
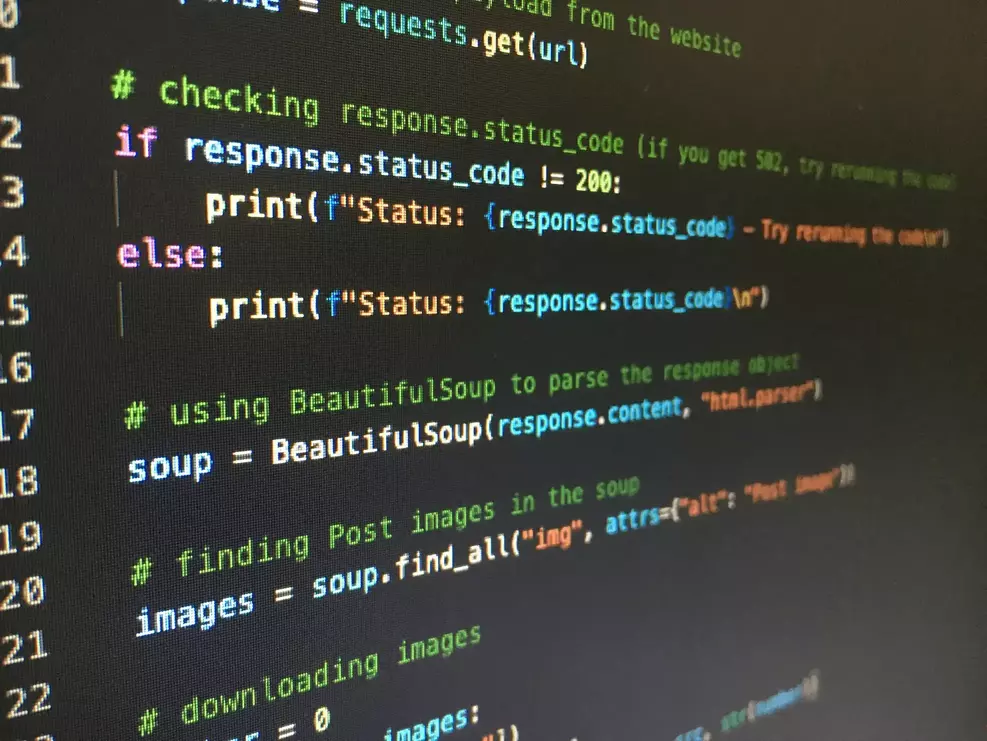
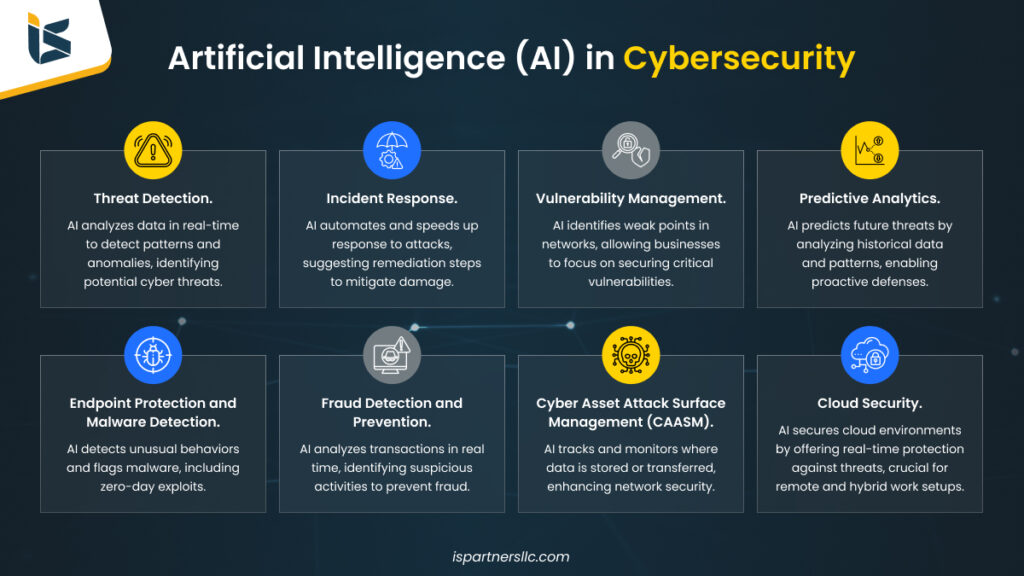
Create excitement through vast arrays of show-focused languages used in… cybersecurity: *python *php *javascript *sql *c photographs. entertainingly showcasing photography, images, and pictures. ideal for show business and media content. Browse our premium languages used in… cybersecurity: *python *php *javascript *sql *c gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All languages used in… cybersecurity: *python *php *javascript *sql *c images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our languages used in… cybersecurity: *python *php *javascript *sql *c gallery offers diverse visual resources to bring your ideas to life. Reliable customer support ensures smooth experience throughout the languages used in… cybersecurity: *python *php *javascript *sql *c selection process. The languages used in… cybersecurity: *python *php *javascript *sql *c collection represents years of careful curation and professional standards. Comprehensive tagging systems facilitate quick discovery of relevant languages used in… cybersecurity: *python *php *javascript *sql *c content. Professional licensing options accommodate both commercial and educational usage requirements. Whether for commercial projects or personal use, our languages used in… cybersecurity: *python *php *javascript *sql *c collection delivers consistent excellence.

























![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/best-programming-languages-for-cybersecurity.jpg)



![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/php.jpg)




![8 Best Programming Languages for Cybersecurity [2023 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/functioning-of-an-sql-injection-800x641.jpg)
![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/jupyter-notebook-ransomware-attack.jpg)







![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/xss.jpg)




![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/c--380x282.jpg)
![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/html-attacks.jpg)

![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/assembly-language.jpg)




![8 Best Programming Languages for Cybersecurity [2023 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/cryptography-768x368.jpg)


































![8 Best Programming Languages for Cybersecurity [2025 Guide]](https://www.springboard.com/blog/wp-content/uploads/2022/11/sql.jpg)





