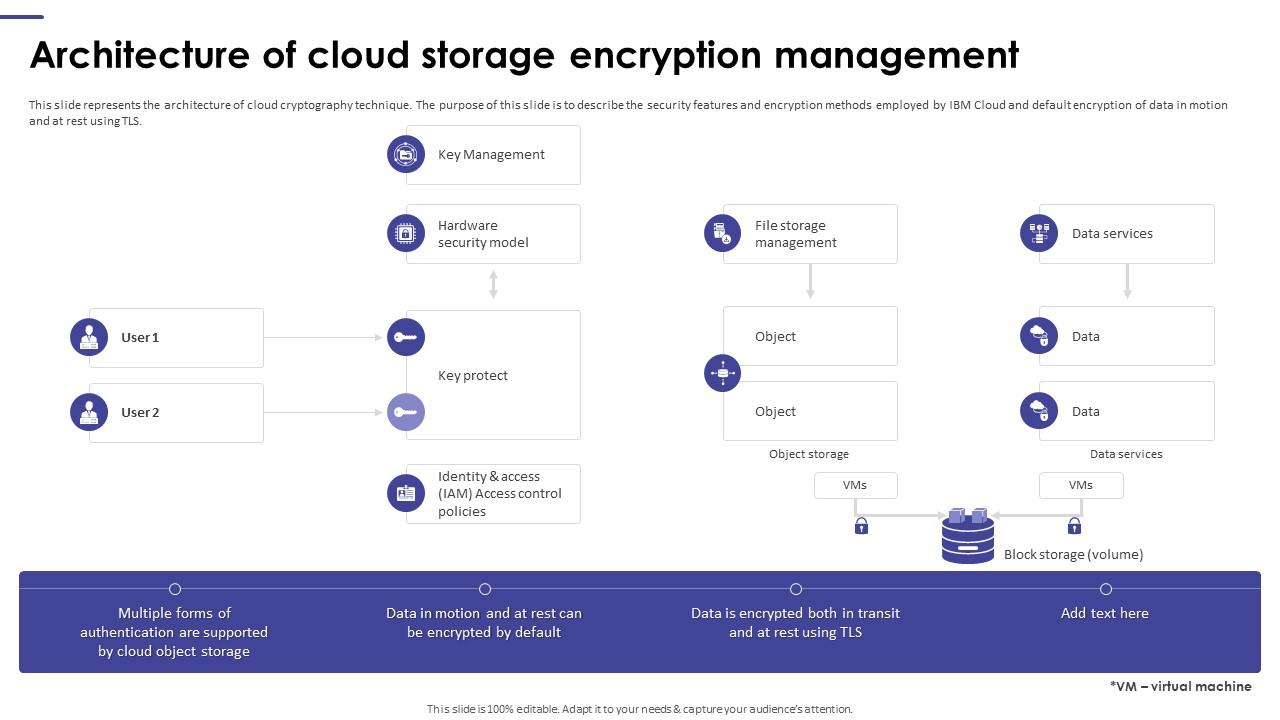
Utilize our extensive image encryption decryption using the proposed architecture of aes resource library containing countless high-quality images. captured using advanced photographic techniques and professional equipment. supporting commercial, educational, and research applications. Browse our premium image encryption decryption using the proposed architecture of aes gallery featuring professionally curated photographs. Perfect for marketing materials, corporate presentations, advertising campaigns, and professional publications All image encryption decryption using the proposed architecture of aes images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Professional photographers and designers trust our image encryption decryption using the proposed architecture of aes images for their consistent quality and technical excellence. The image encryption decryption using the proposed architecture of aes archive serves professionals, educators, and creatives across diverse industries. Regular updates keep the image encryption decryption using the proposed architecture of aes collection current with contemporary trends and styles. Whether for commercial projects or personal use, our image encryption decryption using the proposed architecture of aes collection delivers consistent excellence. Diverse style options within the image encryption decryption using the proposed architecture of aes collection suit various aesthetic preferences. Professional licensing options accommodate both commercial and educational usage requirements.










