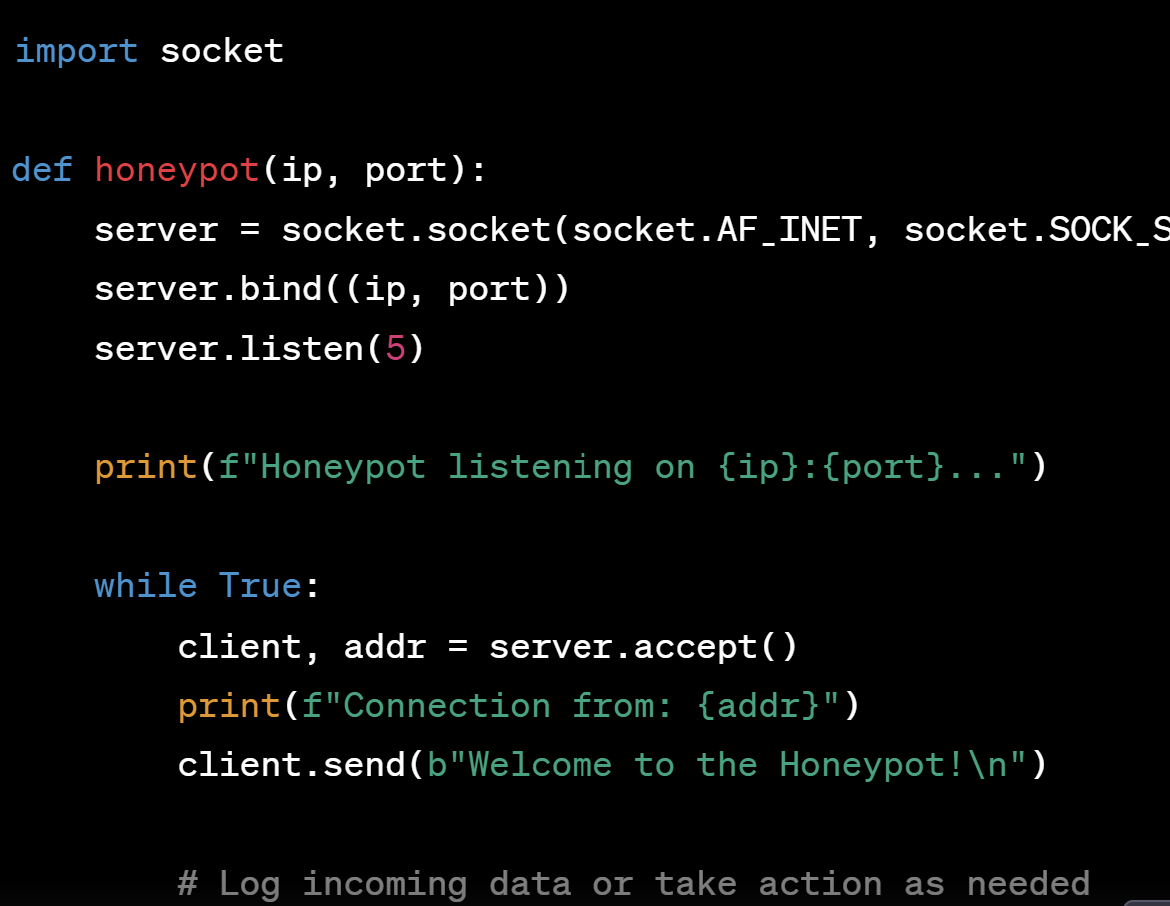
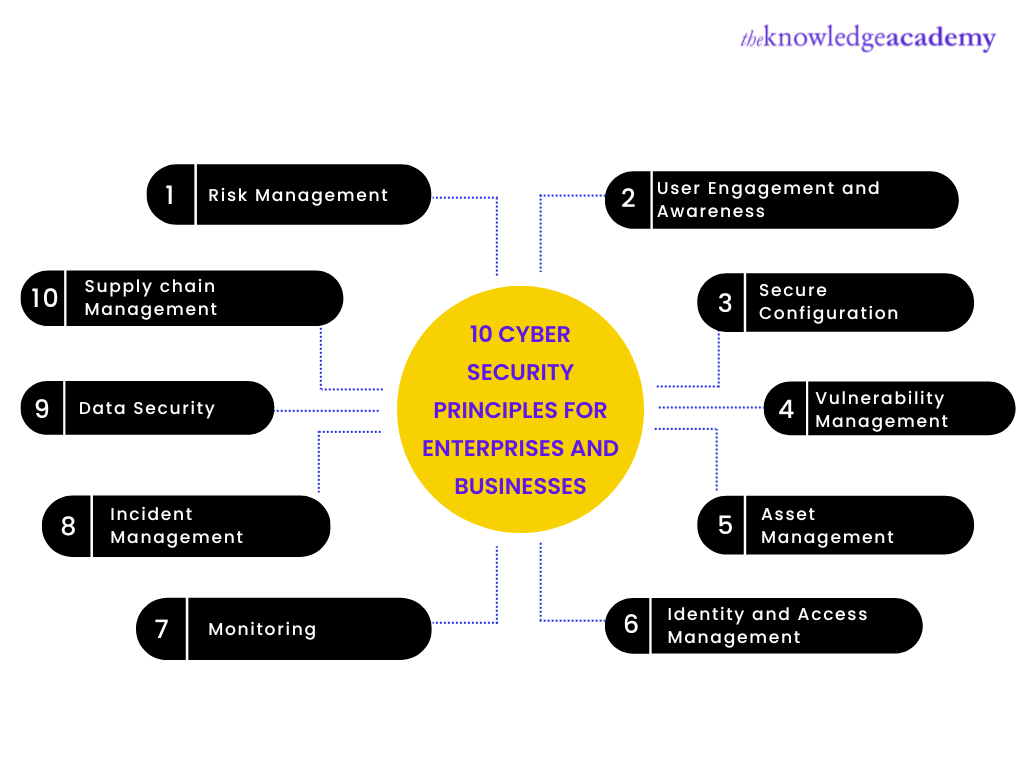
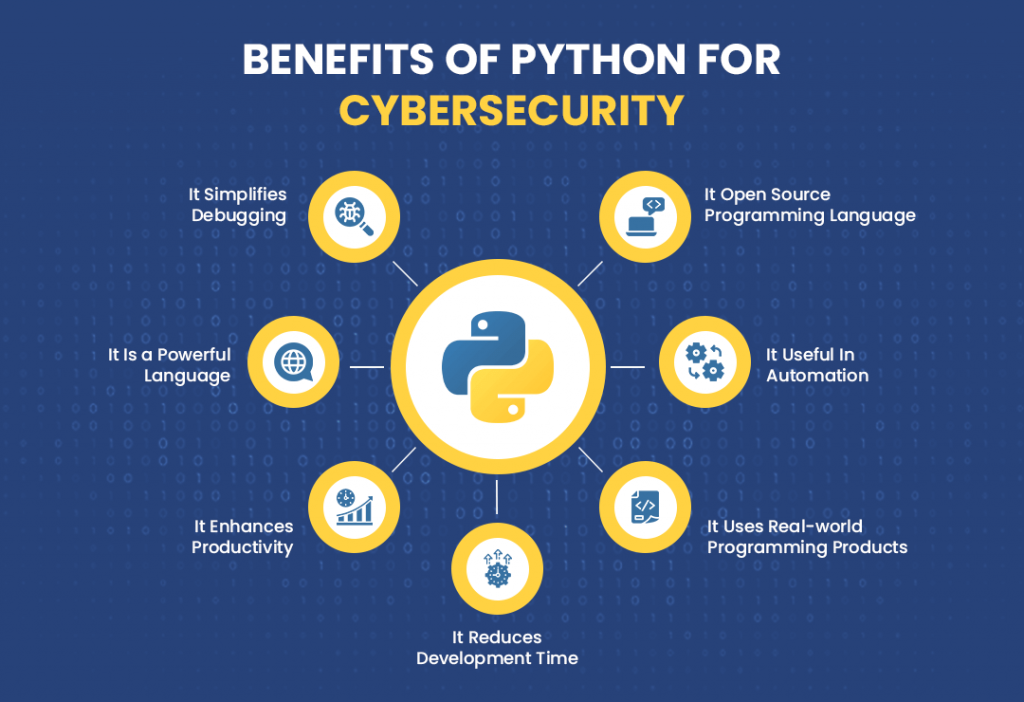
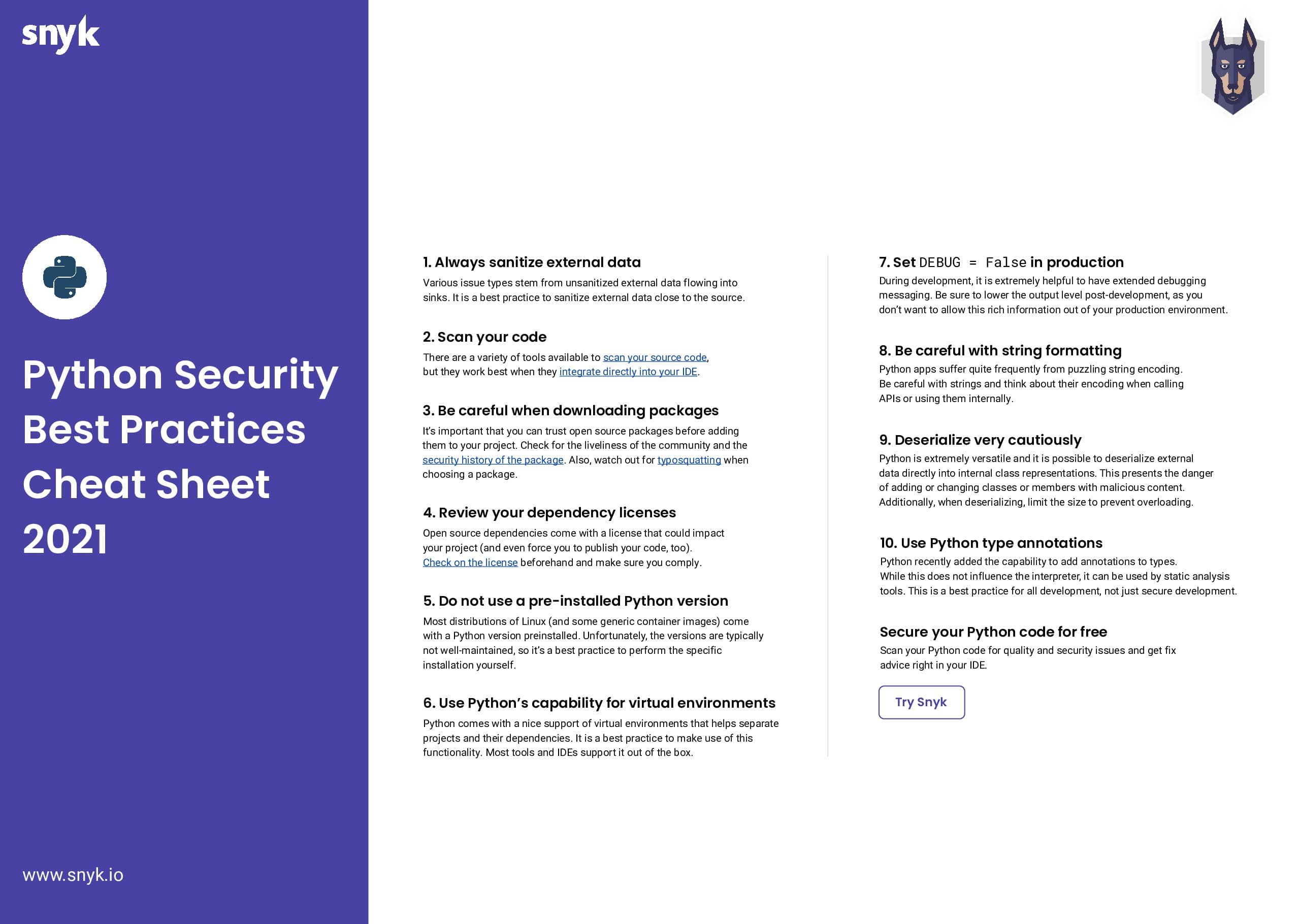
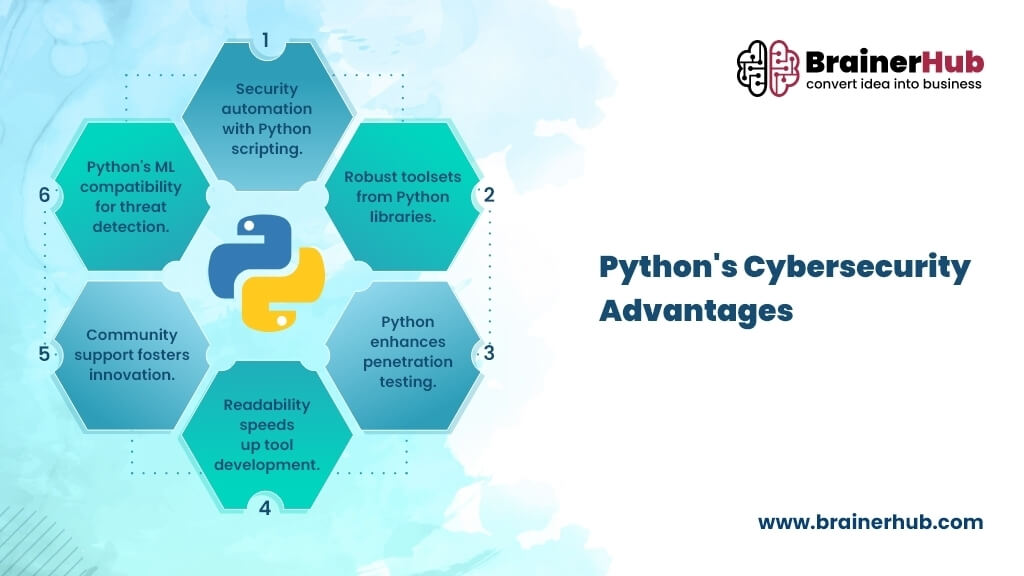
Protect our planet with our remarkable environmental safety cybersecurity: python security: best