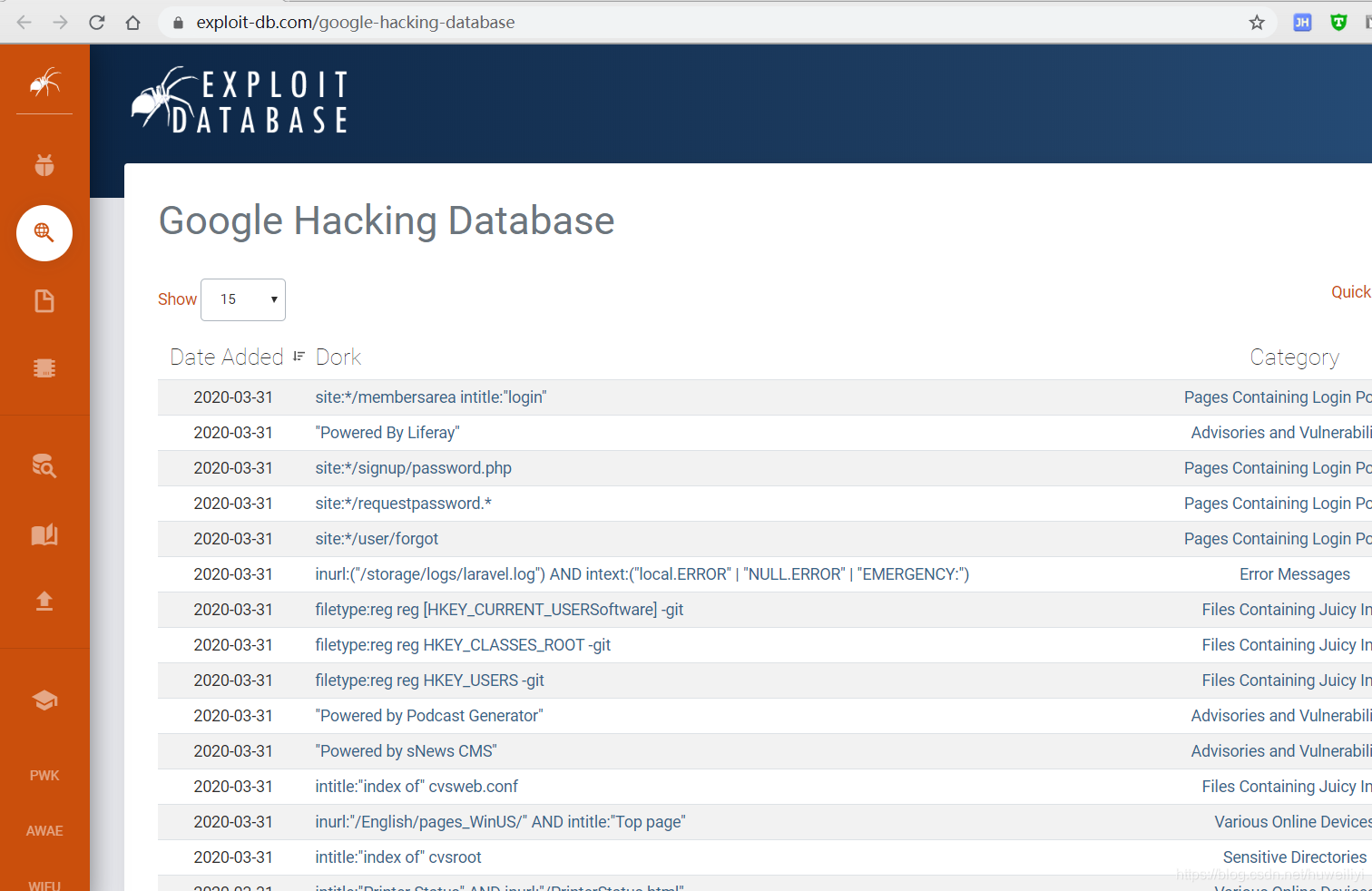
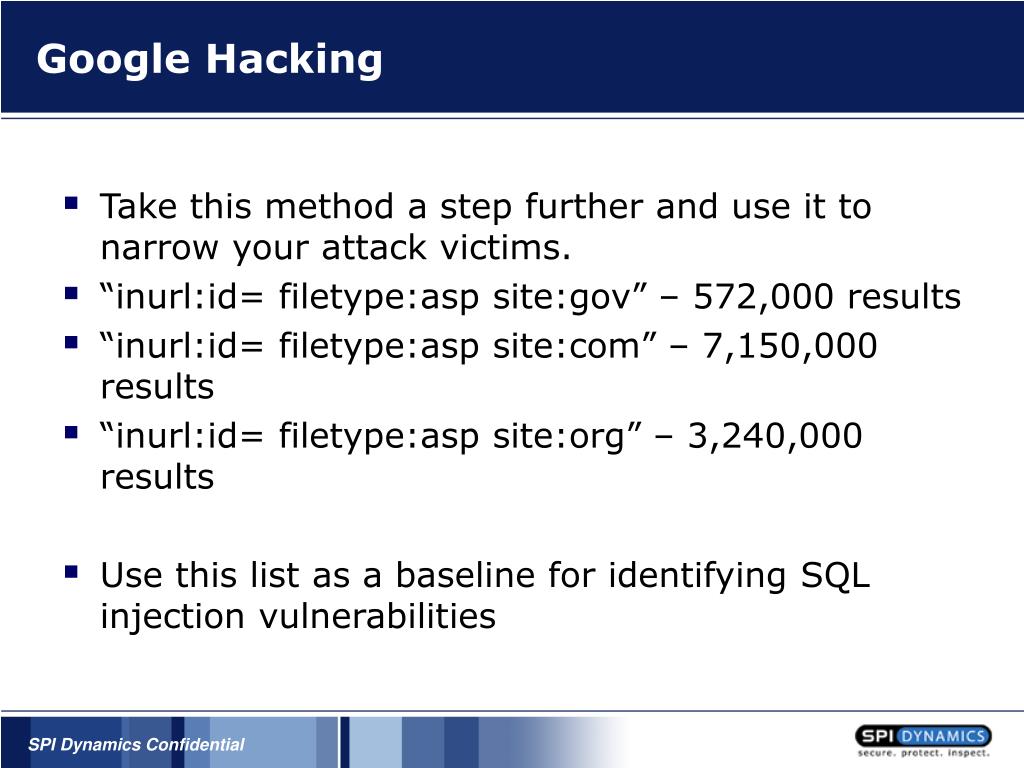
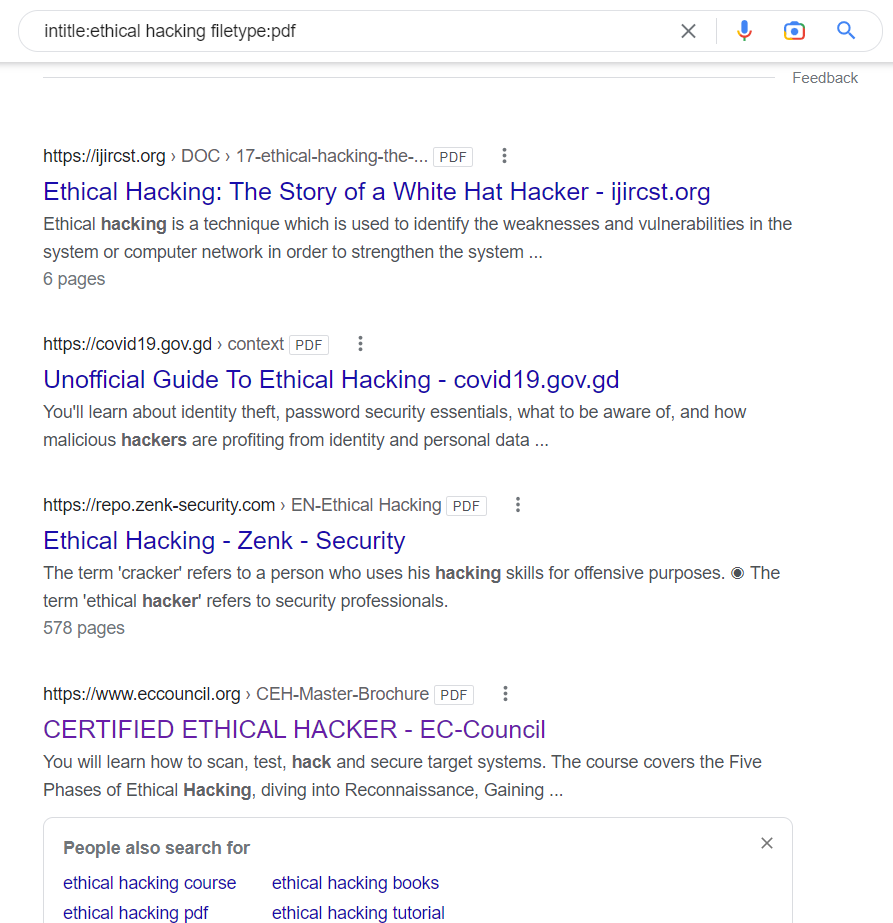
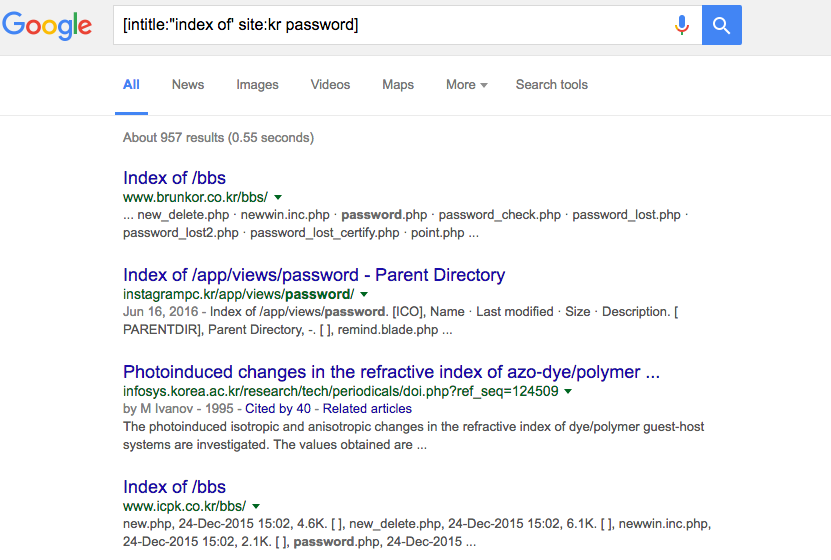
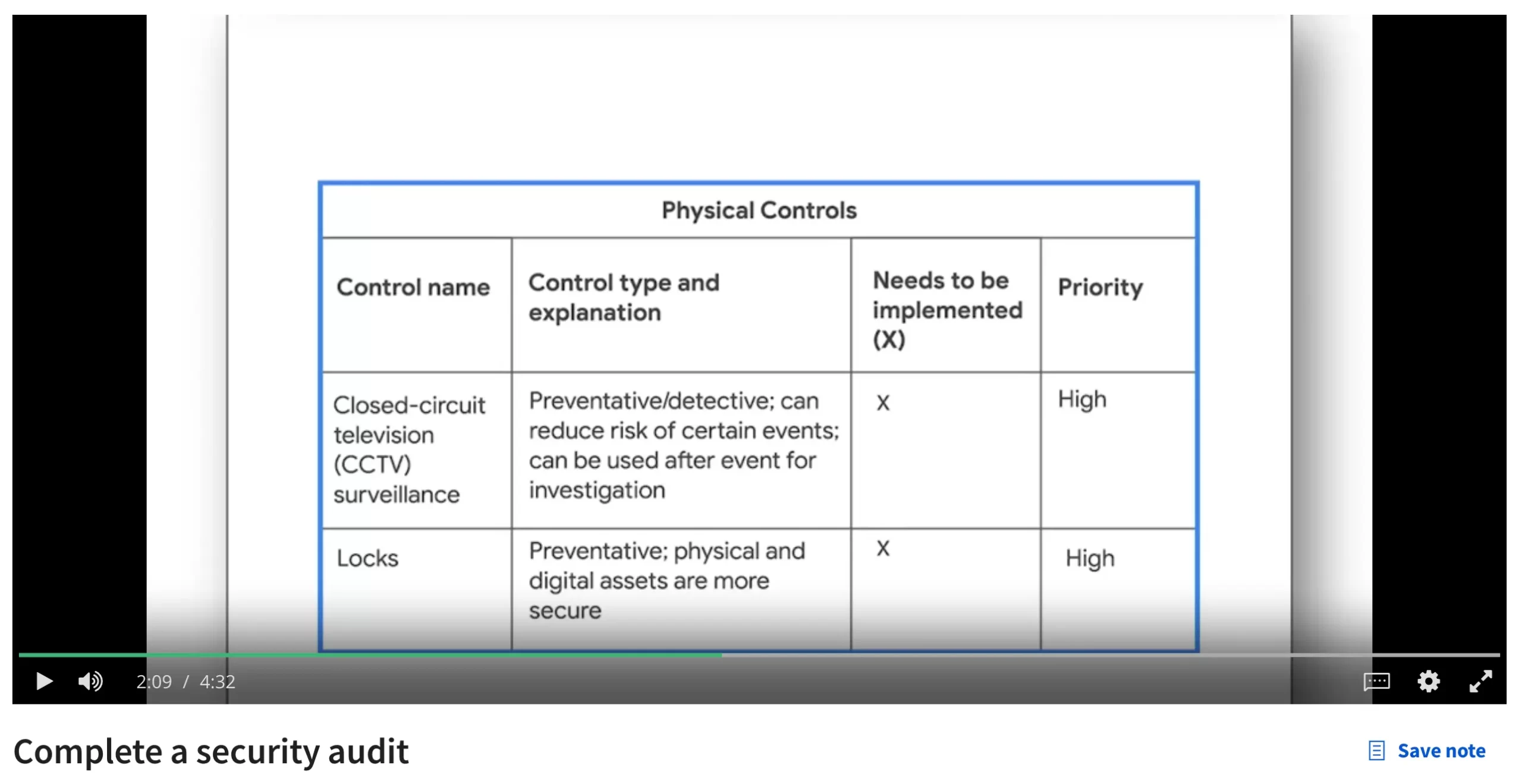
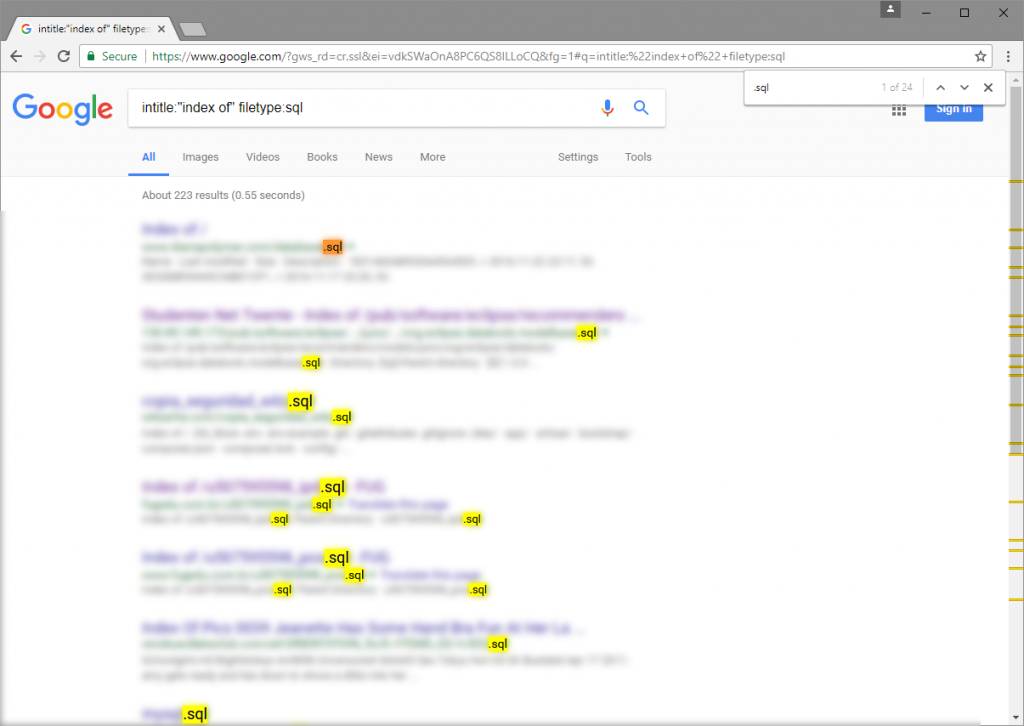
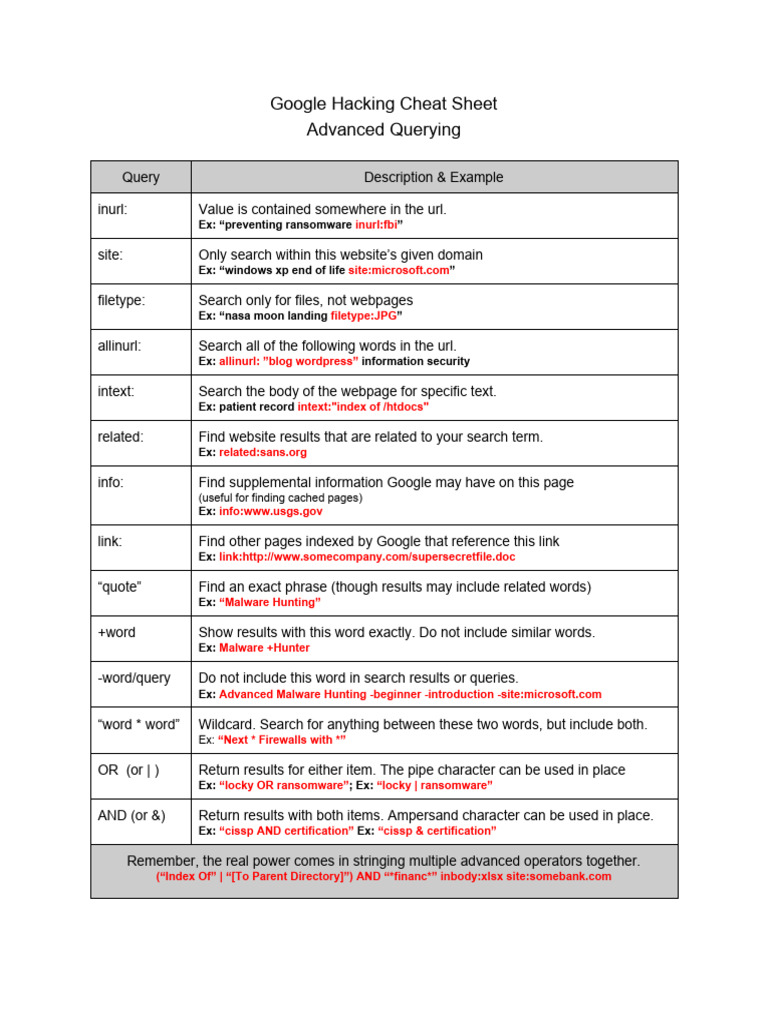
Engage viewers with our entertainment leveraging google for security: google hacking explained - blue goat cyber gallery of numerous spectacular images. spectacularly highlighting color, calm, and peaceful. designed to captivate and engage audiences. Browse our premium leveraging google for security: google hacking explained - blue goat cyber gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All leveraging google for security: google hacking explained - blue goat cyber images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our leveraging google for security: google hacking explained - blue goat cyber gallery offers diverse visual resources to bring your ideas to life. Our leveraging google for security: google hacking explained - blue goat cyber database continuously expands with fresh, relevant content from skilled photographers. Comprehensive tagging systems facilitate quick discovery of relevant leveraging google for security: google hacking explained - blue goat cyber content. Professional licensing options accommodate both commercial and educational usage requirements. Reliable customer support ensures smooth experience throughout the leveraging google for security: google hacking explained - blue goat cyber selection process.