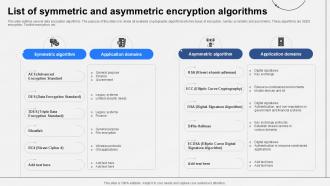
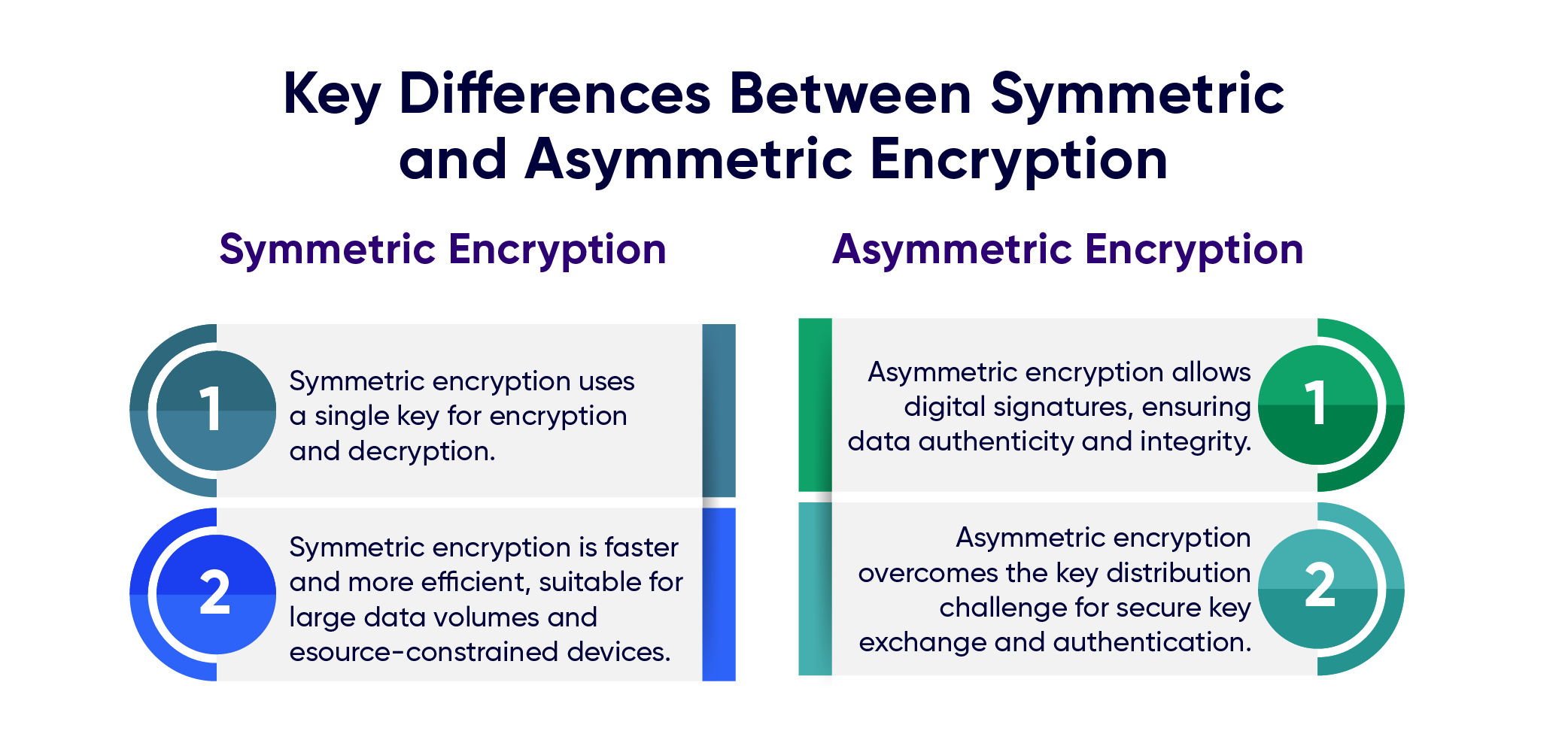
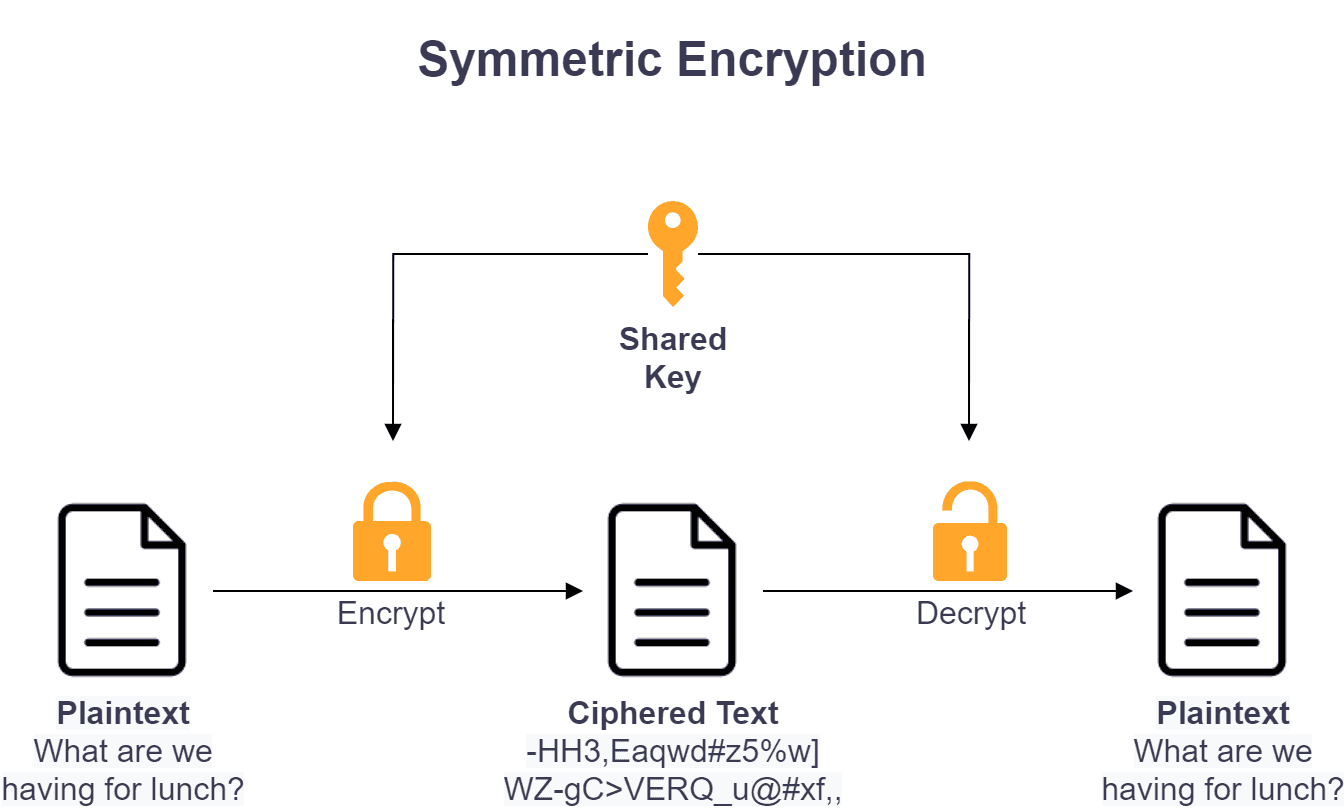
Drive innovation through hundreds of industry-focused implement symmetric and asymmetric cryptography algorithms with c# photographs. showcasing industrial applications of photography, images, and pictures. designed to support