Explore the world with our remarkable travel block cipher modes of operation and cmac for authentication | ppt collection of substantial collections of wanderlust images. adventurously capturing photography, images, and pictures. perfect for travel marketing and tourism. Each block cipher modes of operation and cmac for authentication | ppt image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All block cipher modes of operation and cmac for authentication | ppt images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect block cipher modes of operation and cmac for authentication | ppt images to enhance your visual communication needs. Whether for commercial projects or personal use, our block cipher modes of operation and cmac for authentication | ppt collection delivers consistent excellence. The block cipher modes of operation and cmac for authentication | ppt collection represents years of careful curation and professional standards. Instant download capabilities enable immediate access to chosen block cipher modes of operation and cmac for authentication | ppt images. Cost-effective licensing makes professional block cipher modes of operation and cmac for authentication | ppt photography accessible to all budgets.
































.jpg)





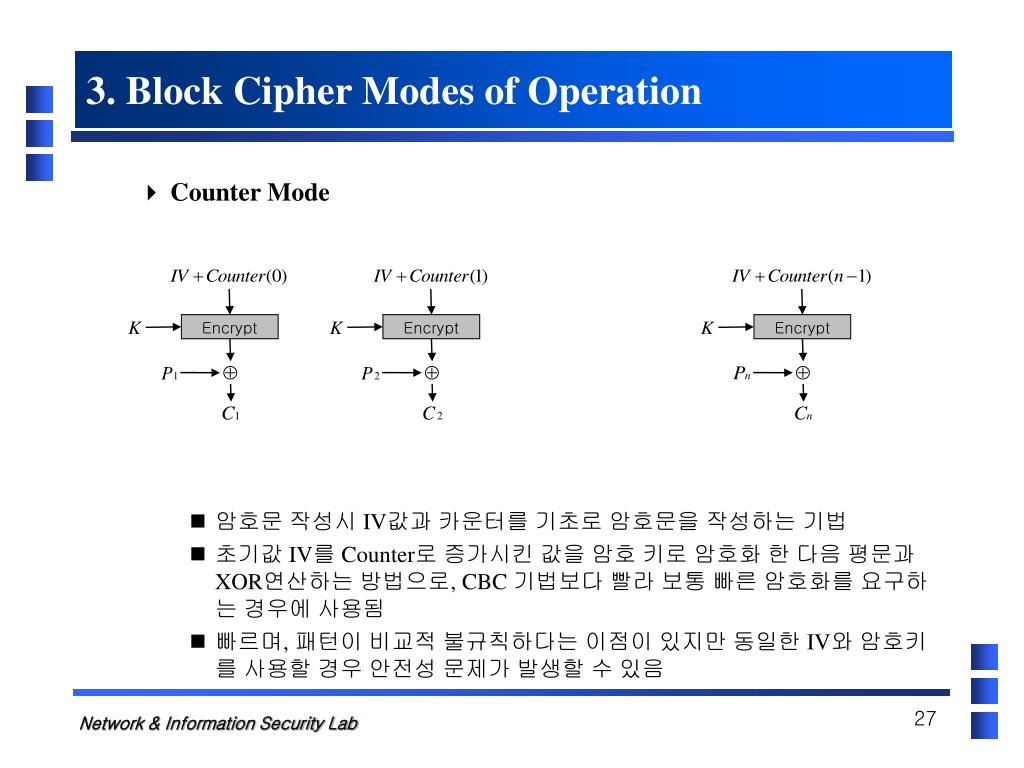

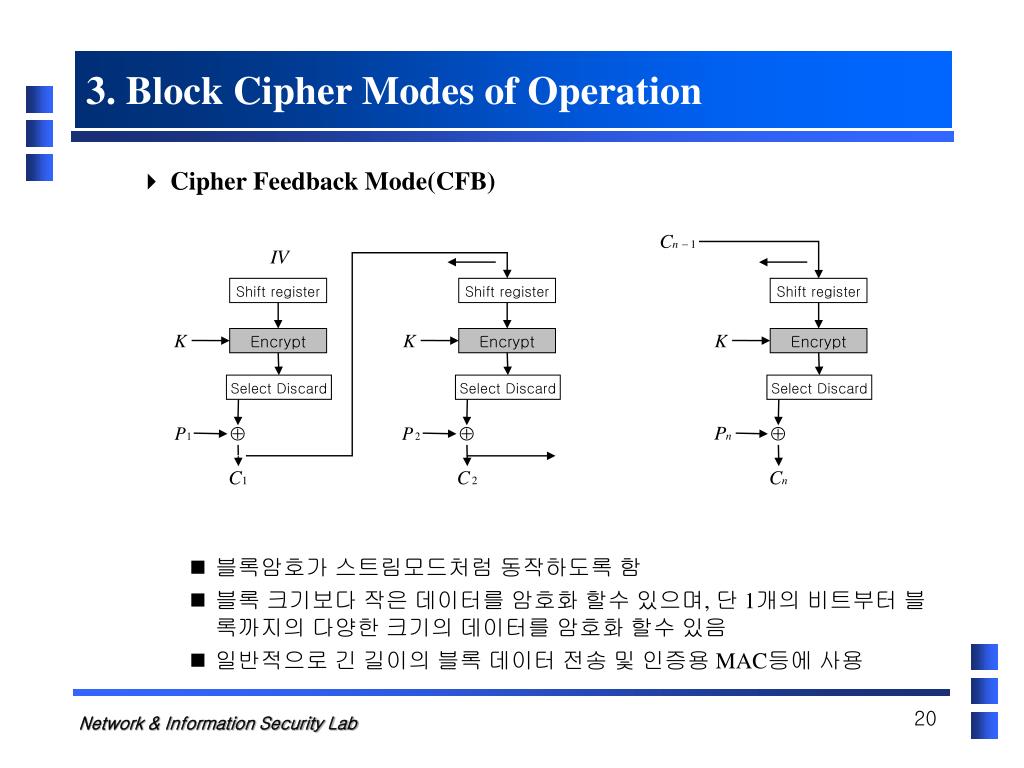

