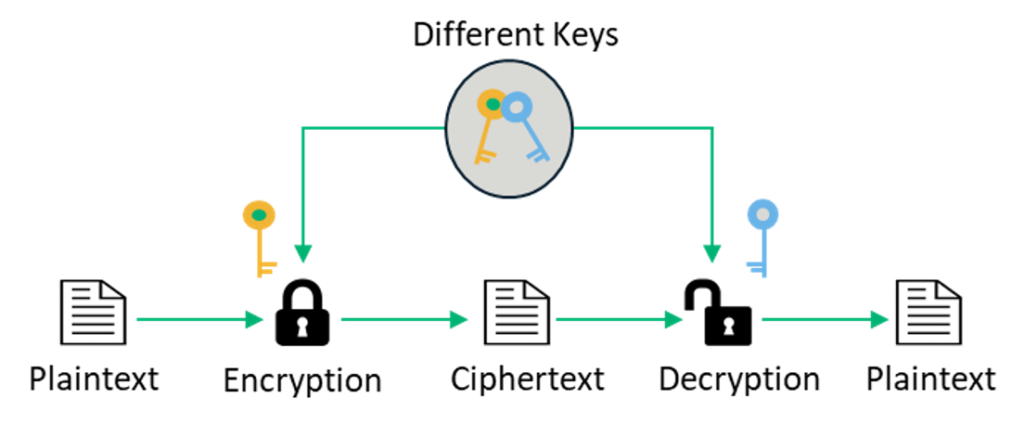
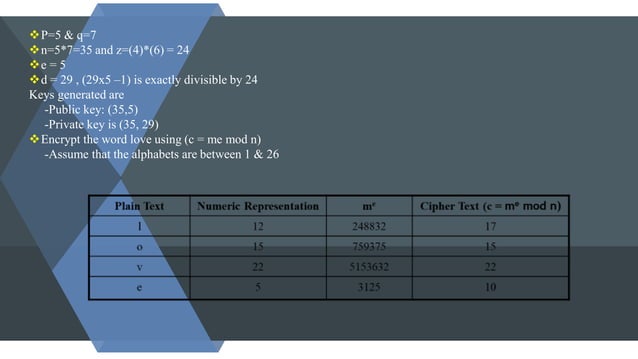
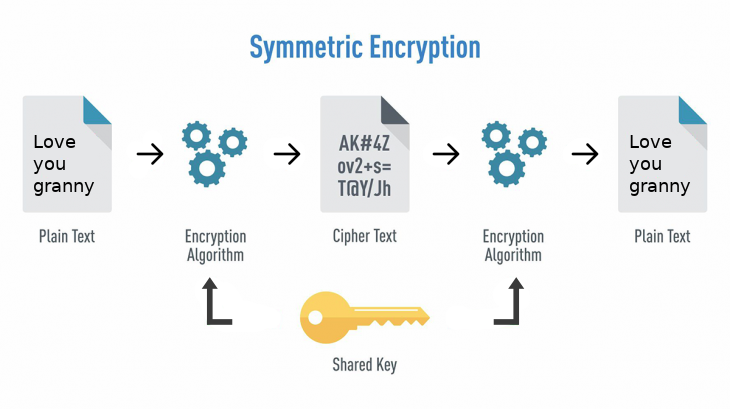
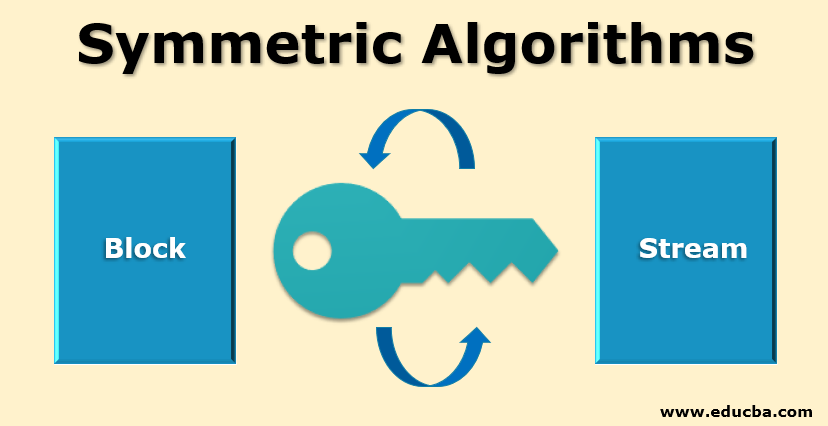
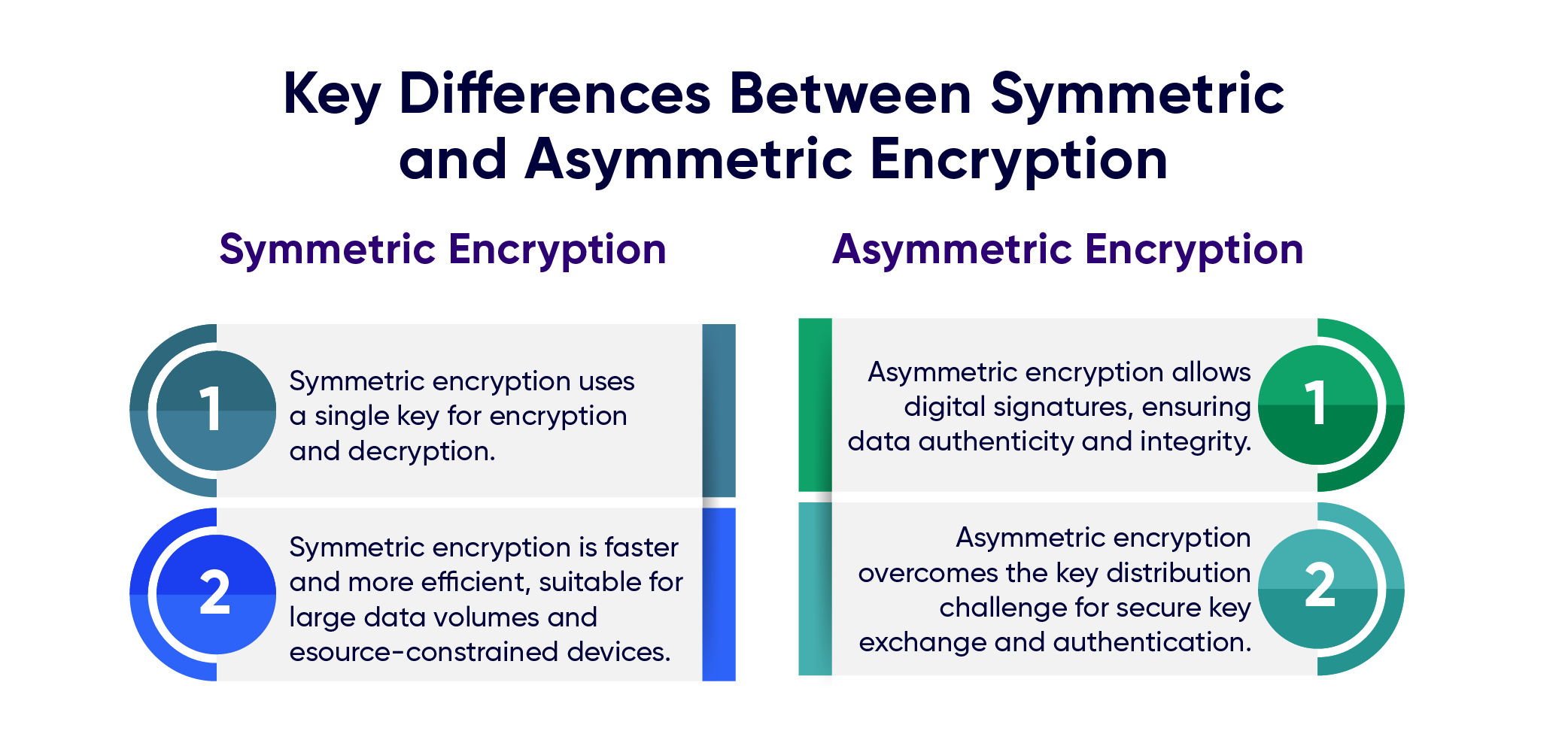
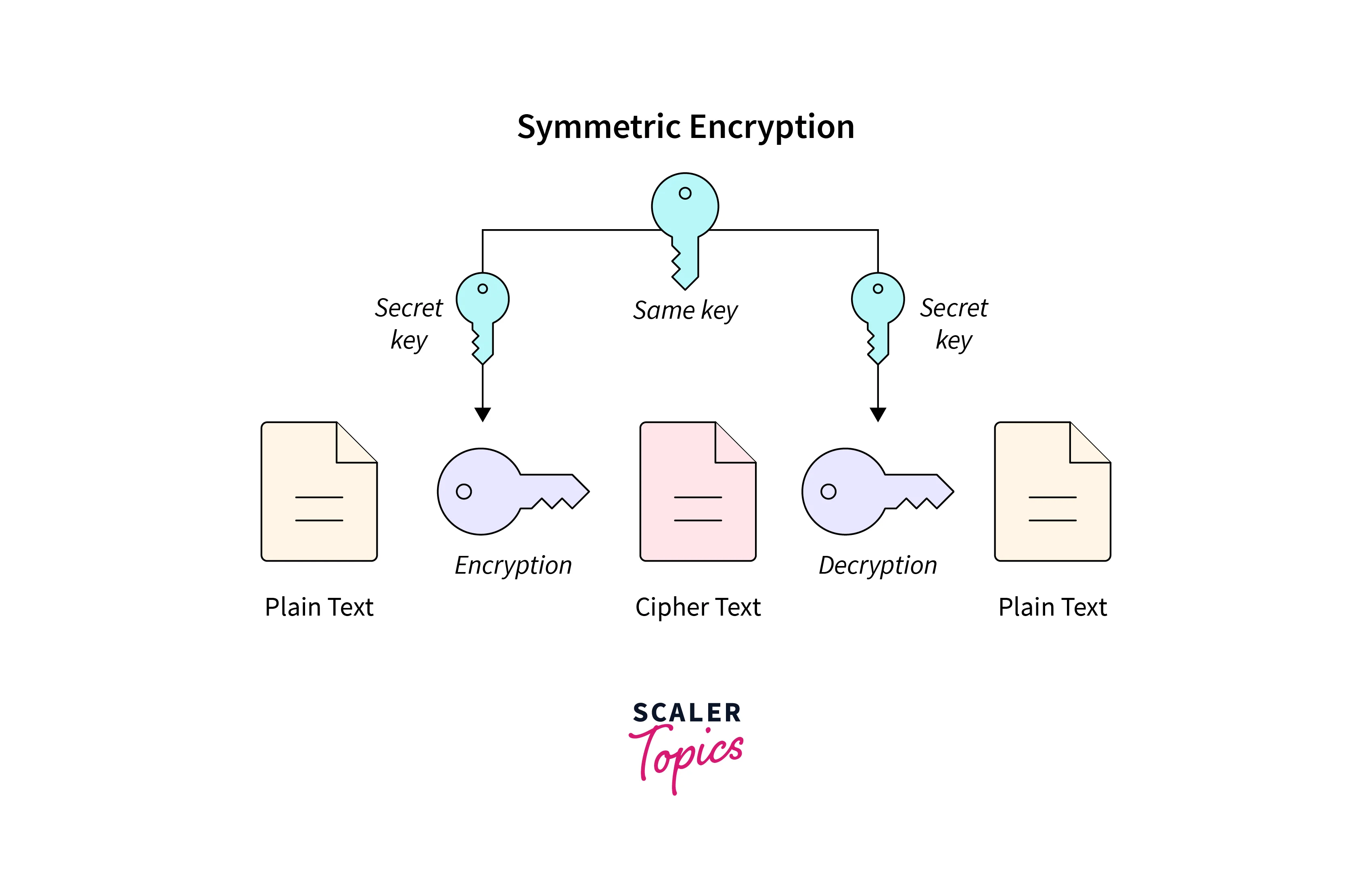
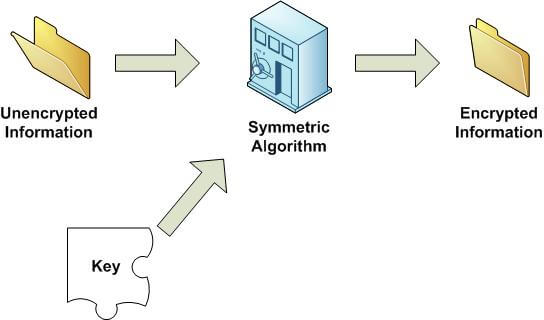
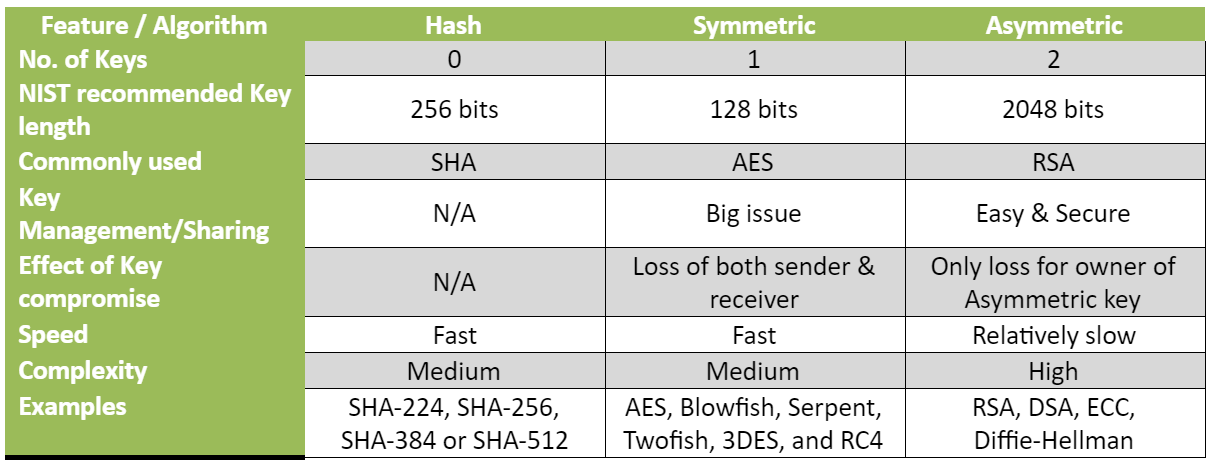
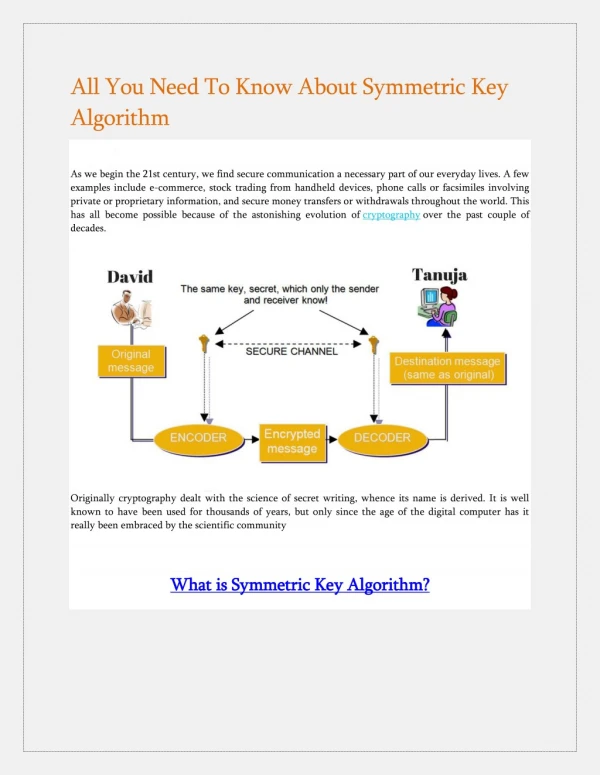
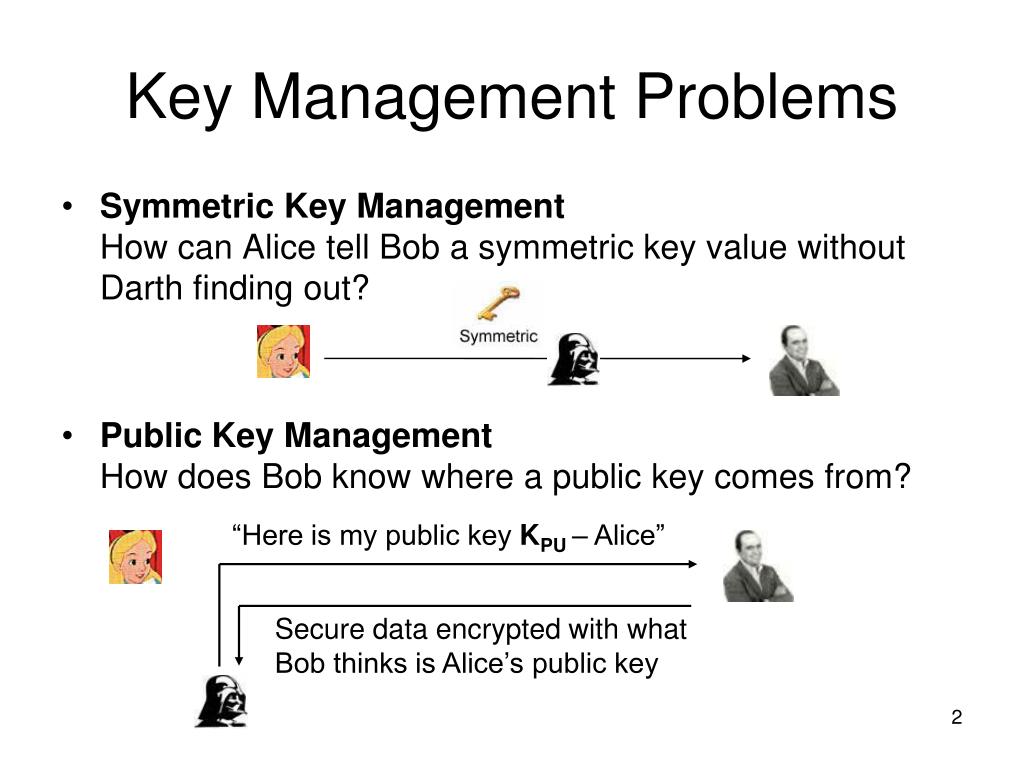
