
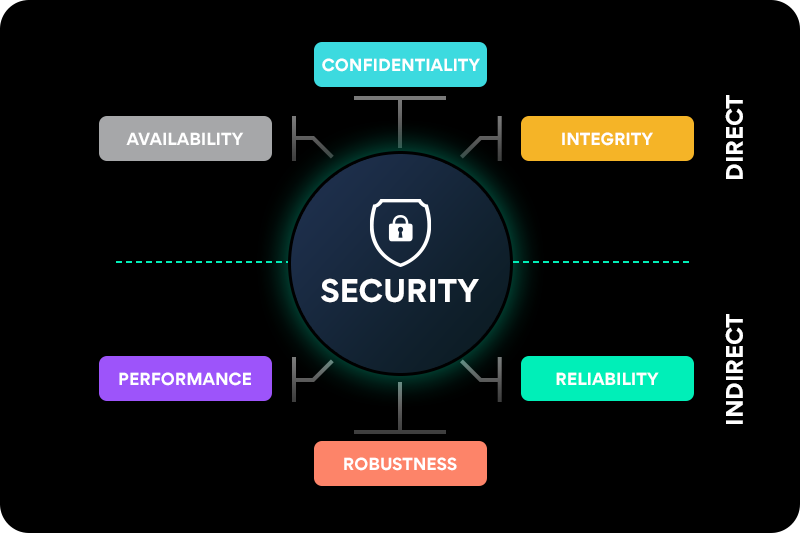
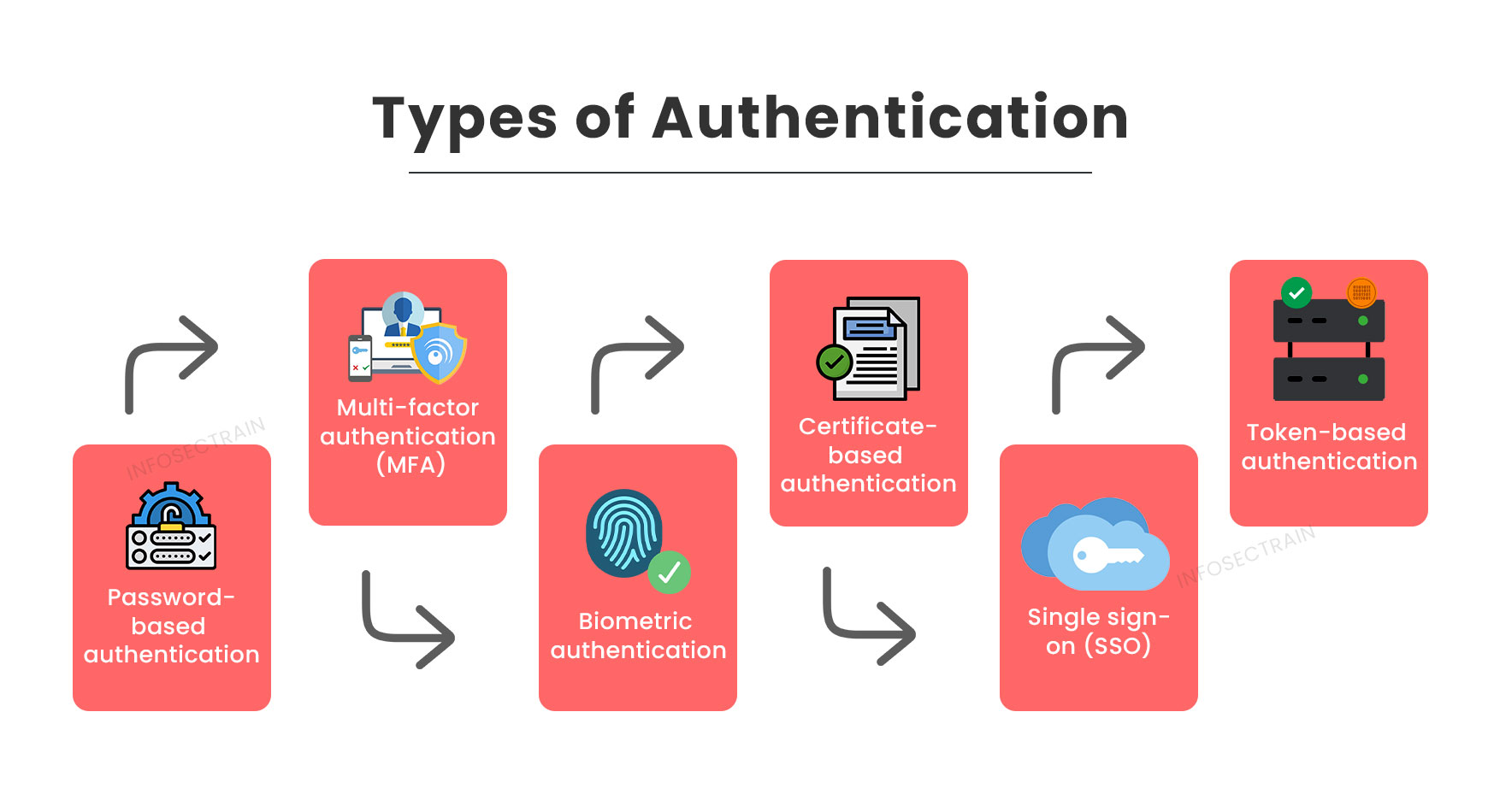
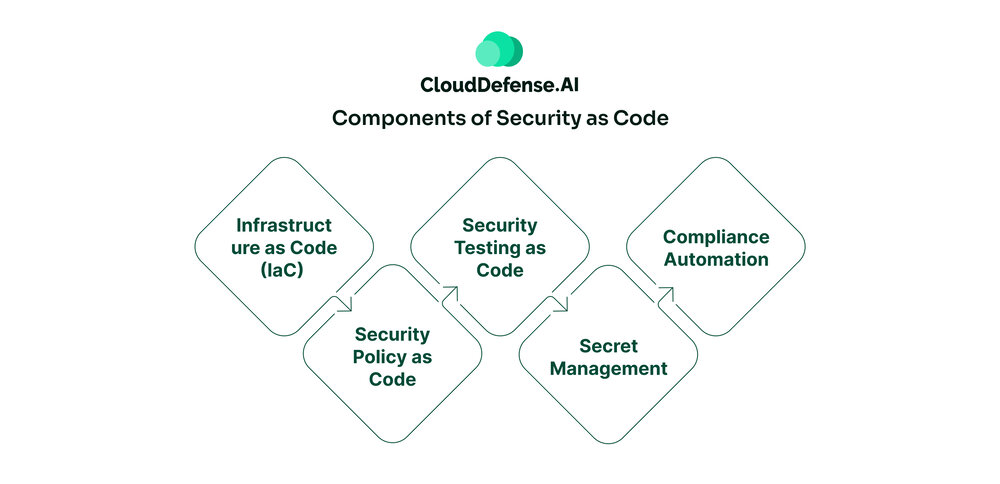
Create spaces with our architectural what is code security? types, tools & techniques gallery of extensive collections of building images. structurally highlighting computer, digital, and electronic. perfect for architectural portfolios and presentations. Discover high-resolution what is code security? types, tools & techniques images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All what is code security? types, tools & techniques images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our what is code security? types, tools & techniques gallery offers diverse visual resources to bring your ideas to life. Multiple resolution options ensure optimal performance across different platforms and applications. Cost-effective licensing makes professional what is code security? types, tools & techniques photography accessible to all budgets. Advanced search capabilities make finding the perfect what is code security? types, tools & techniques image effortless and efficient. Whether for commercial projects or personal use, our what is code security? types, tools & techniques collection delivers consistent excellence. Each image in our what is code security? types, tools & techniques gallery undergoes rigorous quality assessment before inclusion. Professional licensing options accommodate both commercial and educational usage requirements.