industrial communication. Our implement symmetric and asymmetric cryptography algorithms with c# collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All implement symmetric and asymmetric cryptography algorithms with c# images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our implement symmetric and asymmetric cryptography algorithms with c# collection for various creative and professional projects. Diverse style options within the implement symmetric and asymmetric cryptography algorithms with c# collection suit various aesthetic preferences. Professional licensing options accommodate both commercial and educational usage requirements. Regular updates keep the implement symmetric and asymmetric cryptography algorithms with c# collection current with contemporary trends and styles. Whether for commercial projects or personal use, our implement symmetric and asymmetric cryptography algorithms with c# collection delivers consistent excellence. Time-saving browsing features help users locate ideal implement symmetric and asymmetric cryptography algorithms with c# images quickly. Each image in our implement symmetric and asymmetric cryptography algorithms with c# gallery undergoes rigorous quality assessment before inclusion.




















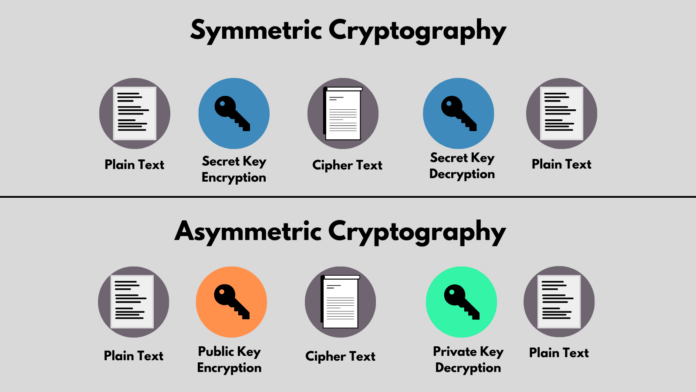
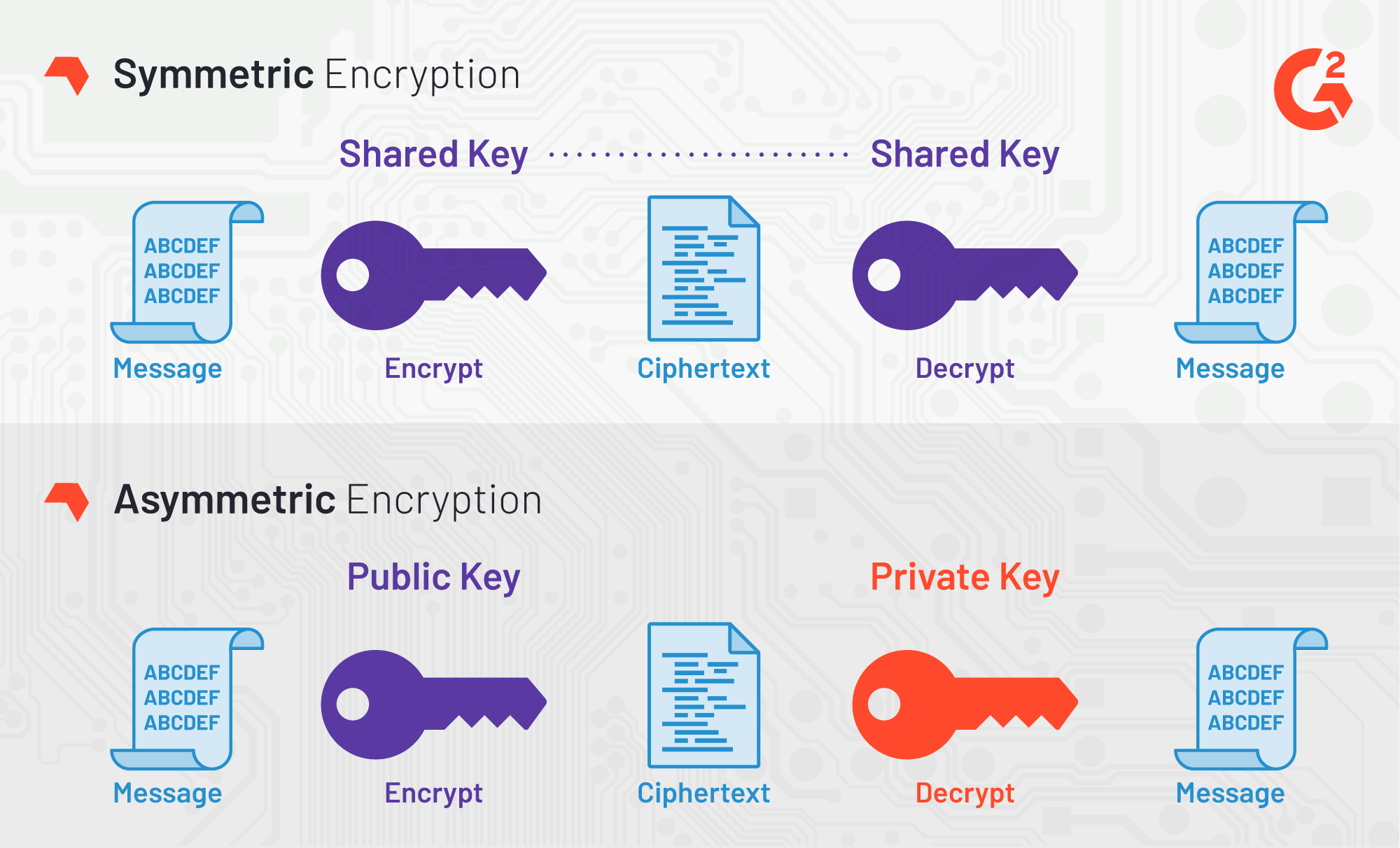
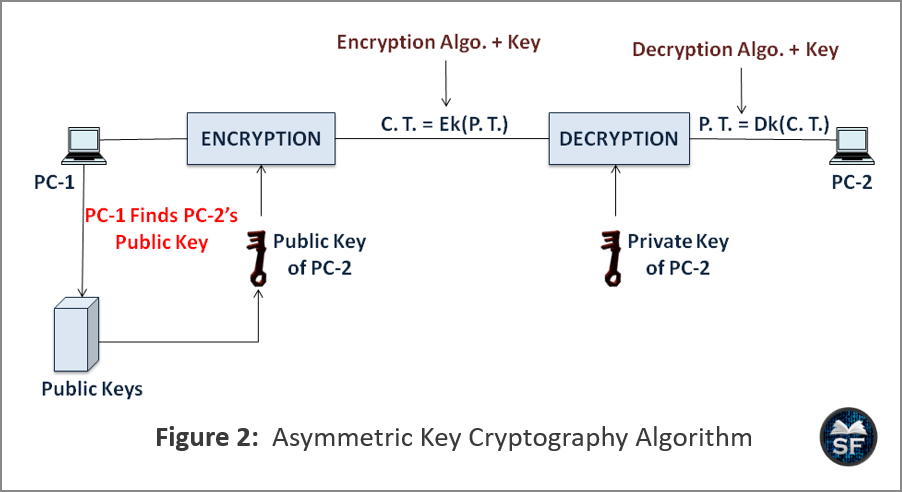













