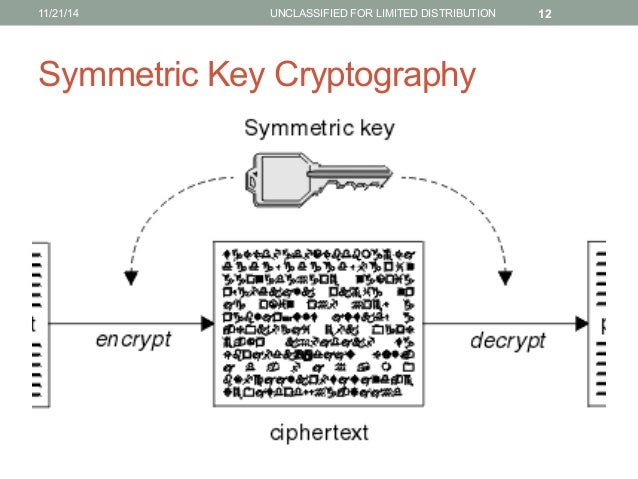
Experience the creative potential of cryptography basics - sobyte with our collection of countless artistic photographs. merging documentary precision with creative imagination and aesthetic beauty. inspiring creativity and emotional connection through visual excellence. Our cryptography basics - sobyte collection features high-quality images with excellent detail and clarity. Ideal for artistic