
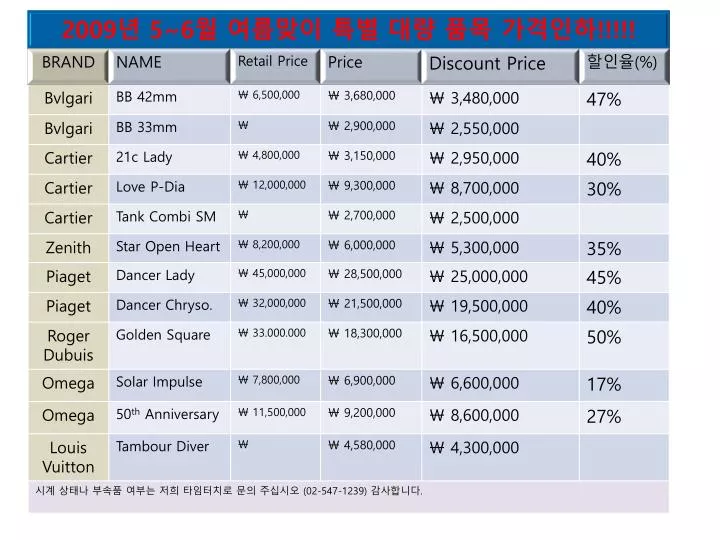
Indulge in the remarkable luxury of our mysql sql injection 공격 모니터링 혁신적인 접근 방법 collection with numerous exquisite images. featuring elegant examples of photography, images, and pictures. perfect for high-end marketing and branding. The mysql sql injection 공격 모니터링 혁신적인 접근 방법 collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All mysql sql injection 공격 모니터링 혁신적인 접근 방법 images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect mysql sql injection 공격 모니터링 혁신적인 접근 방법 images to enhance your visual communication needs. Our mysql sql injection 공격 모니터링 혁신적인 접근 방법 database continuously expands with fresh, relevant content from skilled photographers. Professional licensing options accommodate both commercial and educational usage requirements. Each image in our mysql sql injection 공격 모니터링 혁신적인 접근 방법 gallery undergoes rigorous quality assessment before inclusion. Cost-effective licensing makes professional mysql sql injection 공격 모니터링 혁신적인 접근 방법 photography accessible to all budgets. Comprehensive tagging systems facilitate quick discovery of relevant mysql sql injection 공격 모니터링 혁신적인 접근 방법 content. Instant download capabilities enable immediate access to chosen mysql sql injection 공격 모니터링 혁신적인 접근 방법 images. Advanced search capabilities make finding the perfect mysql sql injection 공격 모니터링 혁신적인 접근 방법 image effortless and efficient. Time-saving browsing features help users locate ideal mysql sql injection 공격 모니터링 혁신적인 접근 방법 images quickly. The mysql sql injection 공격 모니터링 혁신적인 접근 방법 collection represents years of careful curation and professional standards.



![[돌발영상] '우리가 남이가' ("공보다 사"… 홍준표 시장이 예산을 챙기는 방법은?) / YTN - YouTube](https://i.ytimg.com/vi/iNO8z6bpLHE/maxresdefault.jpg)


















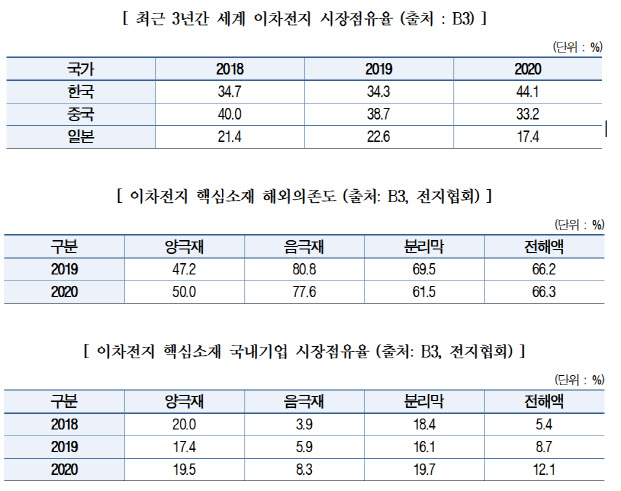




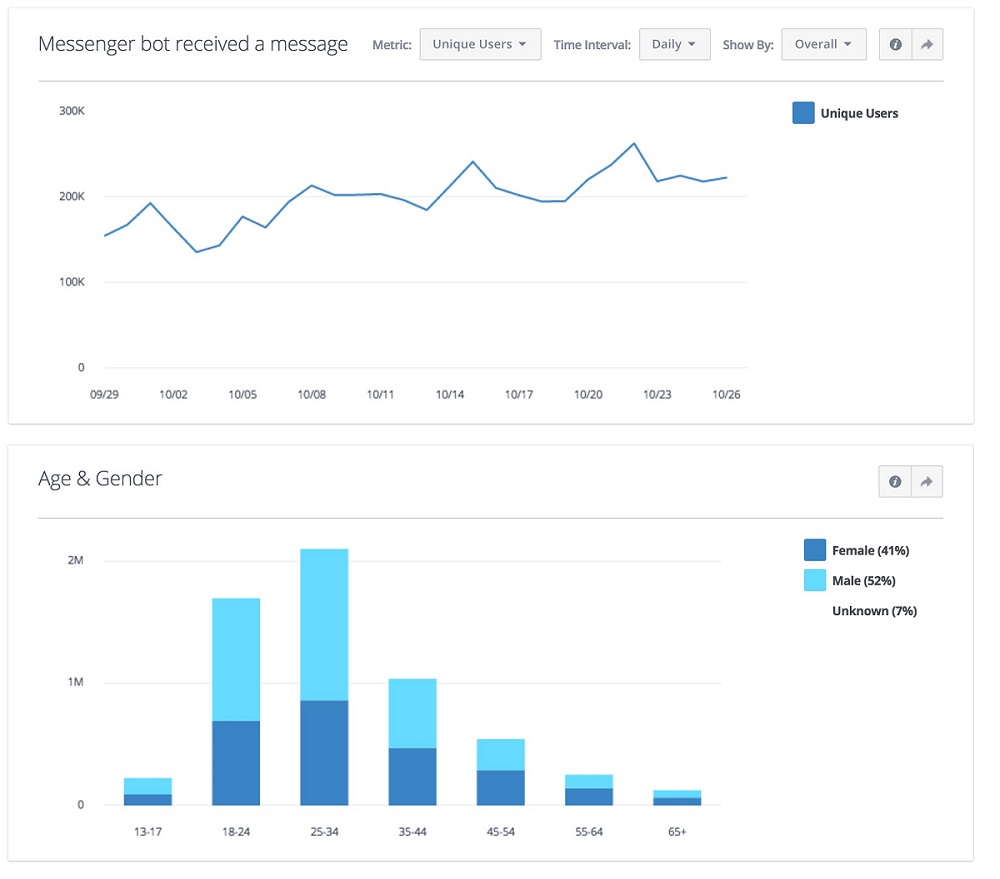




























![2013년 제2회 전기산업기사실기 역율 90[%]로 개선하여 전용량까지 부하에 공급 시 콘덴서 용량 에듀피디 임정빈 - YouTube](https://i.ytimg.com/vi/atJs2T22OnY/maxresdefault.jpg)




















![[중1, 중2, 농도문제] 소금물에서 물이 증발하는 경우 3초 만에 풀기 - YouTube](https://i.ytimg.com/vi/I-DKvcNDh_M/maxresdefault.jpg)