practices for developers collection of substantial collections of conservation images. environmentally documenting photography, images, and pictures. ideal for sustainability initiatives and reporting. Each safety cybersecurity: python security: best practices for developers image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All safety cybersecurity: python security: best practices for developers images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our safety cybersecurity: python security: best practices for developers gallery offers diverse visual resources to bring your ideas to life. Advanced search capabilities make finding the perfect safety cybersecurity: python security: best practices for developers image effortless and efficient. Instant download capabilities enable immediate access to chosen safety cybersecurity: python security: best practices for developers images. Each image in our safety cybersecurity: python security: best practices for developers gallery undergoes rigorous quality assessment before inclusion. The safety cybersecurity: python security: best practices for developers archive serves professionals, educators, and creatives across diverse industries. Reliable customer support ensures smooth experience throughout the safety cybersecurity: python security: best practices for developers selection process.


















.jpg)







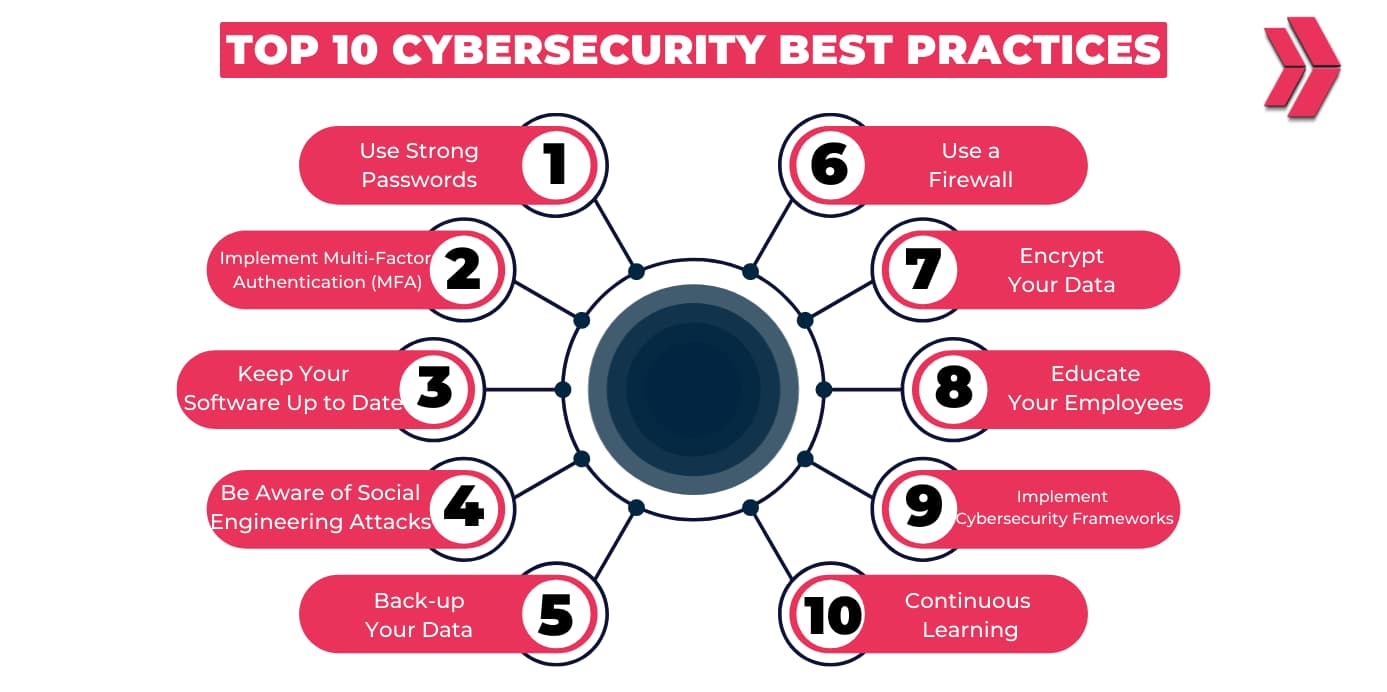
![Top 10 Cyber Security Best Practices [Updated 2025]](https://cdn.mindmajix.com/blog/images/cyber-security