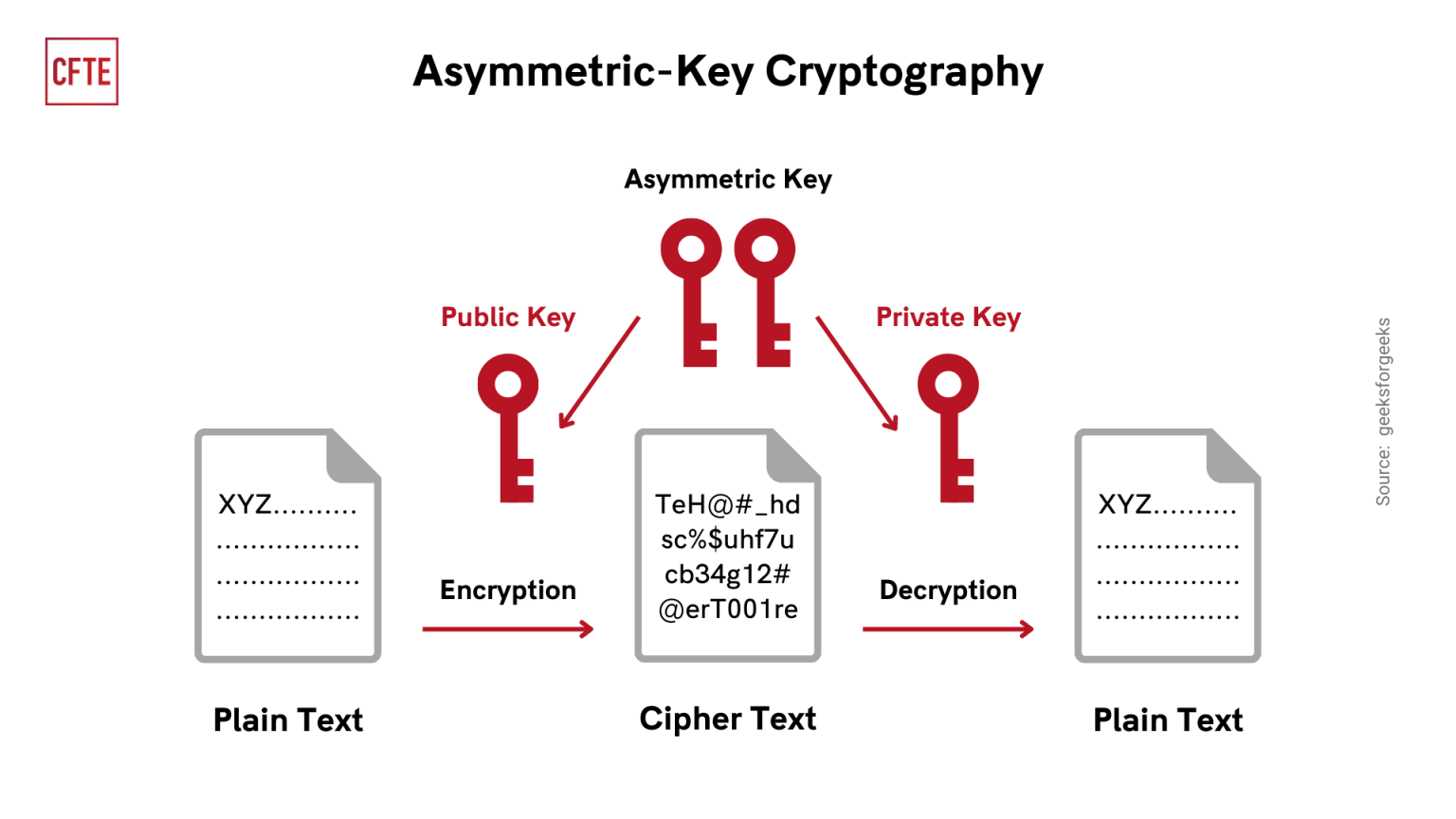



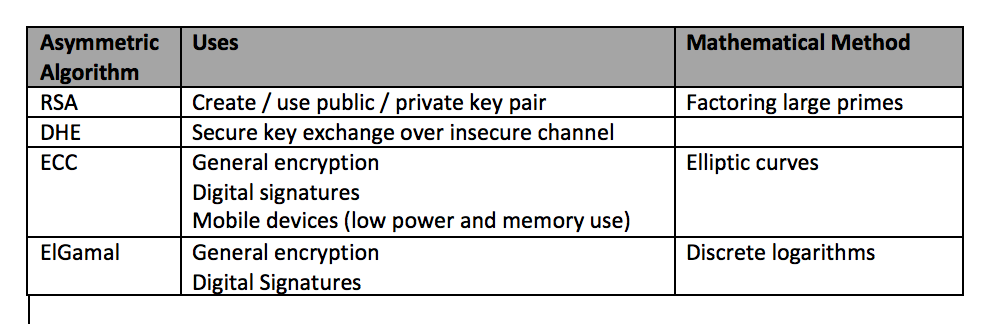
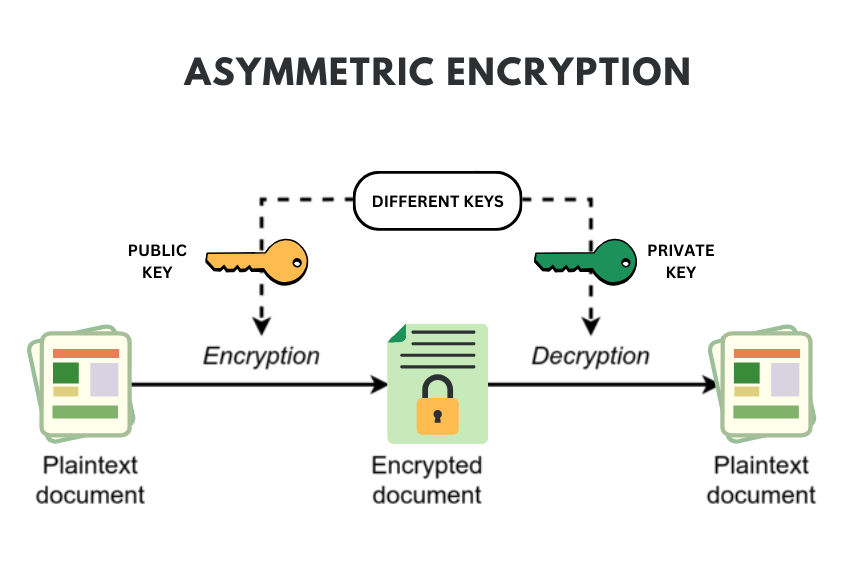

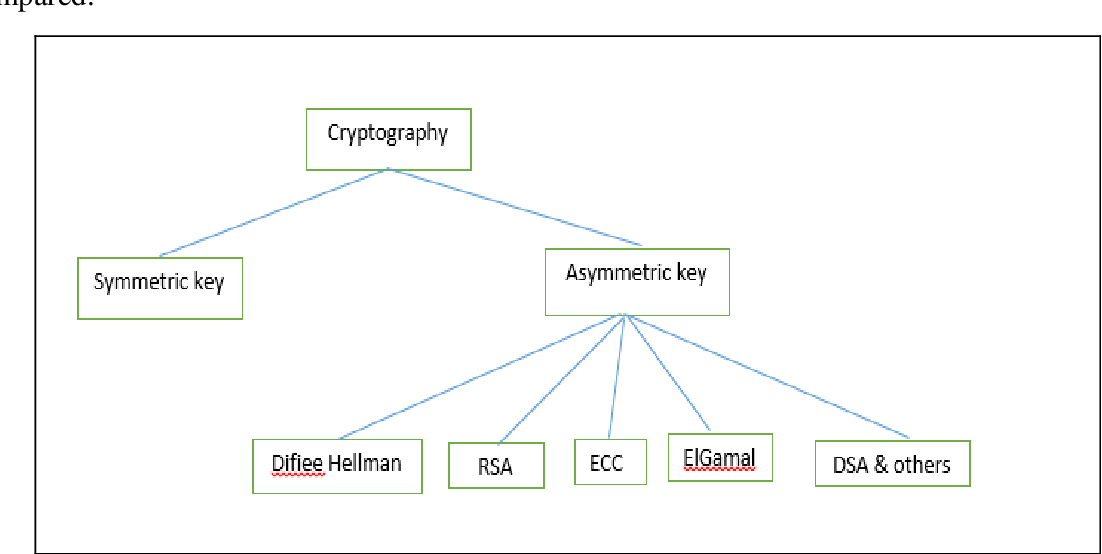






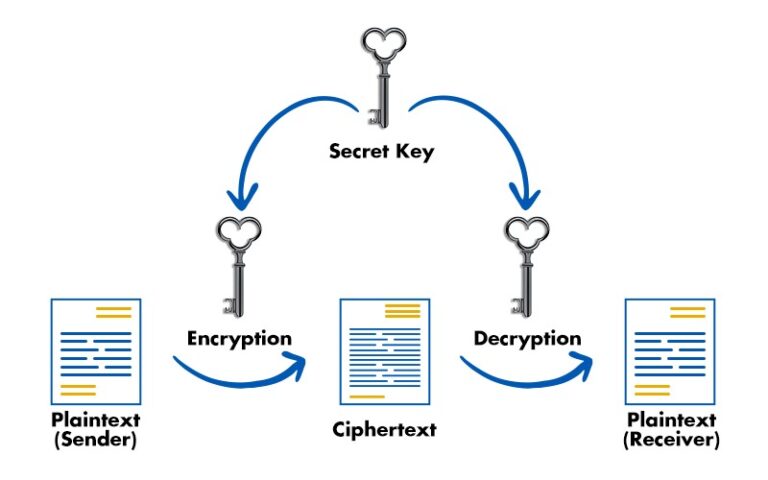
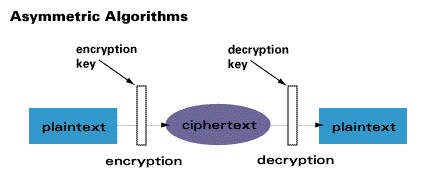



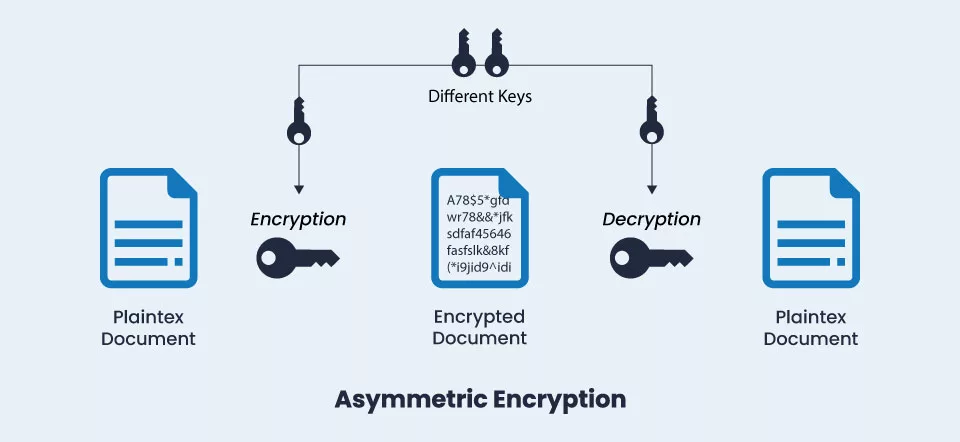



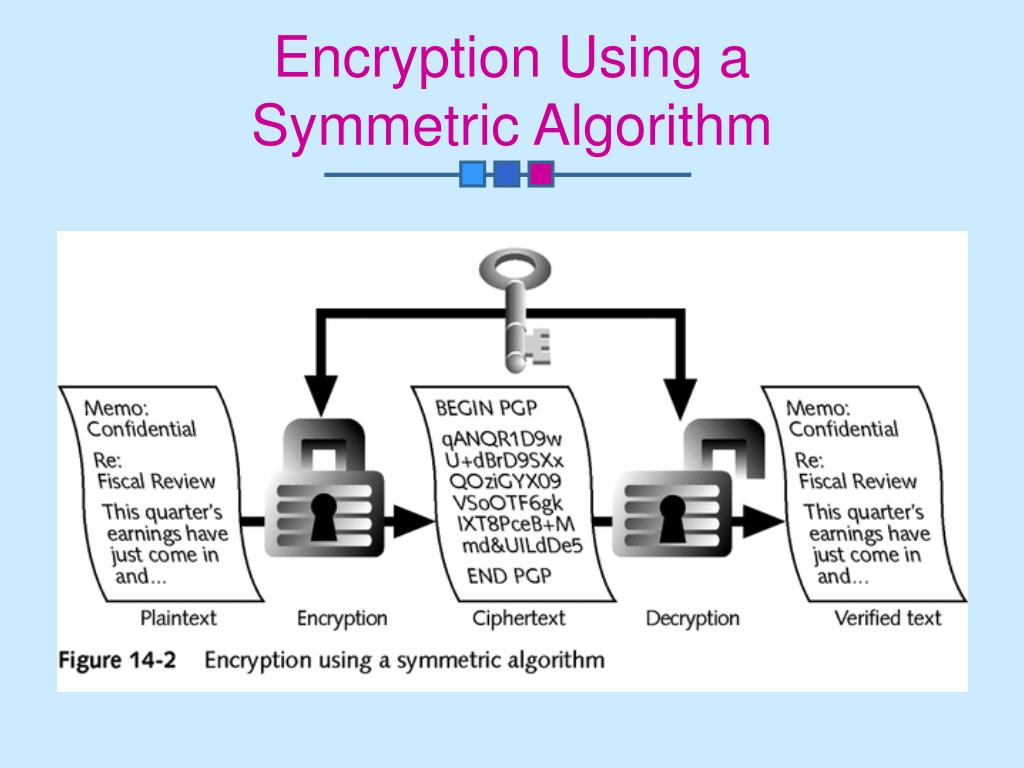






