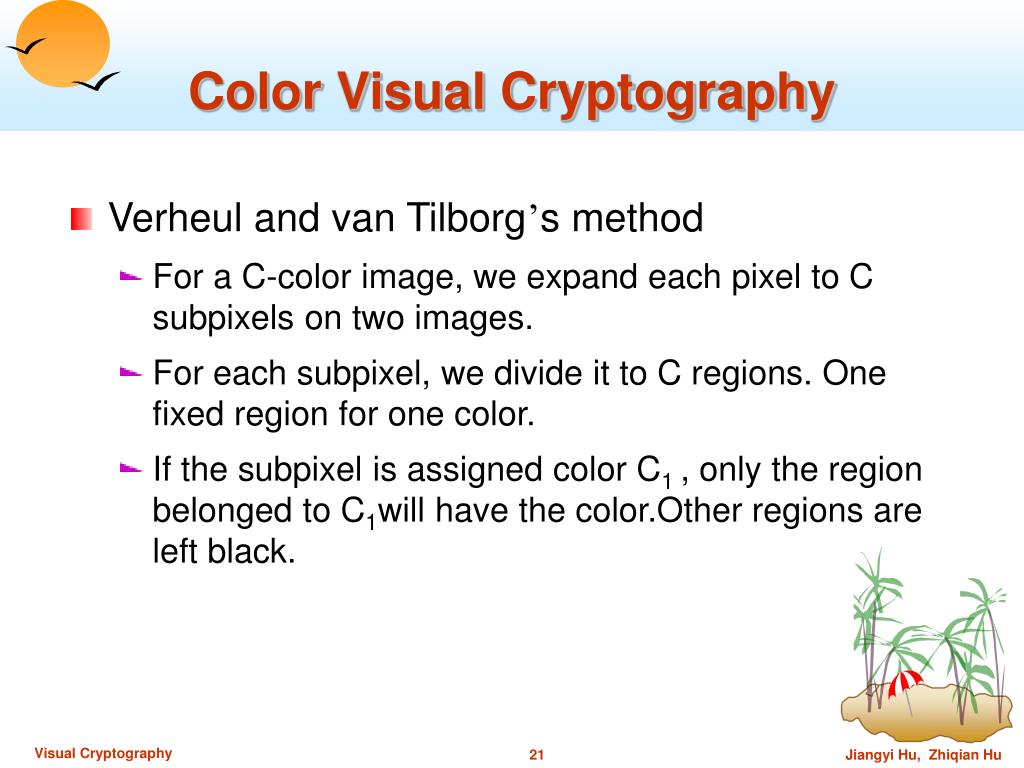
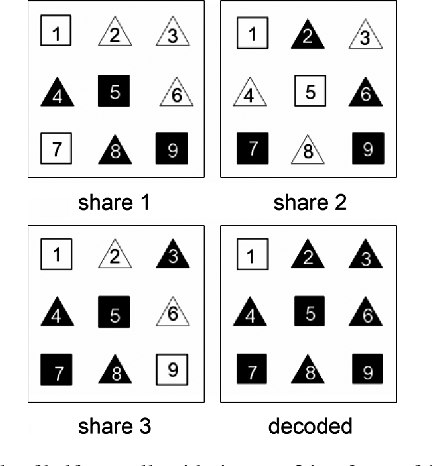
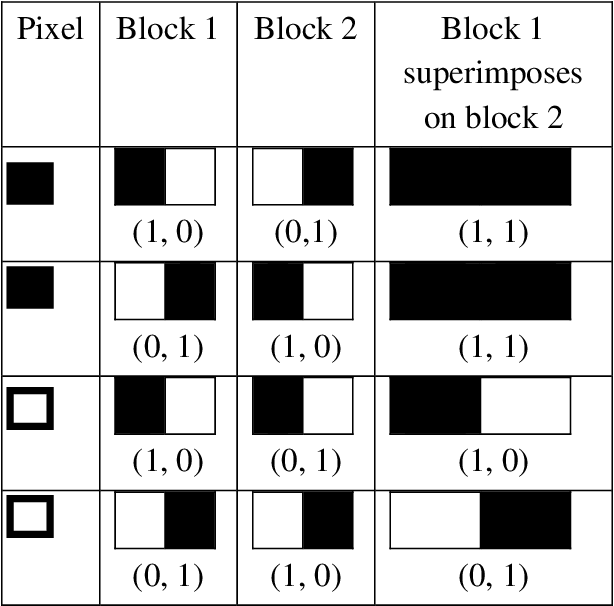
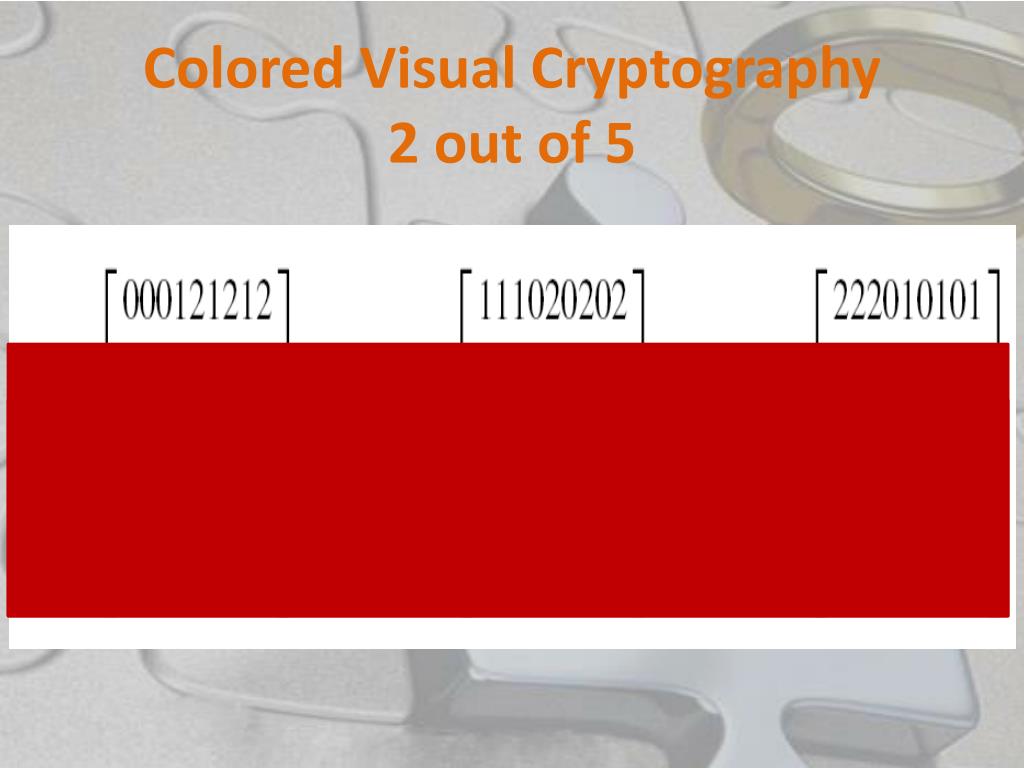
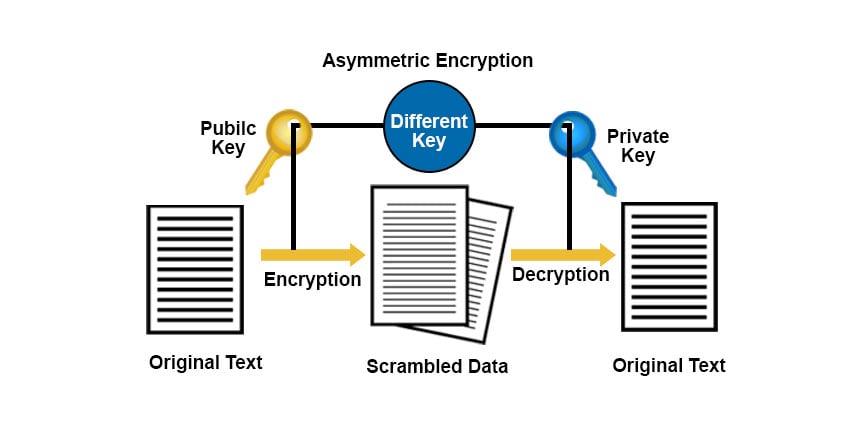
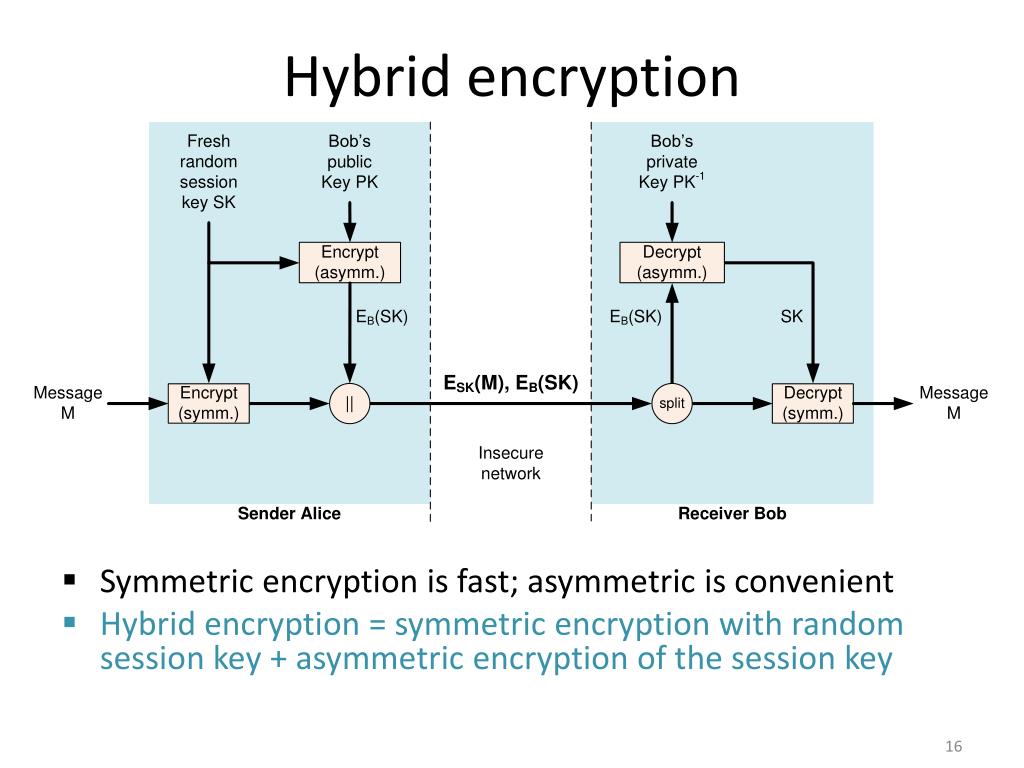
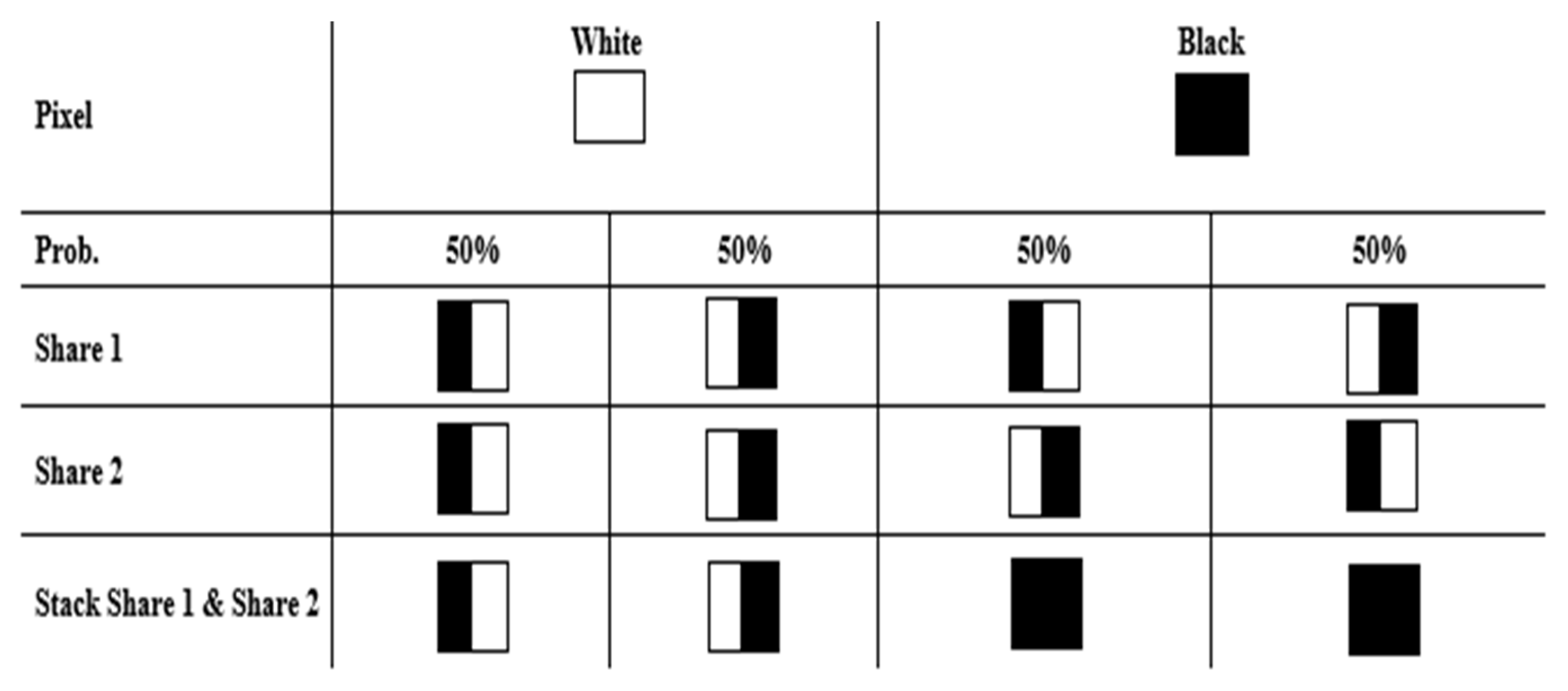
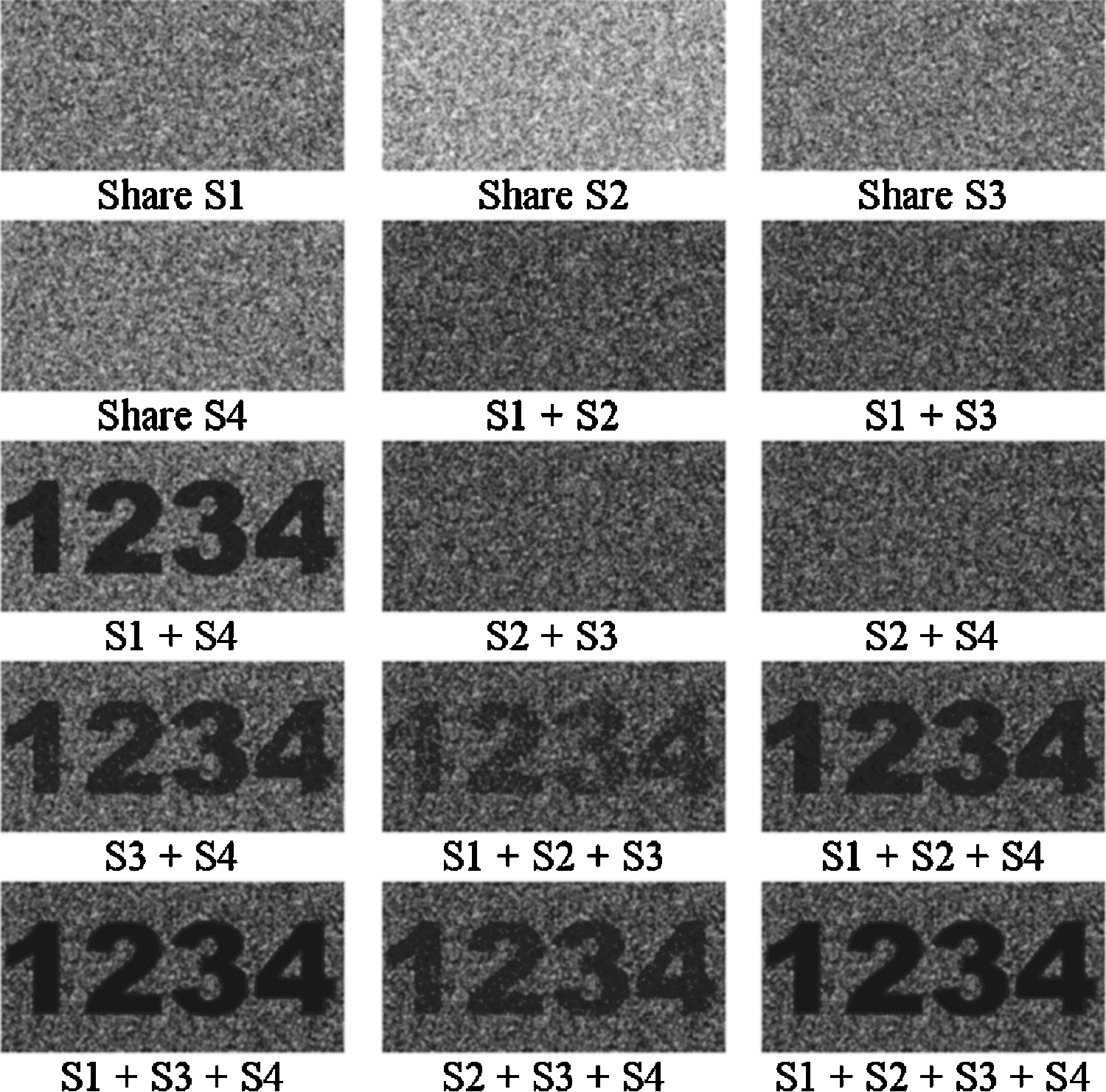