-best-practices-300420.png)















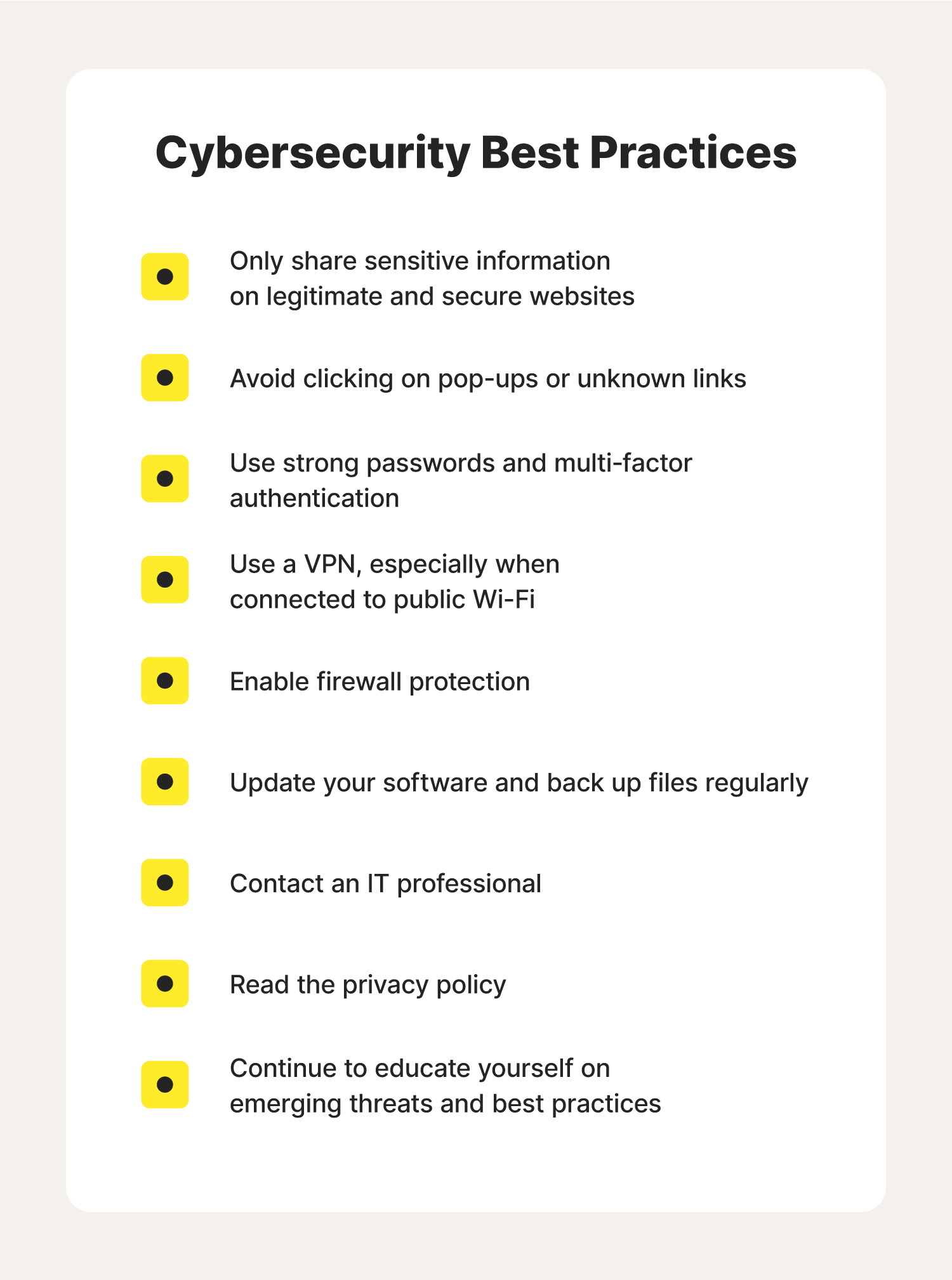
![Cyber Security Checklist [Infographic] - SecurityHQ](https://www.securityhq.com/wp-content/uploads/2022/08/SecurityHQ-Infographic-Cyber-Security-Checklist-531x1024.png)












.jpeg)
















