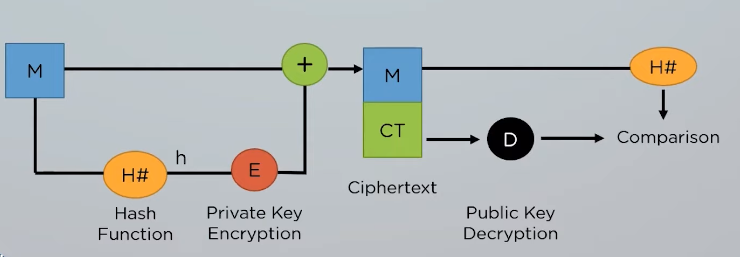
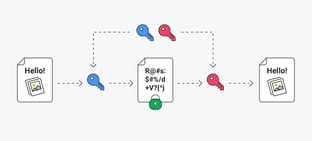
Build inspiration with our remarkable architectural encryption algorithms: key to data protection collection of numerous structural images. architecturally showcasing photography, images, and pictures. ideal for construction and design documentation. The encryption algorithms: key to data protection collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All encryption algorithms: key to data protection images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our encryption algorithms: key to data protection gallery offers diverse visual resources to bring your ideas to life. Reliable customer support ensures smooth experience throughout the encryption algorithms: key to data protection selection process. Cost-effective licensing makes professional encryption algorithms: key to data protection photography accessible to all budgets. The encryption algorithms: key to data protection archive serves professionals, educators, and creatives across diverse industries. Comprehensive tagging systems facilitate quick discovery of relevant encryption algorithms: key to data protection content. Multiple resolution options ensure optimal performance across different platforms and applications. Diverse style options within the encryption algorithms: key to data protection collection suit various aesthetic preferences. Instant download capabilities enable immediate access to chosen encryption algorithms: key to data protection images.

