Indulge your senses with our culinary security best practices for oauth 2.0 gallery of substantial collections of delicious images. appetizingly showcasing photography, images, and pictures. designed to stimulate appetite and interest. Our security best practices for oauth 2.0 collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All security best practices for oauth 2.0 images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect security best practices for oauth 2.0 images to enhance your visual communication needs. Whether for commercial projects or personal use, our security best practices for oauth 2.0 collection delivers consistent excellence. Instant download capabilities enable immediate access to chosen security best practices for oauth 2.0 images. The security best practices for oauth 2.0 archive serves professionals, educators, and creatives across diverse industries. Our security best practices for oauth 2.0 database continuously expands with fresh, relevant content from skilled photographers. Time-saving browsing features help users locate ideal security best practices for oauth 2.0 images quickly. Regular updates keep the security best practices for oauth 2.0 collection current with contemporary trends and styles. Each image in our security best practices for oauth 2.0 gallery undergoes rigorous quality assessment before inclusion.

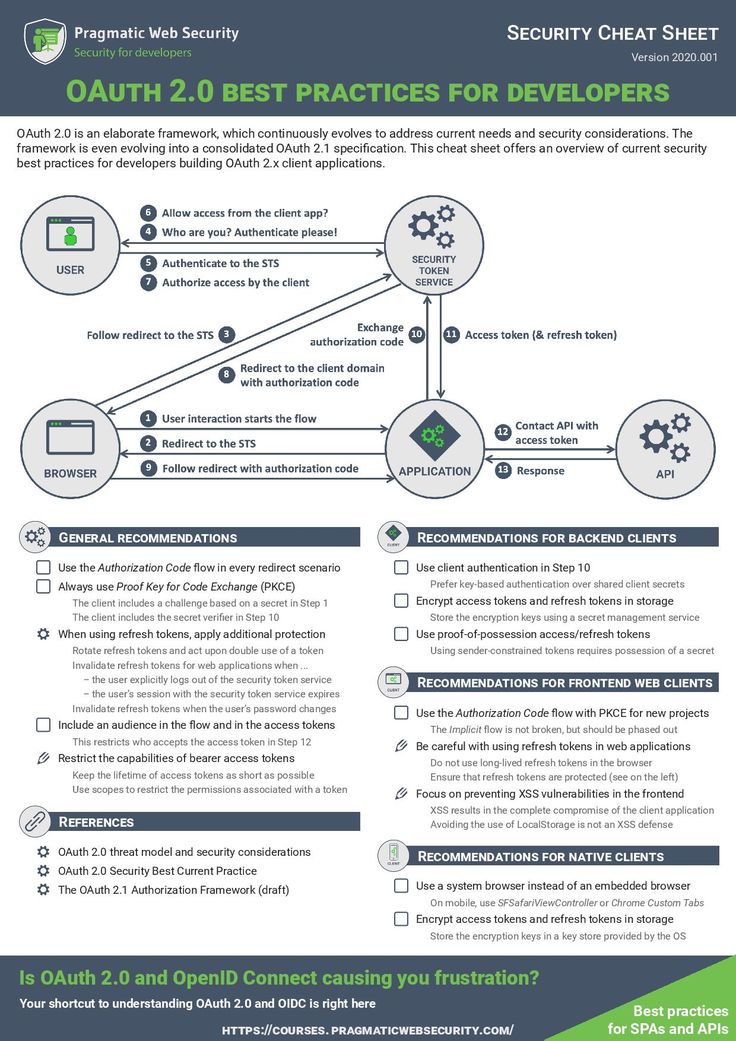

