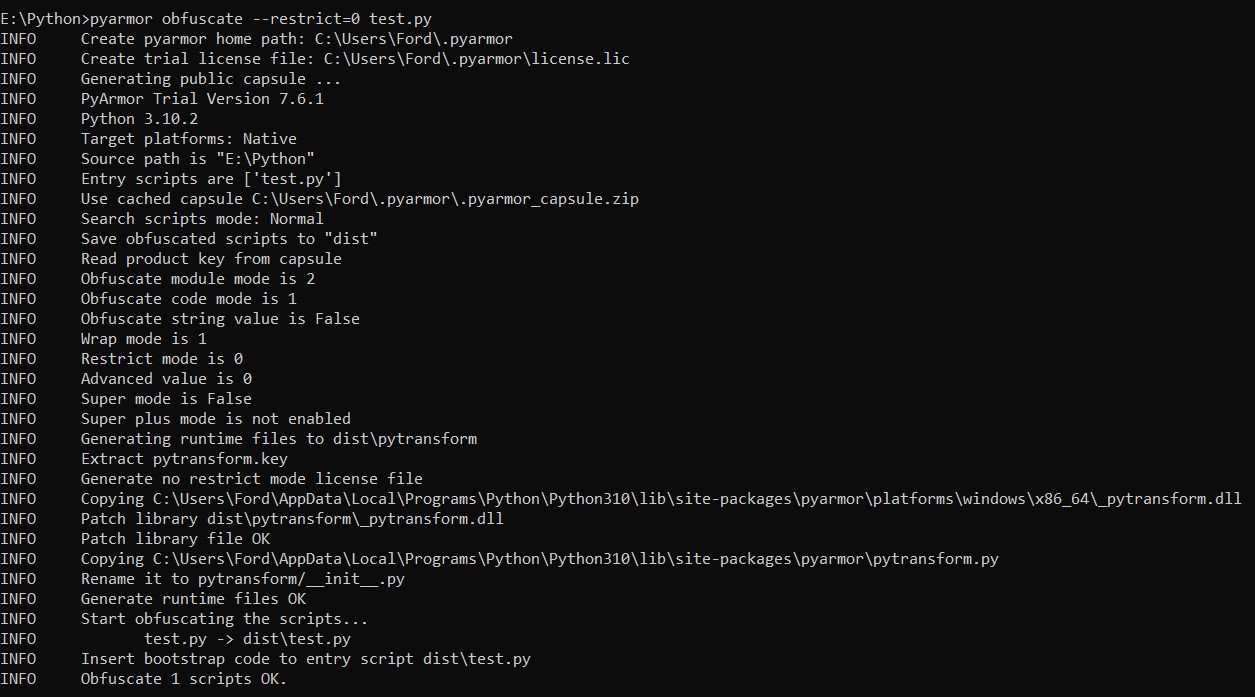
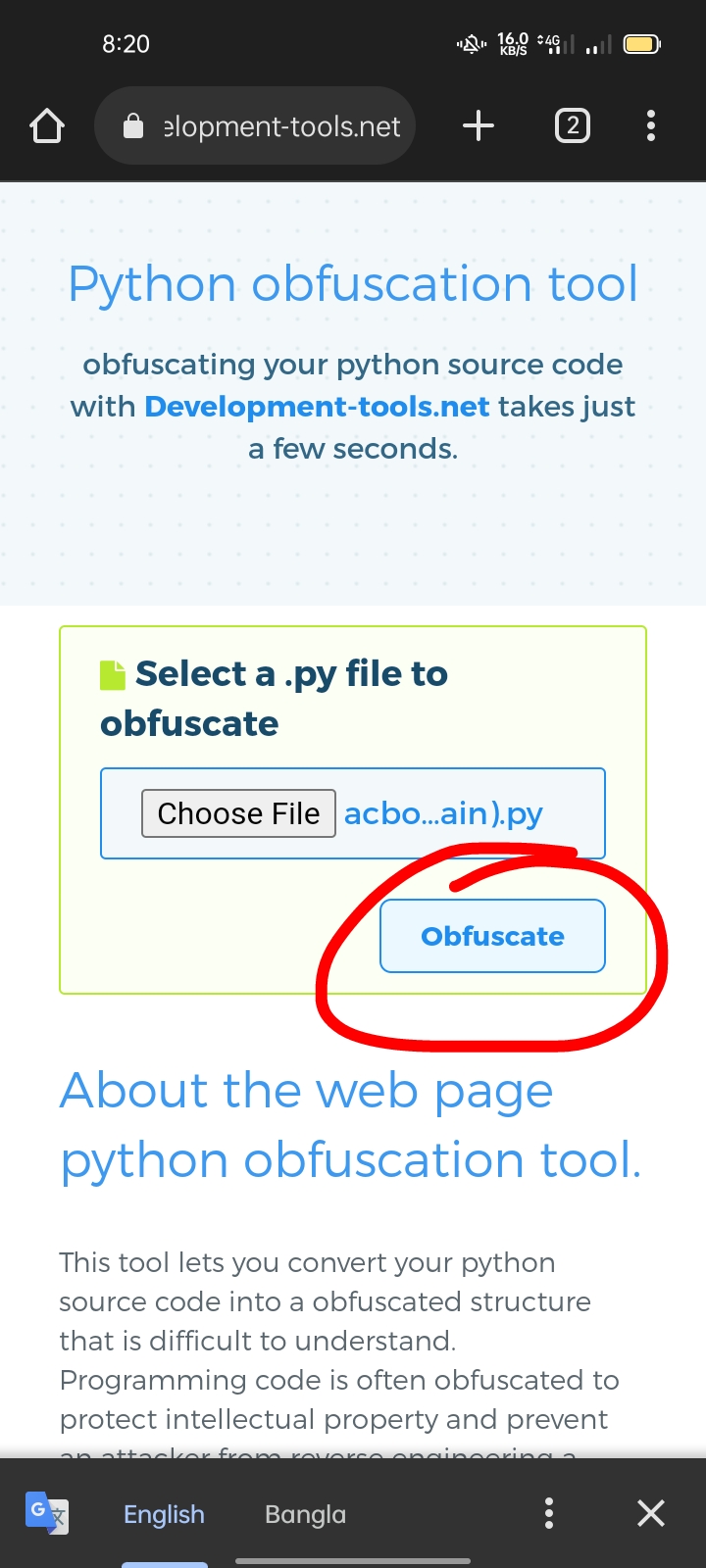
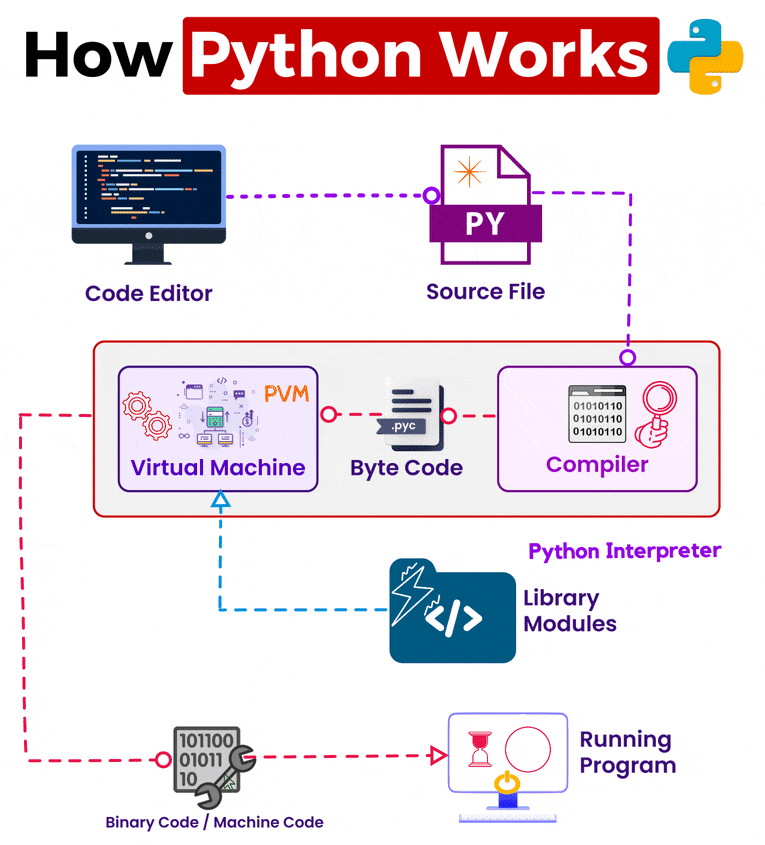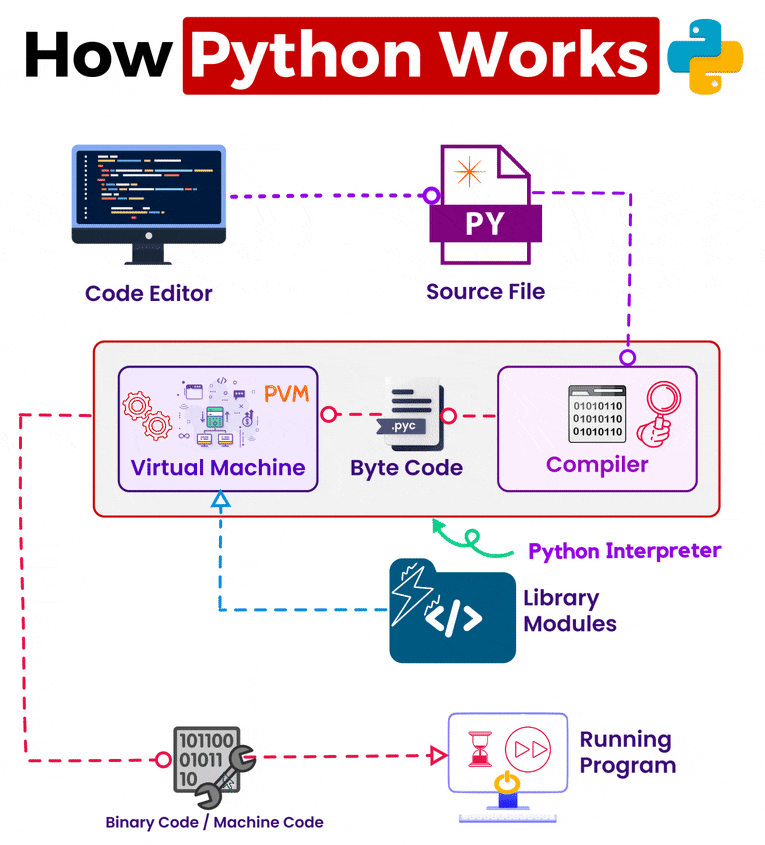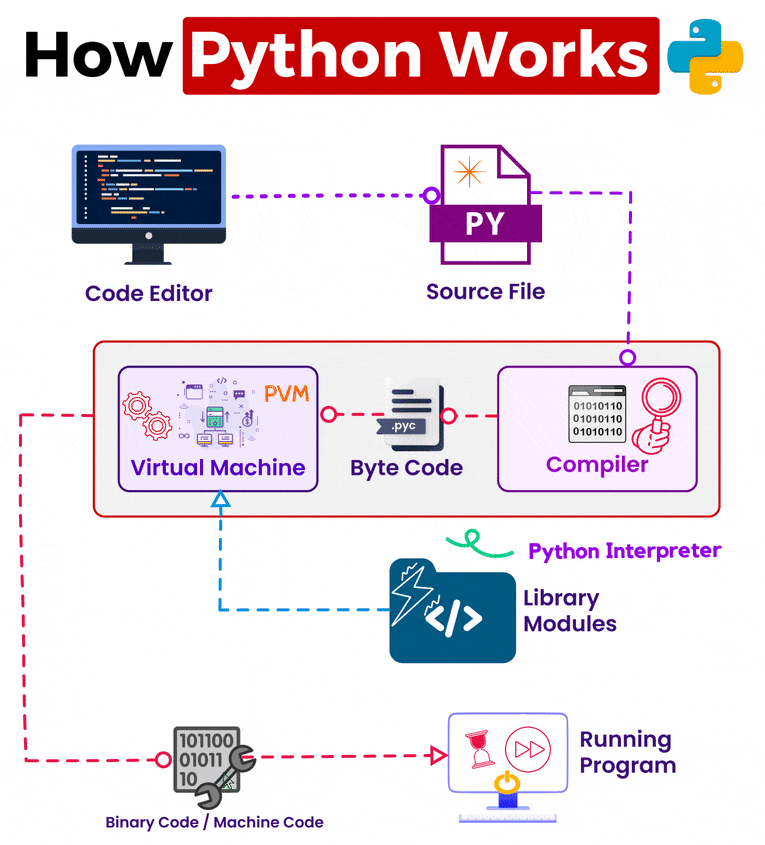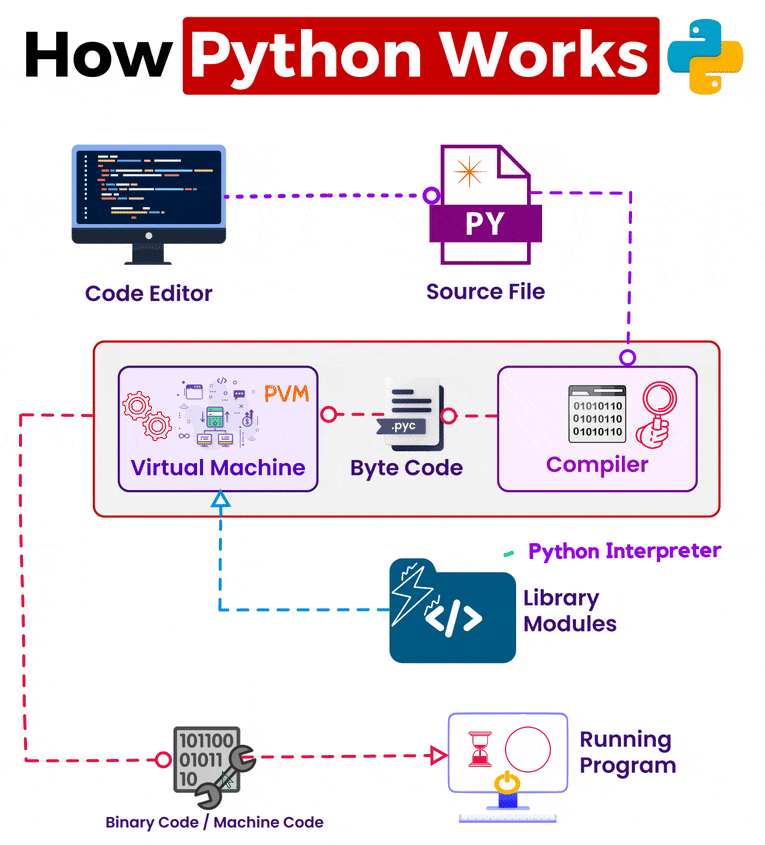
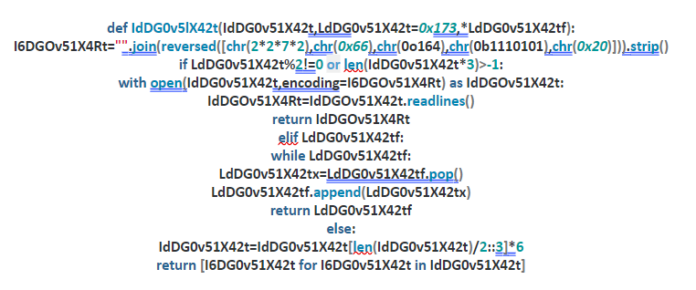
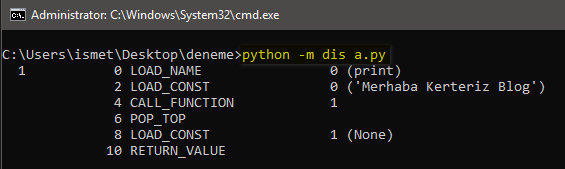
