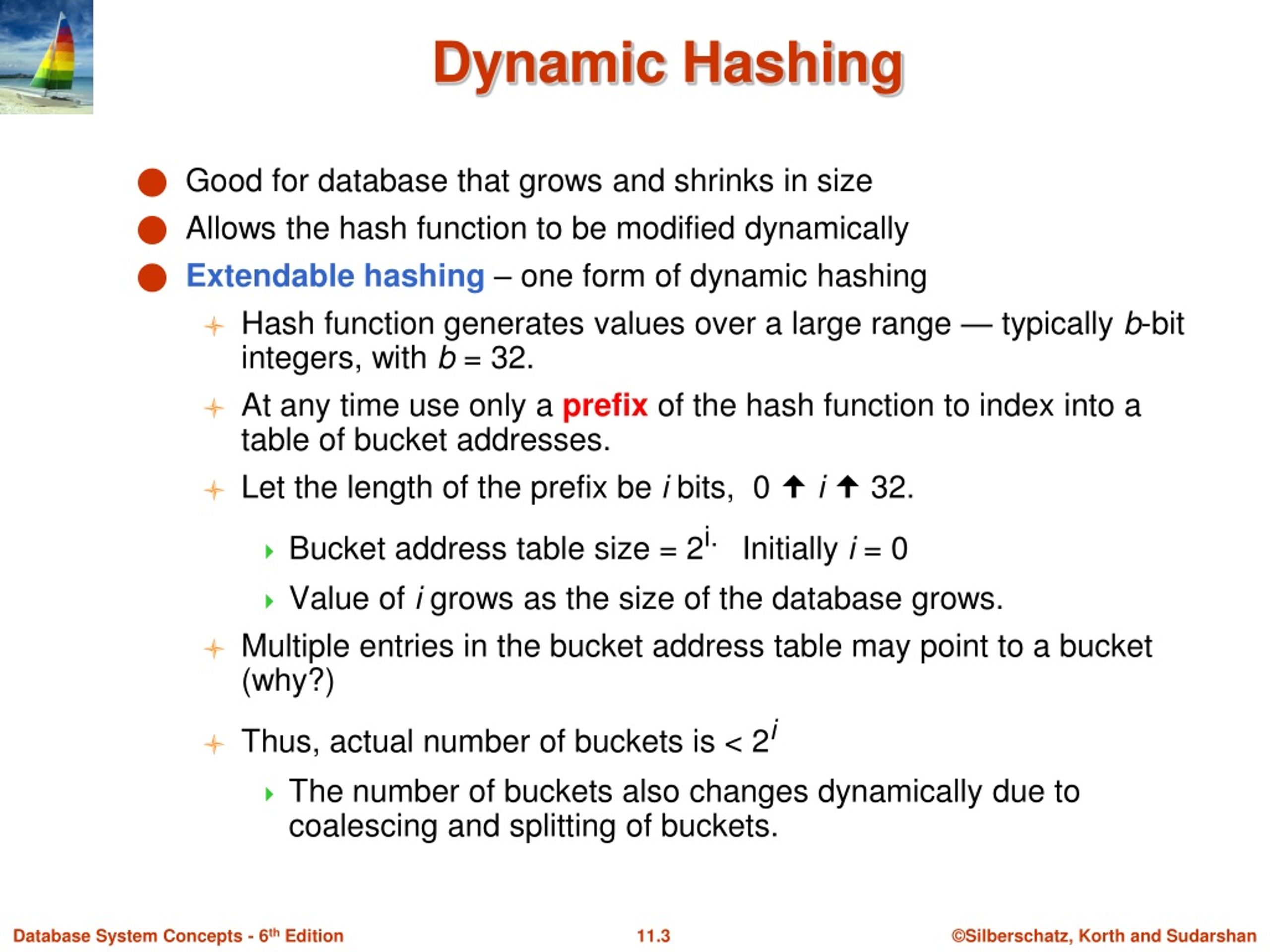
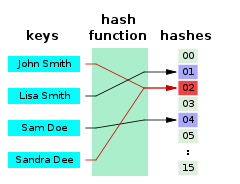
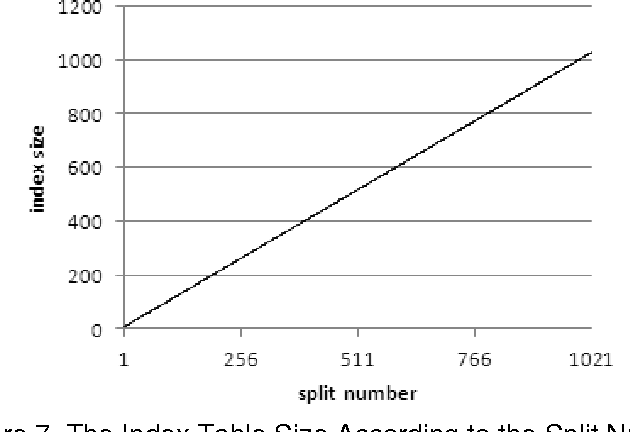
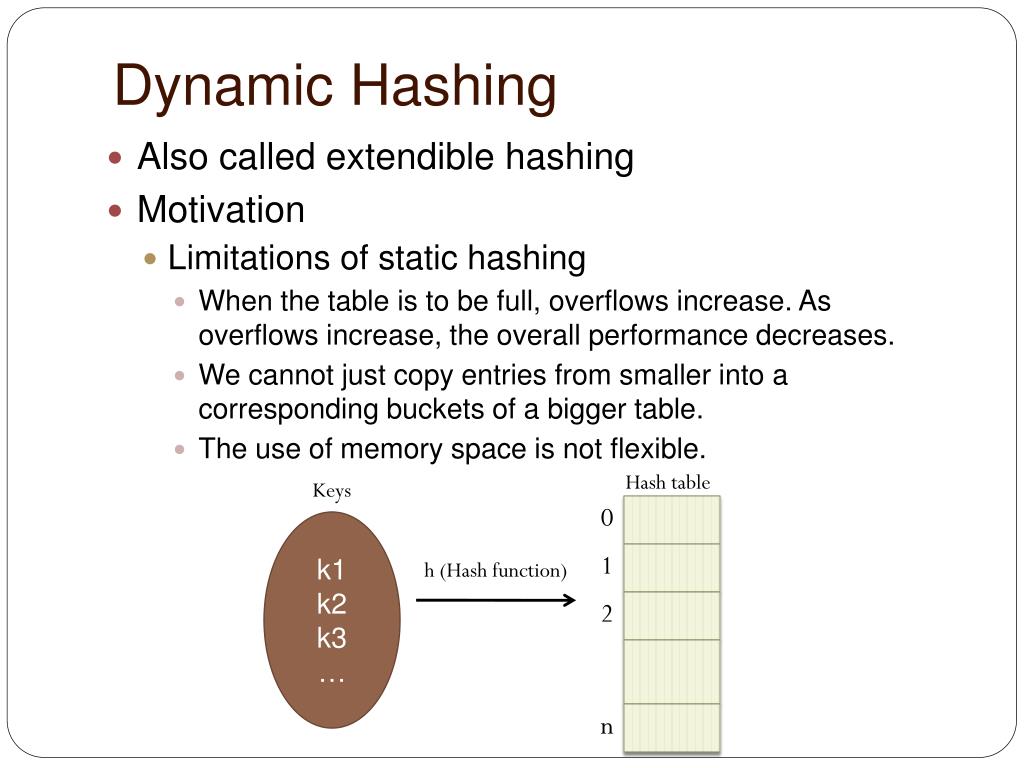
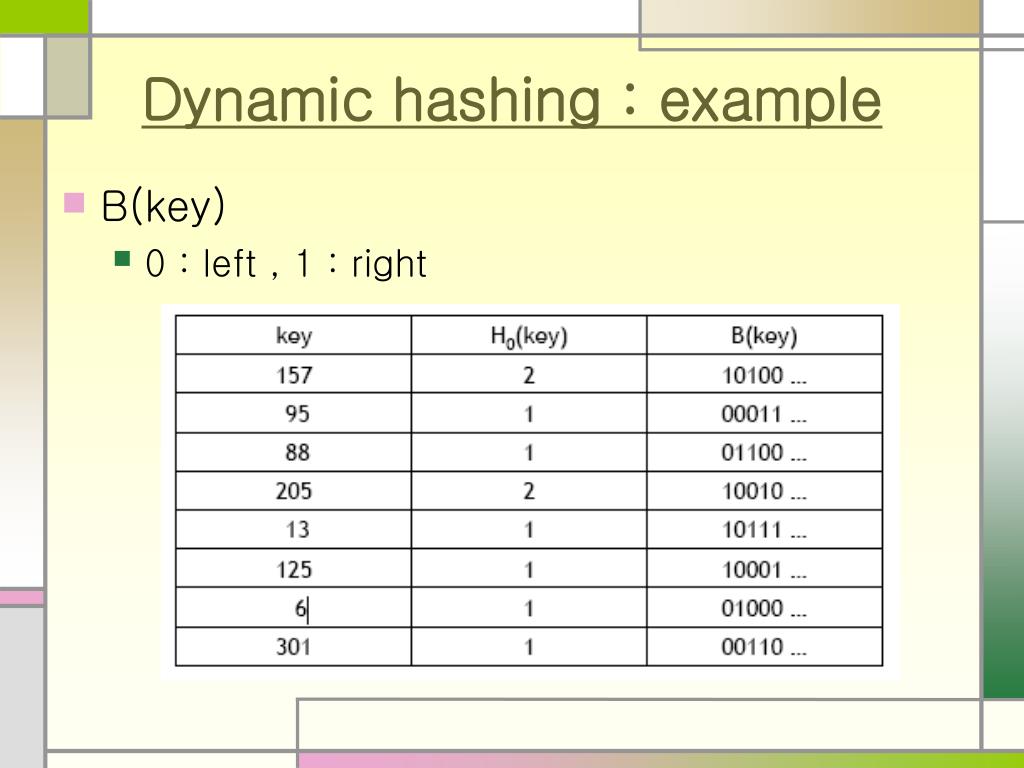
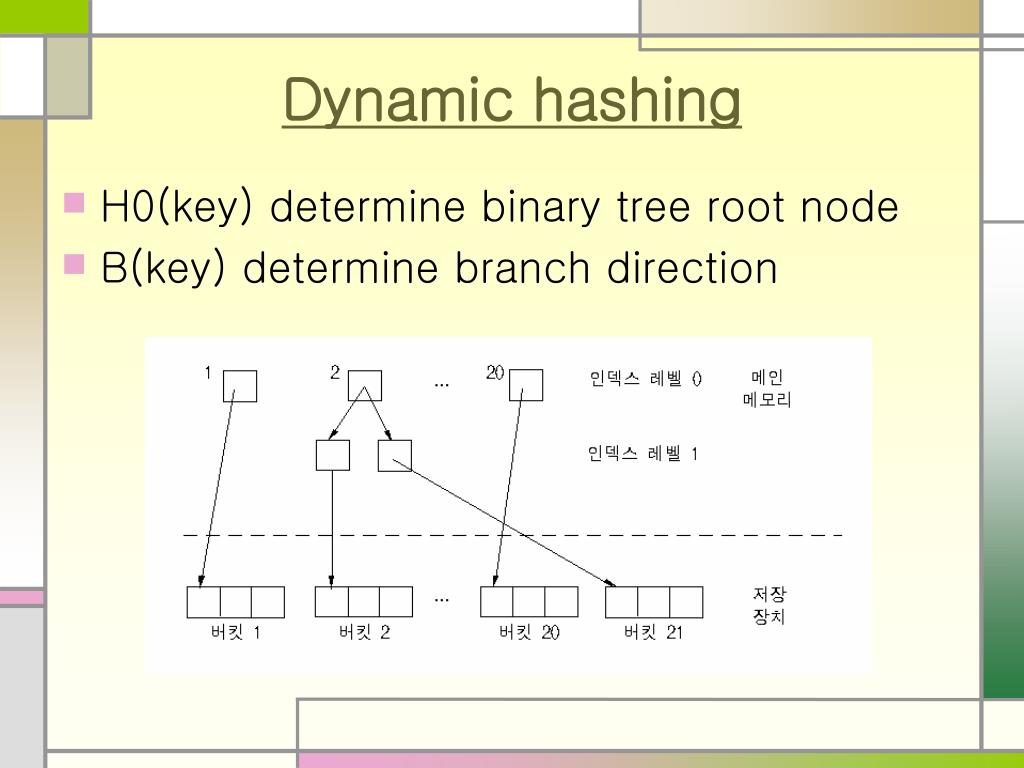
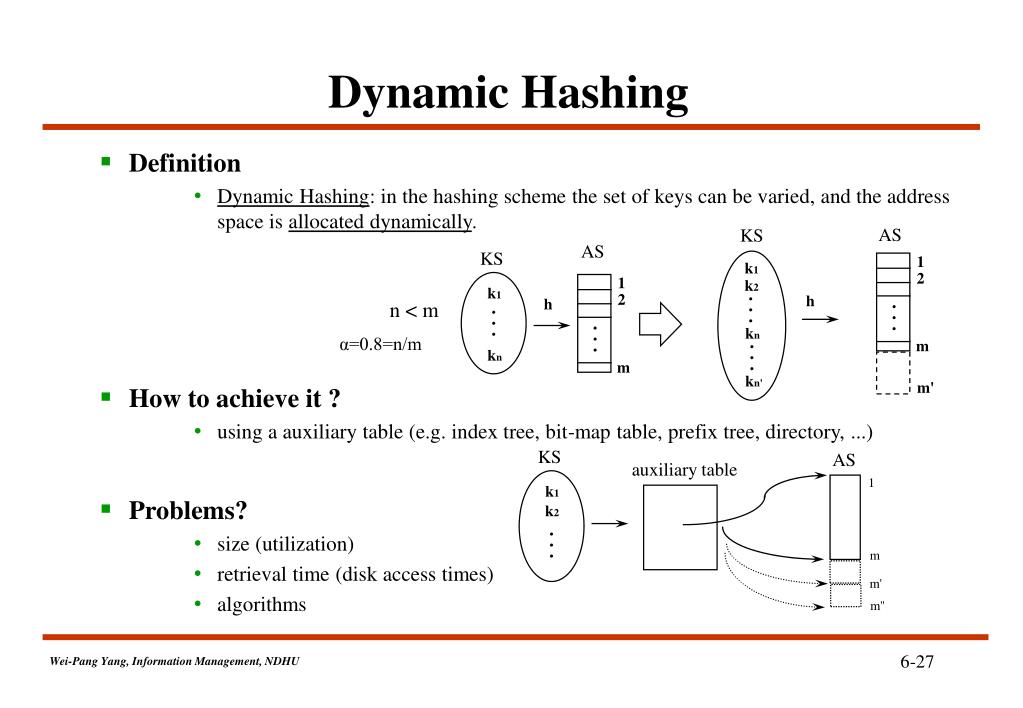
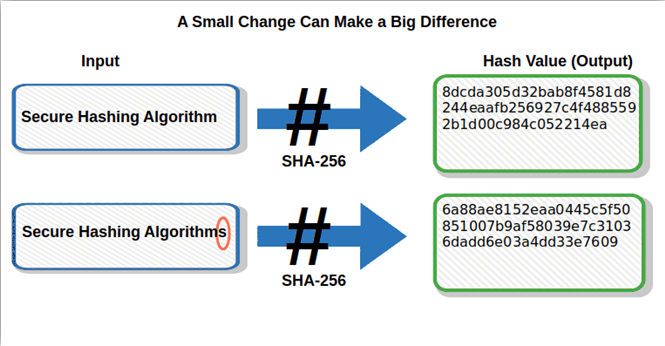
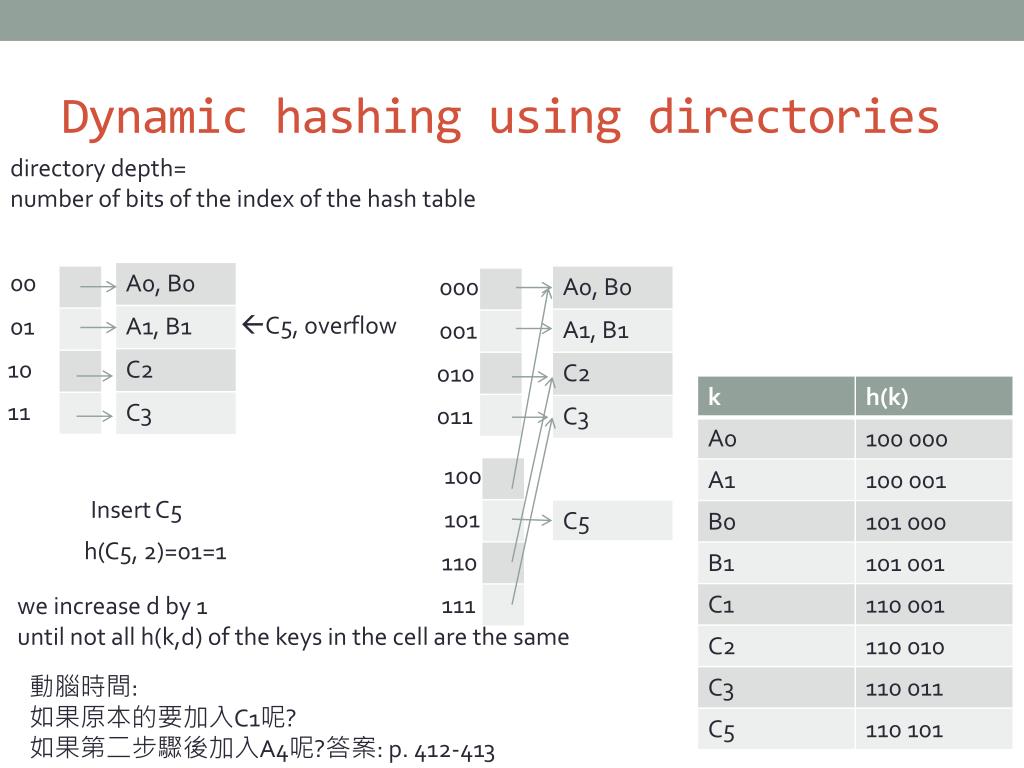
