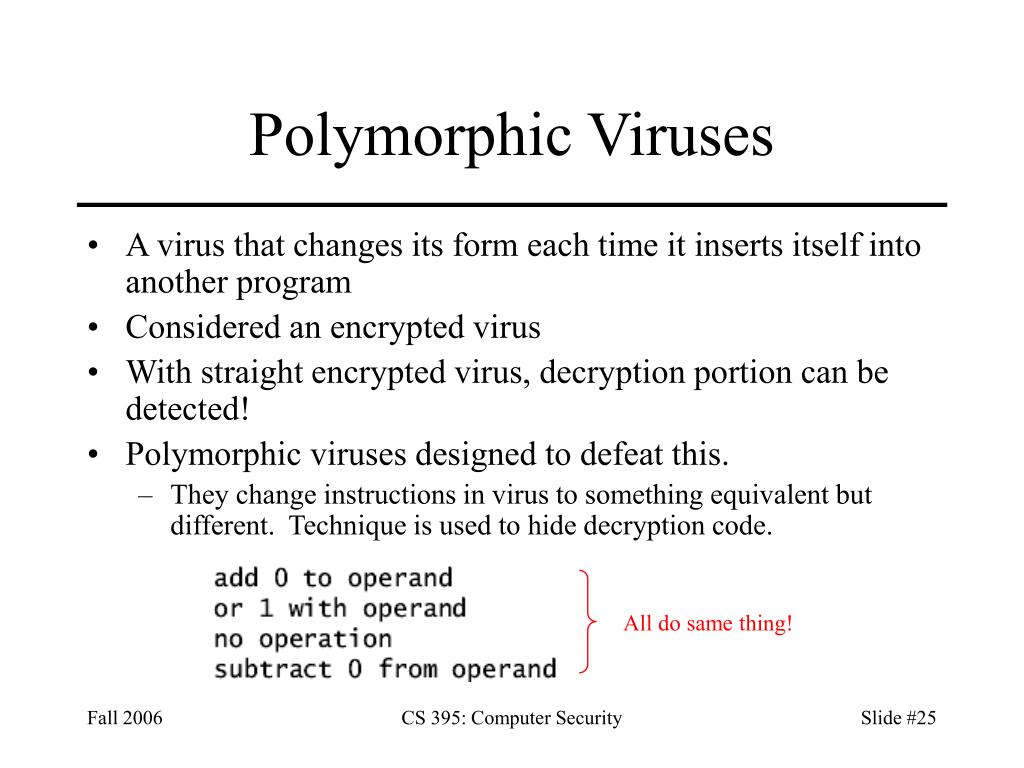
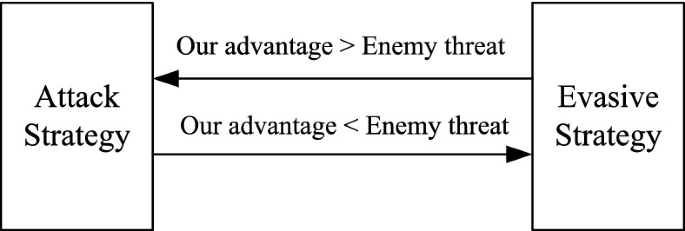
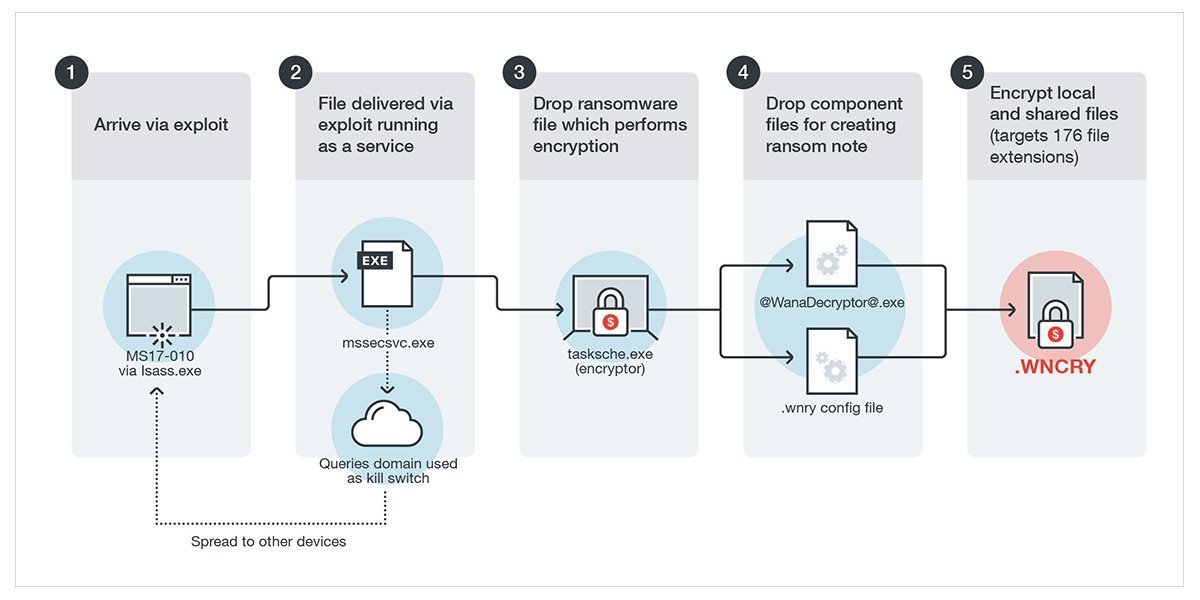
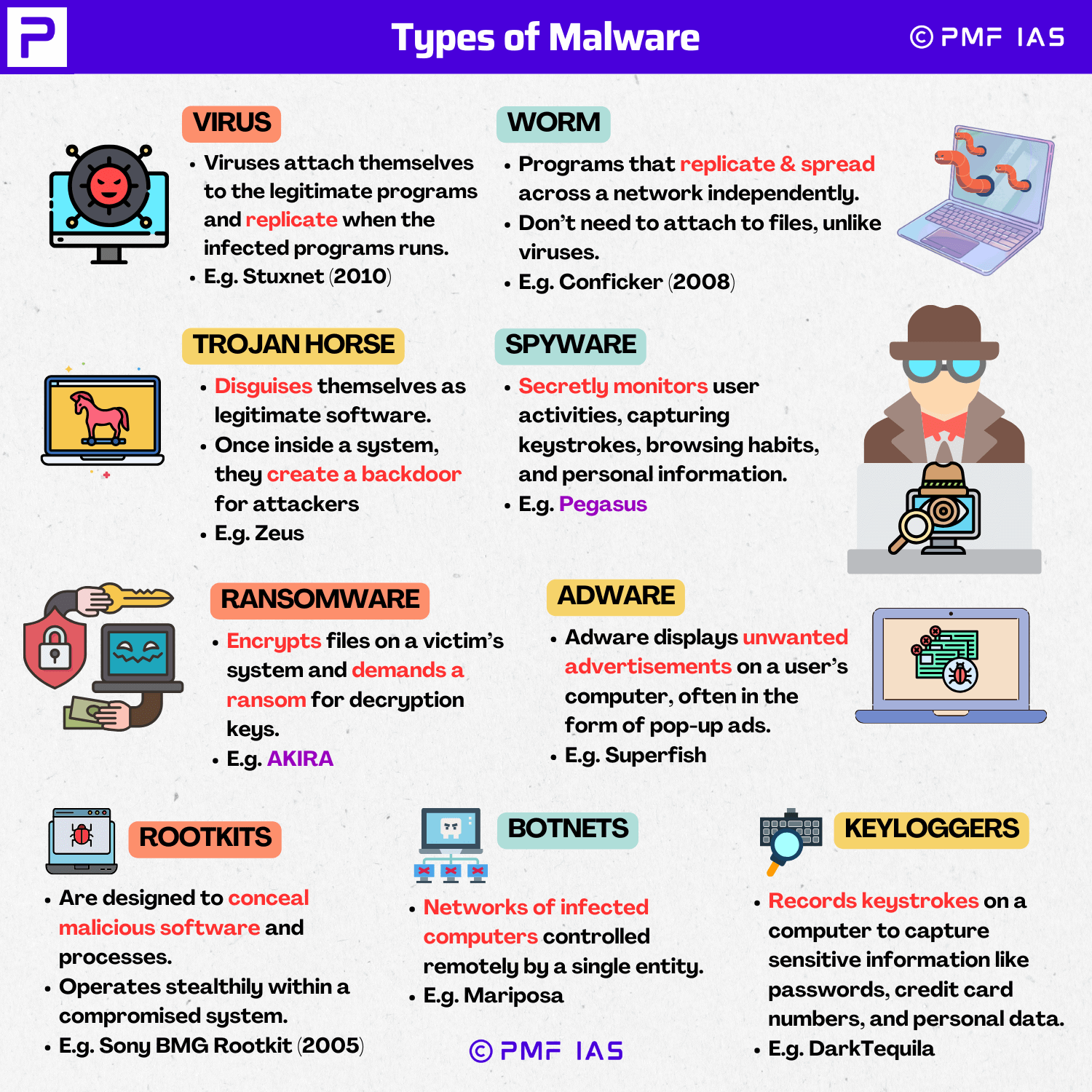
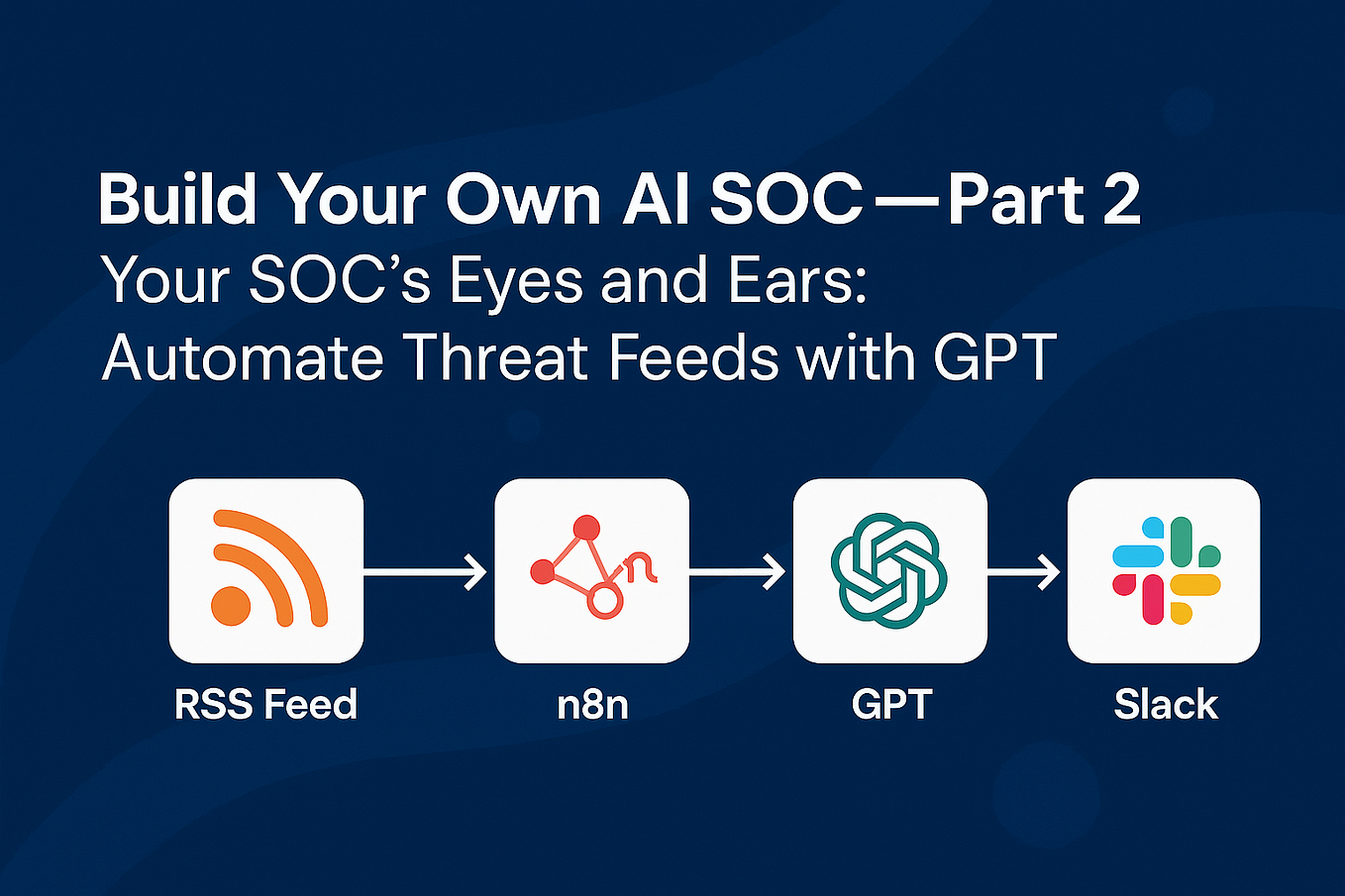
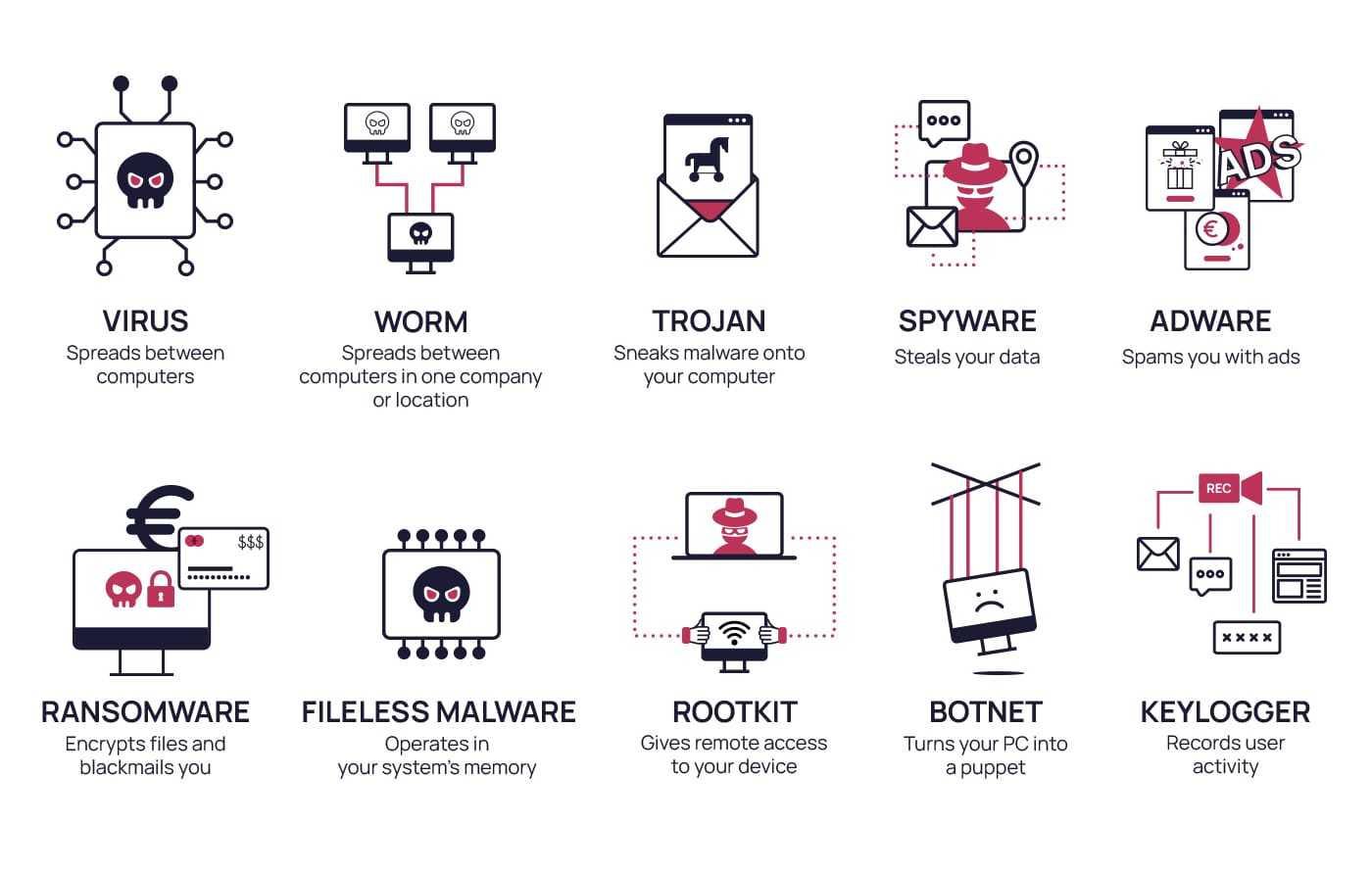
Celebrate competition through hundreds of action-packed polymorphic malware — understanding evasive attack strategies | by photographs. athletically capturing photography, images, and pictures. perfect for sports marketing and media. Our polymorphic malware — understanding evasive attack strategies | by collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All polymorphic malware — understanding evasive attack strategies | by images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our polymorphic malware — understanding evasive attack strategies | by collection for various creative and professional projects. Instant download capabilities enable immediate access to chosen polymorphic malware — understanding evasive attack strategies | by images. Cost-effective licensing makes professional polymorphic malware — understanding evasive attack strategies | by photography accessible to all budgets. Each image in our polymorphic malware — understanding evasive attack strategies | by gallery undergoes rigorous quality assessment before inclusion. The polymorphic malware — understanding evasive attack strategies | by archive serves professionals, educators, and creatives across diverse industries. Whether for commercial projects or personal use, our polymorphic malware — understanding evasive attack strategies | by collection delivers consistent excellence. The polymorphic malware — understanding evasive attack strategies | by collection represents years of careful curation and professional standards.















































