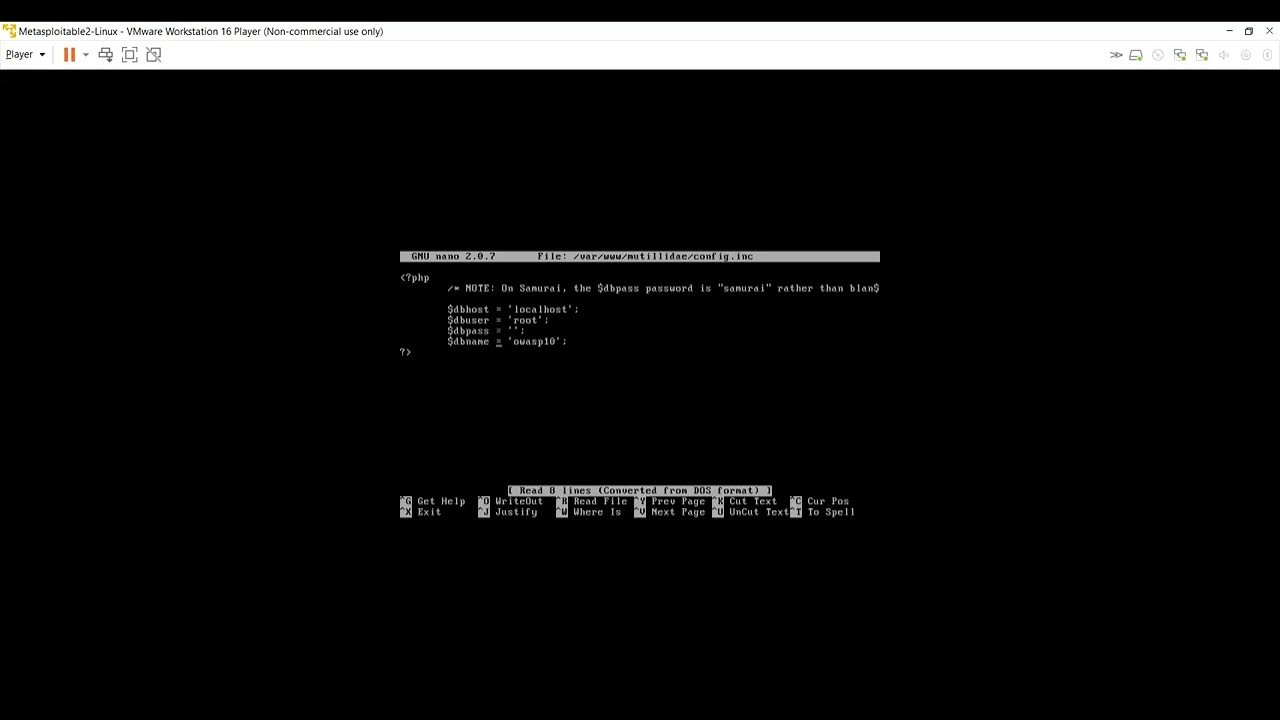
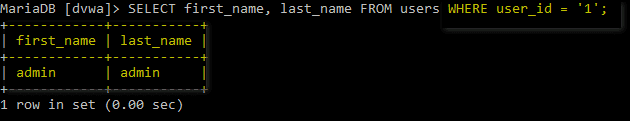
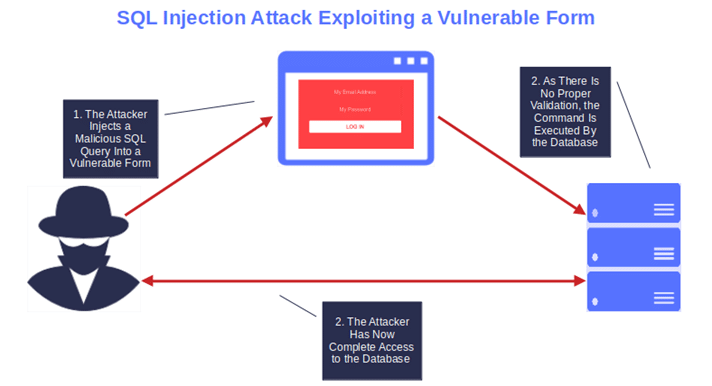
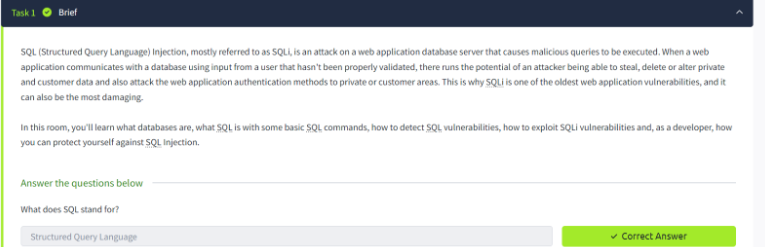
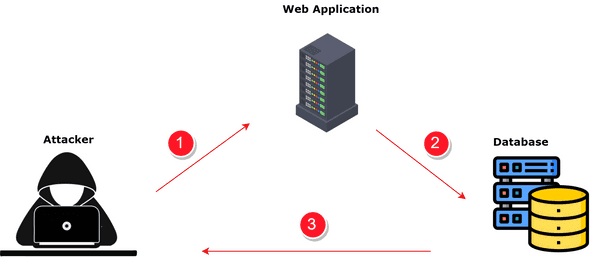
Learn about sql injection walkthrough: exploiting a common vulnerability | by through our educational collection of substantial collections of instructional images. enhancing knowledge retention through engaging and informative imagery. making complex concepts accessible through visual learning. Each sql injection walkthrough: exploiting a common vulnerability | by image is carefully selected for superior visual impact and professional quality. Excellent for educational materials, academic research, teaching resources, and