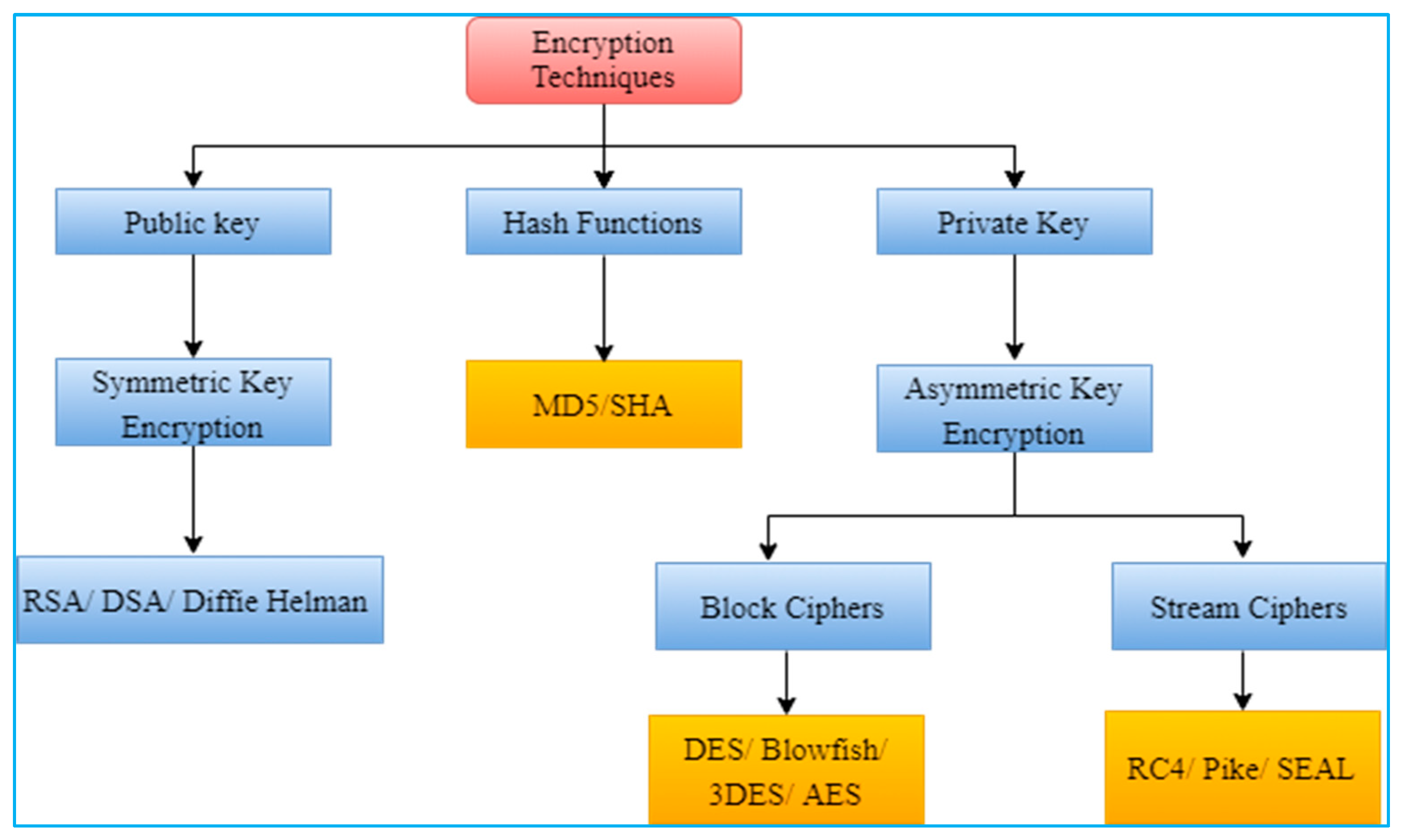


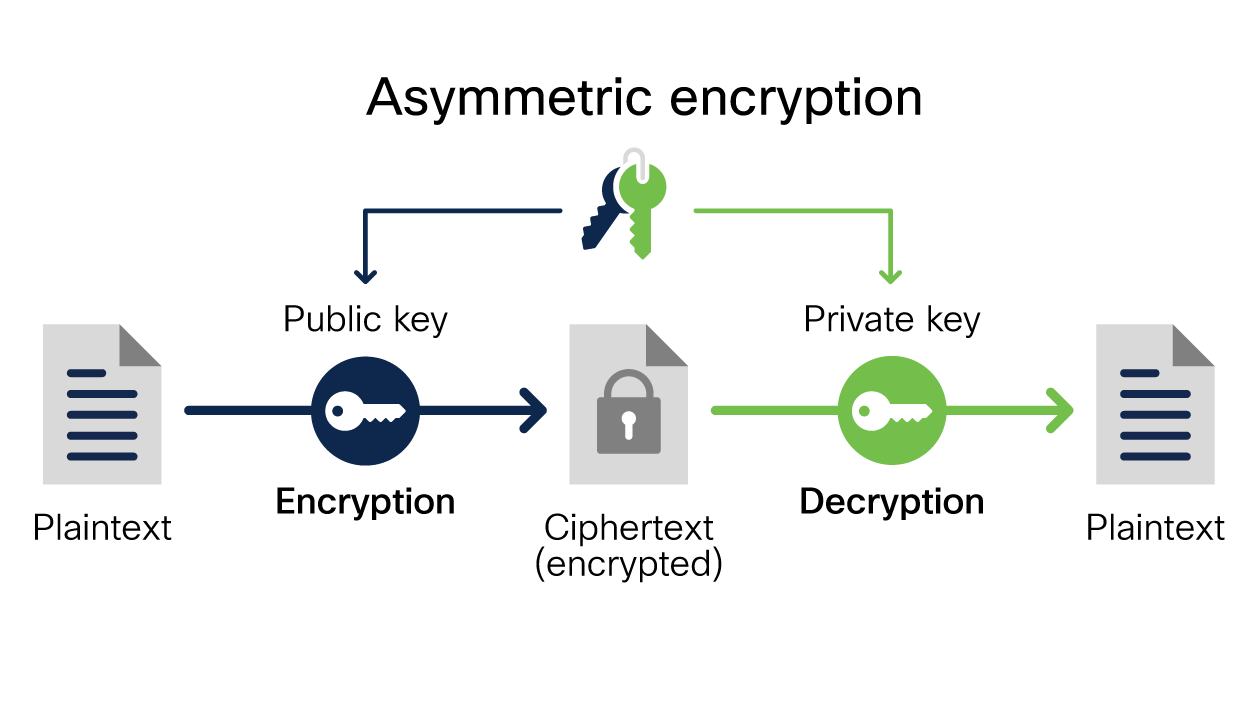
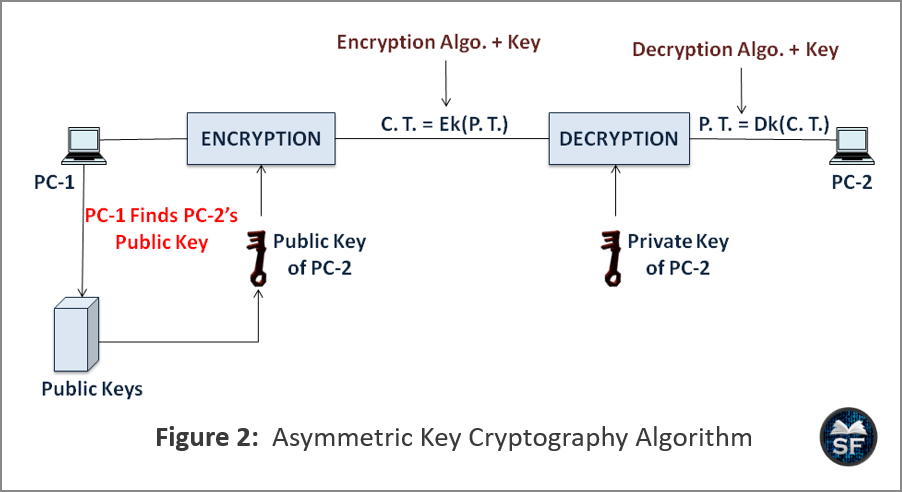

