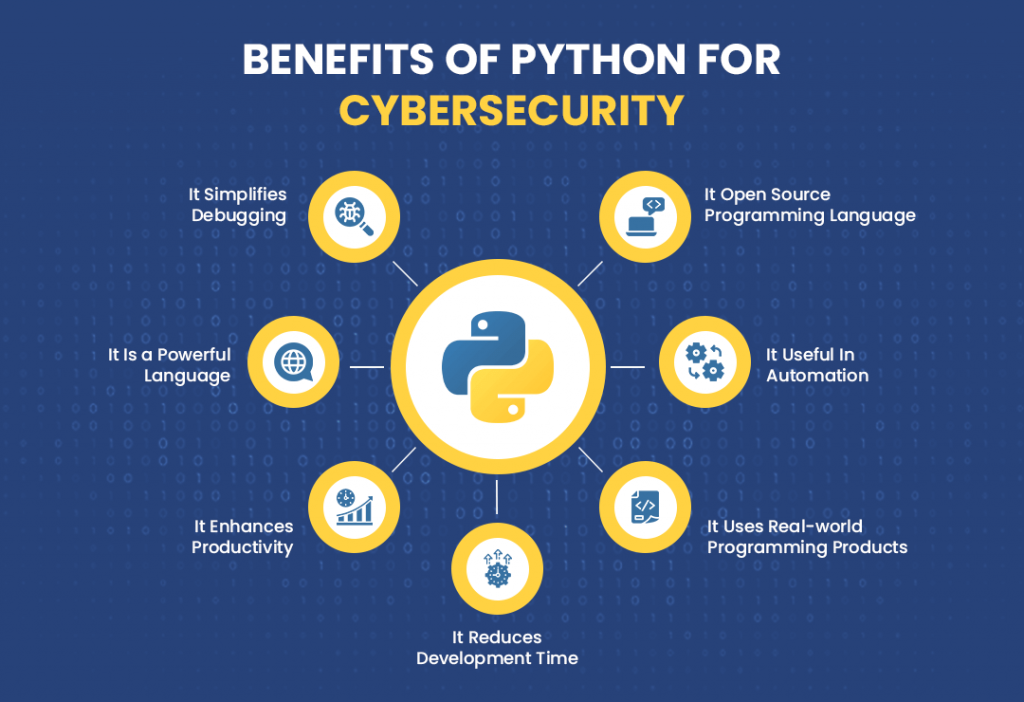
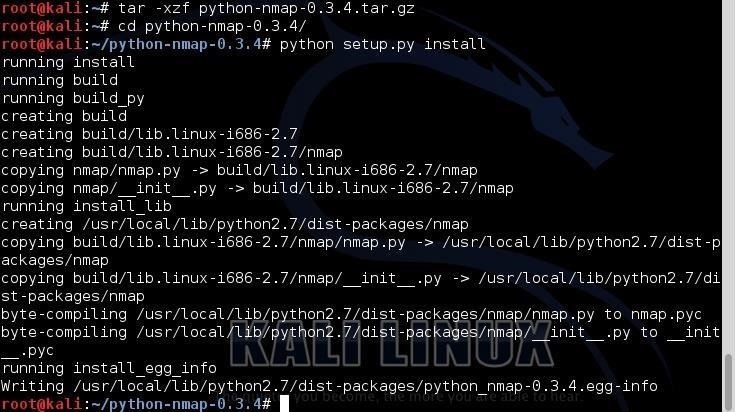
Celebrate the visual poetry of how to use python in hacking - tcm security through vast arrays of carefully composed images. combining innovative composition with emotional depth and visual storytelling. creating lasting impressions through powerful and memorable imagery. Our how to use python in hacking - tcm security collection features high-quality images with excellent detail and clarity. Ideal for artistic projects, creative designs, digital art, and innovative visual expressions All how to use python in hacking - tcm security images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Artists and designers find inspiration in our diverse how to use python in hacking - tcm security gallery, featuring innovative visual approaches. Regular updates keep the how to use python in hacking - tcm security collection current with contemporary trends and styles. Multiple resolution options ensure optimal performance across different platforms and applications. Whether for commercial projects or personal use, our how to use python in hacking - tcm security collection delivers consistent excellence. Time-saving browsing features help users locate ideal how to use python in hacking - tcm security images quickly. Cost-effective licensing makes professional how to use python in hacking - tcm security photography accessible to all budgets.