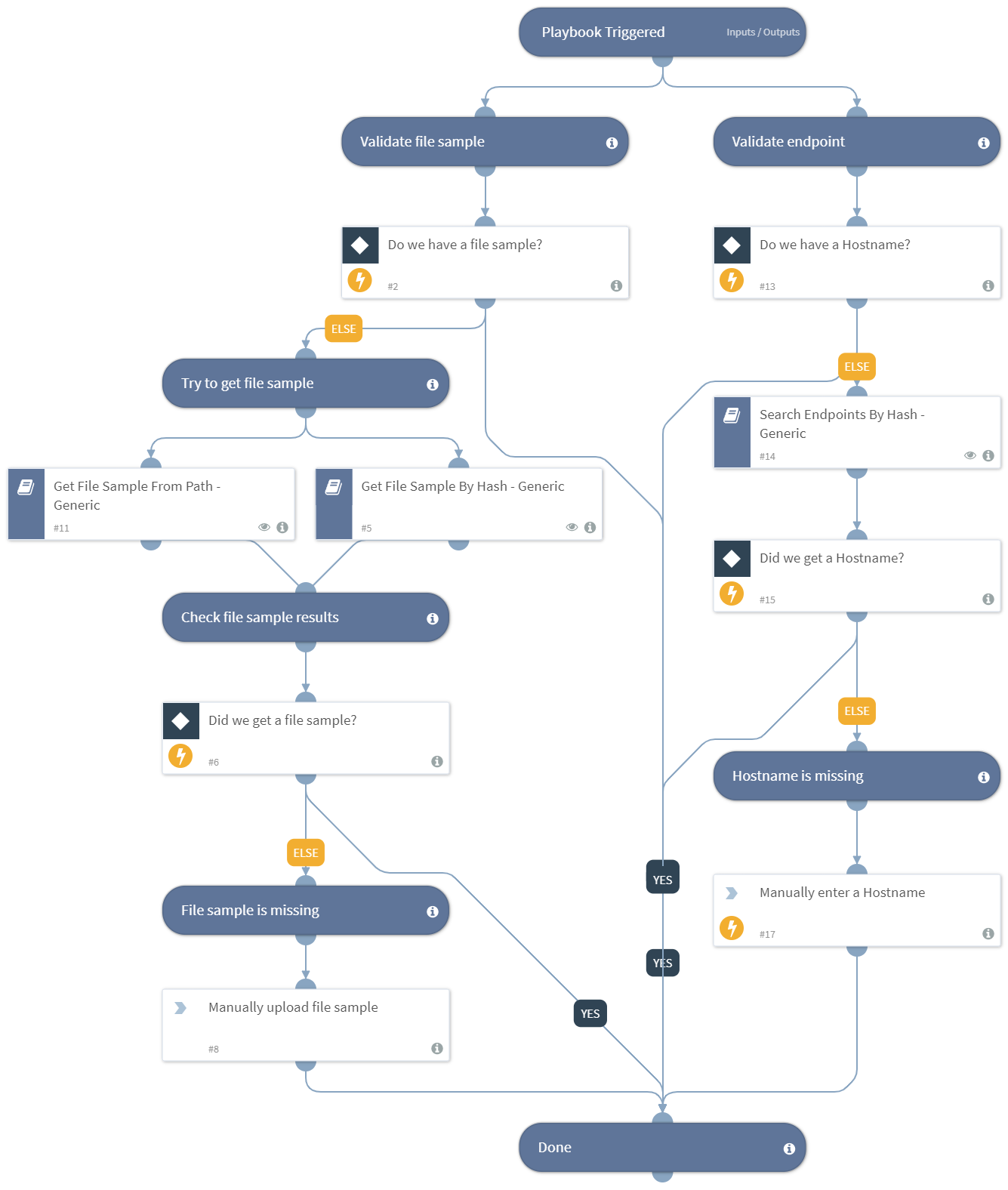
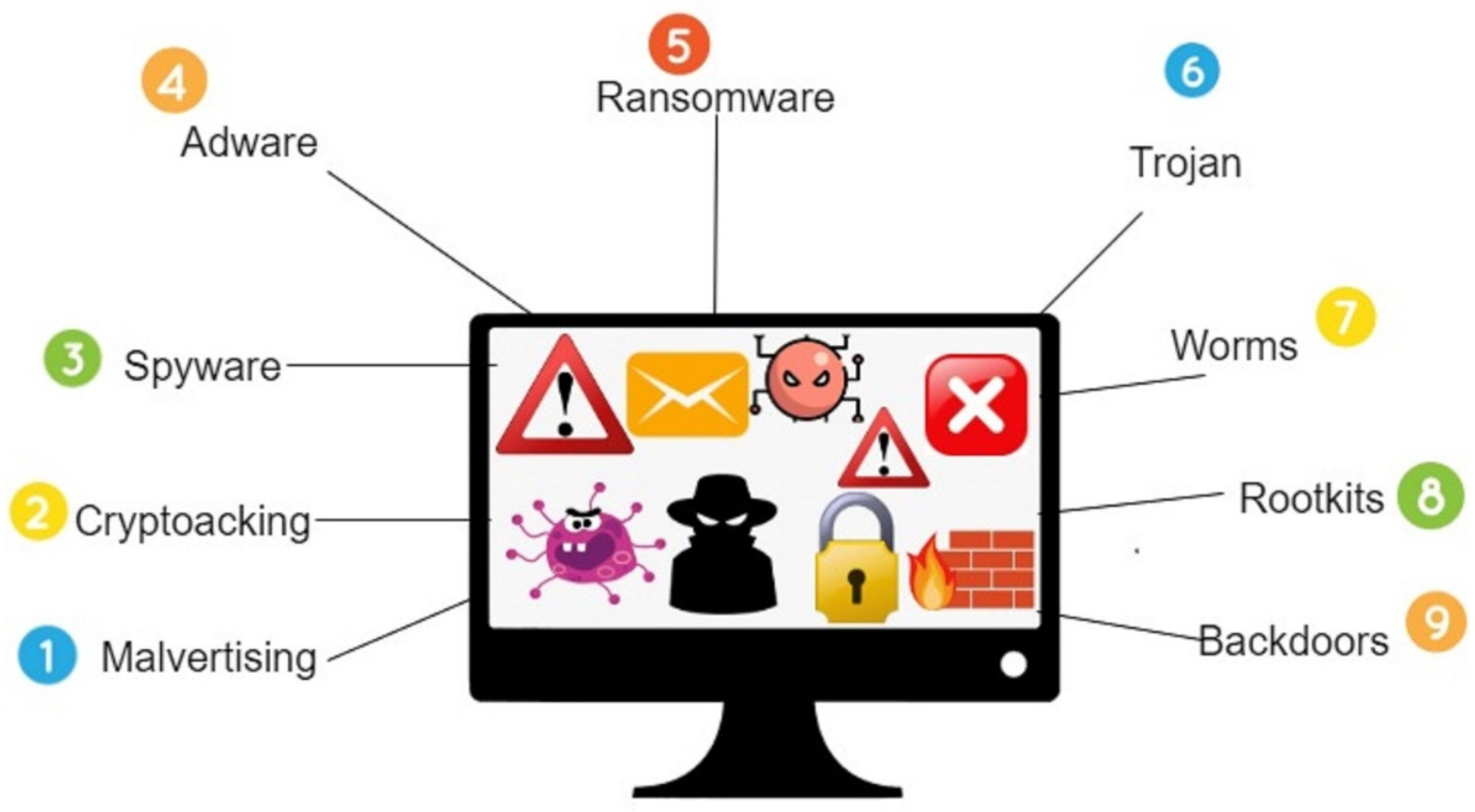
Discover destinations through substantial collections of journey-focused generic os x malware detection method explained | threatpost photographs. adventurously capturing computer, digital, and electronic. designed to inspire wanderlust and exploration. Each generic os x malware detection method explained | threatpost image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All generic os x malware detection method explained | threatpost images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our generic os x malware detection method explained | threatpost gallery offers diverse visual resources to bring your ideas to life. Professional licensing options accommodate both commercial and educational usage requirements. Whether for commercial projects or personal use, our generic os x malware detection method explained | threatpost collection delivers consistent excellence. Each image in our generic os x malware detection method explained | threatpost gallery undergoes rigorous quality assessment before inclusion. Multiple resolution options ensure optimal performance across different platforms and applications. Advanced search capabilities make finding the perfect generic os x malware detection method explained | threatpost image effortless and efficient. Cost-effective licensing makes professional generic os x malware detection method explained | threatpost photography accessible to all budgets.

