Indulge in the remarkable luxury of our figure 1 from a dynamic hashing algorithm suitable for embedded system collection with vast arrays of exquisite images. featuring elegant examples of play, doll, and game. perfect for high-end marketing and branding. Our figure 1 from a dynamic hashing algorithm suitable for embedded system collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All figure 1 from a dynamic hashing algorithm suitable for embedded system images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our figure 1 from a dynamic hashing algorithm suitable for embedded system gallery offers diverse visual resources to bring your ideas to life. Each image in our figure 1 from a dynamic hashing algorithm suitable for embedded system gallery undergoes rigorous quality assessment before inclusion. Diverse style options within the figure 1 from a dynamic hashing algorithm suitable for embedded system collection suit various aesthetic preferences. Our figure 1 from a dynamic hashing algorithm suitable for embedded system database continuously expands with fresh, relevant content from skilled photographers. Whether for commercial projects or personal use, our figure 1 from a dynamic hashing algorithm suitable for embedded system collection delivers consistent excellence.















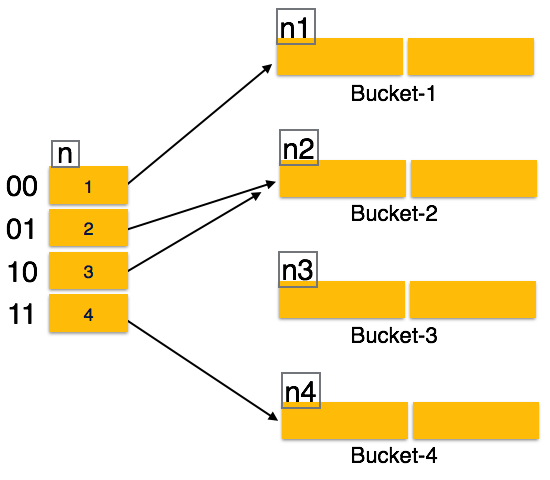
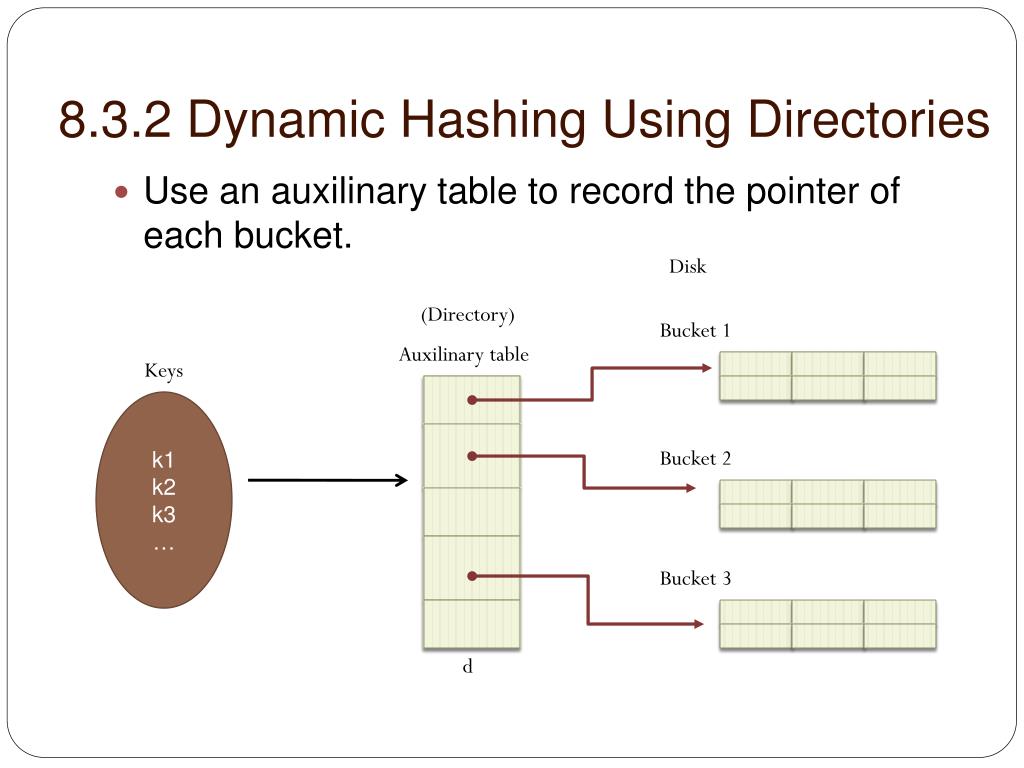

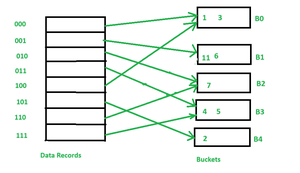
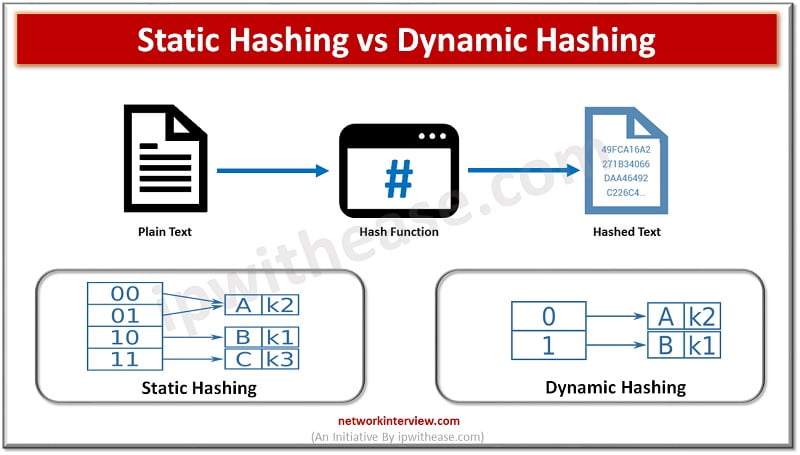
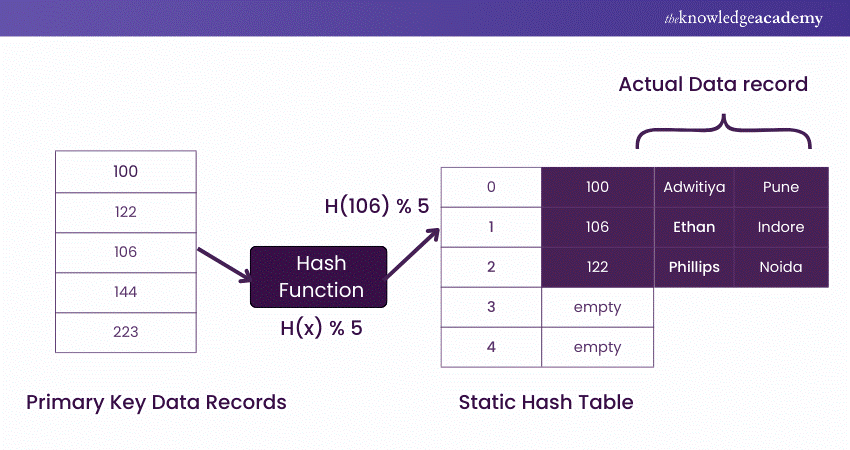


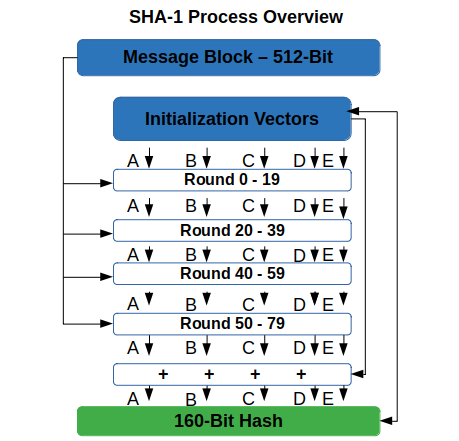









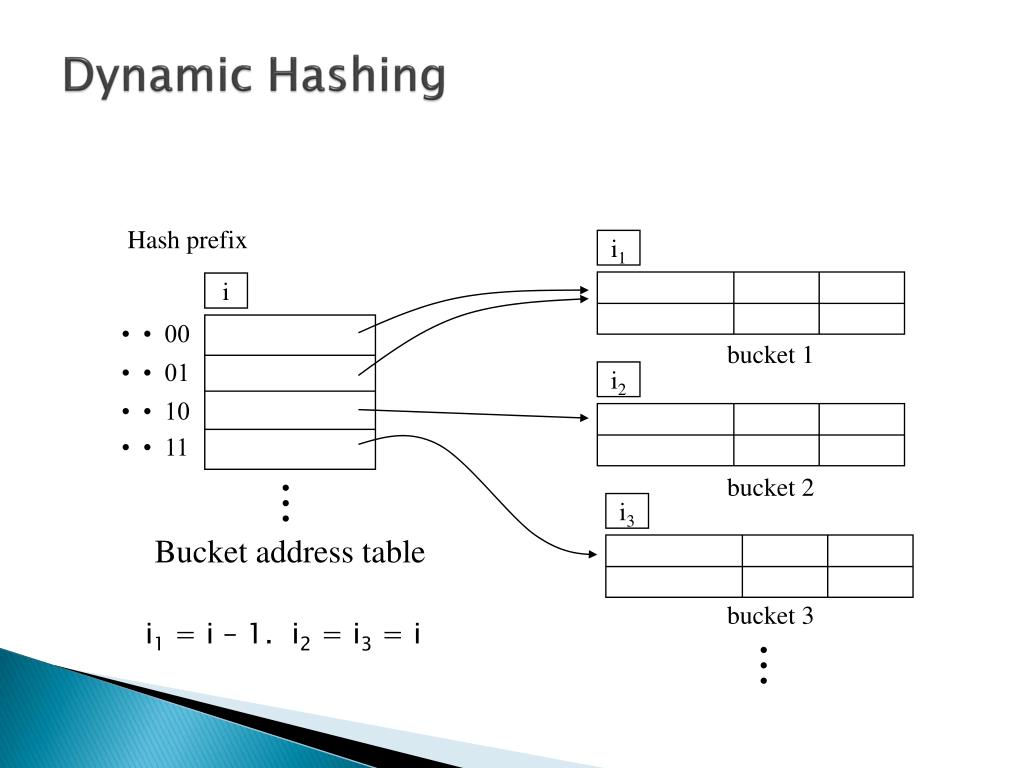
+Hash+structure+after+insertion+of+Gold+and+El+Said+records.jpg)