learning activities All sql injection walkthrough: exploiting a common vulnerability | by images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Educators appreciate the pedagogical value of our carefully selected sql injection walkthrough: exploiting a common vulnerability | by photographs. The sql injection walkthrough: exploiting a common vulnerability | by archive serves professionals, educators, and creatives across diverse industries. Cost-effective licensing makes professional sql injection walkthrough: exploiting a common vulnerability | by photography accessible to all budgets. The sql injection walkthrough: exploiting a common vulnerability | by collection represents years of careful curation and professional standards. Advanced search capabilities make finding the perfect sql injection walkthrough: exploiting a common vulnerability | by image effortless and efficient. Regular updates keep the sql injection walkthrough: exploiting a common vulnerability | by collection current with contemporary trends and styles.




















































![[Web Security Academy] SQL injection vulnerability in WHERE clause ...](https://i.ytimg.com/vi/FE6KRZV8Owg/maxresdefault.jpg)


















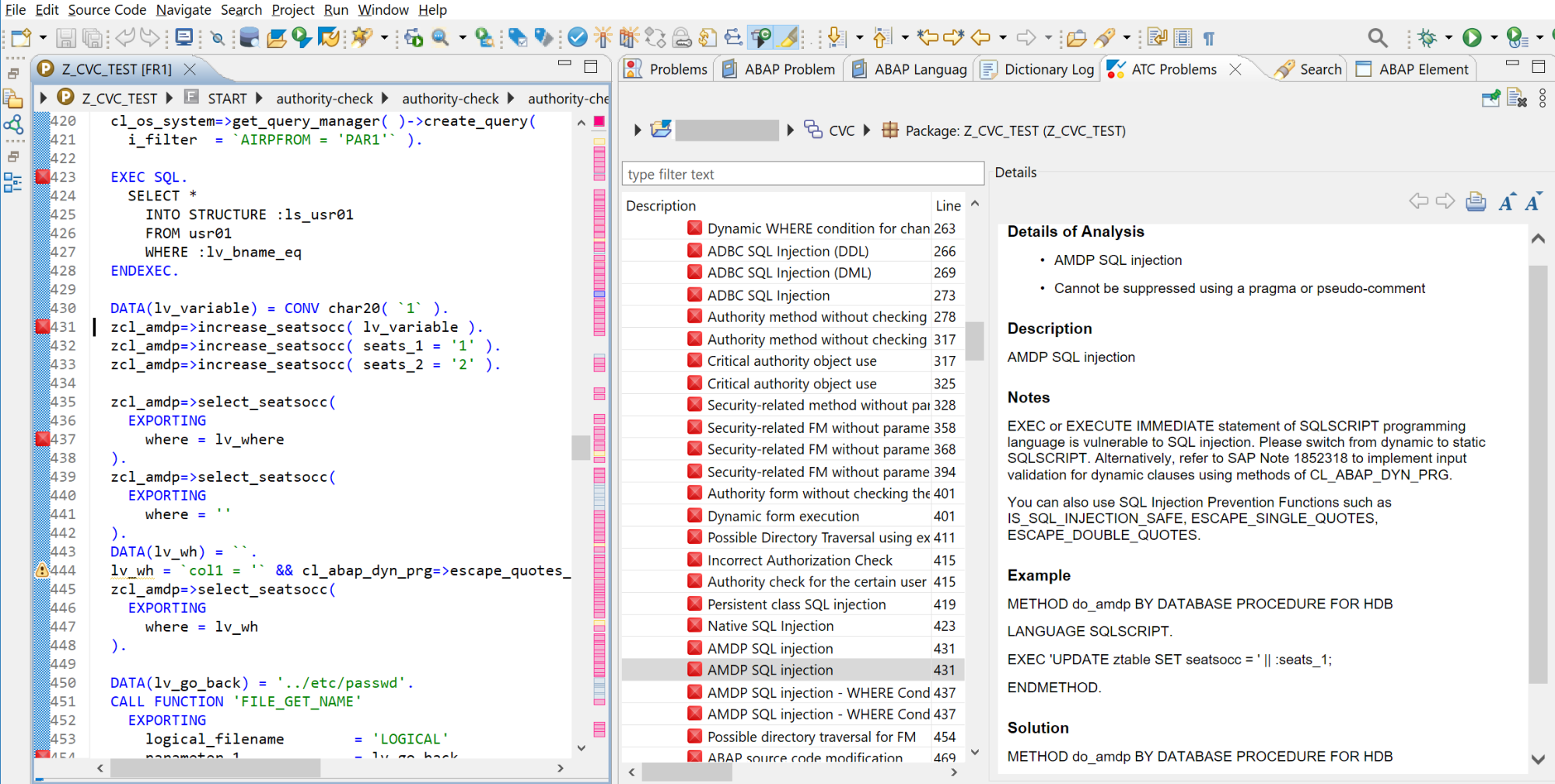





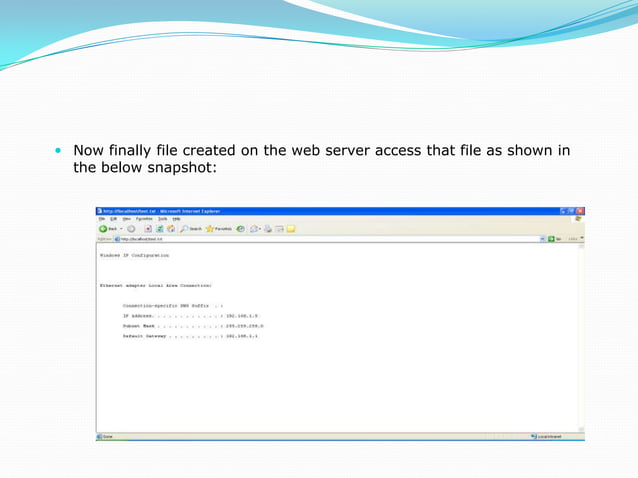



![[DVWA] Blind SQL Injection Walkthrough (low-security) | by ...](https://miro.medium.com/v2/resize:fit:1358/1*ocpeDYSOApZprjDutHXWFQ.jpeg)