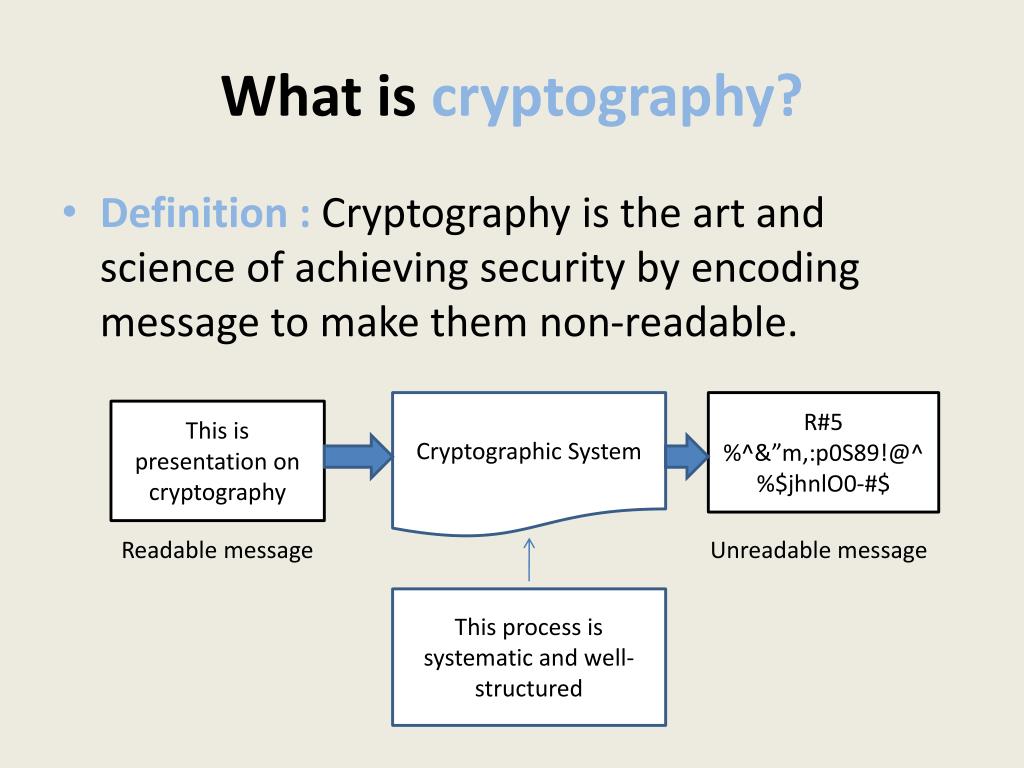
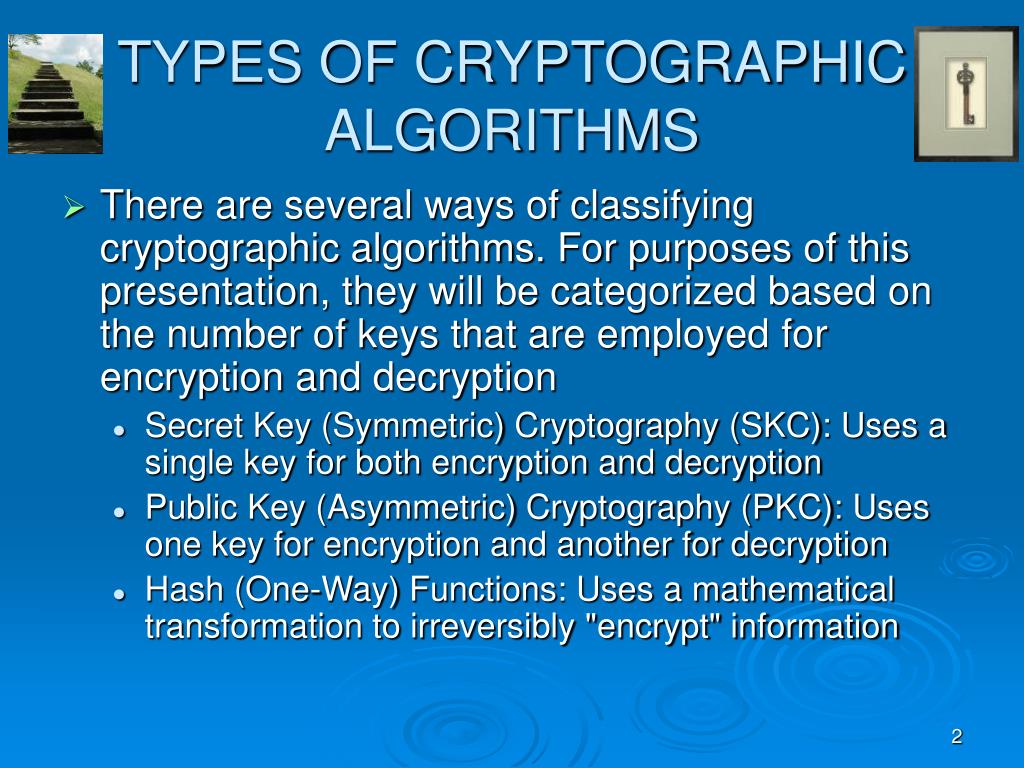
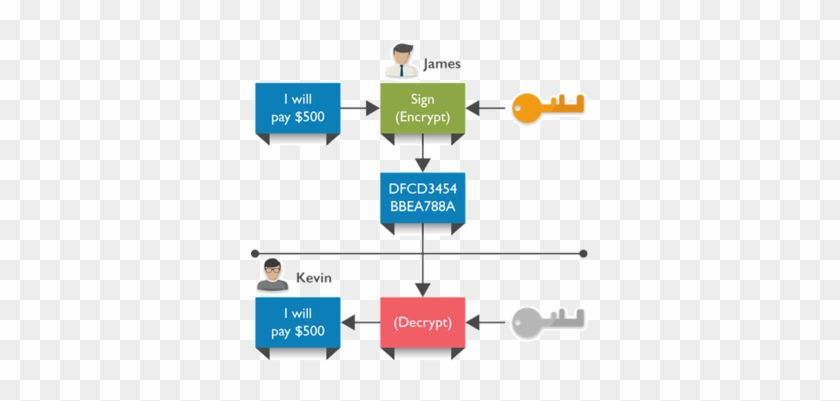
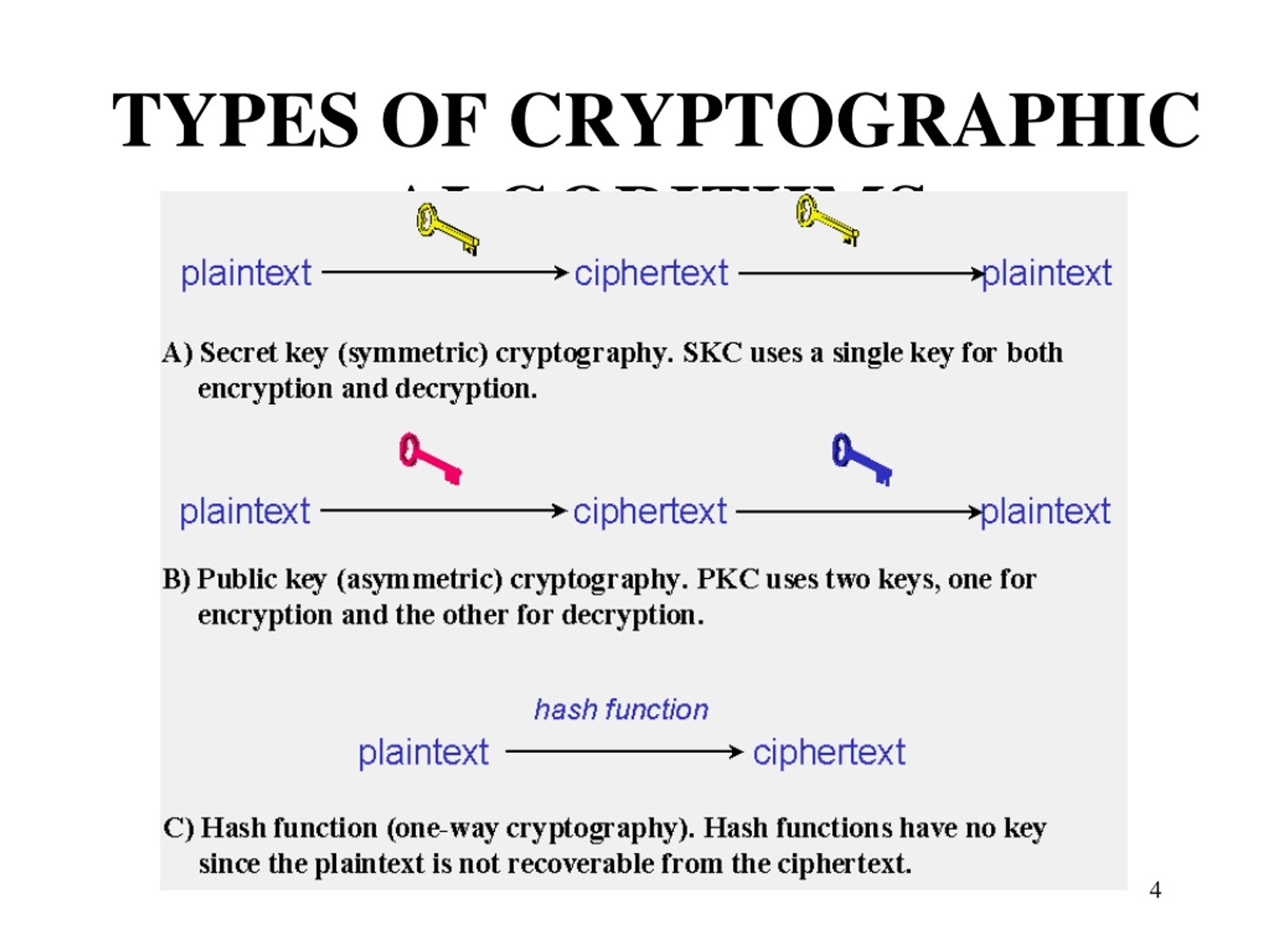
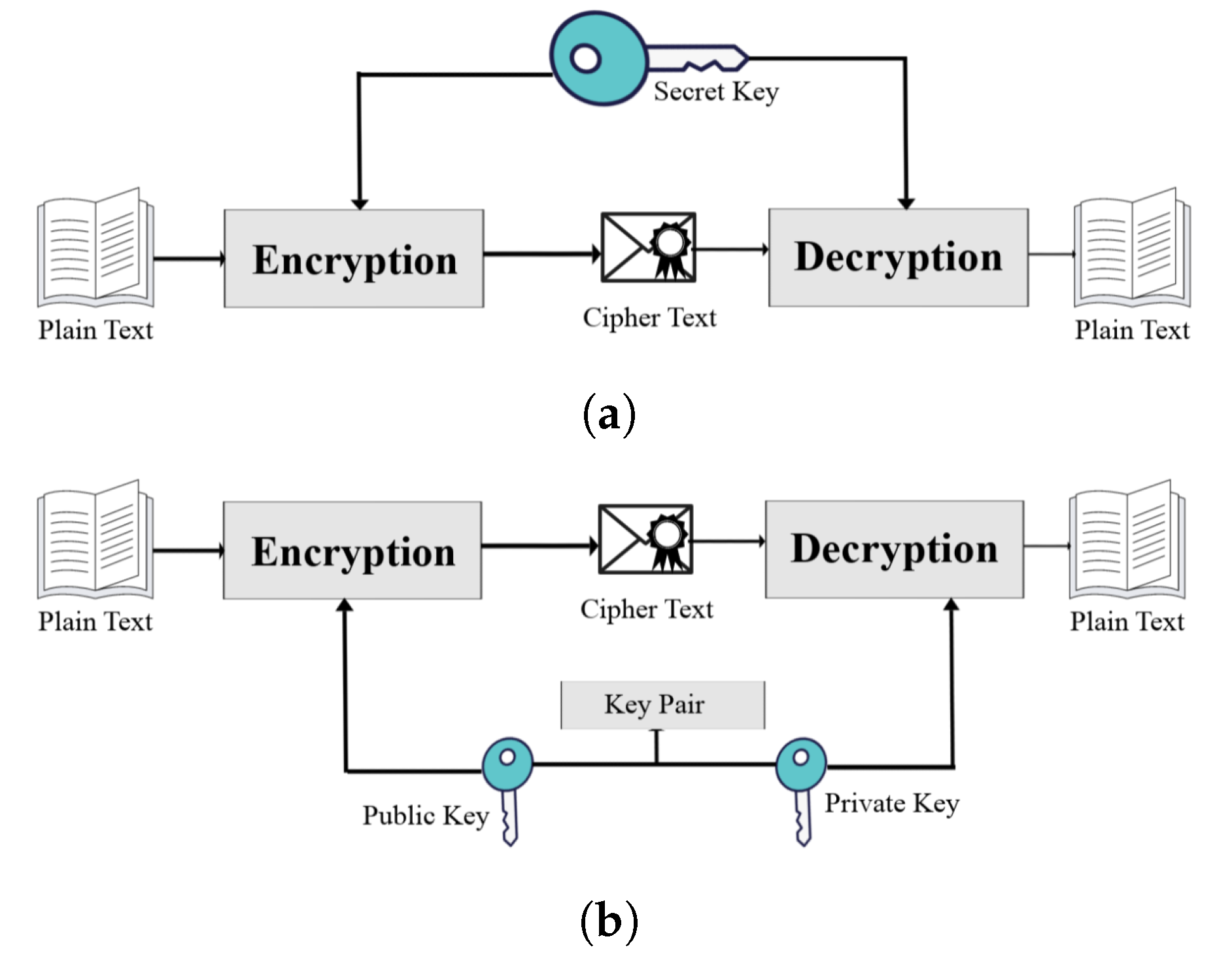
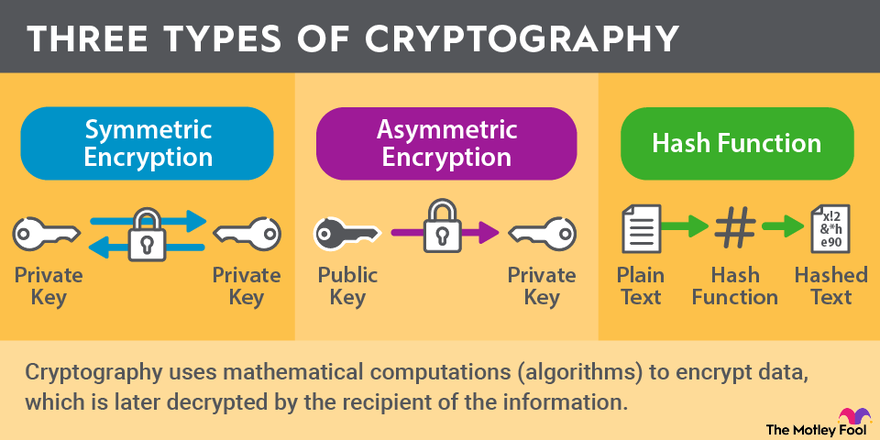
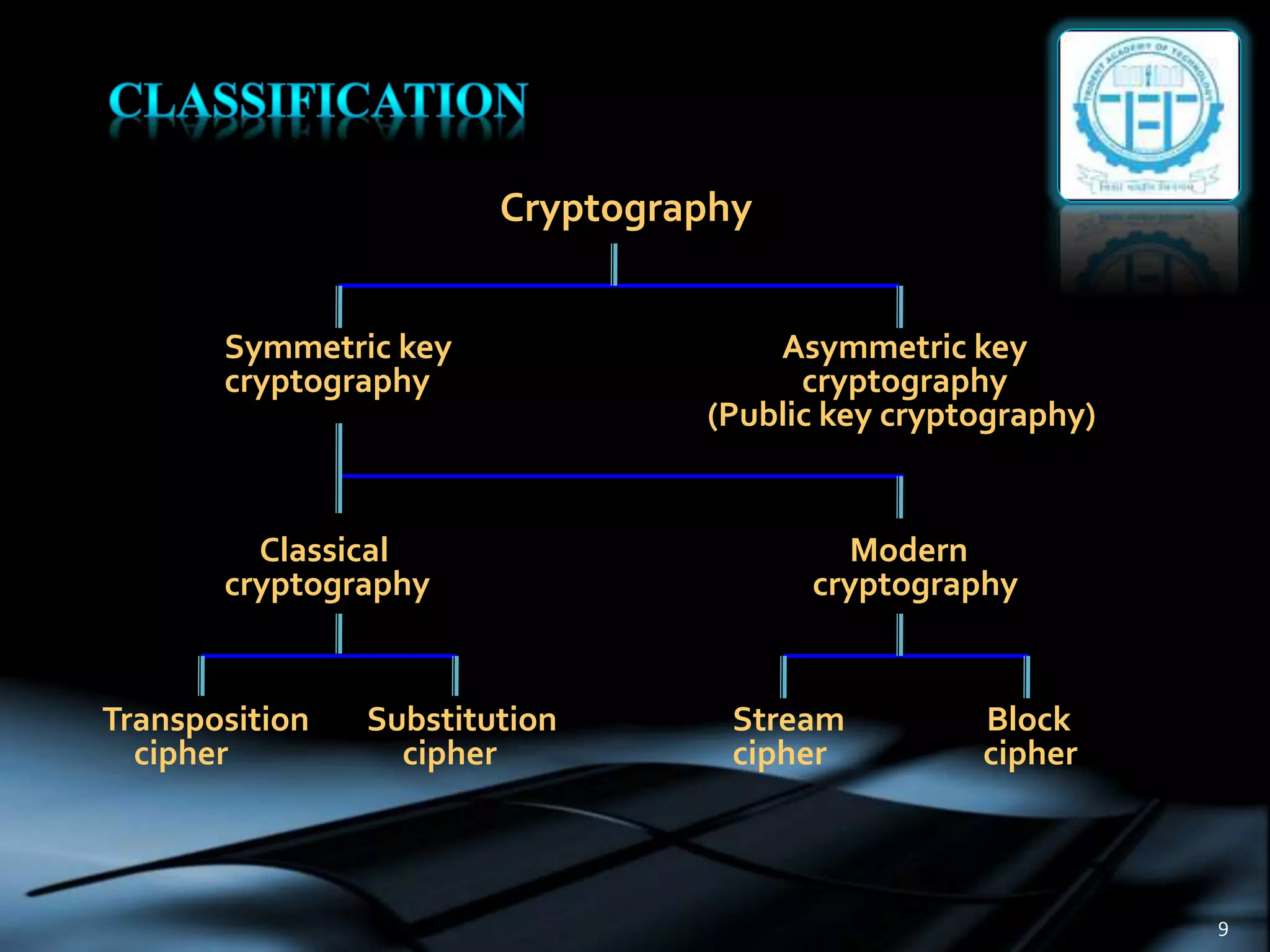
