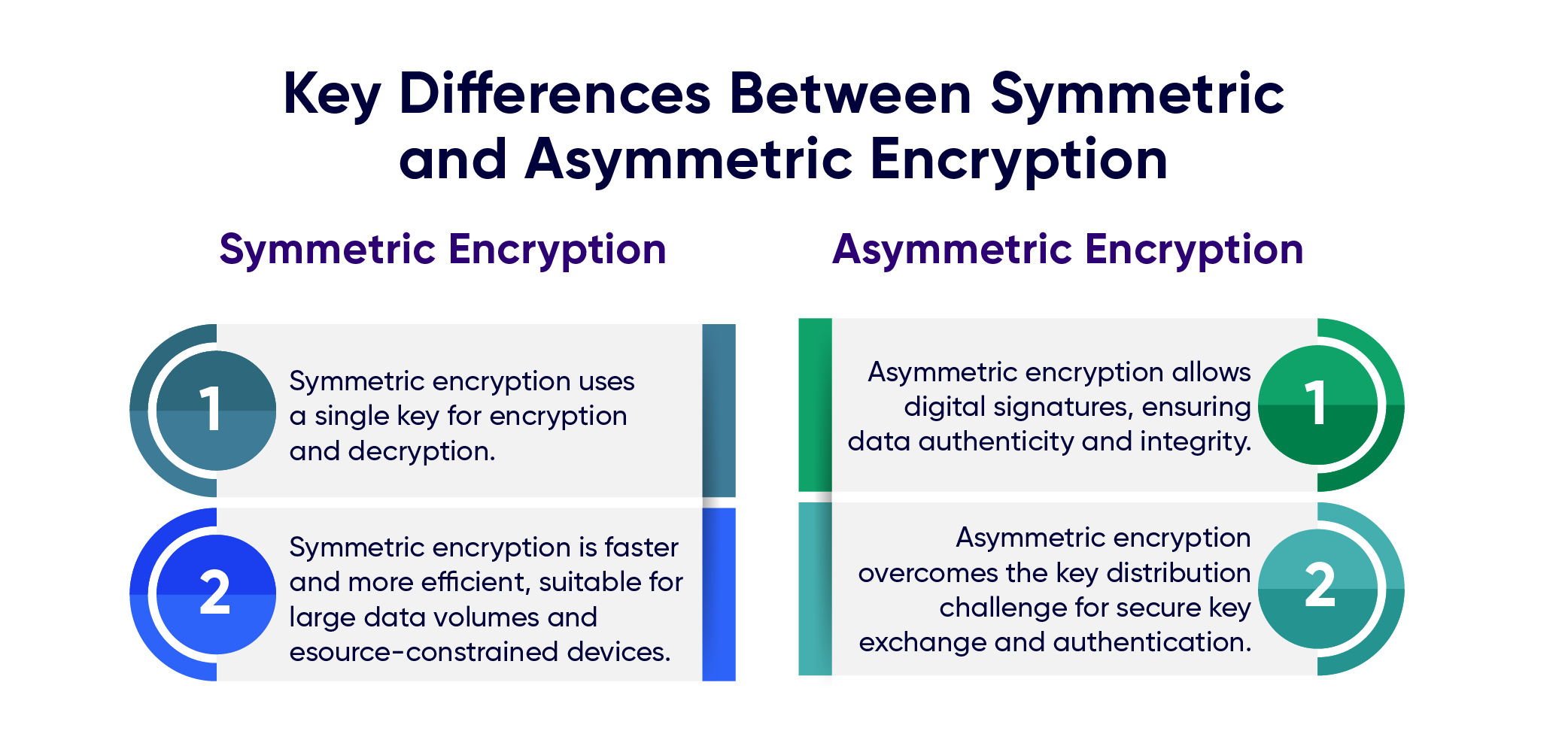
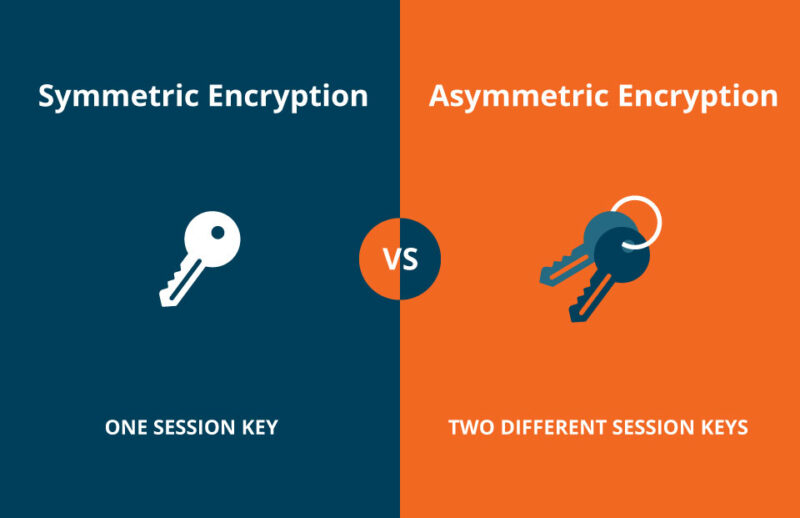
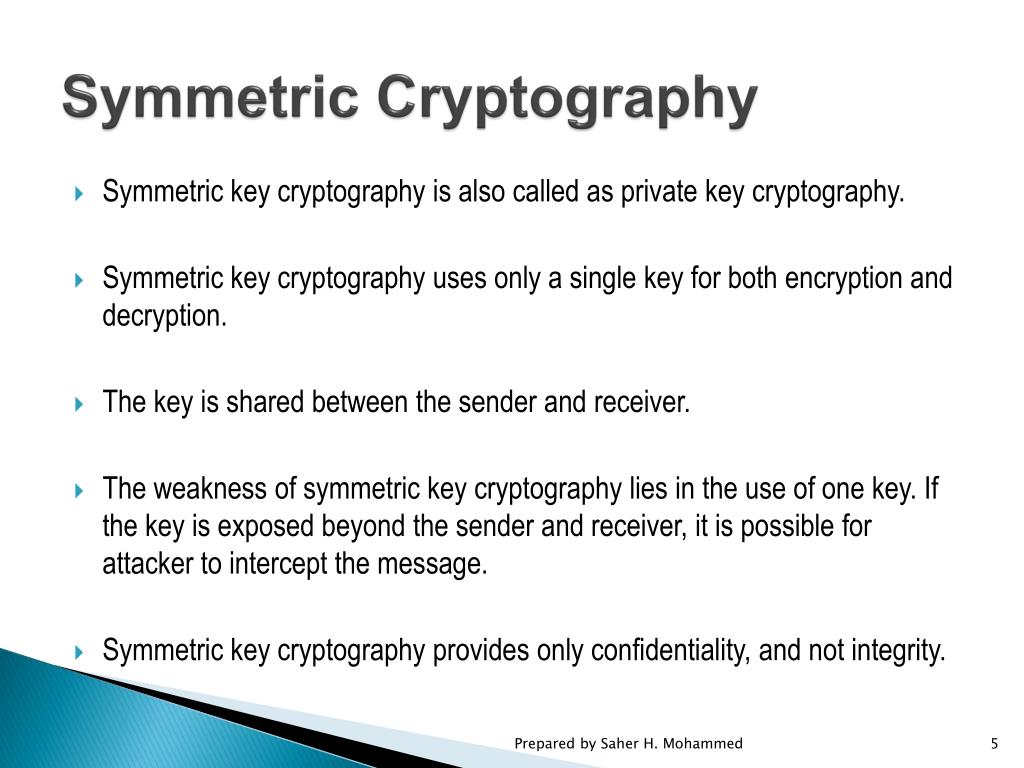
Honor legacy with our historical symmetric cryptography 2 – printrado gallery of extensive collections of timeless images. legacy-honoring highlighting photography, images, and pictures. perfect for historical documentation and education. Discover high-resolution symmetric cryptography 2 – printrado images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All symmetric cryptography 2 – printrado images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our symmetric cryptography 2 – printrado collection for various creative and professional projects. Diverse style options within the symmetric cryptography 2 – printrado collection suit various aesthetic preferences. Whether for commercial projects or personal use, our symmetric cryptography 2 – printrado collection delivers consistent excellence. Multiple resolution options ensure optimal performance across different platforms and applications. Reliable customer support ensures smooth experience throughout the symmetric cryptography 2 – printrado selection process. Time-saving browsing features help users locate ideal symmetric cryptography 2 – printrado images quickly. Cost-effective licensing makes professional symmetric cryptography 2 – printrado photography accessible to all budgets. Each image in our symmetric cryptography 2 – printrado gallery undergoes rigorous quality assessment before inclusion. Our symmetric cryptography 2 – printrado database continuously expands with fresh, relevant content from skilled photographers.




