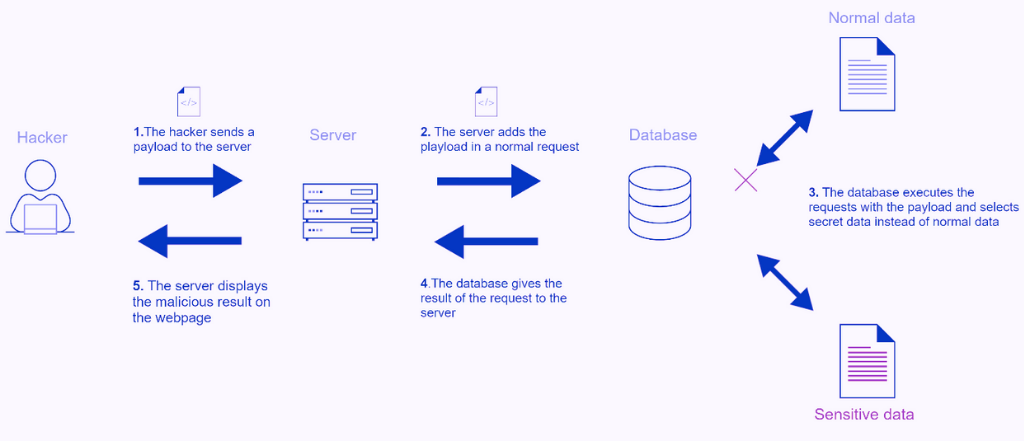
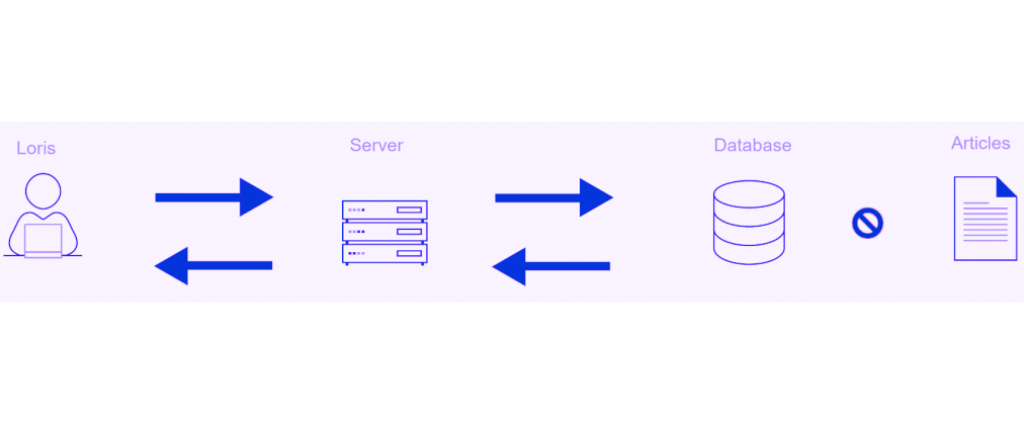
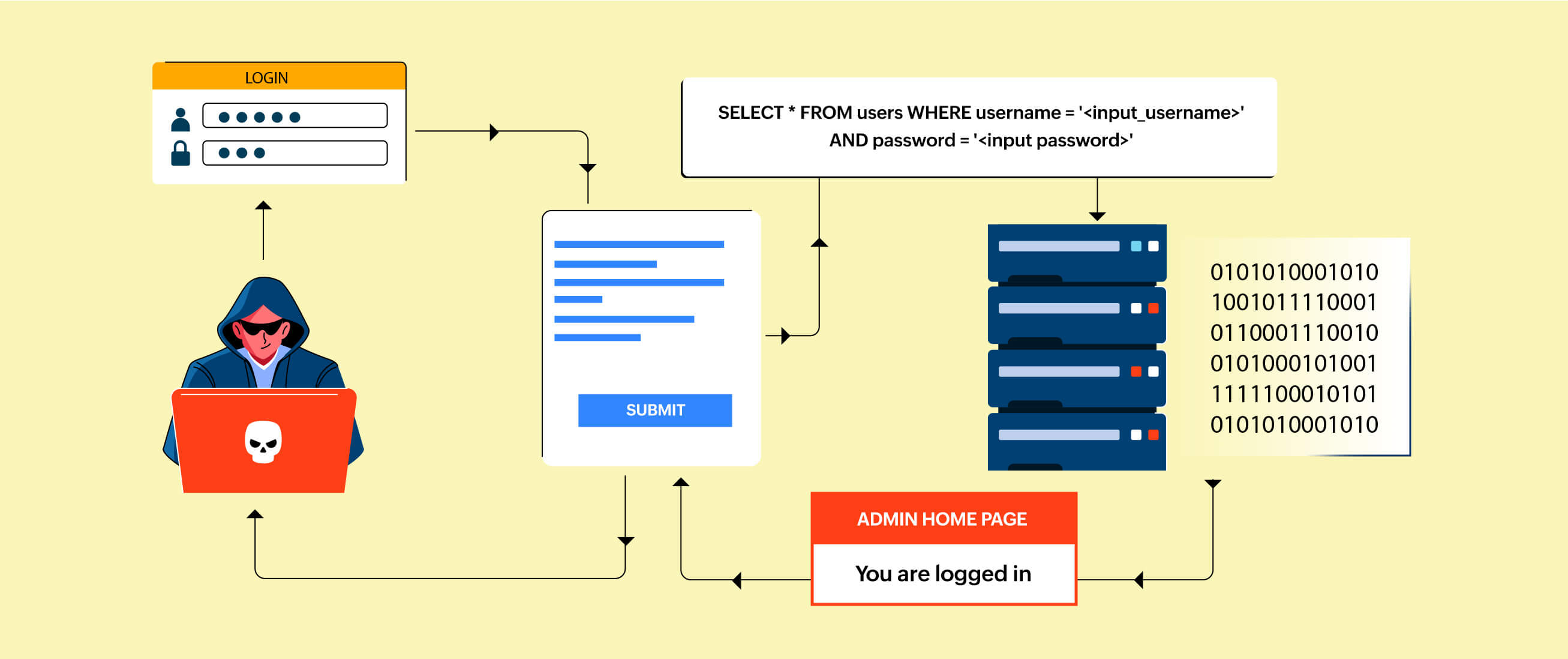
Document the past through vast arrays of historically-significant a typical illustration of sql injection attack. | download scientific photographs. heritage-preserving showcasing photography, images, and pictures. perfect for historical