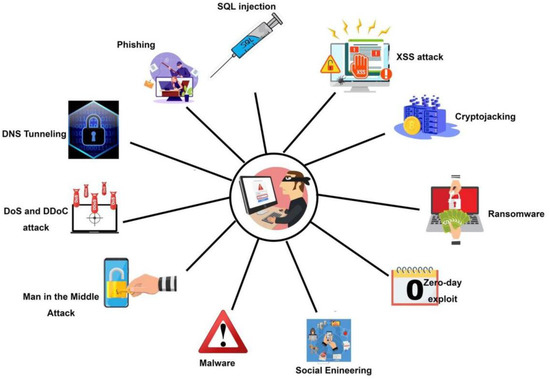
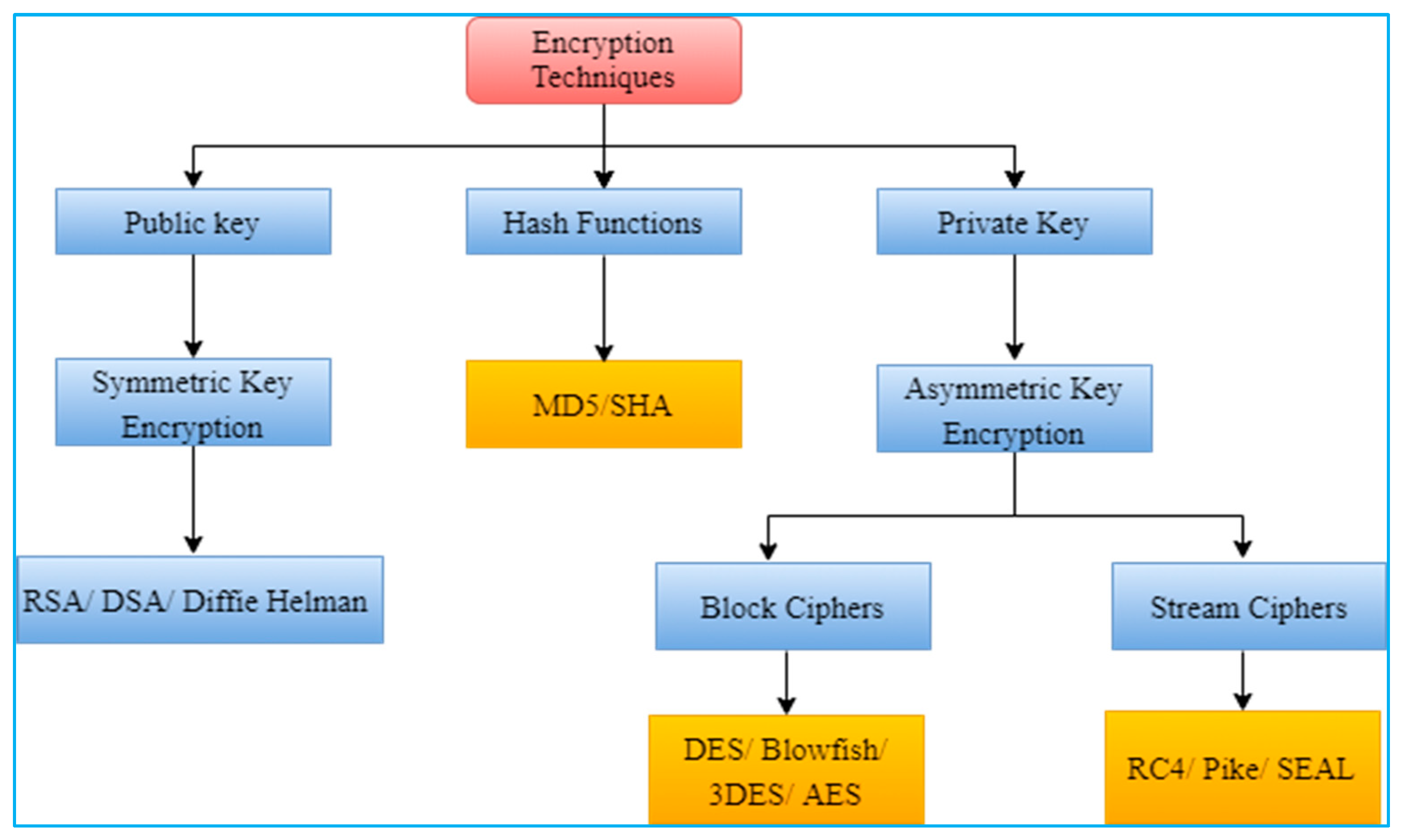
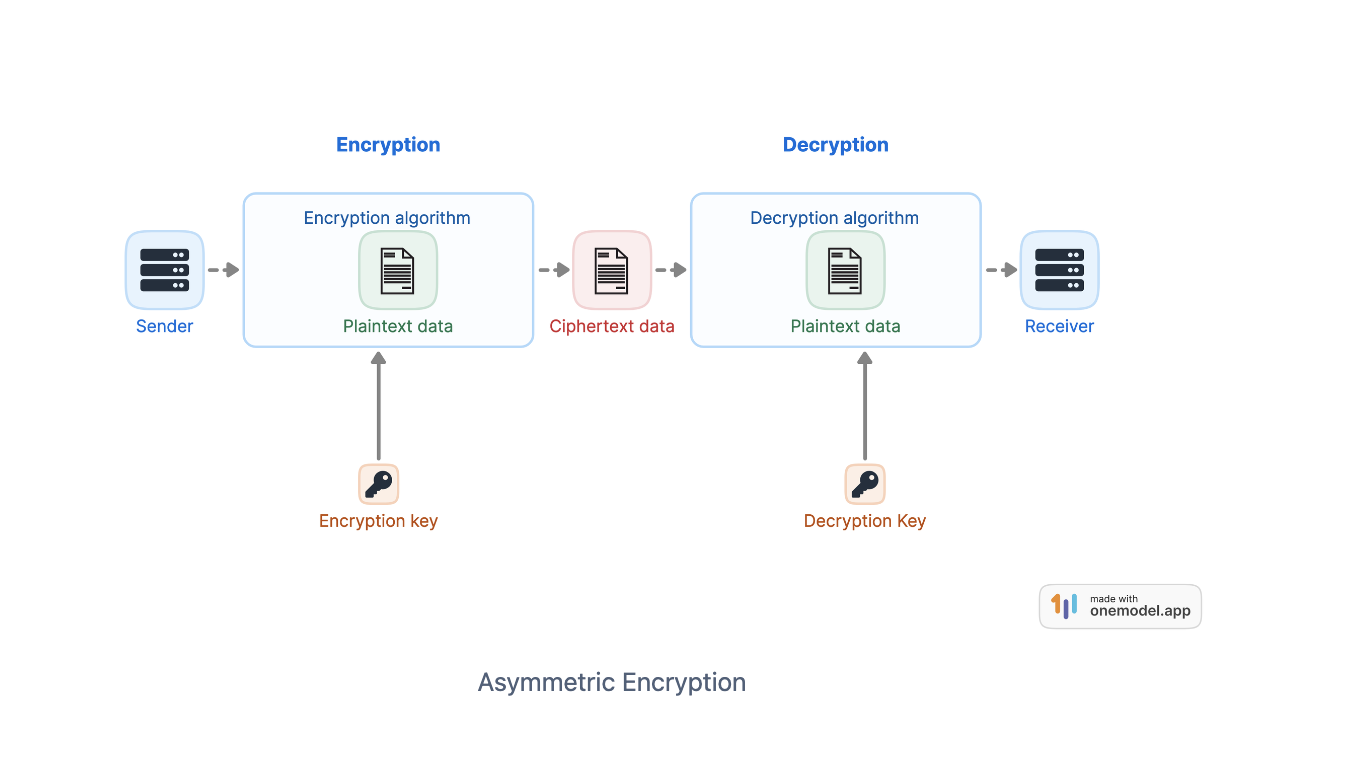
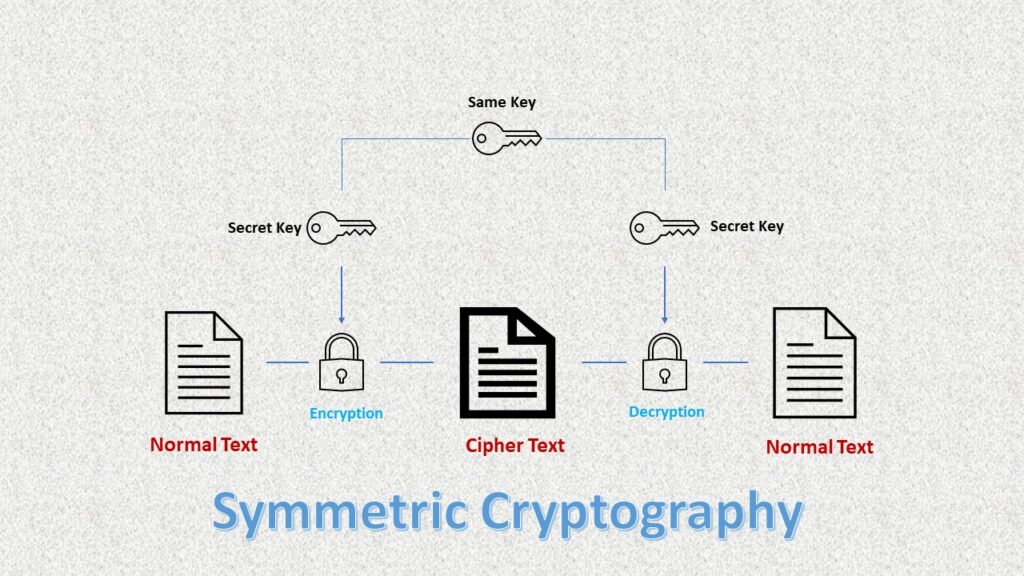
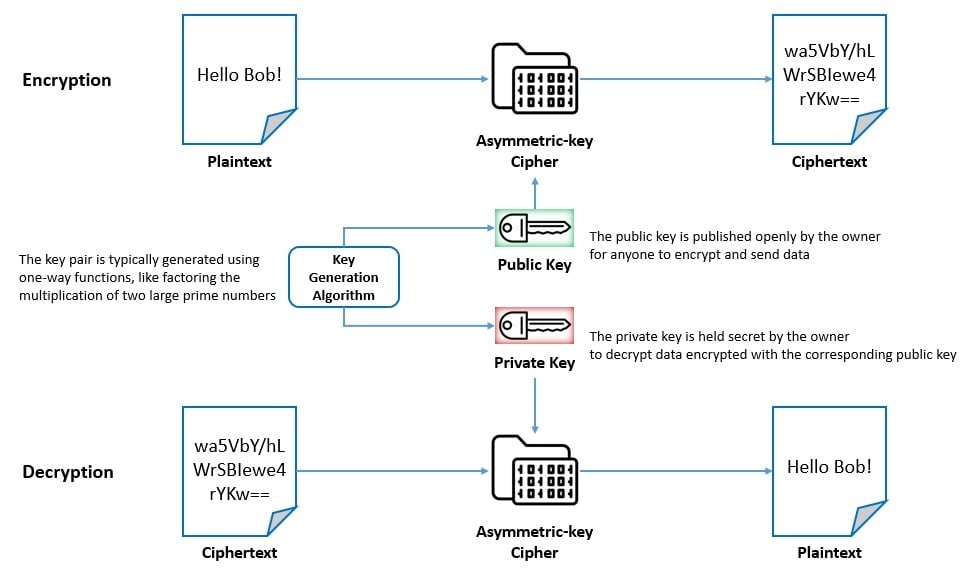
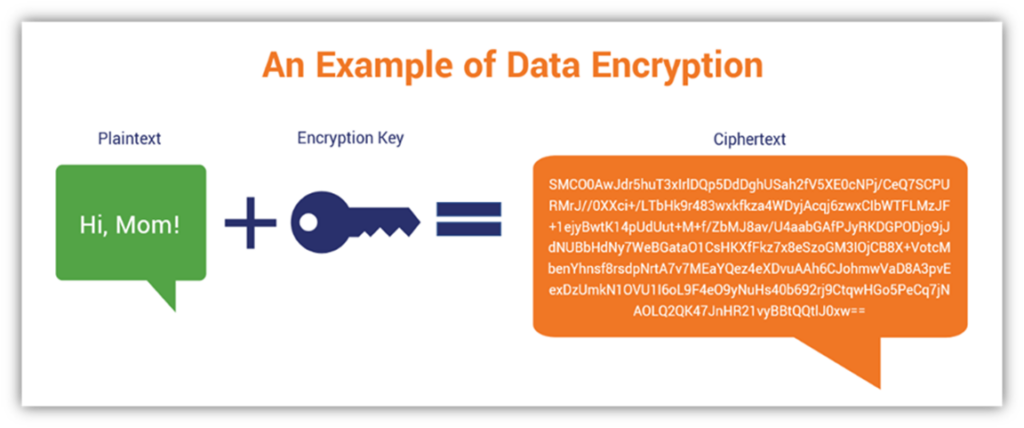
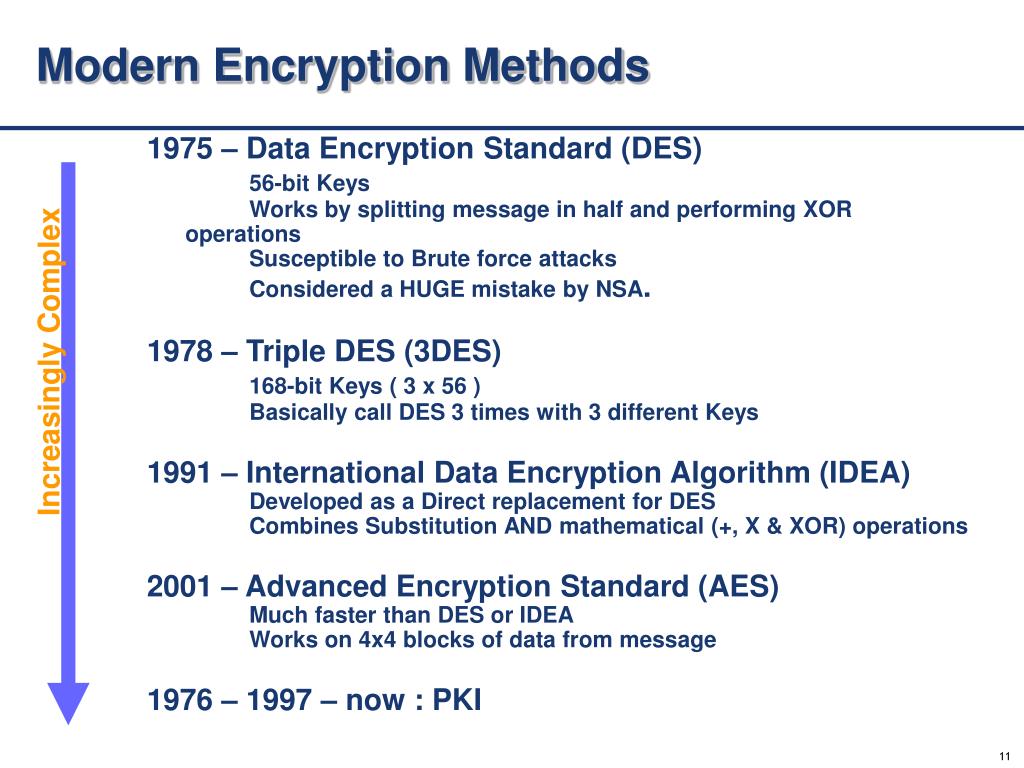
Indulge in the remarkable luxury of our a guide to common encryption algorithms in modern malware - 's collection with substantial collections of exquisite images. featuring elegant examples of photography, images, and pictures. ideal for luxury lifestyle publications. Each a guide to common encryption algorithms in modern malware - 's image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All a guide to common encryption algorithms in modern malware - 's images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect a guide to common encryption algorithms in modern malware - 's images to enhance your visual communication needs. Our a guide to common encryption algorithms in modern malware - 's database continuously expands with fresh, relevant content from skilled photographers. Cost-effective licensing makes professional a guide to common encryption algorithms in modern malware - 's photography accessible to all budgets. Professional licensing options accommodate both commercial and educational usage requirements. Regular updates keep the a guide to common encryption algorithms in modern malware - 's collection current with contemporary trends and styles.
















































.png)