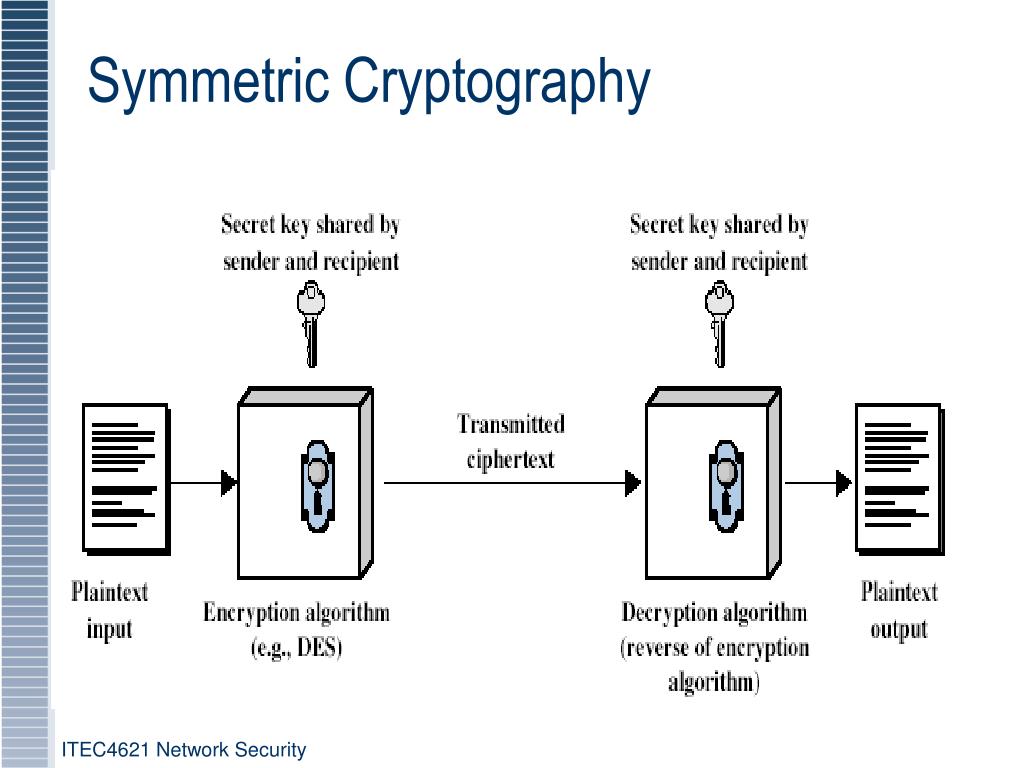








![How Symmetrical Cryptography Works [14]. | Download Scientific Diagram](https://www.researchgate.net/publication/336916852/figure/fig2/AS:819999648260097@1572514559101/How-Symmetrical-Cryptography-Works-14.png)








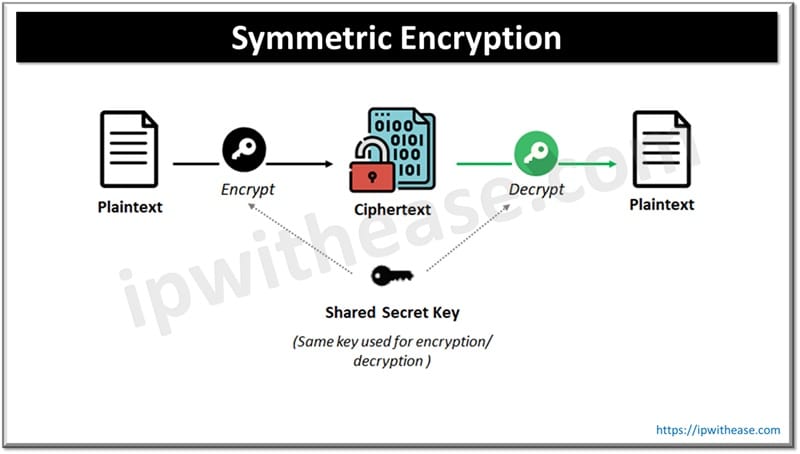




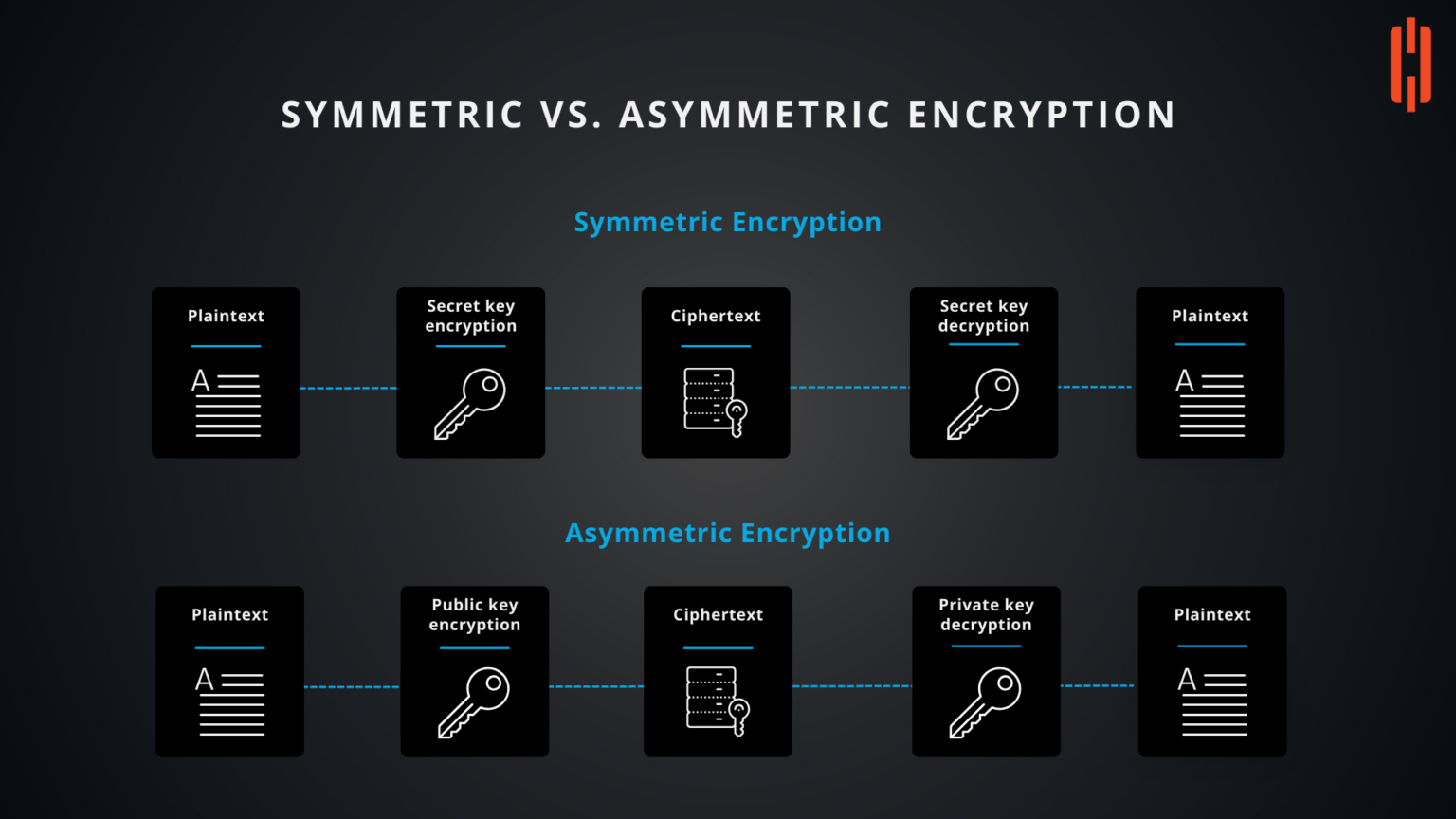
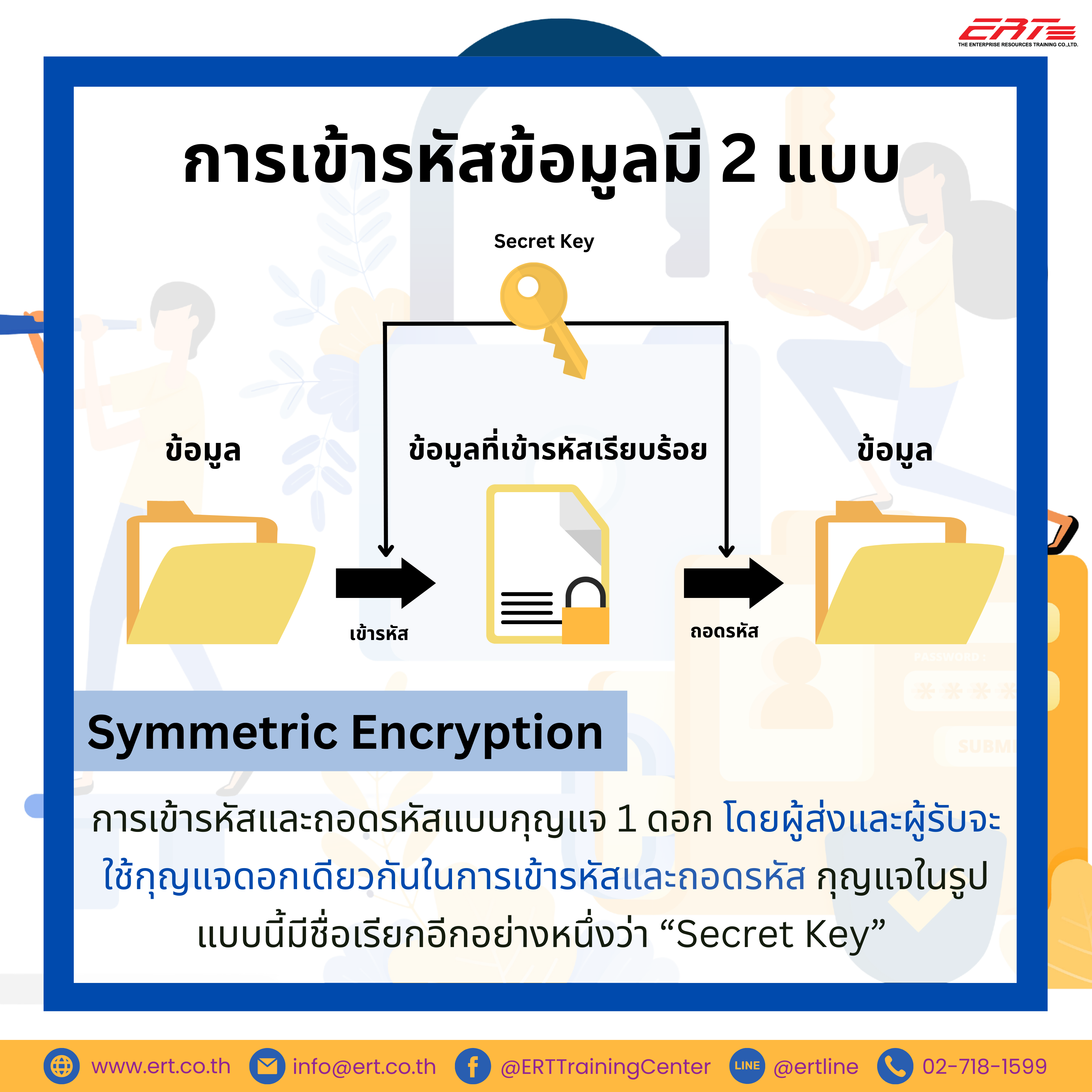


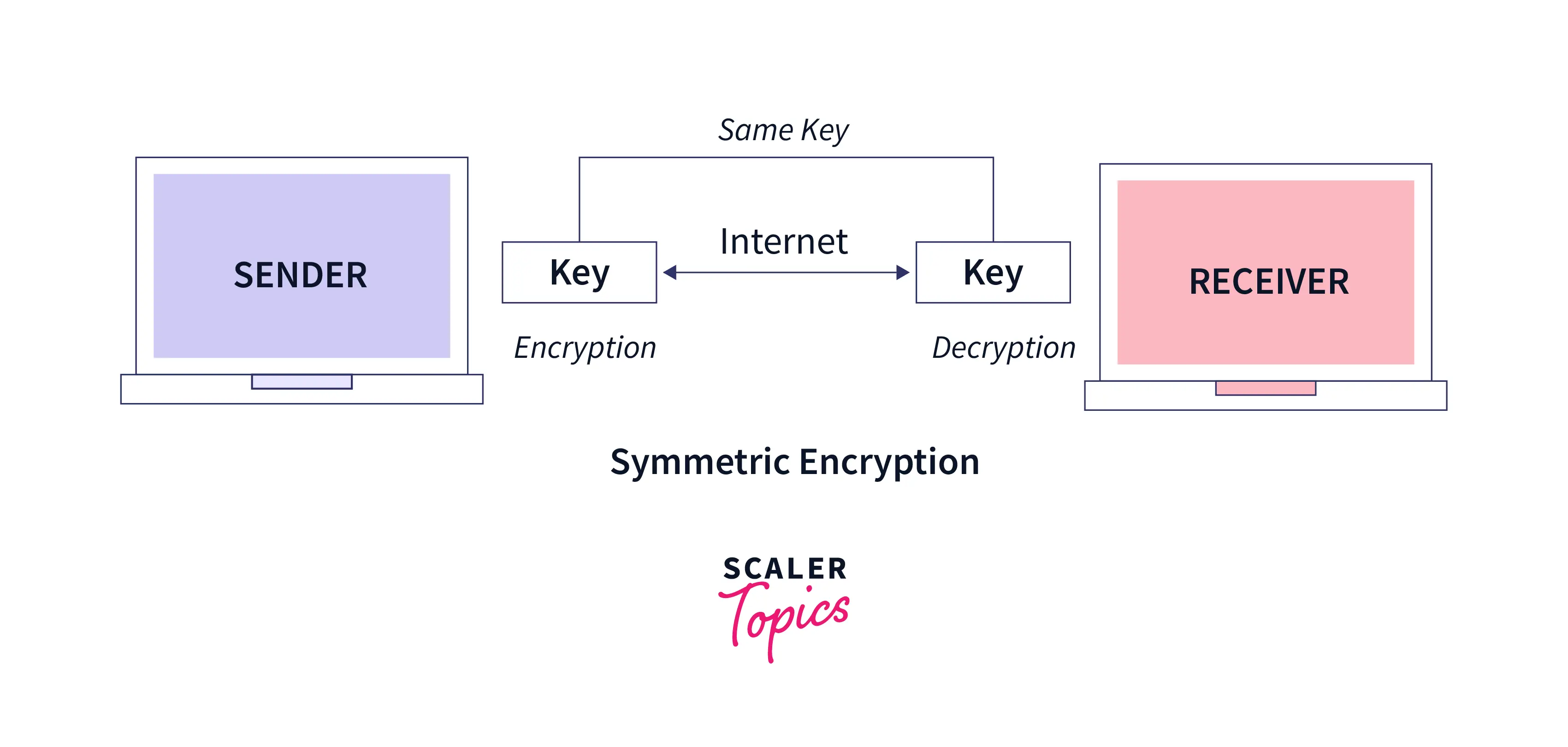