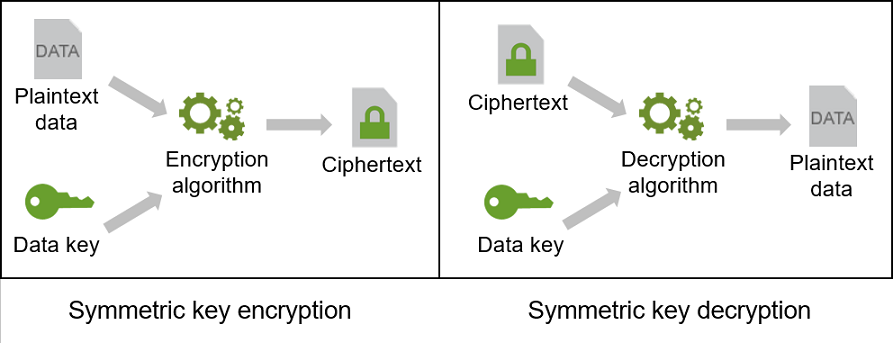


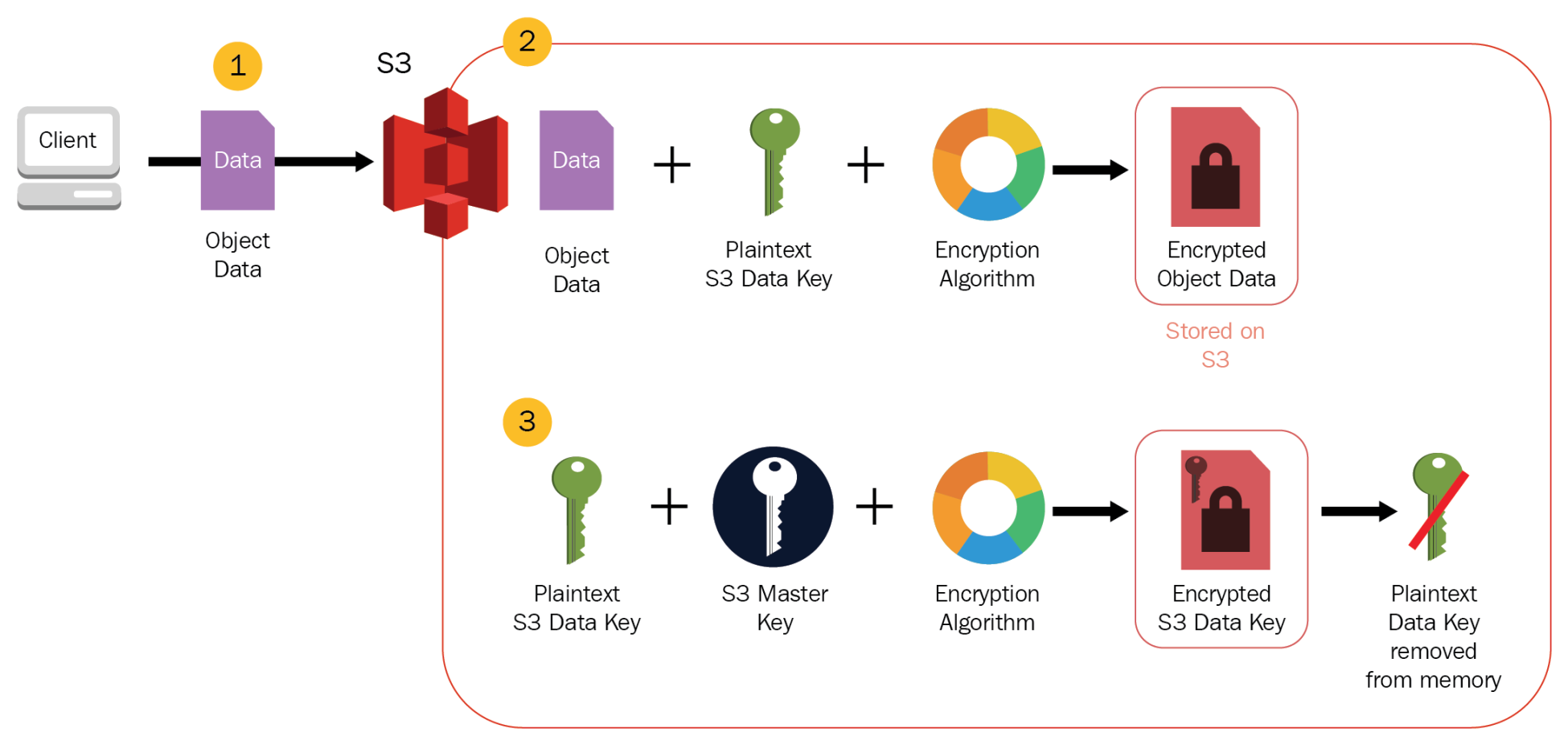
![[AWS SAA] S3 Encryption](https://velog.velcdn.com/images/jungmyeong96/post/7c9a60f1-7fa6-4573-bacb-968759858ad9/image.png)




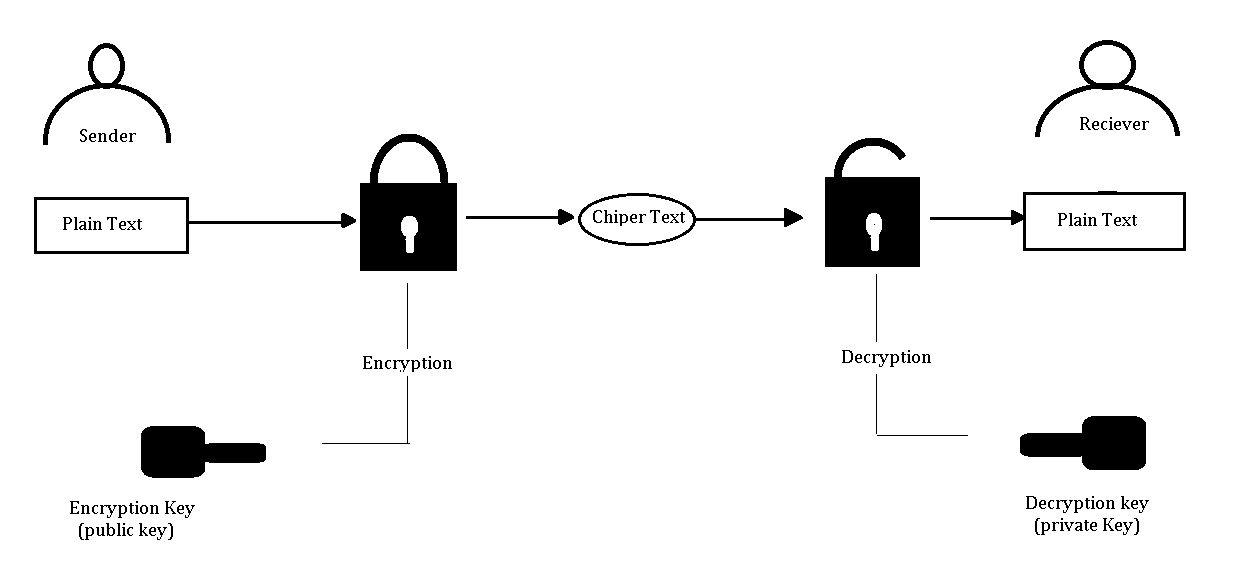
![[AWS] Encrypting your data easily via KMS on AWS – NimTechnology](https://nimtechnology.com/wp-content/uploads/2022/09/image-51.png)