documentation and education. The a typical illustration of sql injection attack. | download scientific collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All a typical illustration of sql injection attack. | download scientific images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect a typical illustration of sql injection attack. | download scientific images to enhance your visual communication needs. Whether for commercial projects or personal use, our a typical illustration of sql injection attack. | download scientific collection delivers consistent excellence. Reliable customer support ensures smooth experience throughout the a typical illustration of sql injection attack. | download scientific selection process. Cost-effective licensing makes professional a typical illustration of sql injection attack. | download scientific photography accessible to all budgets. The a typical illustration of sql injection attack. | download scientific collection represents years of careful curation and professional standards. The a typical illustration of sql injection attack. | download scientific archive serves professionals, educators, and creatives across diverse industries.












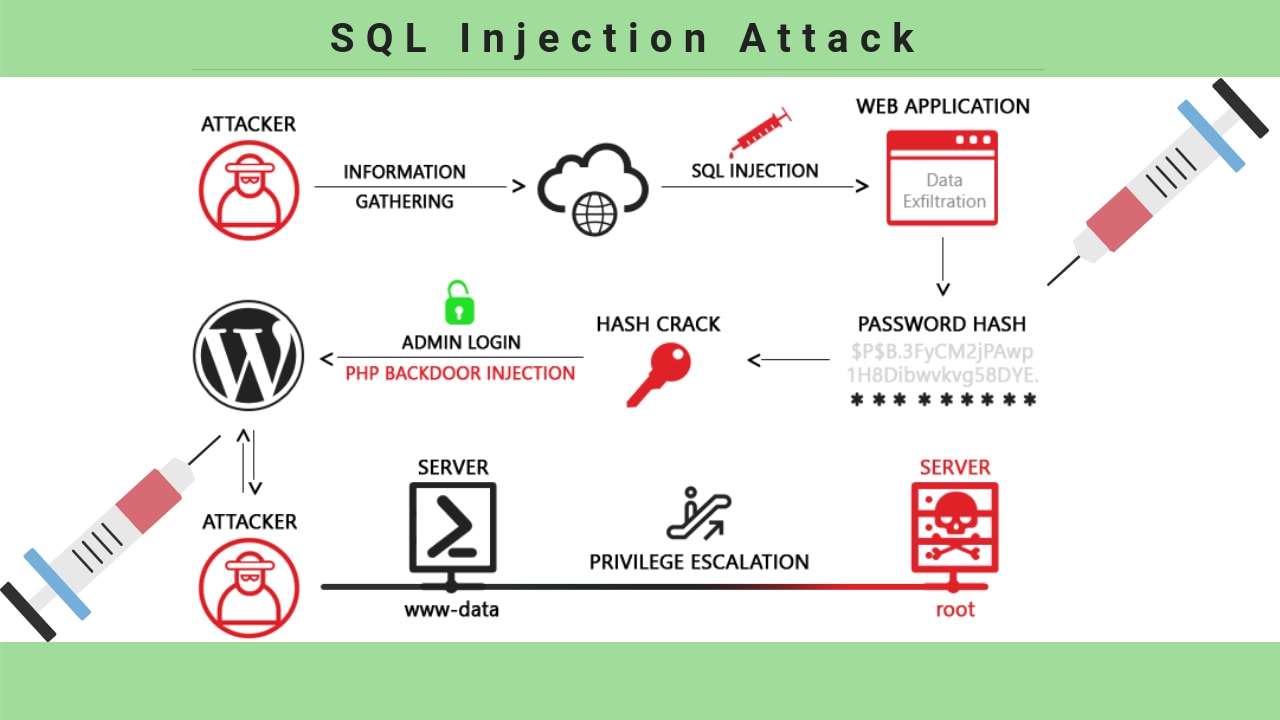


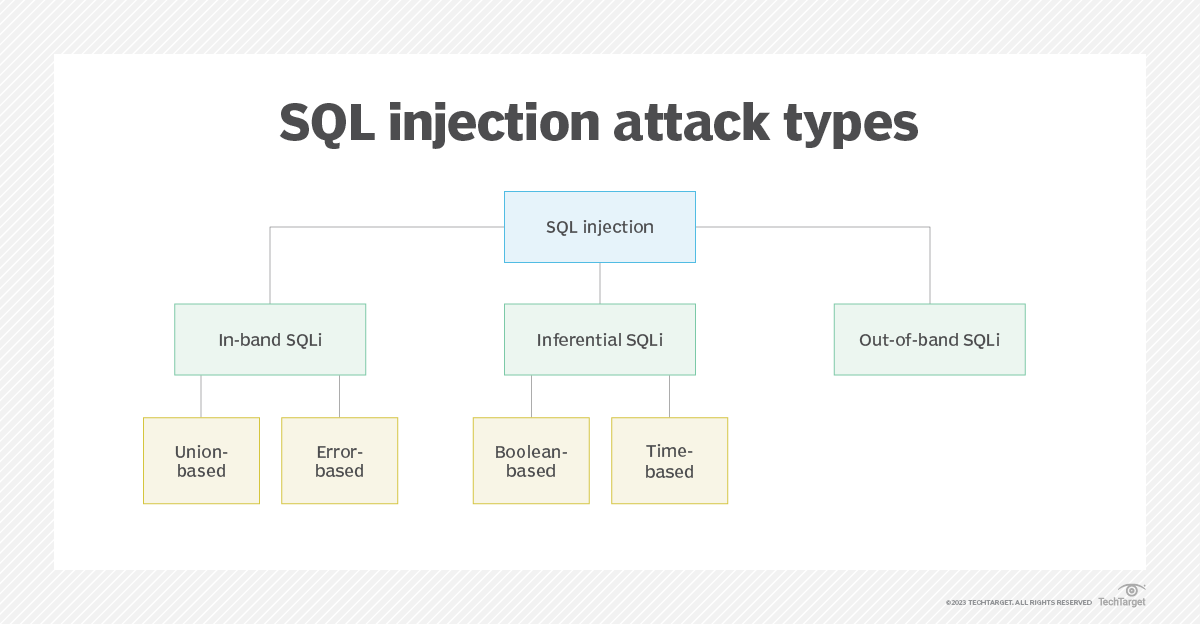

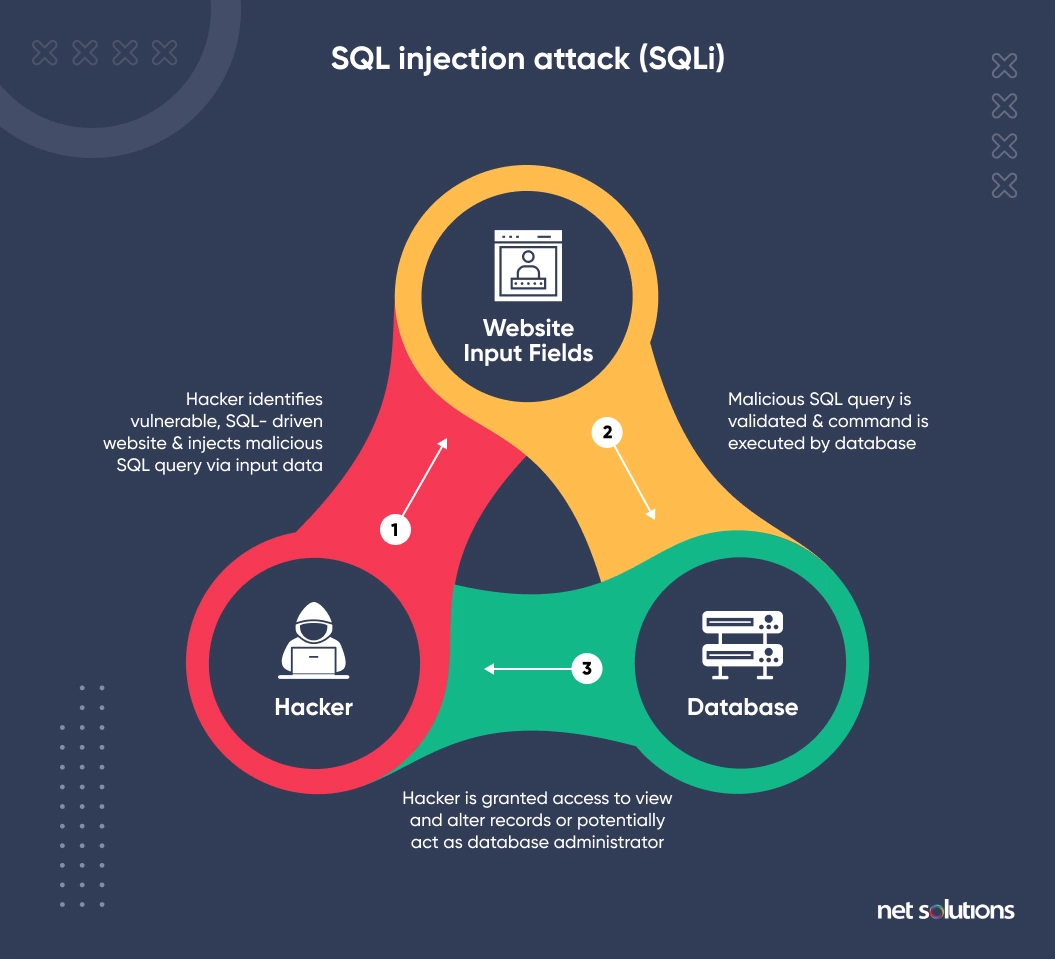




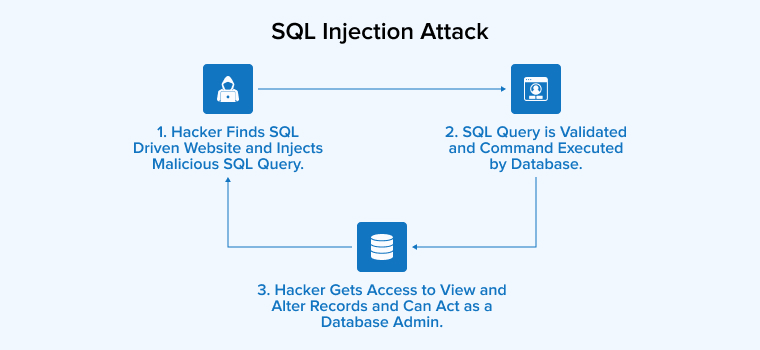

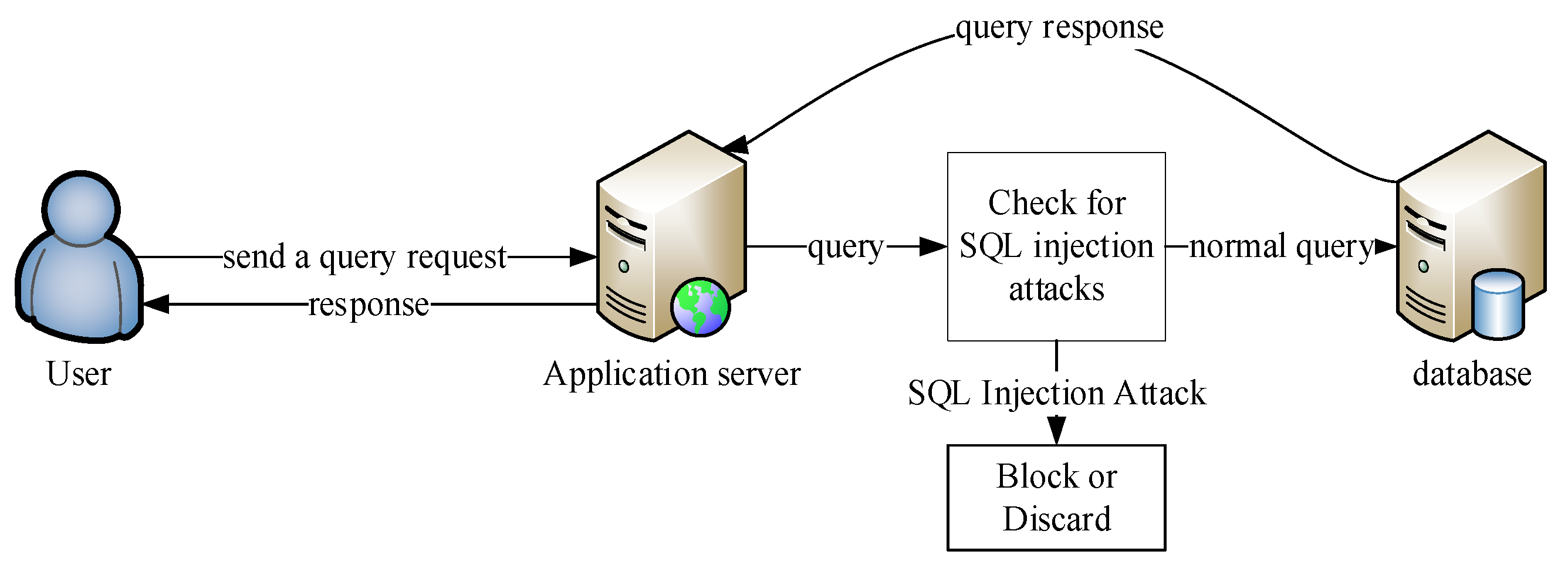
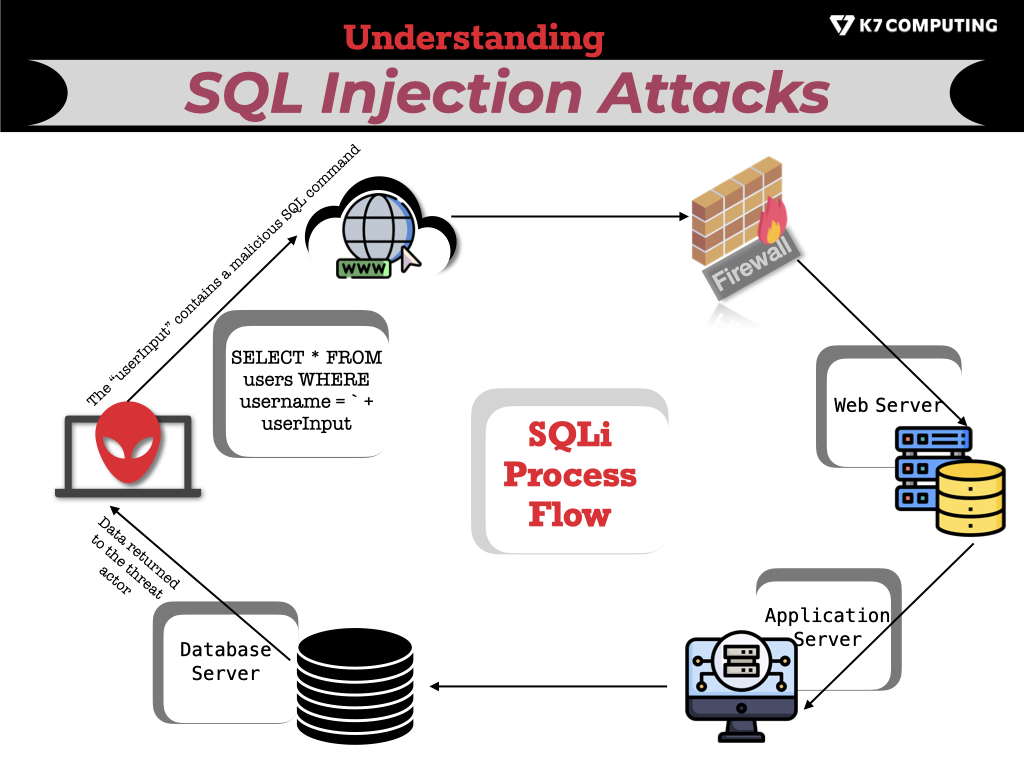