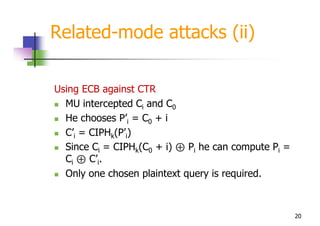
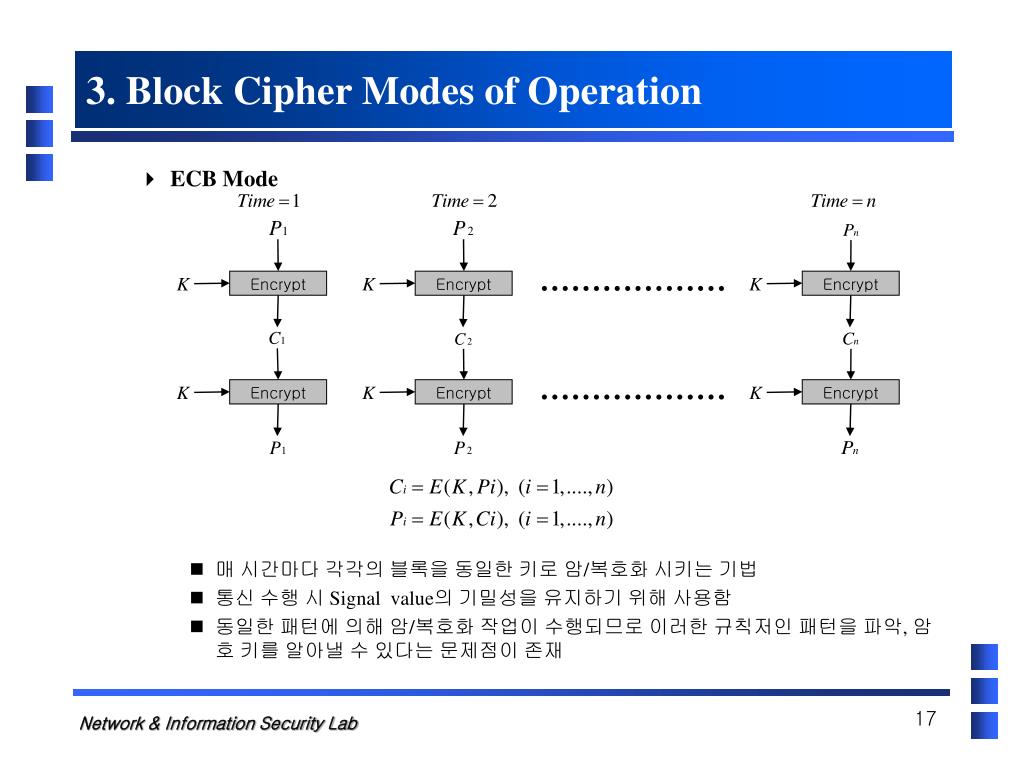
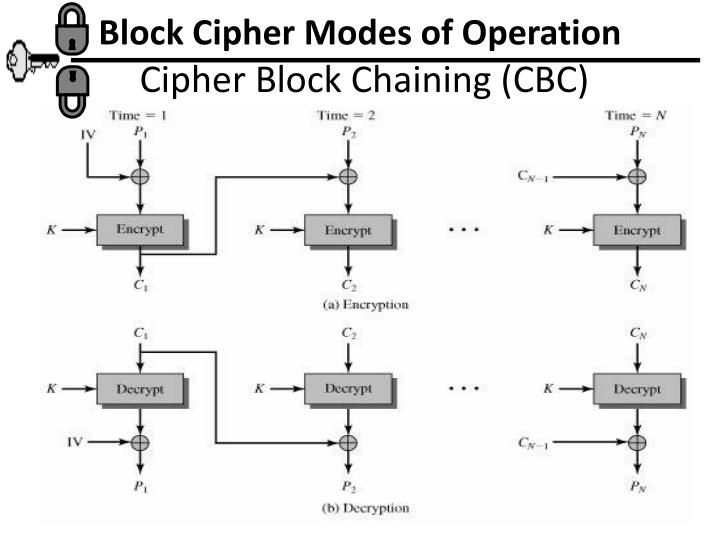
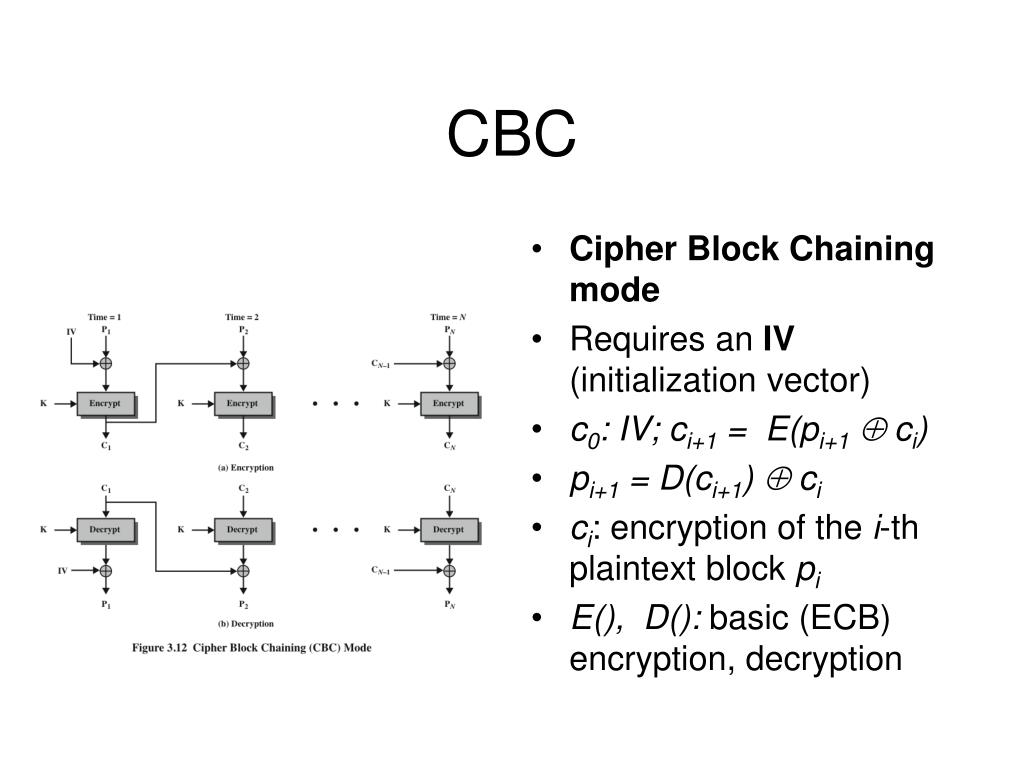
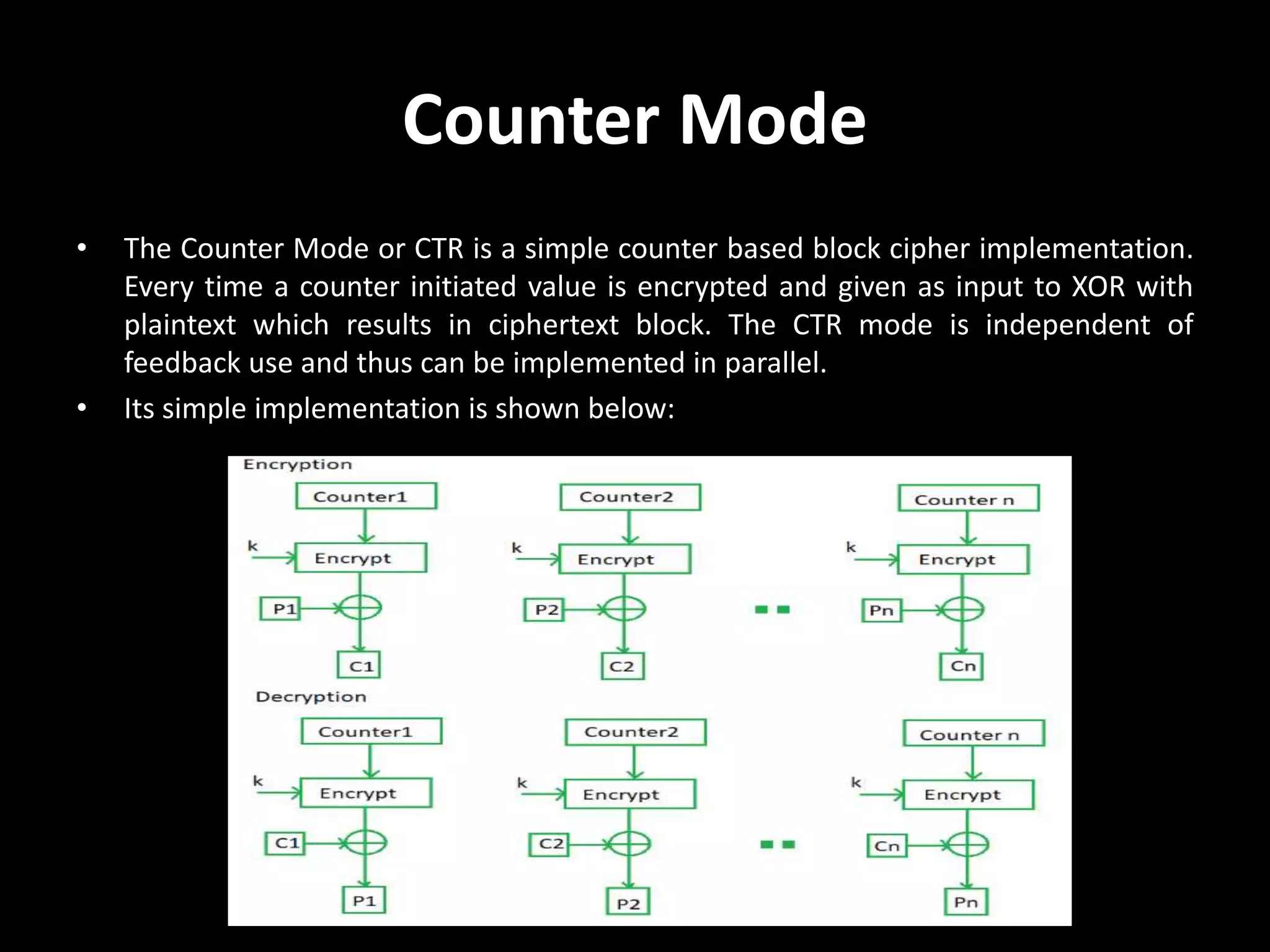
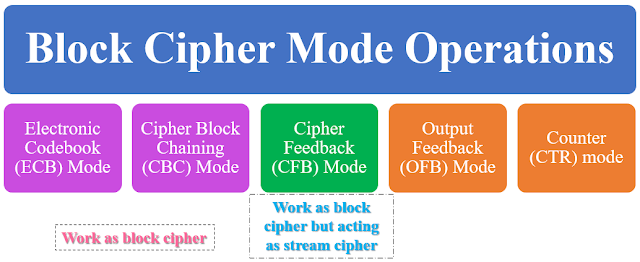





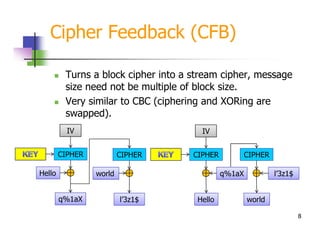