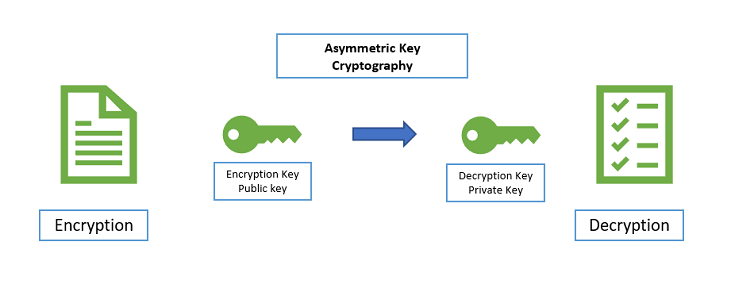


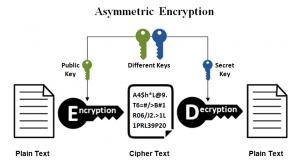
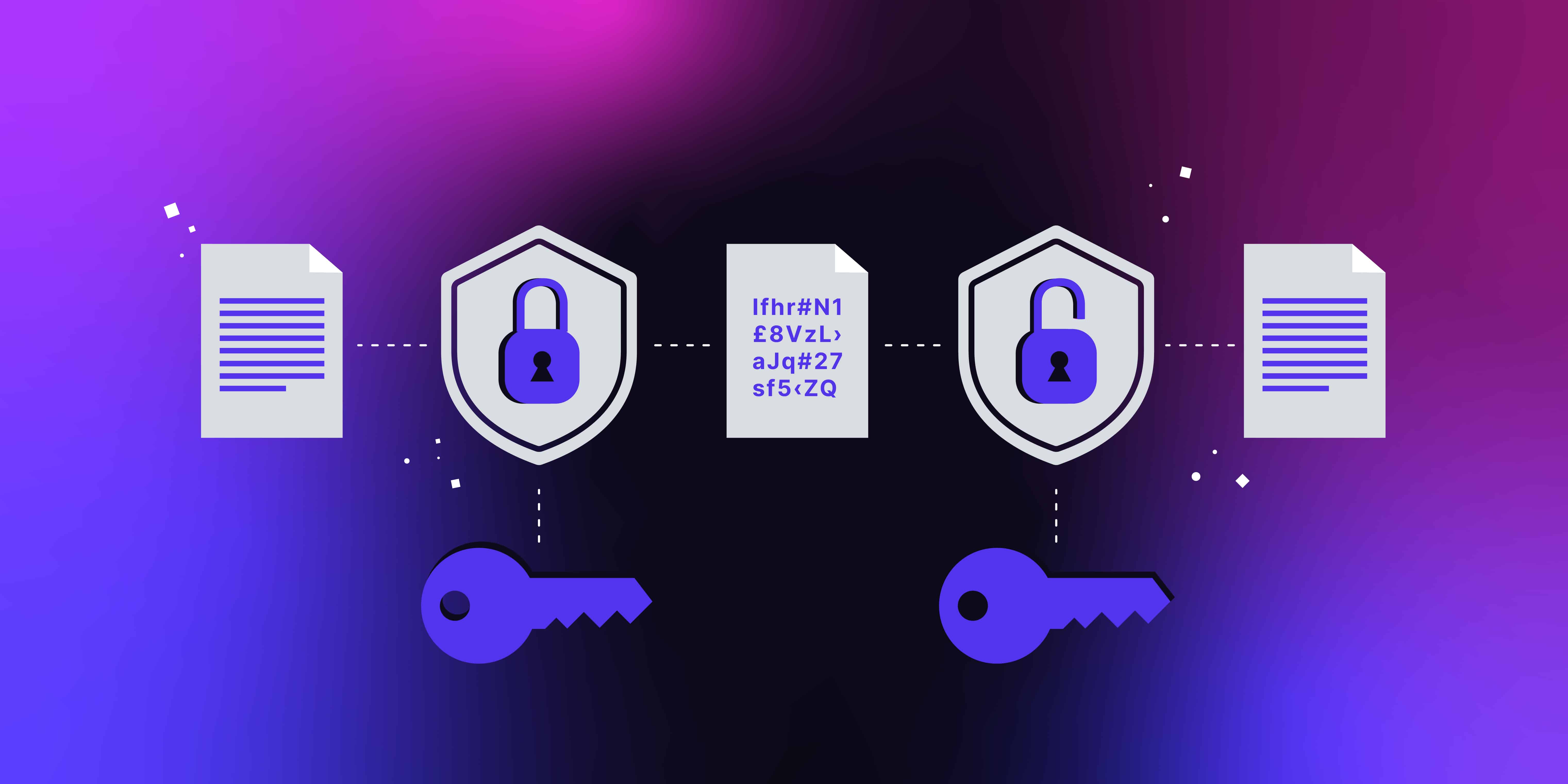
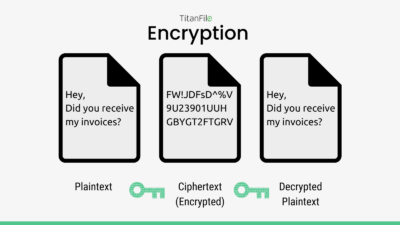






