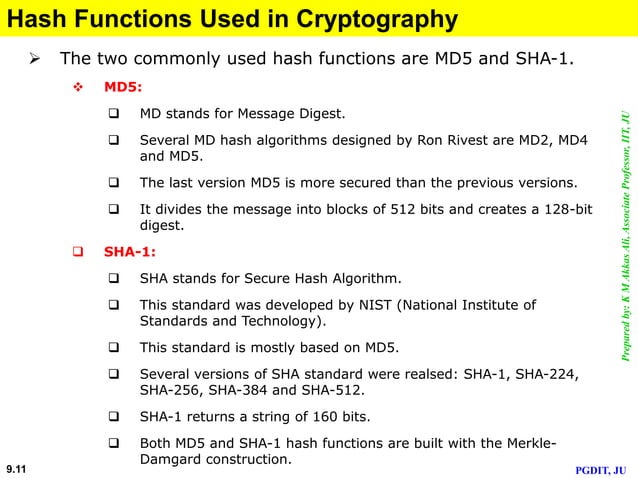
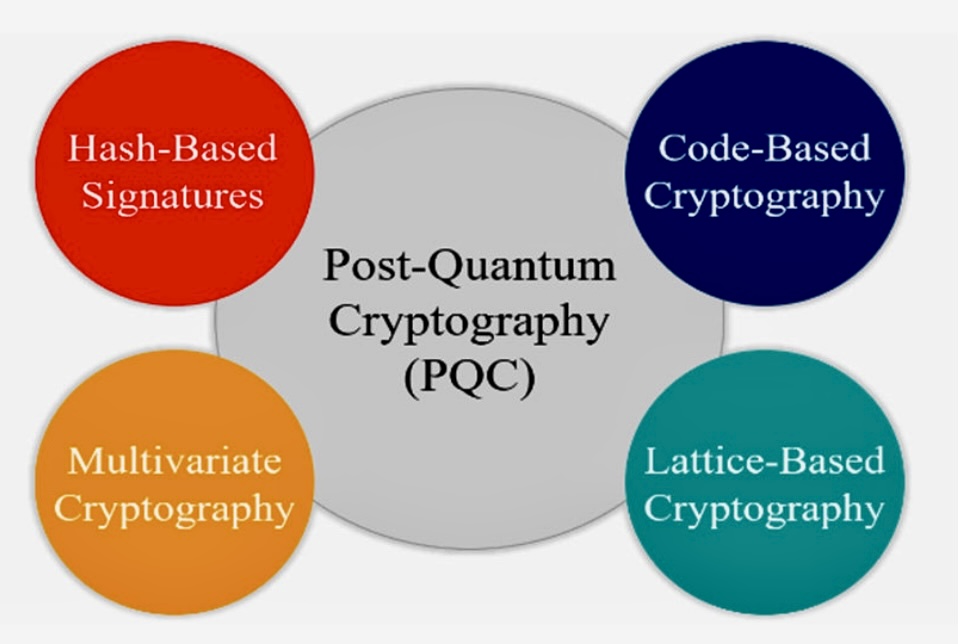
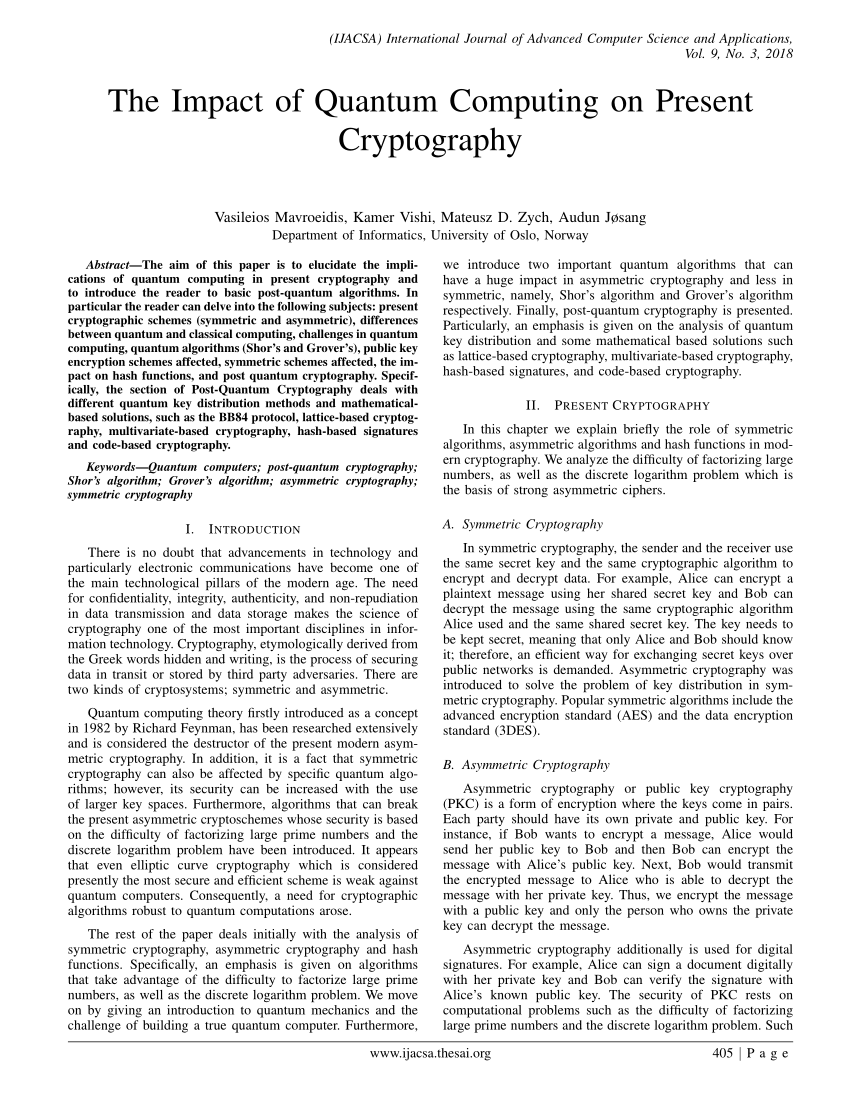
Experience the enduring appeal of can quantum computing compromise cryptographic hash functions securing with substantial collections of traditional images. honoring the classic elements of photography, images, and