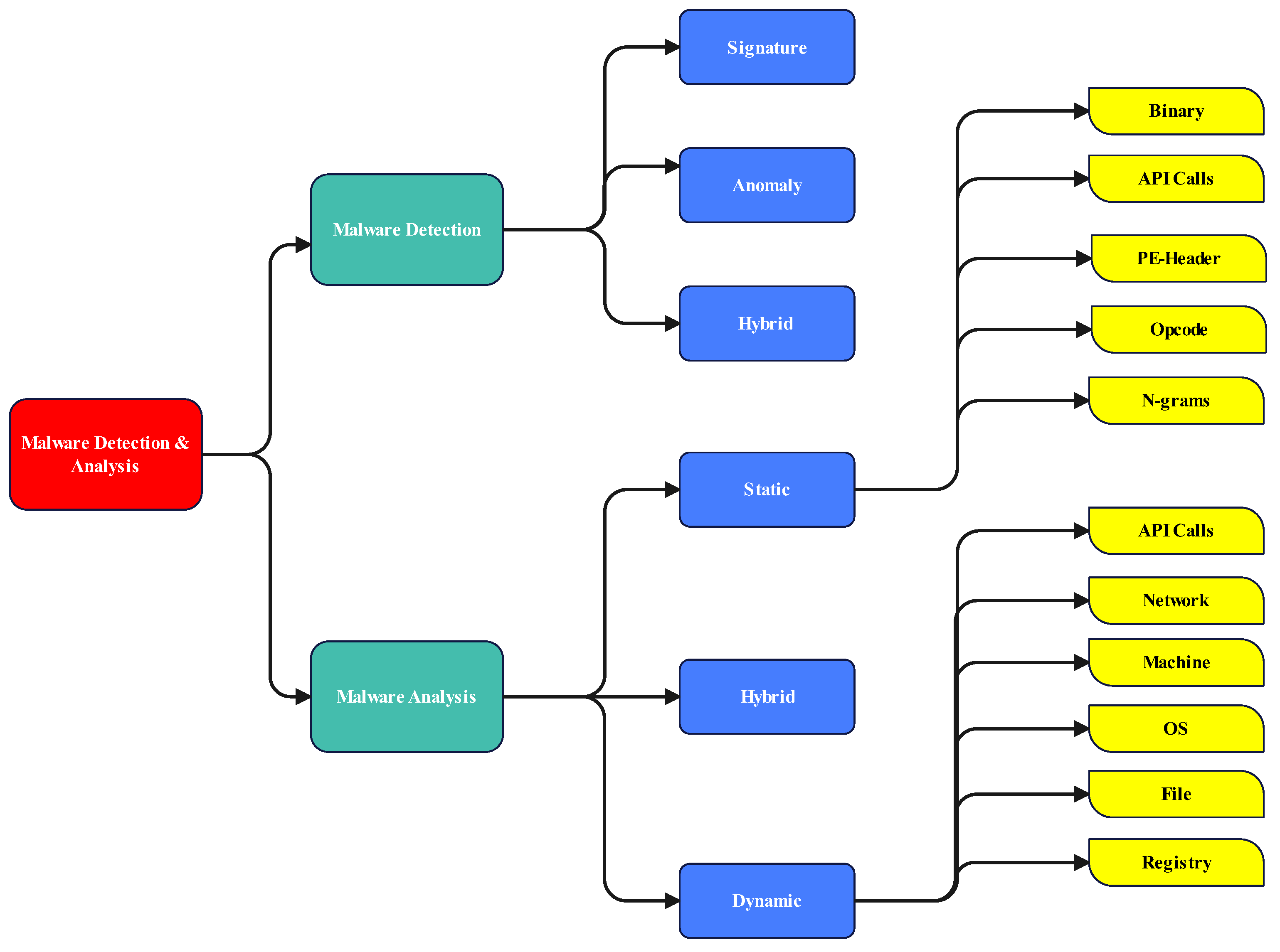










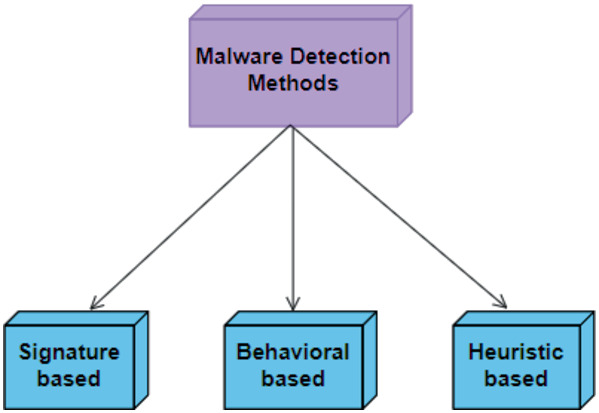










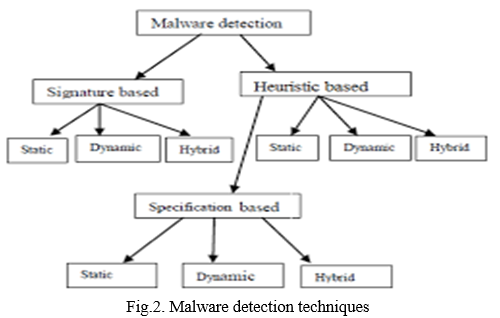




