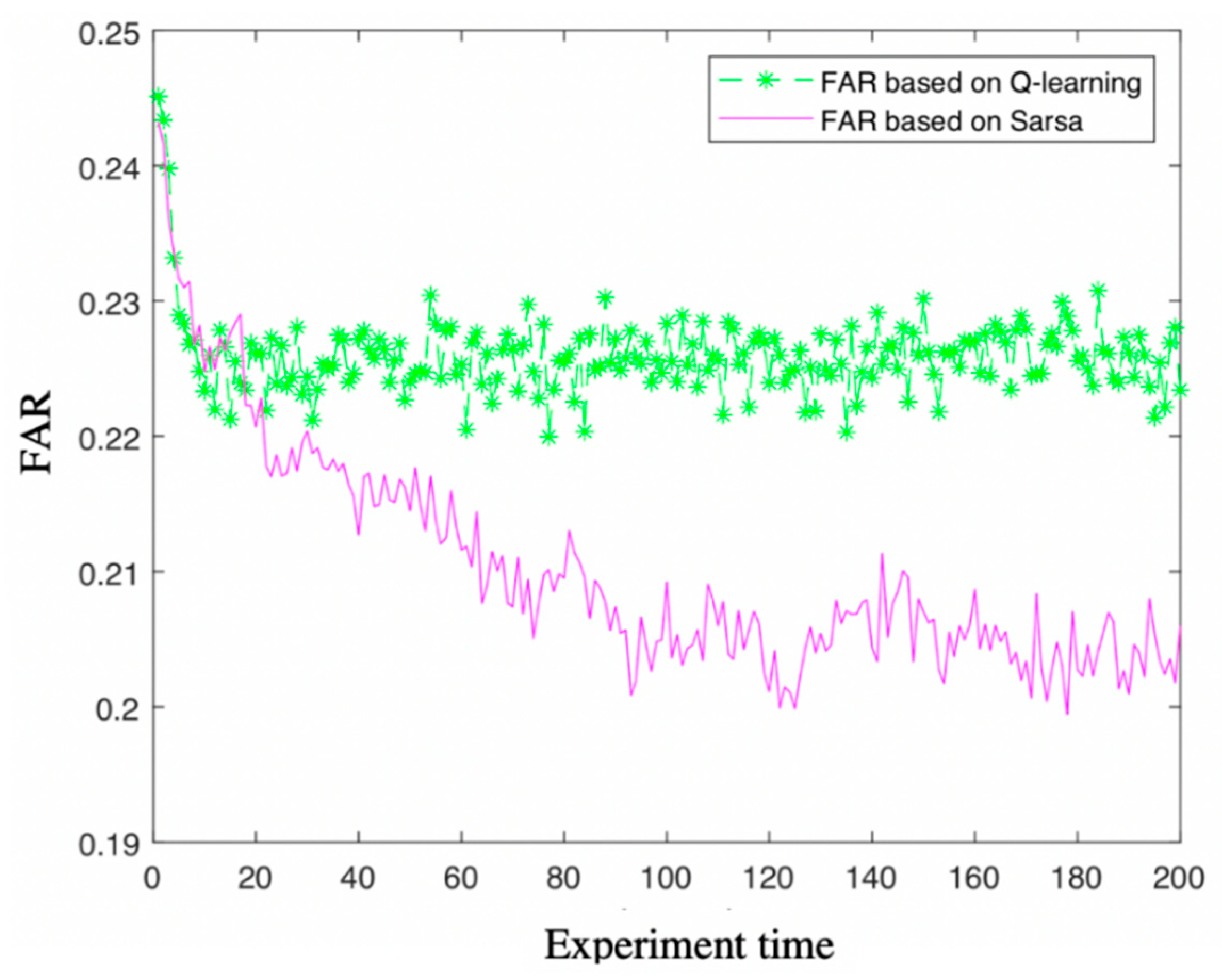
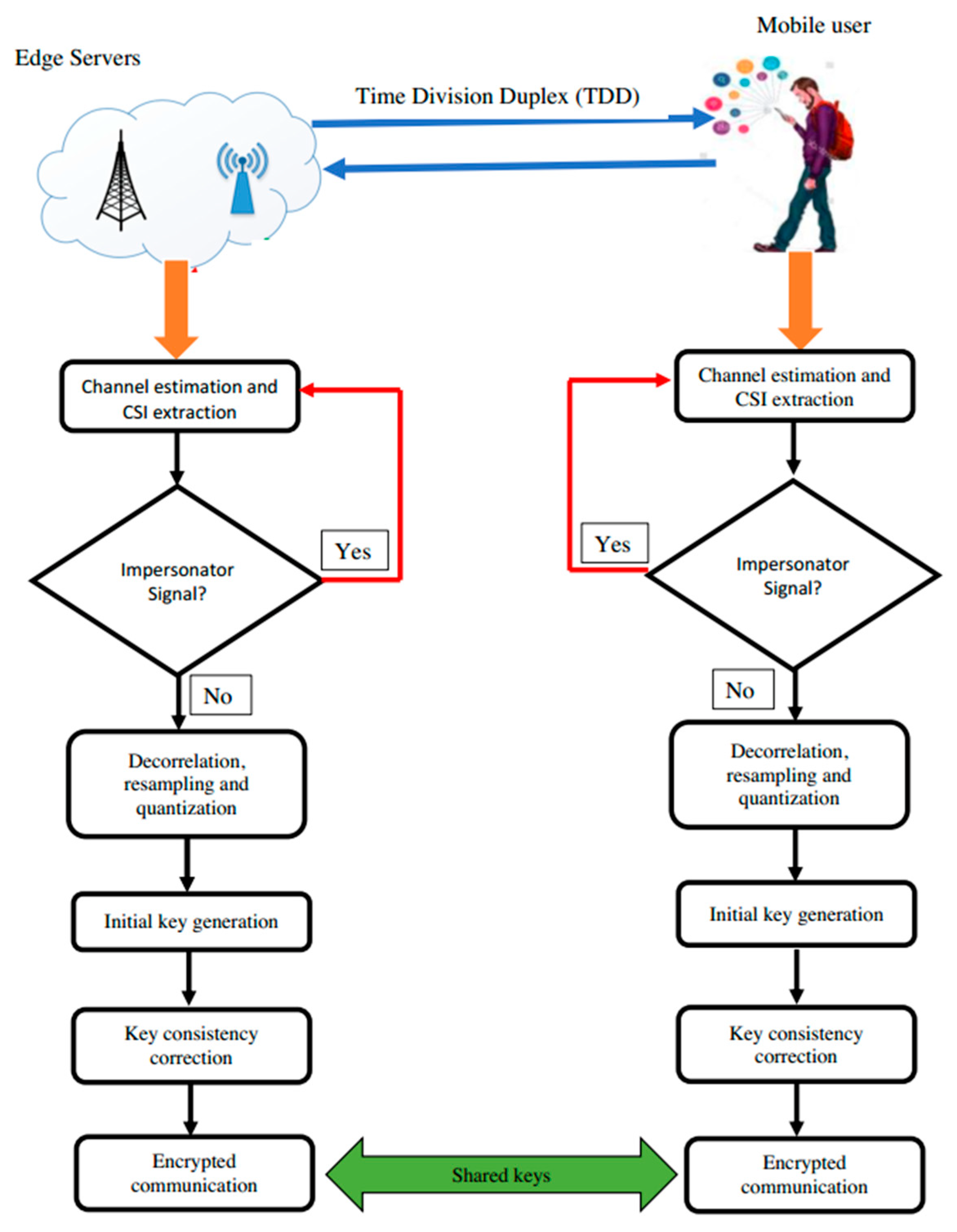
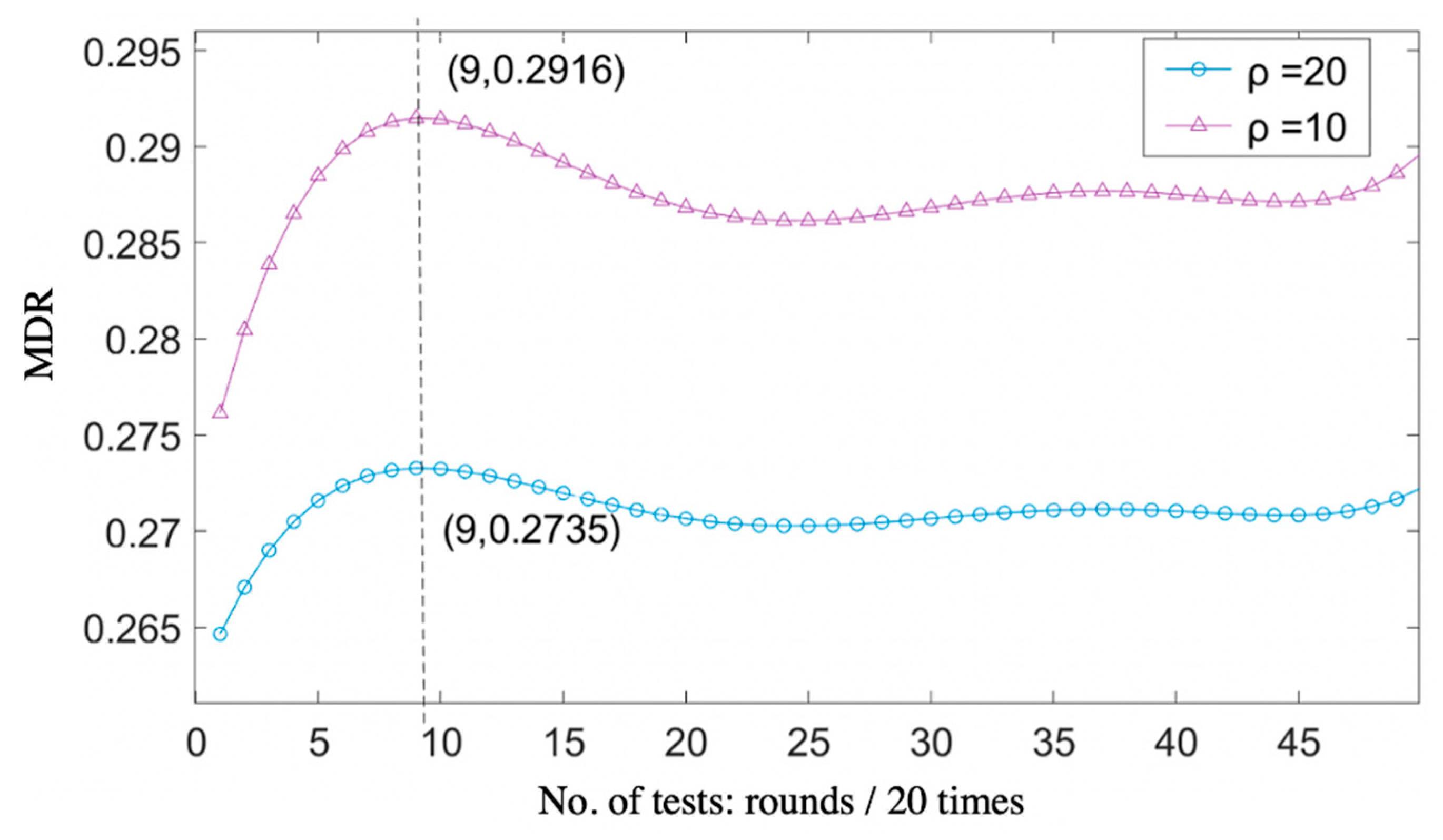
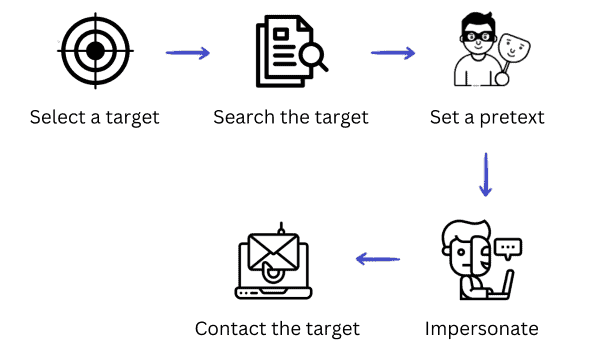
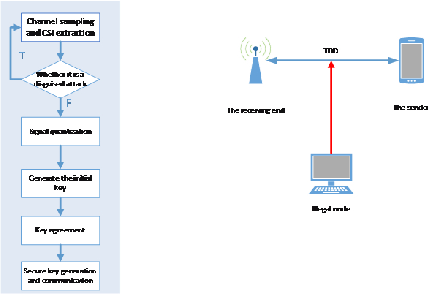
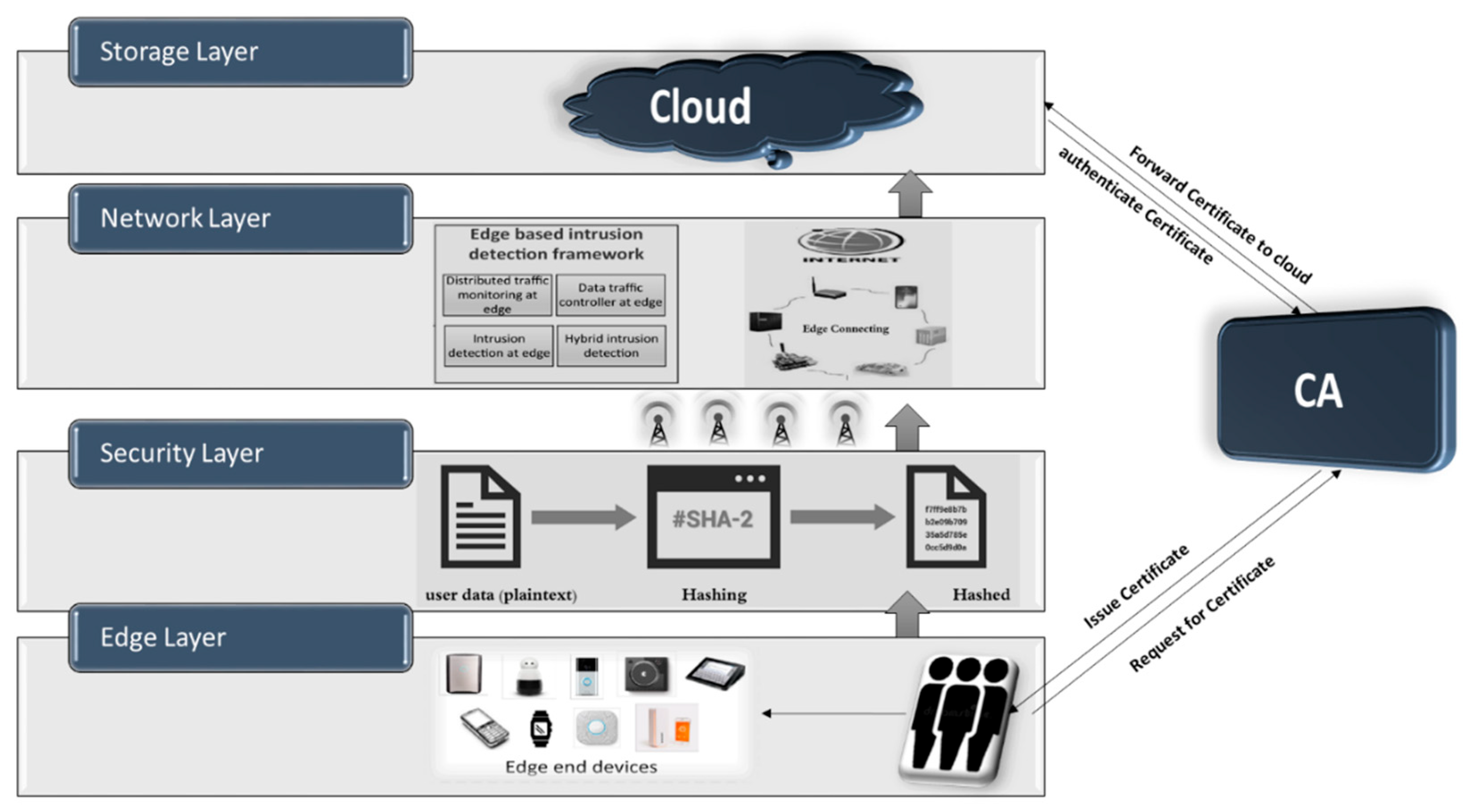