pictures. ideal for traditional publications and documentation. Our can quantum computing compromise cryptographic hash functions securing collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All can quantum computing compromise cryptographic hash functions securing images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our can quantum computing compromise cryptographic hash functions securing collection for various creative and professional projects. Instant download capabilities enable immediate access to chosen can quantum computing compromise cryptographic hash functions securing images. Whether for commercial projects or personal use, our can quantum computing compromise cryptographic hash functions securing collection delivers consistent excellence. Cost-effective licensing makes professional can quantum computing compromise cryptographic hash functions securing photography accessible to all budgets. Reliable customer support ensures smooth experience throughout the can quantum computing compromise cryptographic hash functions securing selection process. Comprehensive tagging systems facilitate quick discovery of relevant can quantum computing compromise cryptographic hash functions securing content.

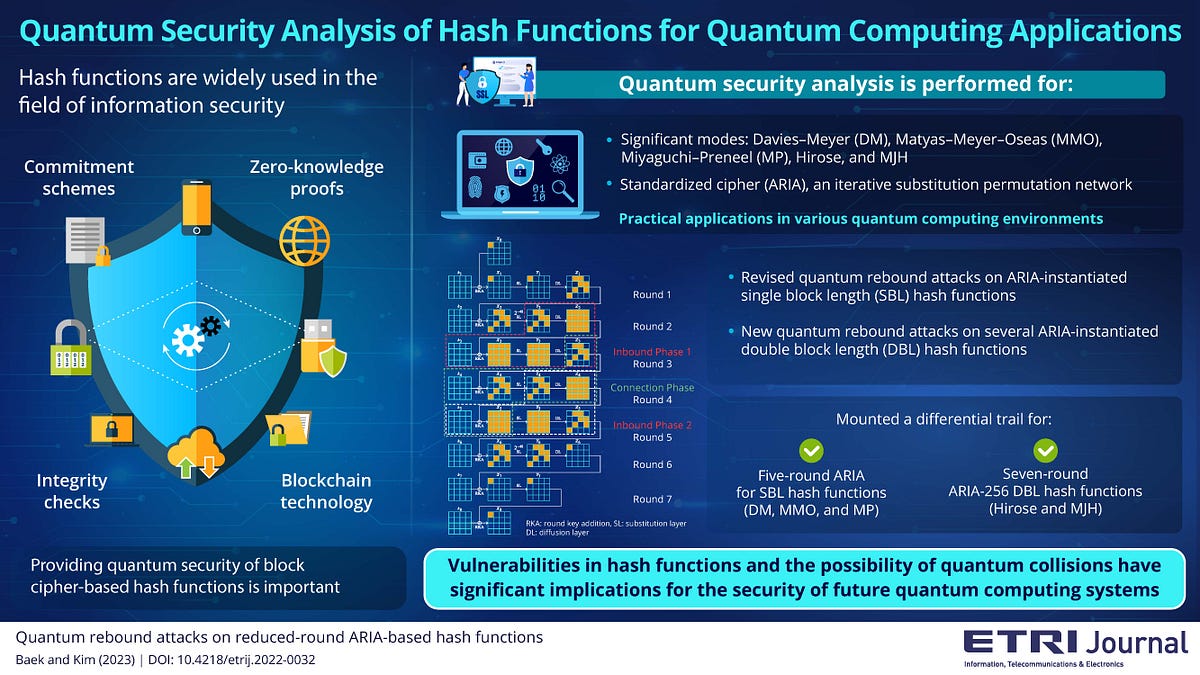



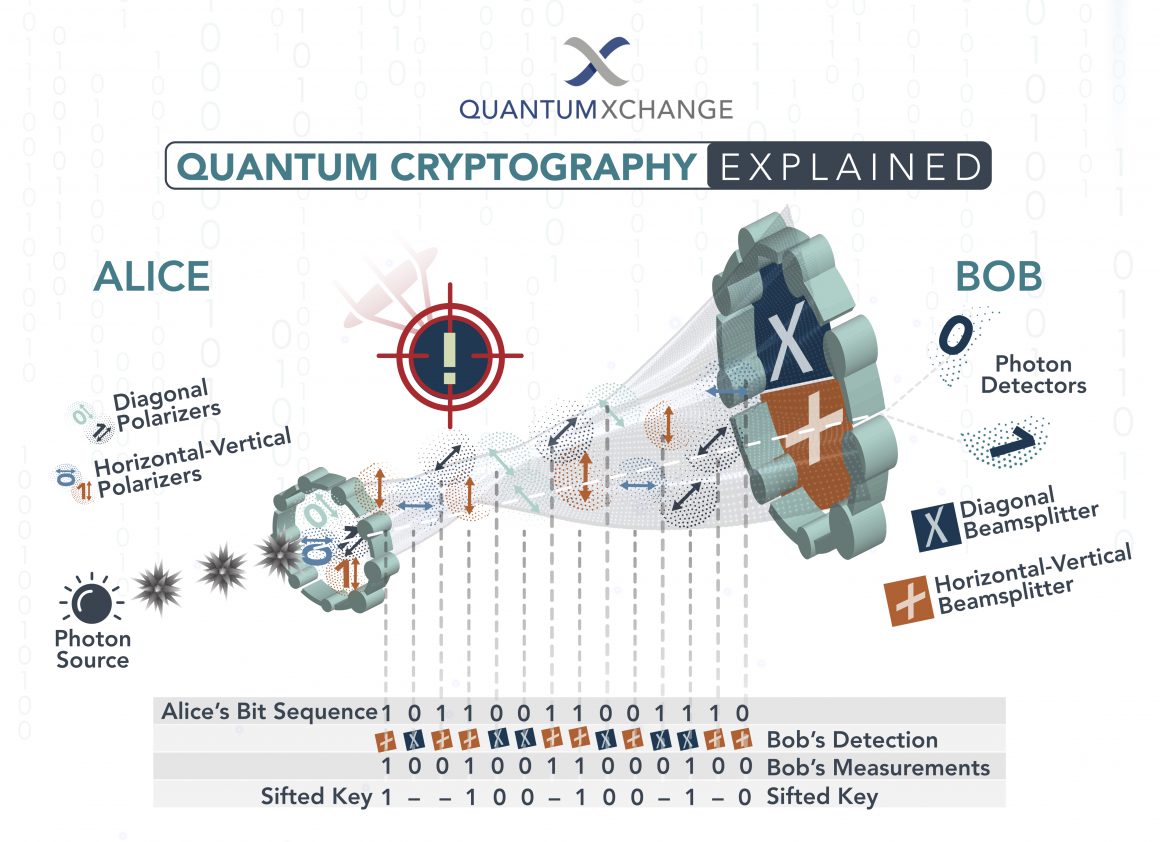



