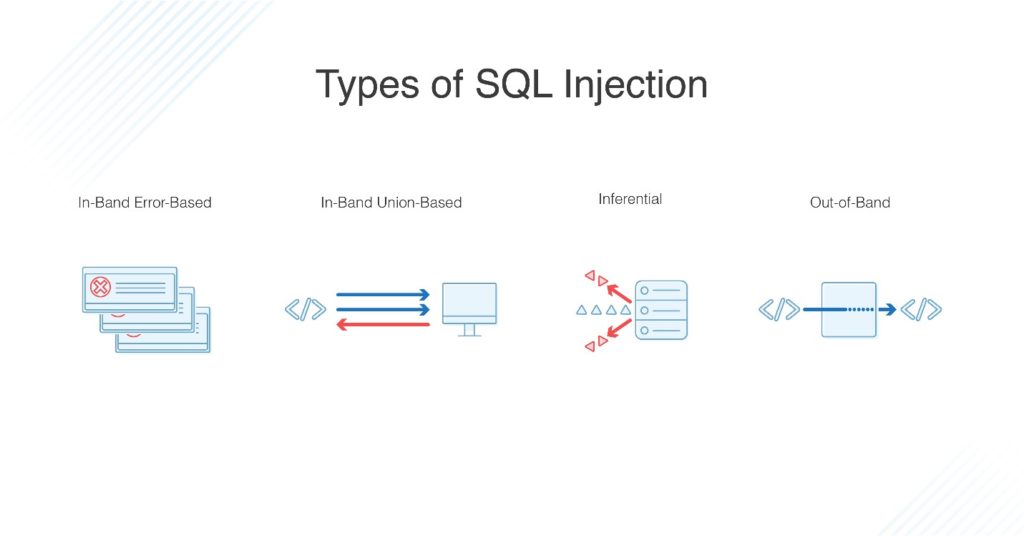
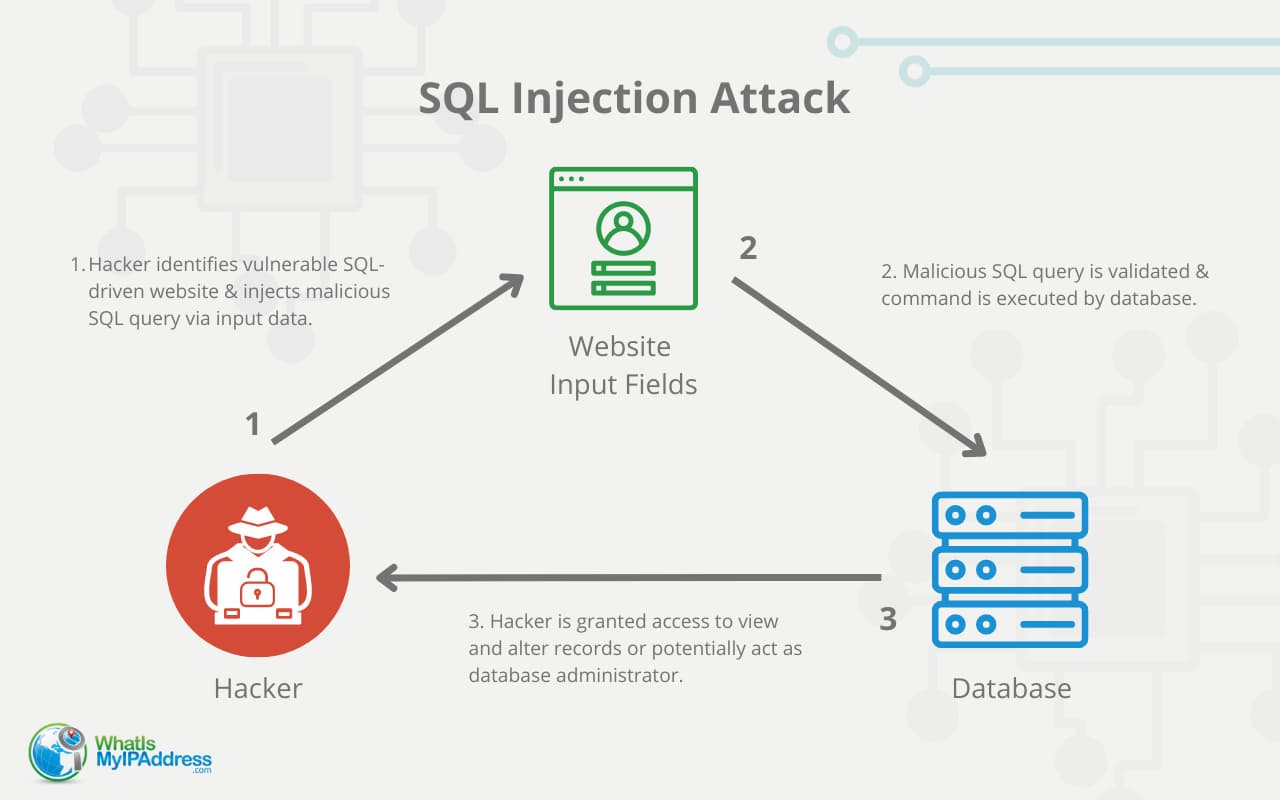


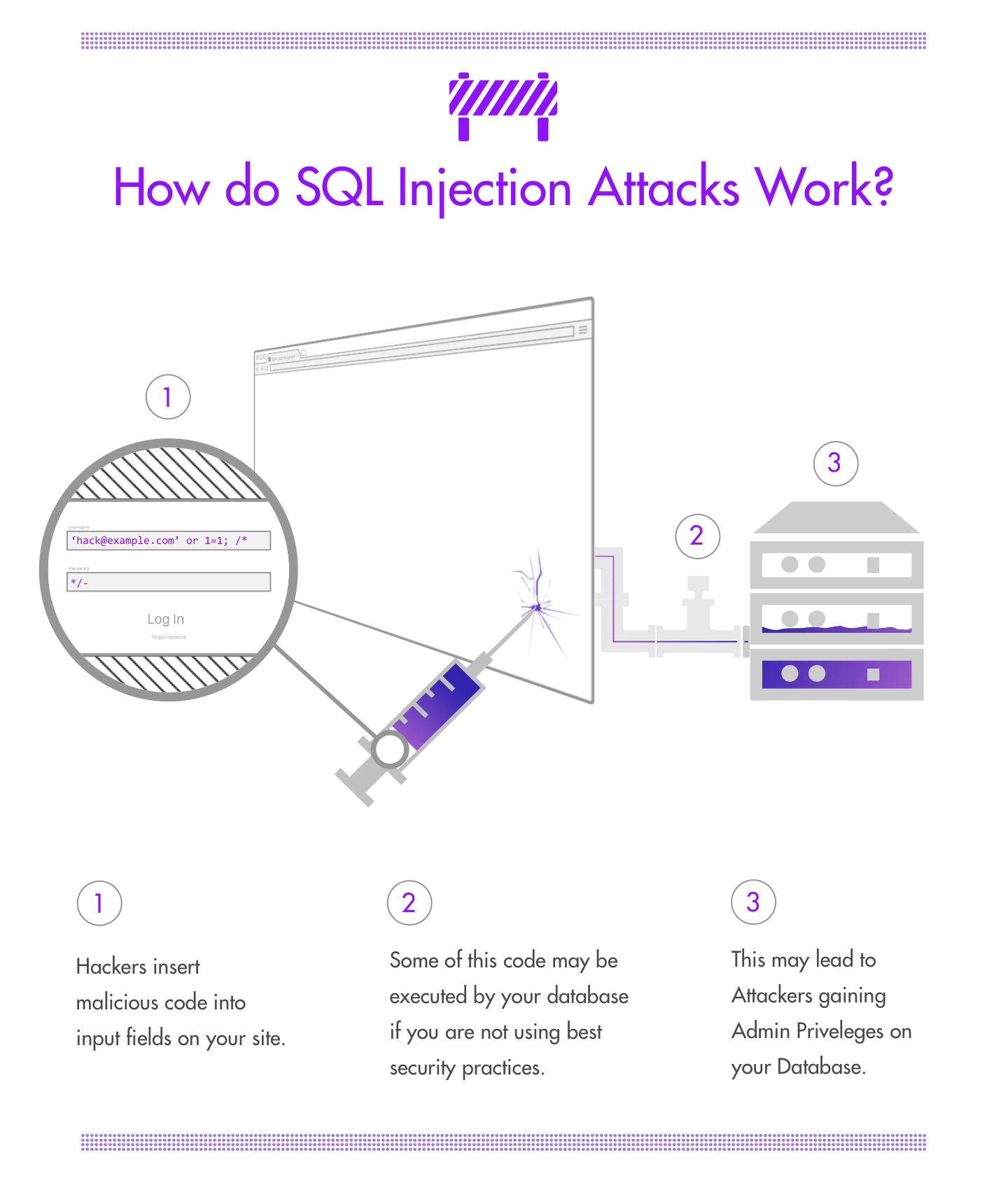










![SQL injection attack process, adopted from [2]. | Download Scientific ...](https://www.researchgate.net/publication/372290757/figure/fig3/AS:11431281174167066@1689163637519/Distribution-of-benign-and-SQL-injection-attacks-in-the-dataset_Q640.jpg)