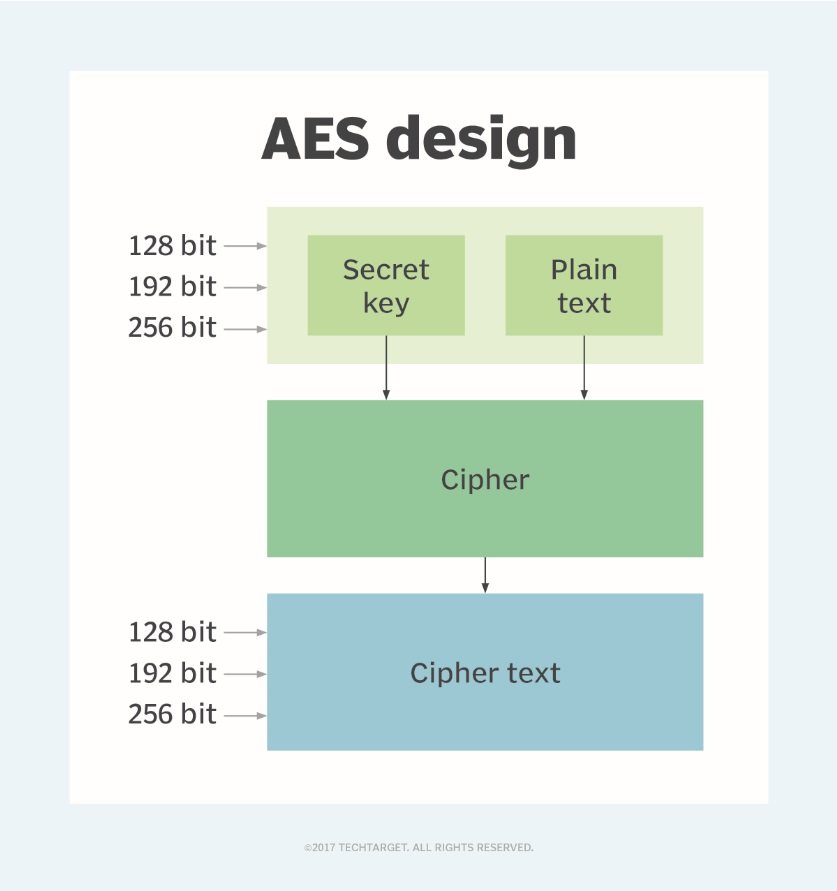

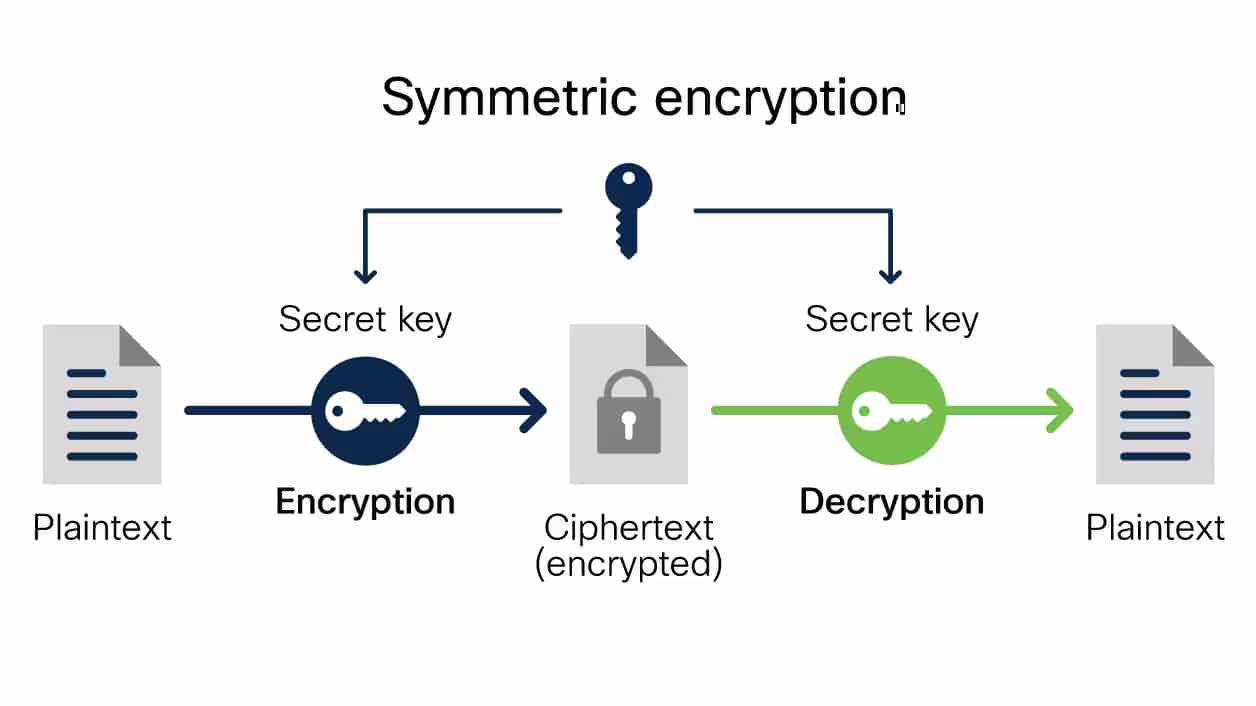


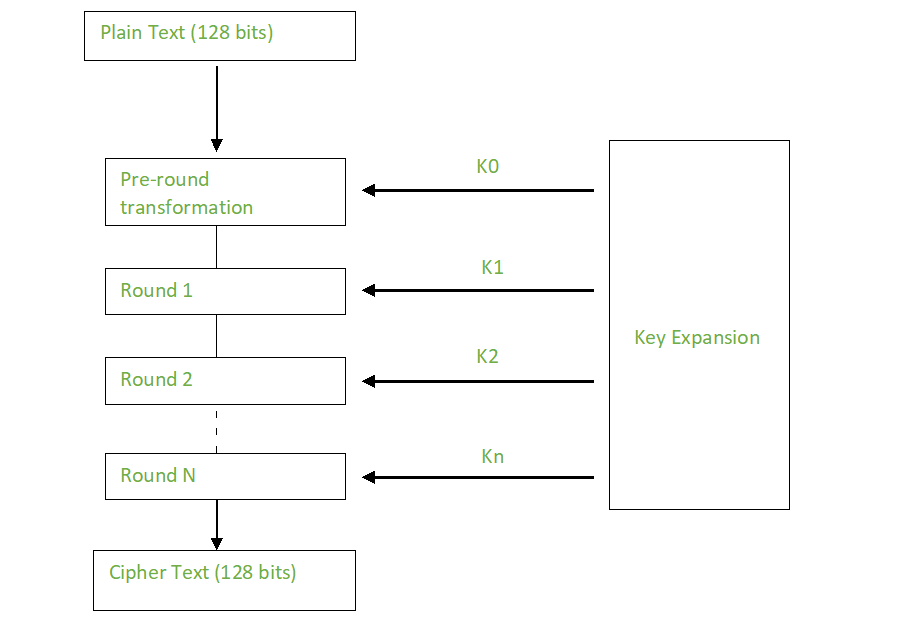
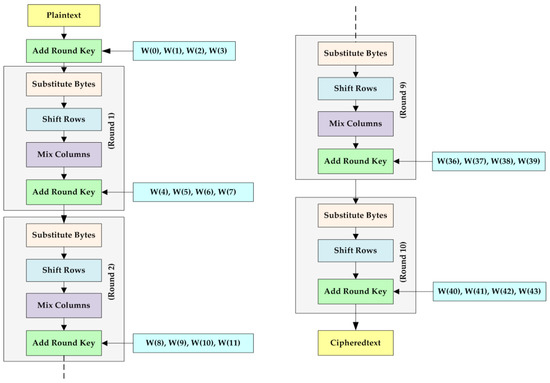
![What is AES Encryption and How it Works? [Detailed Guide]](https://cheapsslweb.com/blog/wp-content/uploads/2022/12/aes-algorithm-working-300x194.jpg)


