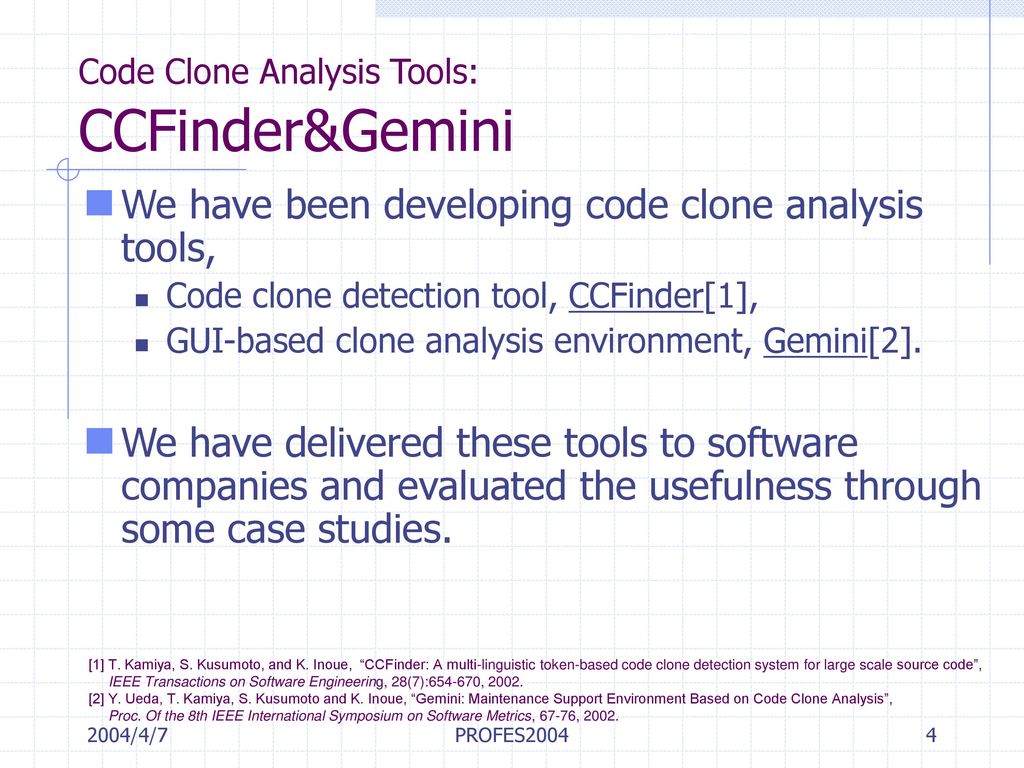
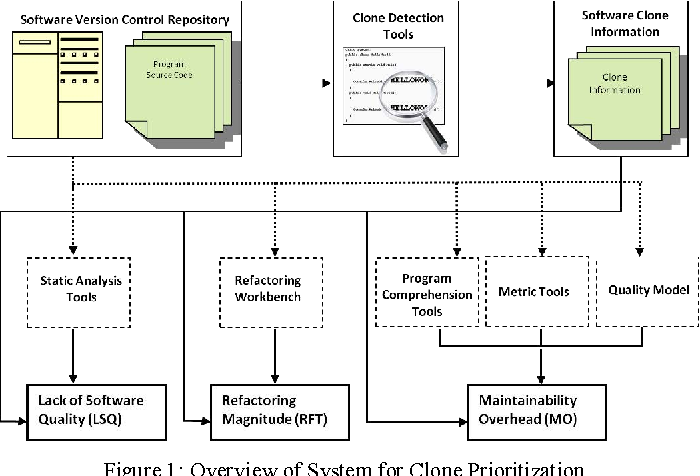
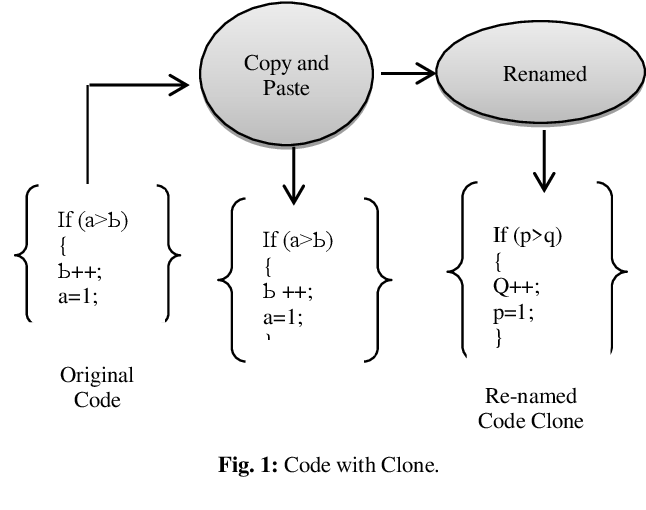
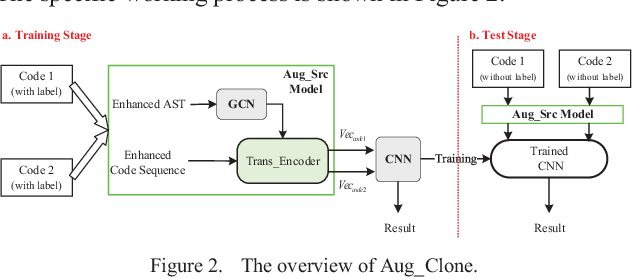
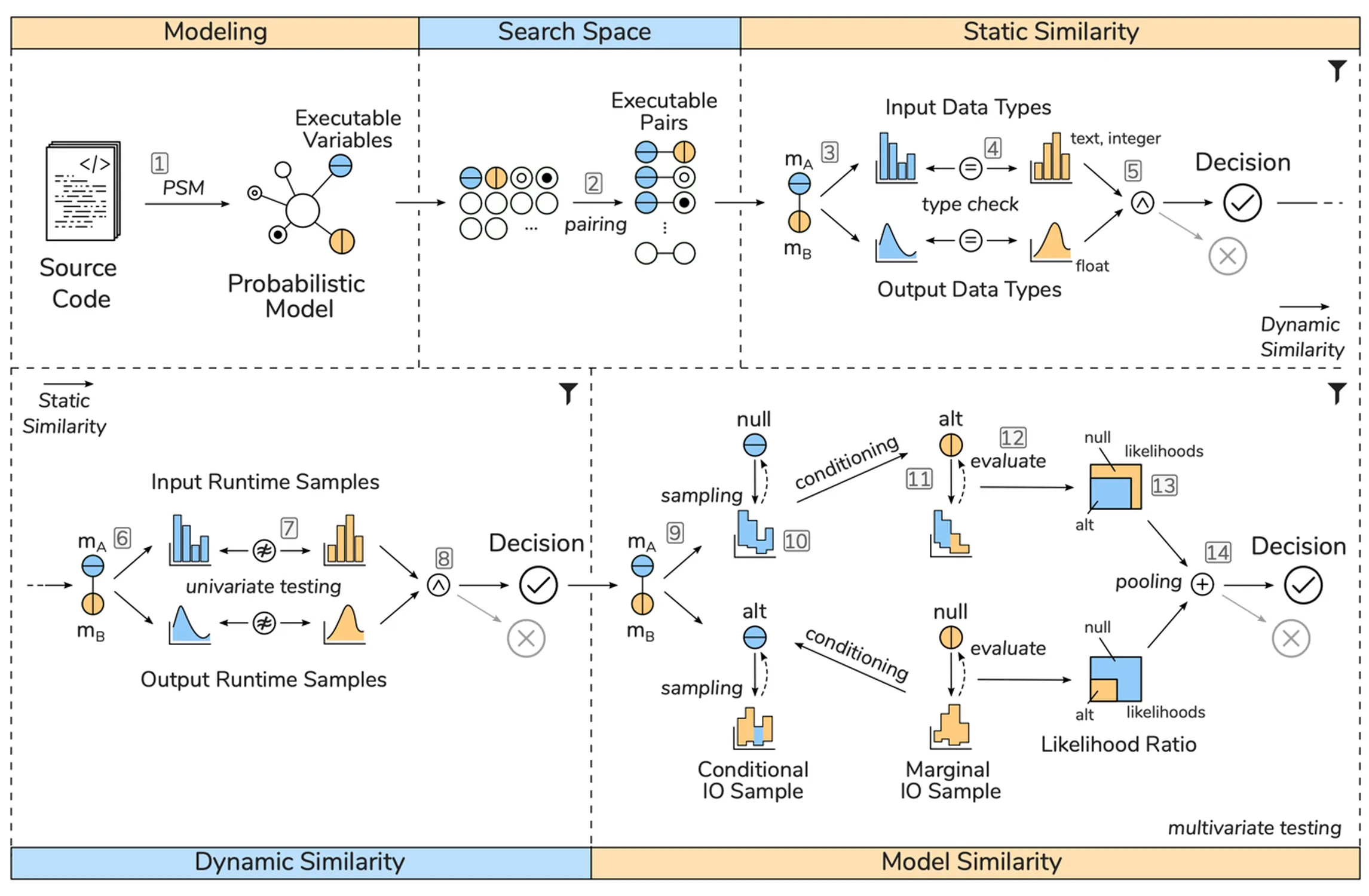
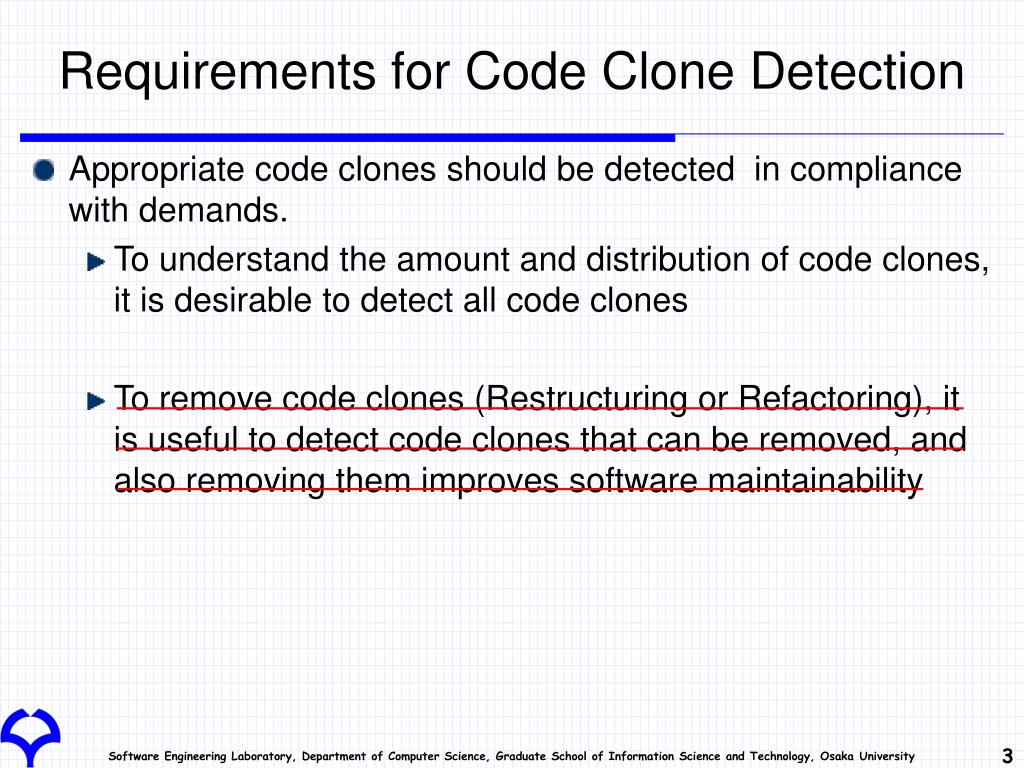
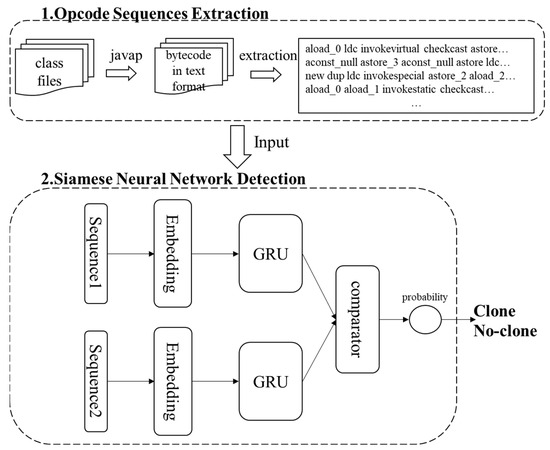
Build enterprises with our business overview of the code clone detection validation process pipeline gallery of comprehensive galleries of strategic images. strategically presenting photography, images, and pictures. perfect for