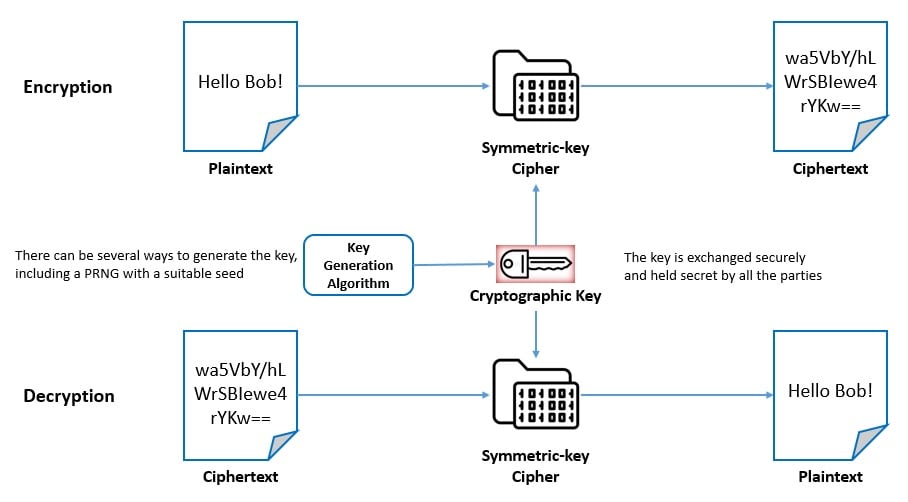









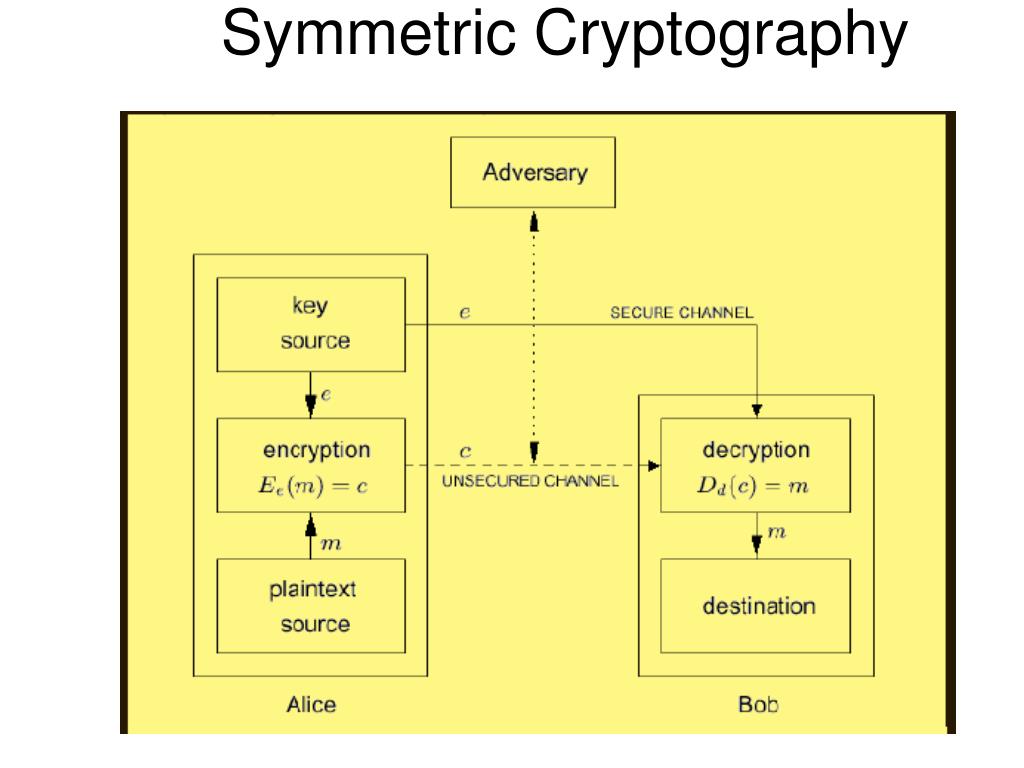

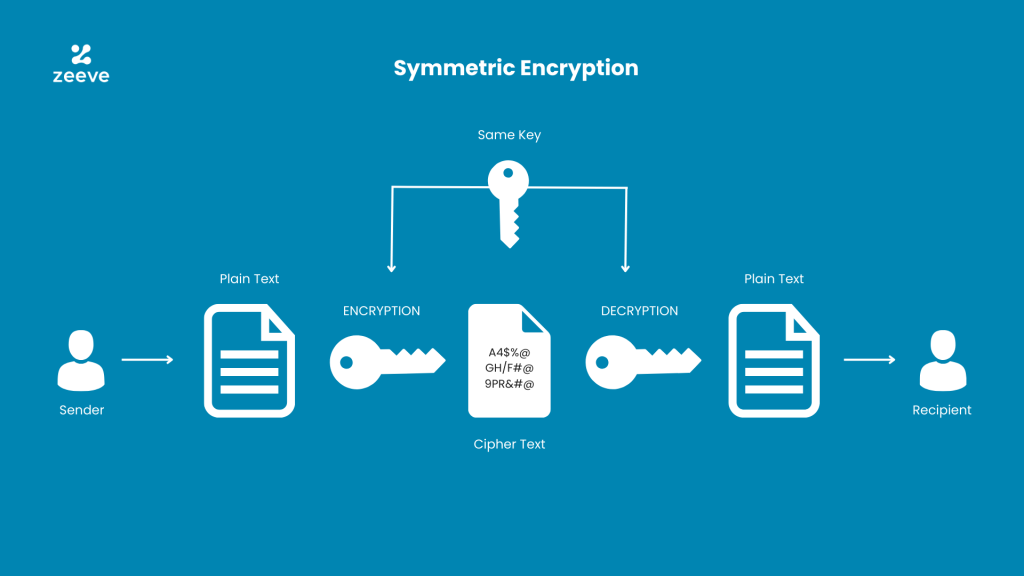
![Symmetric Encryption [5] | Download Scientific Diagram](https://www.researchgate.net/publication/341738673/figure/fig1/AS