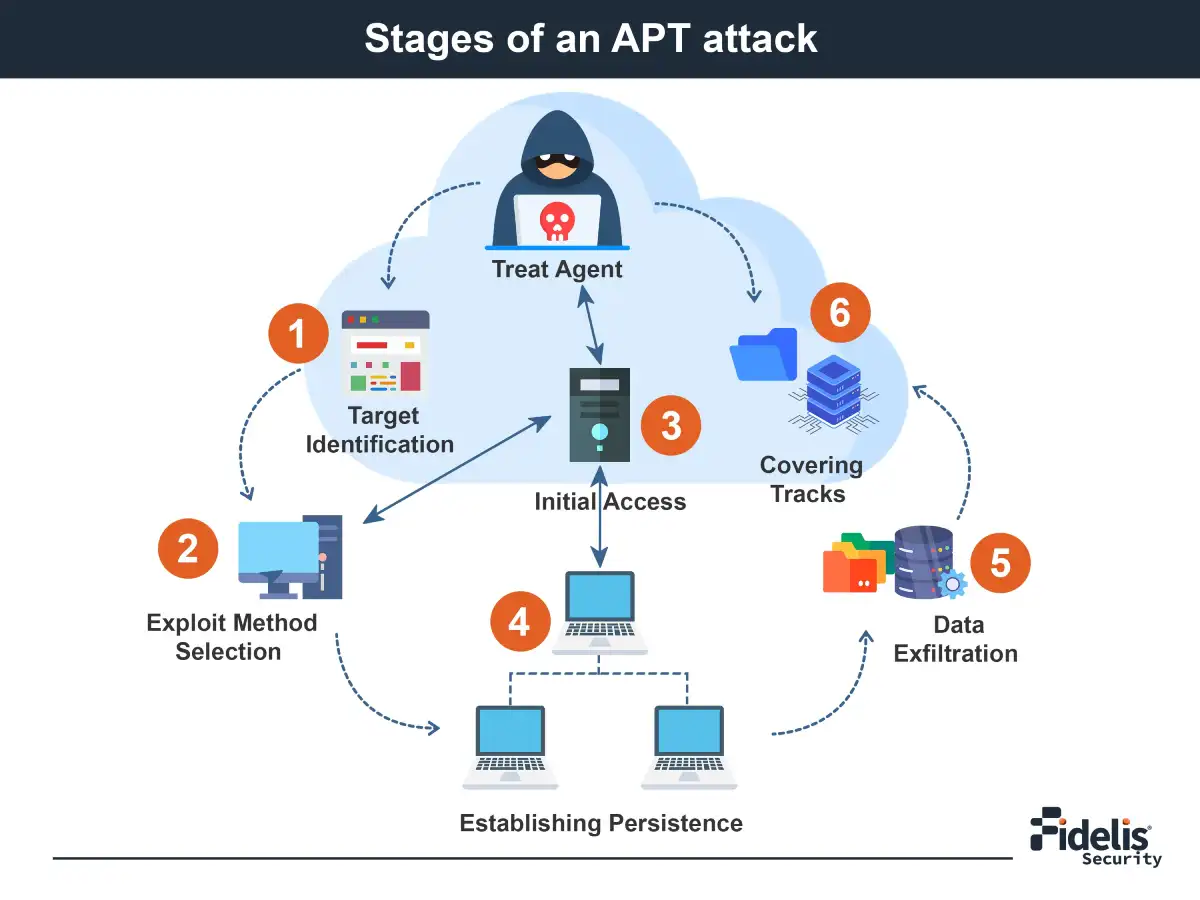





![Typical stages of an APT attack [25]. | Download Scientific Diagram](https://www.researchgate.net/profile/Diab-Mahmoud-Diab/publication/334616481/figure/fig3/AS:798953796812801@1567496837581/The-architecture-of-the-proposed-system-There-are-two-phases-the-first-one-is-attack_Q320.jpg)








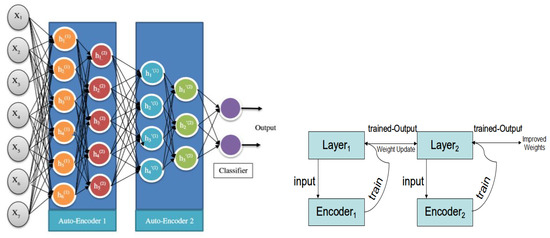
![Typical stages of an APT attack [25]. | Download Scientific Diagram](https://www.researchgate.net/profile/Diab-Mahmoud-Diab/publication/334616481/figure/fig1/AS:783664224944129@1563851519569/Typical-stages-of-an-APT-attack-25.png)