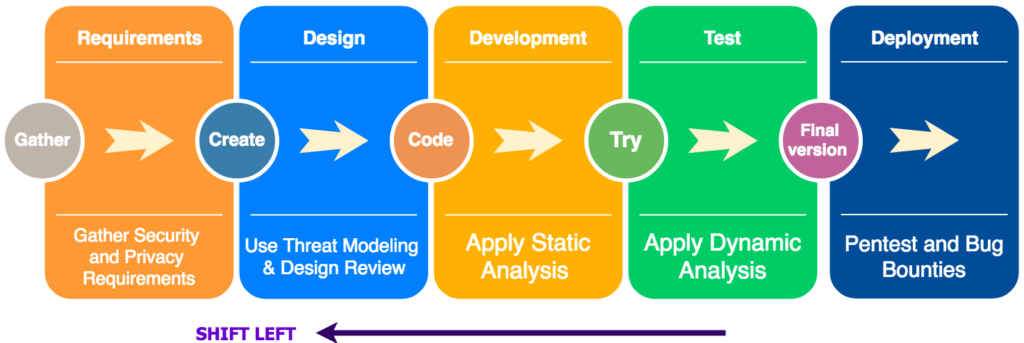







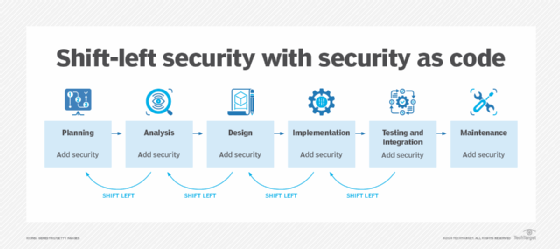

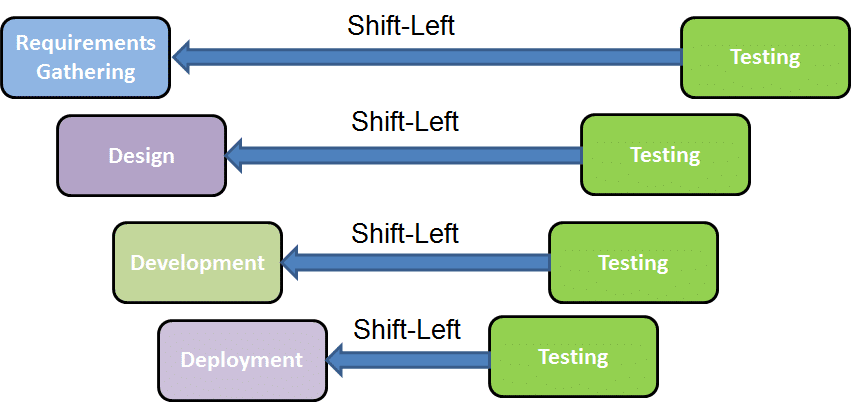
![Key Steps to Assess and Enhance Software Security [Part 5]: Adopt ...](https://miro.medium.com/v2/resize:fit:1000/1*Atg-4E66SqHXfdP1gX6g1w.jpeg)

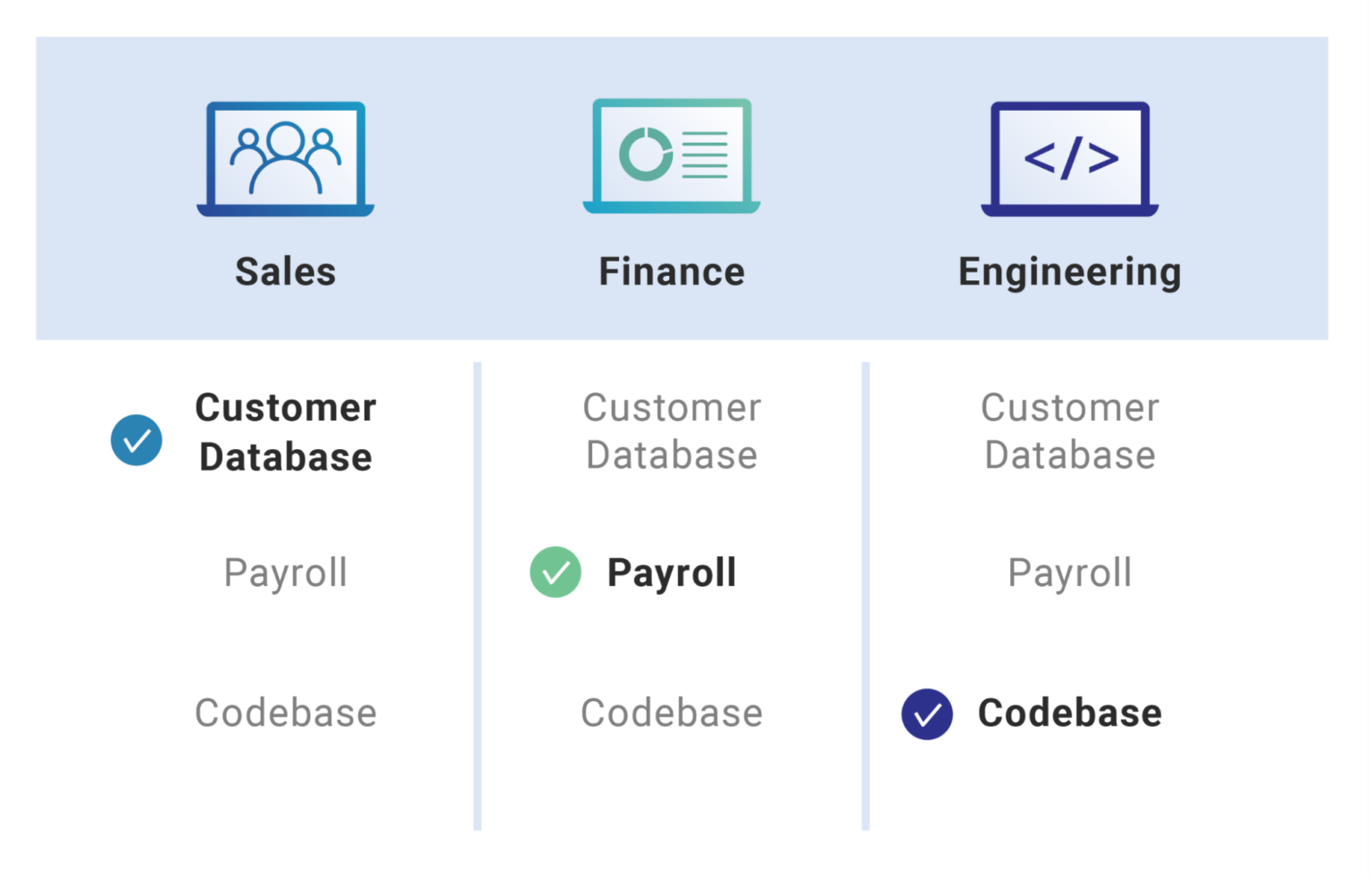









.jpg)






















































![Classification of the Security Solutions (see [2,9,35-140]). | Download ...](https://www.researchgate.net/profile/Nafiseh-Soveizi/publication/371083168/figure/fig5/AS:11431281172732776@1688644286240/Classification-of-the-Security-Solutions-see-2-9-35-140_Q320.jpg)