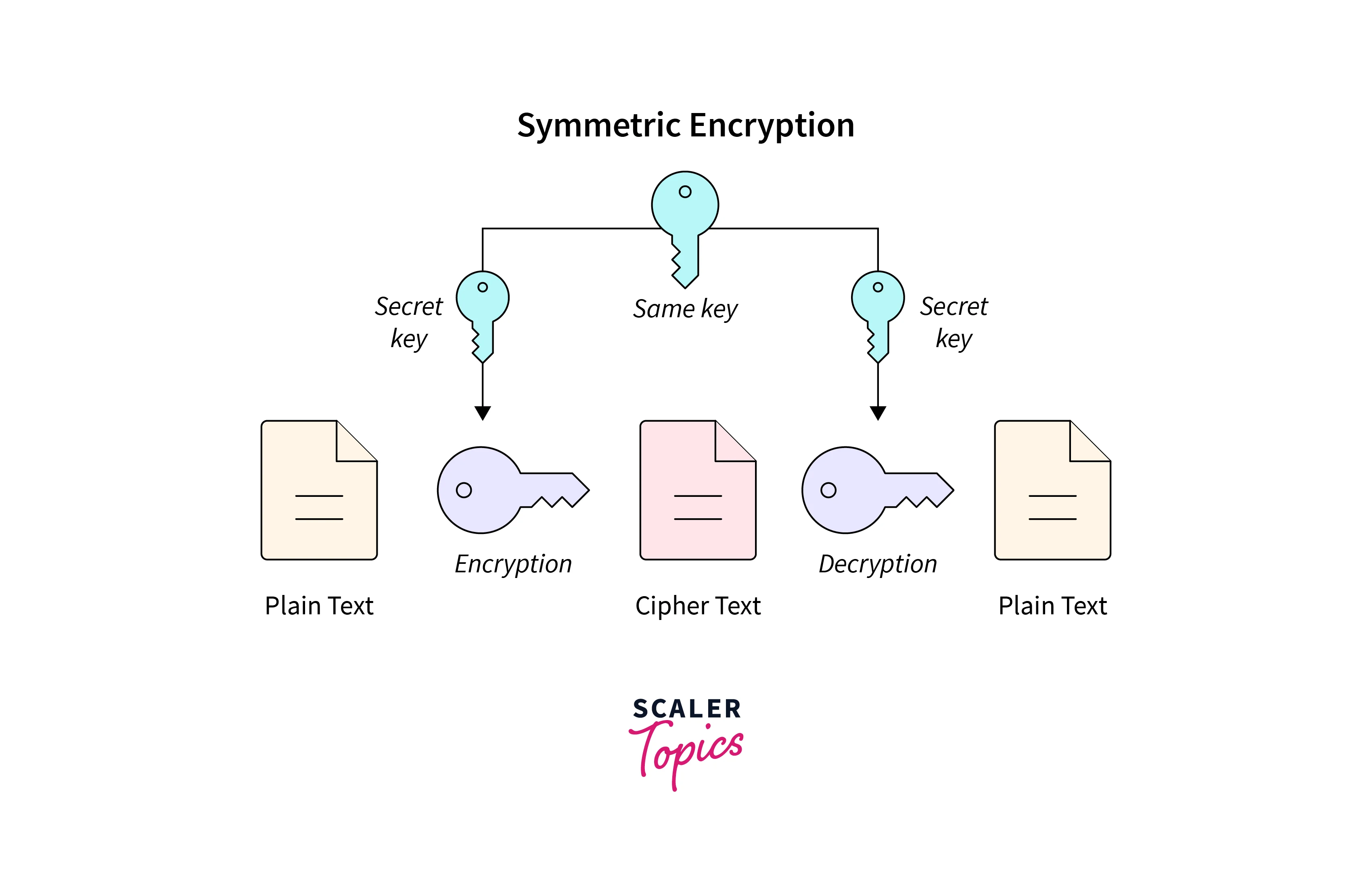
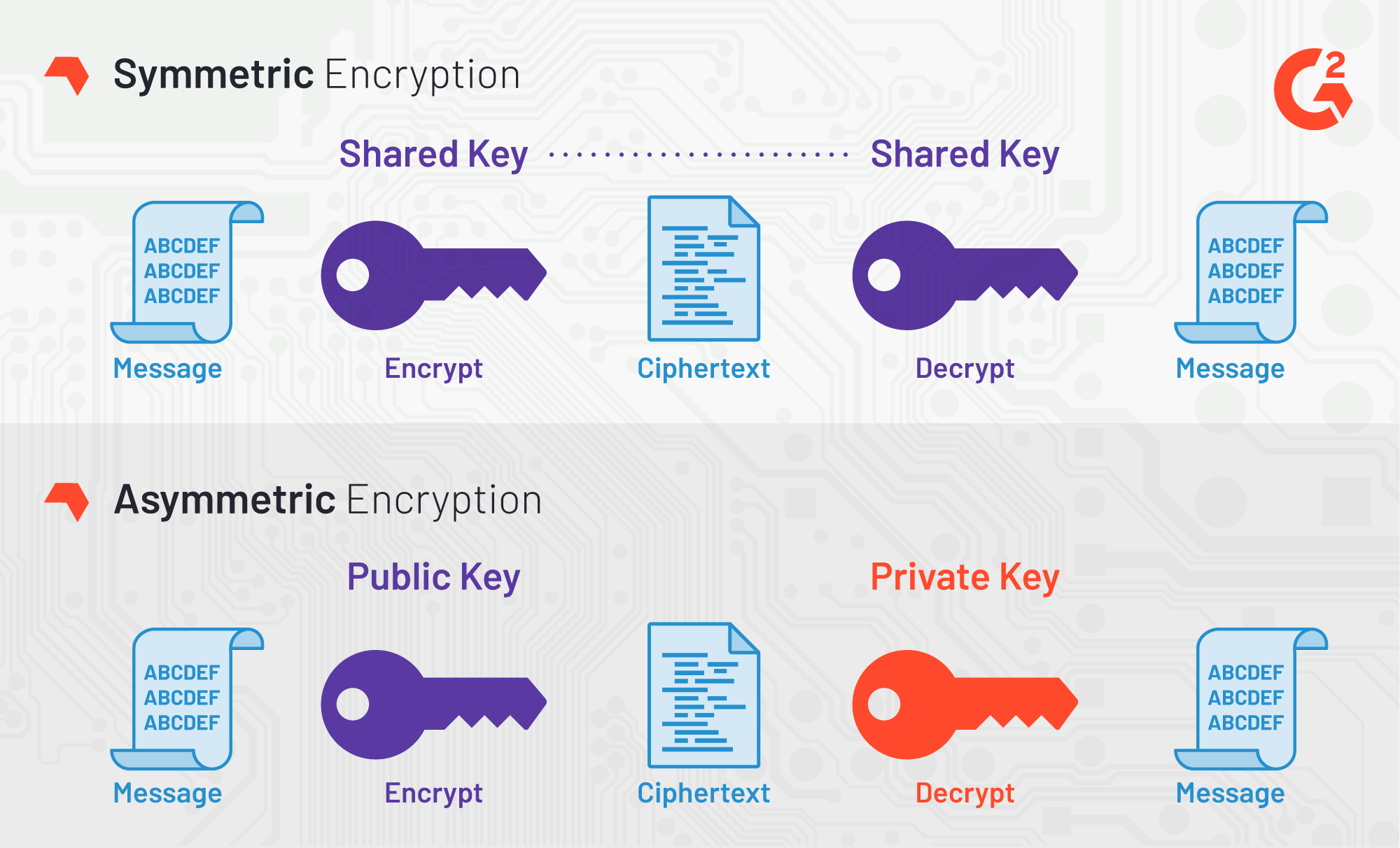