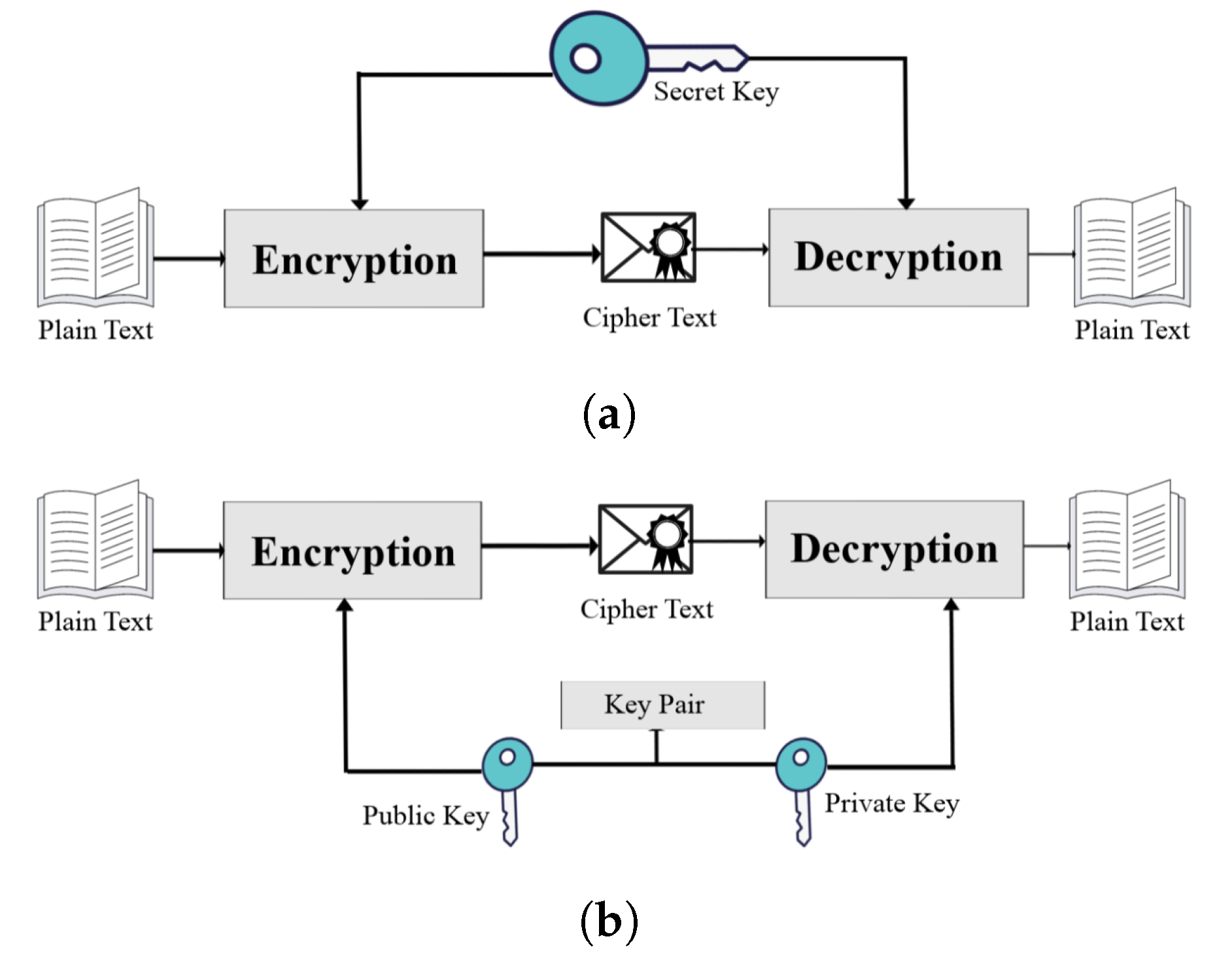

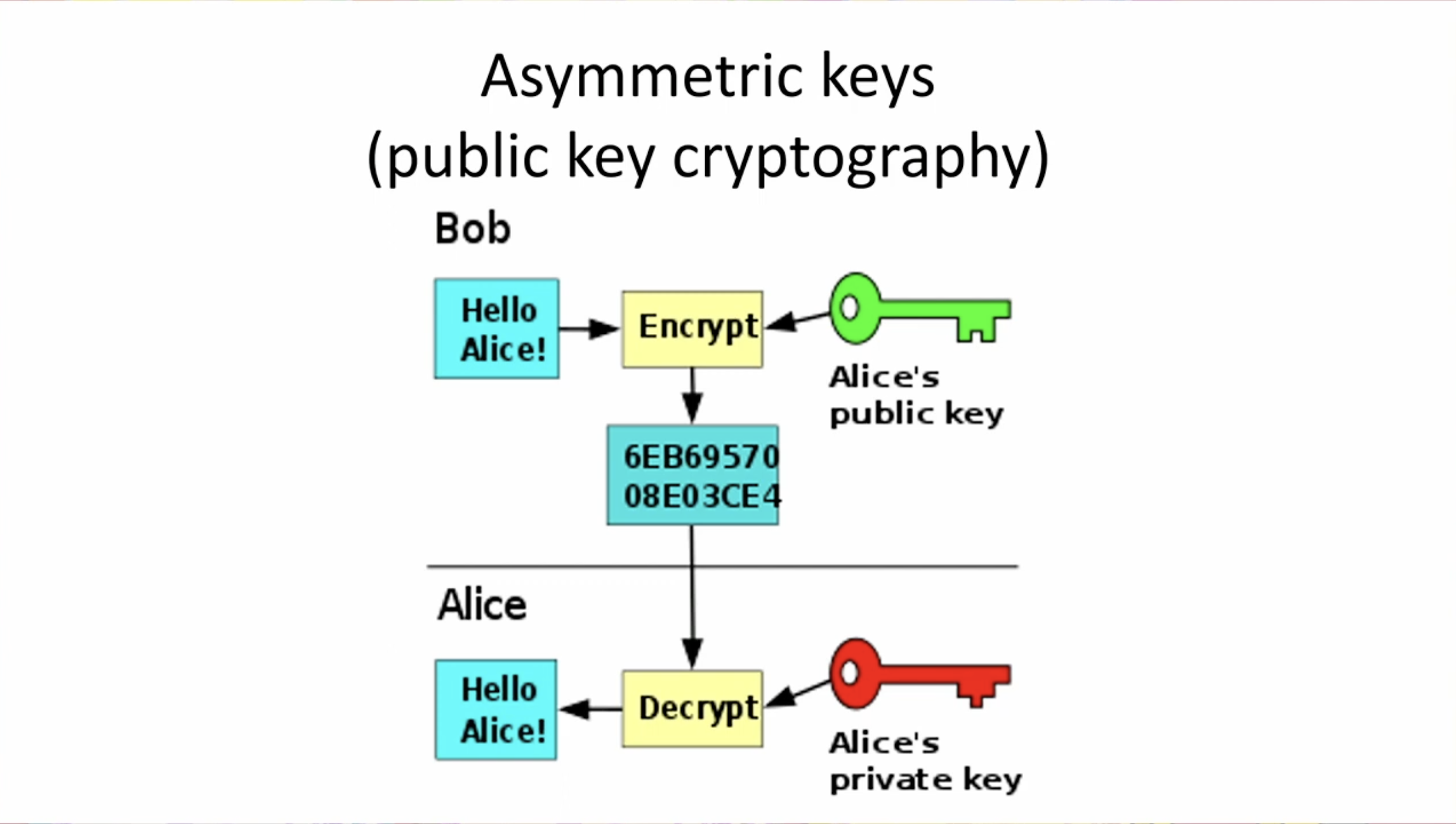

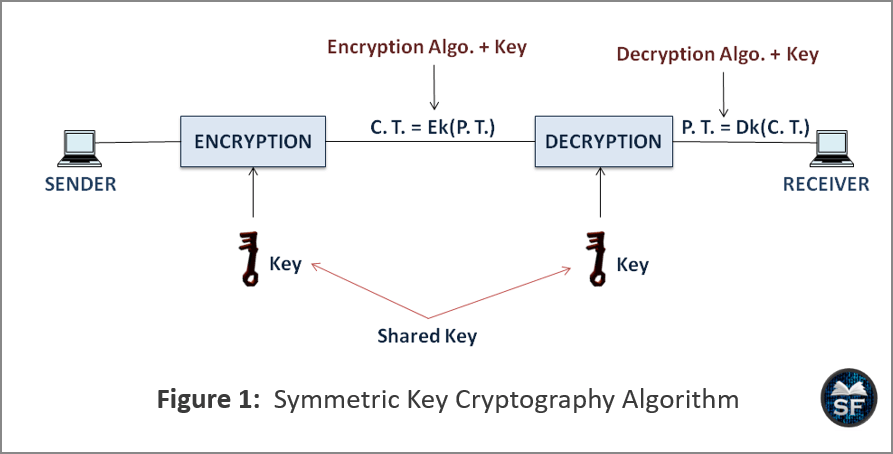
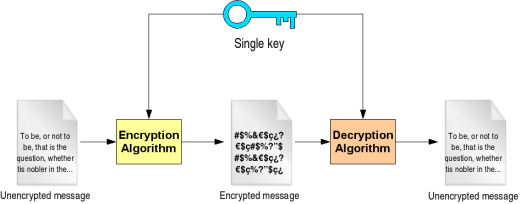
![[Review] 3 Main Types of Encryption: Hash, Symmetric, Asymmetric](https://cdn-images-1.medium.com/max/1200/1*23RpkZuWAeSP7x0YdMtsdQ.png)
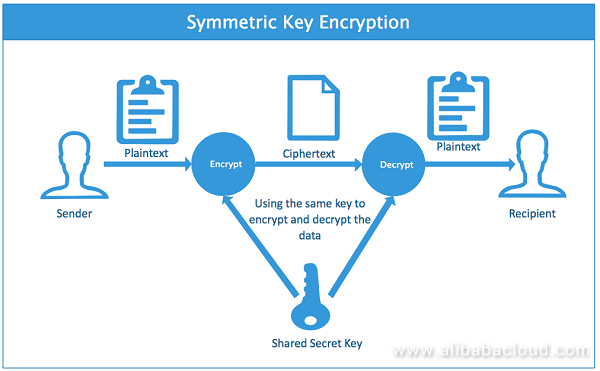

