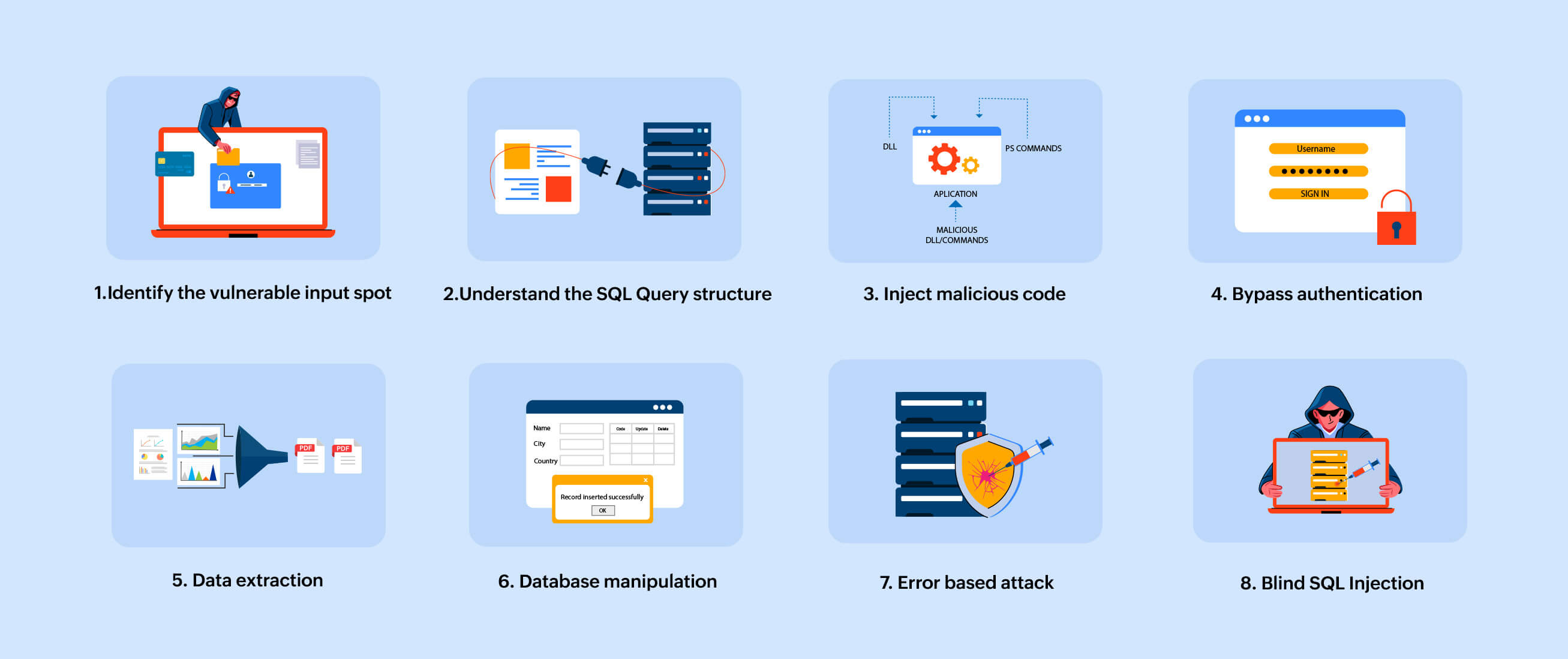



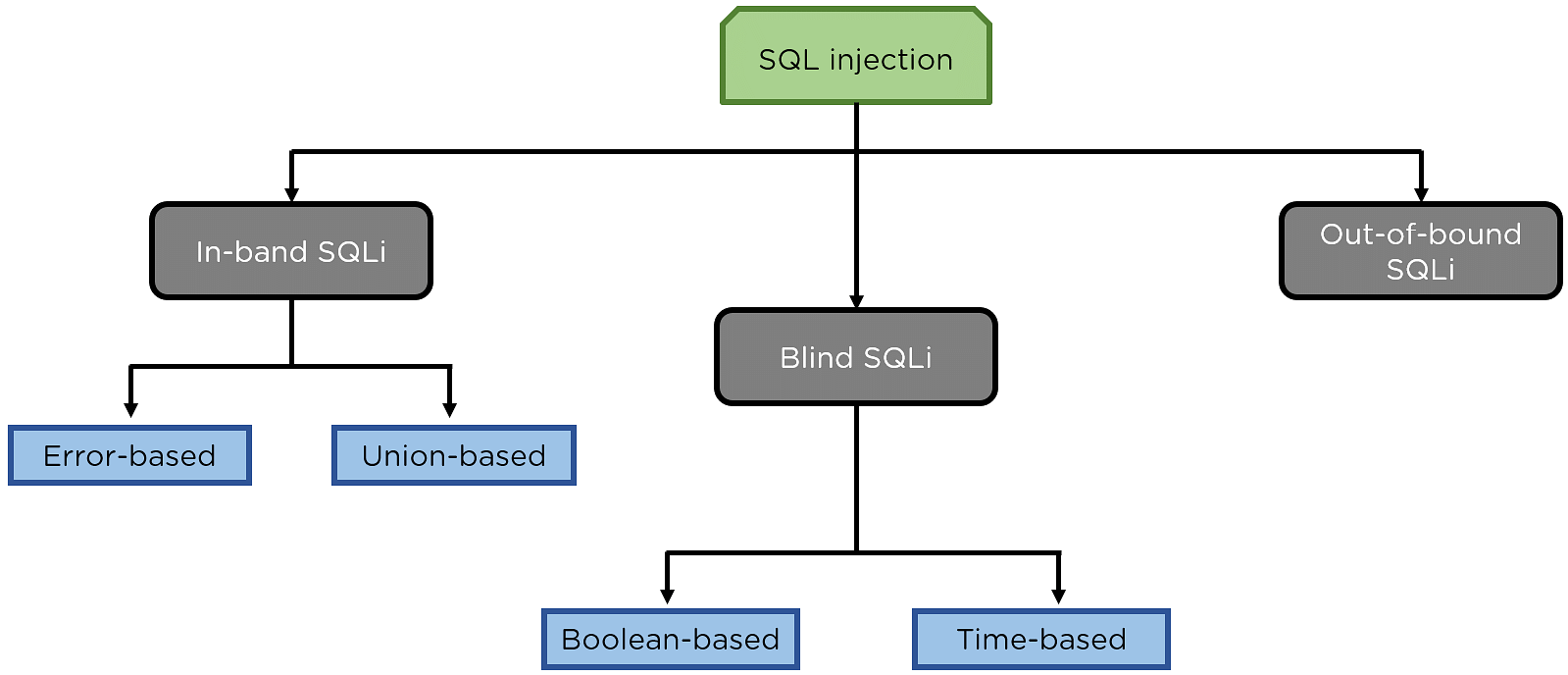









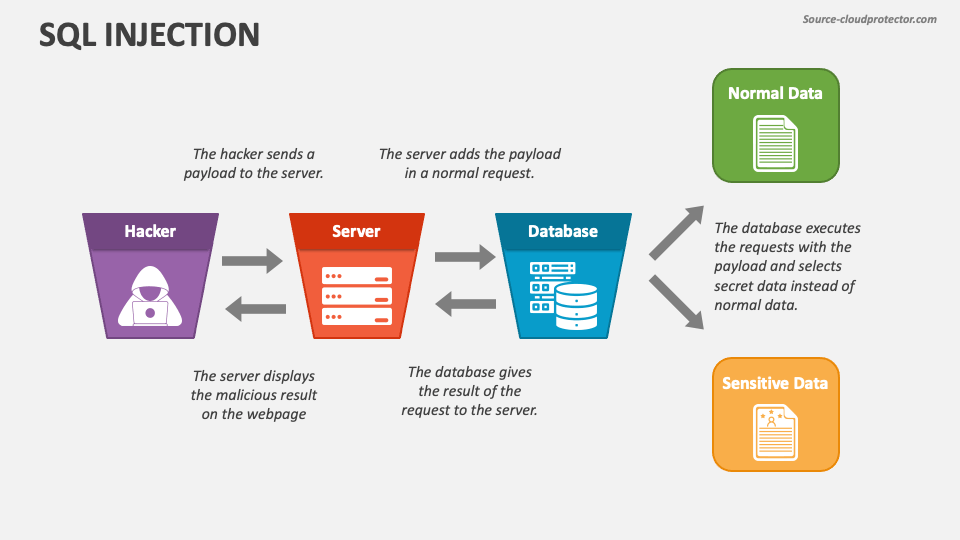







![[PPT] - A Classification of SQL Injection Attack Techniques and ...](https://c.sambuz.com/117502/a-classification-of-sql-injection-attack-techniques-and-l.jpg)
