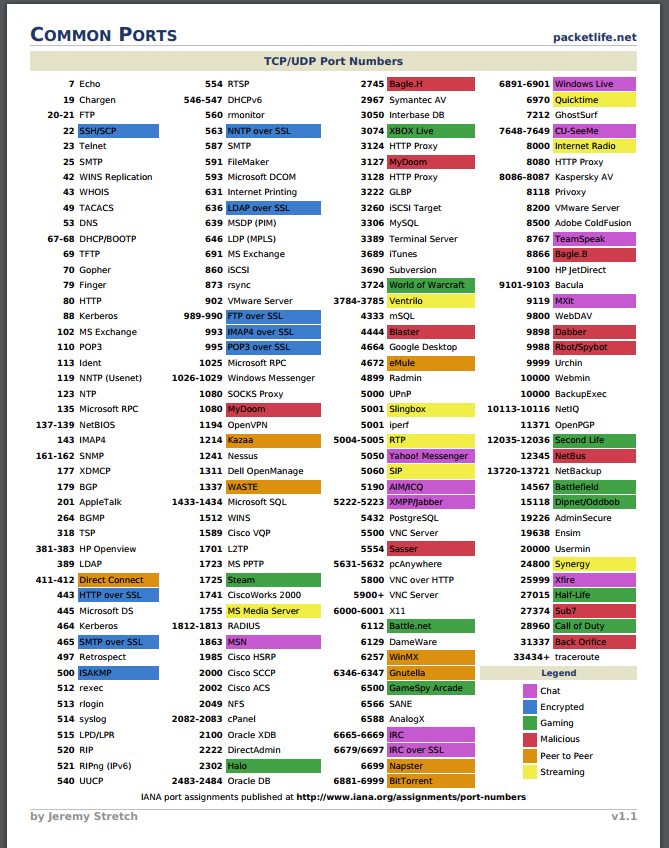
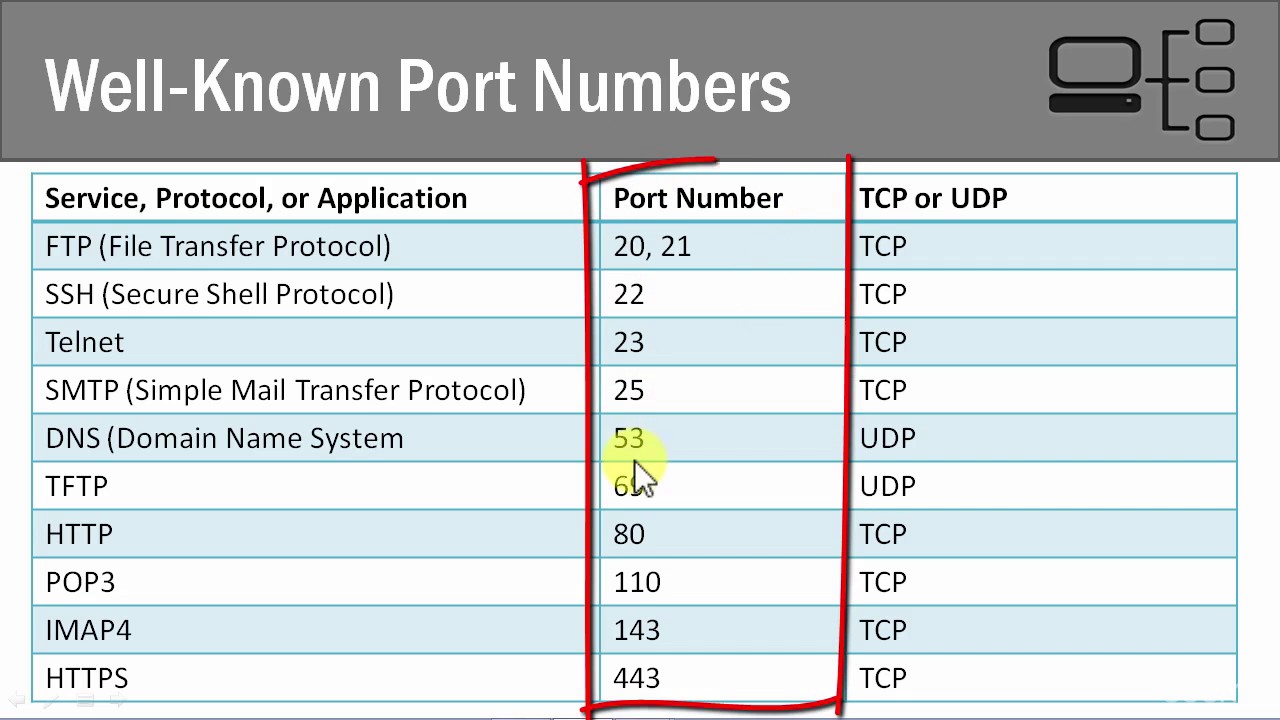
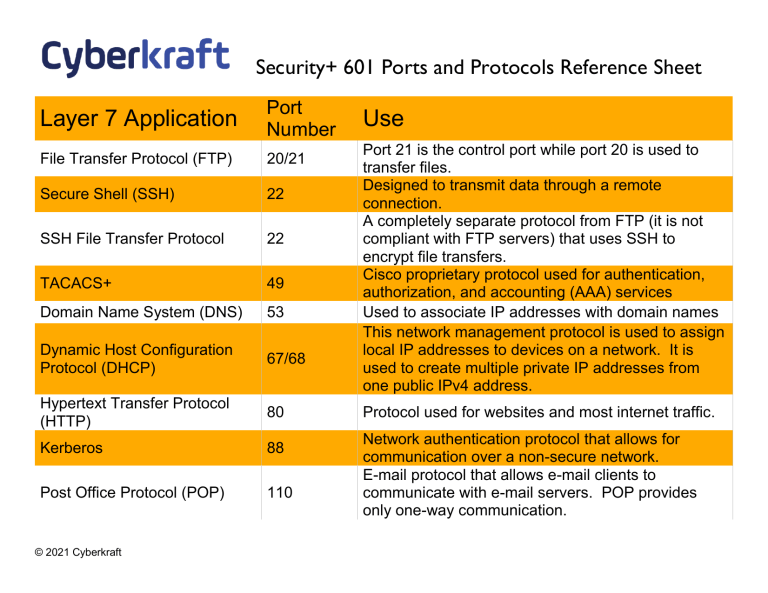
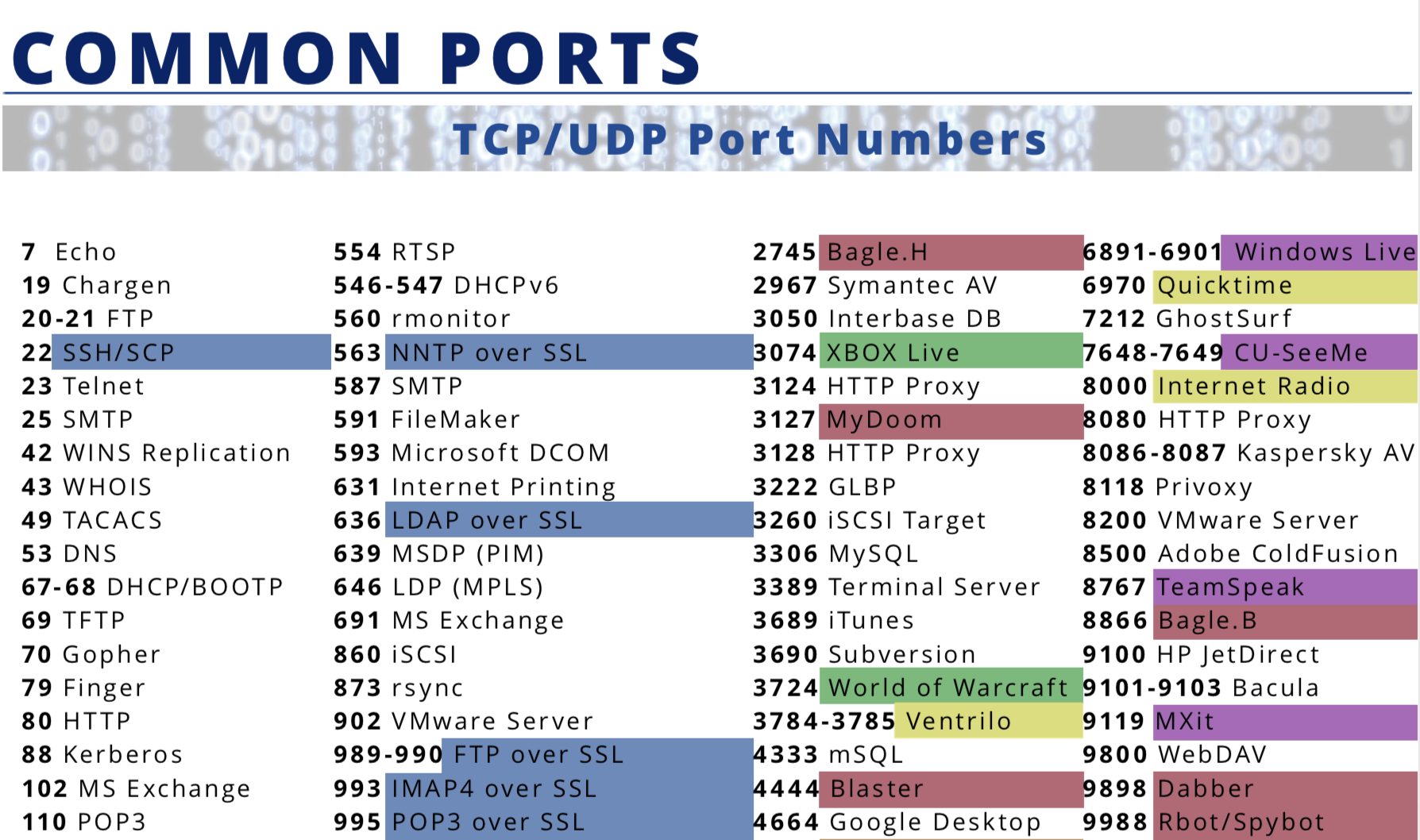
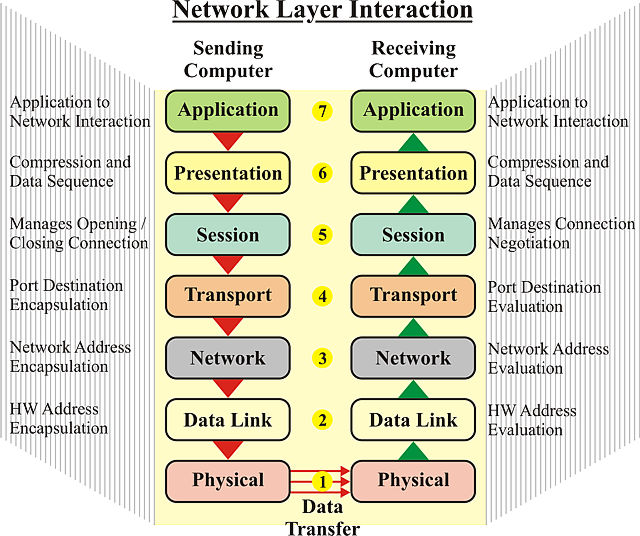
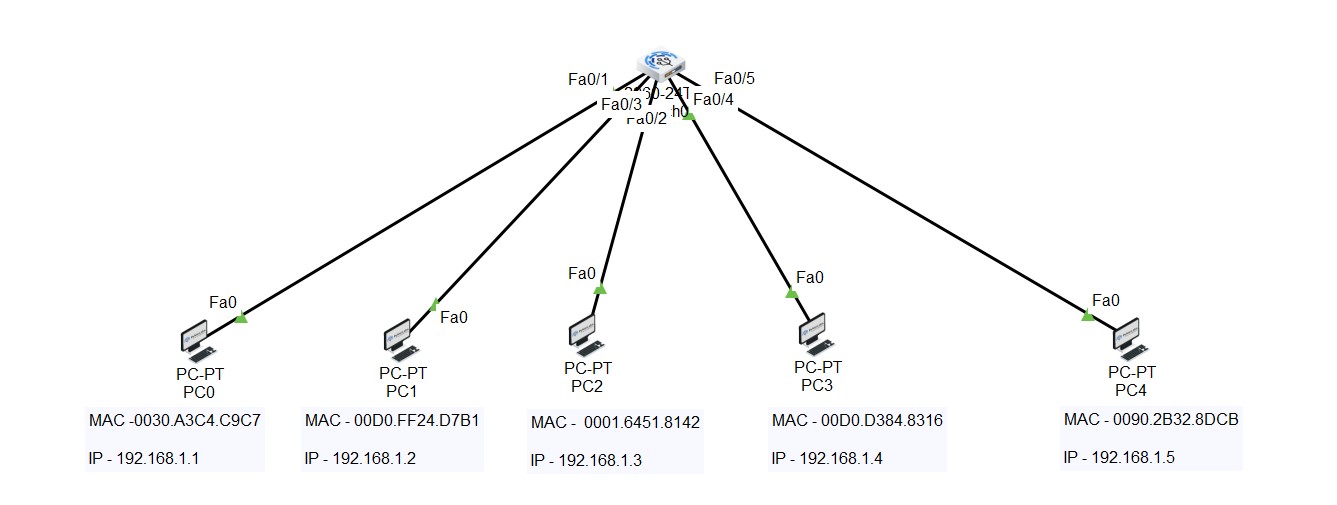
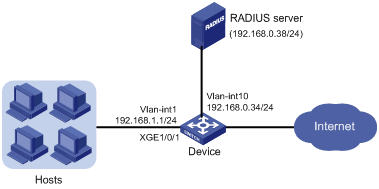
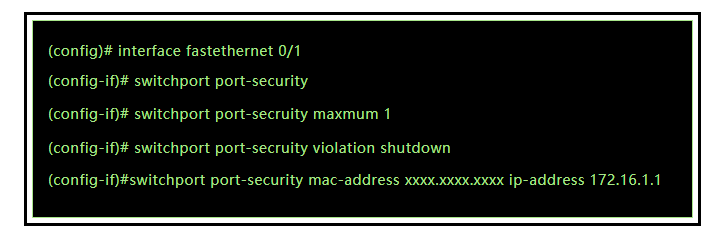
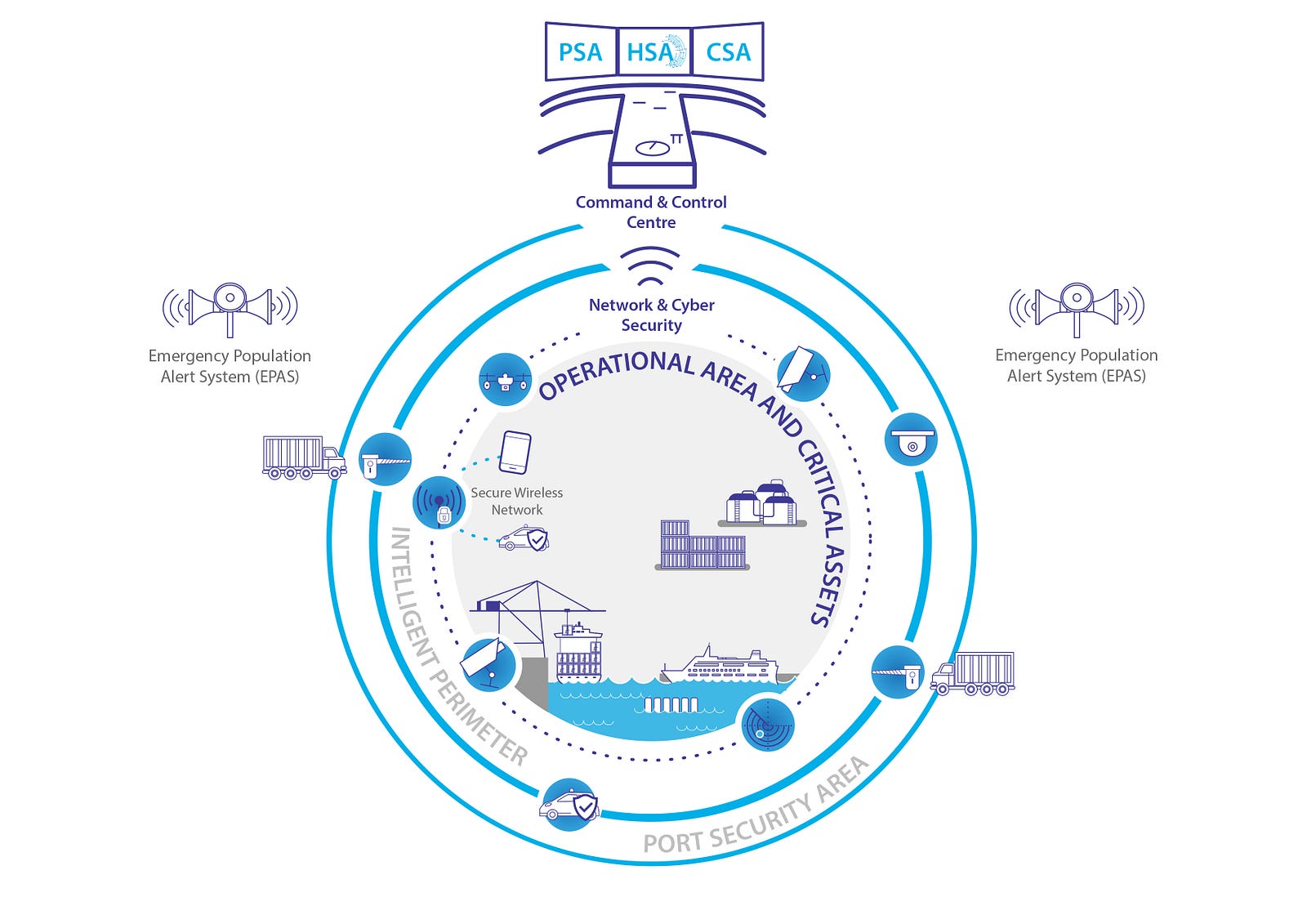