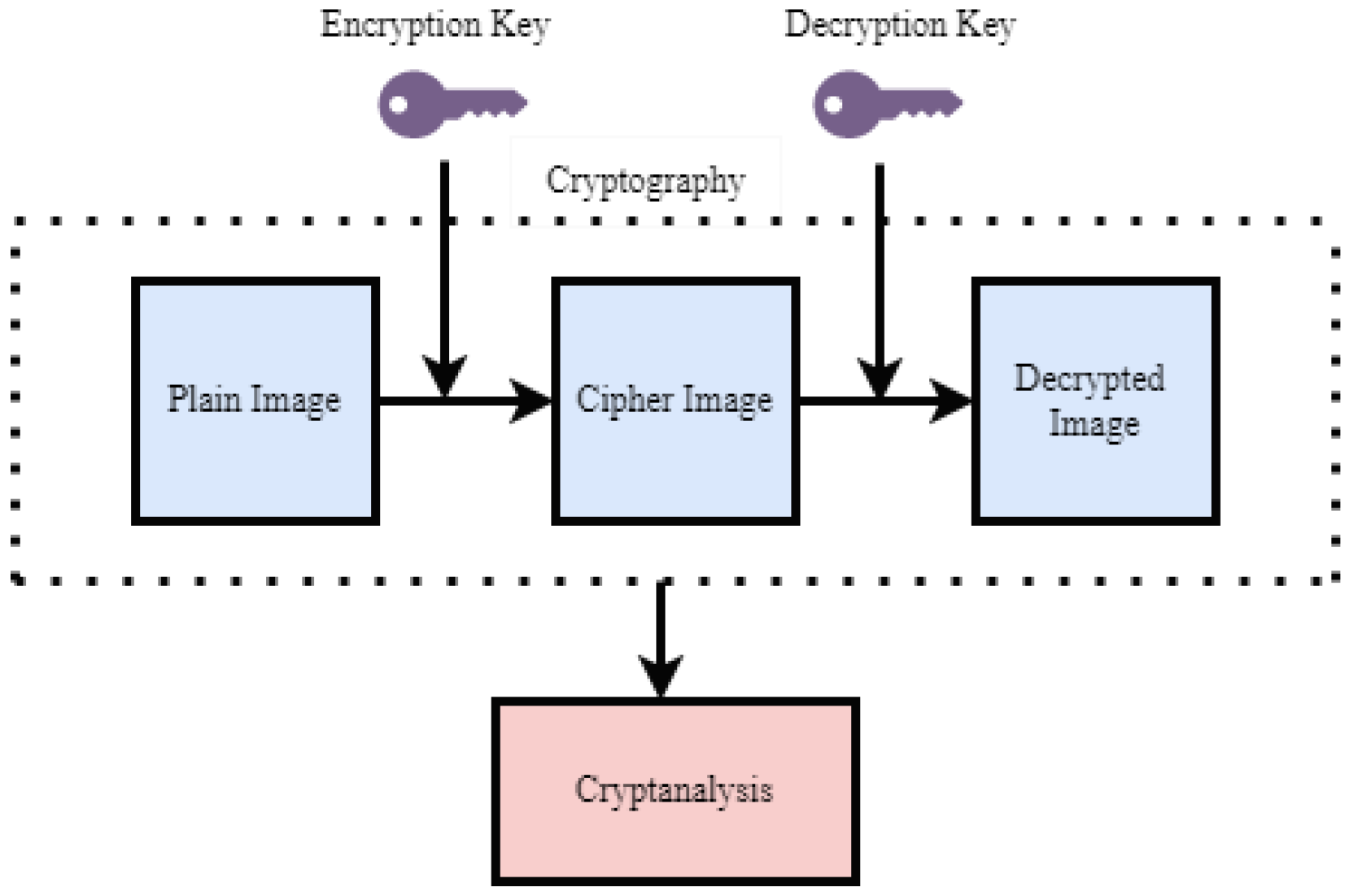














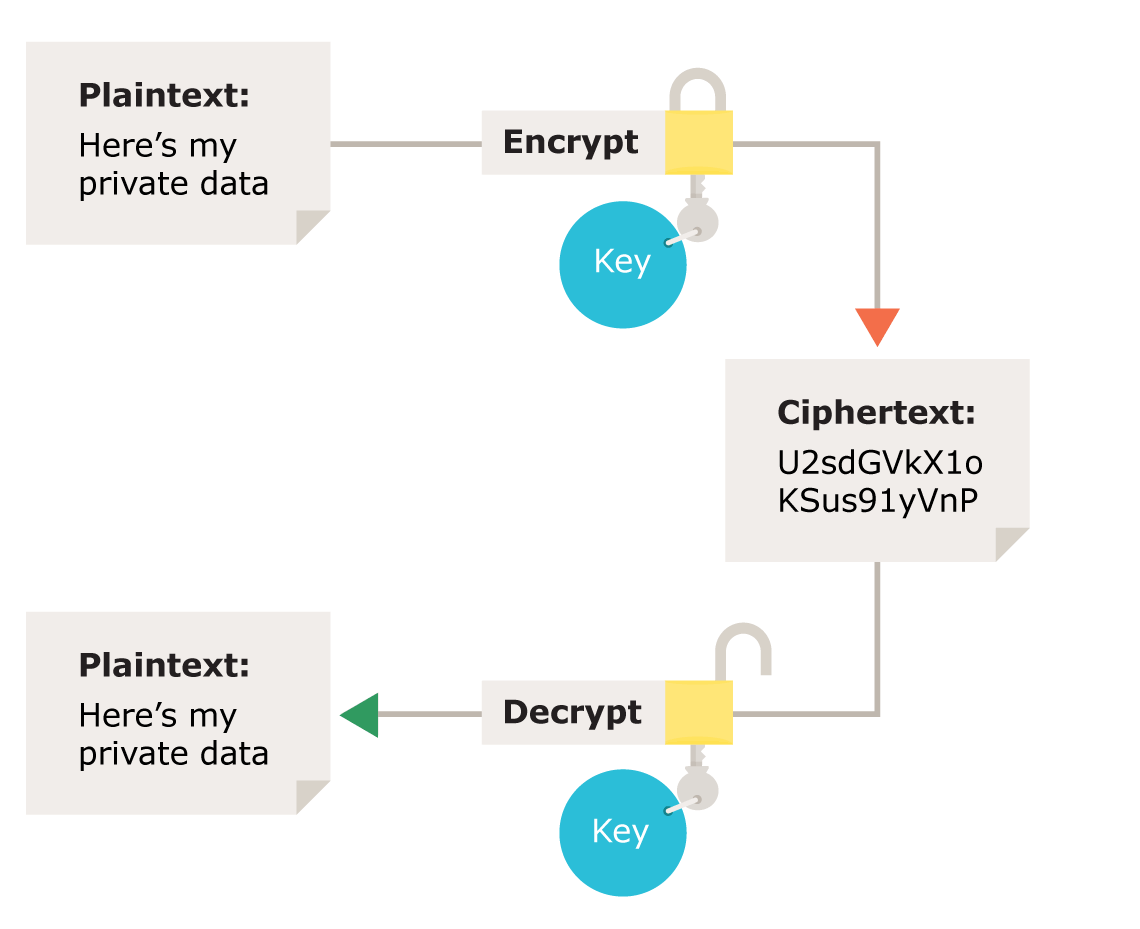
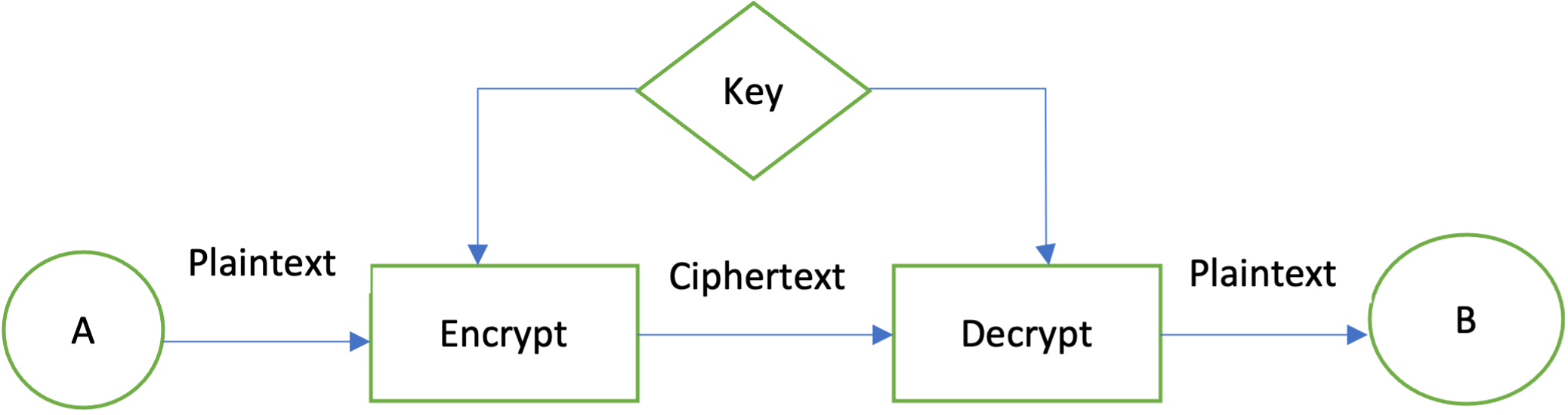
![Process of encryption and decryption [6]. | Download Scientific Diagram](https://www.researchgate.net/profile/Muhammad-Ehsan-Rana/publication/354888594/figure/download/fig1/AS:1086795429220352@1636123630648/Process-of-encryption-and-decryption-6.jpg)






















![AES Encryption and Decryption [5]. | Download Scientific Diagram](https://www.researchgate.net/publication/333048037/figure/fig2/AS:758084523790336@1557752843611/AES-Encryption-and-Decryption-5.png)


![AES-ECC hybrid encryption system [8]. | Download Scientific Diagram](https://www.researchgate.net/publication/362678406/figure/fig2/AS:11431281119374650@1676067863760/AES-ECC-hybrid-encryption-system-8_Q640.jpg)







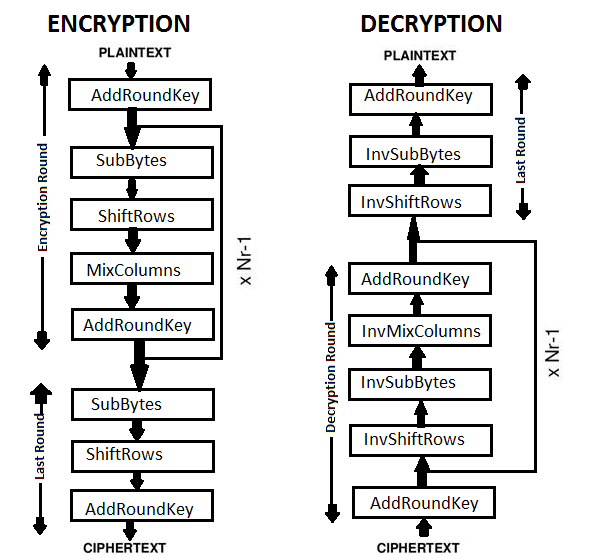












![Encryption and Decryption of AES [9] | Download Scientific Diagram](https://www.researchgate.net/profile/Arya_Wicaksana/publication/339095220/figure/download/fig1/AS:1161688841752576@1653979611283/Encryption-and-Decryption-of-AES-9.png)