.jpg)


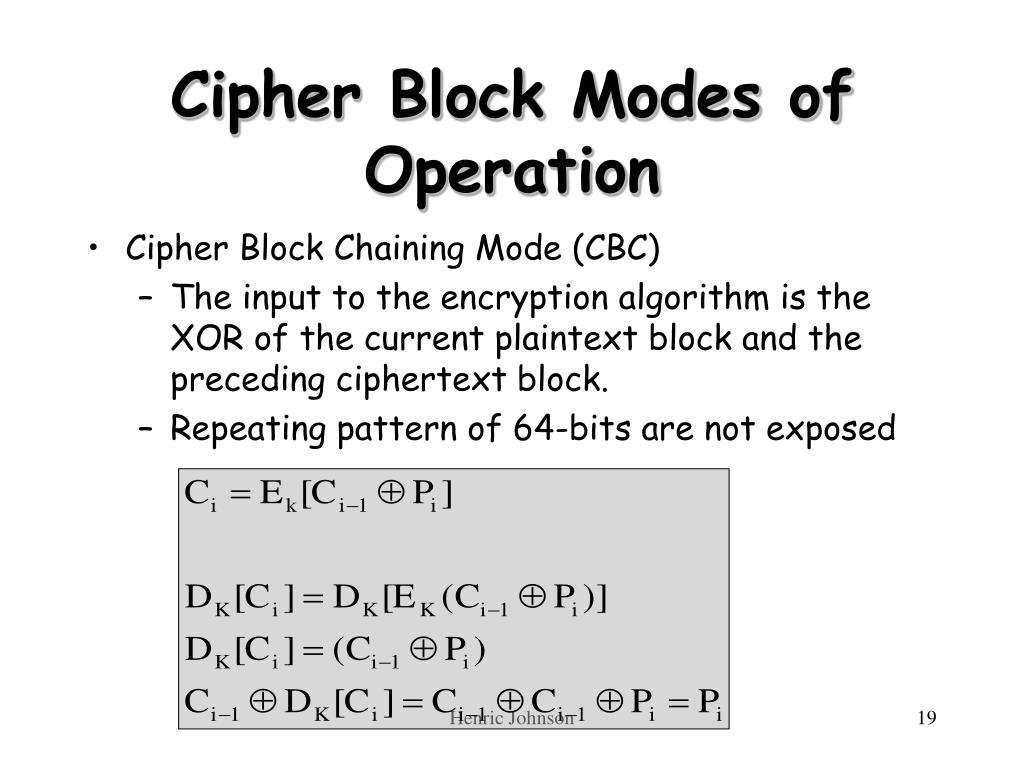

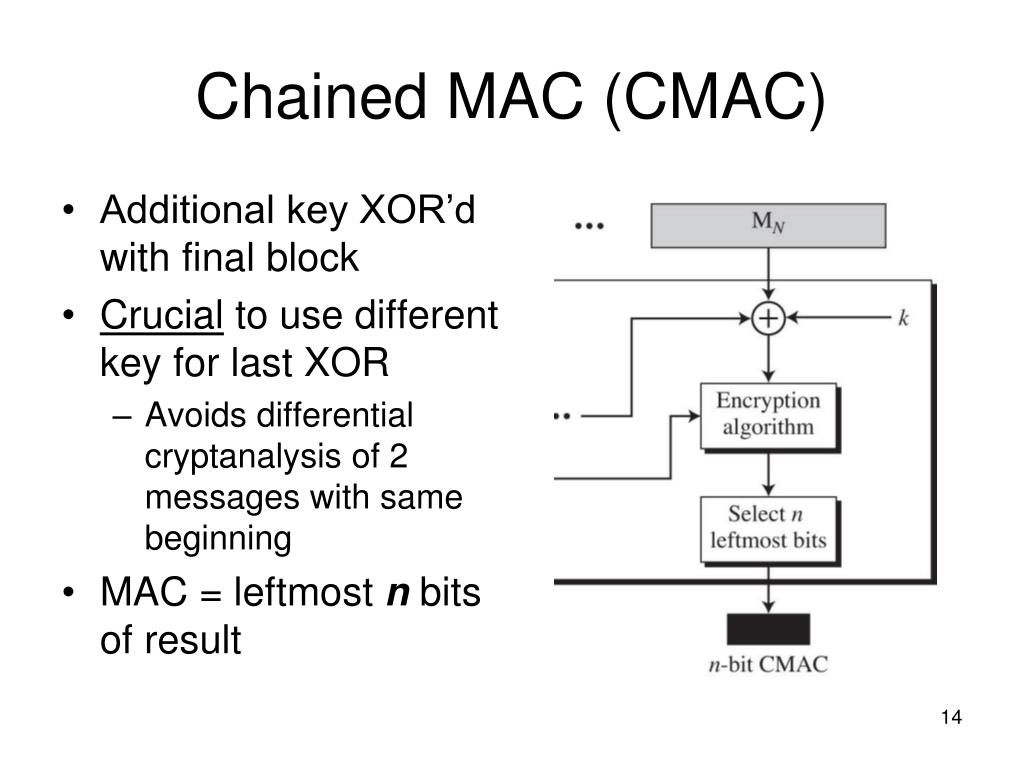
+Encryption:.jpg)

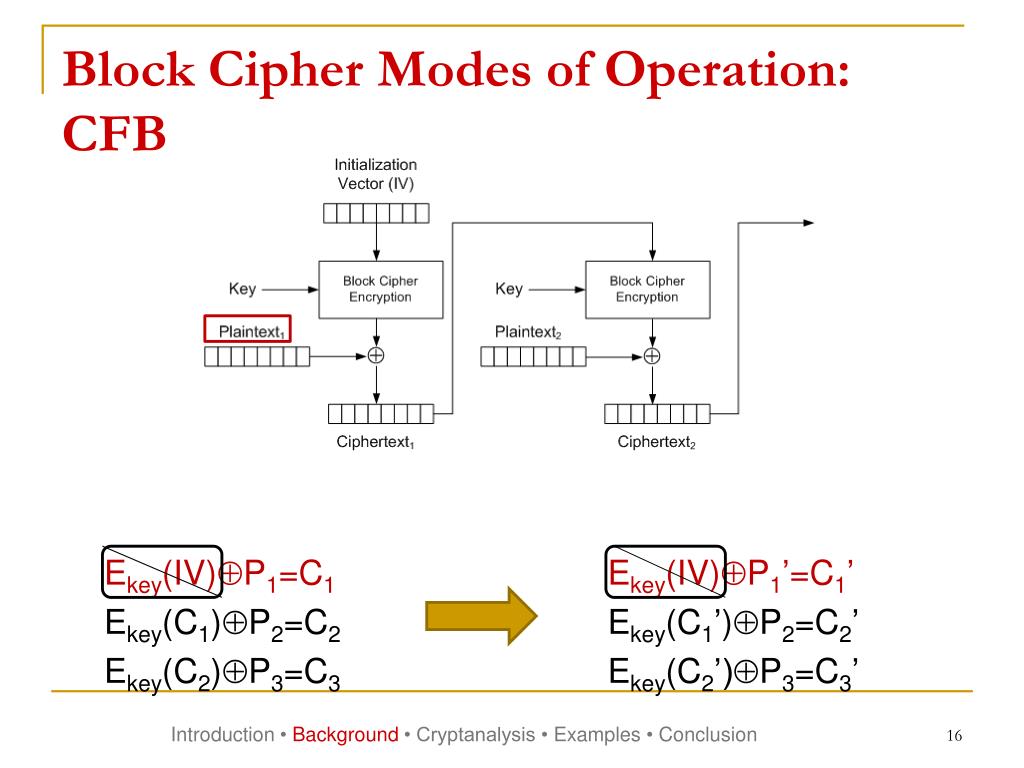
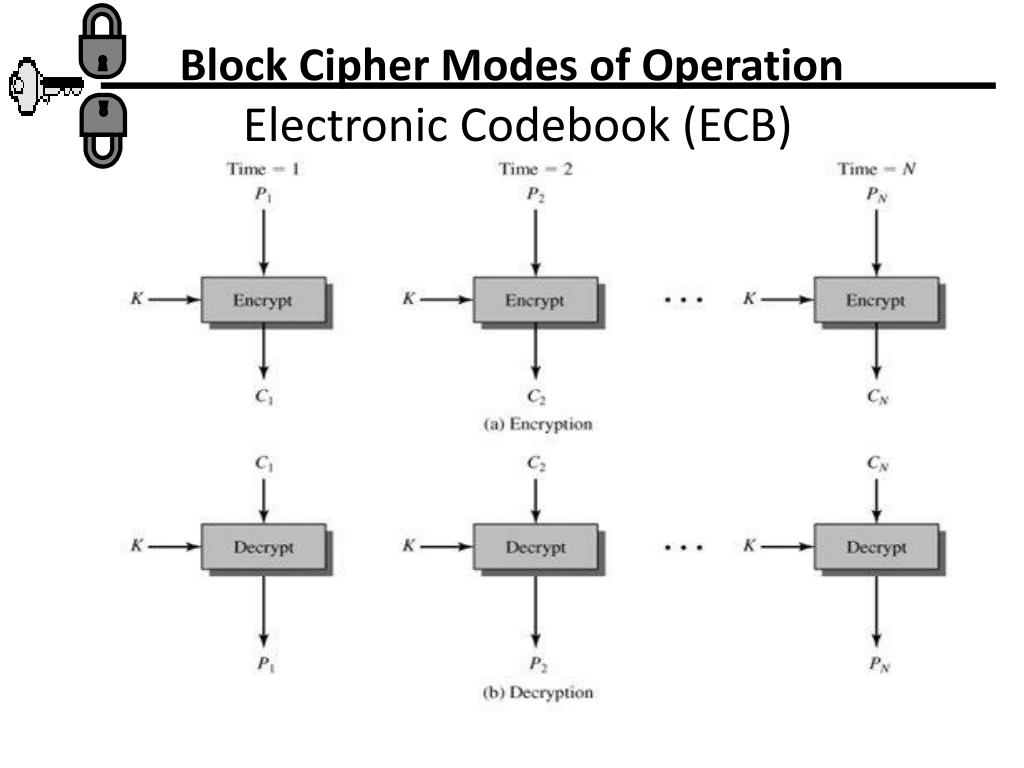






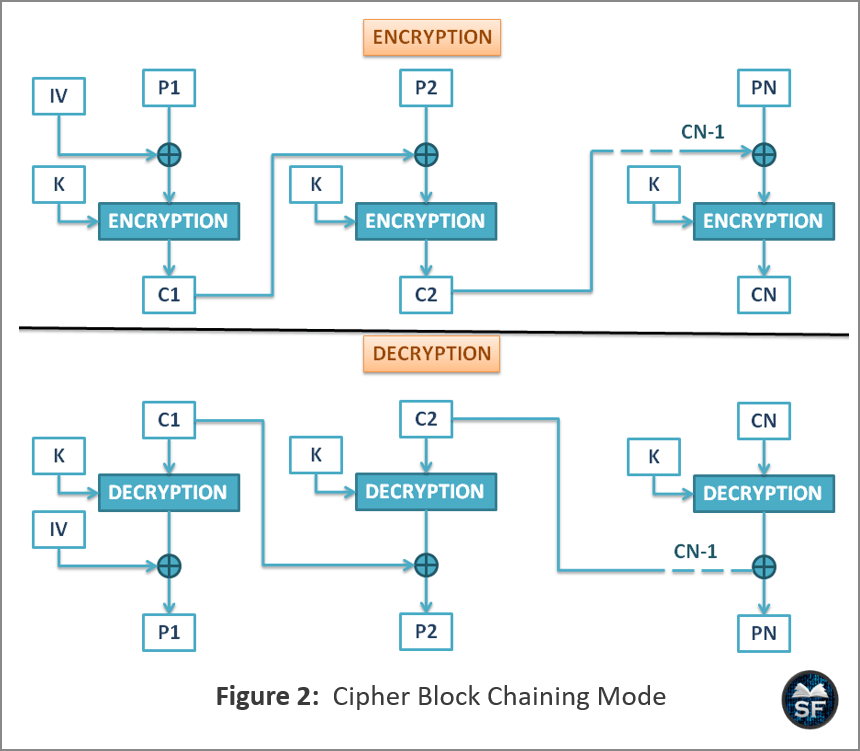