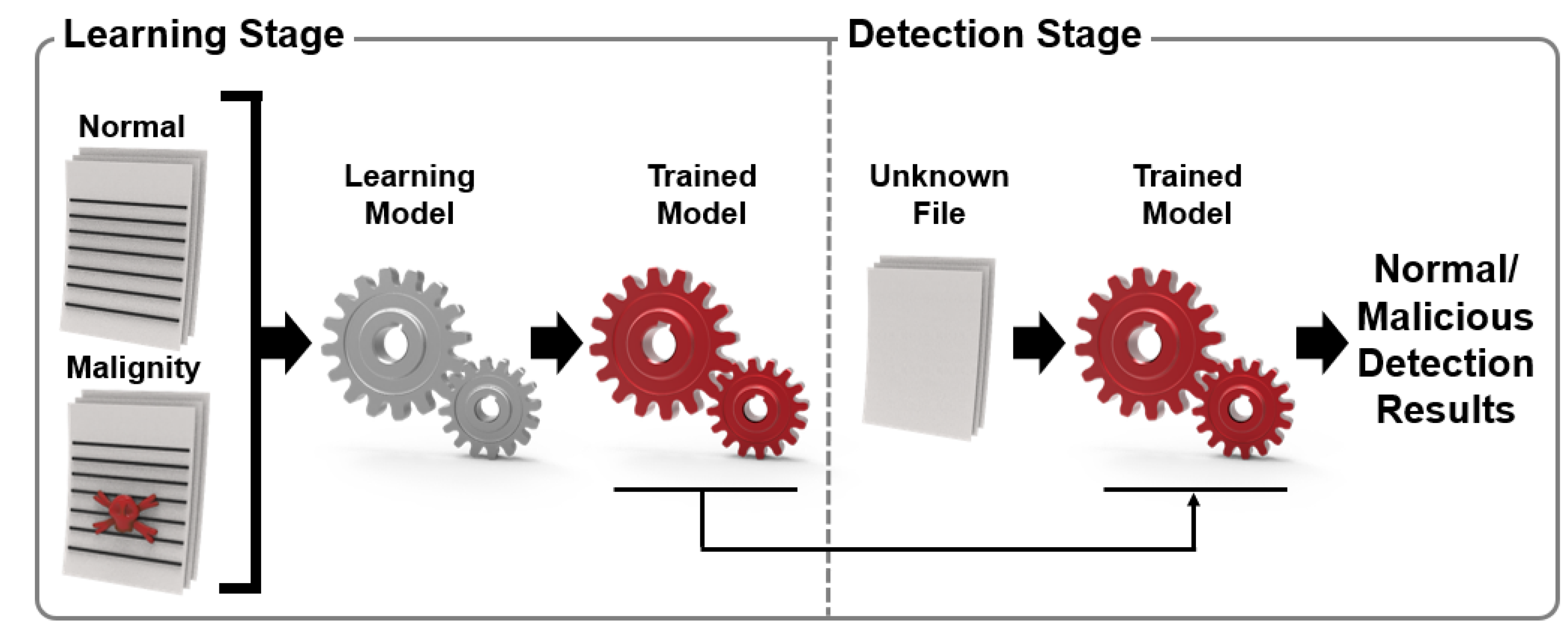
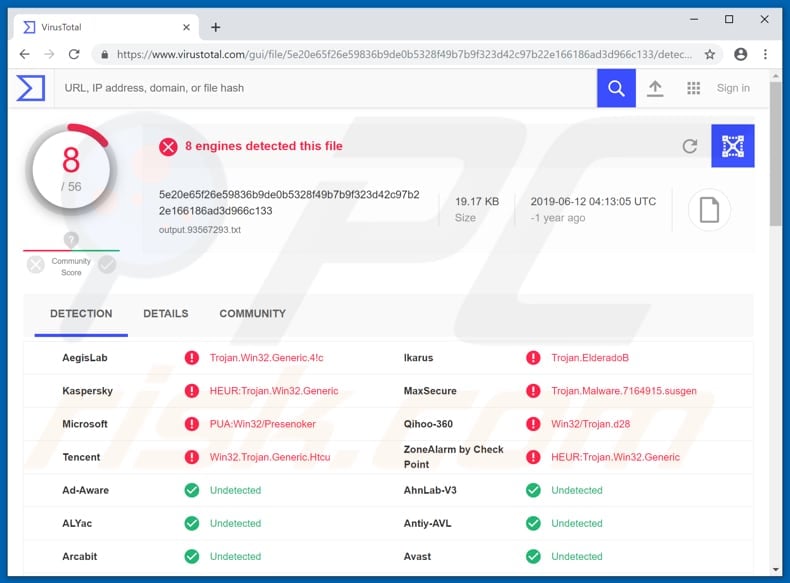






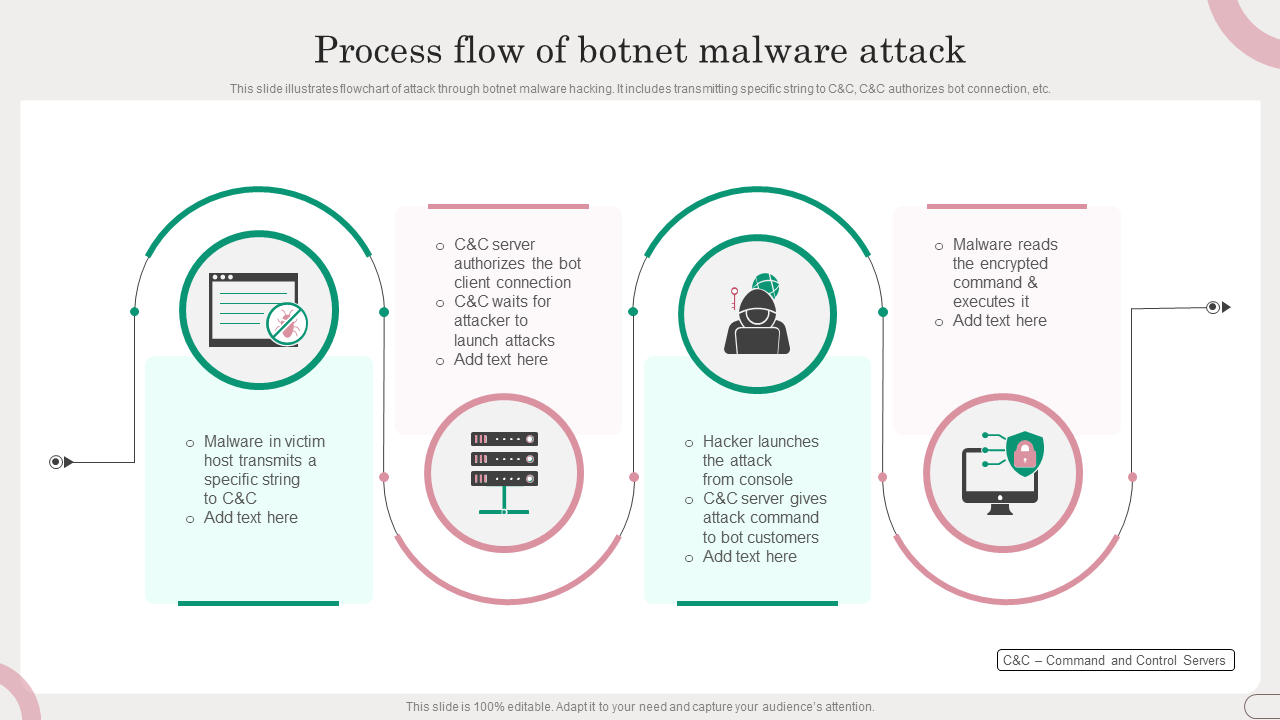

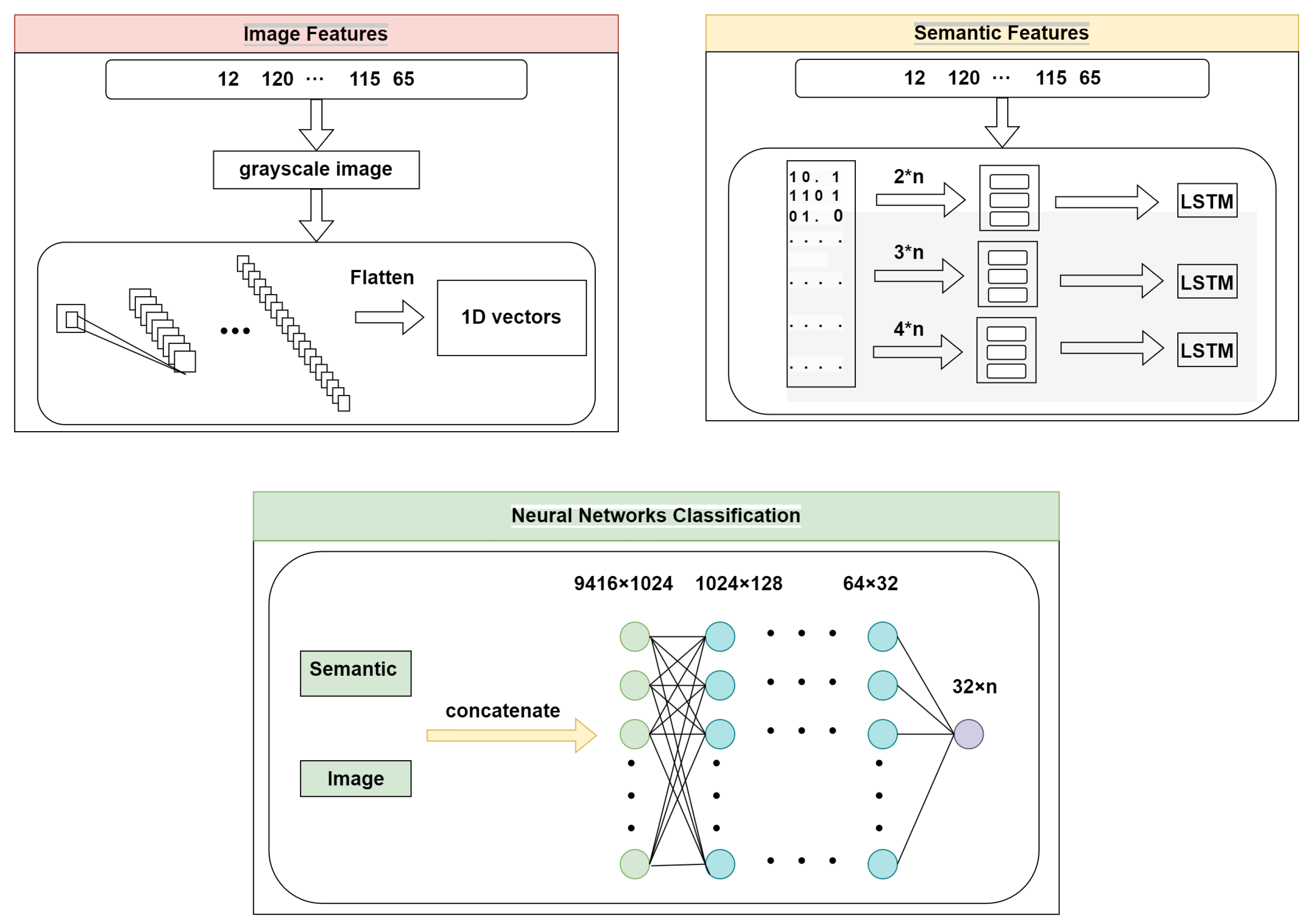