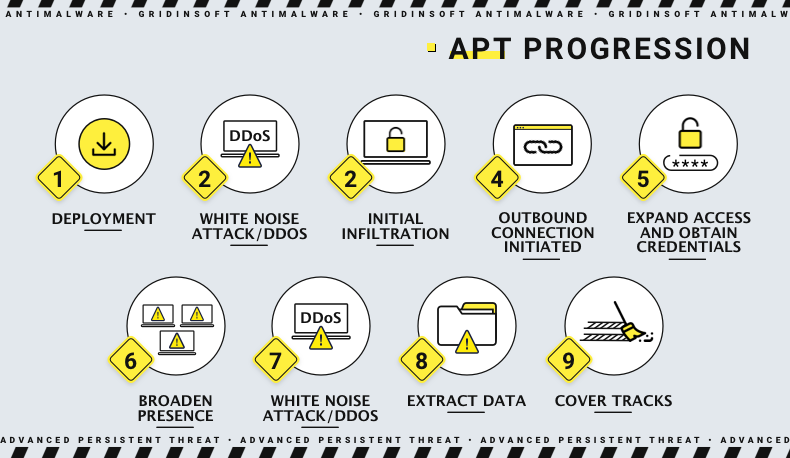

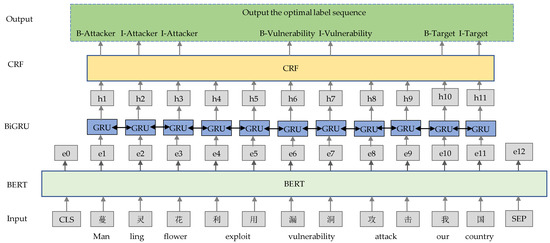


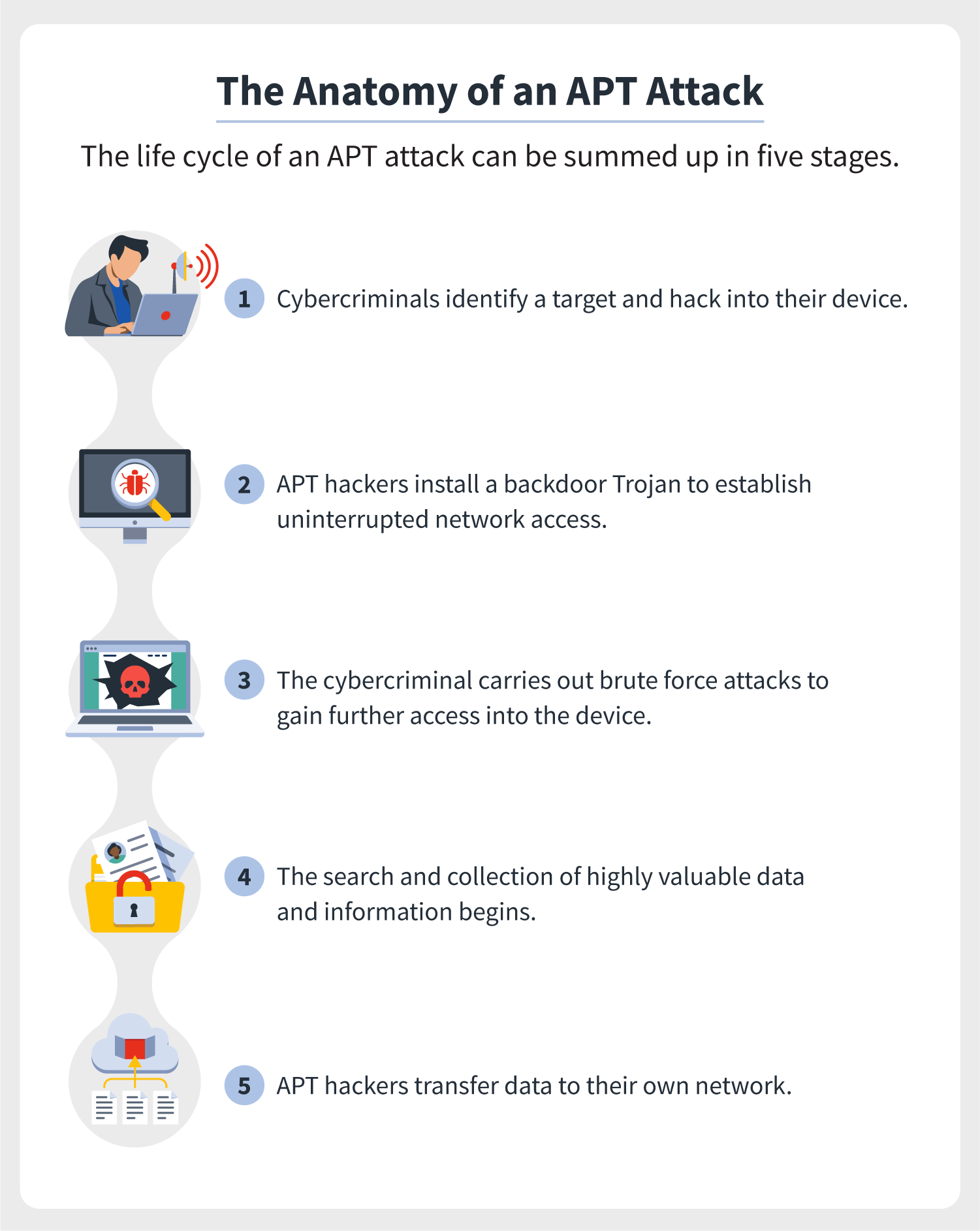


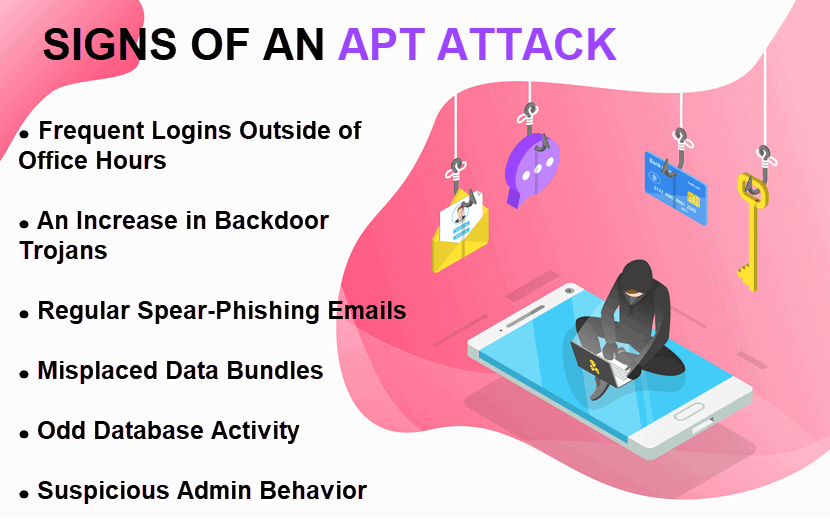



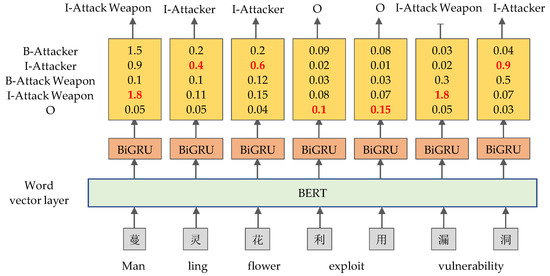