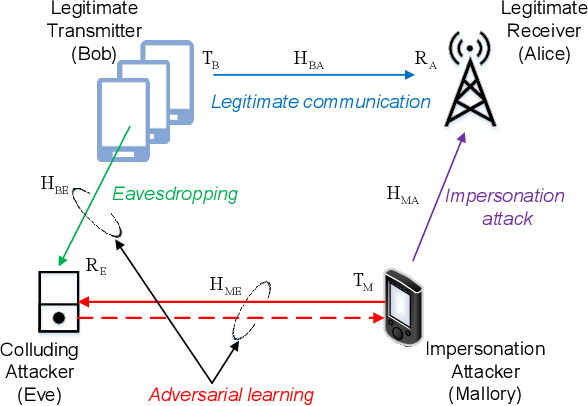
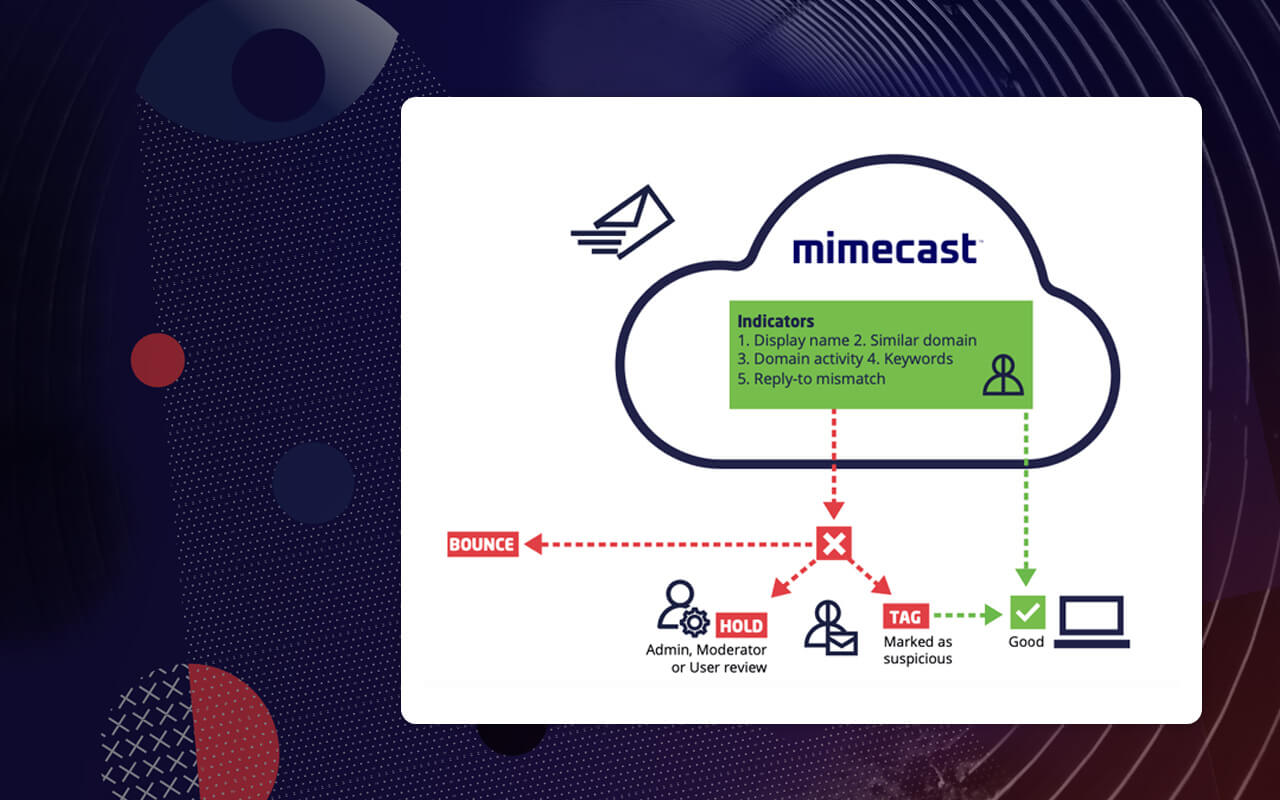
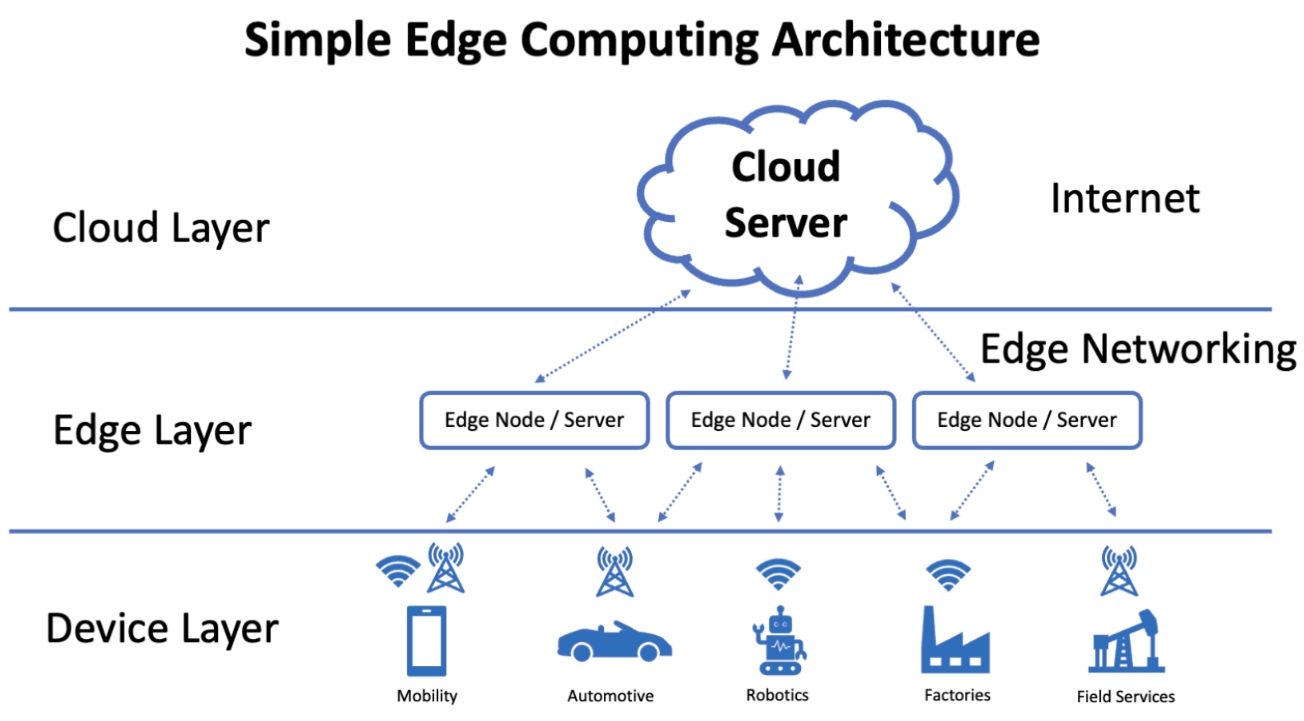
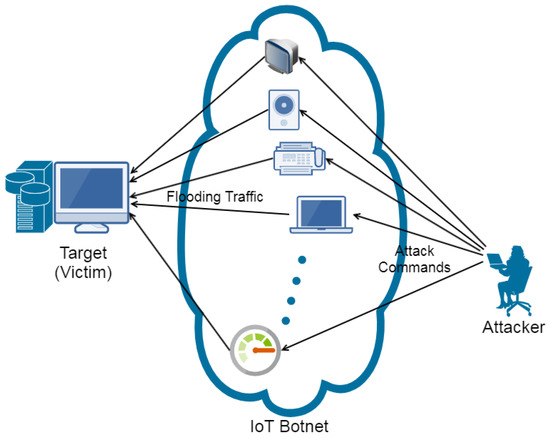
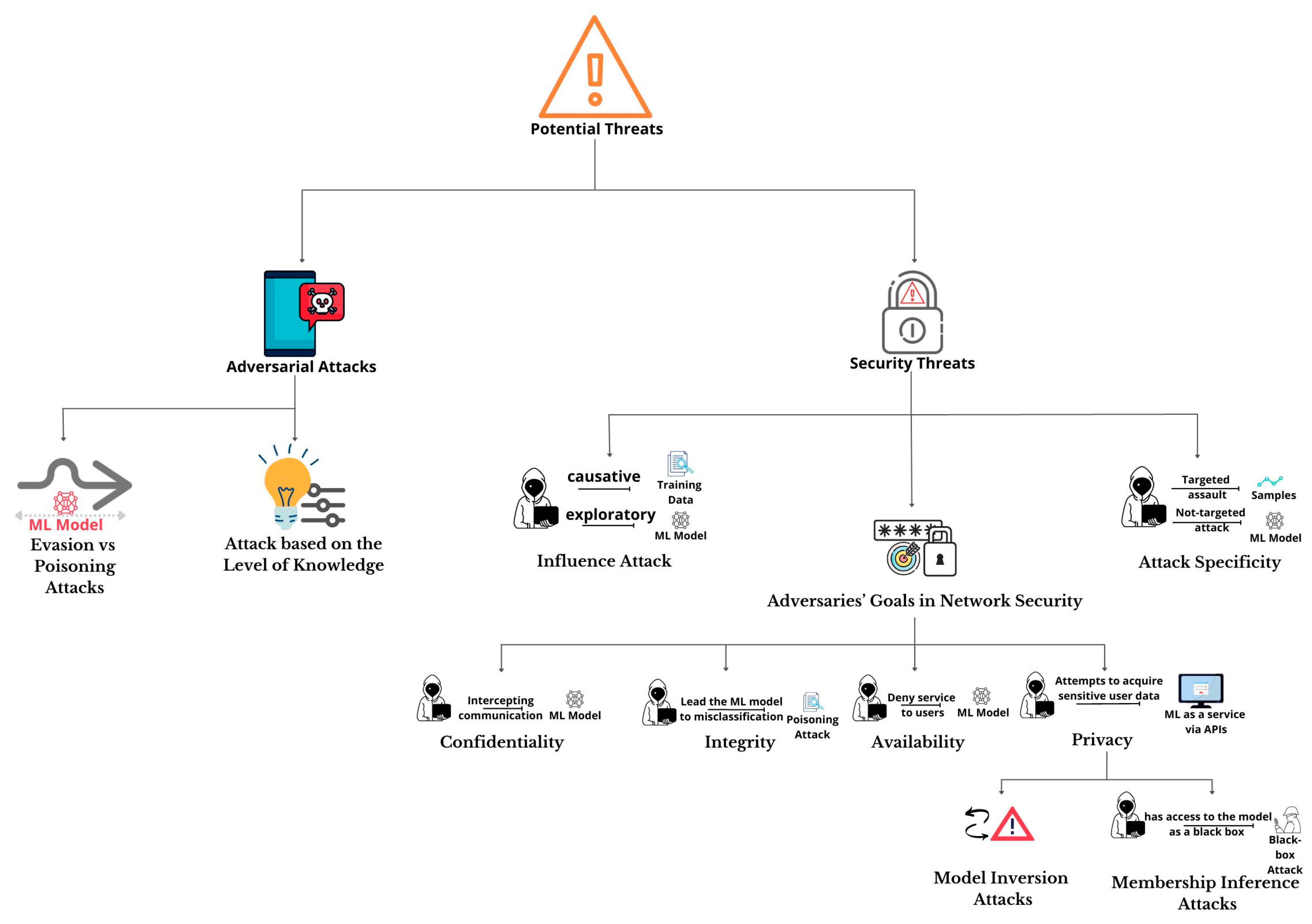
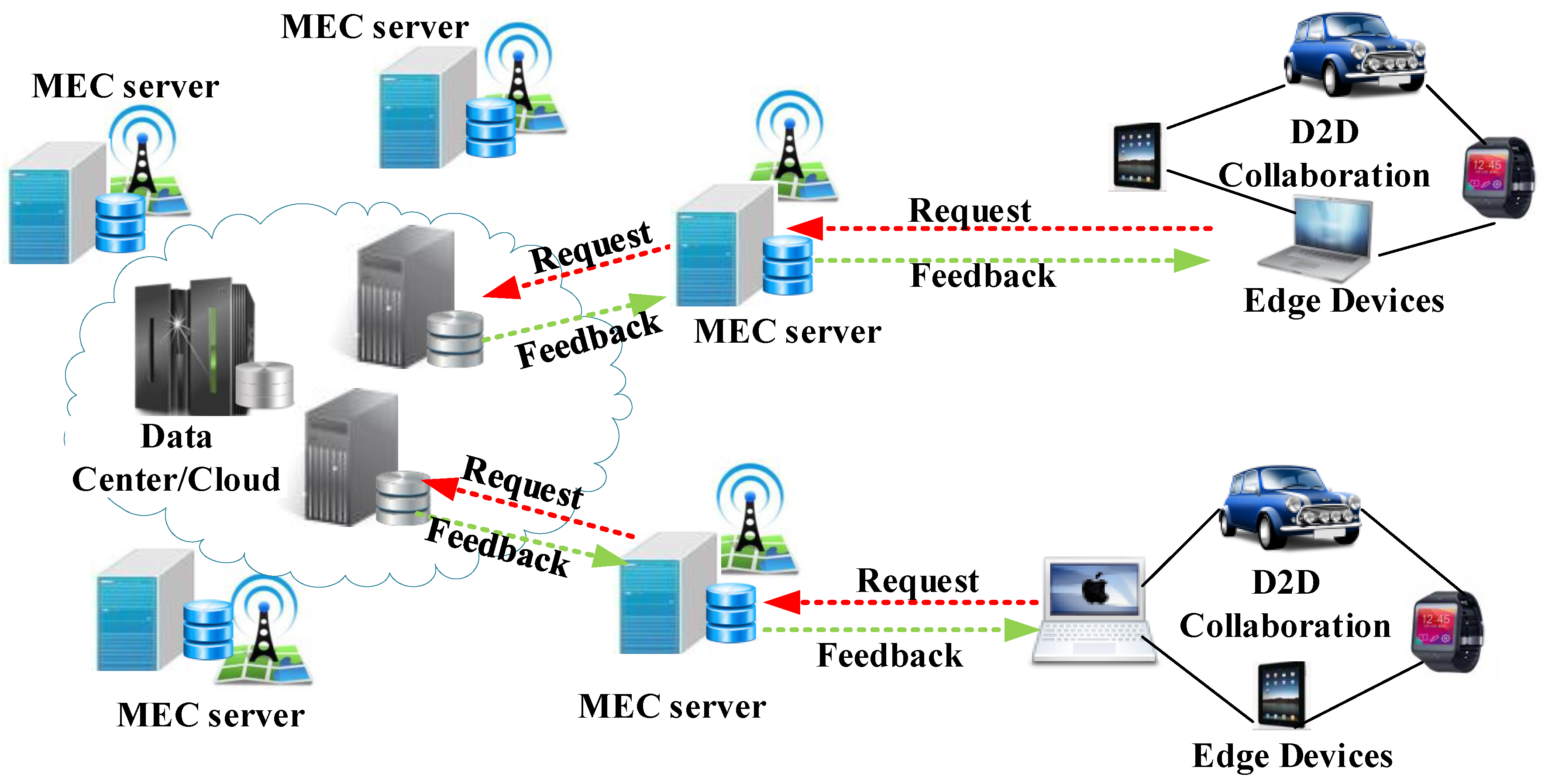
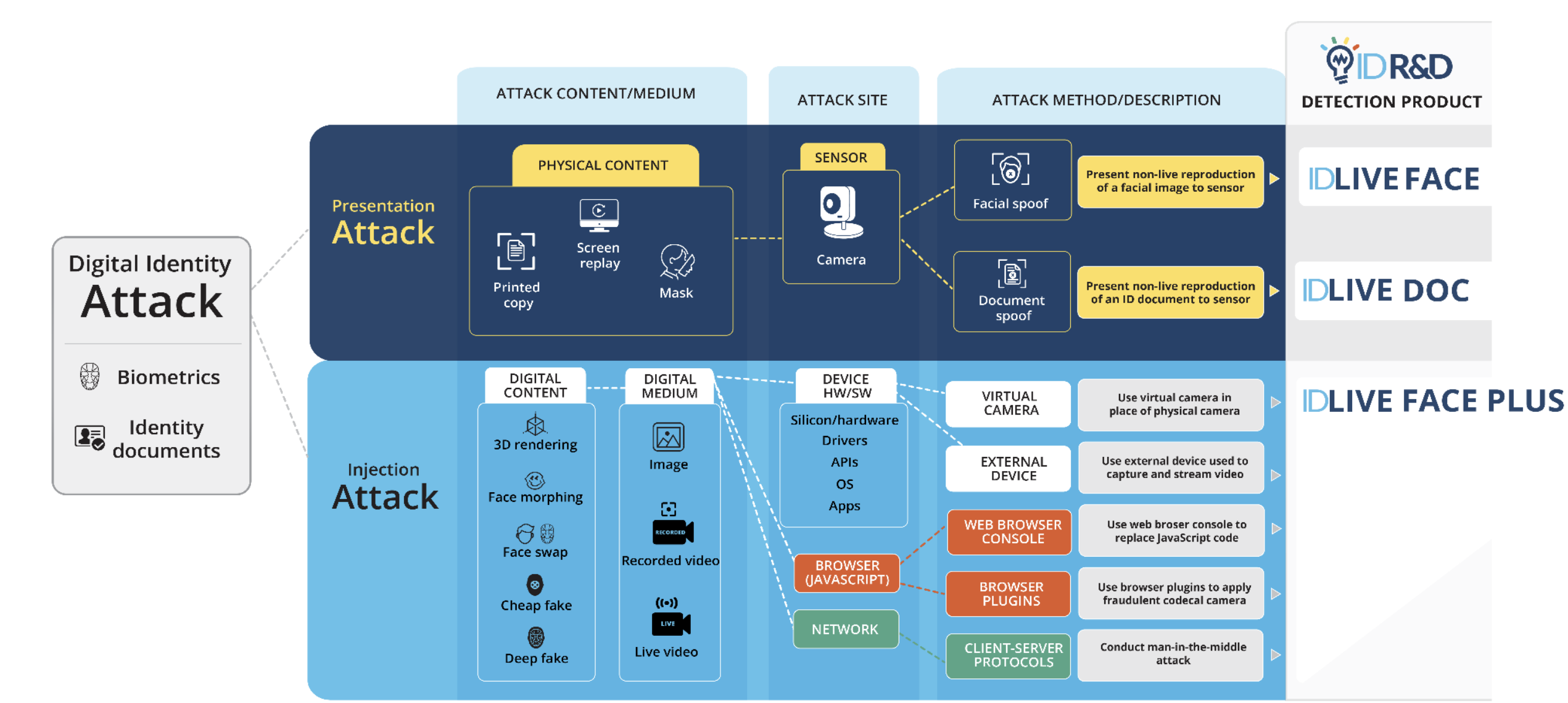