![Malware detection techniques [25]. | Download Scientific Diagram](https://www.researchgate.net/publication/354060018/figure/fig1/AS:1059608101654529@1629641666928/Malware-detection-techniques-25_Q640.jpg)






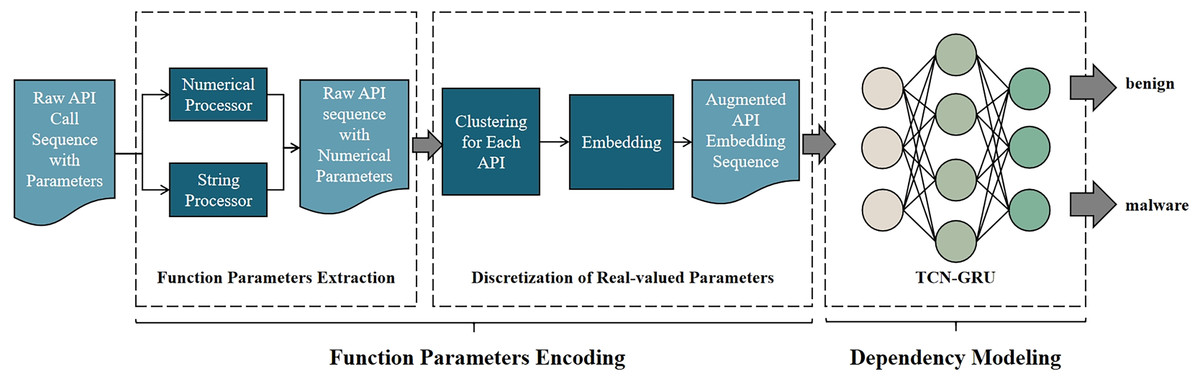

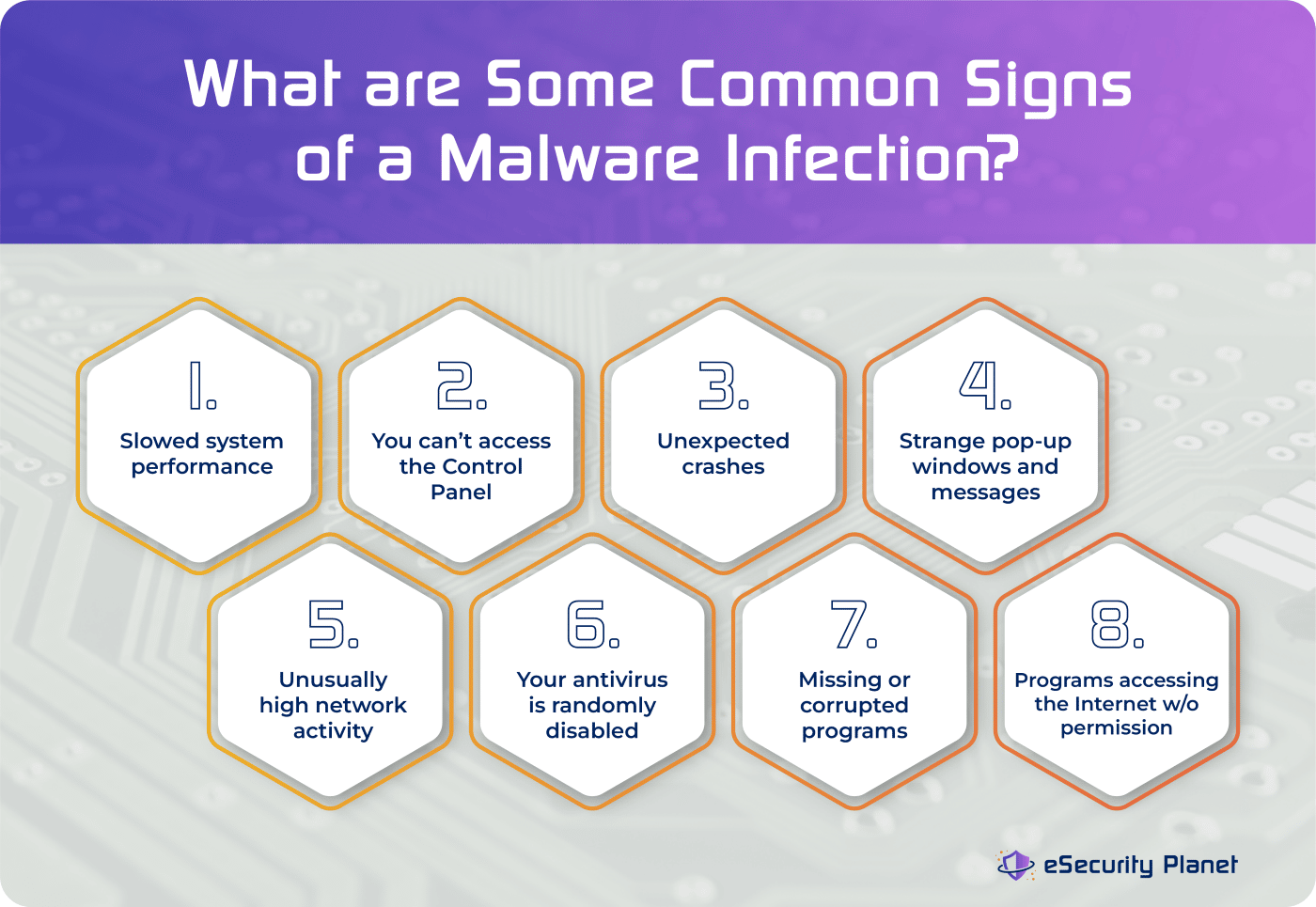