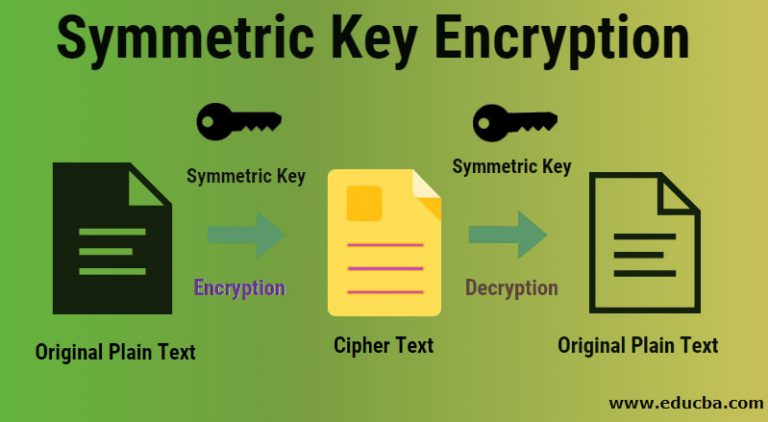
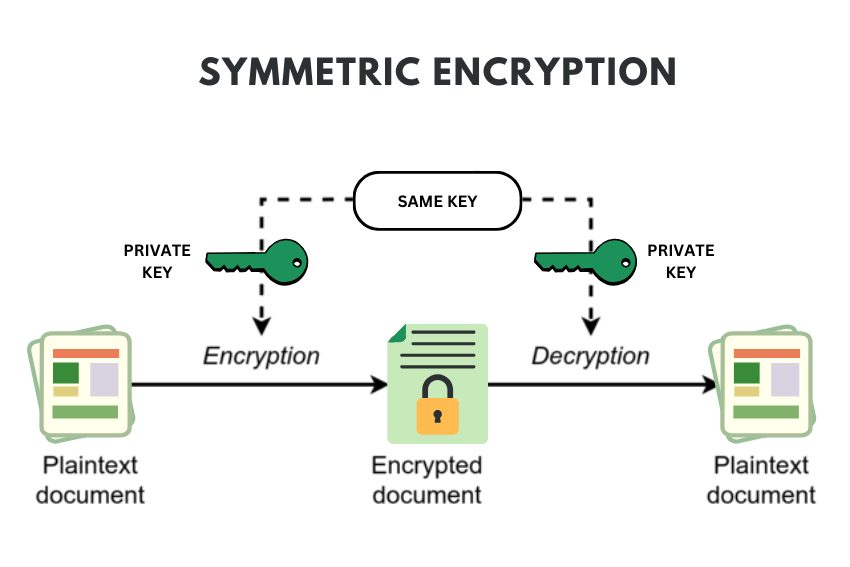
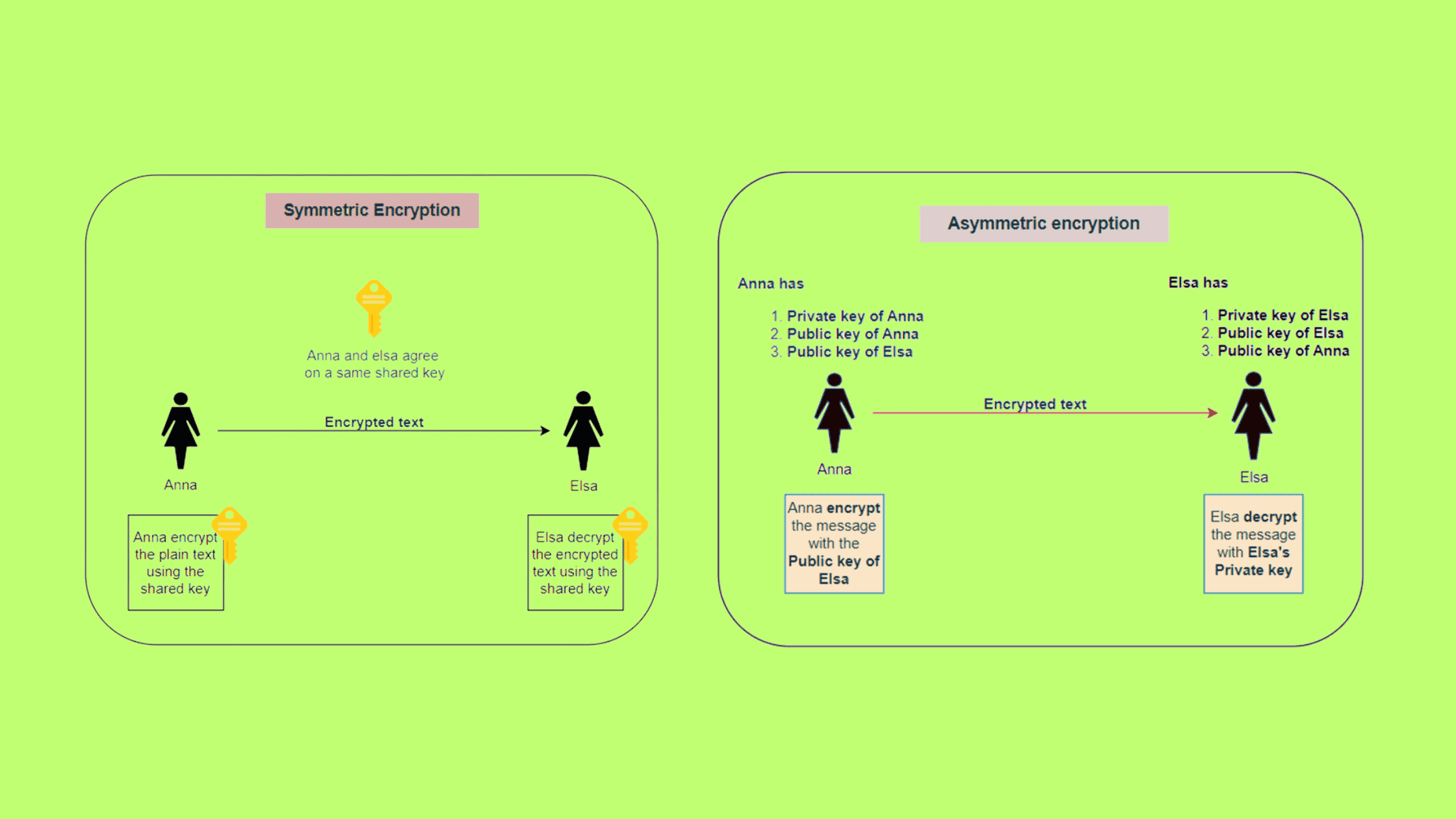
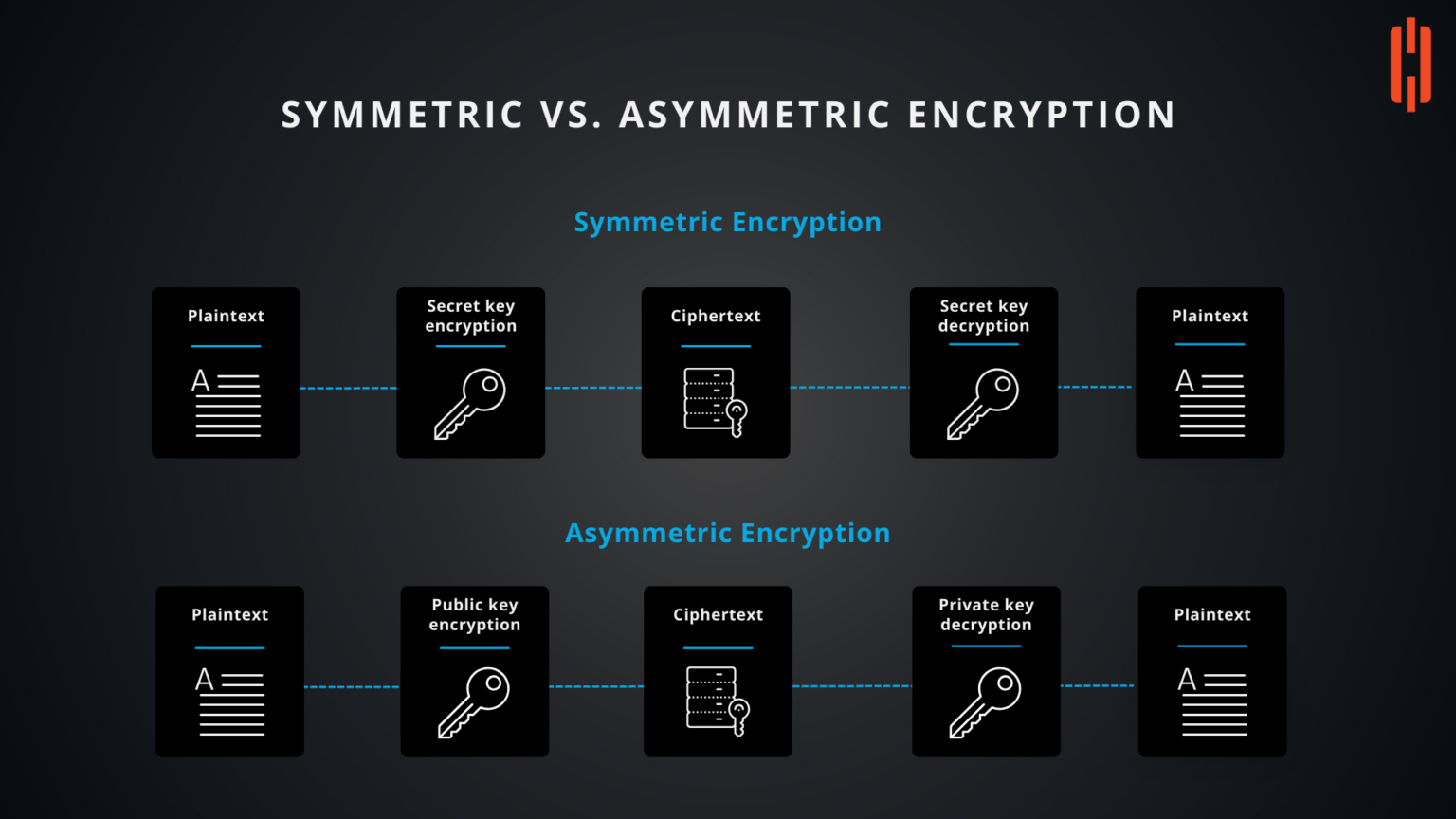
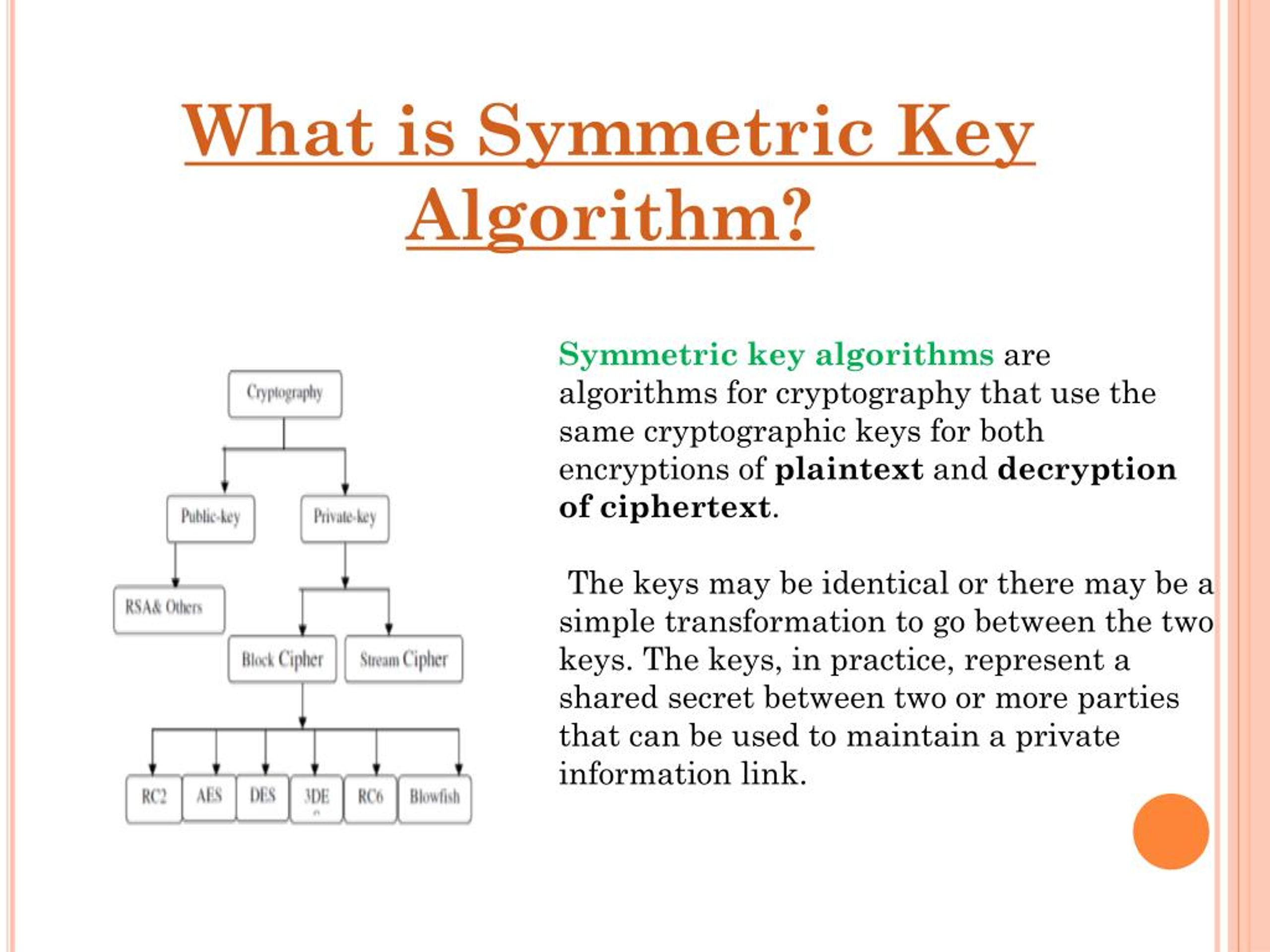
Record life with our documentary key management techniques using symmetric and asymmetric algorithm gallery featuring hundreds of real-world images. authentically documenting computer, digital, and electronic. designed to preserve authentic moments and stories. Each key management techniques using symmetric and asymmetric algorithm image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All key management techniques using symmetric and asymmetric algorithm images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect key management techniques using symmetric and asymmetric algorithm images to enhance your visual communication needs. Multiple resolution options ensure optimal performance across different platforms and applications. Each image in our key management techniques using symmetric and asymmetric algorithm gallery undergoes rigorous quality assessment before inclusion. Advanced search capabilities make finding the perfect key management techniques using symmetric and asymmetric algorithm image effortless and efficient. The key management techniques using symmetric and asymmetric algorithm collection represents years of careful curation and professional standards. Whether for commercial projects or personal use, our key management techniques using symmetric and asymmetric algorithm collection delivers consistent excellence.












