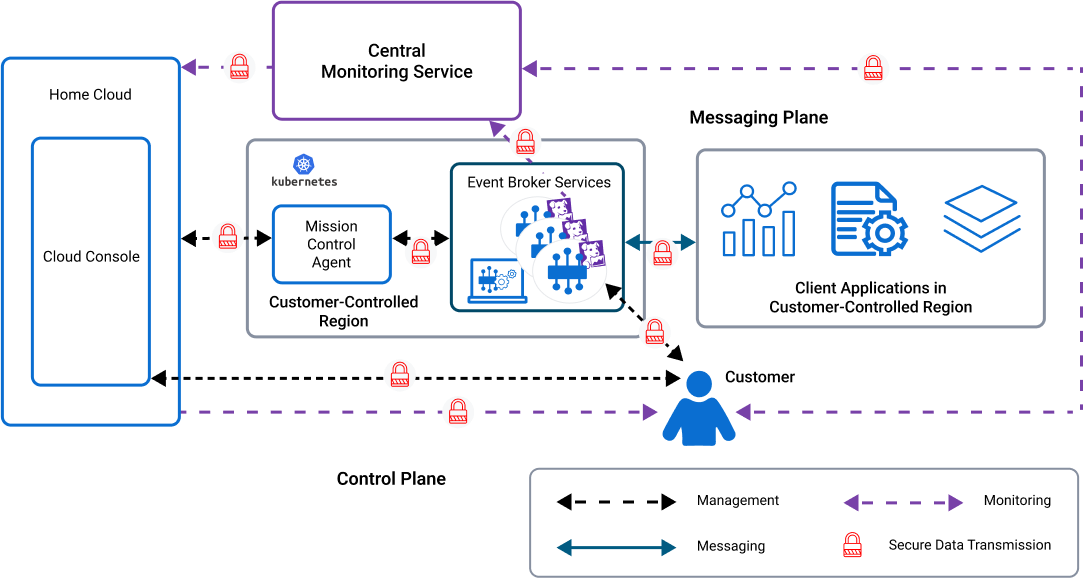
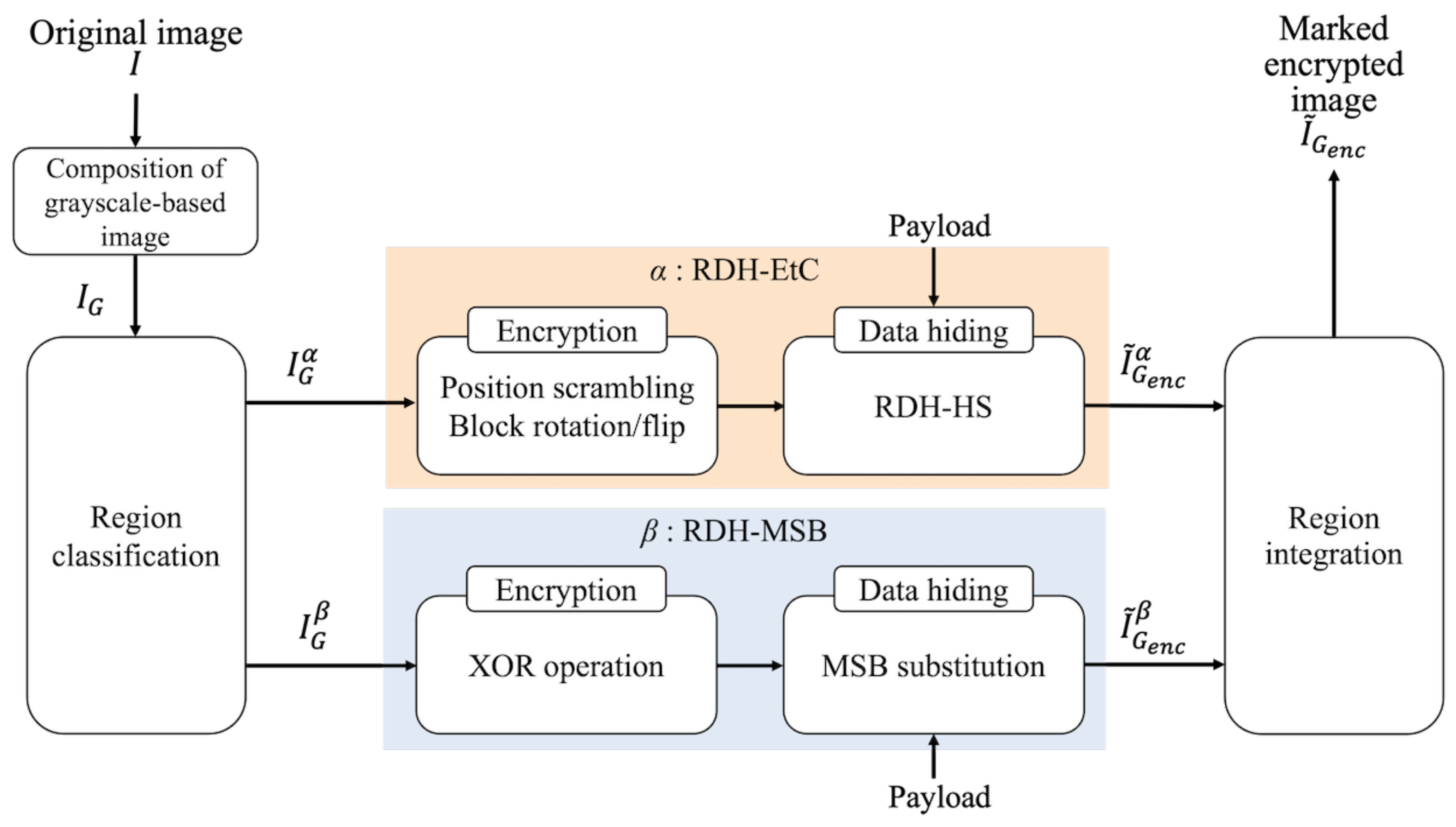
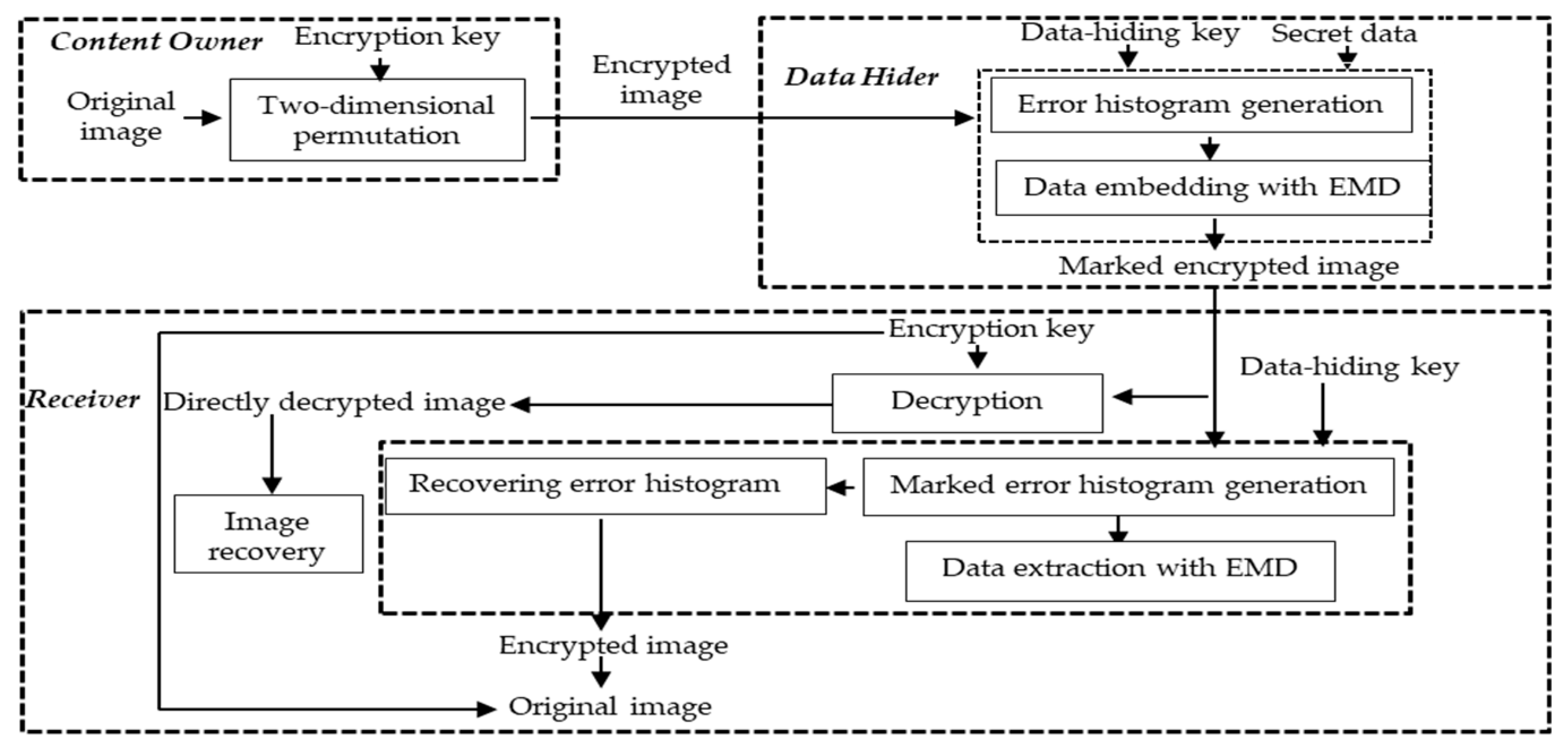
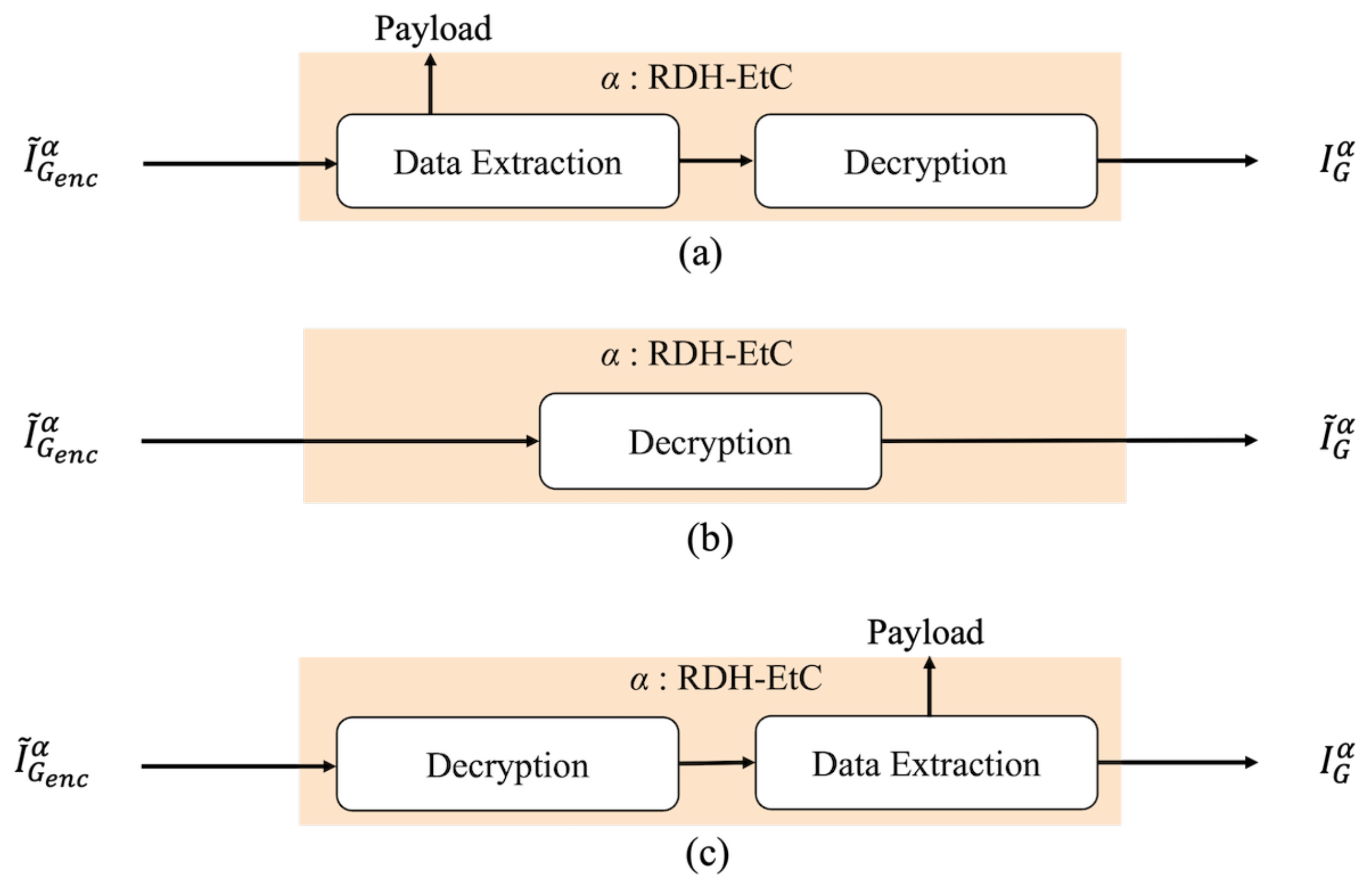
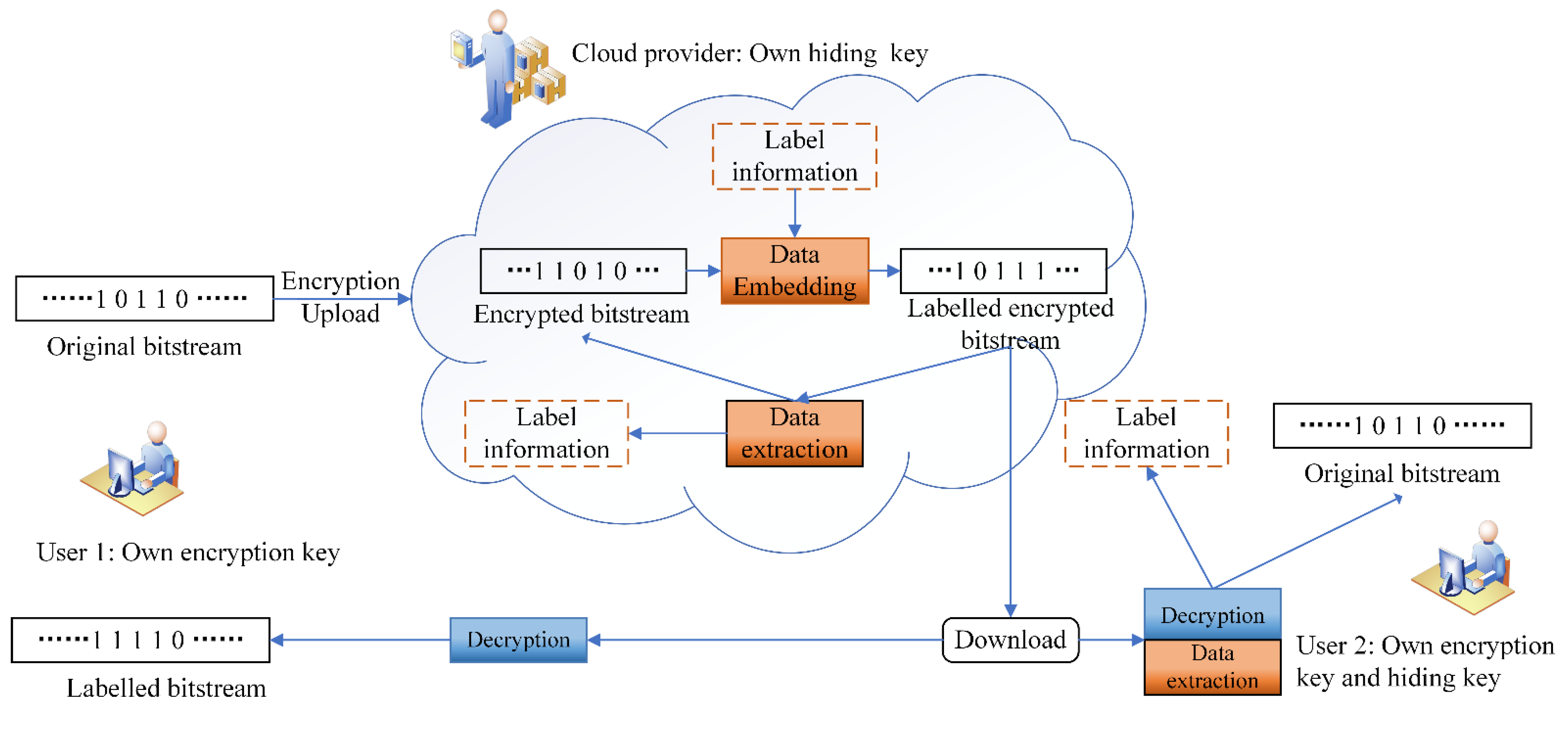
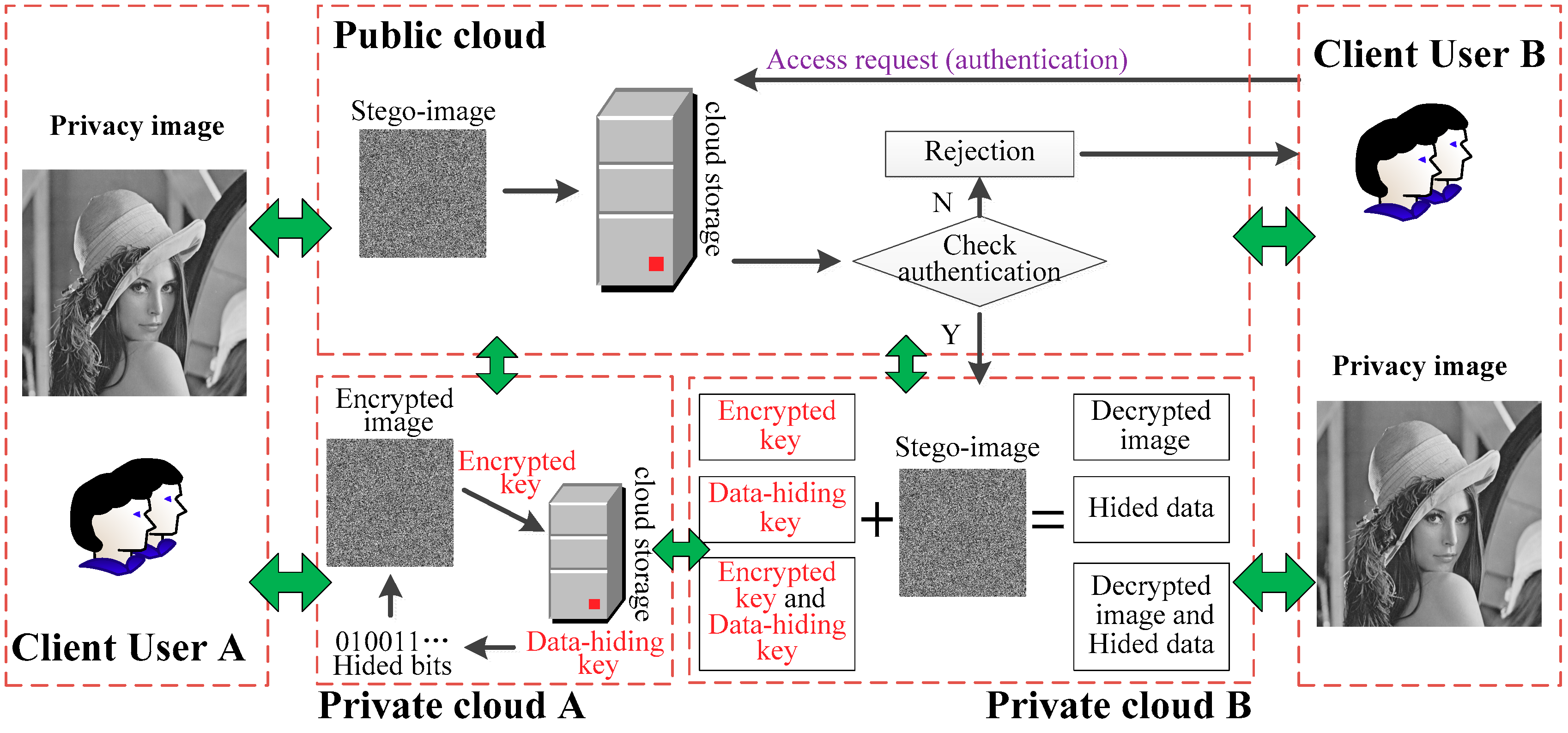
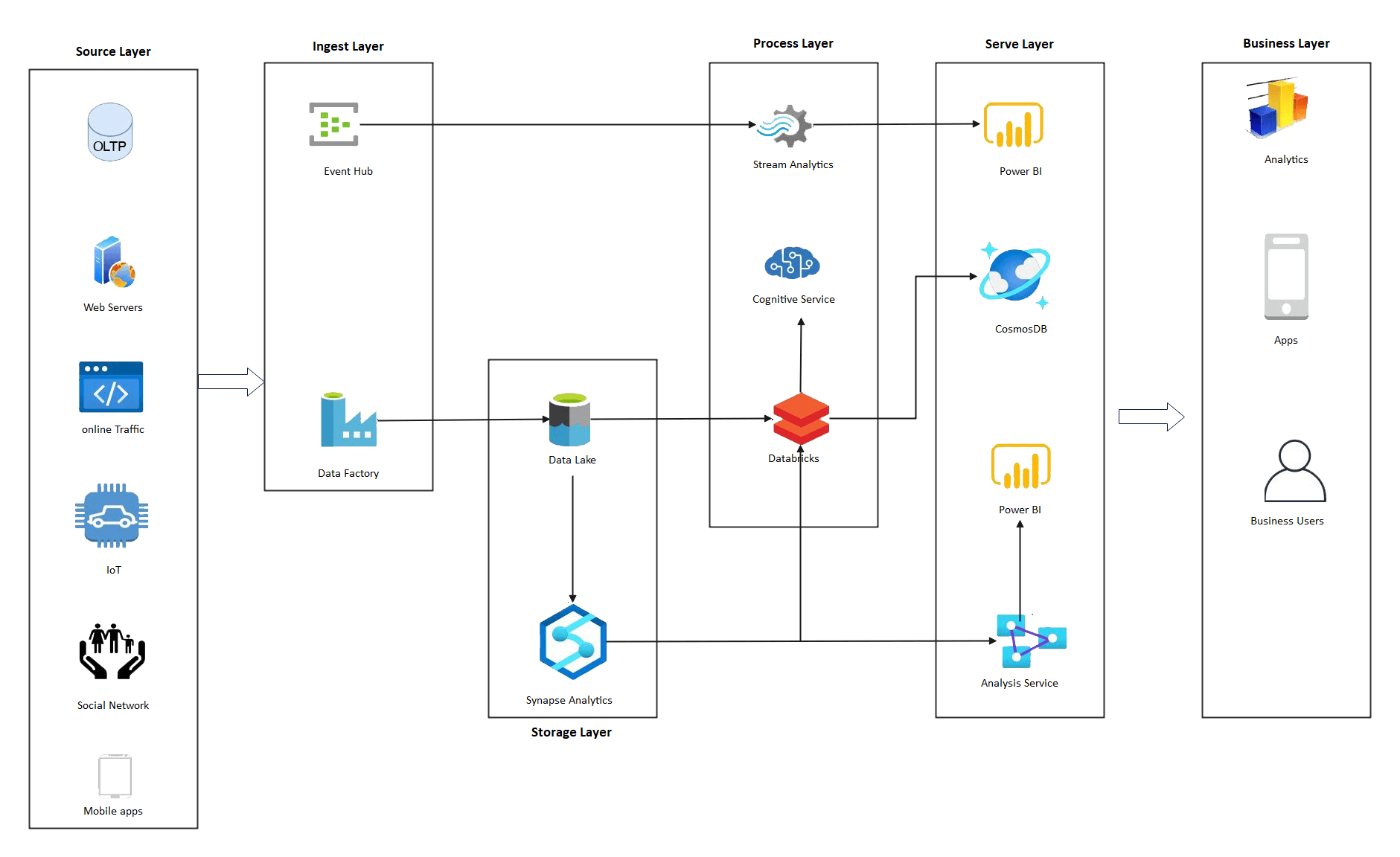
Live your best life through vast arrays of lifestyle-focused architecture diagram of encryption 2) data hiding in encrypted