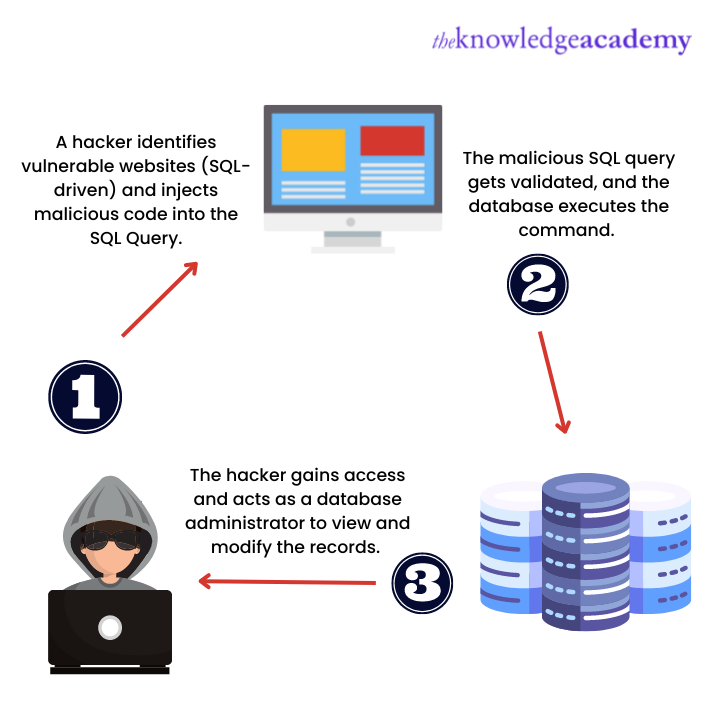
























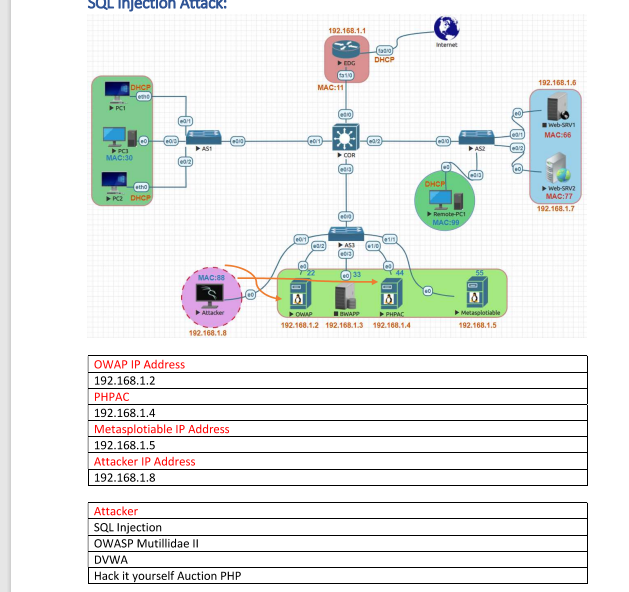
![[PDF] A Real-World Implementation of SQL Injection Attack Using Open ...](https://i1.rgstatic.net/publication/328972796_A_Real-World_Implementation_of_SQL_Injection_Attack_Using_Open_Source_Tools_for_Enhanced_Cybersecurity_Learning/links/5f7cf816a6fdccfd7b4c9306/largepreview.png)