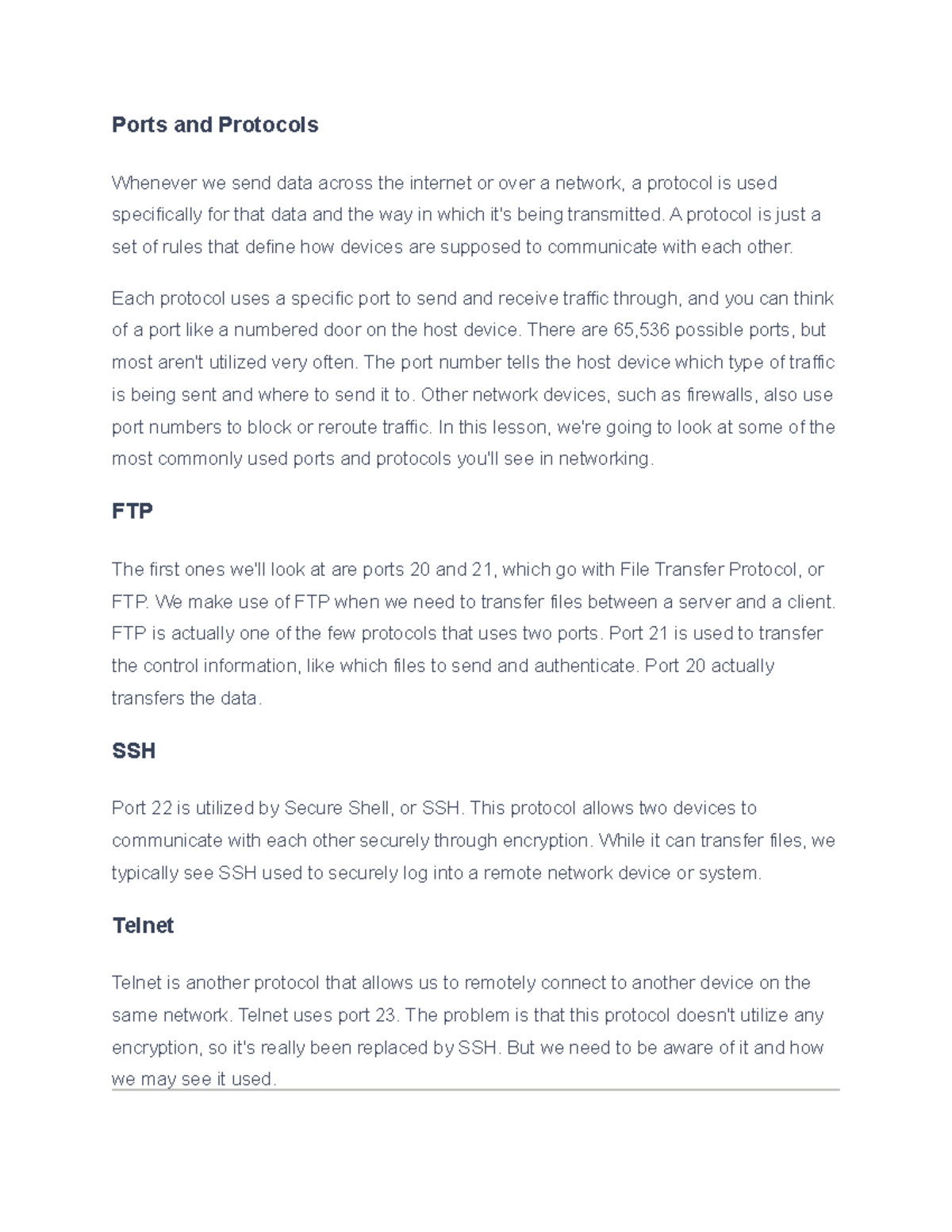
Study the characteristics of understanding common ports in cybersecurity: what they are and how to using our comprehensive set of countless learning images. enhancing knowledge retention through engaging and informative imagery. encouraging critical thinking and analytical skill development. The understanding common ports in cybersecurity: what they are and how to collection maintains consistent quality standards across all images. Excellent for educational materials, academic research, teaching resources, and learning activities All understanding common ports in cybersecurity: what they are and how to images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our understanding common ports in cybersecurity: what they are and how to images support learning objectives across diverse educational environments. Instant download capabilities enable immediate access to chosen understanding common ports in cybersecurity: what they are and how to images. Multiple resolution options ensure optimal performance across different platforms and applications. The understanding common ports in cybersecurity: what they are and how to collection represents years of careful curation and professional standards. Comprehensive tagging systems facilitate quick discovery of relevant understanding common ports in cybersecurity: what they are and how to content. Our understanding common ports in cybersecurity: what they are and how to database continuously expands with fresh, relevant content from skilled photographers.