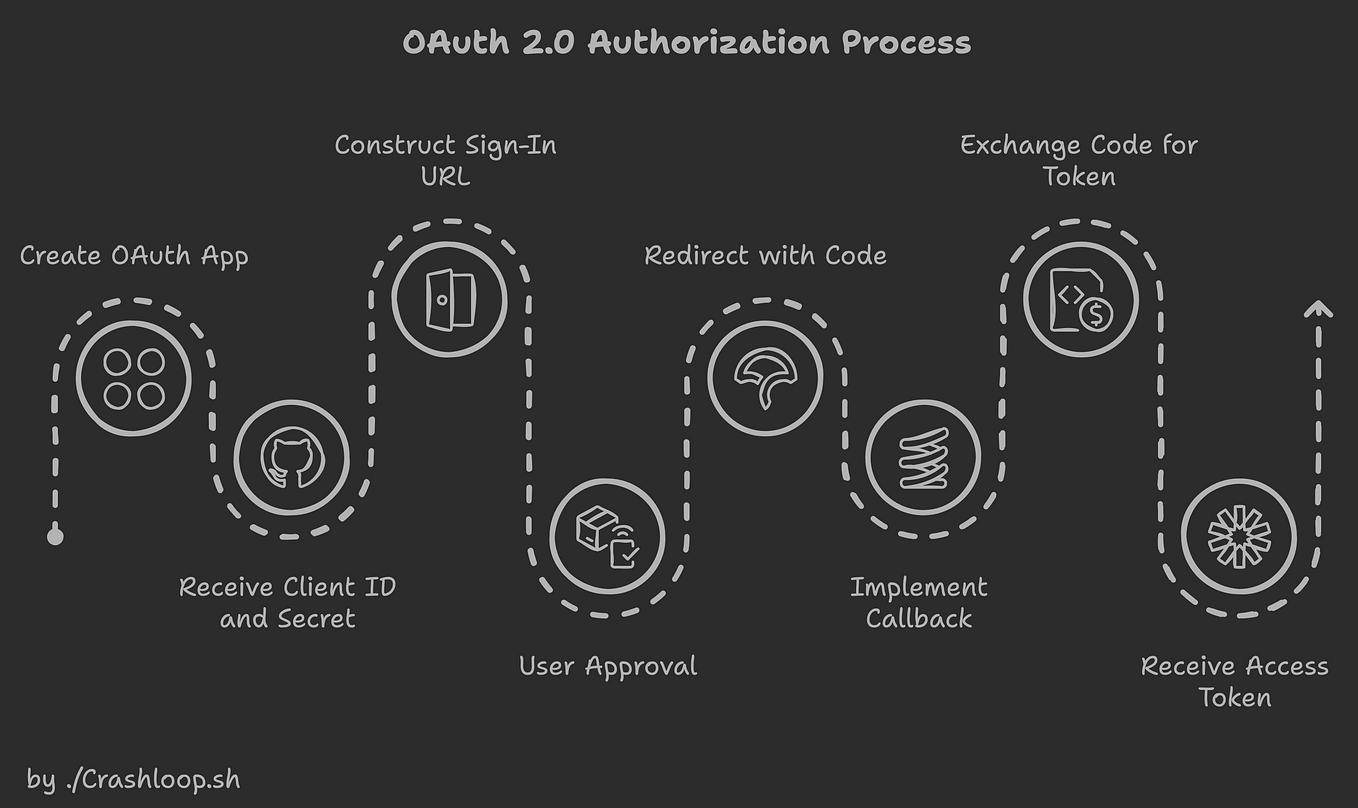
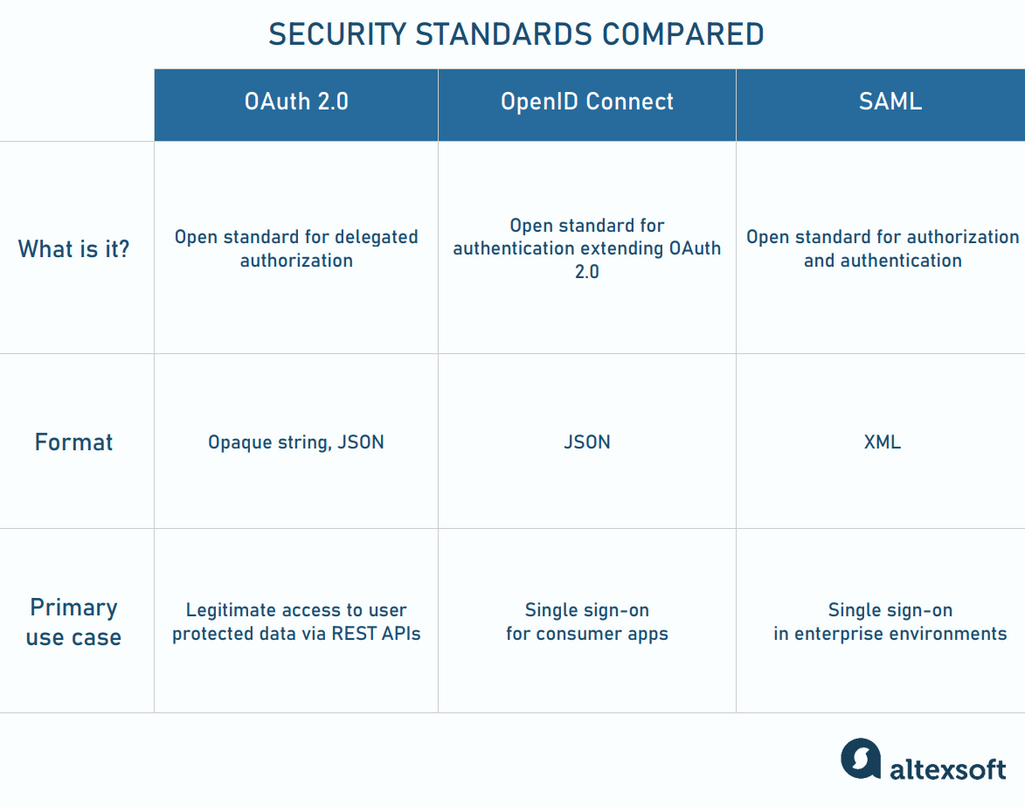











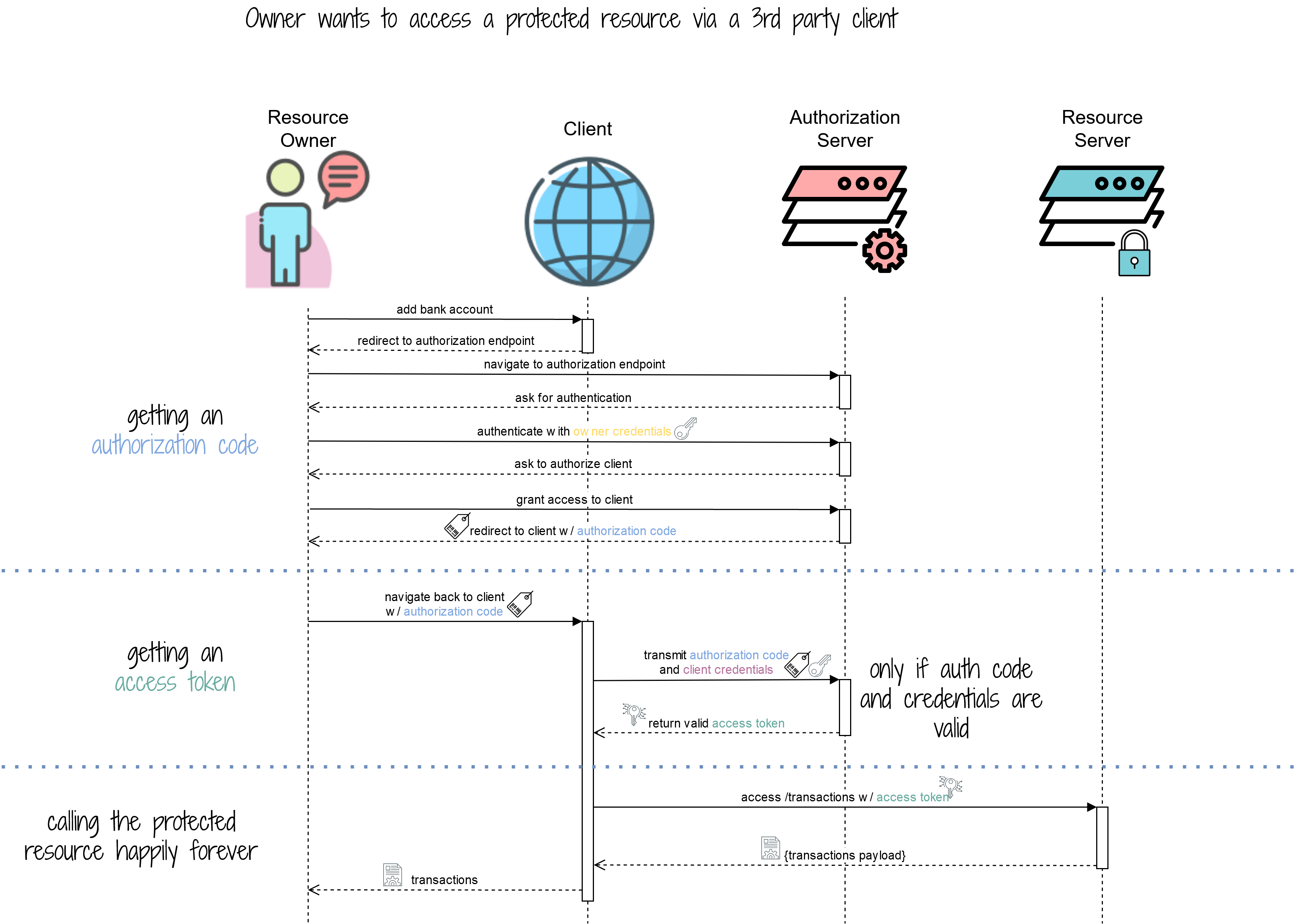



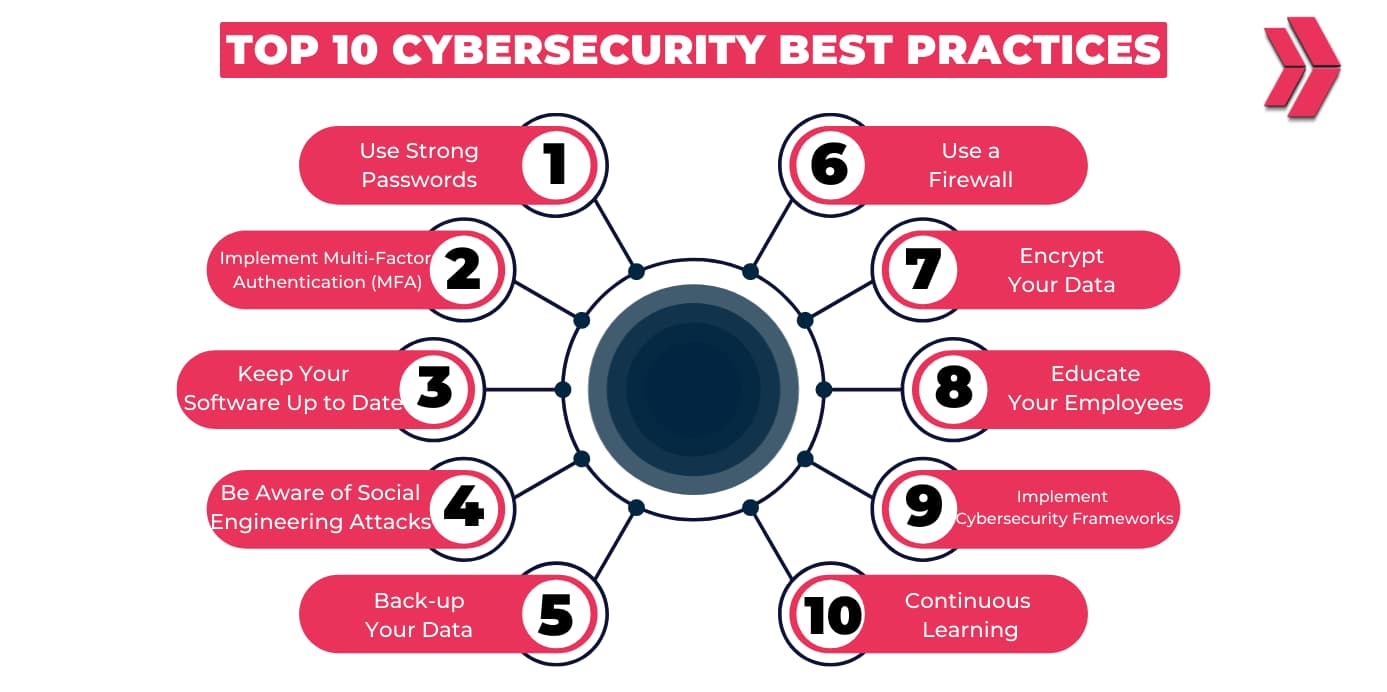


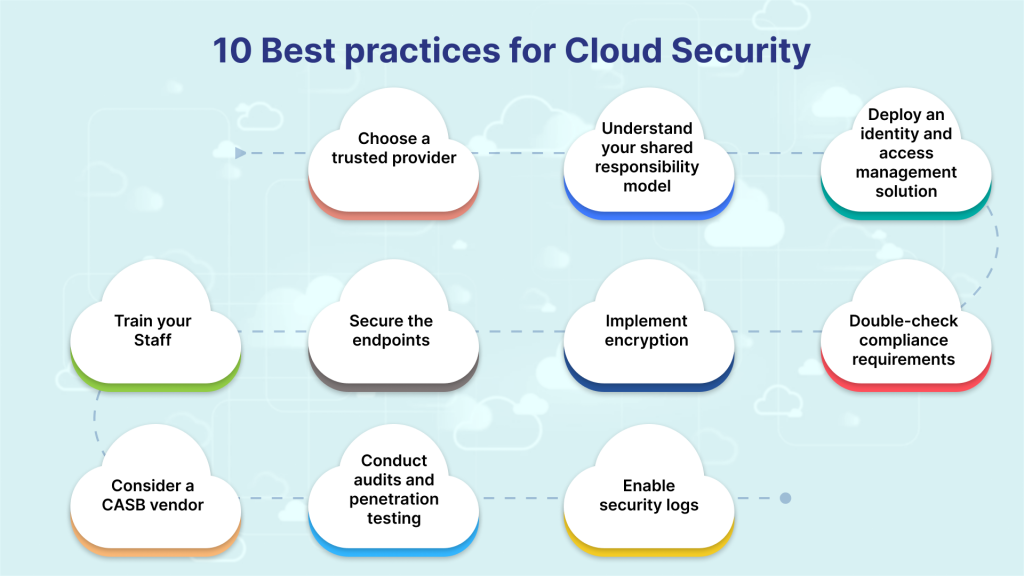