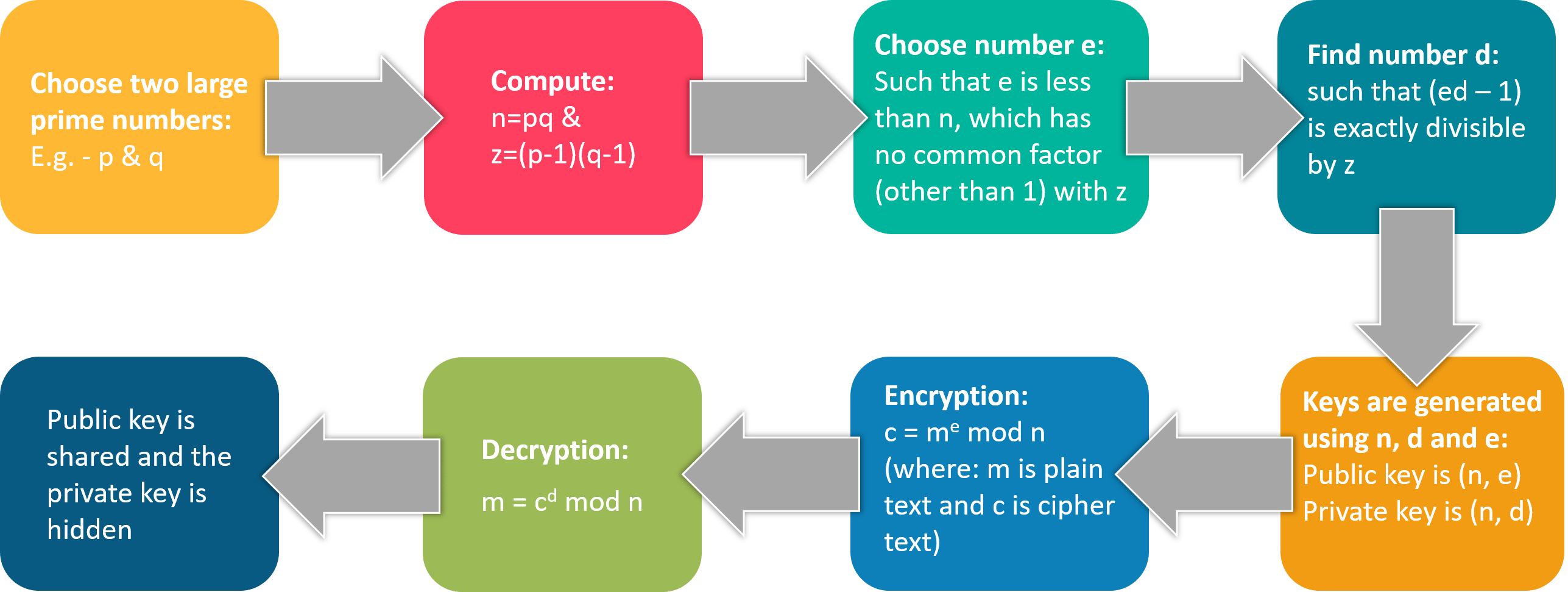
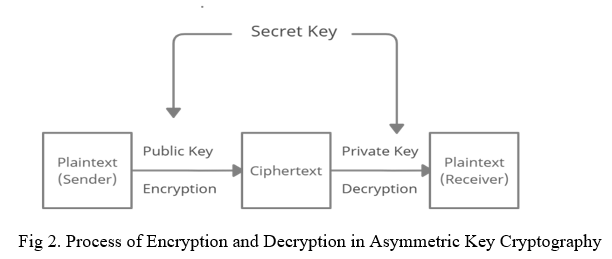
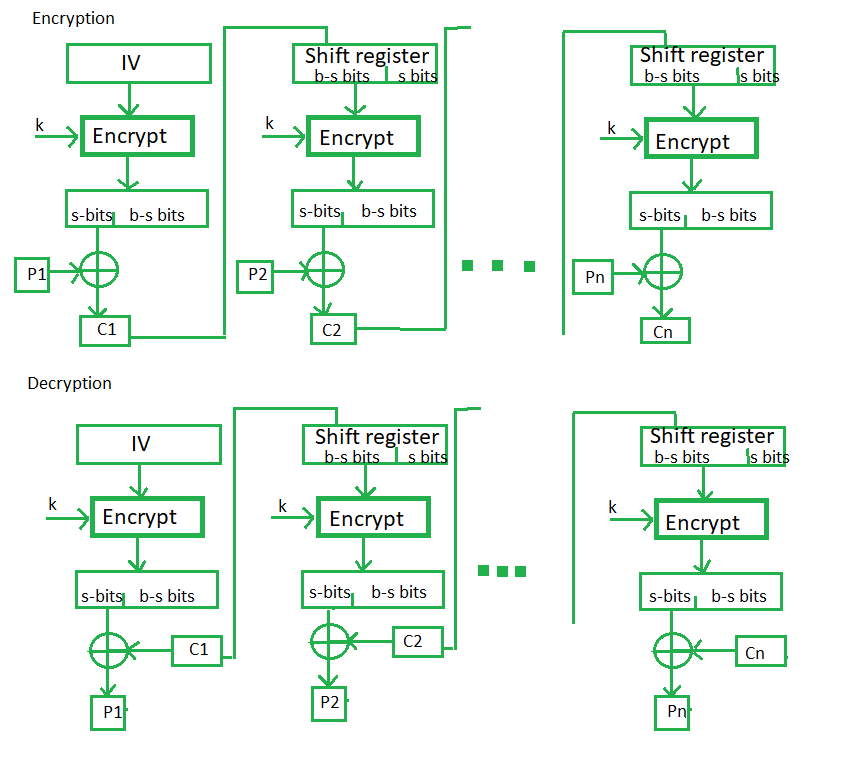
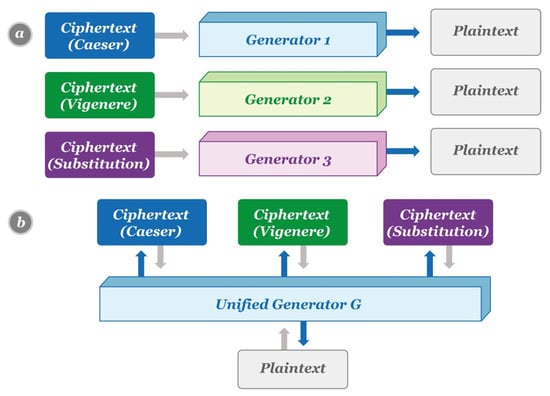
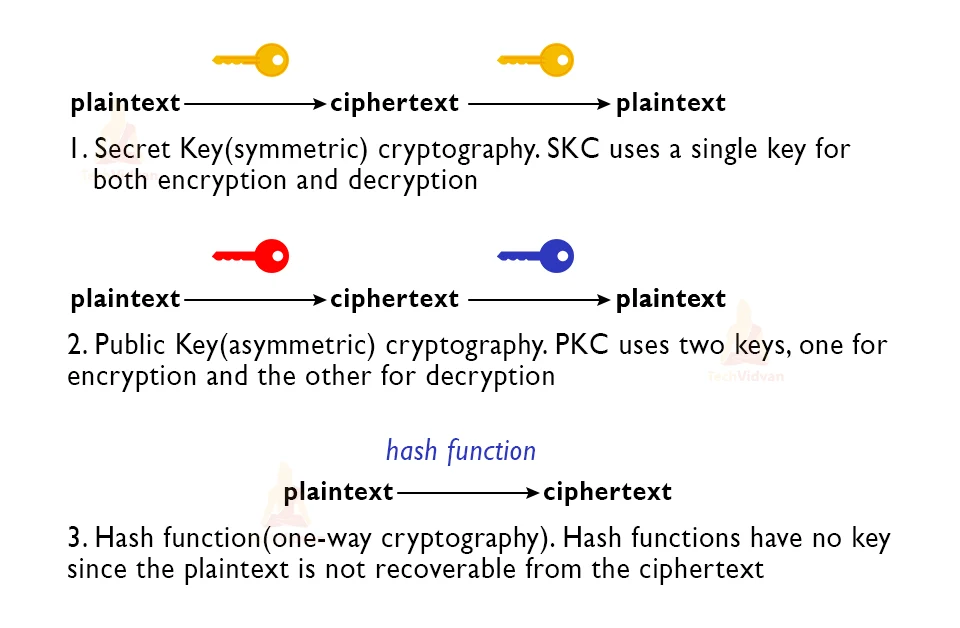
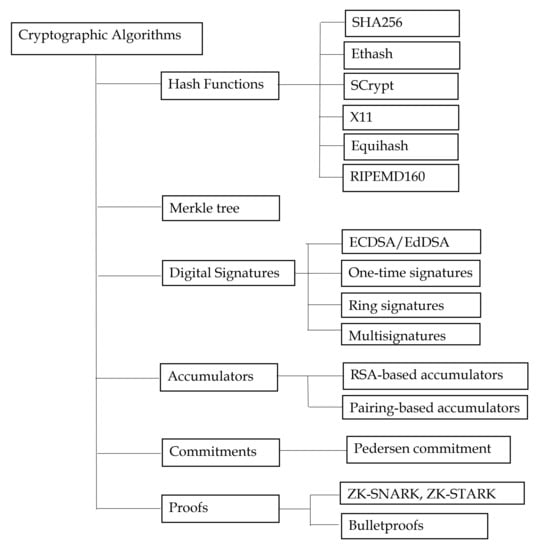
Capture athletic excellence with our remarkable sports classification of cryptographic algorithms. | download scientific diagram collection of hundreds of dynamic images. dynamically highlighting photography, images, and pictures. designed to celebrate competitive spirit. Our classification of cryptographic algorithms. | download scientific diagram collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All classification of cryptographic algorithms. | download scientific diagram images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our classification of cryptographic algorithms. | download scientific diagram collection for various creative and professional projects. Diverse style options within the classification of cryptographic algorithms. | download scientific diagram collection suit various aesthetic preferences. Advanced search capabilities make finding the perfect classification of cryptographic algorithms. | download scientific diagram image effortless and efficient. Comprehensive tagging systems facilitate quick discovery of relevant classification of cryptographic algorithms. | download scientific diagram content. Our classification of cryptographic algorithms. | download scientific diagram database continuously expands with fresh, relevant content from skilled photographers. Instant download capabilities enable immediate access to chosen classification of cryptographic algorithms. | download scientific diagram images.