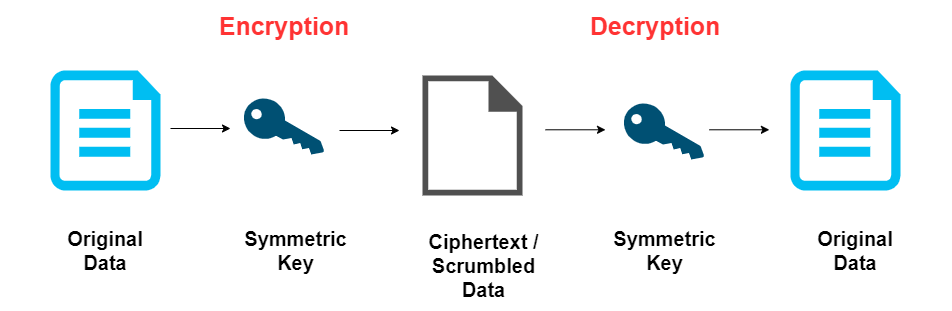




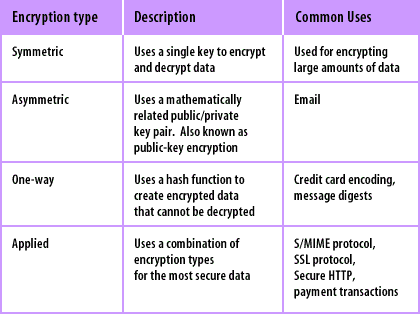

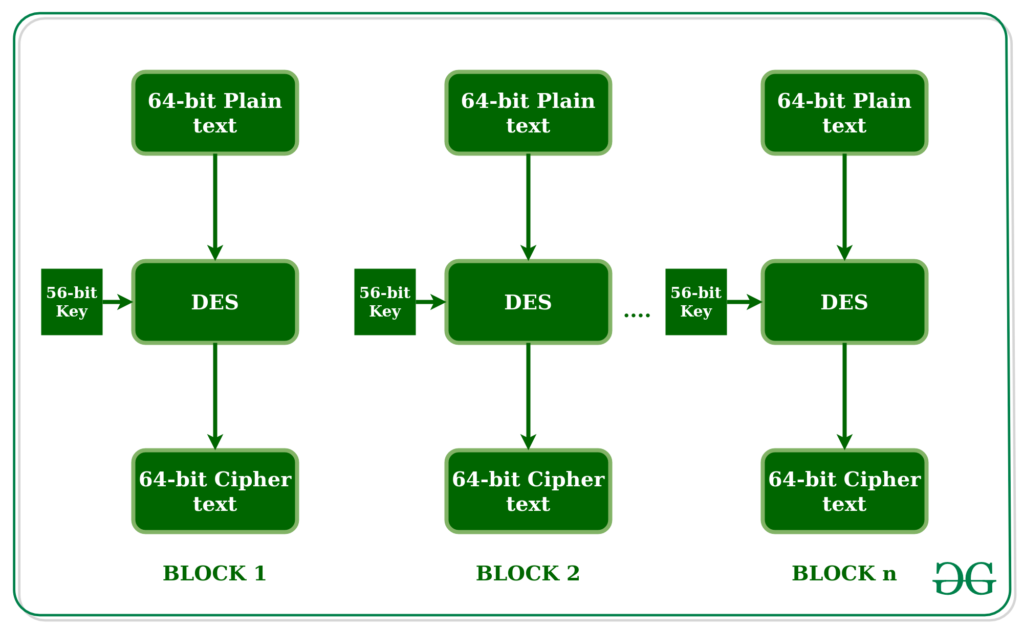


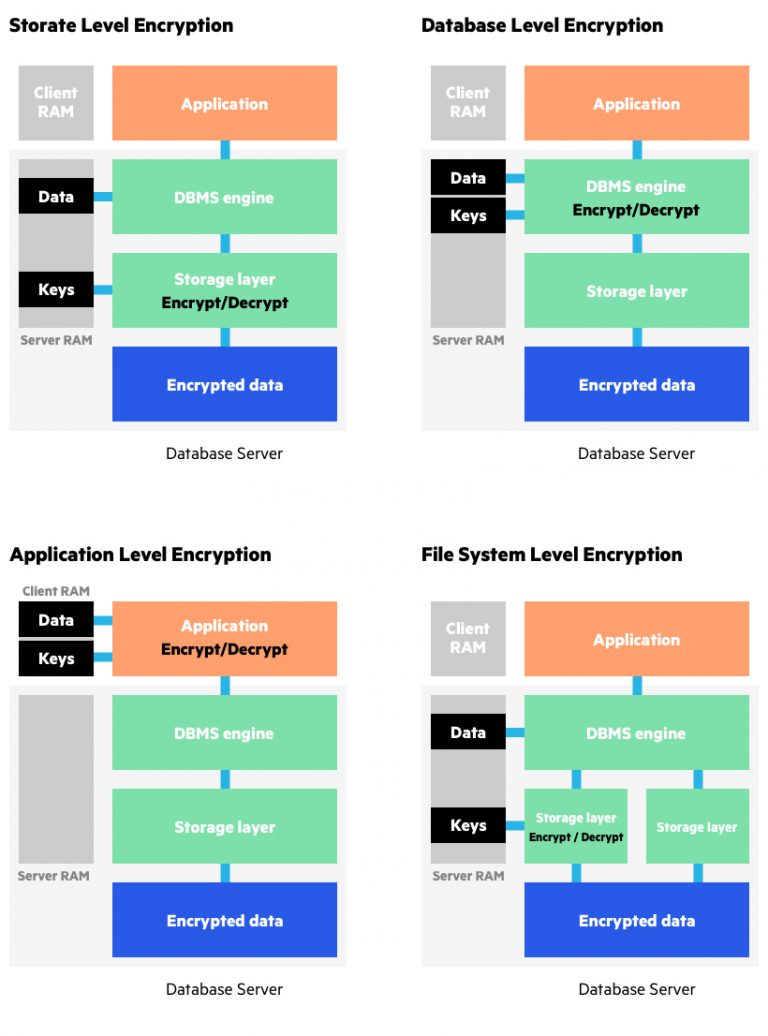

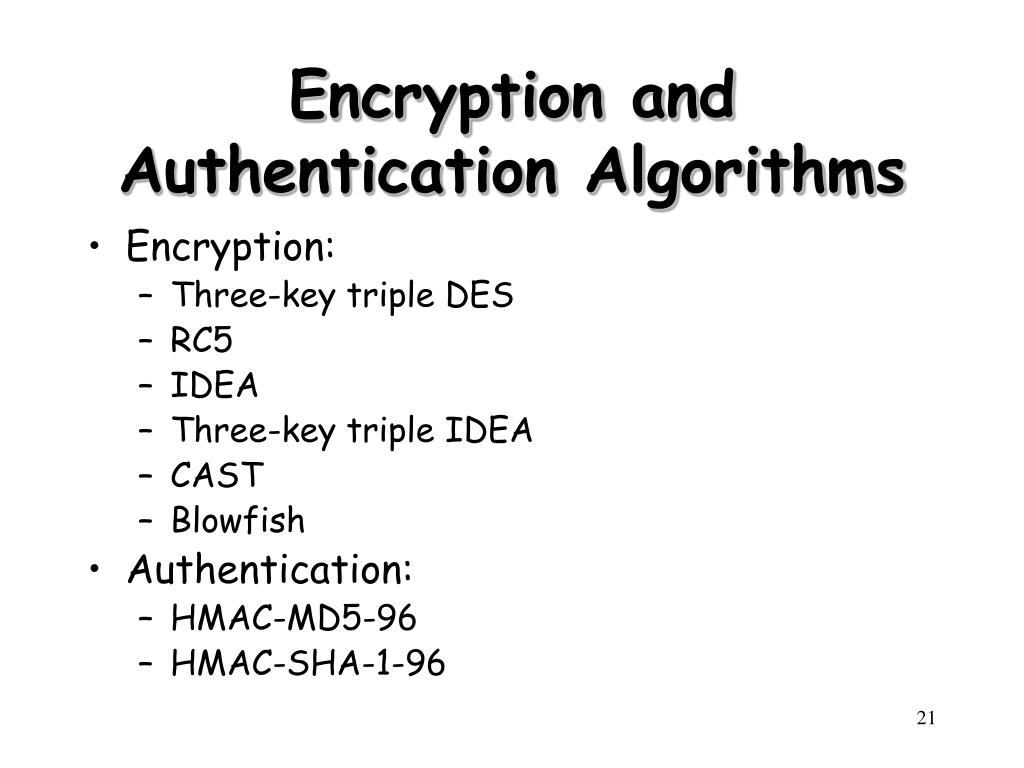