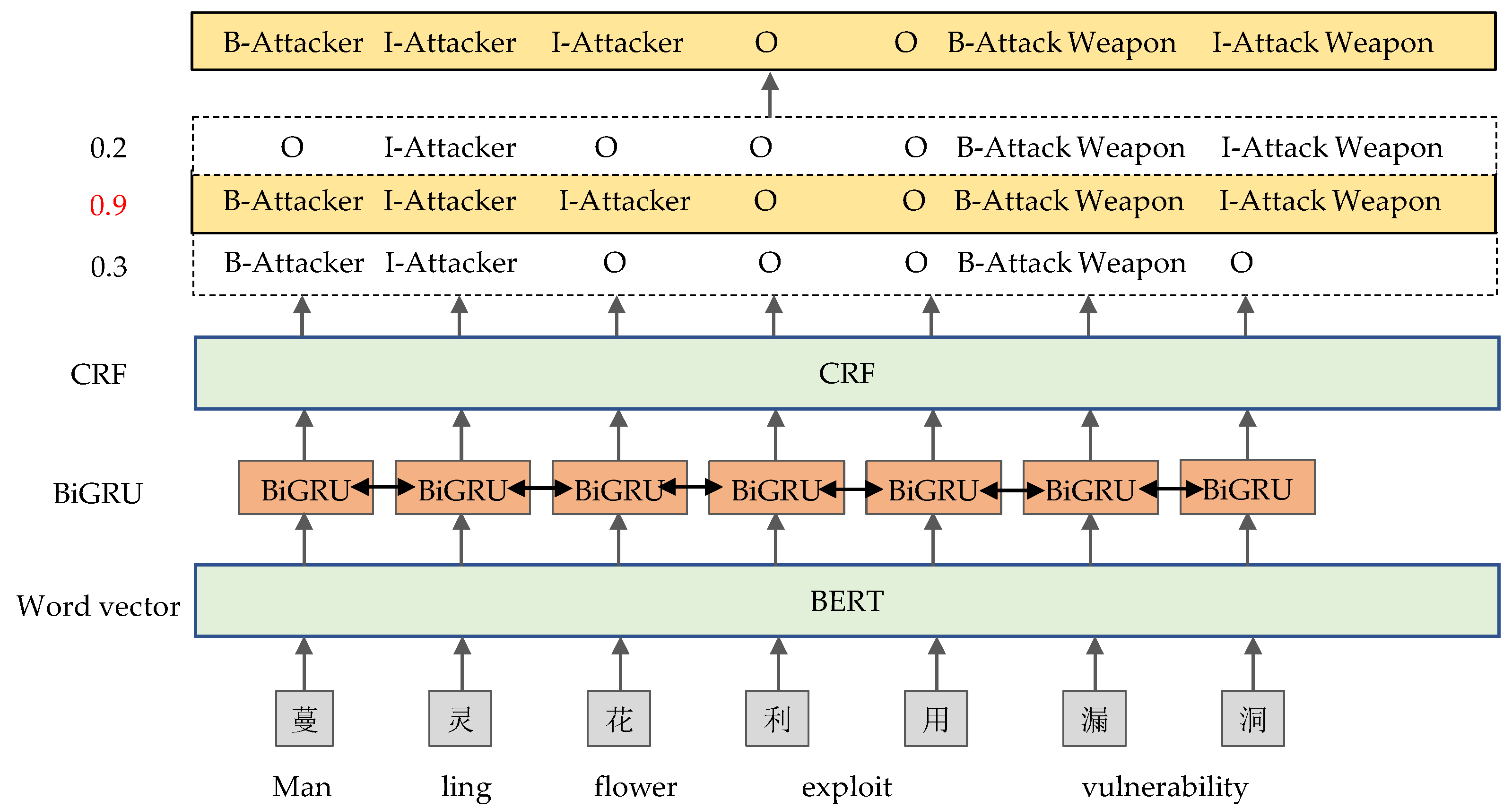
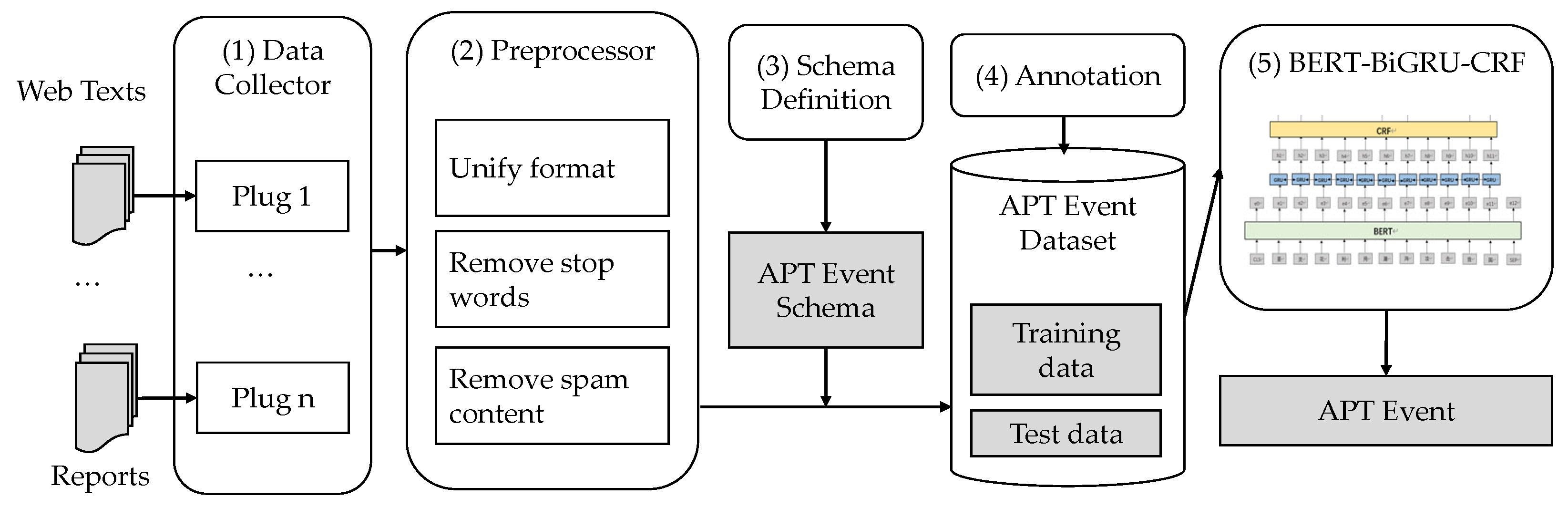