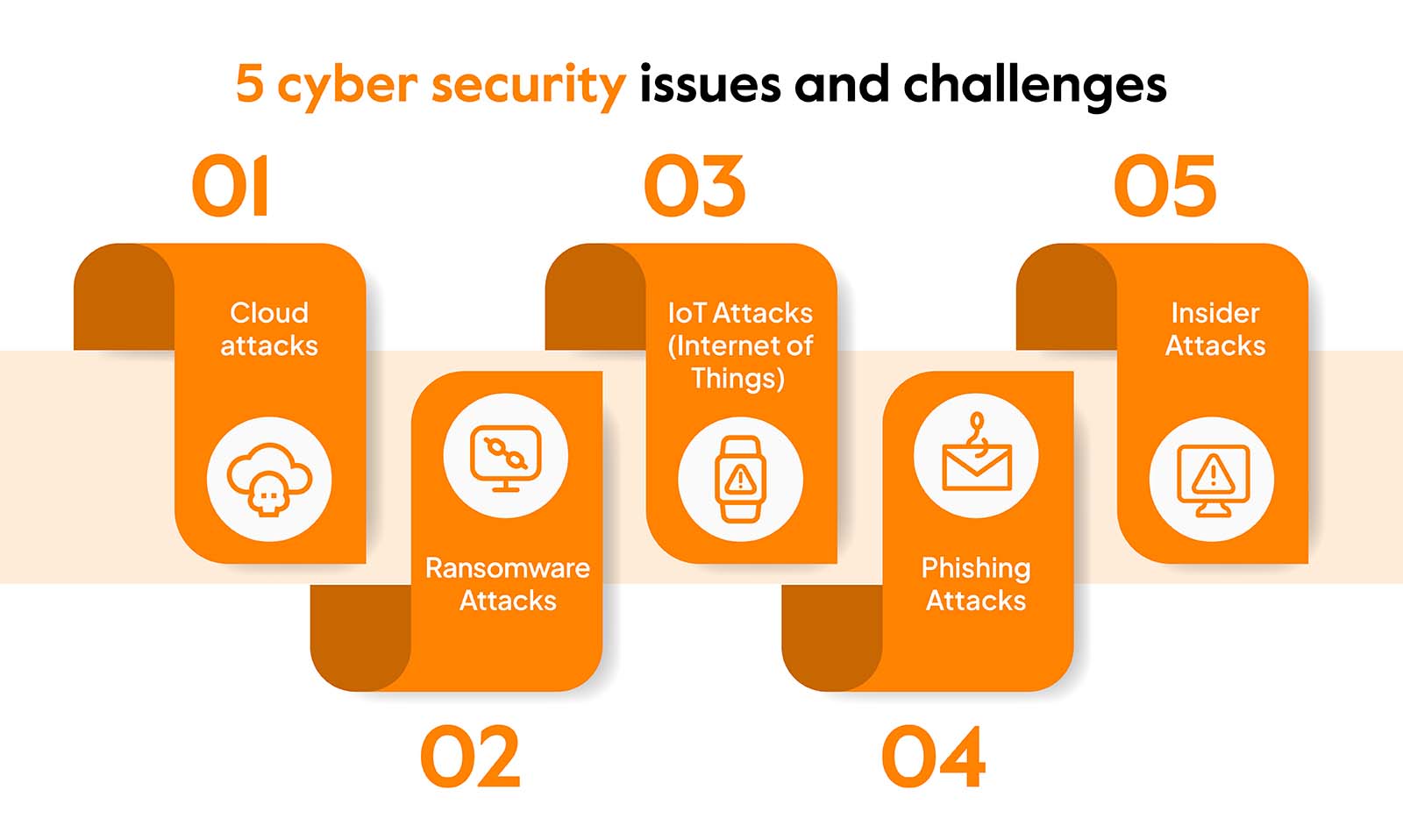



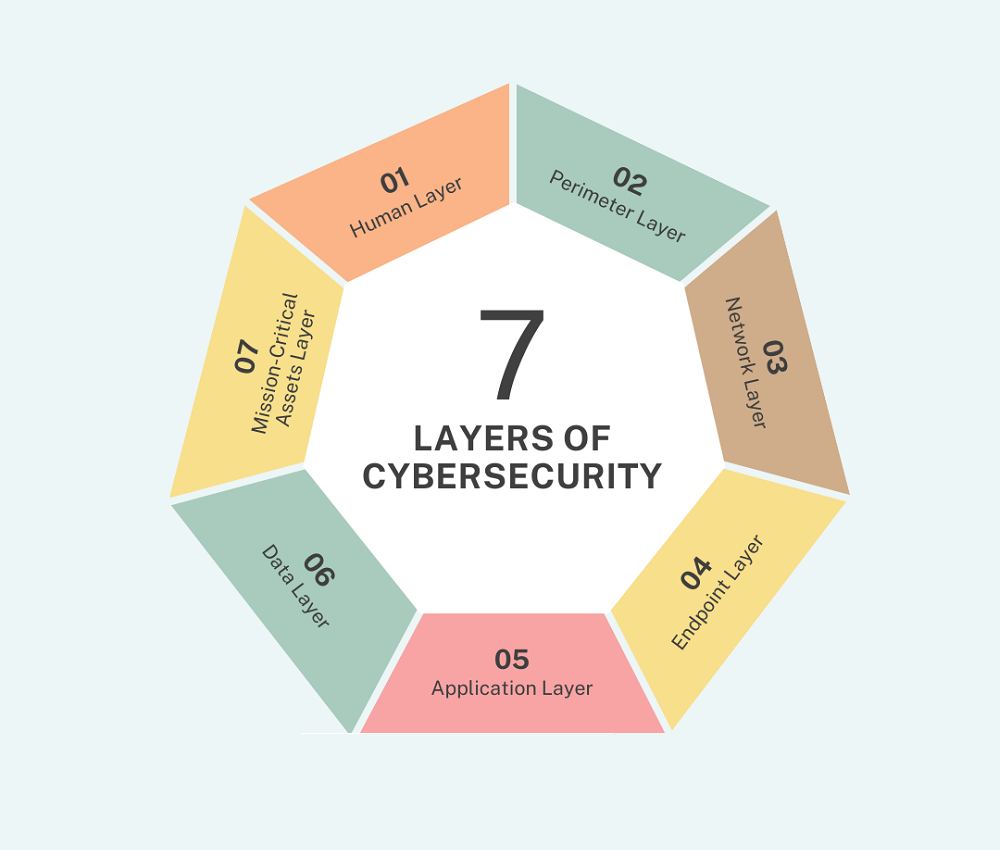





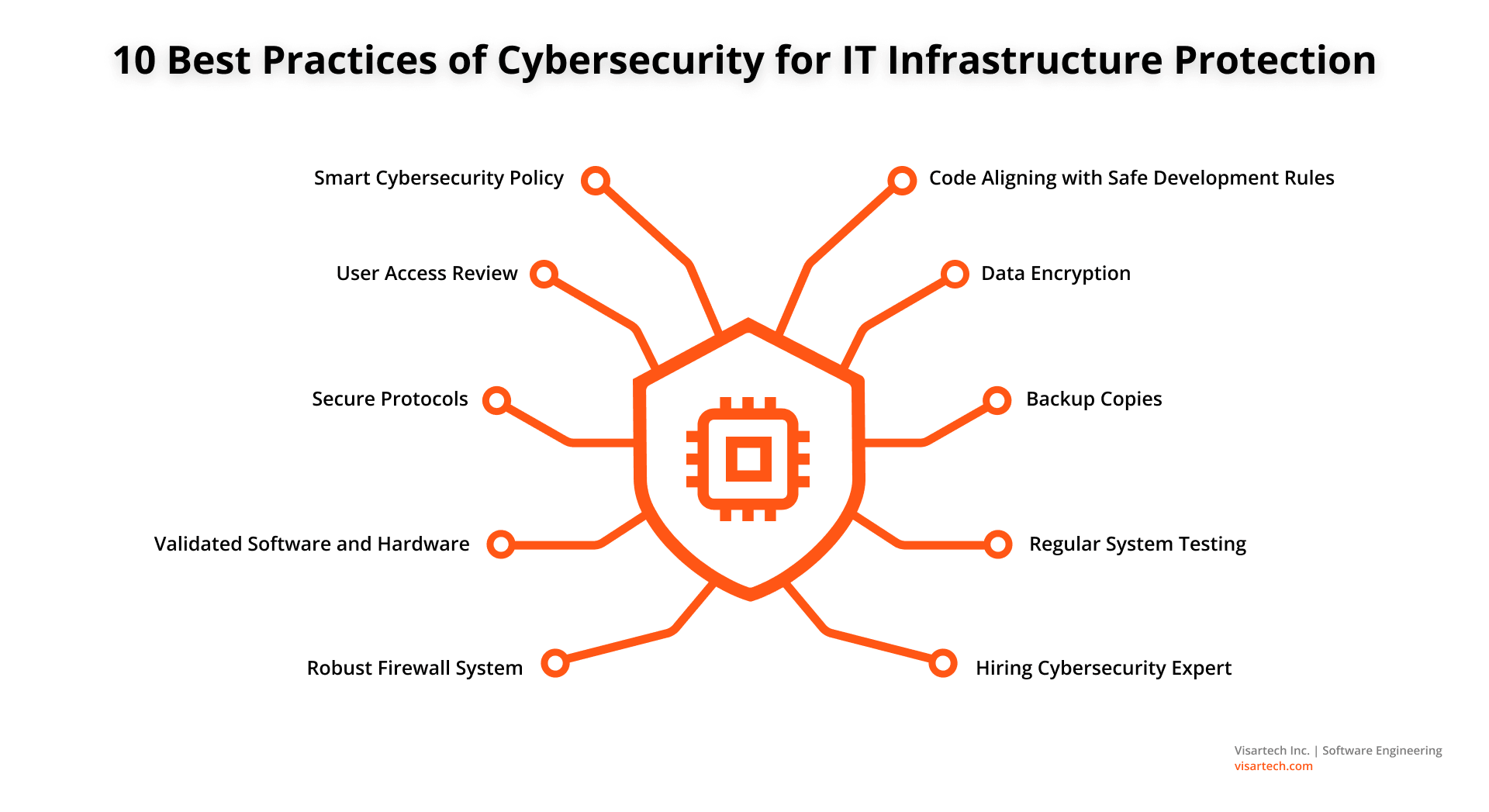
![[Checklist] 12 Top Tasks to Build a Business Cybersecurity Foundation](https://www.lhtservices.com/wp-content/uploads/2023/02/2023.1.27-Image-Cybersecurity-Checklist-PDF-1-768x1069.png)