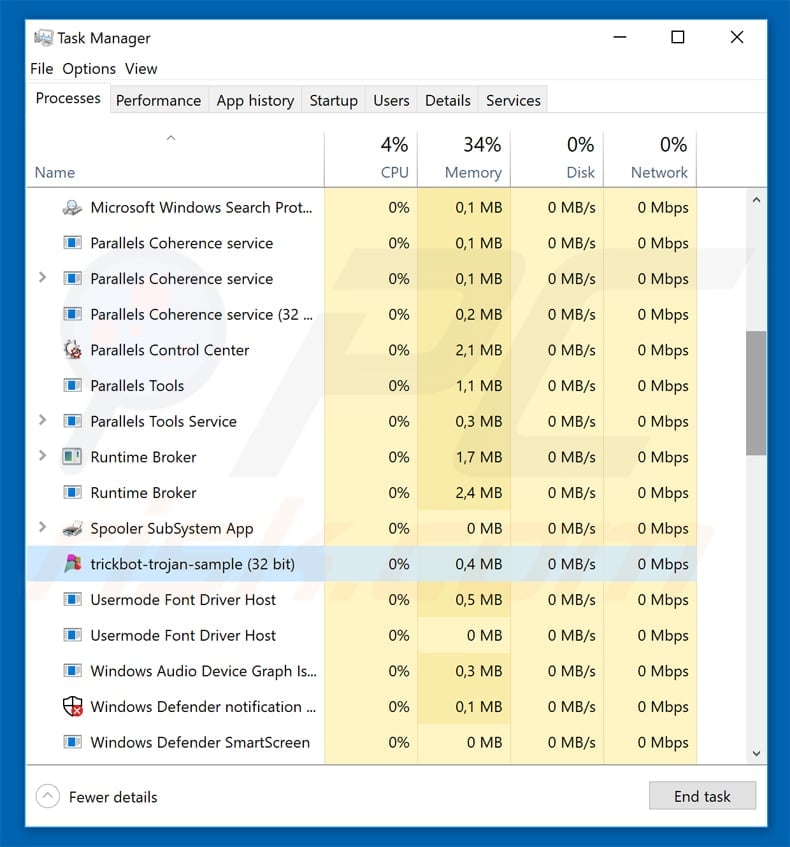

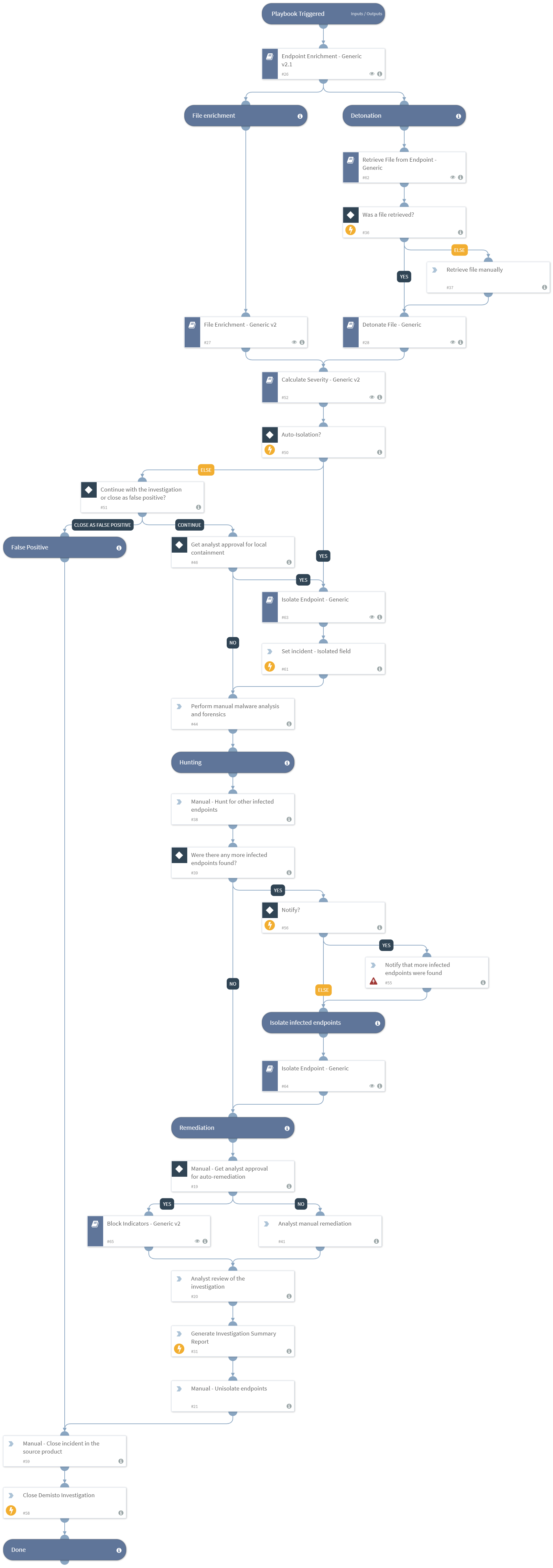











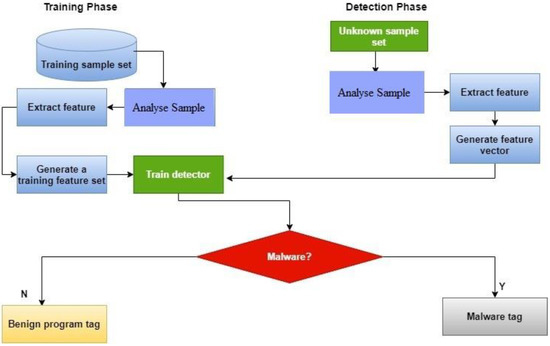
![Malware Detection flowchart [64] | Download Scientific Diagram](https://www.researchgate.net/publication/353349240/figure/fig1/AS:1047678087606273@1626797329751/Malware-Detection-flowchart-64.png)