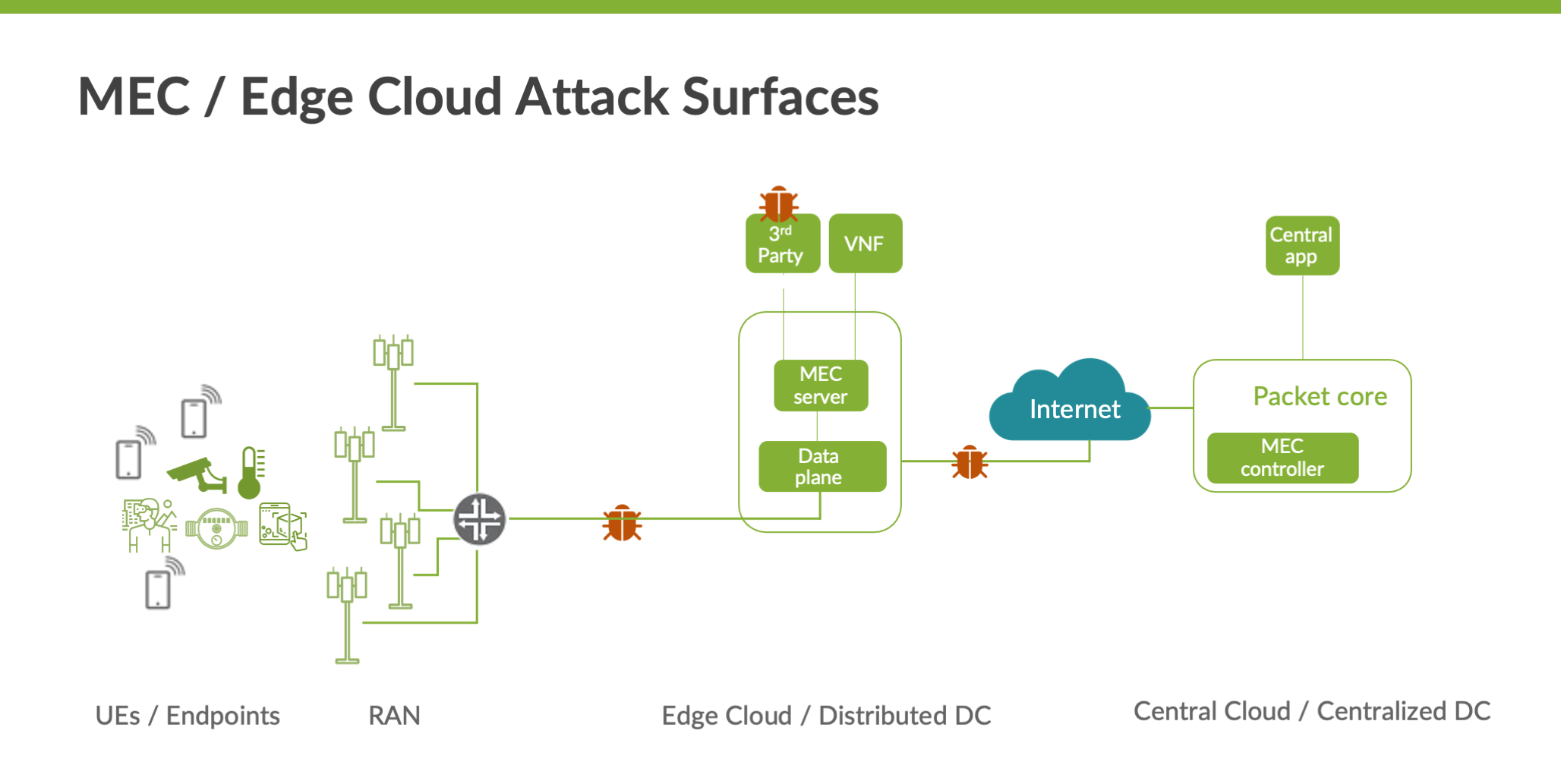
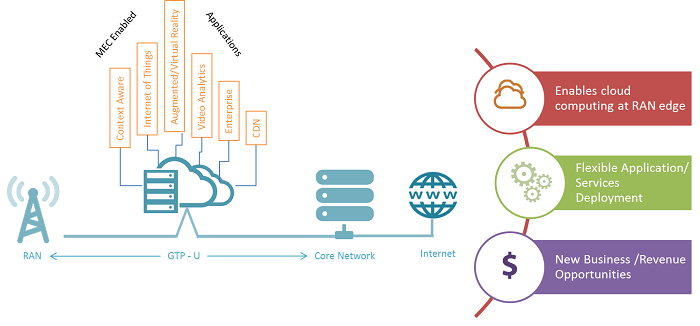
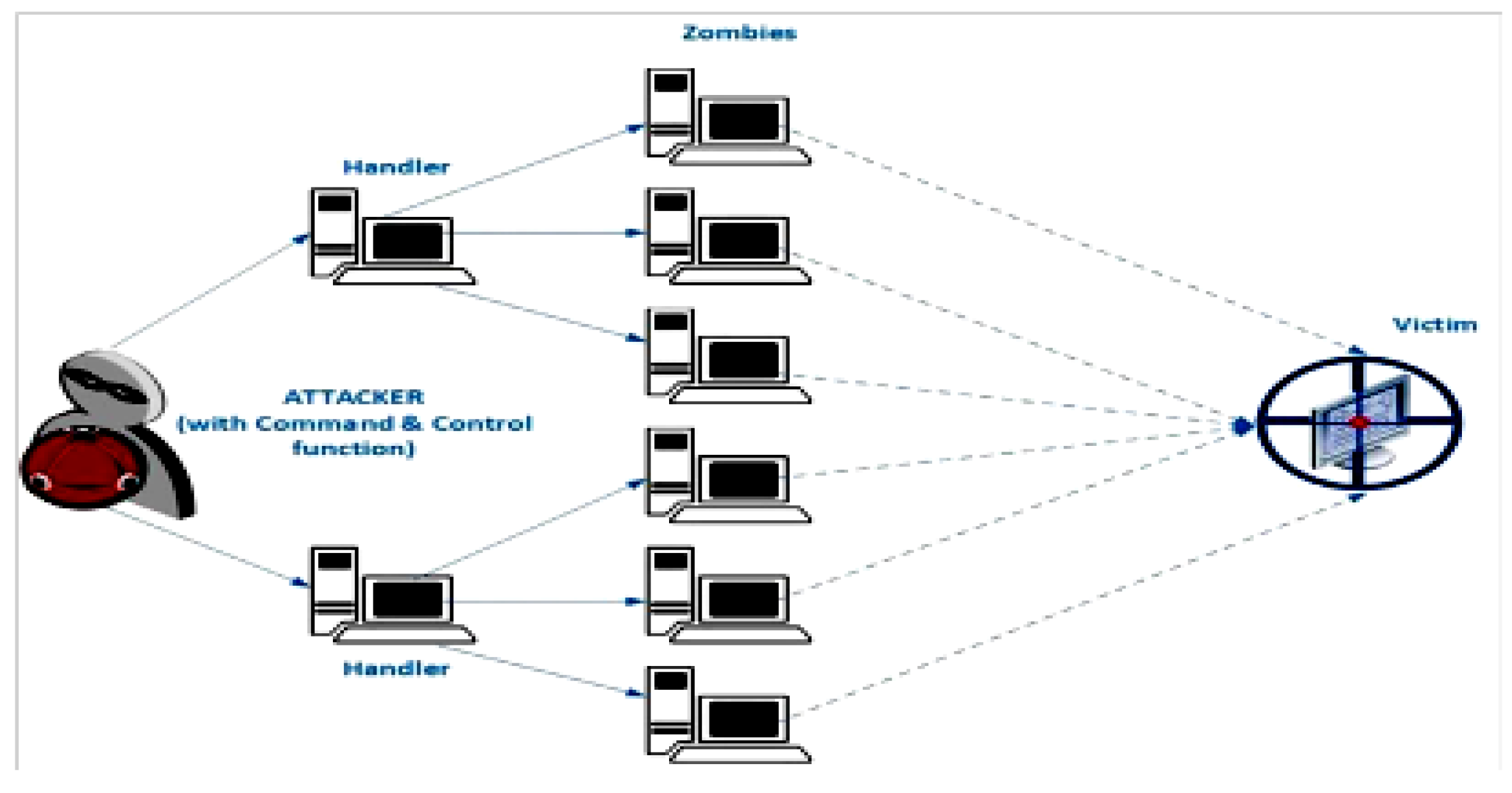
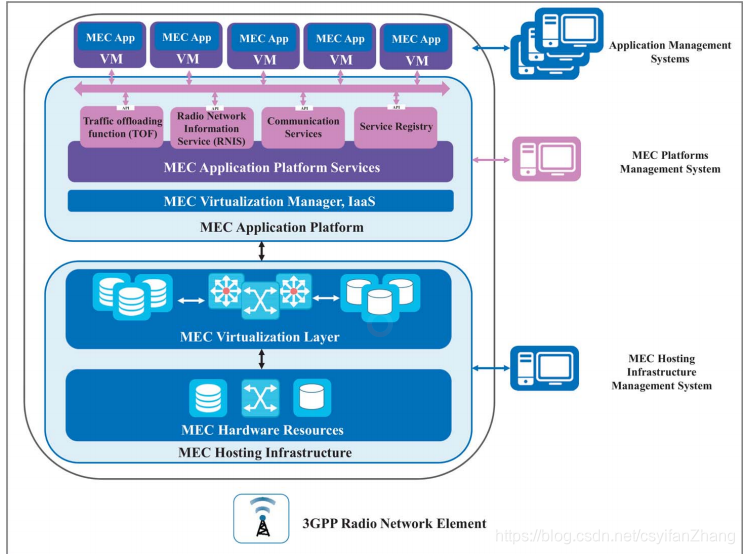
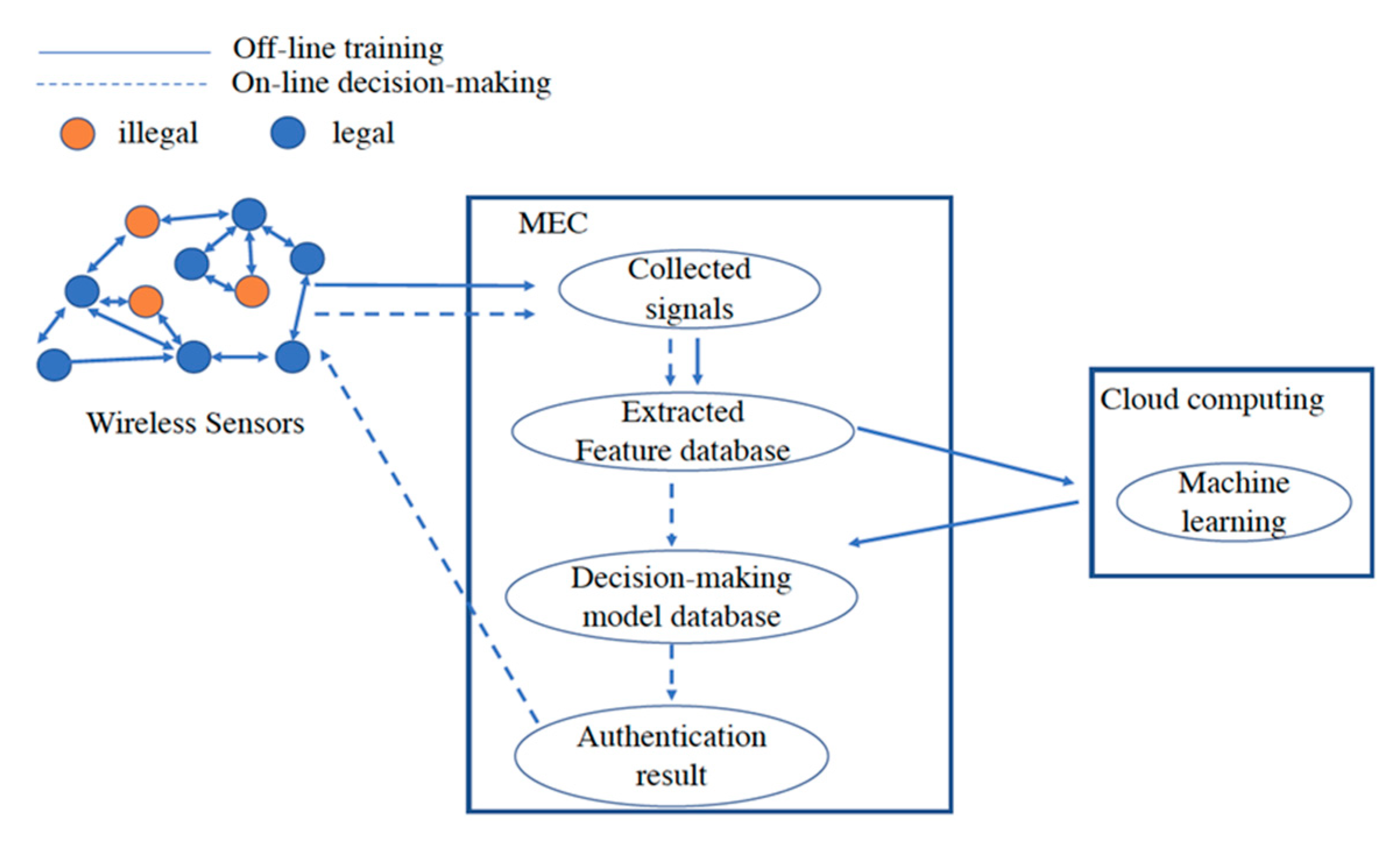
Facilitate learning with our scientific impersonation attack detection in mobile edge computing by levering gallery of numerous educational images. precisely illustrating photography, images, and pictures. perfect for research publications and studies. Each impersonation attack detection in mobile edge computing by levering image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All impersonation attack detection in mobile edge computing by levering images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our impersonation attack detection in mobile edge computing by levering gallery offers diverse visual resources to bring your ideas to life. Our impersonation attack detection in mobile edge computing by levering database continuously expands with fresh, relevant content from skilled photographers. Whether for commercial projects or personal use, our impersonation attack detection in mobile edge computing by levering collection delivers consistent excellence. The impersonation attack detection in mobile edge computing by levering archive serves professionals, educators, and creatives across diverse industries. Multiple resolution options ensure optimal performance across different platforms and applications. Instant download capabilities enable immediate access to chosen impersonation attack detection in mobile edge computing by levering images.