:11431281127319798@1678997683334/Symmetric-Encryption-5_Q640.jpg)
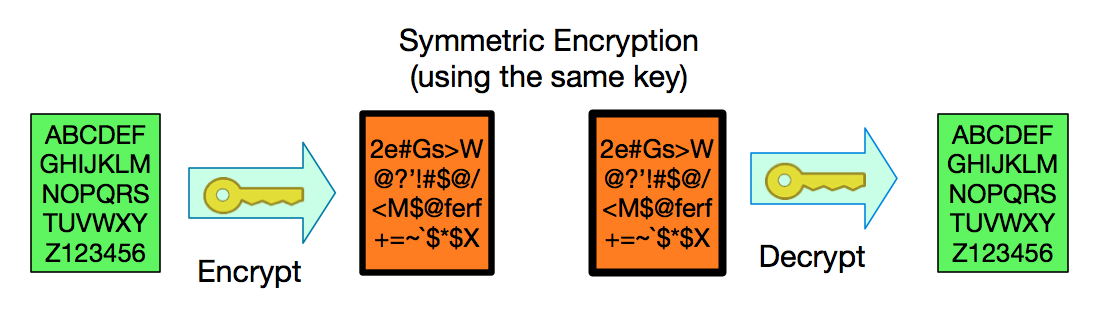

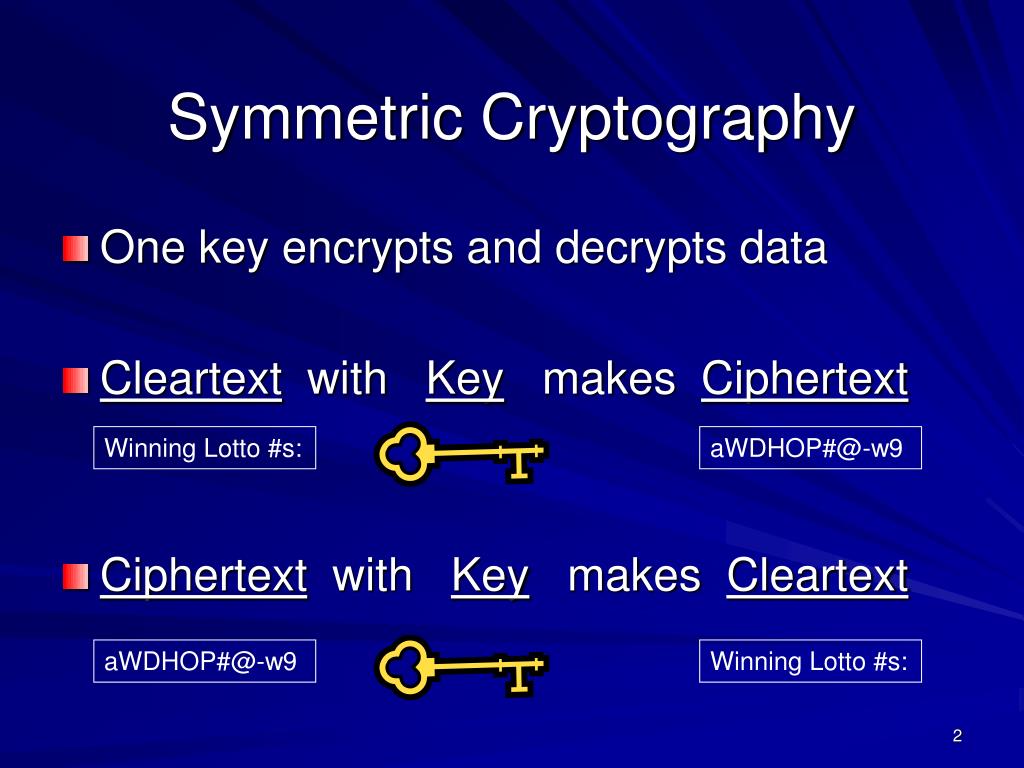


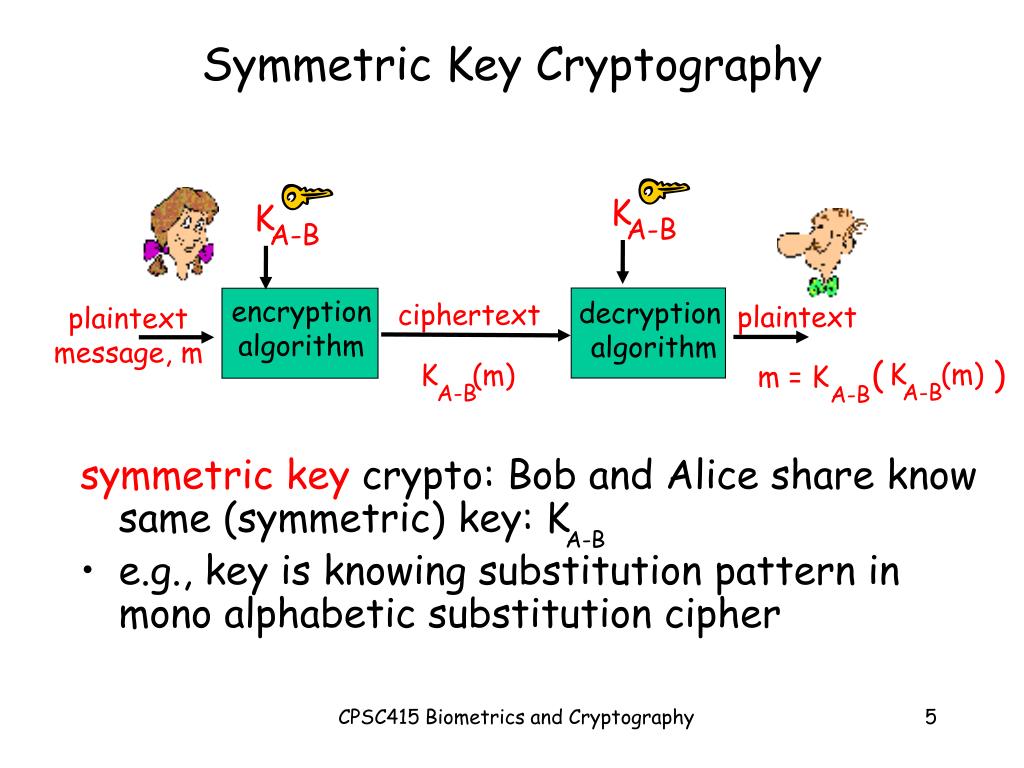
![Symmetric Cryptography System [7] | Download