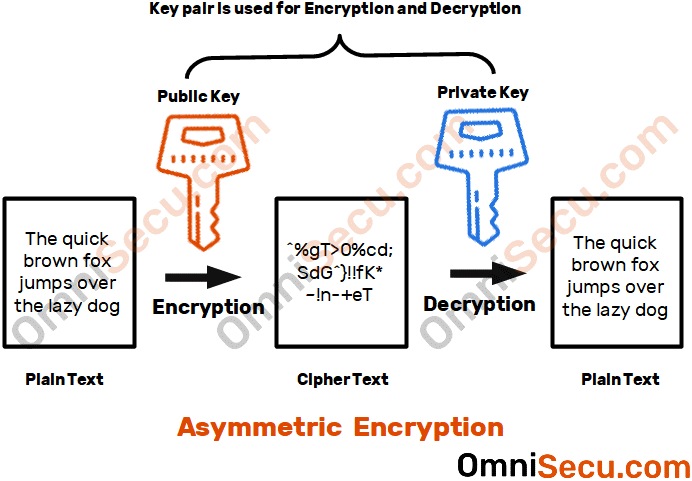
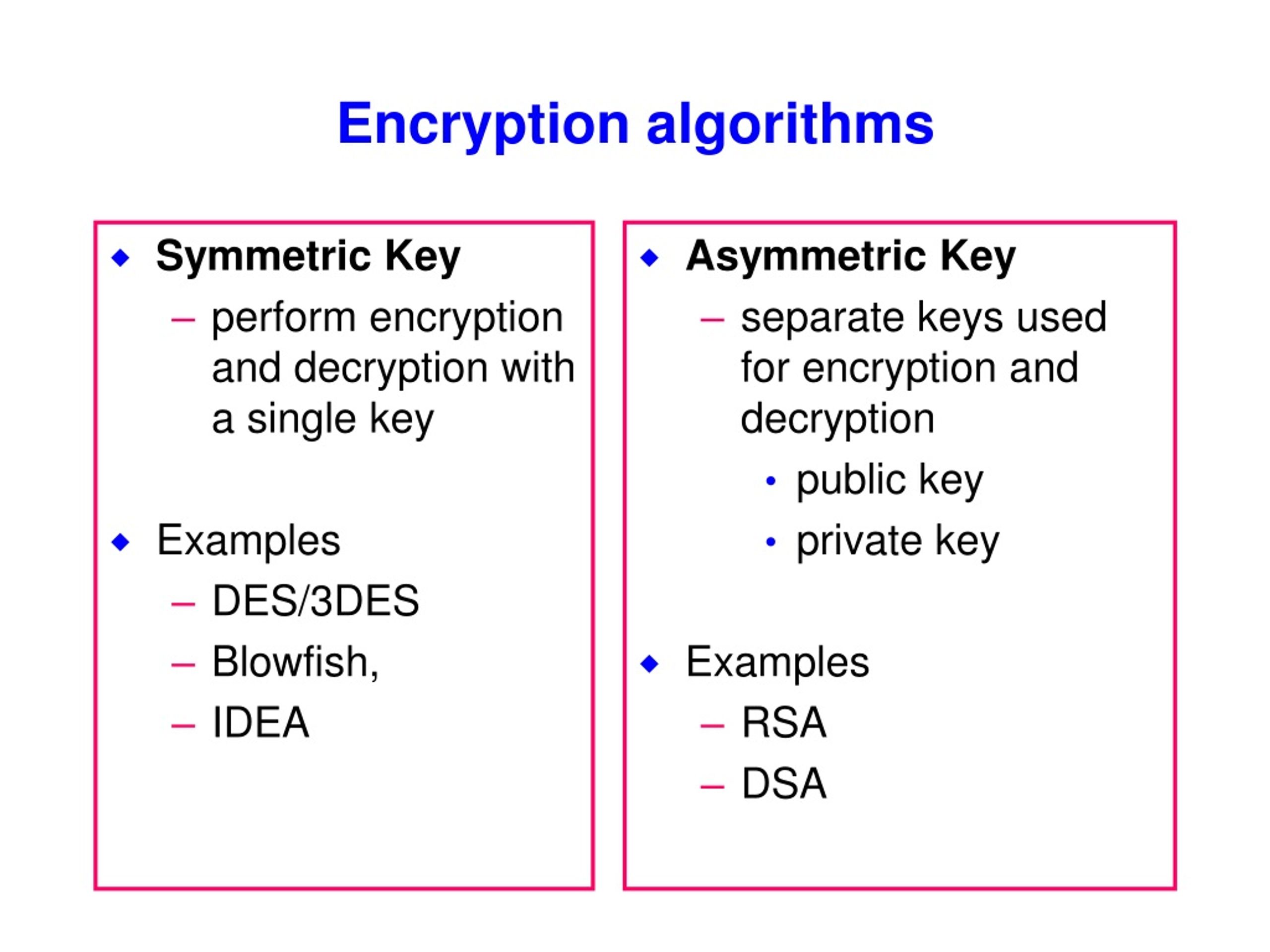
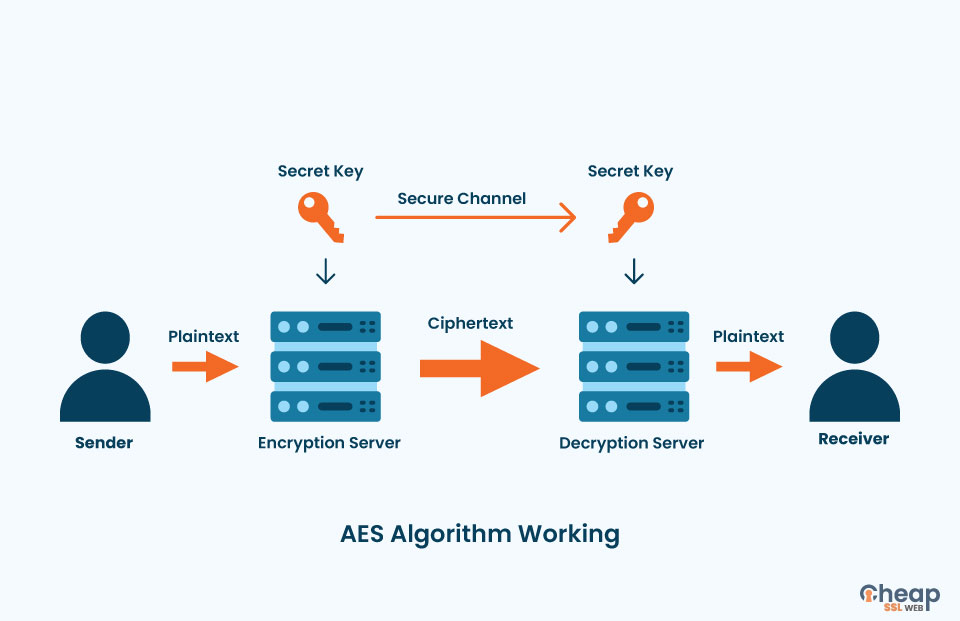
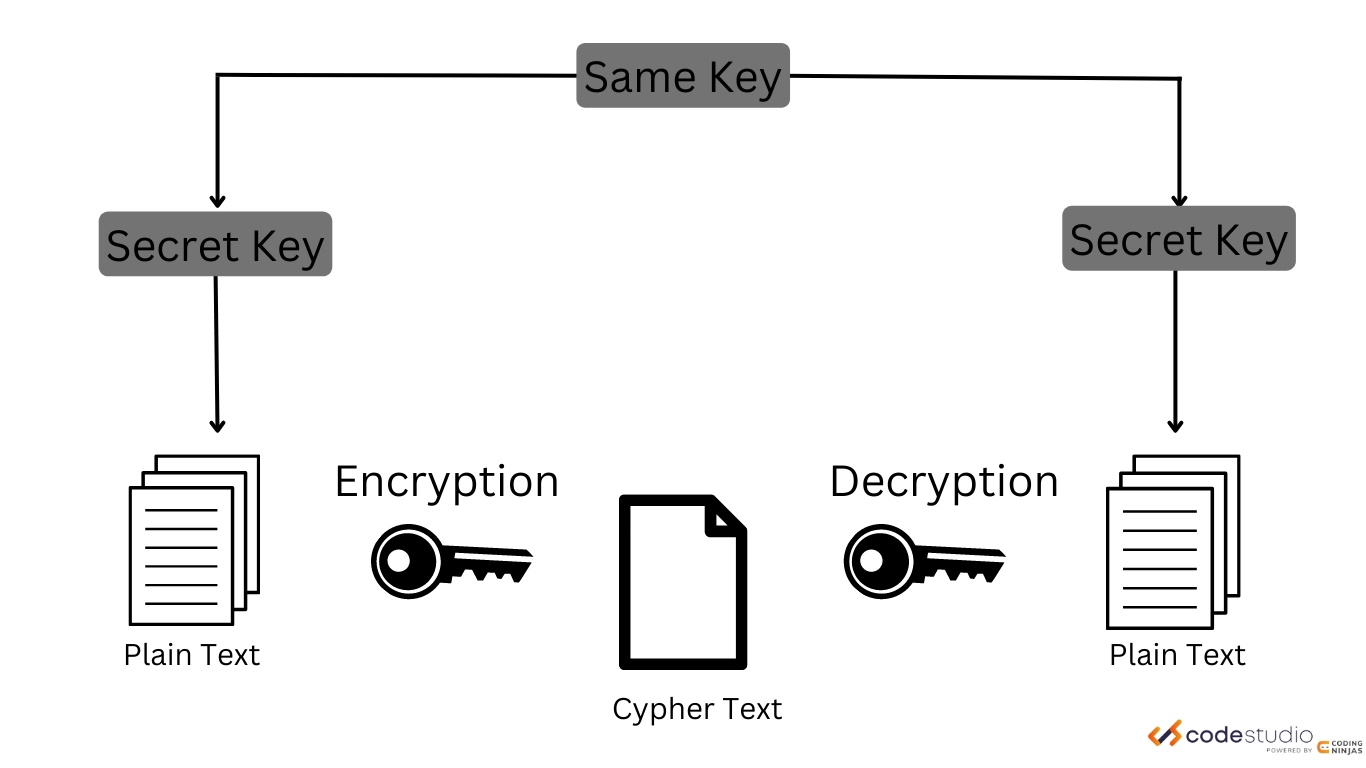