projects, creative designs, digital art, and innovative visual expressions All cryptography basics - sobyte images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Each cryptography basics - sobyte image offers fresh perspectives that enhance creative projects and visual storytelling. Multiple resolution options ensure optimal performance across different platforms and applications. Regular updates keep the cryptography basics - sobyte collection current with contemporary trends and styles. The cryptography basics - sobyte collection represents years of careful curation and professional standards. Instant download capabilities enable immediate access to chosen cryptography basics - sobyte images. Advanced search capabilities make finding the perfect cryptography basics - sobyte image effortless and efficient. Each image in our cryptography basics - sobyte gallery undergoes rigorous quality assessment before inclusion. Comprehensive tagging systems facilitate quick discovery of relevant cryptography basics - sobyte content.
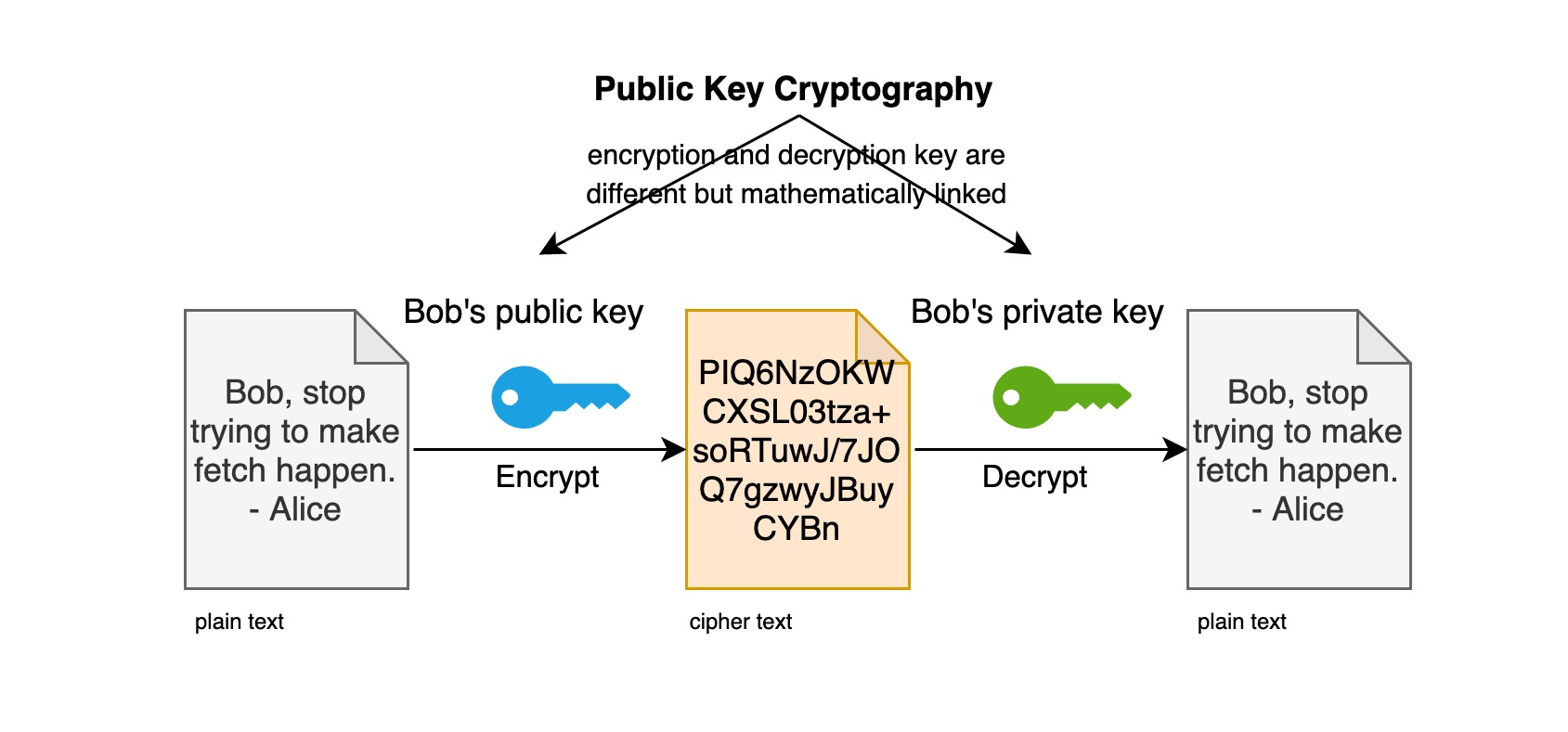
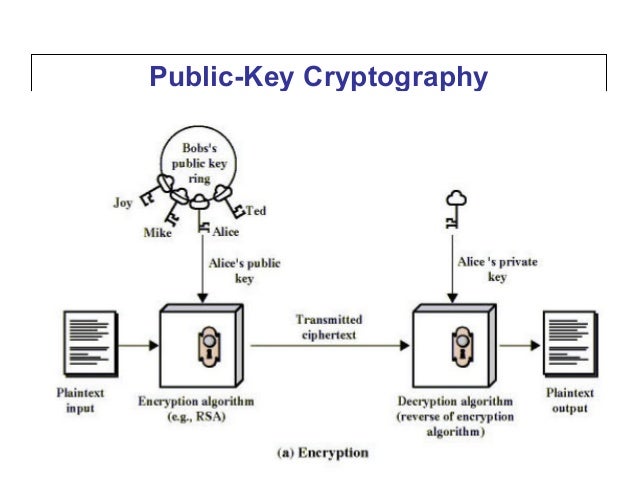

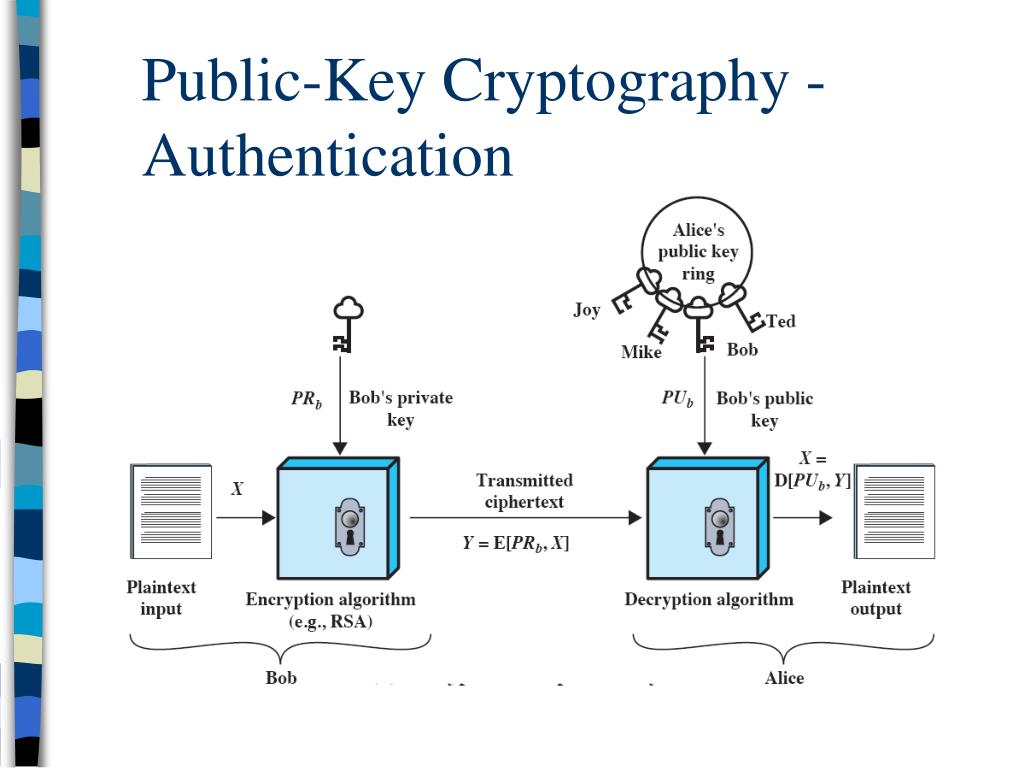

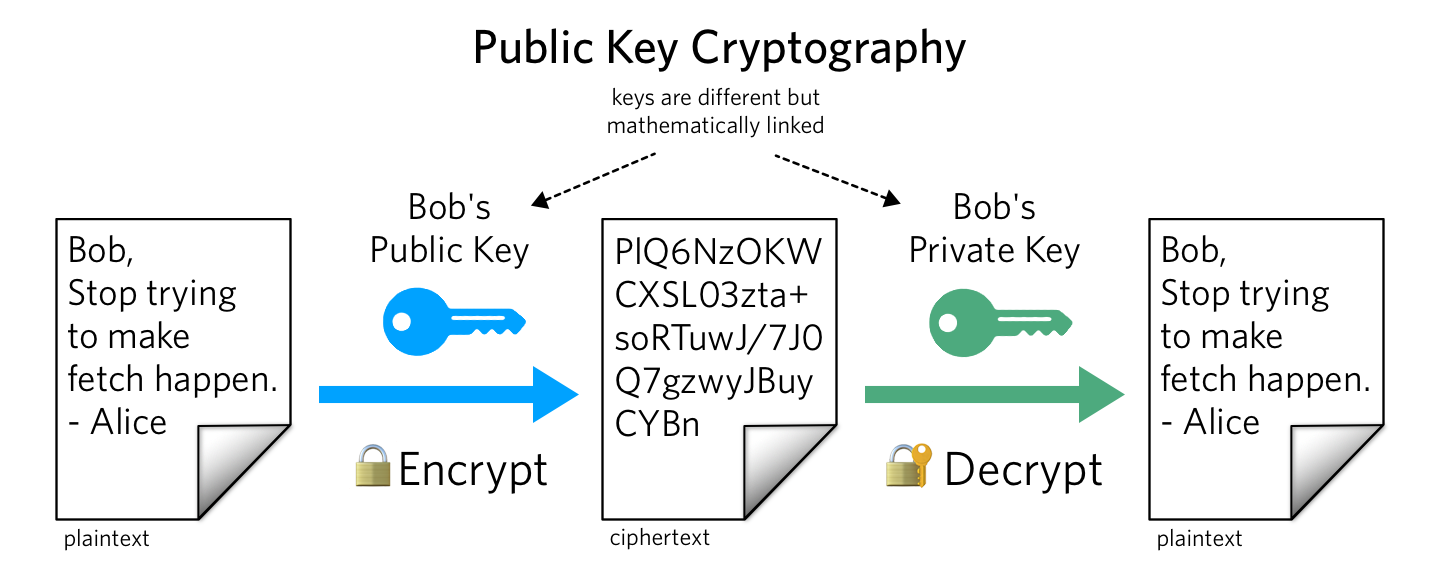
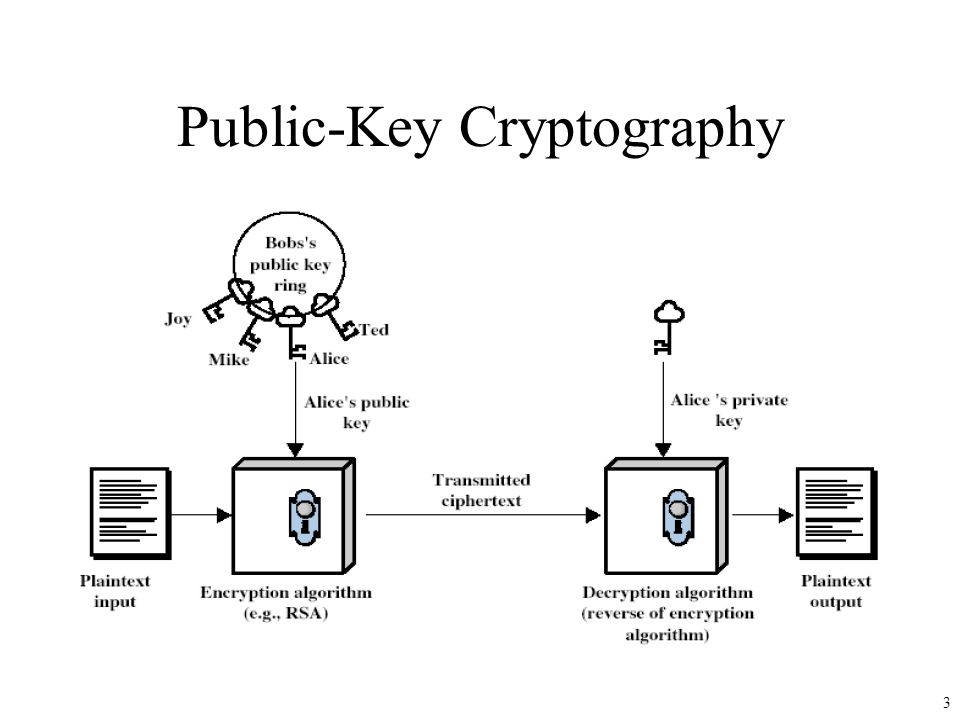
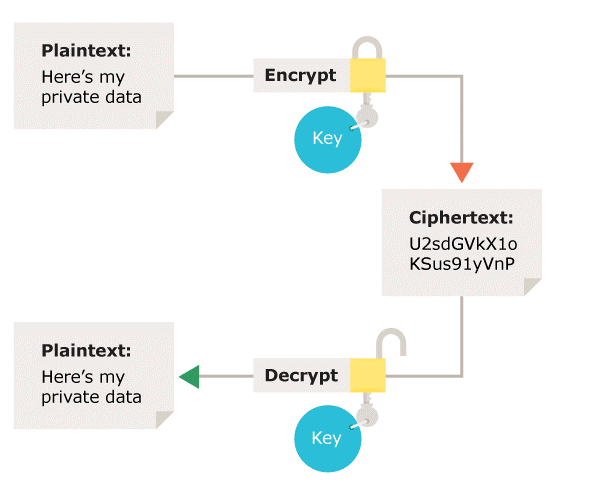




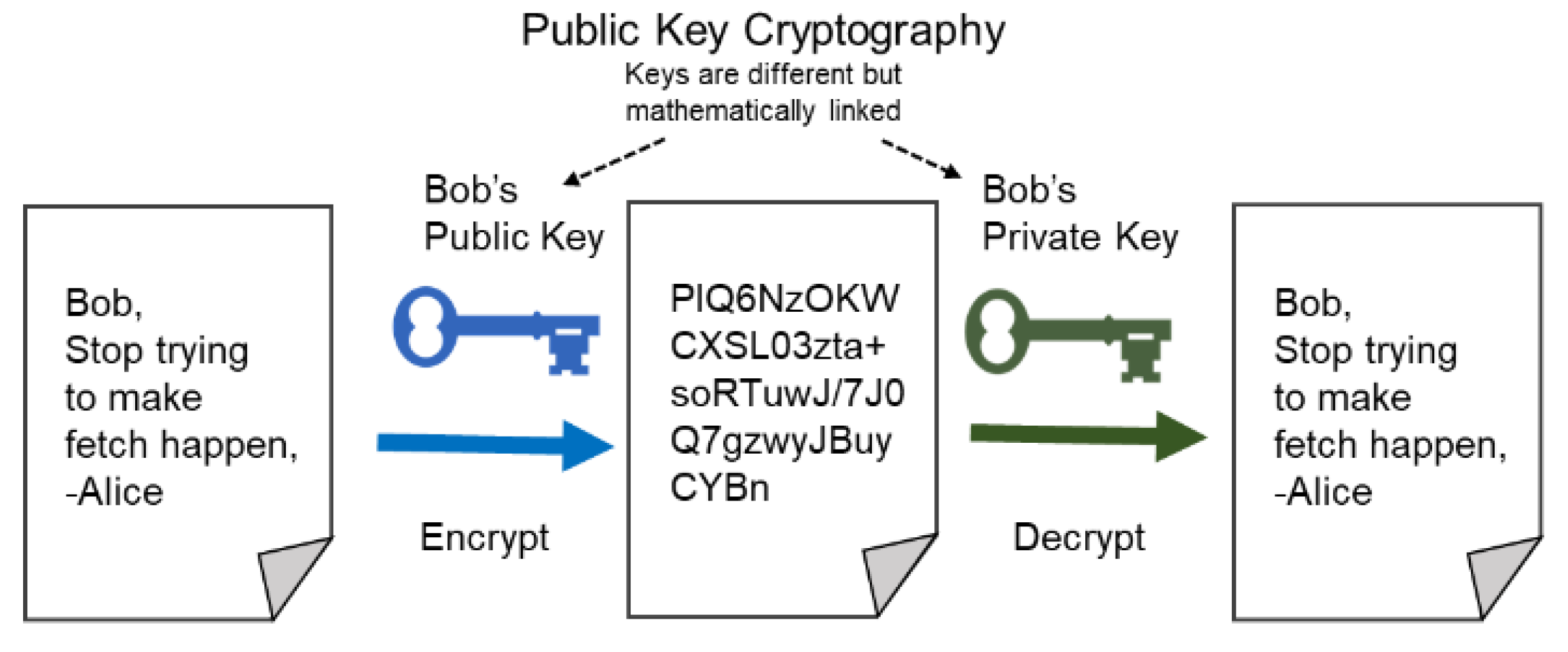