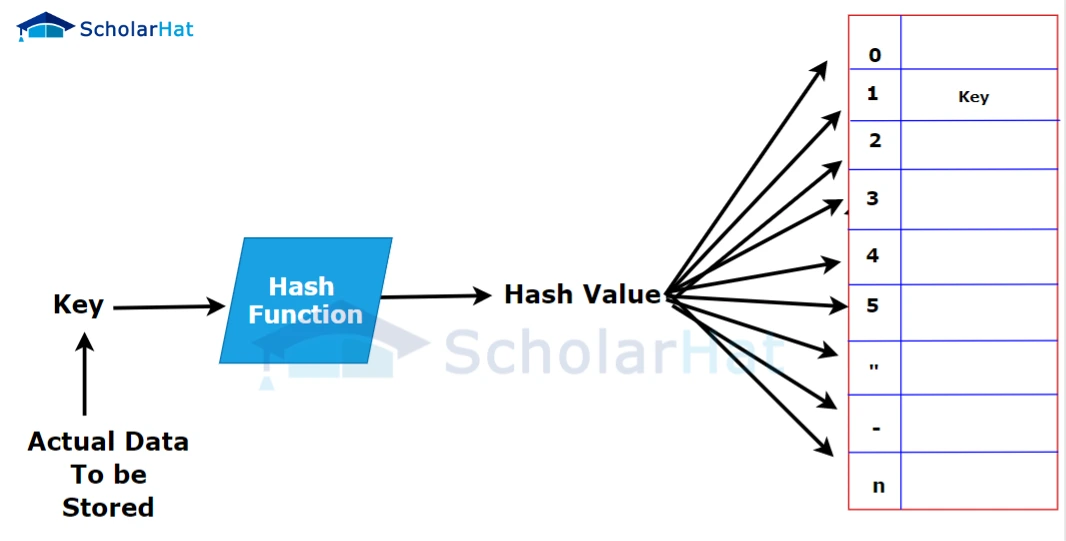
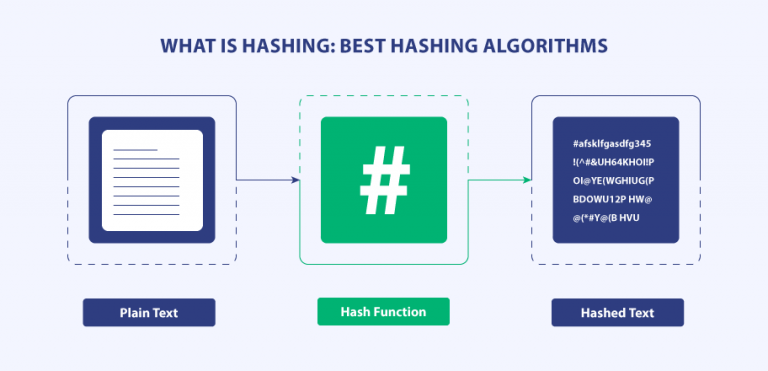
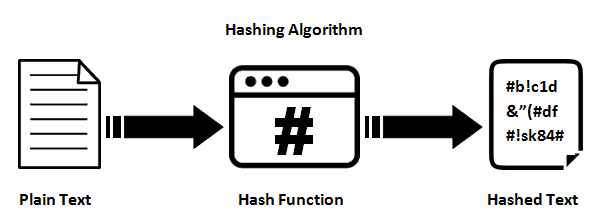
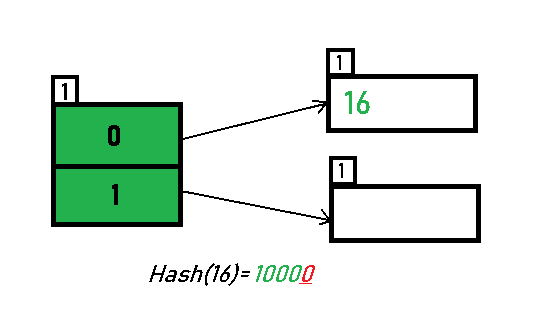
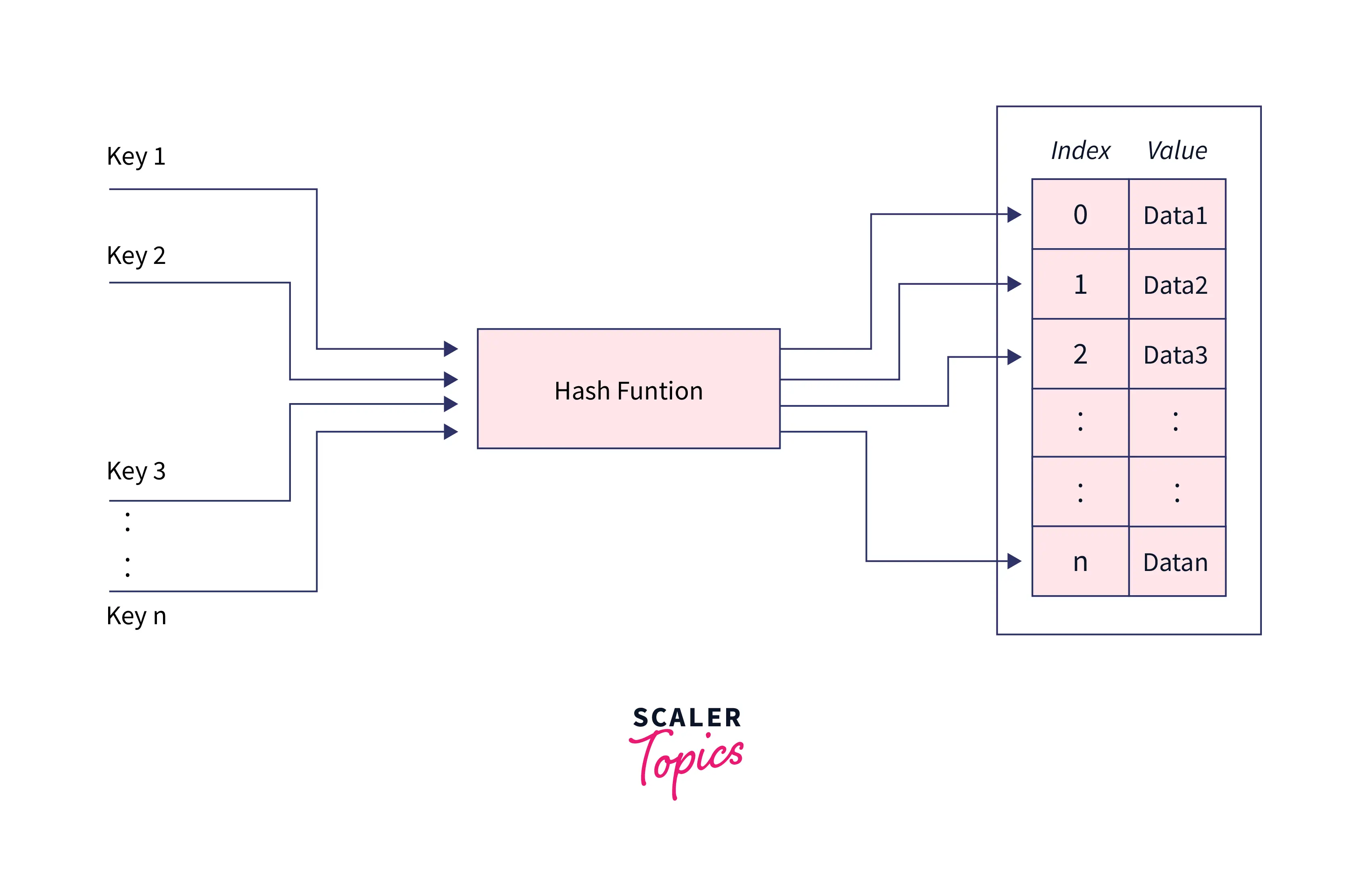
![Hash Function in Data Structure: Types and Functions [With Examples]](https://dotnettrickscloud.blob.core.windows.net/article/data%20structures/3720230920105435.webp)