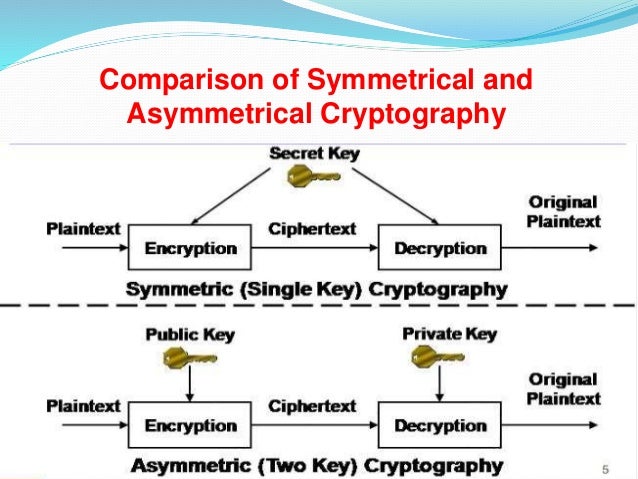
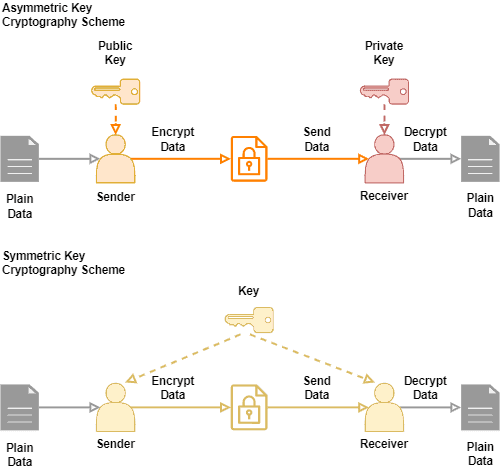



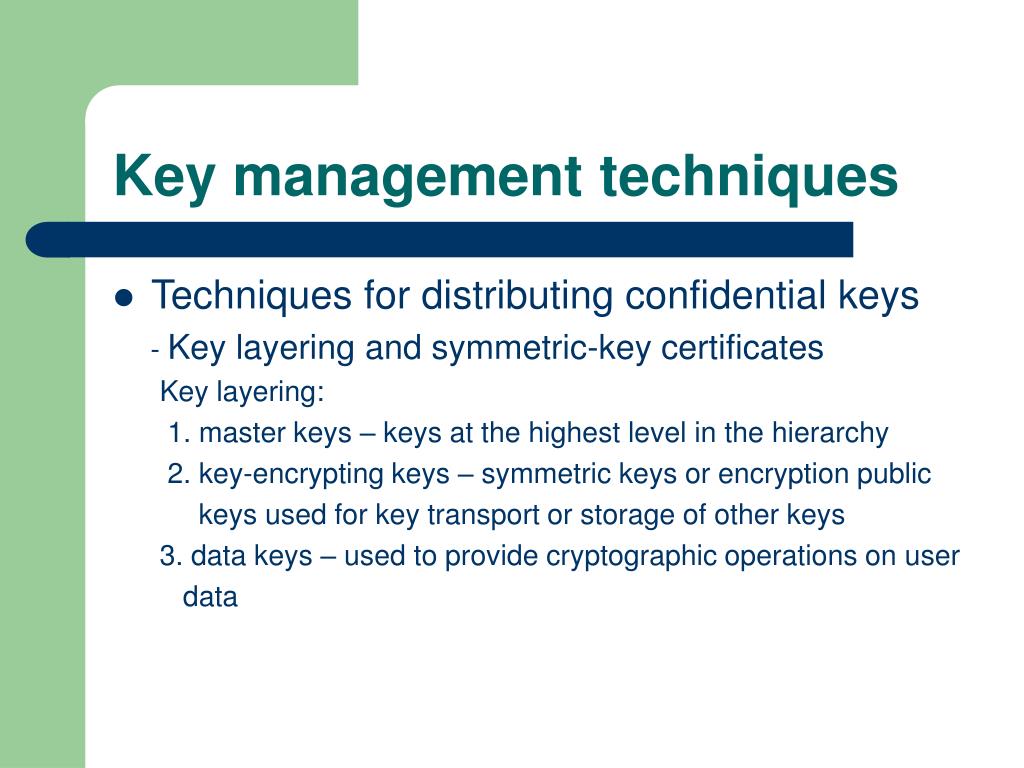

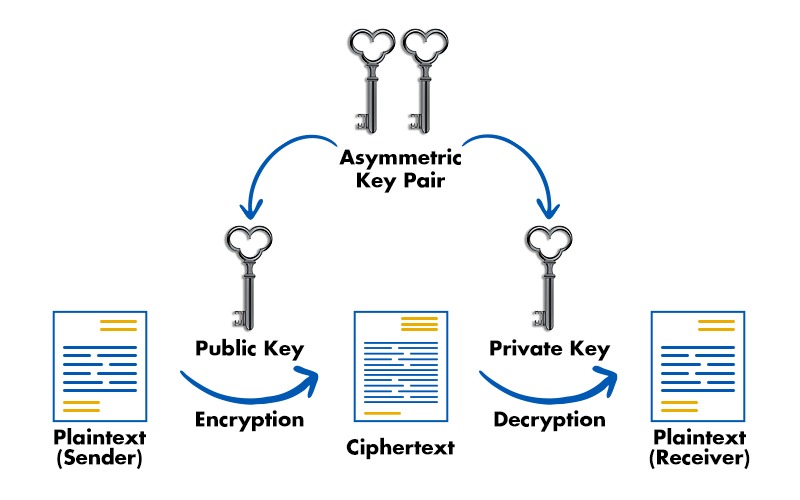




