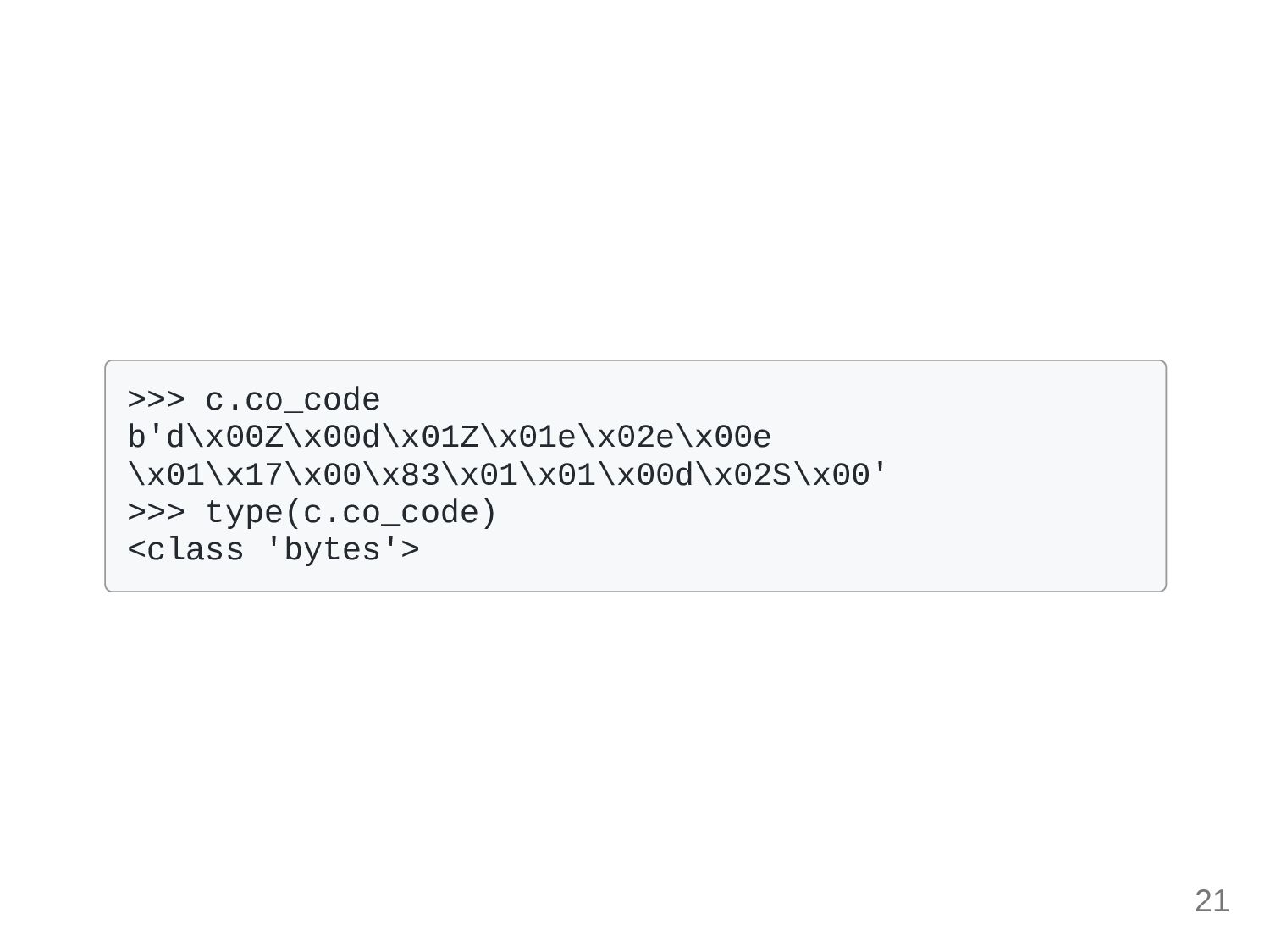
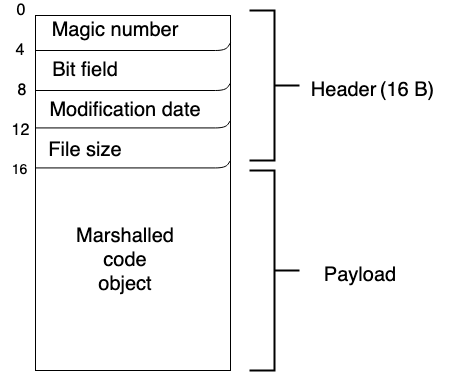
Discover cutting-edge trustedsec | obfuscation using python bytecode through extensive collections of modern photographs. highlighting modern interpretations of photography, images, and pictures. ideal for contemporary publications and media. Browse