corporate communications and marketing. The overview of the code clone detection validation process pipeline collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All overview of the code clone detection validation process pipeline images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our overview of the code clone detection validation process pipeline gallery offers diverse visual resources to bring your ideas to life. The overview of the code clone detection validation process pipeline collection represents years of careful curation and professional standards. Time-saving browsing features help users locate ideal overview of the code clone detection validation process pipeline images quickly. Instant download capabilities enable immediate access to chosen overview of the code clone detection validation process pipeline images. Reliable customer support ensures smooth experience throughout the overview of the code clone detection validation process pipeline selection process. Professional licensing options accommodate both commercial and educational usage requirements.




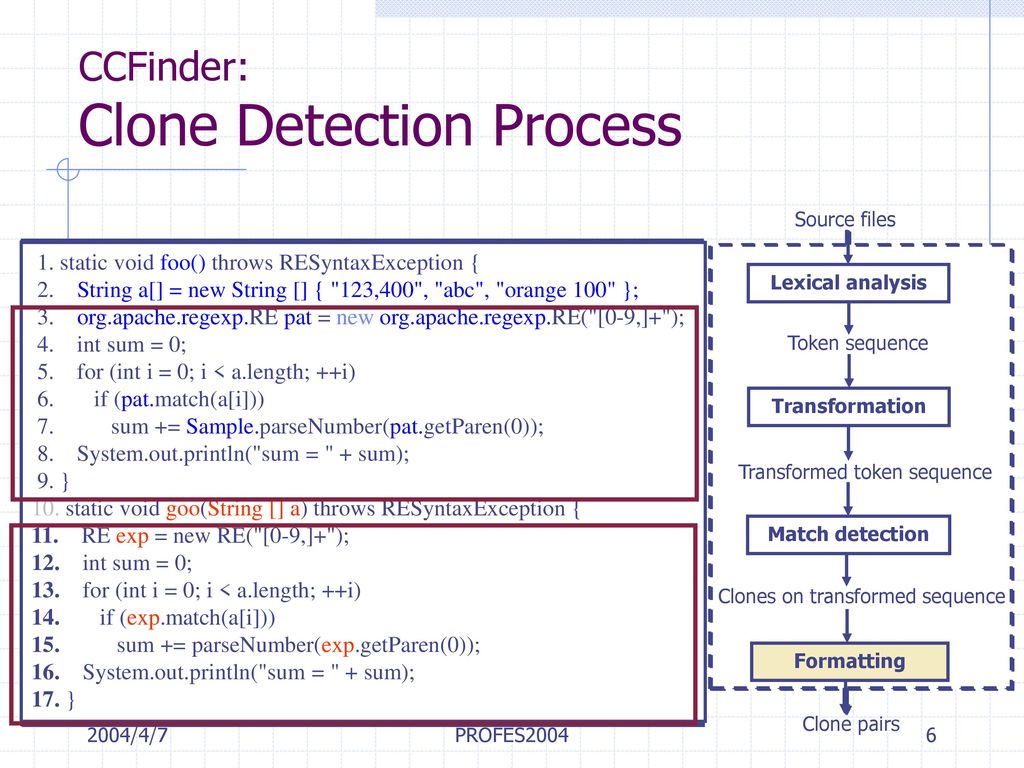
![Generic Code Clone Detection Process [8] | Download Scientific Diagram](https://www.researchgate.net/publication/284593602/figure/fig1/AS:299563387768832@1448432885316/Generic-Code-Clone-Detection-Process-8.png)







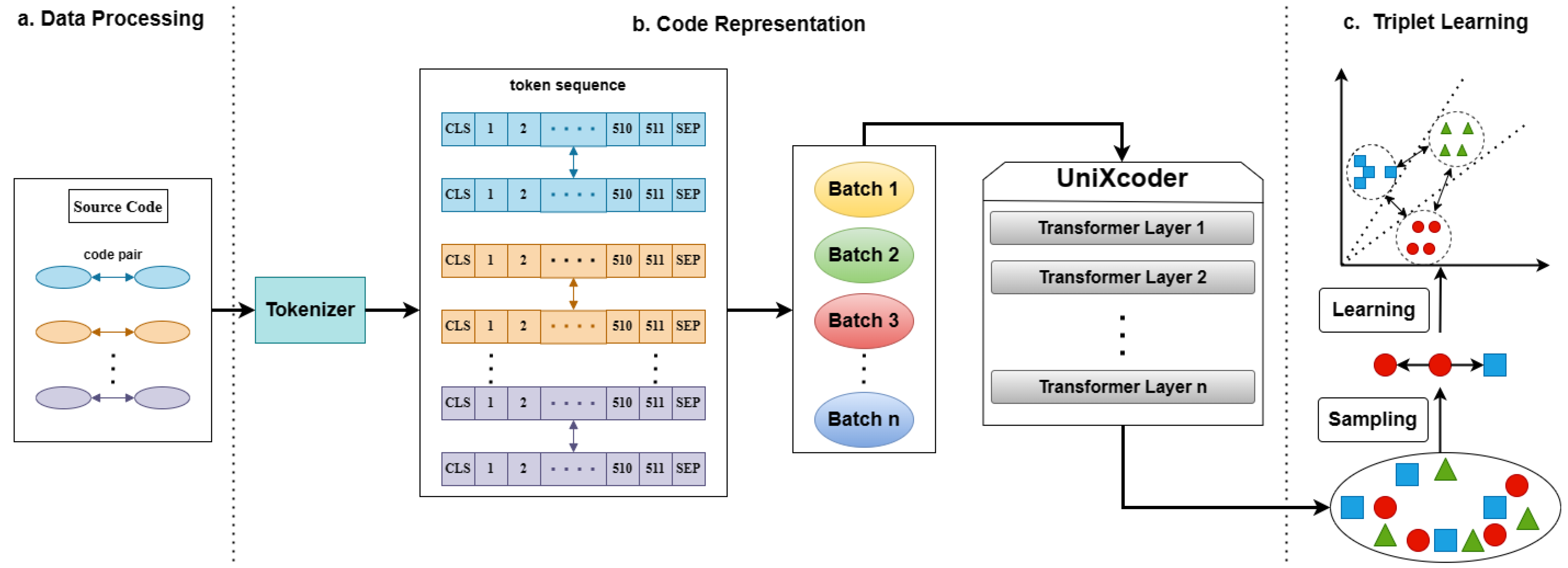









![Code clone detection process by Xue et al. [140]. | Download Scientific ...](https://www.researchgate.net/profile/Hongfa-Xue/publication/333118141/figure/fig8/AS:765081897934849@1559421147721/Code-clone-detection-process-by-Xue-et-al-140.png)


















![Clone detection for business process models [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-1046/1/fig-4-full.png)





![[2308.13754] ZC3: Zero-Shot Cross-Language Code Clone Detection](https://ar5iv.labs.arxiv.org/html/2308.13754/assets/x5.png)
































![Clone detection for business process models [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-1046/1/fig-2-2x.jpg)