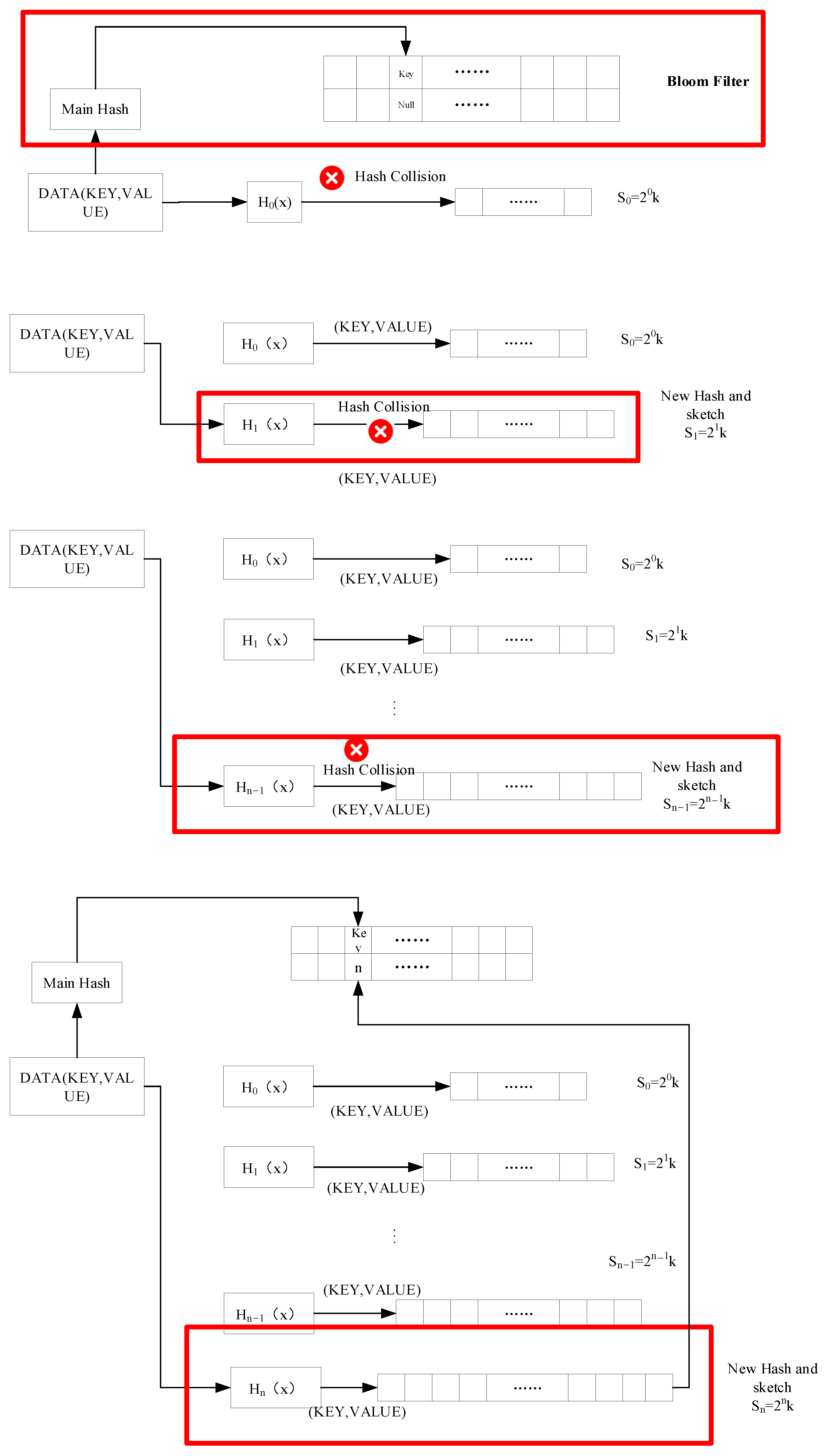



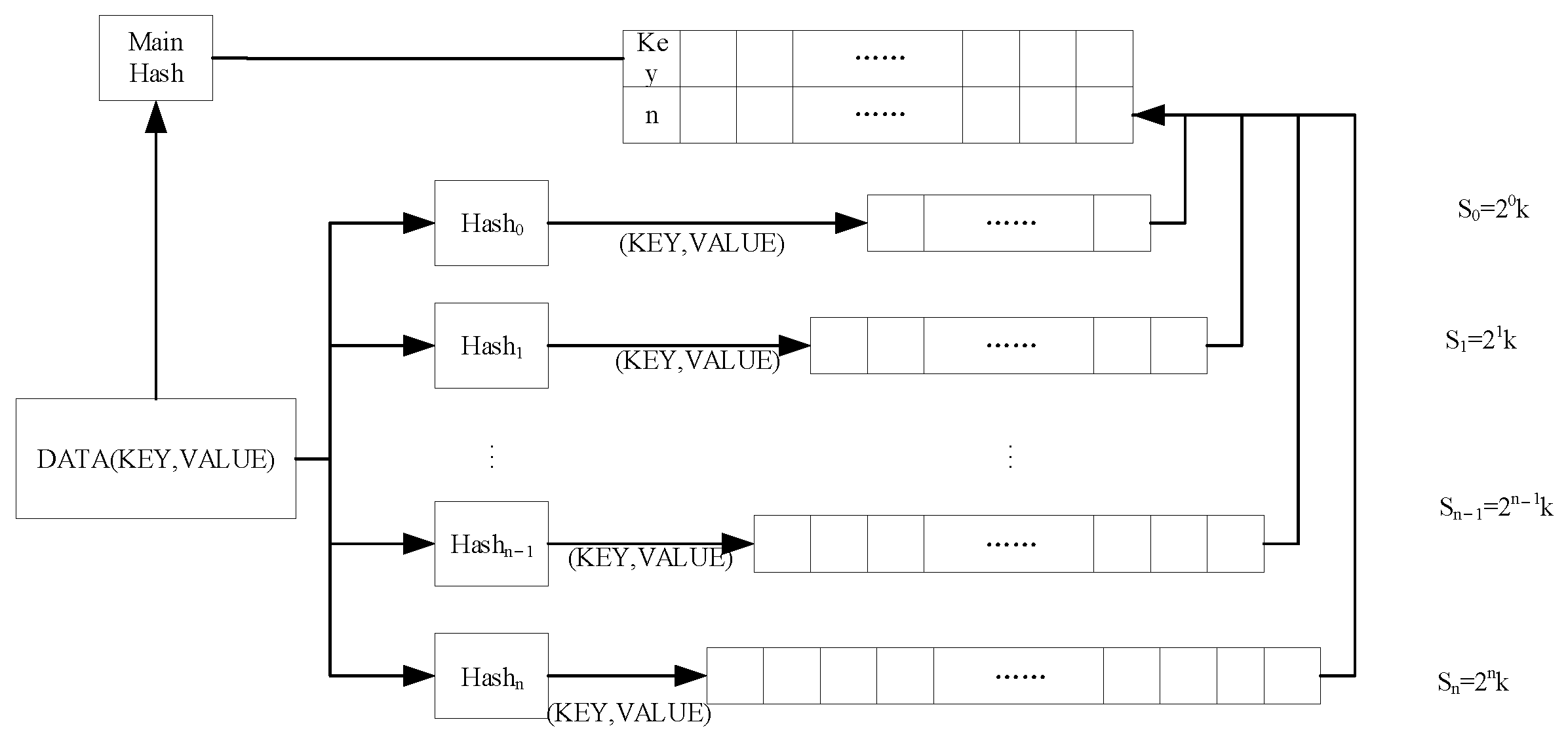