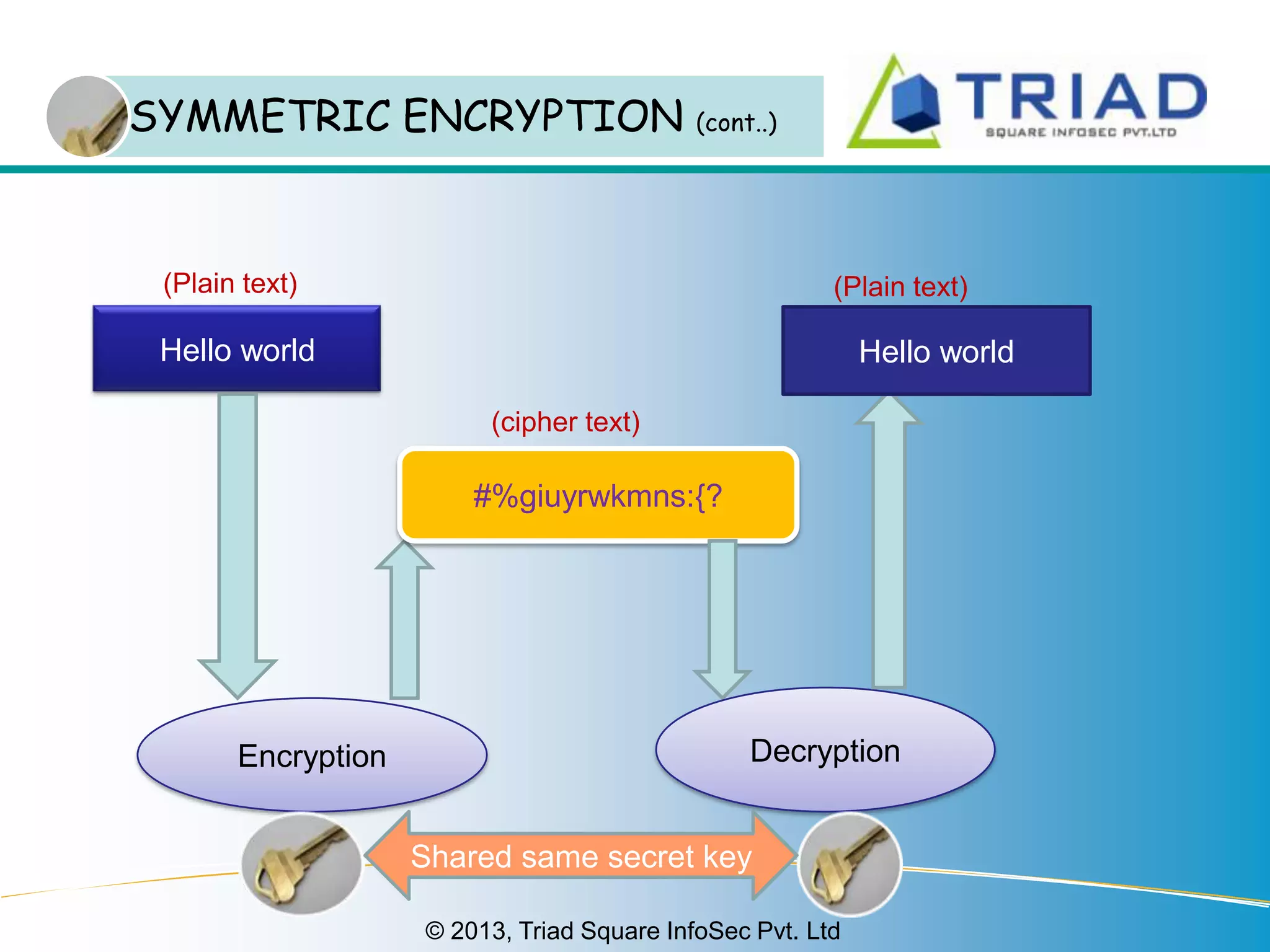








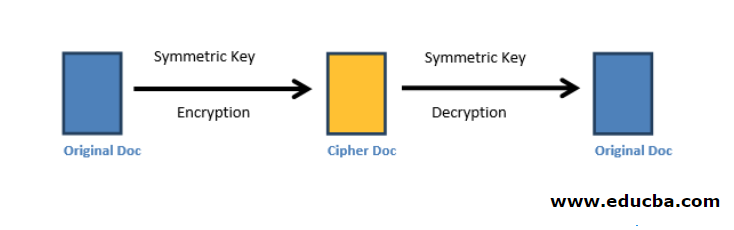



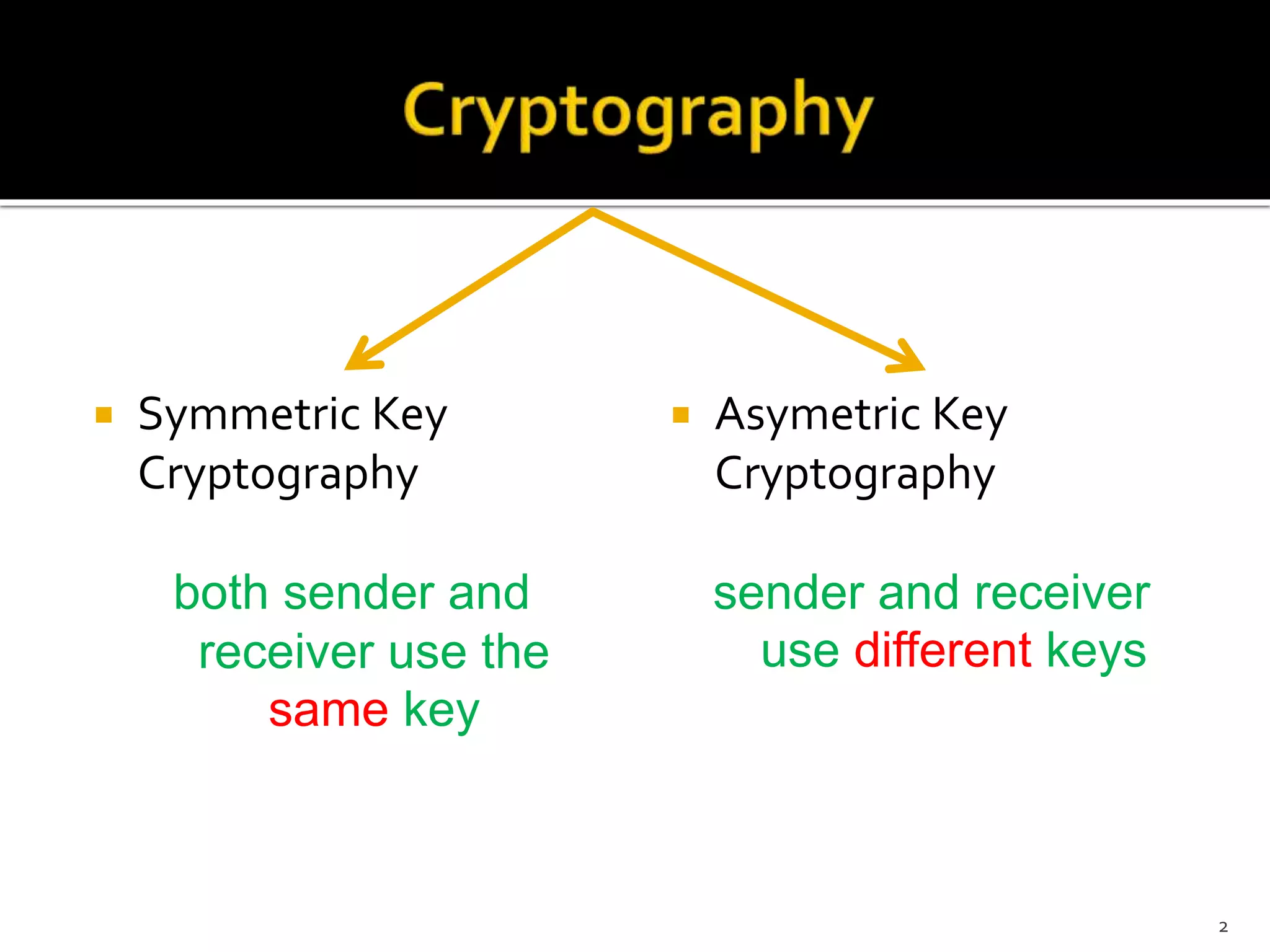