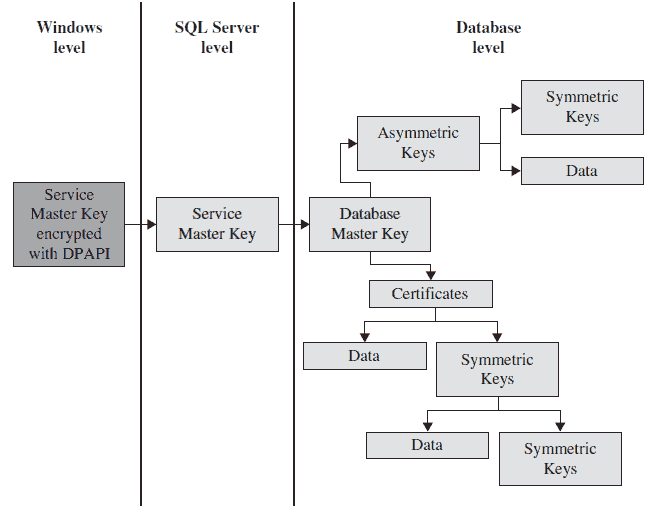
![3 Cryptography Techniques [14]. Data Encryption Standard Algorithm ...](https://www.researchgate.net/profile/Dr-Kashmar/publication/367240386/figure/fig2/AS:11431281113741362@1674062743070/Cryptography-Techniques-14-Data-Encryption-Standard-Algorithm-DES-The-United.png)