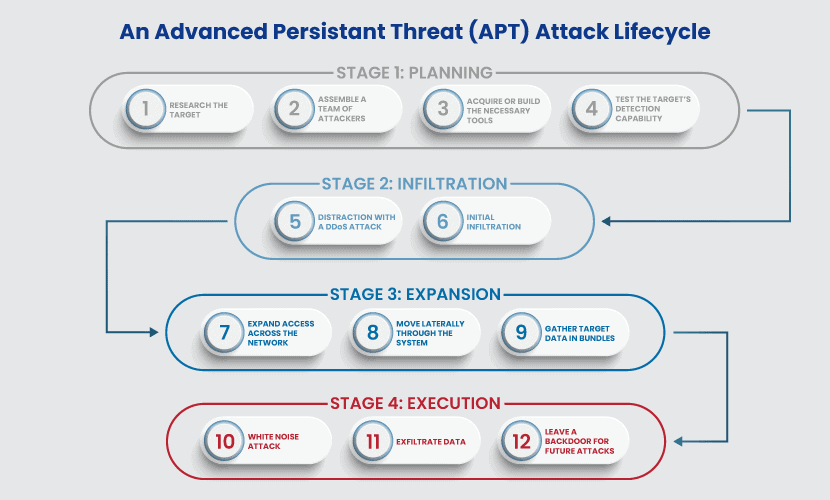
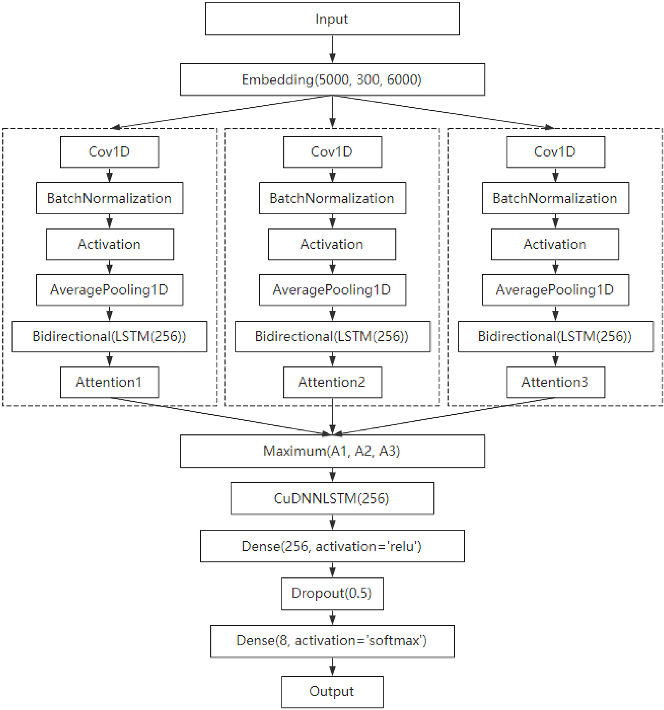