our premium trustedsec | obfuscation using python bytecode gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All trustedsec | obfuscation using python bytecode images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our trustedsec | obfuscation using python bytecode collection for various creative and professional projects. Cost-effective licensing makes professional trustedsec | obfuscation using python bytecode photography accessible to all budgets. Diverse style options within the trustedsec | obfuscation using python bytecode collection suit various aesthetic preferences. Professional licensing options accommodate both commercial and educational usage requirements. Instant download capabilities enable immediate access to chosen trustedsec | obfuscation using python bytecode images. The trustedsec | obfuscation using python bytecode archive serves professionals, educators, and creatives across diverse industries. Our trustedsec | obfuscation using python bytecode database continuously expands with fresh, relevant content from skilled photographers. Reliable customer support ensures smooth experience throughout the trustedsec | obfuscation using python bytecode selection process.










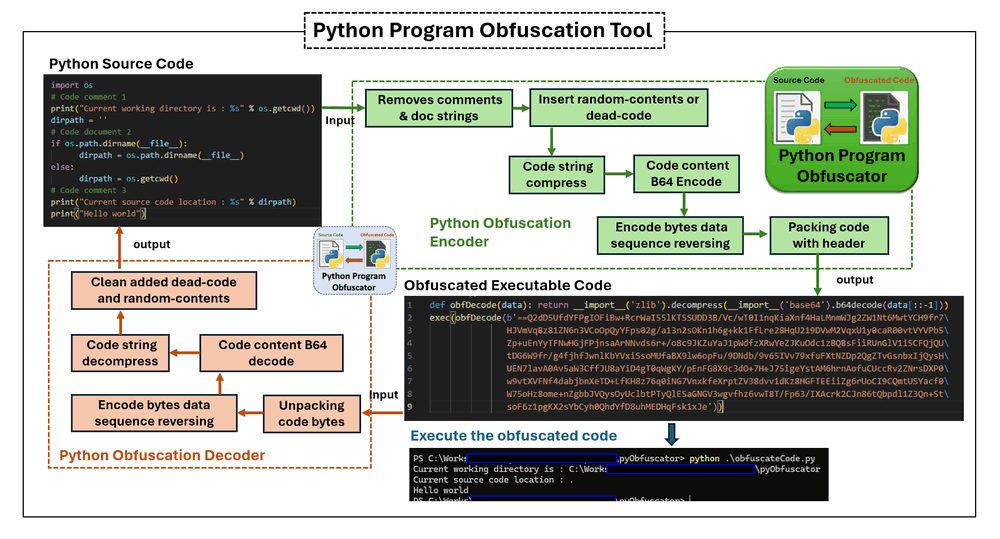








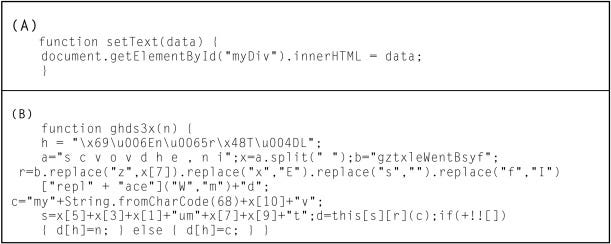