![Cipher Block Chaining Mode of Operation [8] | Download Scientific Diagram](https://www.researchgate.net/profile/Bazara-Barry/publication/280305957/figure/fig1/AS:645369771851776@1530879552178/Electronic-Codebook-Mode-of-Operation-8_Q320.jpg)


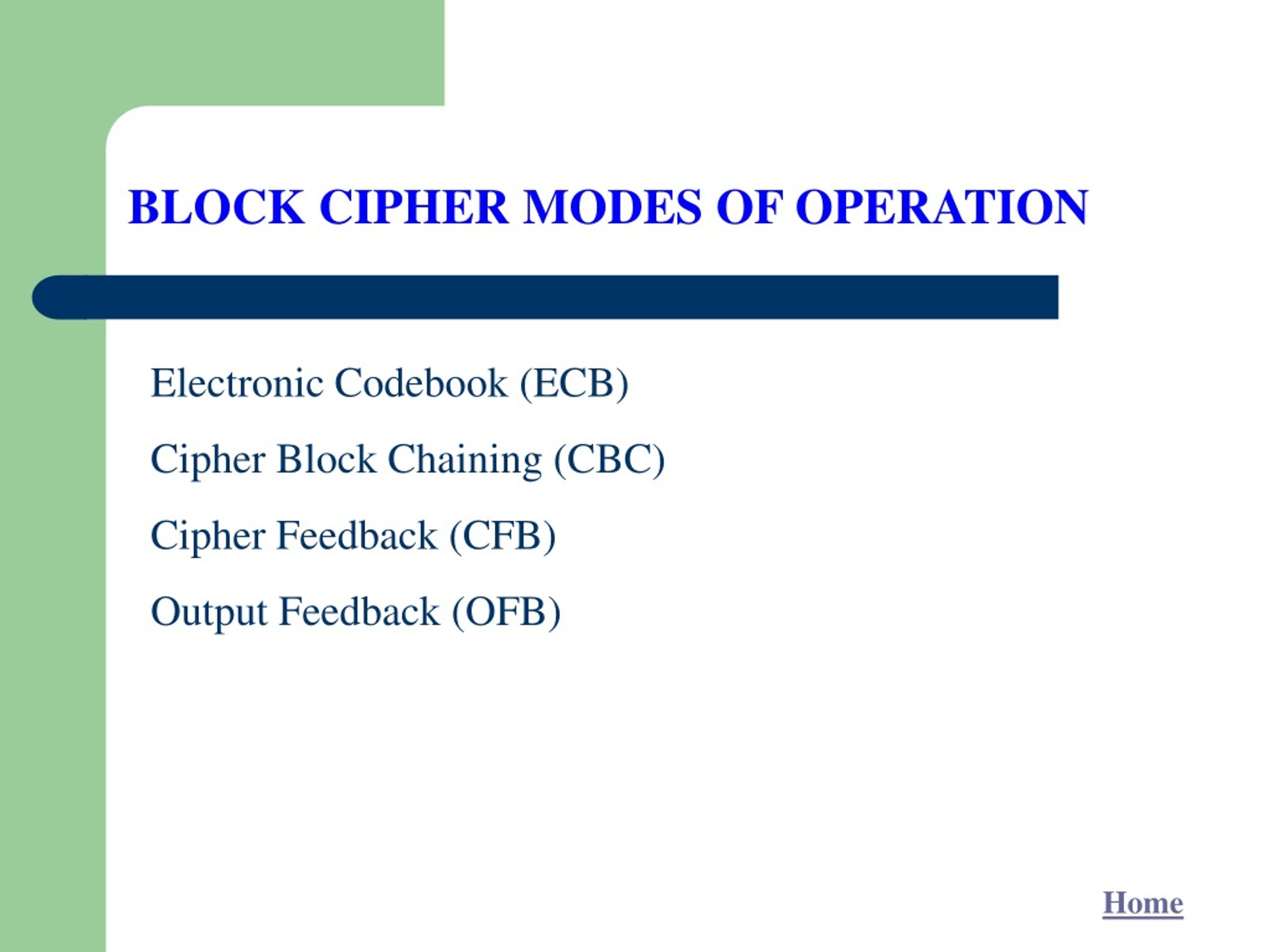
+is+a+widely+used+mode.jpg)