Scientific Diagram](https://www.researchgate.net/profile/Gerald-Arada/publication/354185308/figure/fig1/AS:1061779438321664@1630159353024/Symmetric-Cryptography-System-7.jpg)

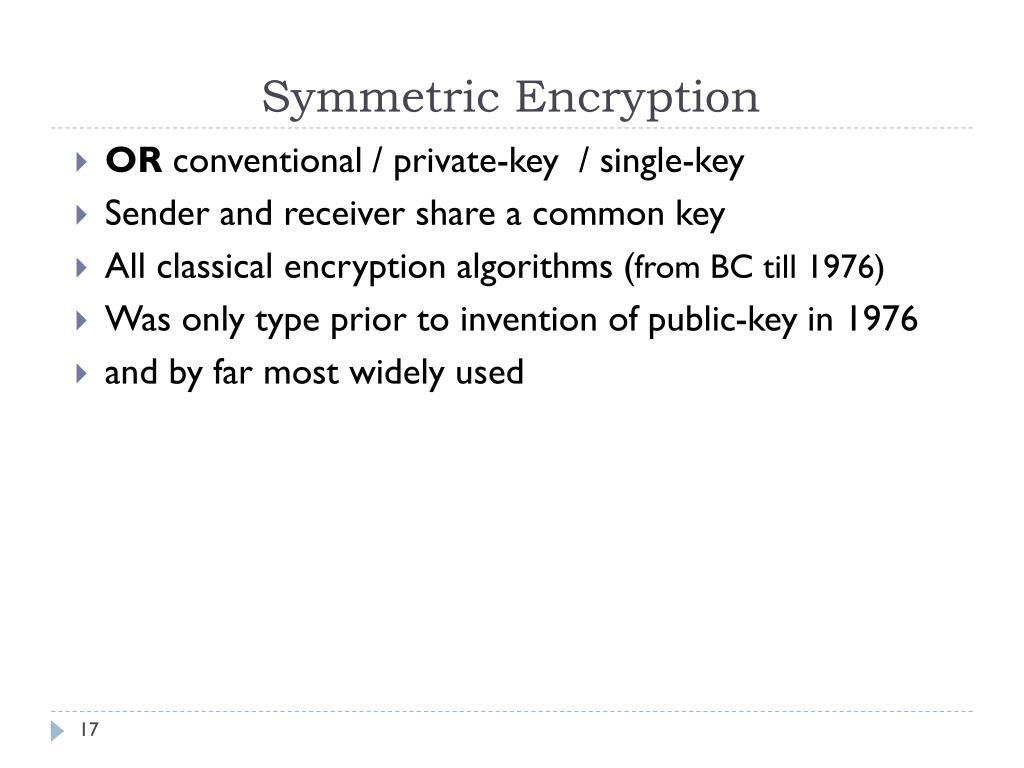























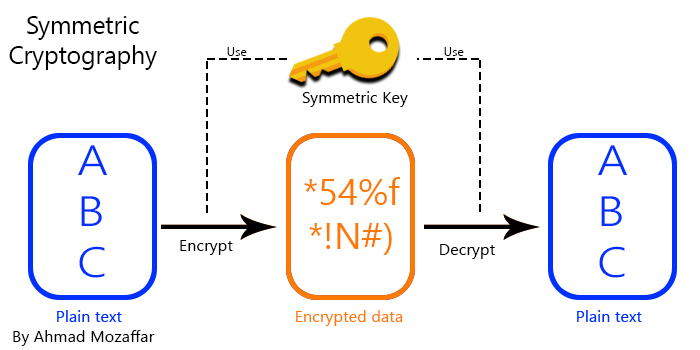
![Symmetric encryption [17] | Download Scientific Diagram](https://www.researchgate.net/publication/343025050/figure/fig1/AS:914594046423042@1595067621685/Symmetric-encryption-17.png)