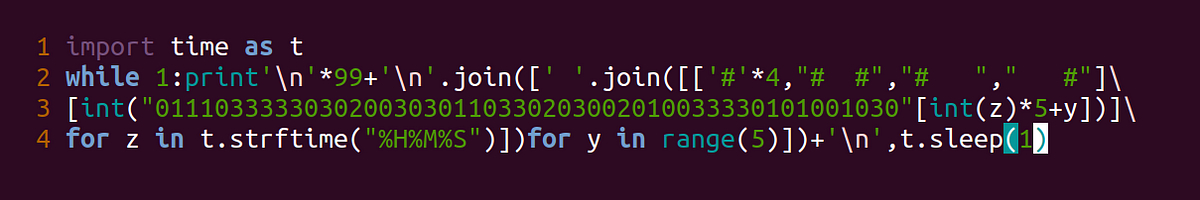

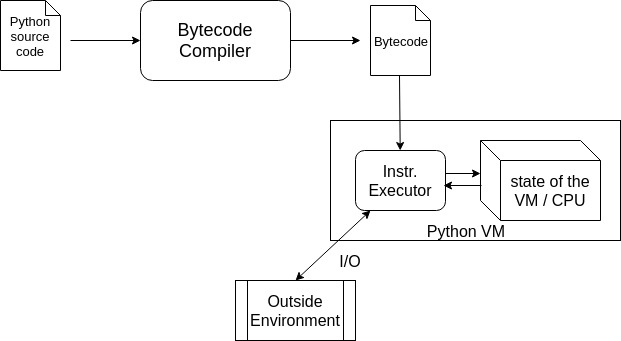



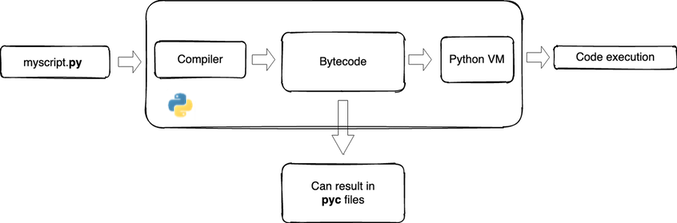






/filters:no_upscale()/articles/anatomy-code-obfuscation/en/resources/73-1667851620388.jpeg)


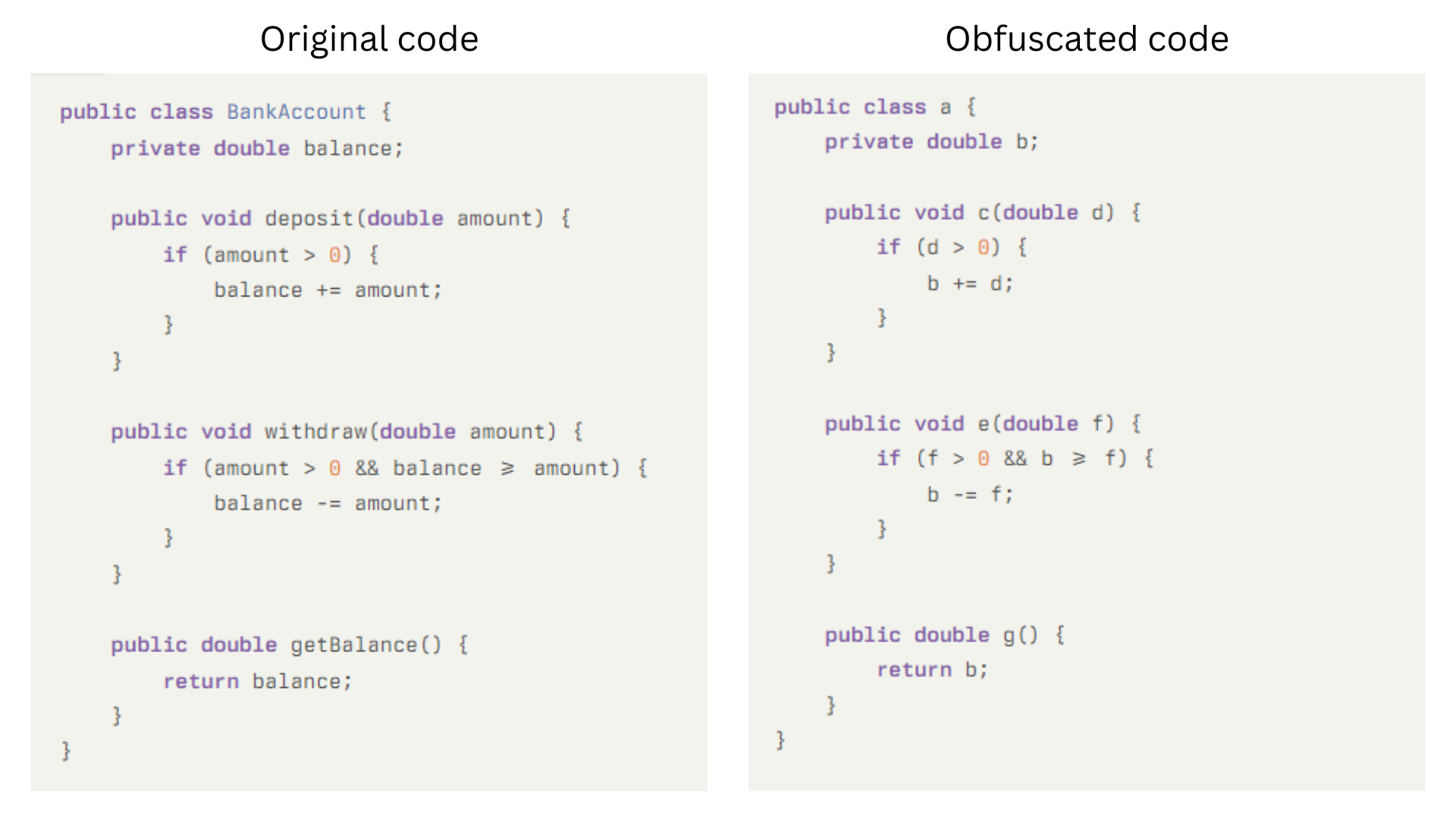




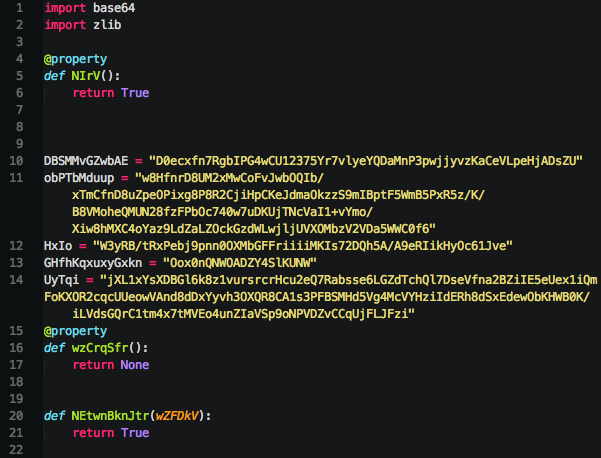