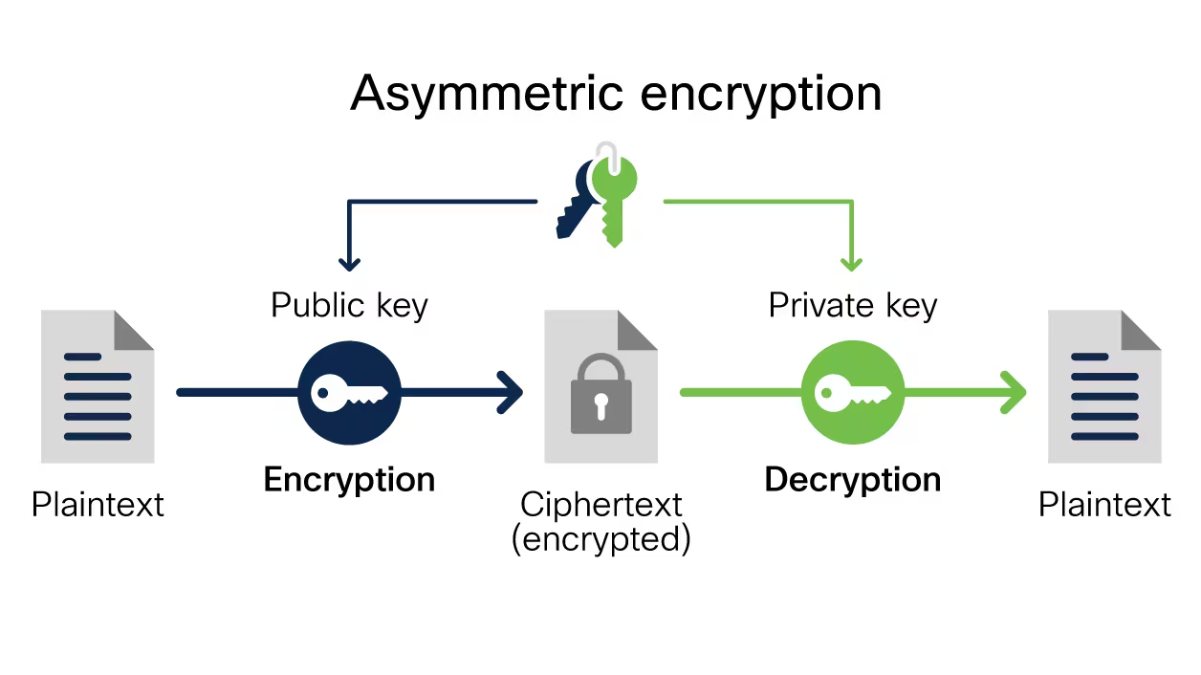
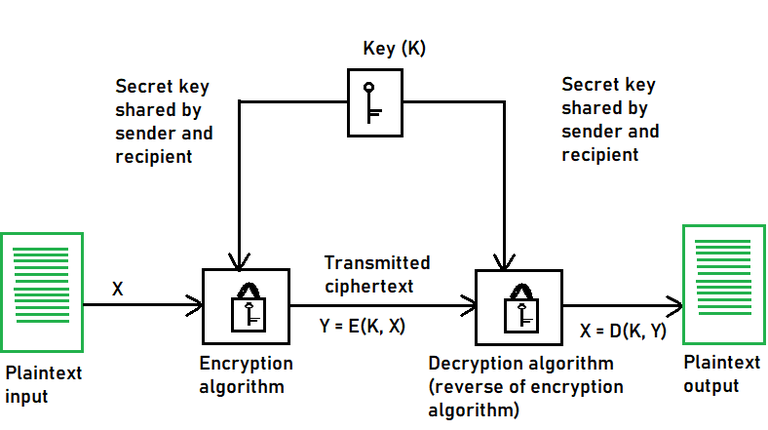






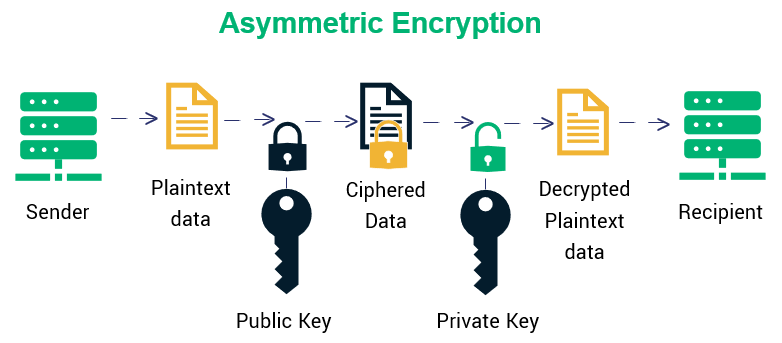
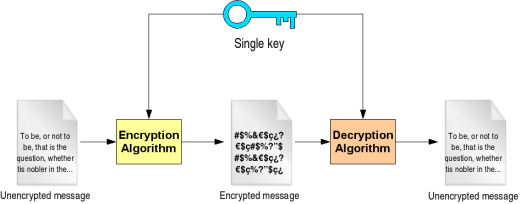







.jpg)