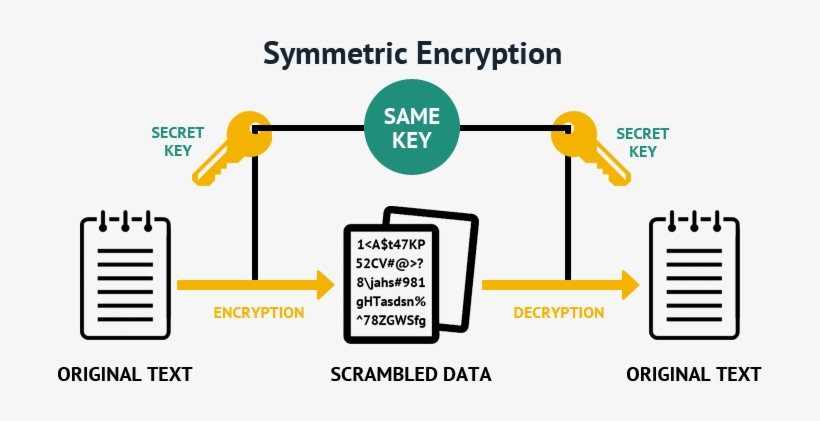
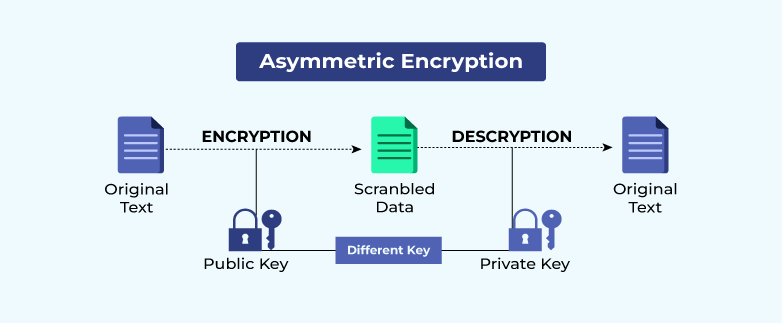
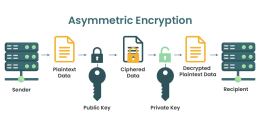
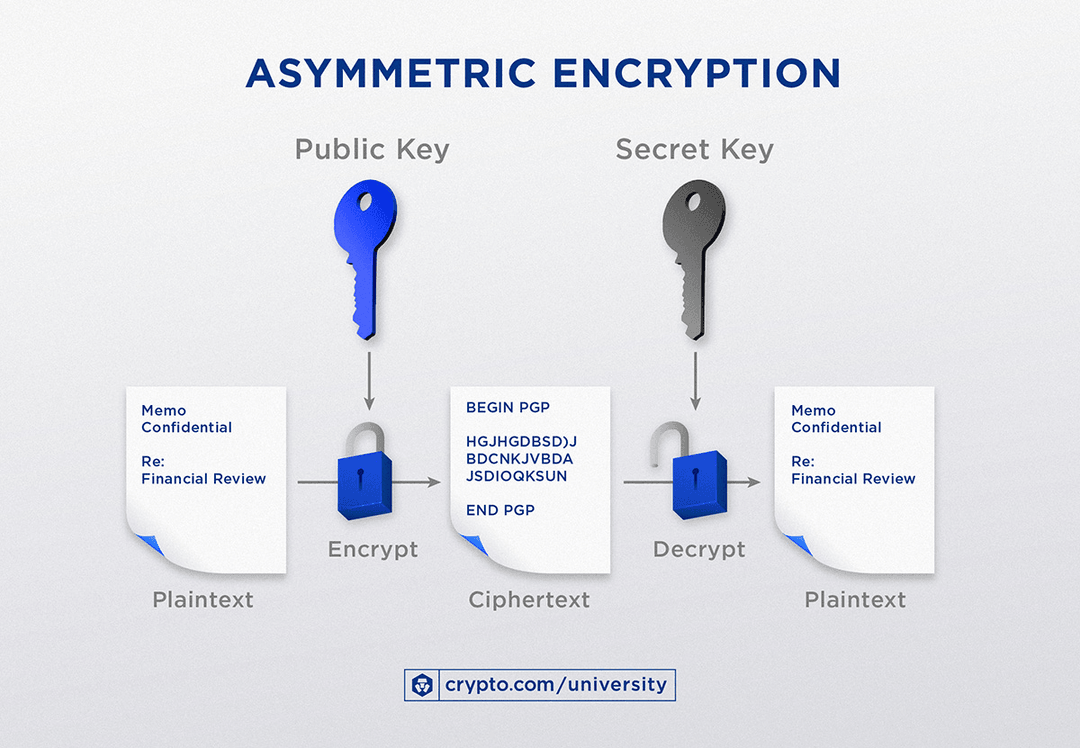
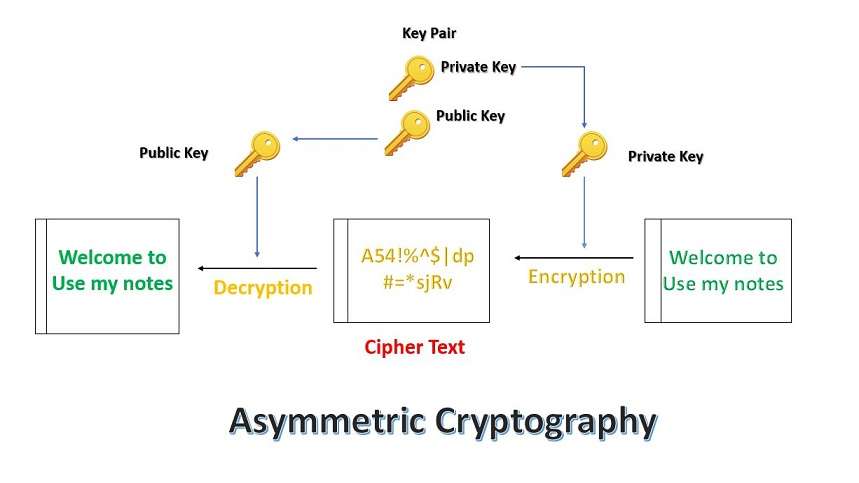
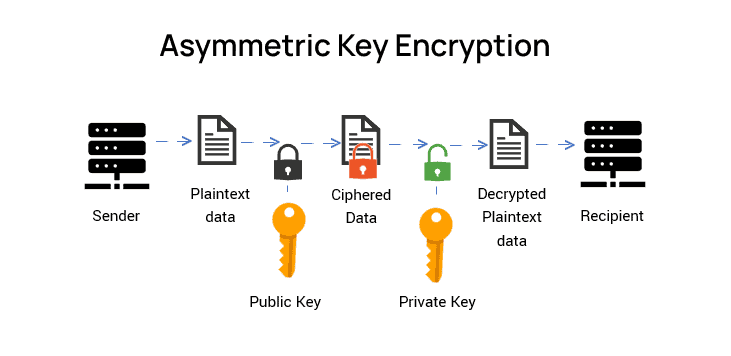
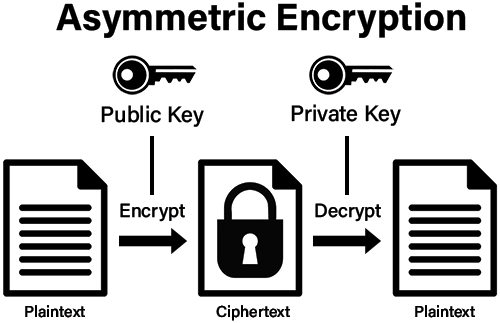
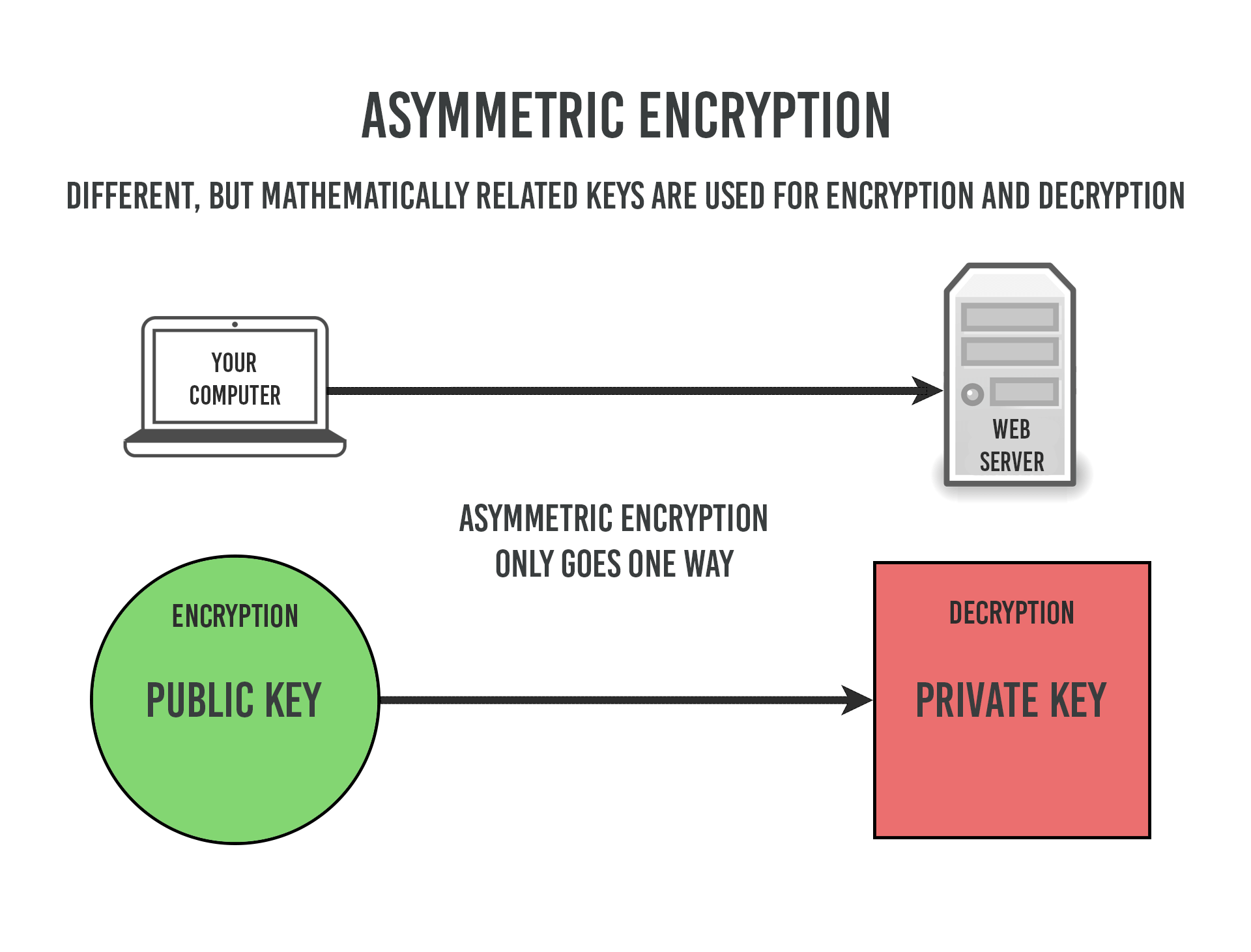
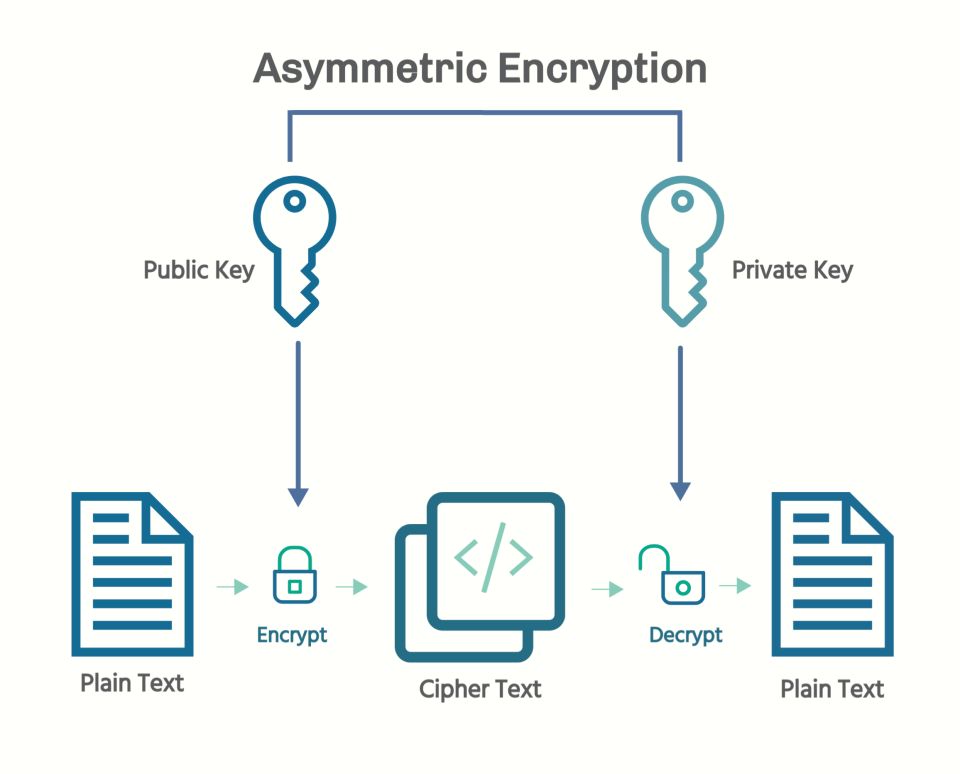
Power progress with our remarkable industrial asymmetric vs symmetric encryption: definitions & differences - hashed collection of substantial collections of manufacturing images. highlighting manufacturing processes for photography, images, and pictures. ideal for manufacturing and production content. Each asymmetric vs symmetric encryption: definitions & differences - hashed image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All asymmetric vs symmetric encryption: definitions & differences - hashed images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our asymmetric vs symmetric encryption: definitions & differences - hashed collection for various creative and professional projects. Professional licensing options accommodate both commercial and educational usage requirements. Each image in our asymmetric vs symmetric encryption: definitions & differences - hashed gallery undergoes rigorous quality assessment before inclusion. The asymmetric vs symmetric encryption: definitions & differences - hashed collection represents years of careful curation and professional standards. Multiple resolution options ensure optimal performance across different platforms and applications. Comprehensive tagging systems facilitate quick discovery of relevant asymmetric vs symmetric encryption: definitions & differences - hashed content. Reliable customer support ensures smooth experience throughout the asymmetric vs symmetric encryption: definitions & differences - hashed selection process.