![Classification of Cryptography [16] | Download Scientific Diagram](https://www.researchgate.net/publication/322276861/figure/fig1/AS:581599352049664@1515675499015/Classification-of-Cryptography-16.png)



















![Classification of Cryptography [16] | Download Scientific Diagram](https://www.researchgate.net/profile/Falah-Ahmed-3/publication/322276861/figure/fig1/AS:581599352049664@1515675499015/Classification-of-Cryptography-16_Q320.jpg)


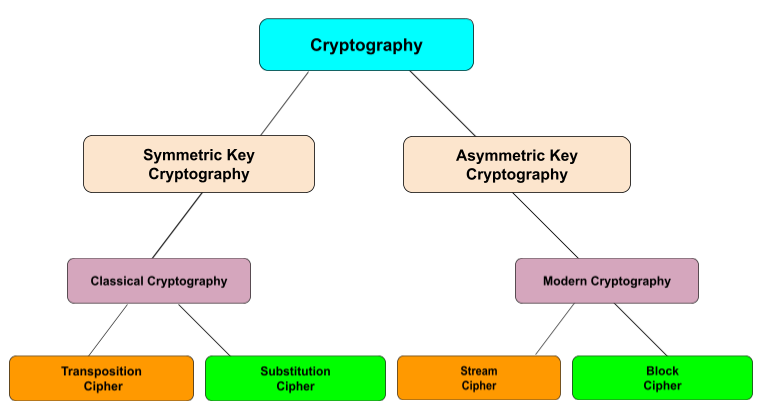
![Classification of cryptographic techniques [26] | Download Scientific ...](https://www.researchgate.net/publication/311520856/figure/fig7/AS:941687379603456@1601527175387/Classification-of-cryptographic-techniques-26.gif)
![3: Cryptography classification [19]. | Download Scientific Diagram](https://www.researchgate.net/profile/Ahmed-Radwan-59/publication/361115870/figure/fig3/AS:1164014755291138@1654534152590/Cryptography-classification-19_Q640.jpg)



![27 Classification of Cryptography [38] | Download Scientific Diagram](https://www.researchgate.net/publication/339446723/figure/fig11/AS:862008329121813@1582530209823/Classification-of-Cryptography-38.jpg)
















![Overview of Cryptography [6] | Download Scientific Diagram](https://www.researchgate.net/publication/295256333/figure/fig1/AS:339627161473078@1457984833940/Overview-of-Cryptography-6.png)













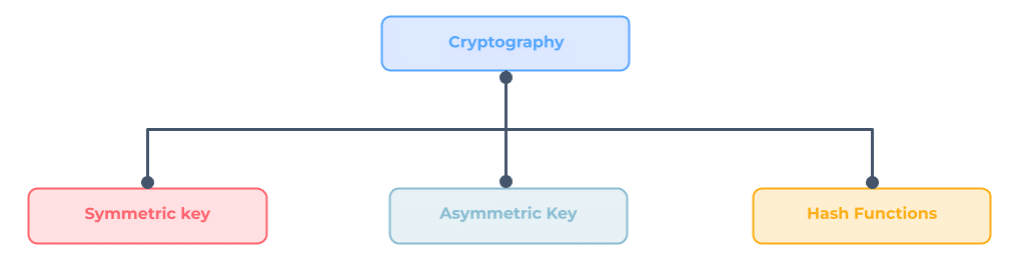








![Classification of different encryption algorithms [10]. | Download ...](https://www.researchgate.net/publication/350655579/figure/fig2/AS:1080288956416095@1634572366951/Classification-of-different-encryption-algorithms-10_Q640.jpg)