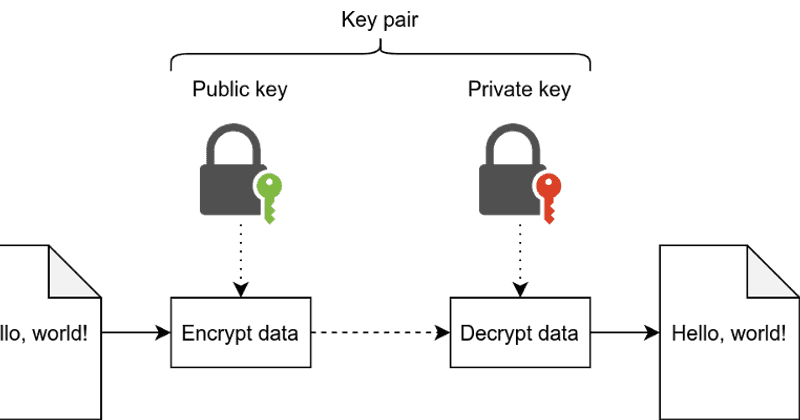
![Proposed system model [5] | Download Scientific Diagram](https://www.researchgate.net/profile/Ani-Boneva-2/publication/363528433/figure/fig2/AS:11431281084288358@1663122079472/Proposed-system-model-5_Q320.jpg)


![Identity Based Encryption System [11] | Download Scientific Diagram](https://www.researchgate.net/profile/Neela-Madheswari/publication/344924540/figure/fig2/AS:951525