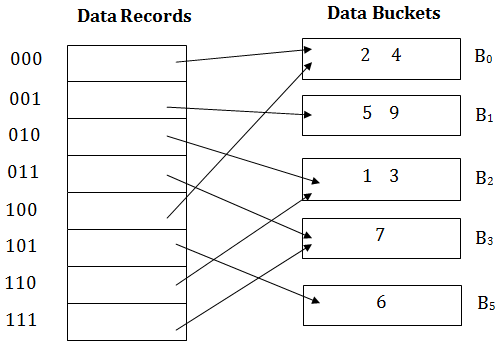



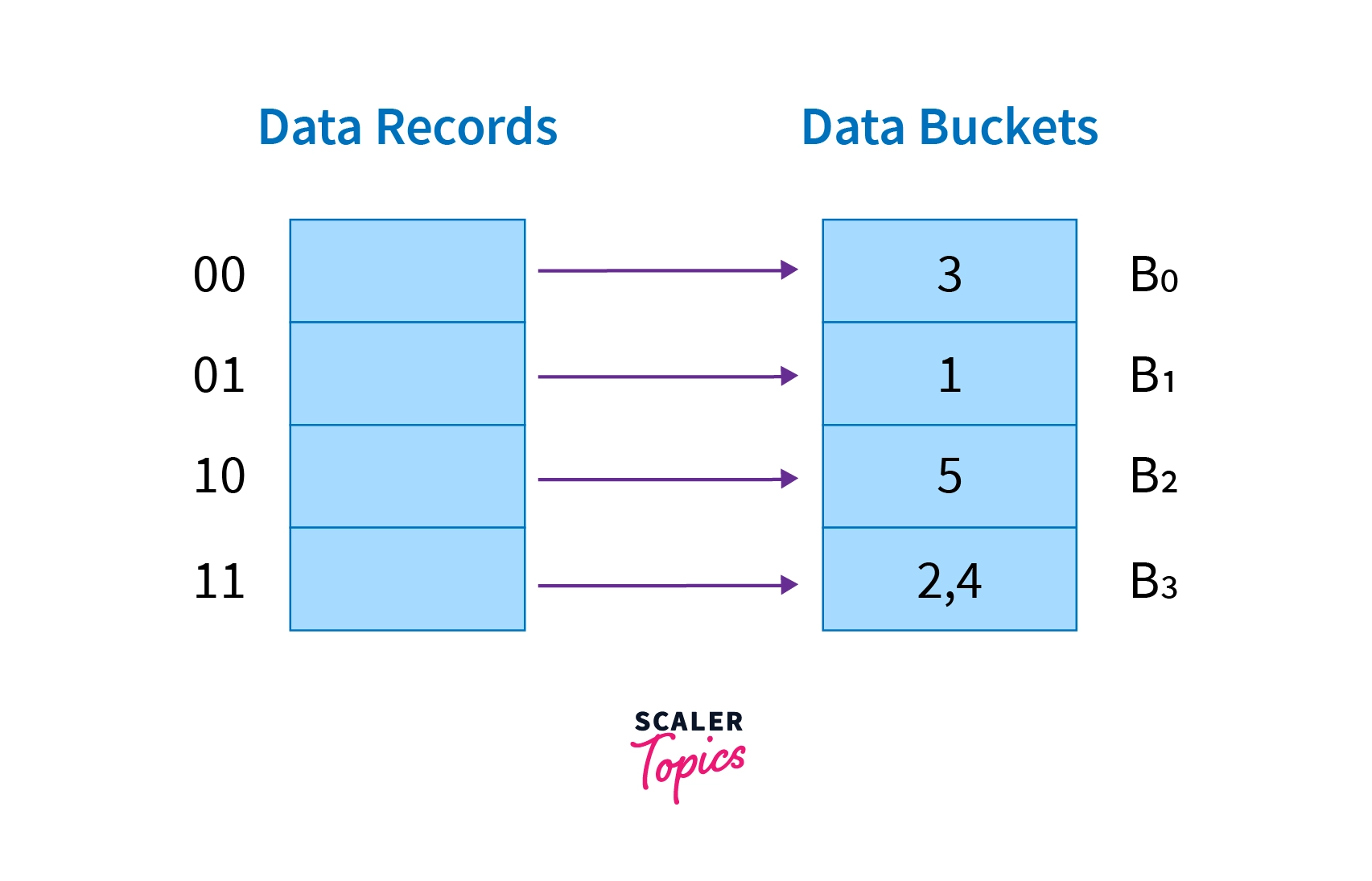


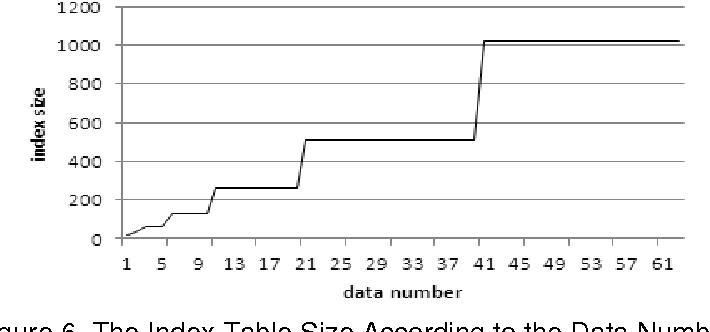
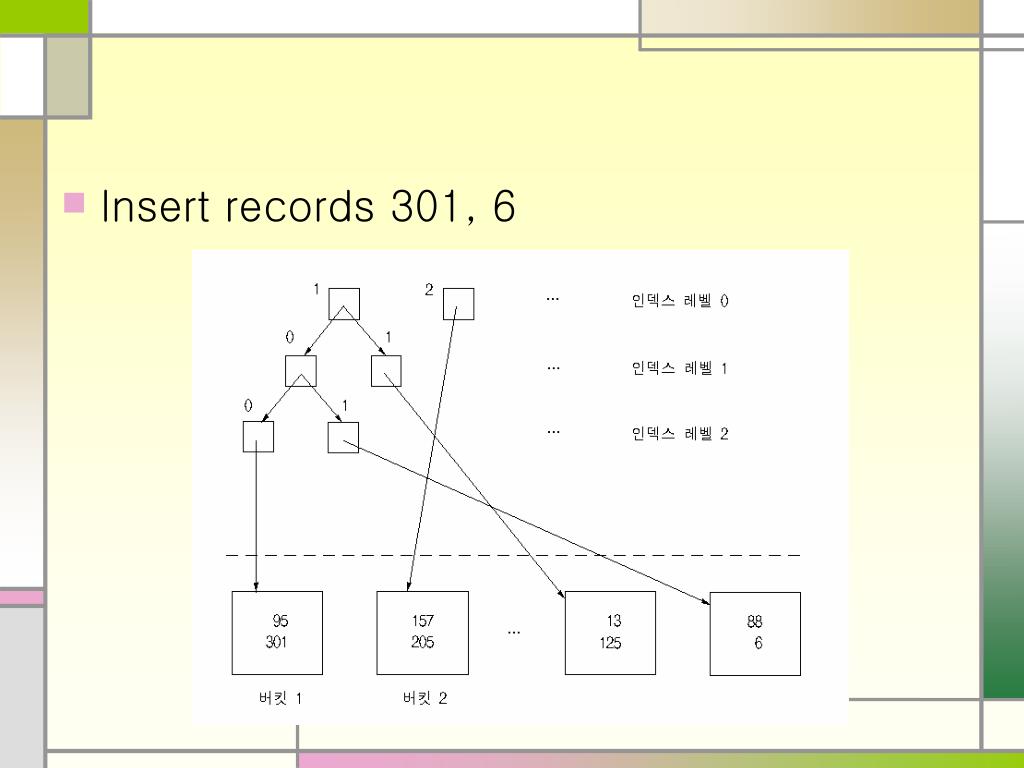
+And+after+insertion+of+Kim+record+in+previous.jpg)
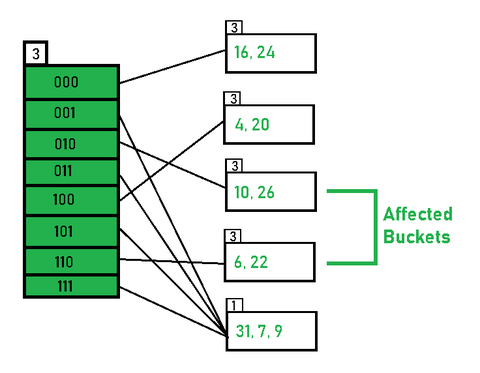

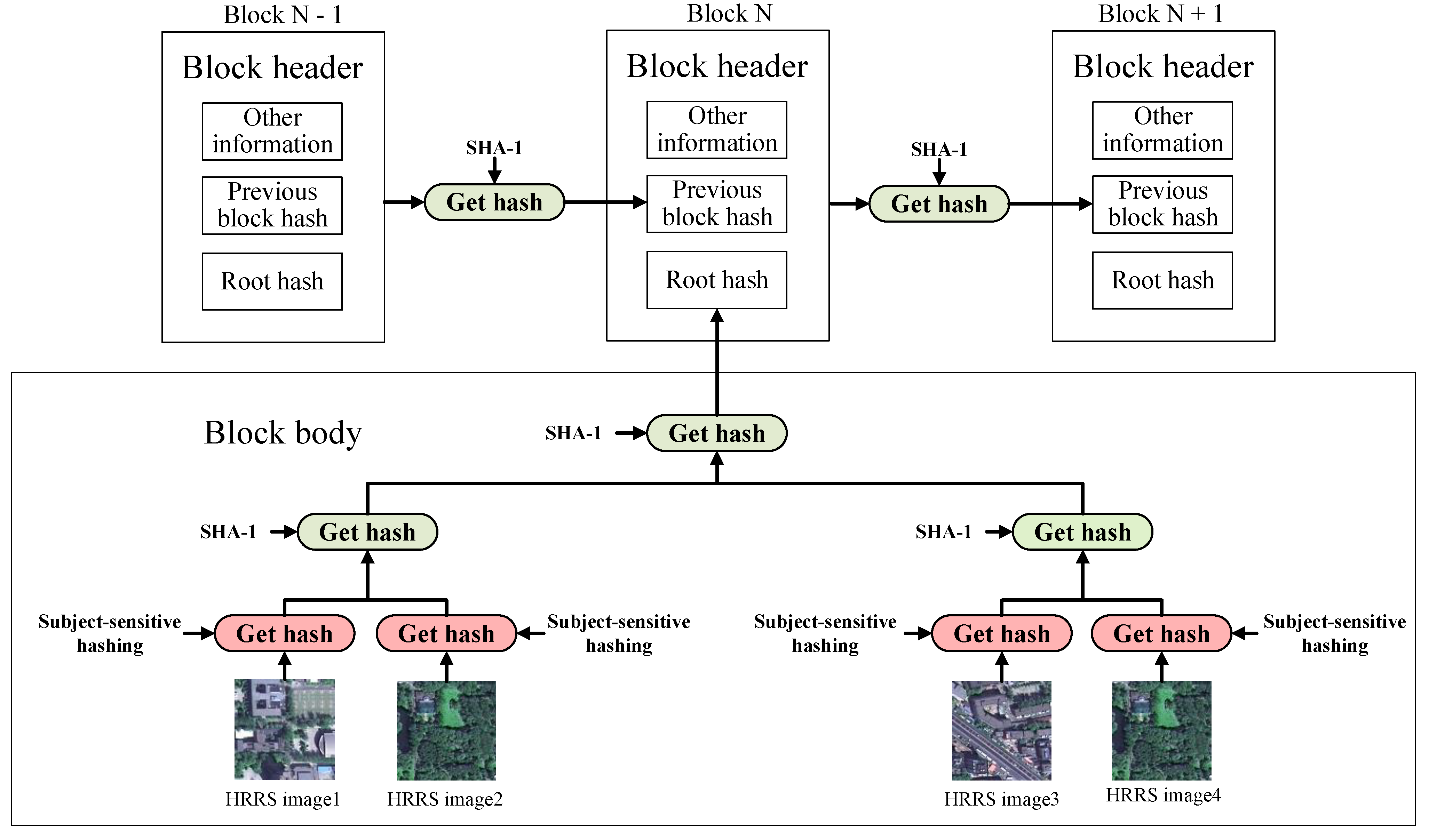

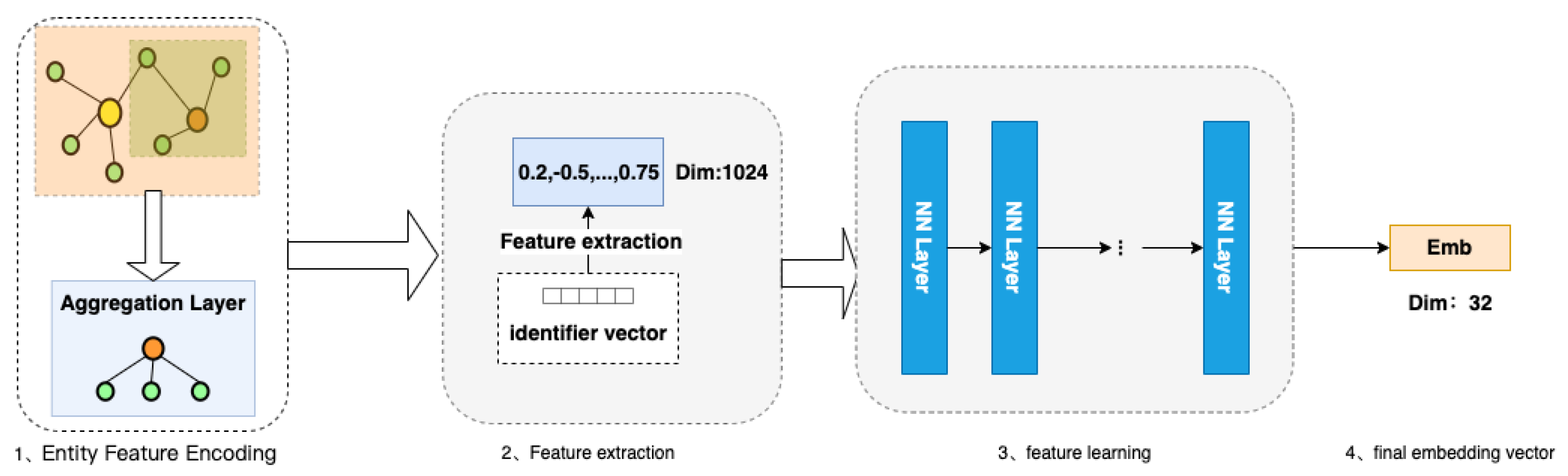
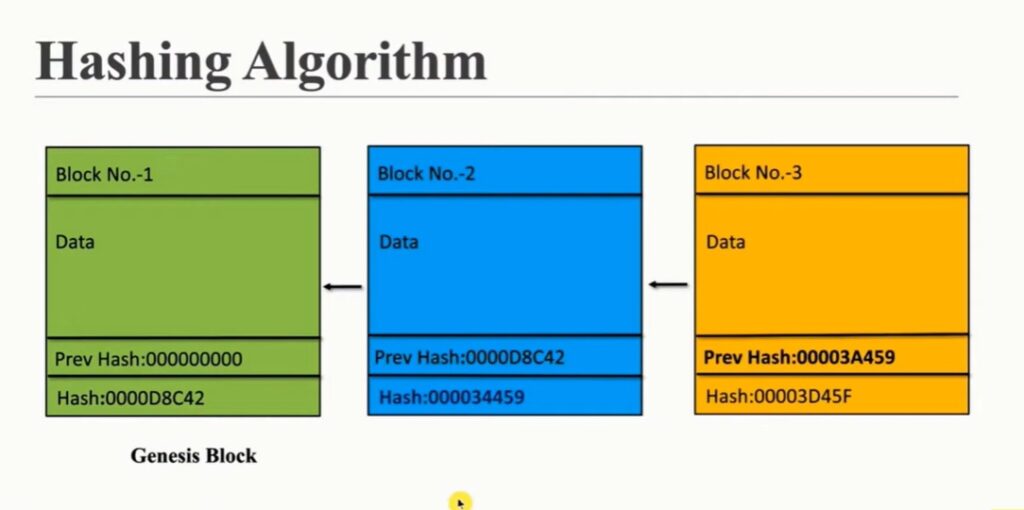





