
Experience the excitement of 🔍 side-channel recon: how attackers use timing, headers, and metadata with our extensive gallery of comprehensive galleries of images. highlighting the adventurous spirit of photography, images, and pictures. ideal for travel bloggers and adventure photographers. Discover high-resolution 🔍 side-channel recon: how attackers use timing, headers, and metadata images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All 🔍 side-channel recon: how attackers use timing, headers, and metadata images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our 🔍 side-channel recon: how attackers use timing, headers, and metadata collection for various creative and professional projects. Multiple resolution options ensure optimal performance across different platforms and applications. Cost-effective licensing makes professional 🔍 side-channel recon: how attackers use timing, headers, and metadata photography accessible to all budgets. The 🔍 side-channel recon: how attackers use timing, headers, and metadata archive serves professionals, educators, and creatives across diverse industries. Diverse style options within the 🔍 side-channel recon: how attackers use timing, headers, and metadata collection suit various aesthetic preferences. Comprehensive tagging systems facilitate quick discovery of relevant 🔍 side-channel recon: how attackers use timing, headers, and metadata content.

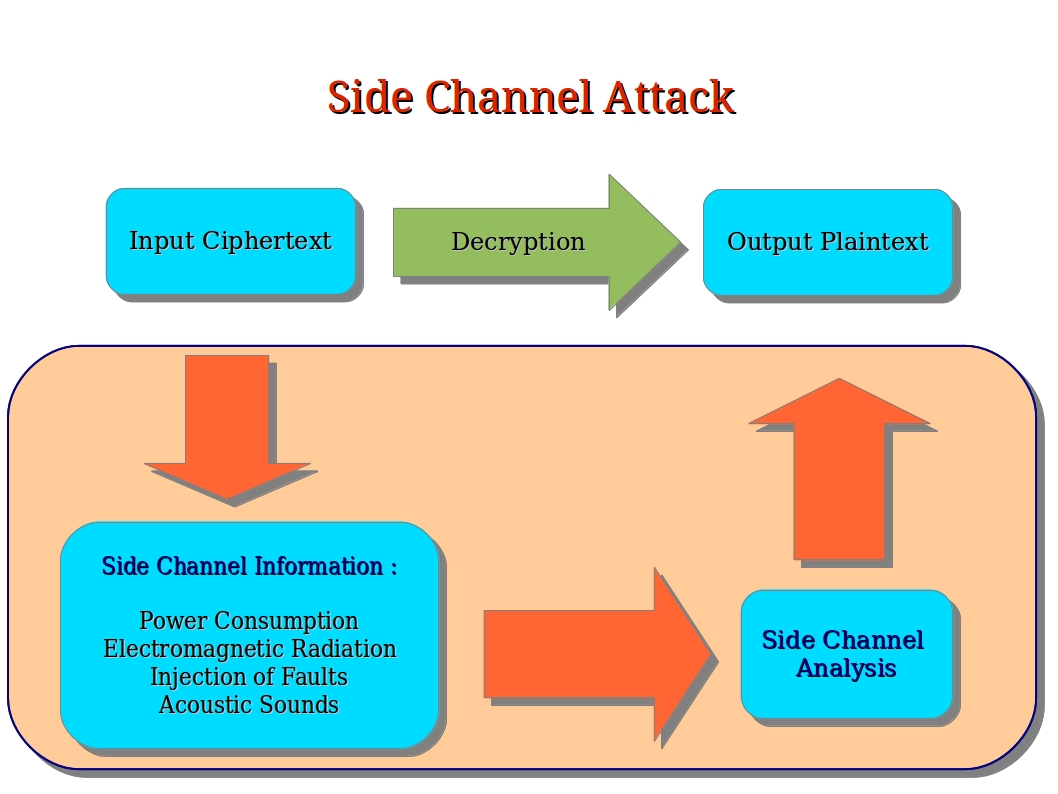
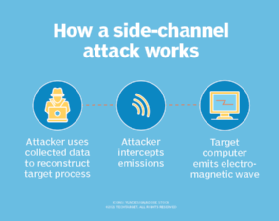
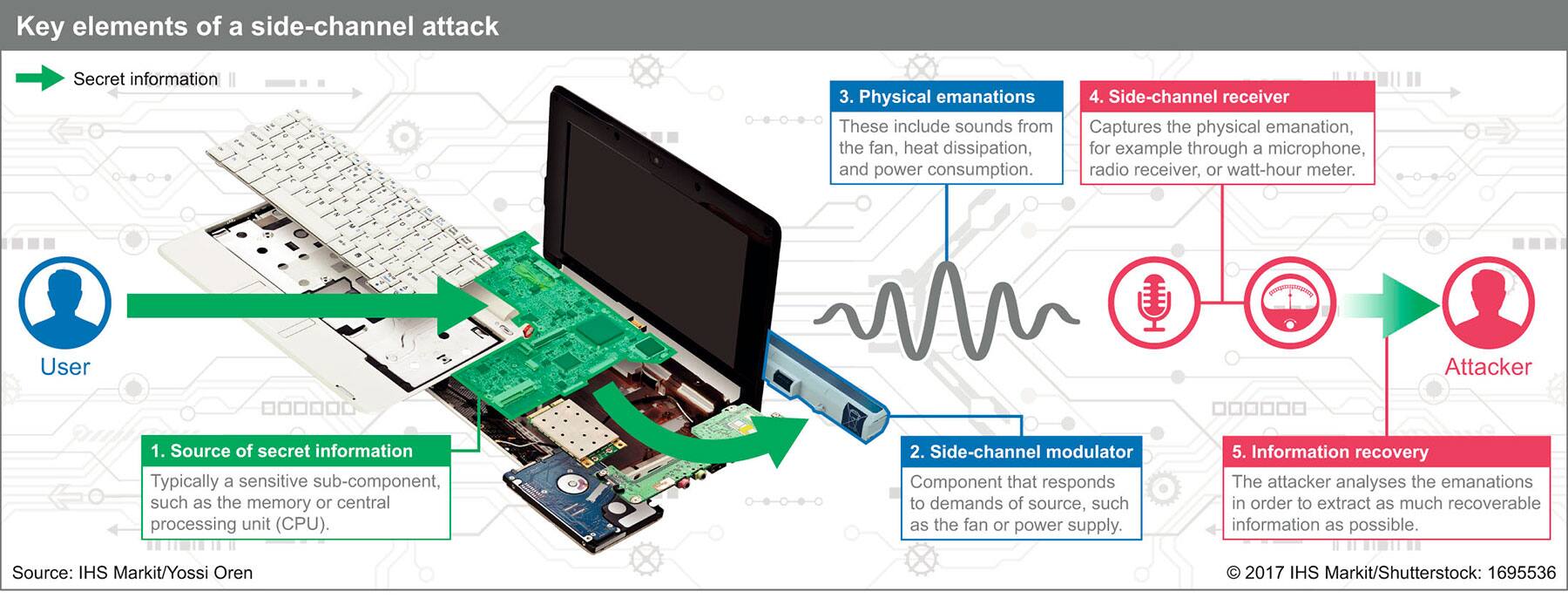
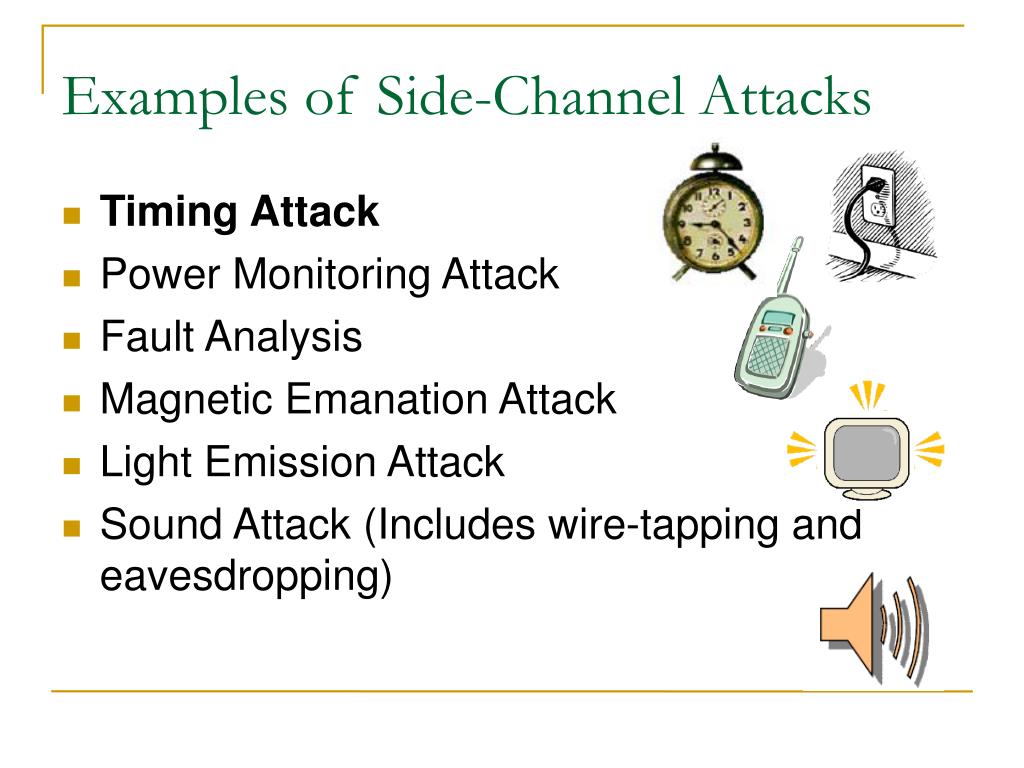

































































































.jpg)