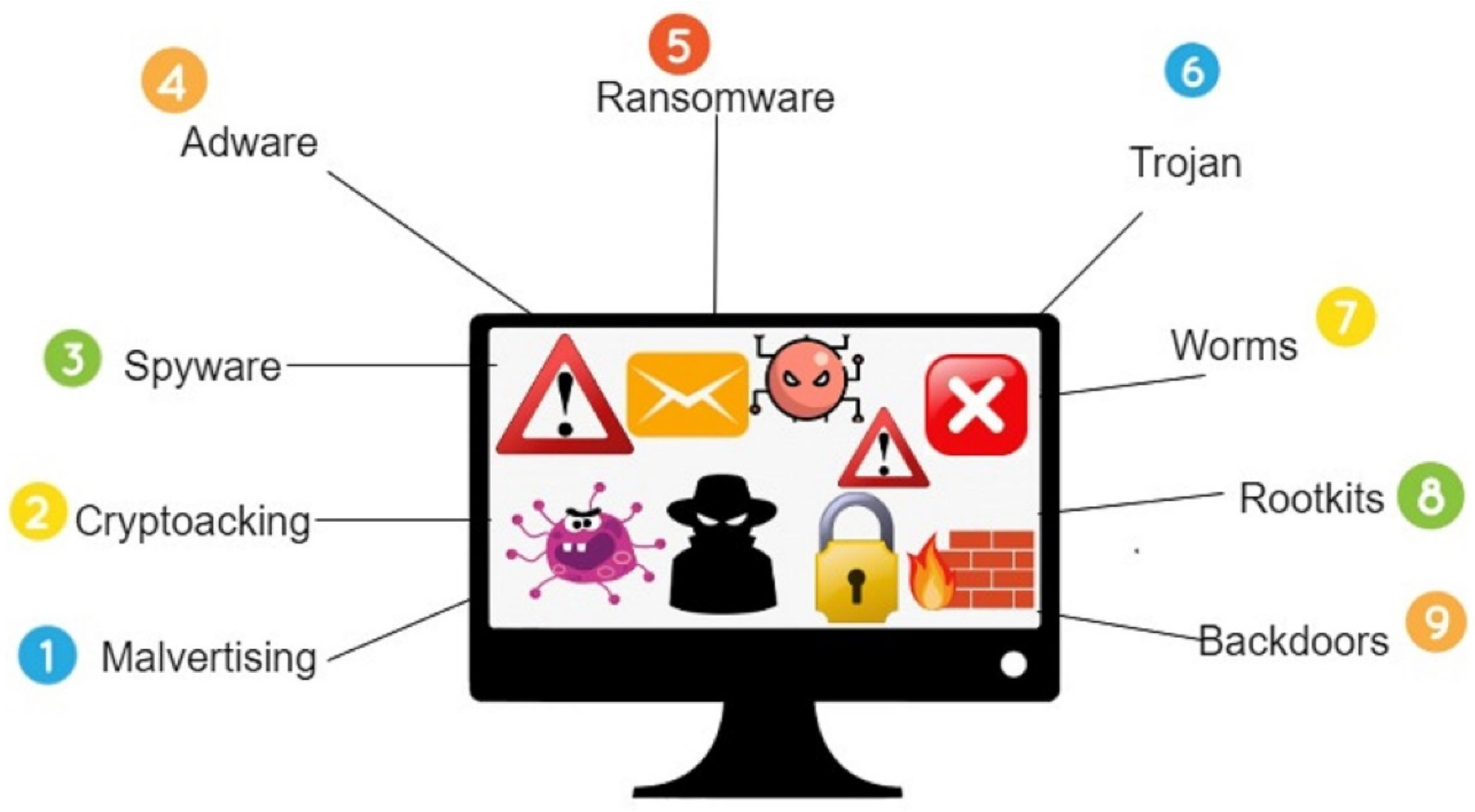








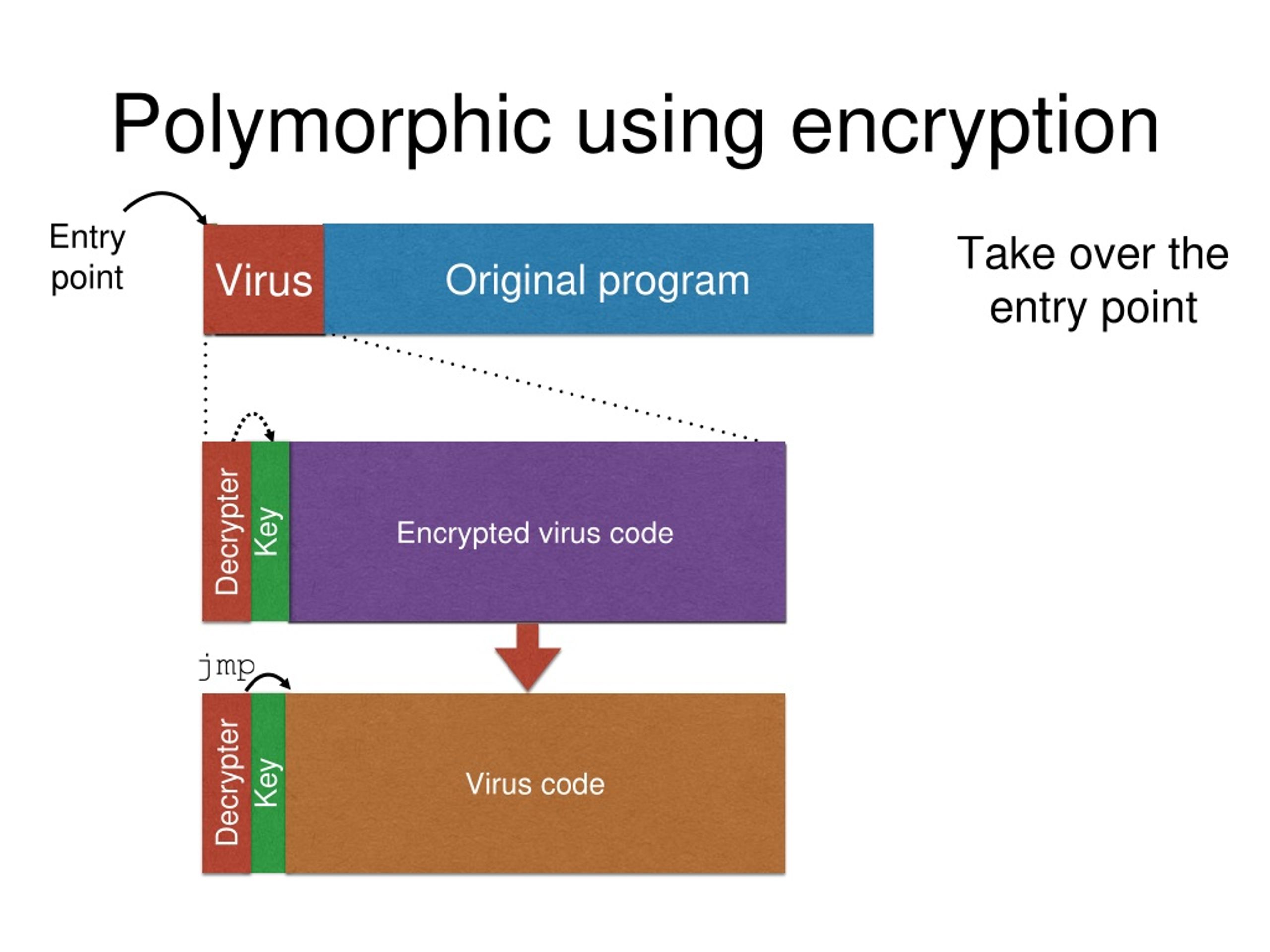