044129794@1603872657332/Identity-Based-Encryption-System-11_Q320.jpg)




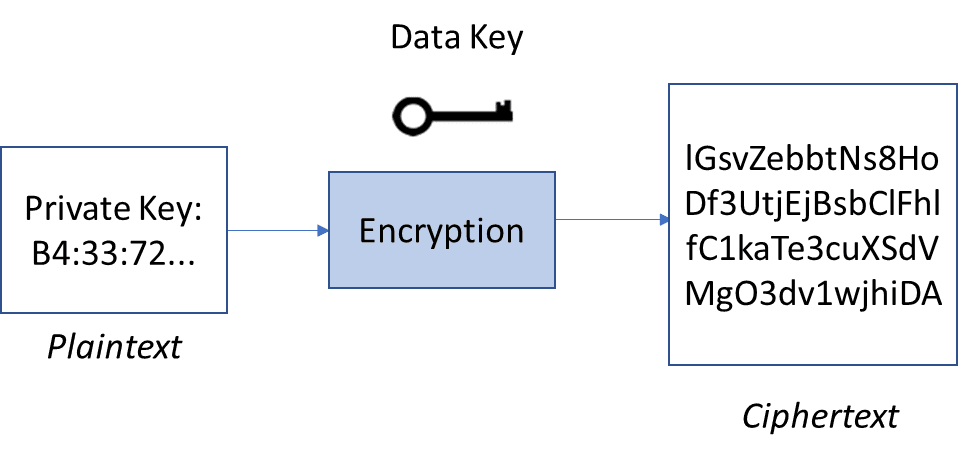




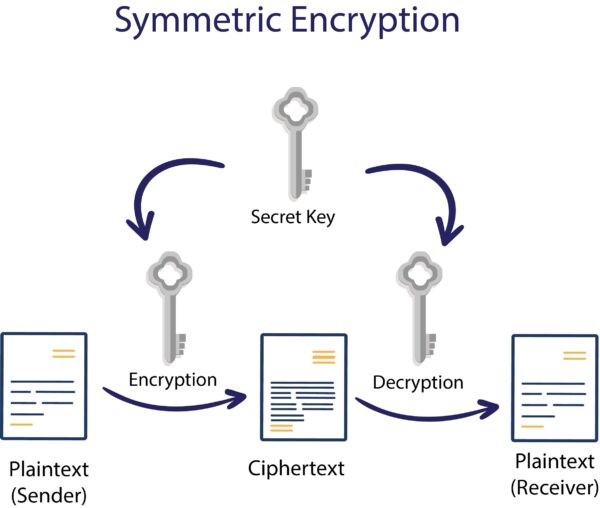
![Asymmetric Cryptography System [7] For this paper, the proposed ...](https://www.researchgate.net/profile/Gerald-Arada/publication/354185308/figure/fig2/AS:1061779438325760@1630159353052/Asymmetric-Cryptography-System-7-For-this-paper-the-proposed-algorithm-is-compared-to.jpg)