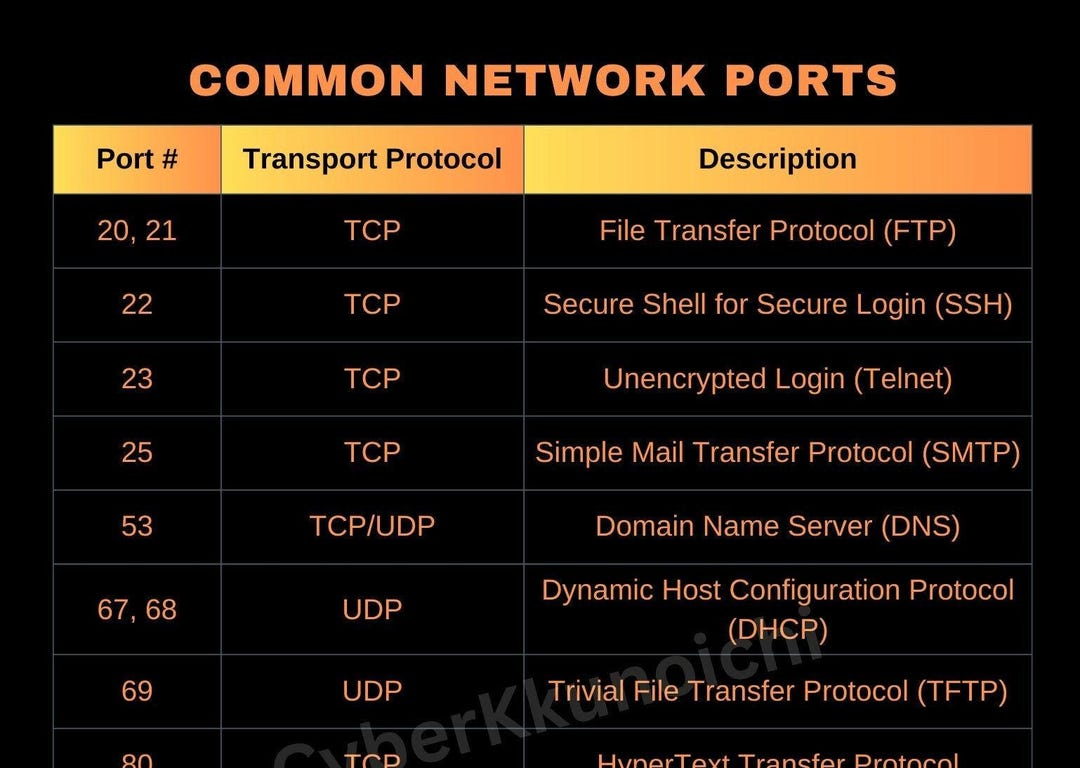

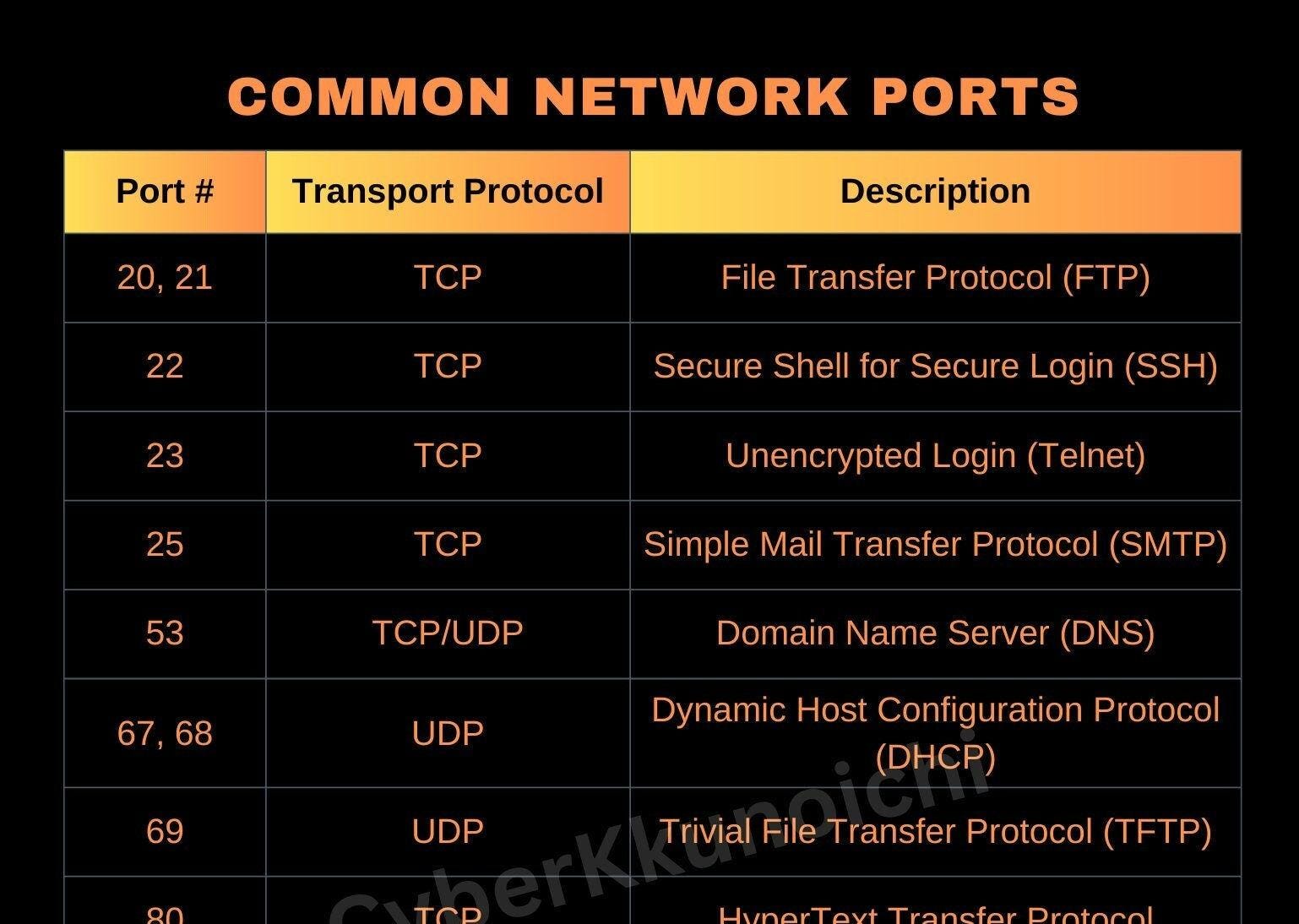




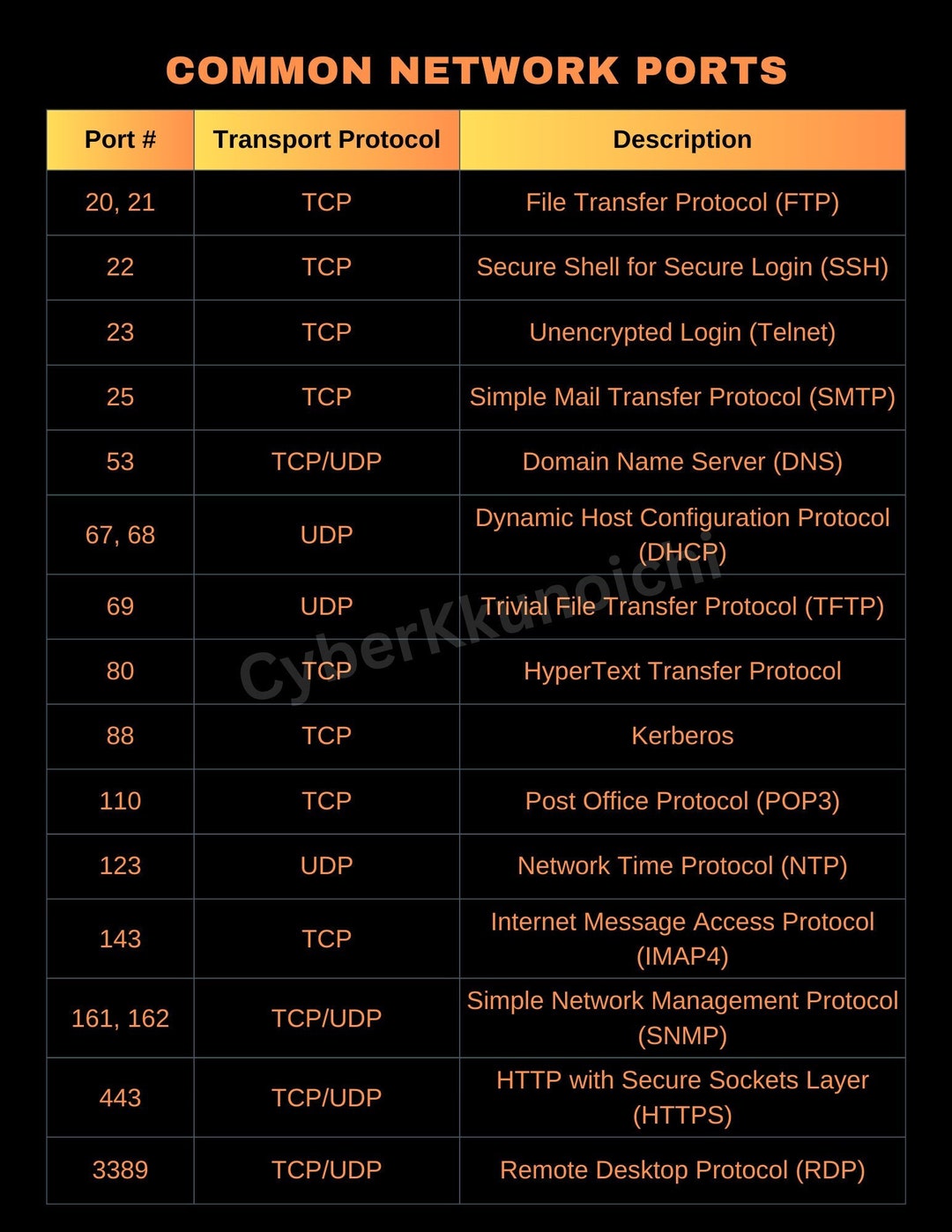