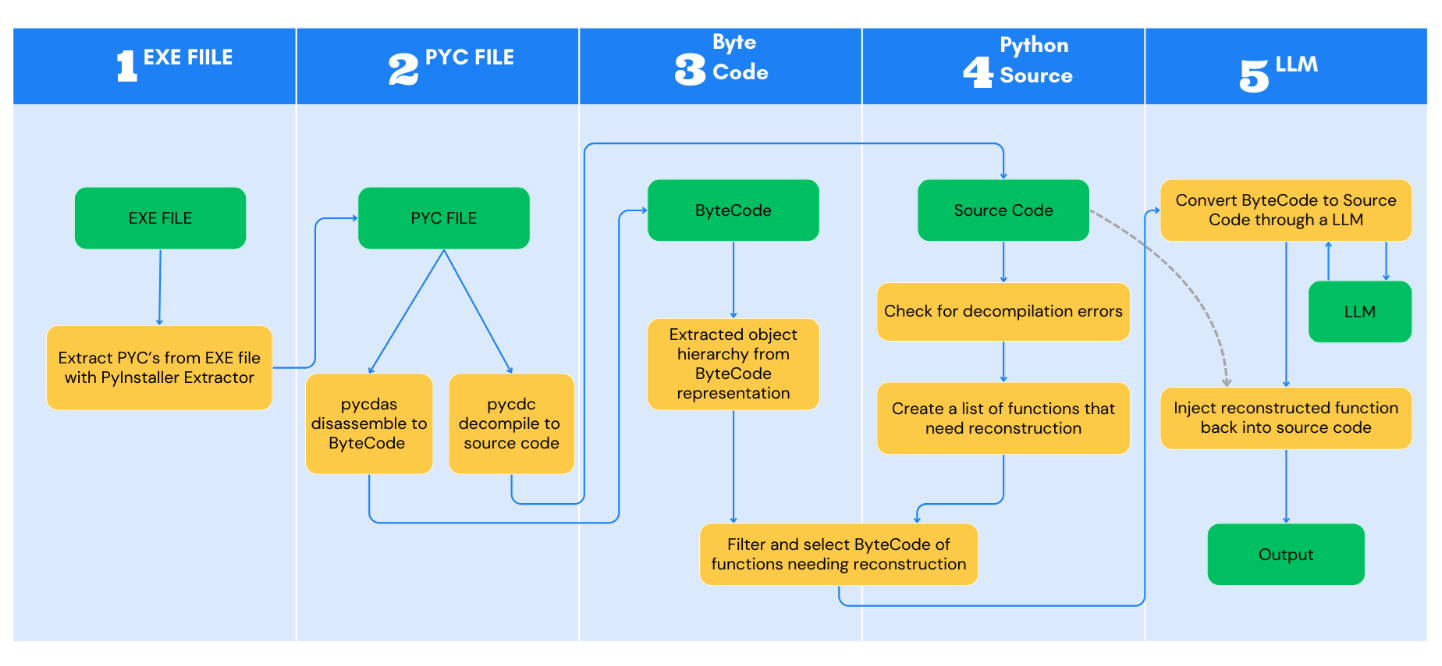

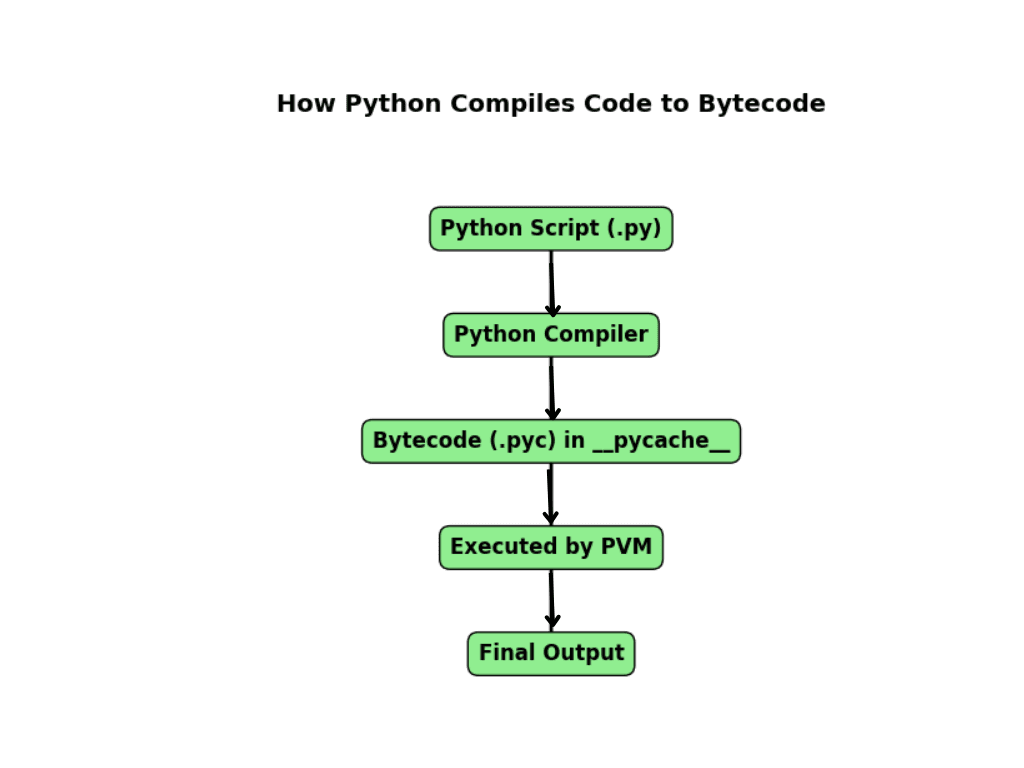















![Inter-Process Communication (IPC) in Python [with Examples] | Apriorit](https://www.apriorit.com/wp-content/uploads/2025/07/v1-1-blog-article-How-to-protect-your-Android-app-via-obfuscation-using-Java-bytecode-transformation-cover.jpg)