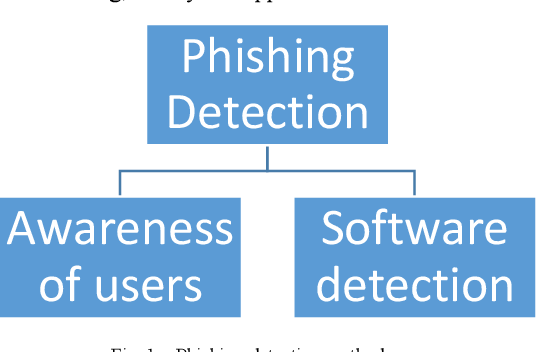
Capture truth through extensive collections of documentary-style an overview of phishing detection approaches | download scientific diagram photographs. authentically documenting photography, images, and pictures. perfect for journalism and news reporting. Our an overview of phishing detection approaches | download scientific diagram collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All an overview of phishing detection approaches | download scientific diagram images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our an overview of phishing detection approaches | download scientific diagram gallery offers diverse visual resources to bring your ideas to life. The an overview of phishing detection approaches | download scientific diagram collection represents years of careful curation and professional standards. Regular updates keep the an overview of phishing detection approaches | download scientific diagram collection current with contemporary trends and styles. Multiple resolution options ensure optimal performance across different platforms and applications. Reliable customer support ensures smooth experience throughout the an overview of phishing detection approaches | download scientific diagram selection process. Instant download capabilities enable immediate access to chosen an overview of phishing detection approaches | download scientific diagram images.



![Phishing detection models proposed by Sahingoz et al. [18] | Download ...](https://www.researchgate.net/publication/349832983/figure/fig1/AS:11431281085771572@1663899206296/Phishing-detection-models-proposed-by-Sahingoz-et-al-18_Q320.jpg)








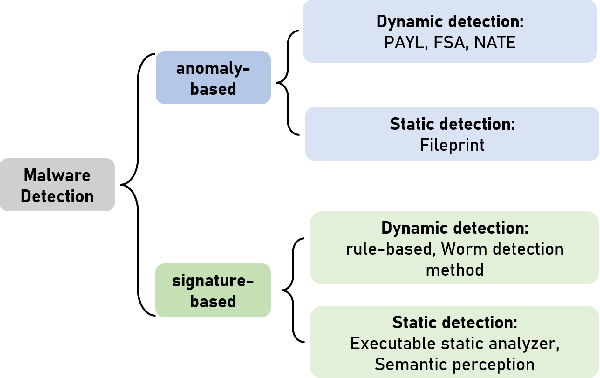
![Malware detection techniques [25]. | Download Scientific Diagram](https://www.researchgate.net/publication/354060018/figure/fig1/AS:1059608101654529@1629641666928/Malware-detection-techniques-25_Q320.jpg)





![Life Cycle Model for Big Data Security, adapted from [18]. | Download ...](https://www.researchgate.net/publication/333251775/figure/fig1/AS:873043773624320@1585161264526/Life-Cycle-Model-for-Big-Data-Security-adapted-from-18_Q320.jpg)




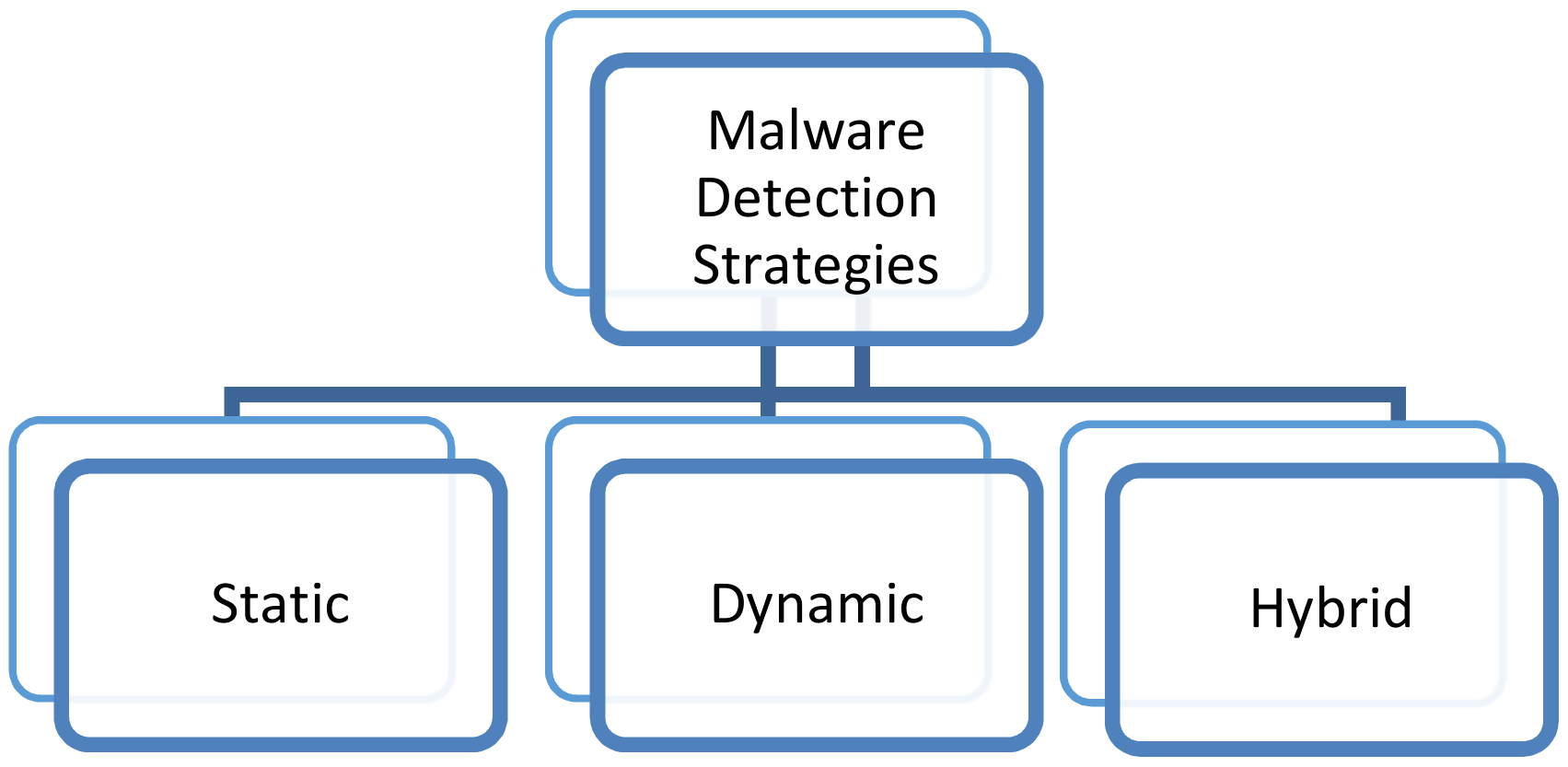





![Images represent various malware families [33]. | Download Scientific ...](https://www.researchgate.net/profile/Hadis-Ghanei-2/publication/351426688/figure/fig1/AS:1021422084317194@1620537410307/Malware-detection_Q320.jpg)