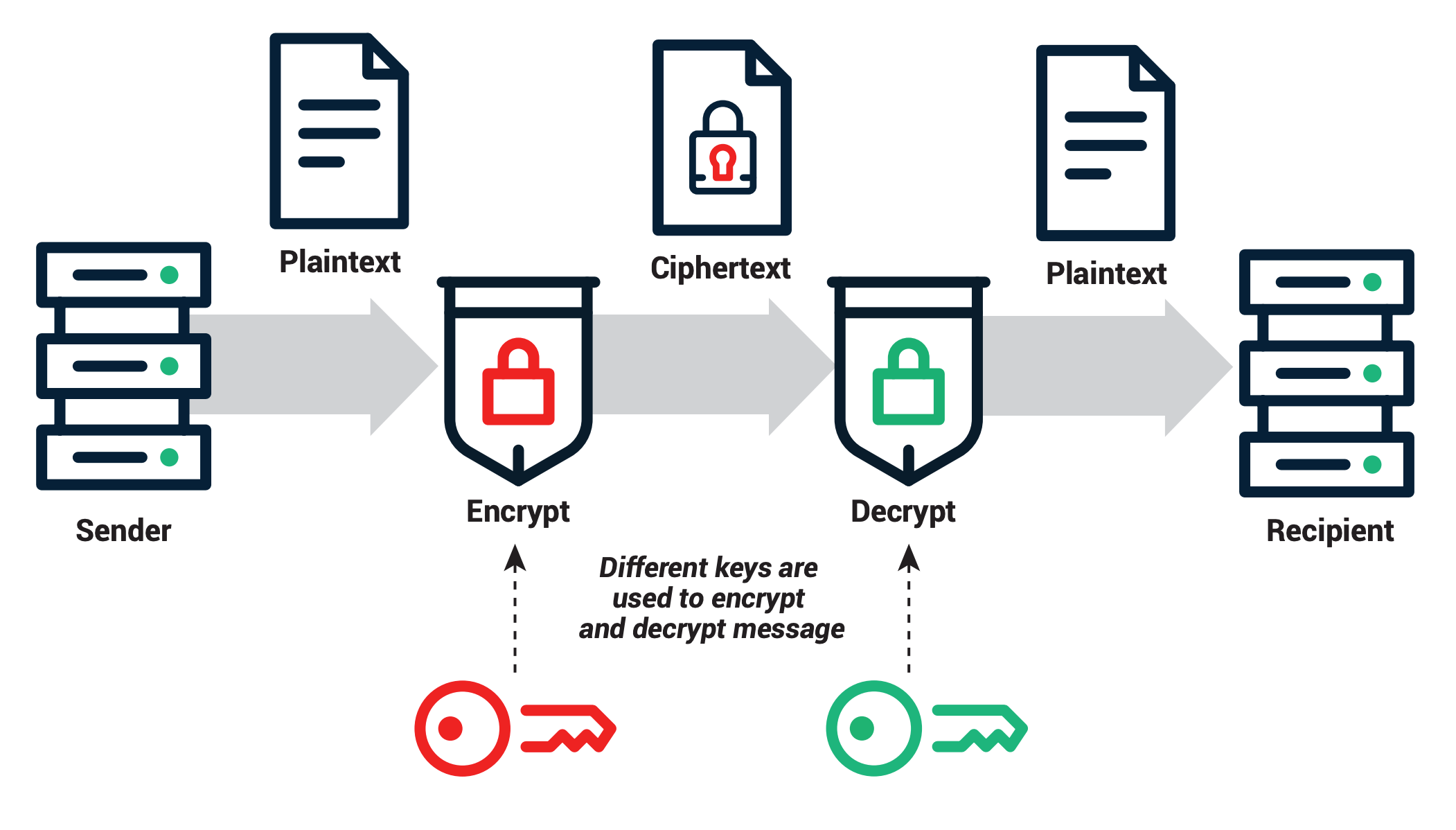
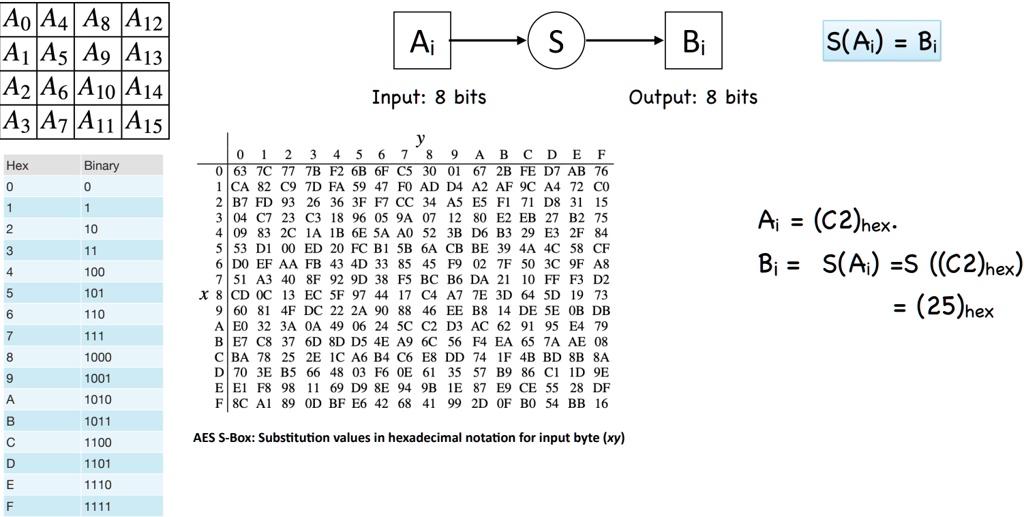
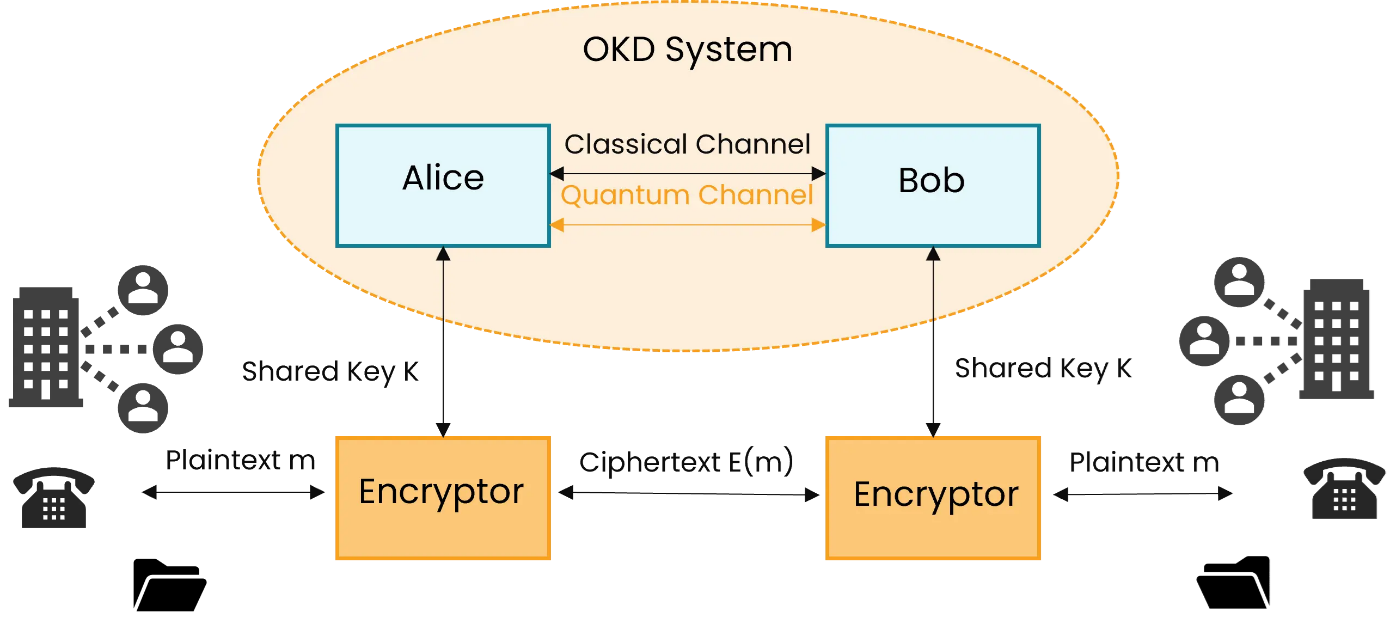
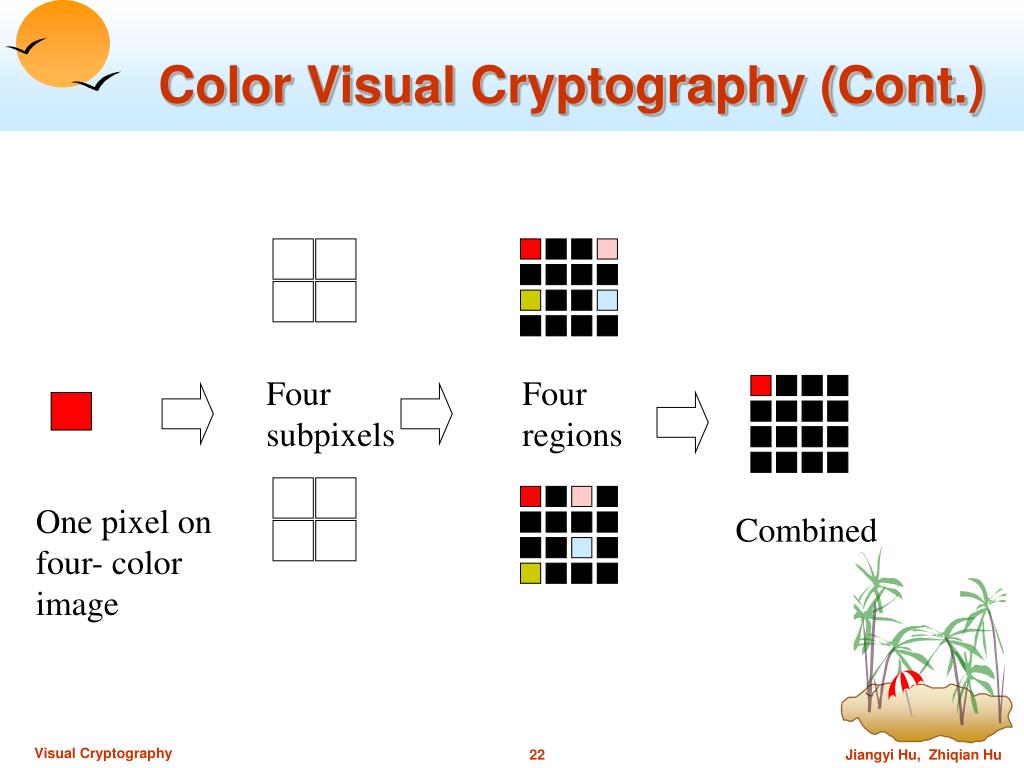
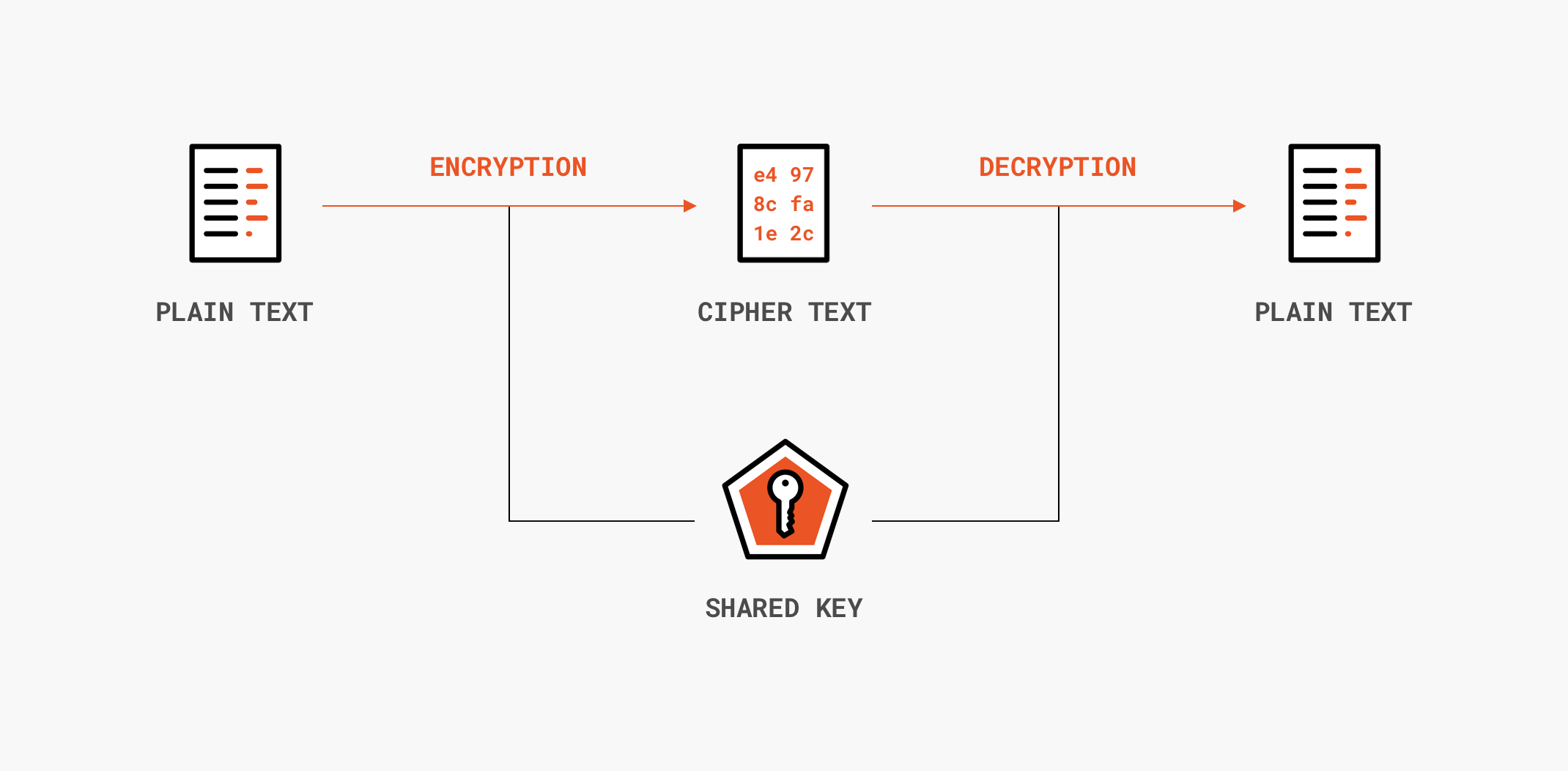
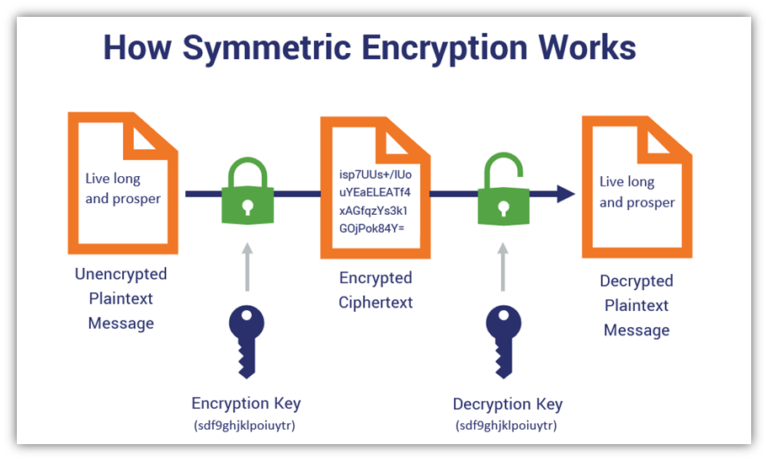
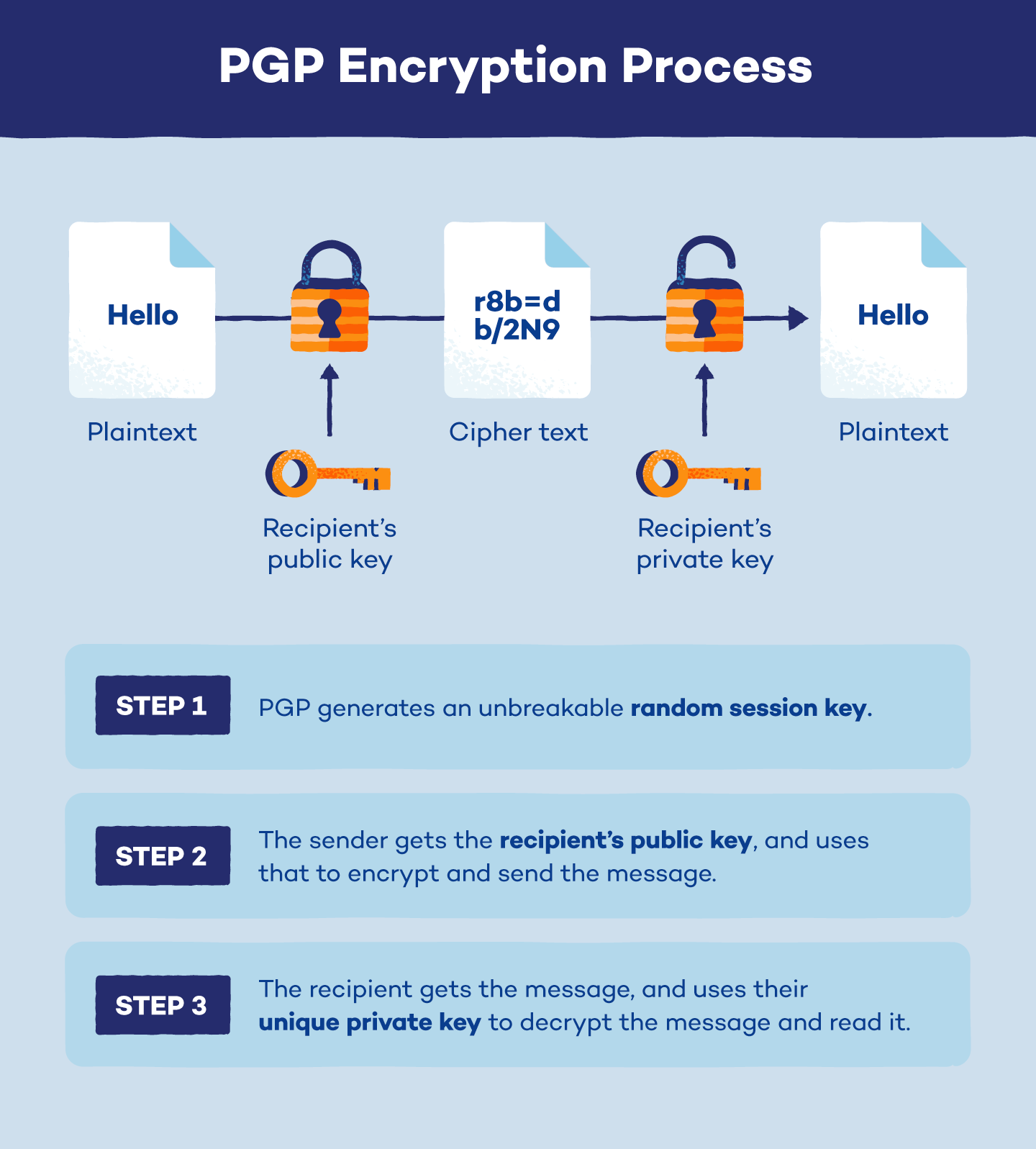
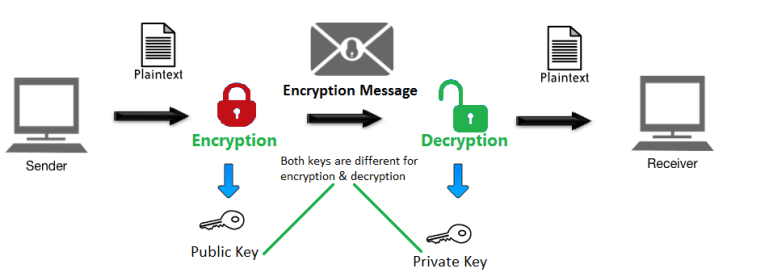
Power progress with our remarkable industrial visual cryptography demonstrated through a { 2 , 2 } -scheme: (a collection of comprehensive galleries of manufacturing images. documenting production methods of artistic, creative, and design. perfect for industrial documentation and training. Each visual cryptography demonstrated through a { 2 , 2 } -scheme: (a image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All visual cryptography demonstrated through a { 2 , 2 } -scheme: (a images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our visual cryptography demonstrated through a { 2 , 2 } -scheme: (a collection for various creative and professional projects. Each image in our visual cryptography demonstrated through a { 2 , 2 } -scheme: (a gallery undergoes rigorous quality assessment before inclusion. Advanced search capabilities make finding the perfect visual cryptography demonstrated through a { 2 , 2 } -scheme: (a image effortless and efficient. Diverse style options within the visual cryptography demonstrated through a { 2 , 2 } -scheme: (a collection suit various aesthetic preferences. Our visual cryptography demonstrated through a { 2 , 2 } -scheme: (a database continuously expands with fresh, relevant content from skilled photographers. Regular updates keep the visual cryptography demonstrated through a { 2 , 2 } -scheme: (a collection current with contemporary trends and styles.