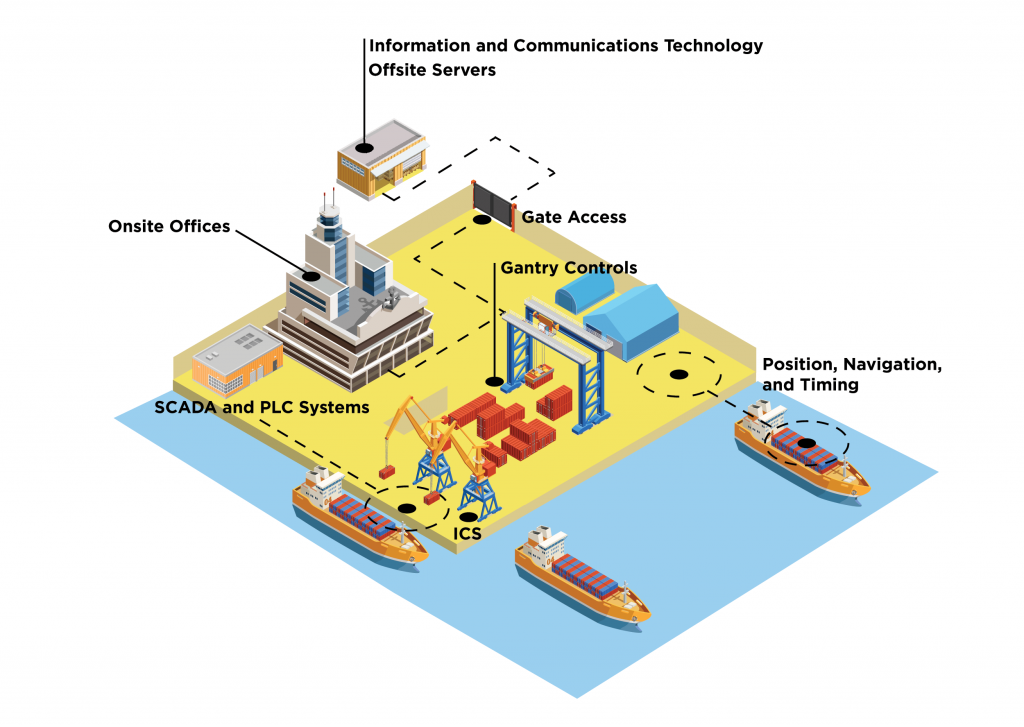
![Cyber Security Technical Interview [CHEATCODES] - DETECTX | Cloud ...](https://www.detectx.com.au/wp-content/uploads/2022/11/oC7YNJjVQySybEW6rV6u_Common_Ports.png)