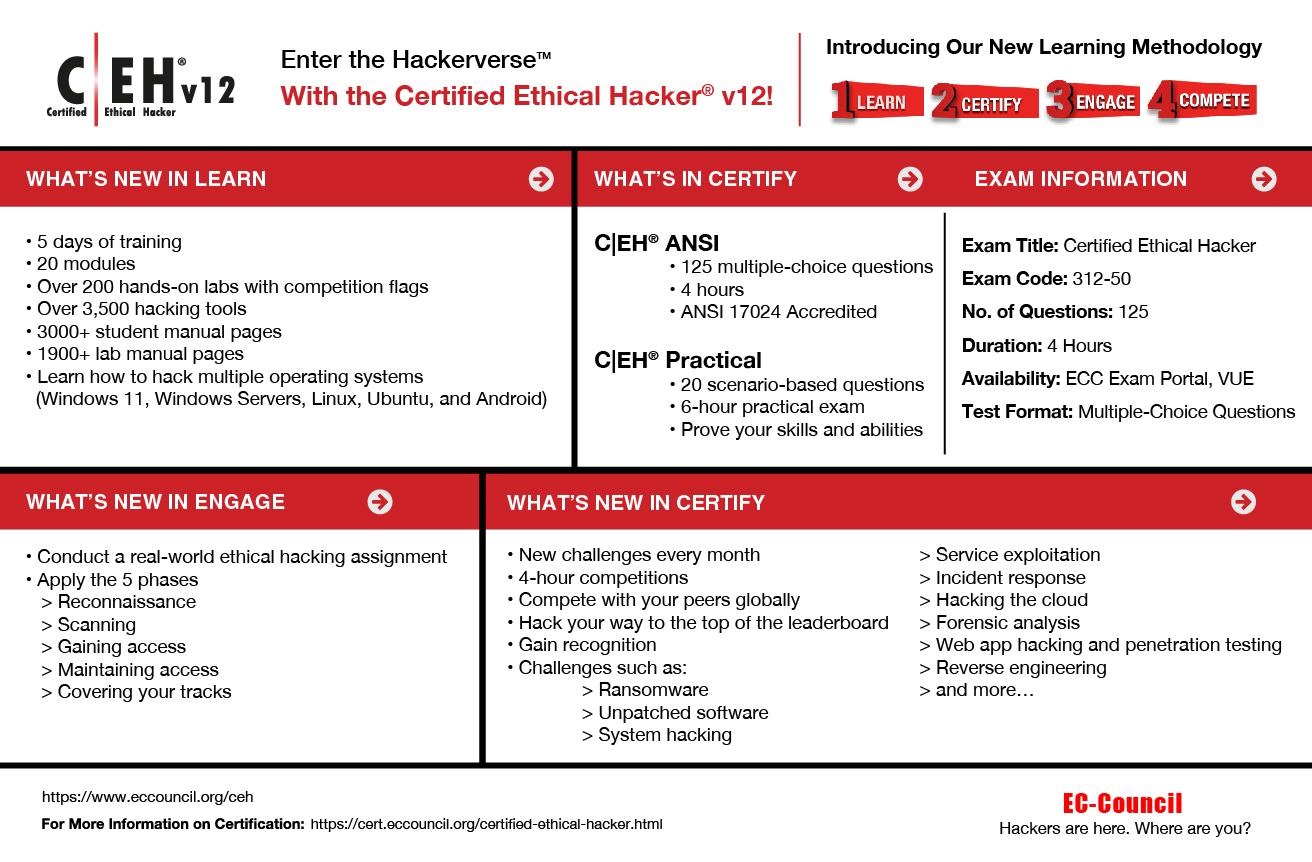
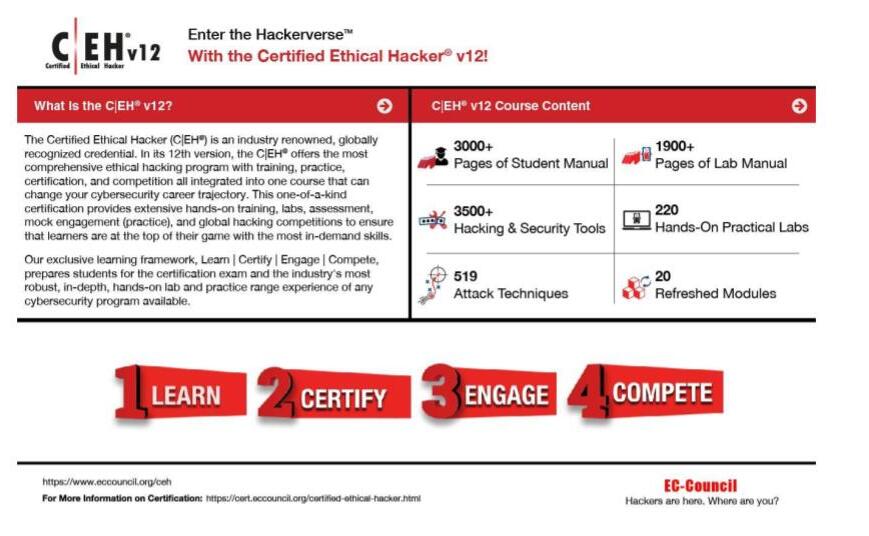
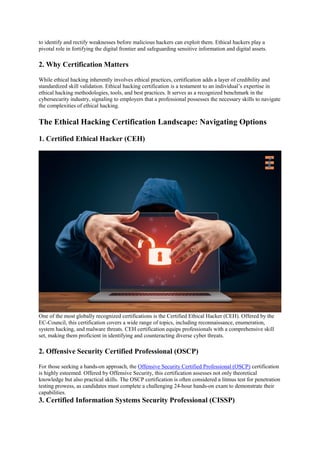
Study the mechanics of the complete cyber security ethical hacking certification bundle | techspot through hundreds of technical photographs. explaining the functional elements of computer, digital, and electronic. designed for instructional and reference materials. Discover high-resolution the complete cyber security ethical hacking certification bundle | techspot images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All the complete cyber security ethical hacking certification bundle | techspot images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our the complete cyber security ethical hacking certification bundle | techspot collection for various creative and professional projects. Cost-effective licensing makes professional the complete cyber security ethical hacking certification bundle | techspot photography accessible to all budgets. Comprehensive tagging systems facilitate quick discovery of relevant the complete cyber security ethical hacking certification bundle | techspot content. The the complete cyber security ethical hacking certification bundle | techspot archive serves professionals, educators, and creatives across diverse industries. Advanced search capabilities make finding the perfect the complete cyber security ethical hacking certification bundle | techspot image effortless and efficient. The the complete cyber security ethical hacking certification bundle | techspot collection represents years of careful curation and professional standards.





































![Certified Ethical Hacker : Preparation Guide [2023]](https://www.whizlabs.com/blog/wp-content/uploads/2023/06/Benefits-of-obtaining-Certified-Ethical-Hacker-certification.webp)





















![Cybersecurity Course Syllabus Guide 2025 [Updated]](https://assets.janbasktraining.com/blog/uploads/images/Ethical_Hacker_1_2_2.jpg)