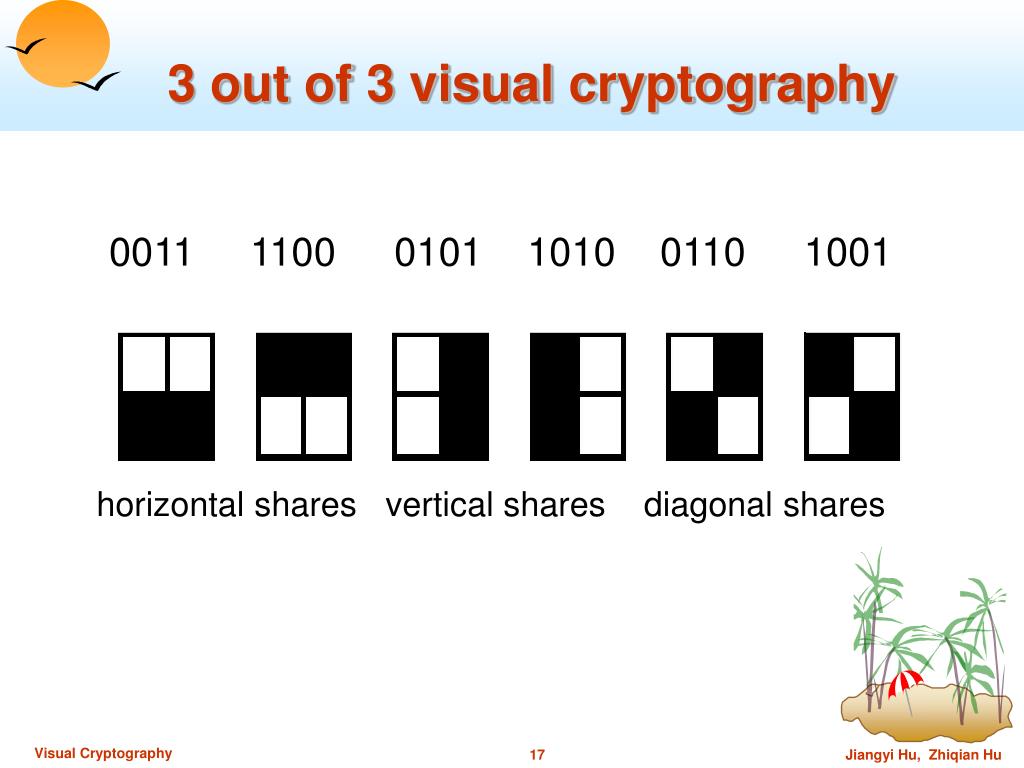

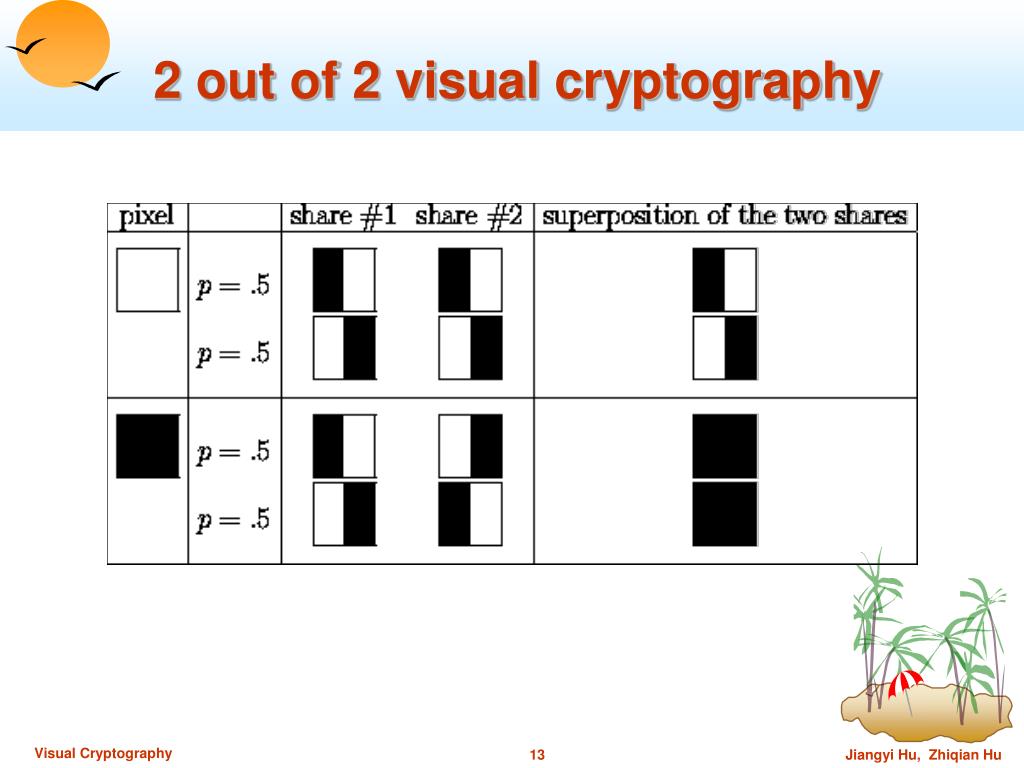
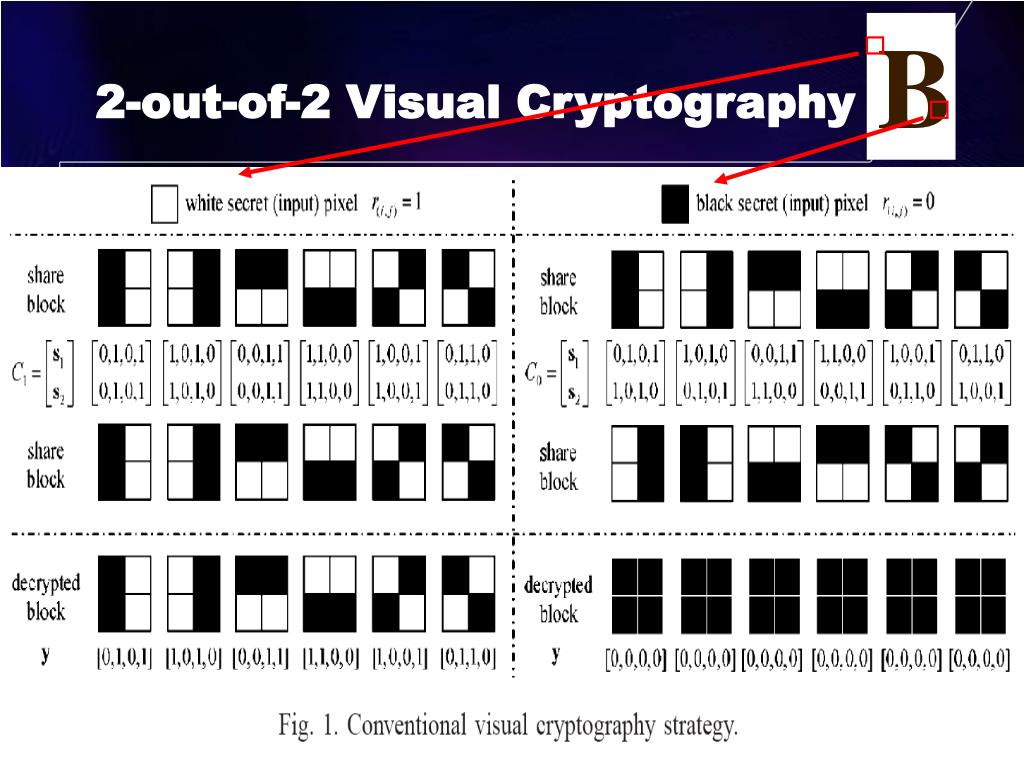
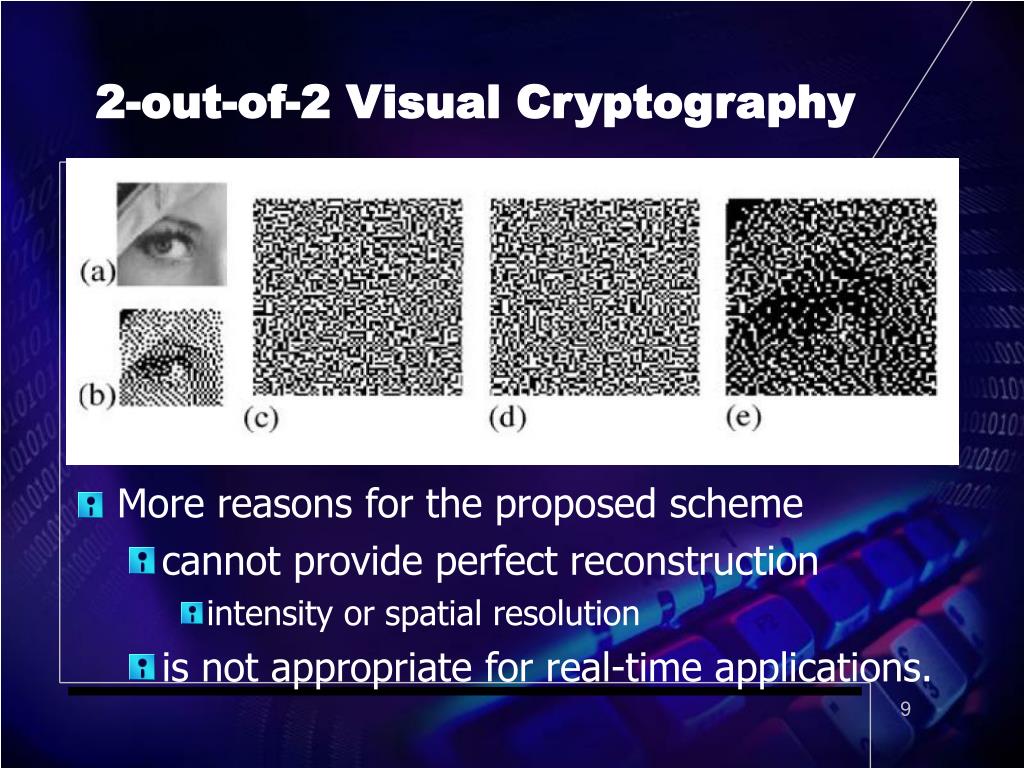
![Examples of visual cryptography proposed by Naor and Shamir [12]. (a ...](https://www.researchgate.net/profile/Ruofei_Du5/publication/335197771/figure/download/fig2/AS:884642278293505@1587926563705/Examples-of-visual-cryptography-proposed-by-Naor-and-Shamir-12-a-shows-six-valid.png)






.jpg)













+--Visual+Cryptography.jpg)

![(2,2) Size invariant Visual Cryptography[2][4] | Download Scientific ...](https://www.researchgate.net/profile/Manoj-Kumar-192/publication/328460589/figure/fig2/AS:11431281133796221@1680318010389/2-2-Size-invariant-Visual-Cryptography23_Q320.jpg)




![Comparison with existing and system [3] C. Halftone visual cryptography ...](https://mavink.com/images/loadingwhitetransparent.gif)










![(2,2) Size invariant Visual Cryptography[2][4] | Download Scientific ...](https://www.researchgate.net/publication/328460589/figure/fig3/AS:11431281133803058@1680318011051/2-2-Size-invariant-Visual-Cryptography24.jpg)