photographs. inspiring lifestyle choices through photography, images, and pictures. designed to inspire positive life choices. Browse our premium architecture diagram of encryption 2) data hiding in encrypted gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All architecture diagram of encryption 2) data hiding in encrypted images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our architecture diagram of encryption 2) data hiding in encrypted collection for various creative and professional projects. Each image in our architecture diagram of encryption 2) data hiding in encrypted gallery undergoes rigorous quality assessment before inclusion. Whether for commercial projects or personal use, our architecture diagram of encryption 2) data hiding in encrypted collection delivers consistent excellence. Multiple resolution options ensure optimal performance across different platforms and applications. The architecture diagram of encryption 2) data hiding in encrypted archive serves professionals, educators, and creatives across diverse industries. Diverse style options within the architecture diagram of encryption 2) data hiding in encrypted collection suit various aesthetic preferences.






![A blockchain-based traceable and secure data-sharing scheme [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2023/cs-1337/1/fig-1-full.png)














![[Full Overview] Everything About Conceptual Architecture Diagram](https://cms.boardmix.com/images/articles/what-is-a-conceptual-architecture-diagram.png)

![Reversible data hiding in encryption domain [69]. | Download Scientific ...](https://www.researchgate.net/profile/Upendra-Raju-Konduru/publication/323470424/figure/fig3/AS:606853826355200@1521696635006/figure-fig3_Q640.jpg)











![[2024 Full Overview] What Are Architecture Diagrams?](https://cms.boardmix.com/images/articles/what-is-an-architecture-diagram.png)




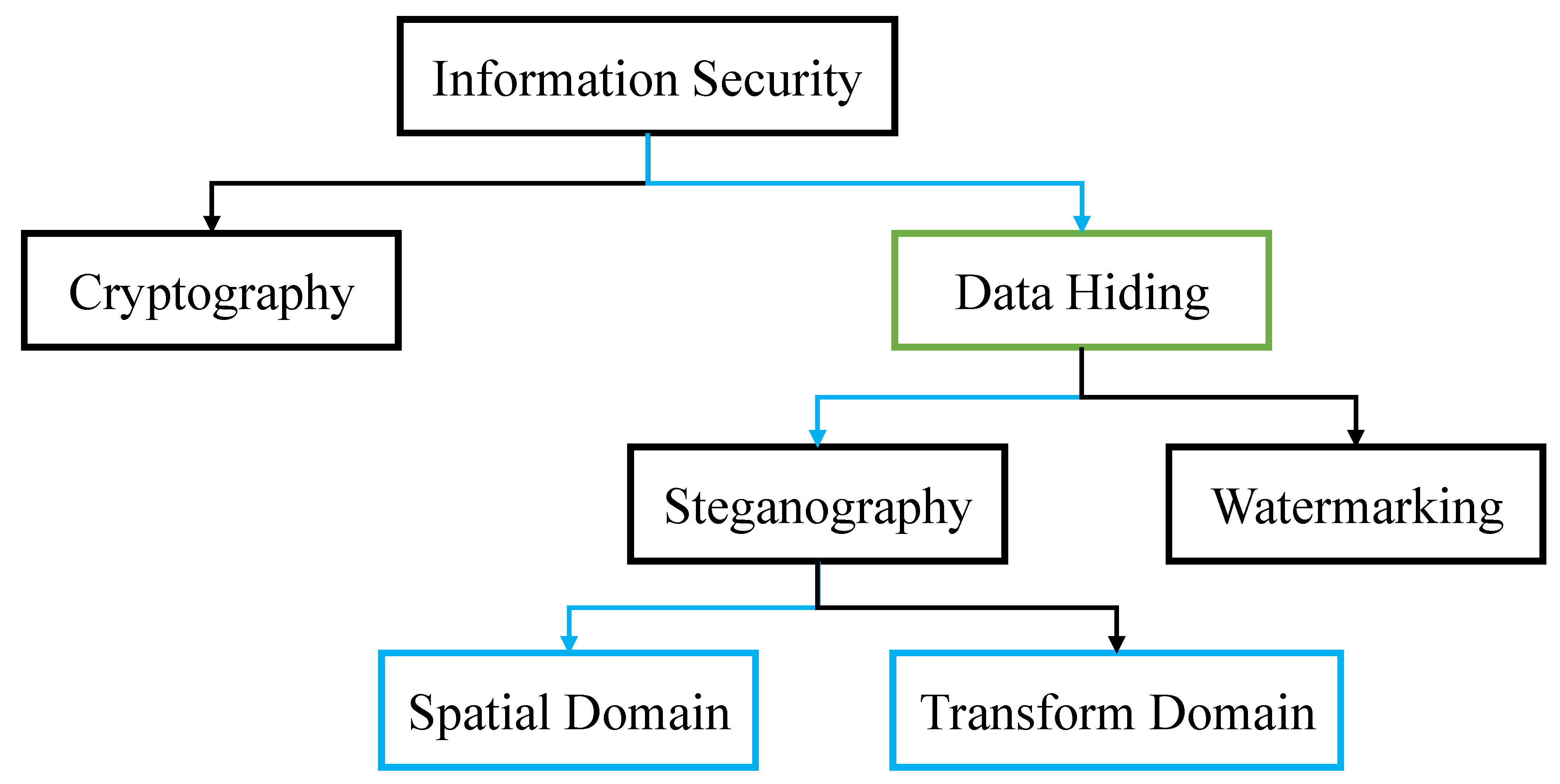
![Different types of data hiding [17] | Download Scientific Diagram](https://www.researchgate.net/publication/348294709/figure/fig2/AS:11431281104767916@1670245755599/Different-types-of-data-hiding-17.png)










![Architecture of the encryption algorithm presented in [18] | Download ...](https://www.researchgate.net/publication/328744578/figure/fig12/AS:941736721399848@1601538939785/Architecture-of-the-encryption-algorithm-presented-in-18.png)




















![Different types of data hiding [17] | Download Scientific Diagram](https://www.researchgate.net/profile/Nandita-Sharma-7/publication/348294709/figure/fig2/AS:11431281104767916@1670245755599/Different-types-of-data-hiding-17_Q320.jpg)

![Architecture of Encryption Block[2] | Download Scientific Diagram](https://www.researchgate.net/profile/Balwinder-Lakha/publication/286725244/figure/fig1/AS:360469543047168@1462954044324/Architecture-of-Encryption-Block2_Q320.jpg)