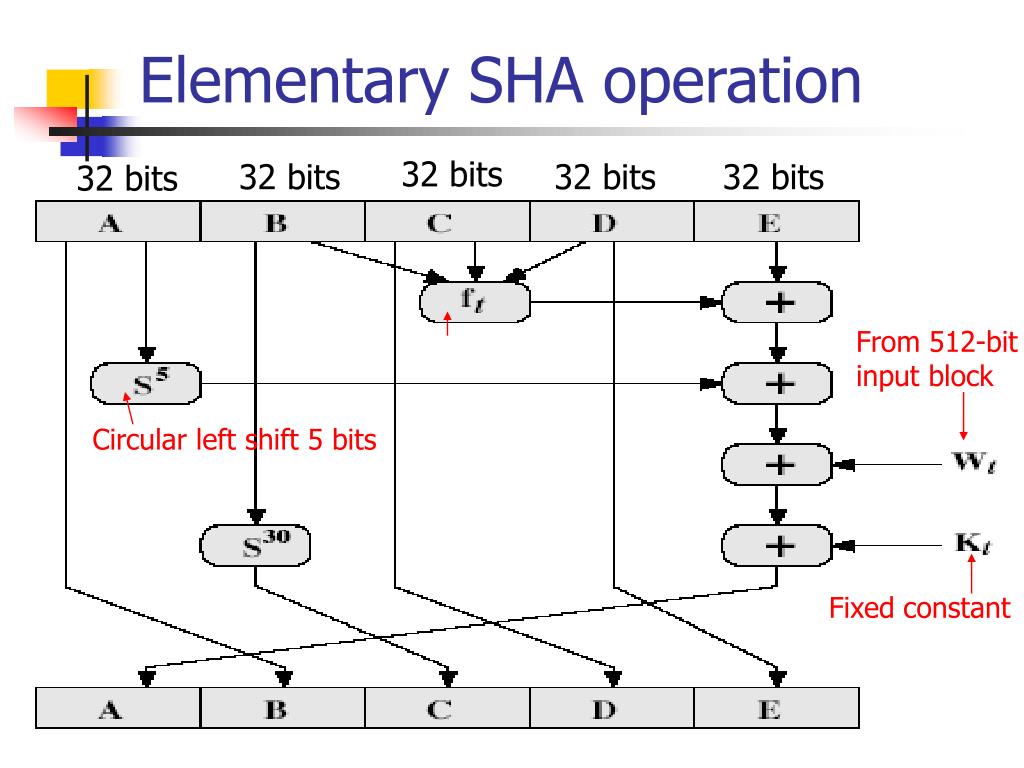
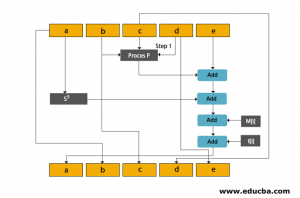
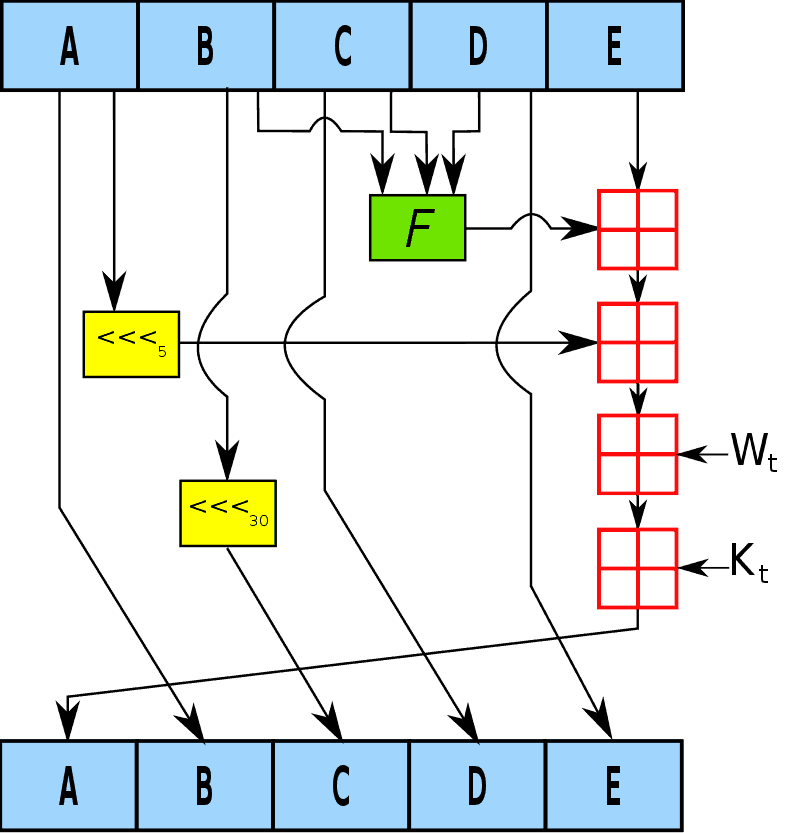
![2: How a Round in the SHA-1 Hashing Algorithm Works [MRR08] | Download ...](https://www.researchgate.net/publication/220080811/figure/fig10/AS:669006163873795@1536514907284/How-a-Round-in-the-SHA-1-Hashing-Algorithm-Works-MRR08.jpg)







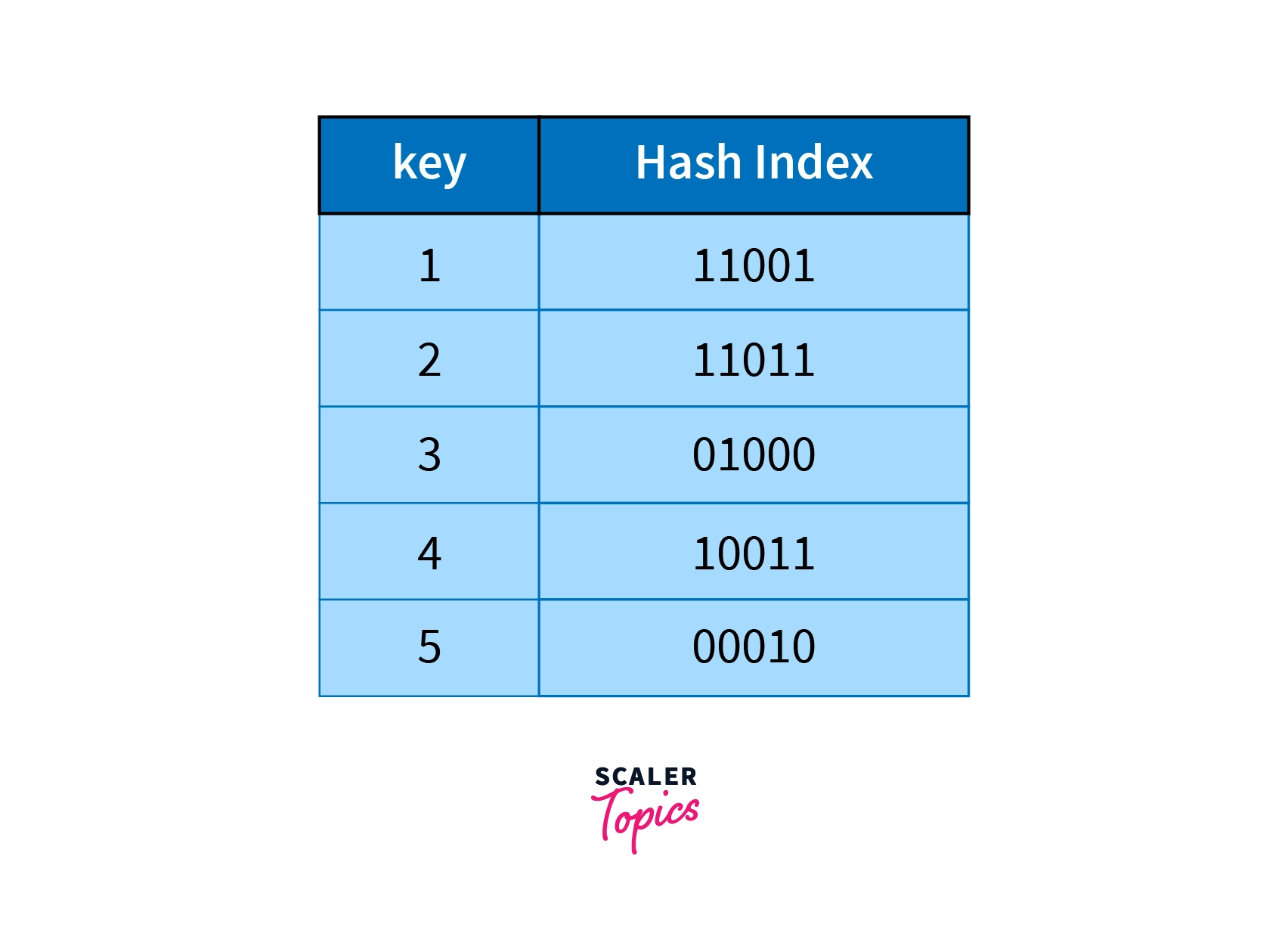
.jpg)