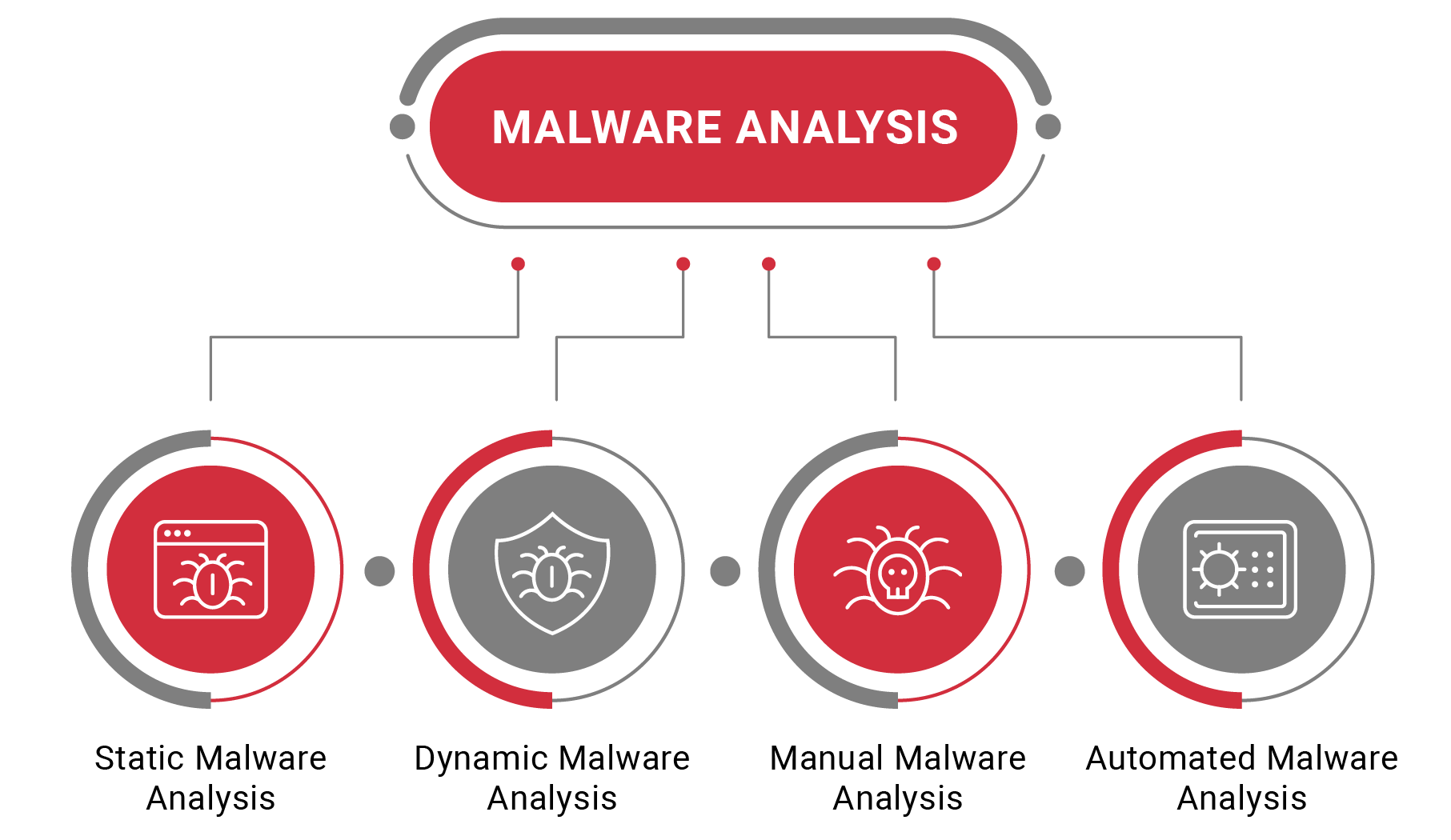

















![Blockchain attacks taxonomy as proposed by [94] | Download Scientific ...](https://www.researchgate.net/publication/374732678/figure/fig2/AS:11431281199322491@1697563367266/Blockchain-attacks-taxonomy-as-proposed-by-94.png)


.jpg)