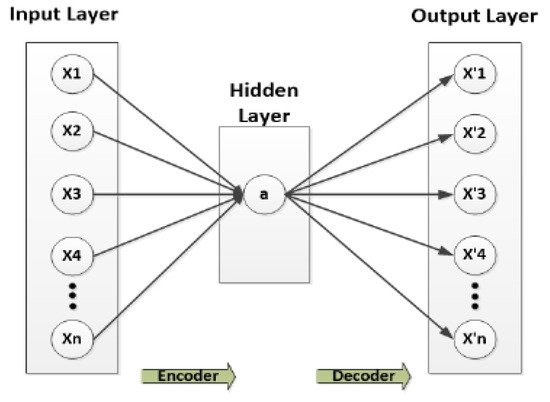





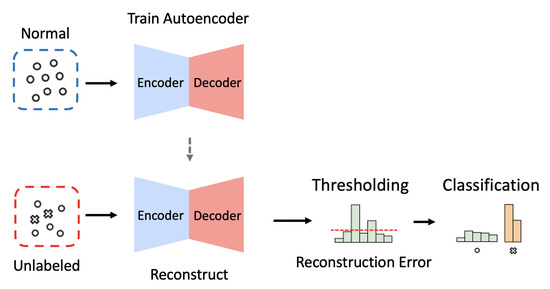

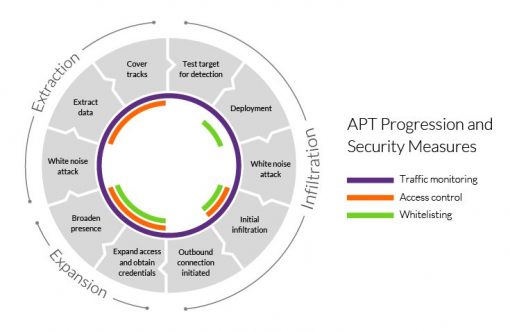








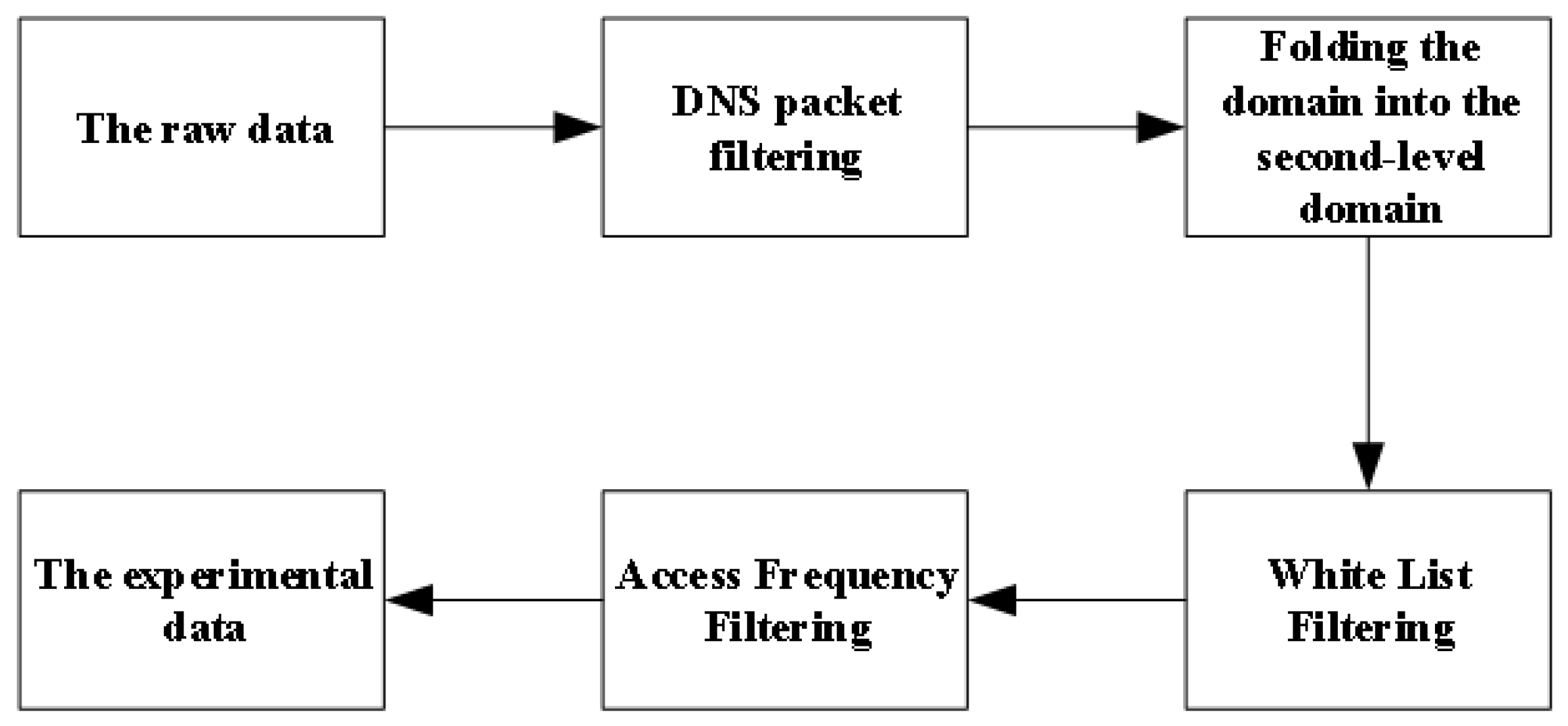
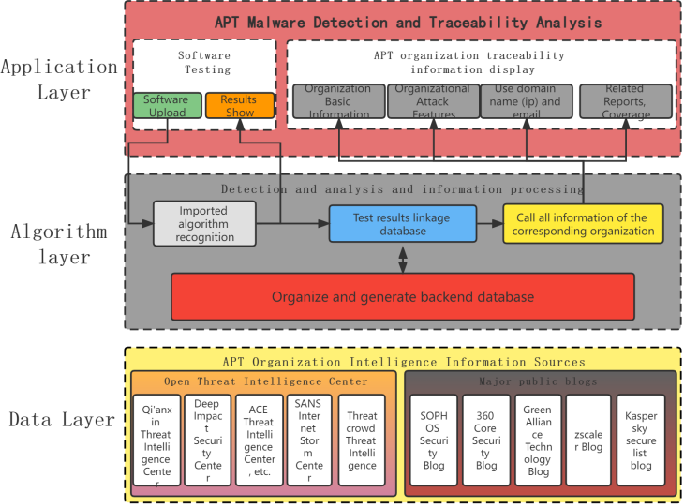
%20detection.jpg)