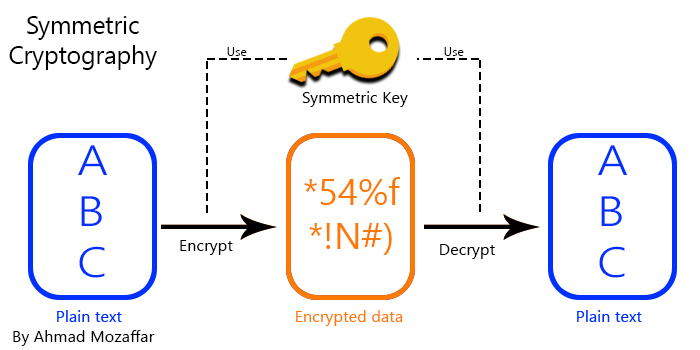
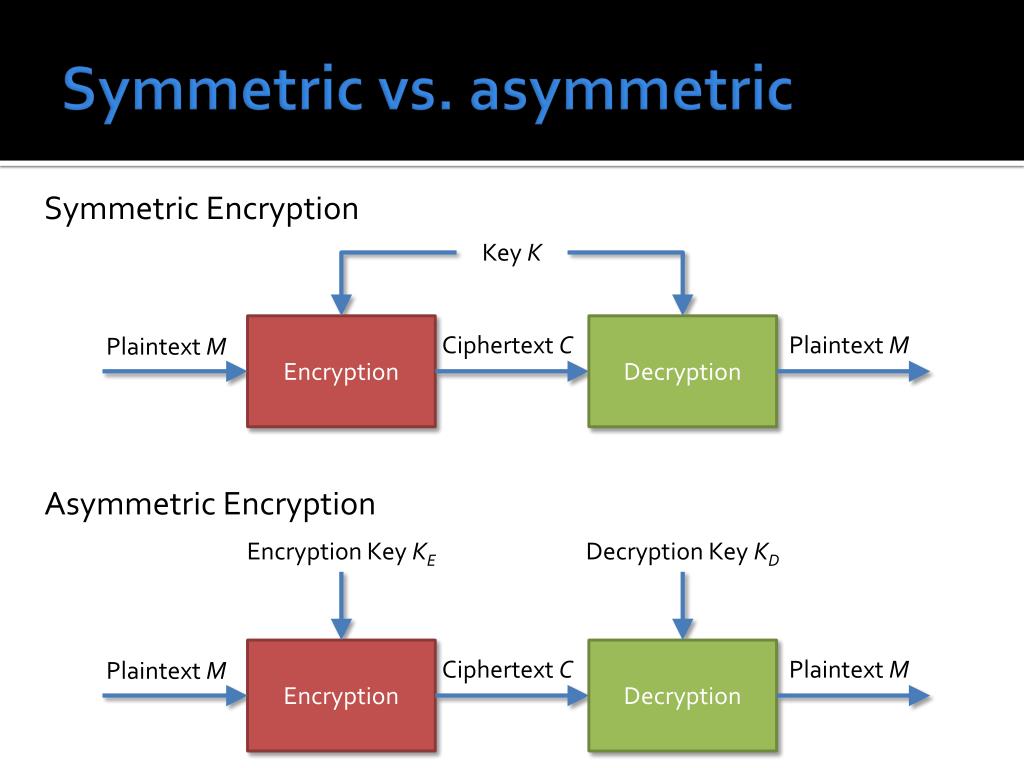
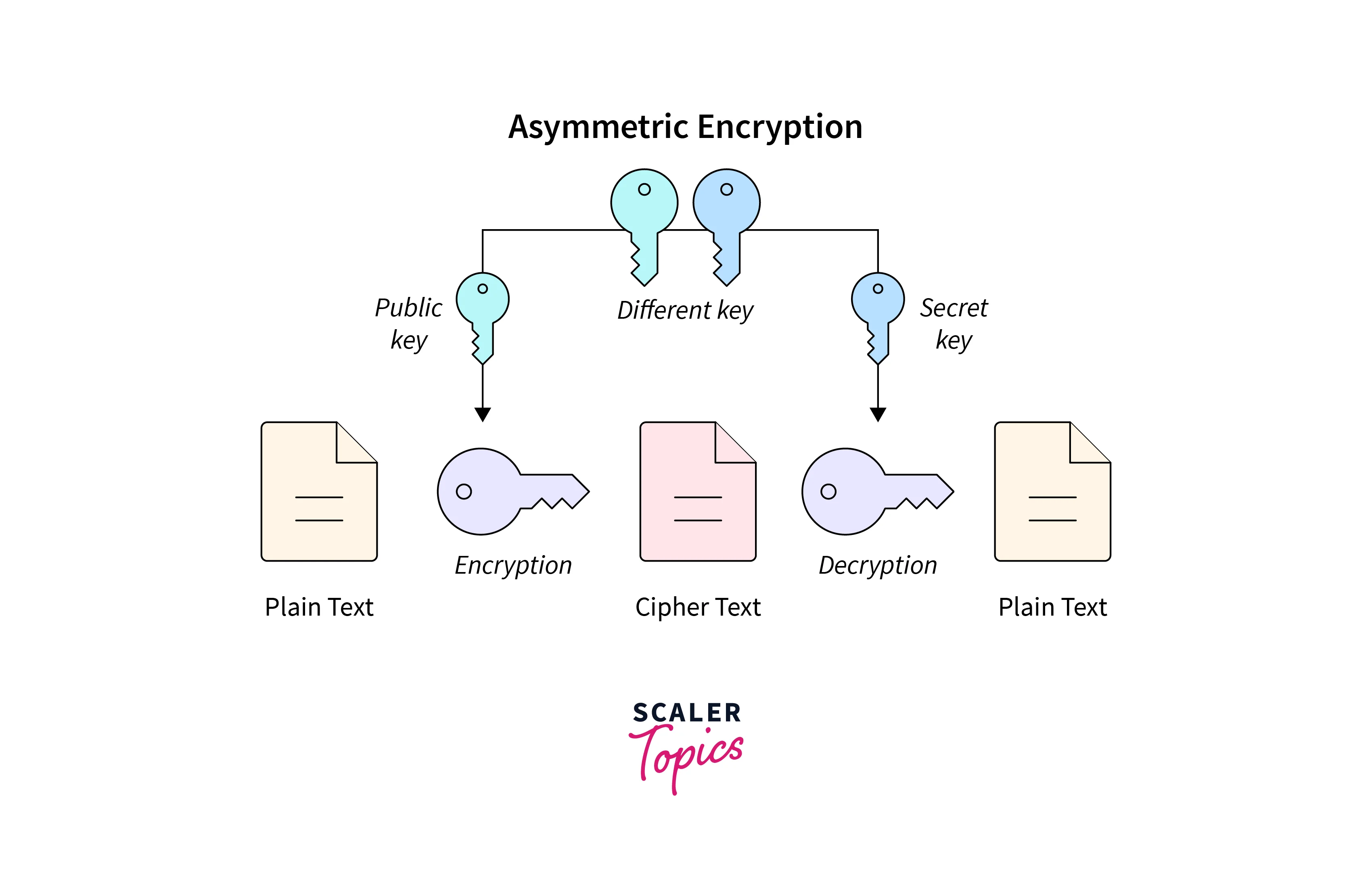
![4: Asymmetric Cryptography [23]. | Download Scientific Diagram](https://www.researchgate.net/profile/Haneen_Alaswad/publication/361140493/figure/fig1/AS:1164313729474568@1654605433813/Symmetric-Cryptography-23_Q320.jpg)