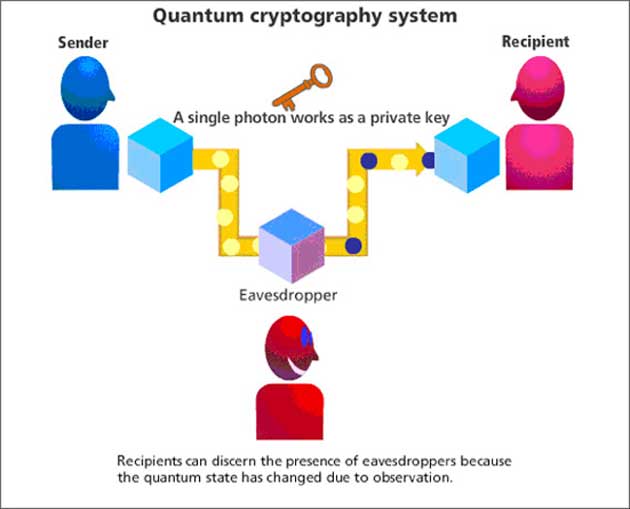

:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
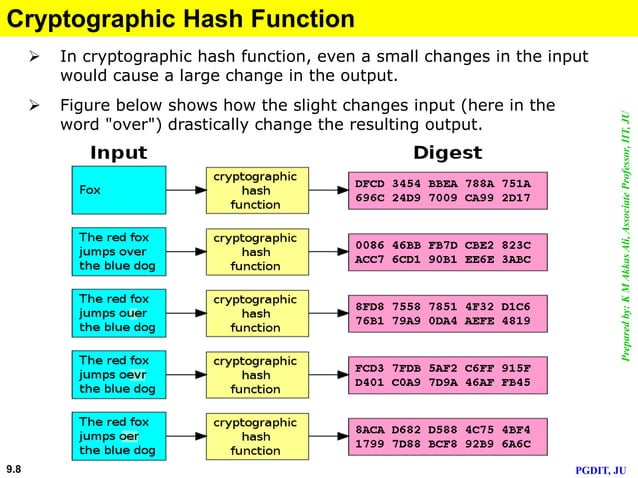










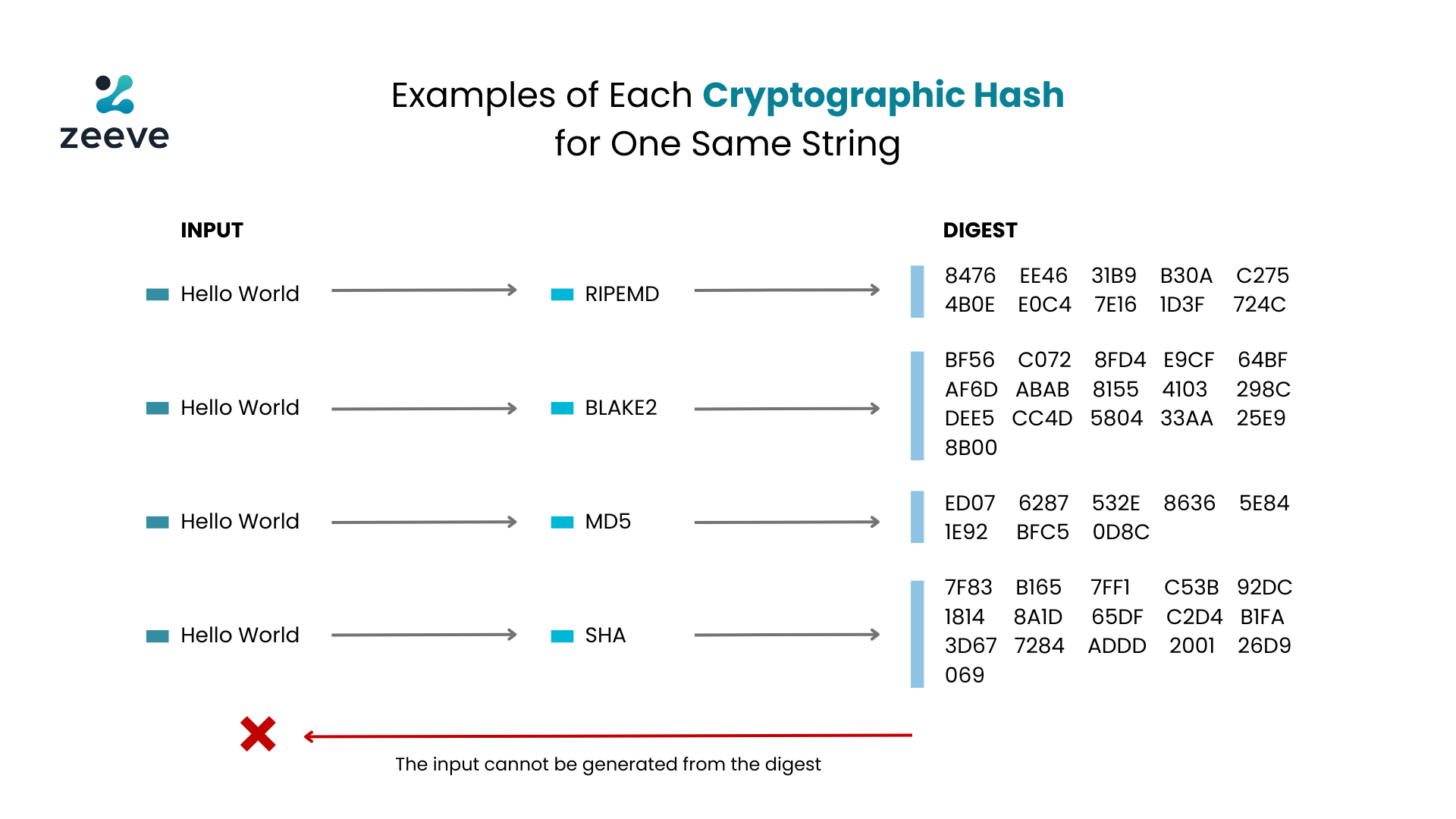




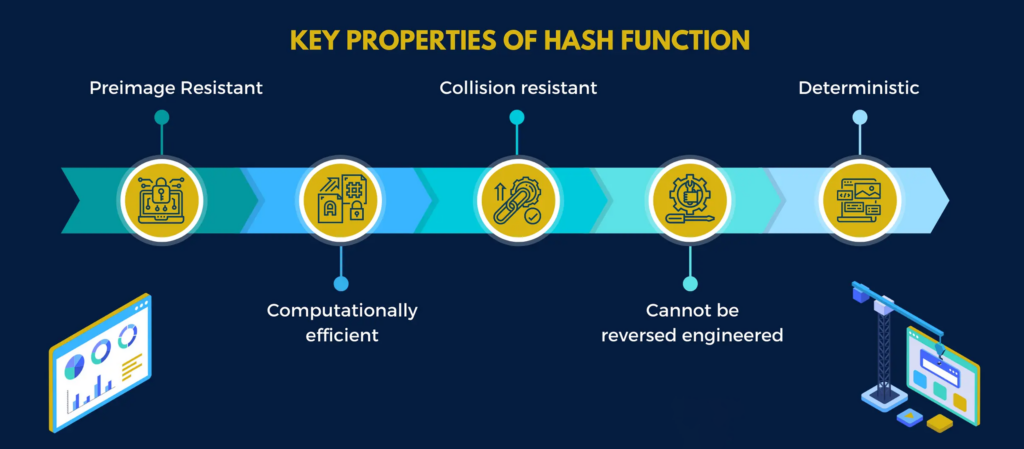


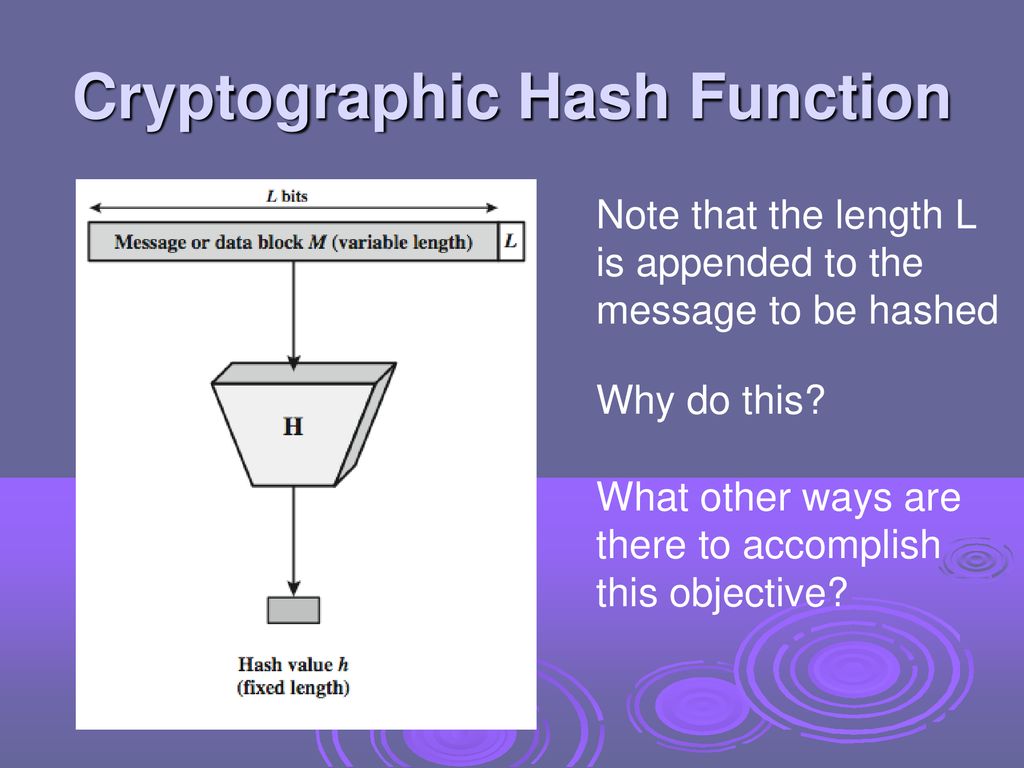



.jpg)












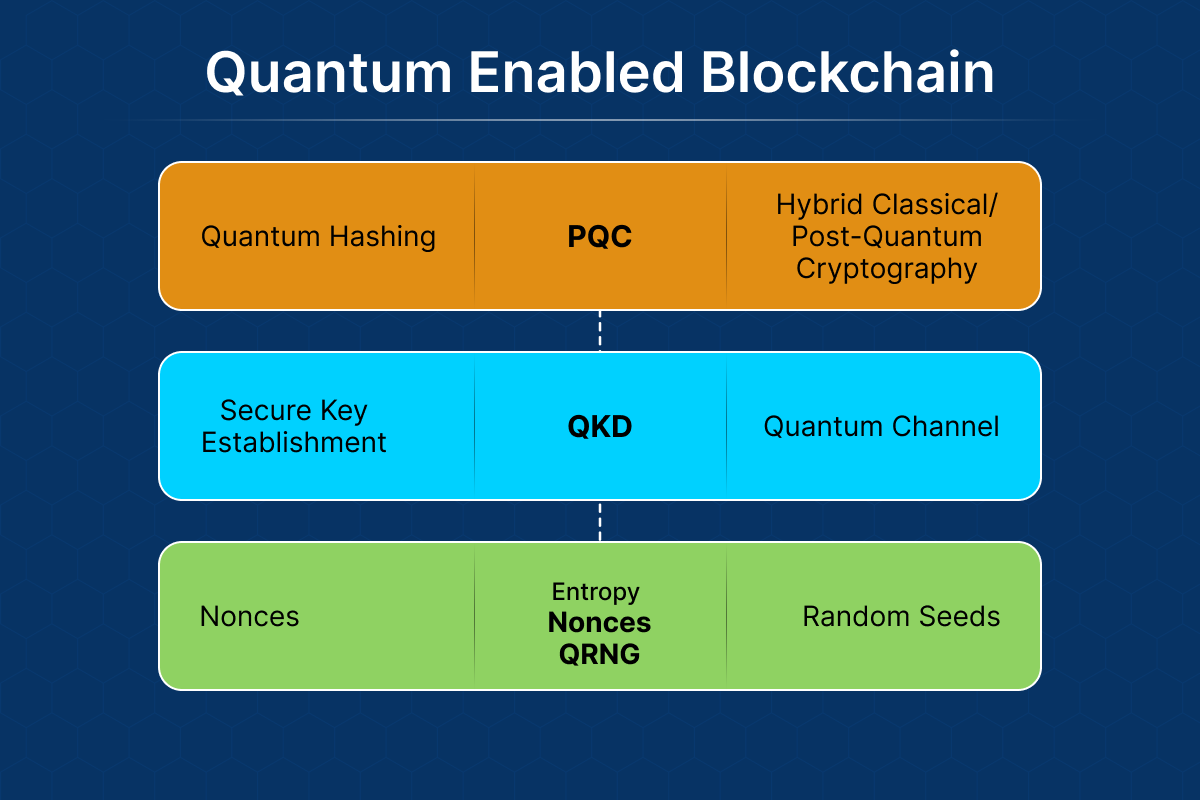
.png)