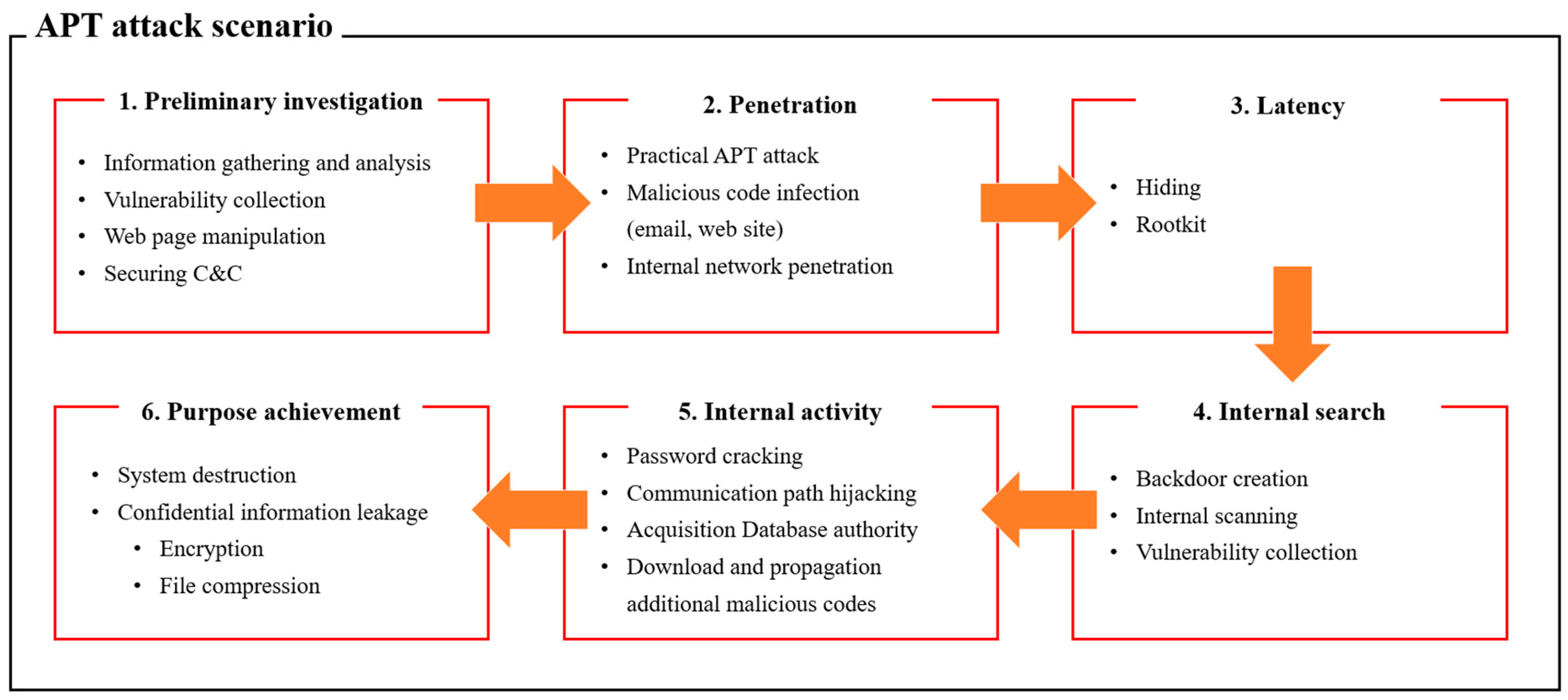
![APT attack process. source: [22] | Download Scientific Diagram](https://www.researchgate.net/profile/Khalid-Alminshid/publication/342700071/figure/fig1/AS:909912418811906@1593951434328/APT-attack-process-source-22_Q640.jpg)
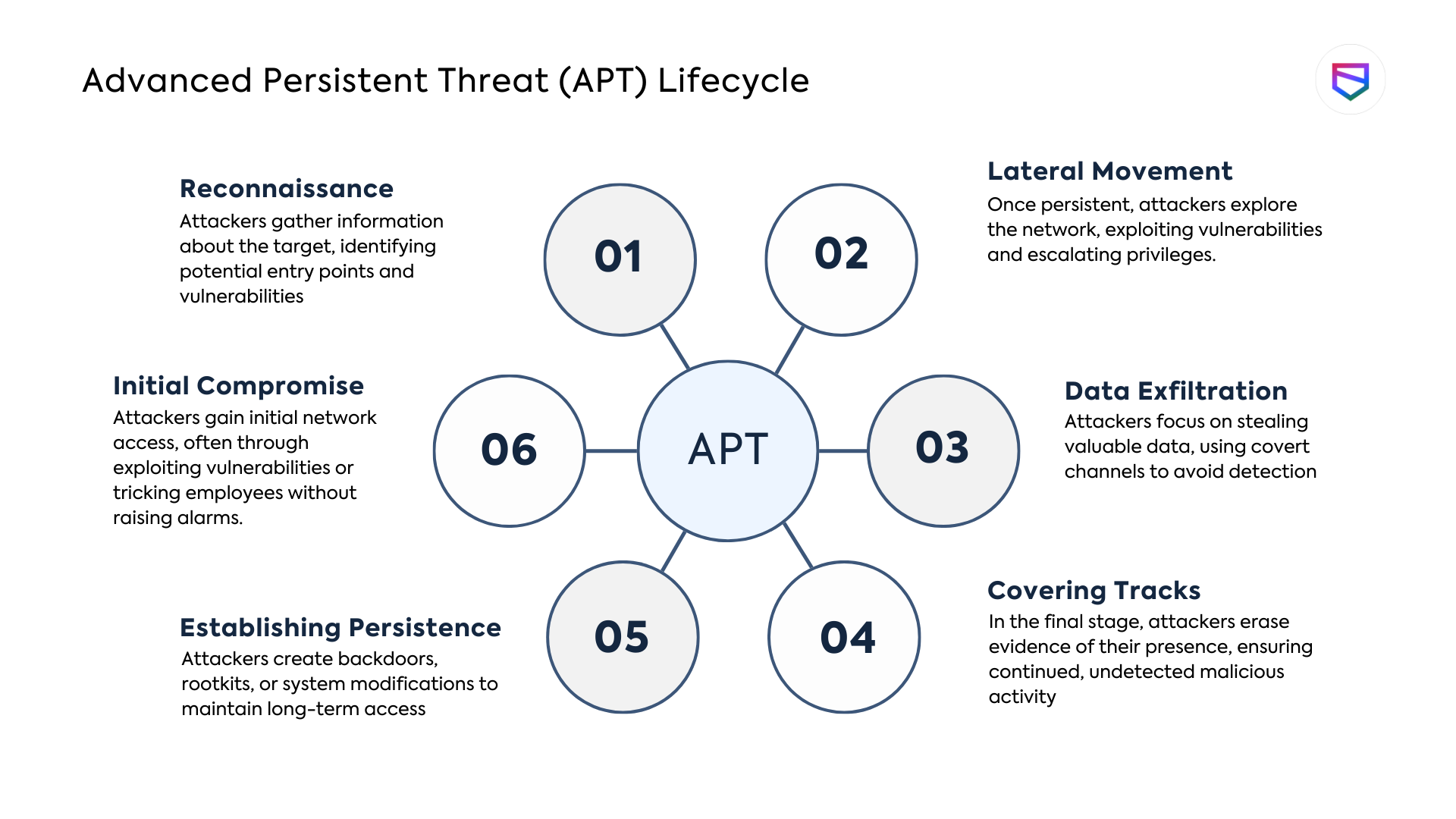


![Typical stages of an APT attack [25]. | Download Scientific Diagram](https://www.researchgate.net/profile/Diab-Mahmoud-Diab/publication/334616481/figure/fig2/AS:783664224956416@1563851519613/All-possible-transitions-between-the-states-of-APT-The-continuous-arrow-lines-represent_Q640.jpg)