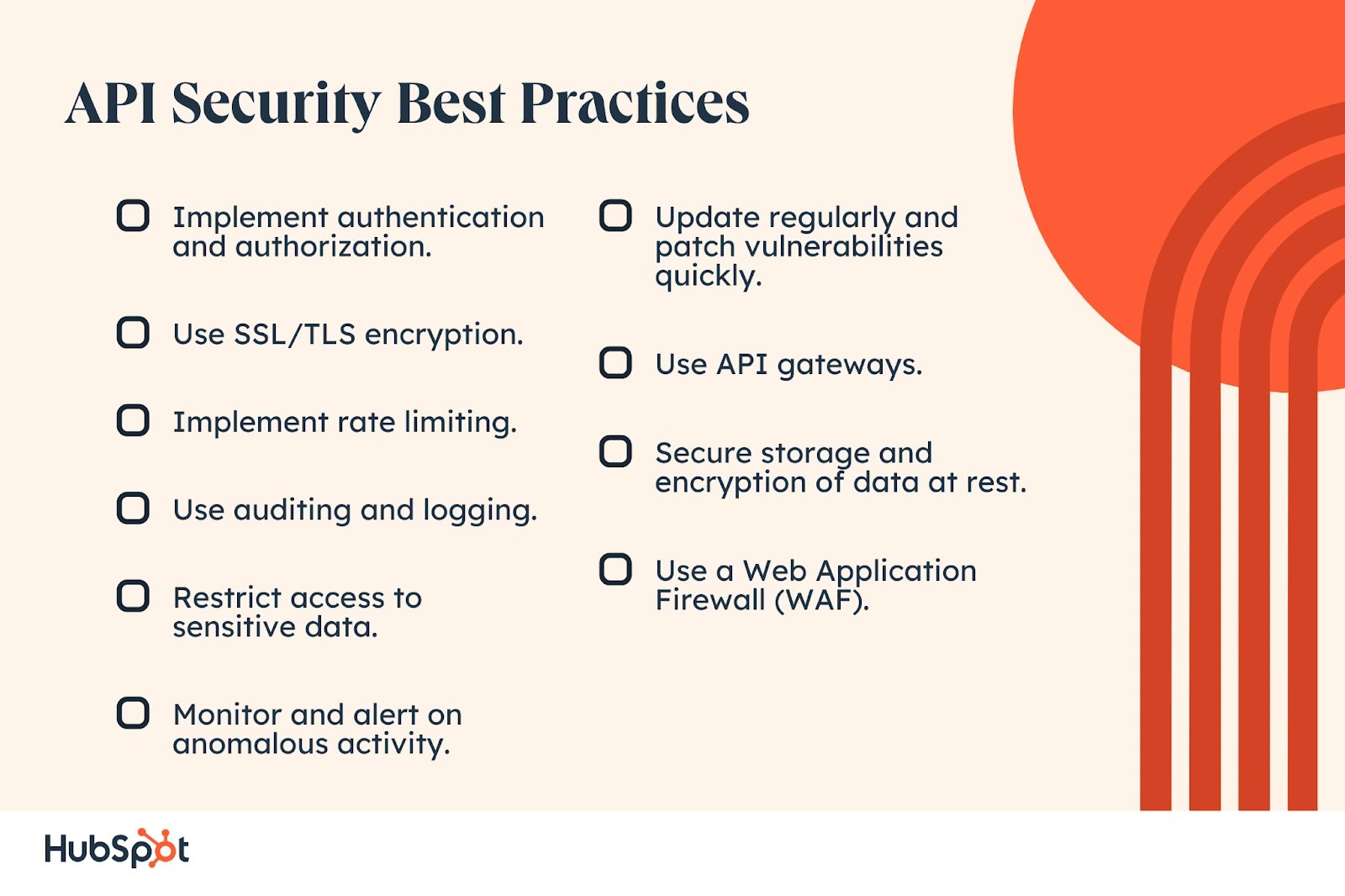
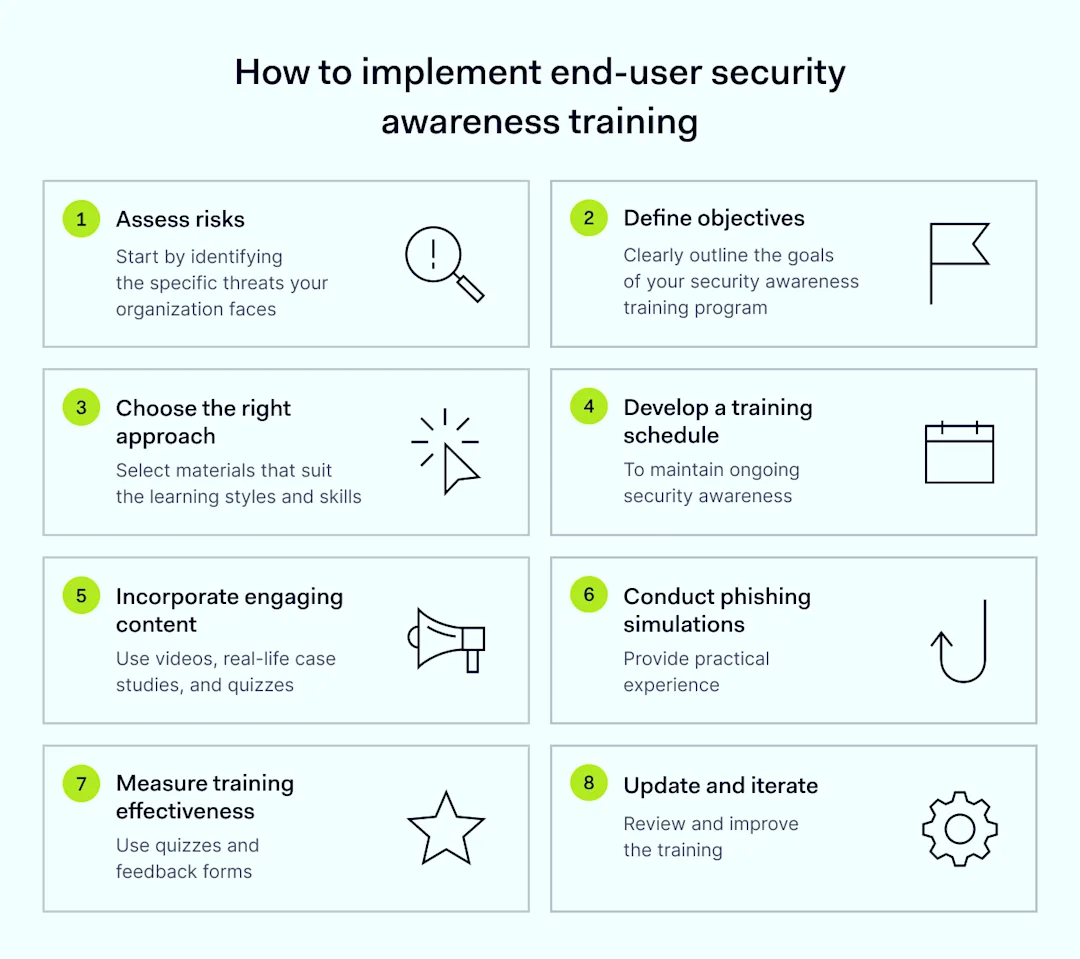
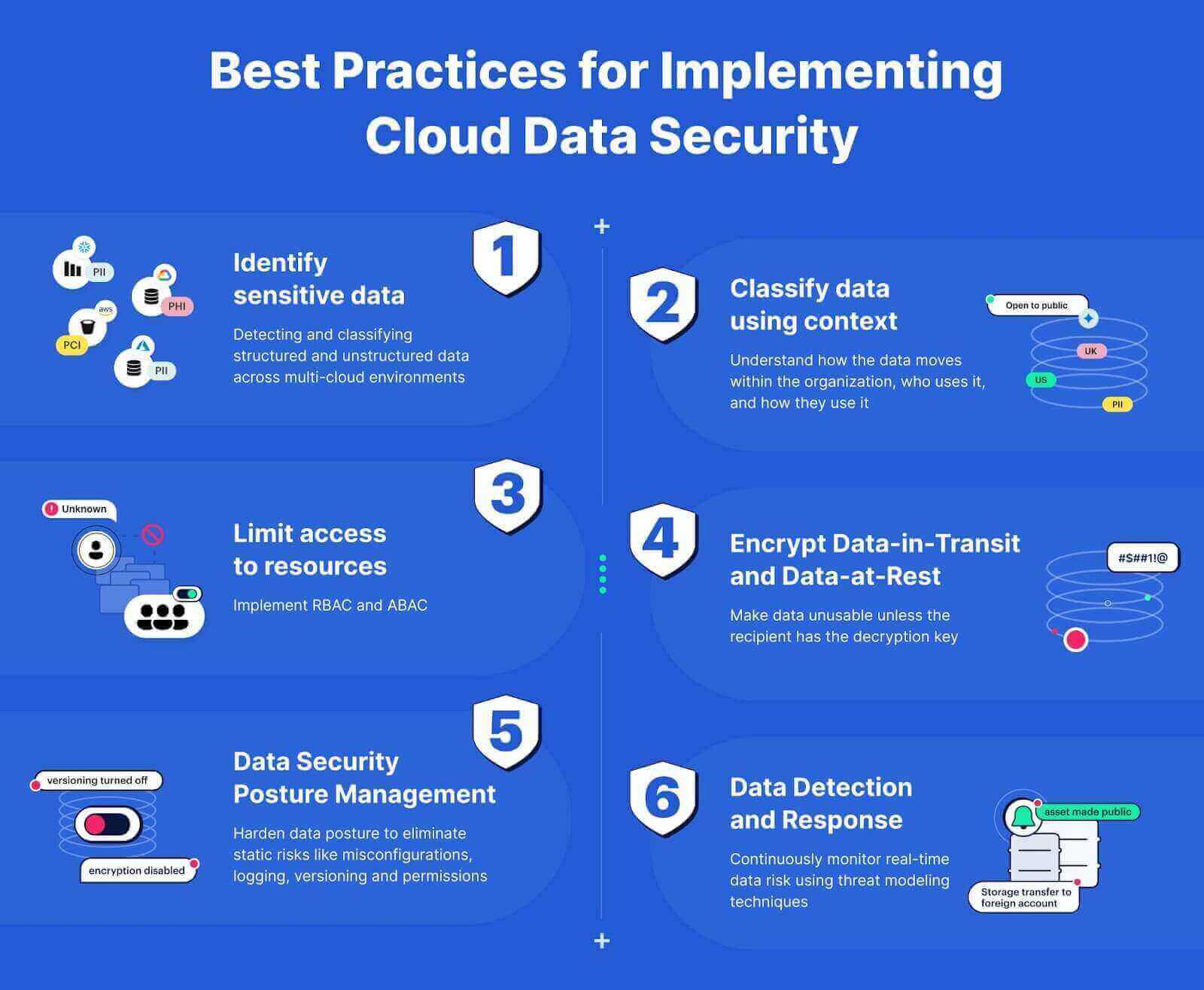
















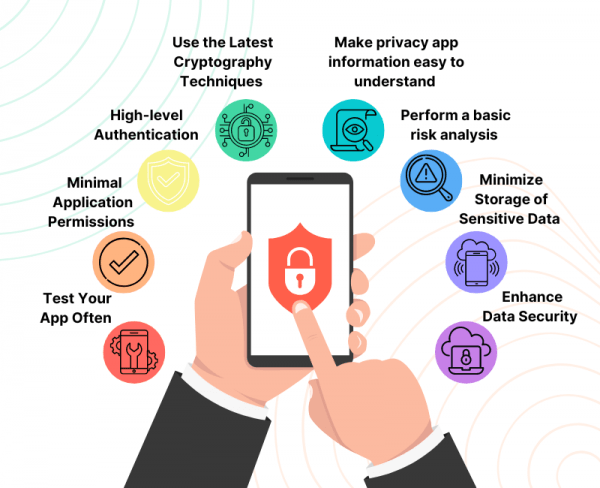




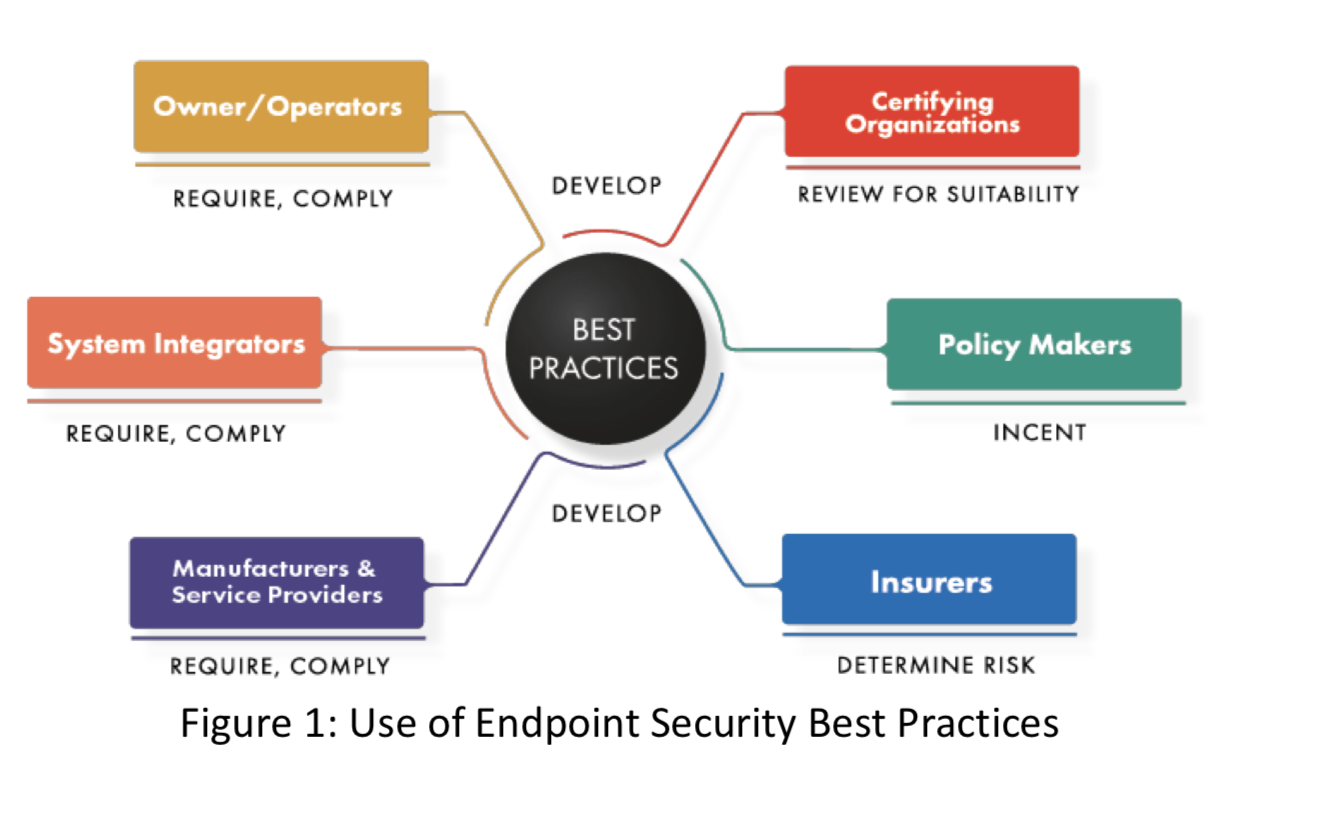
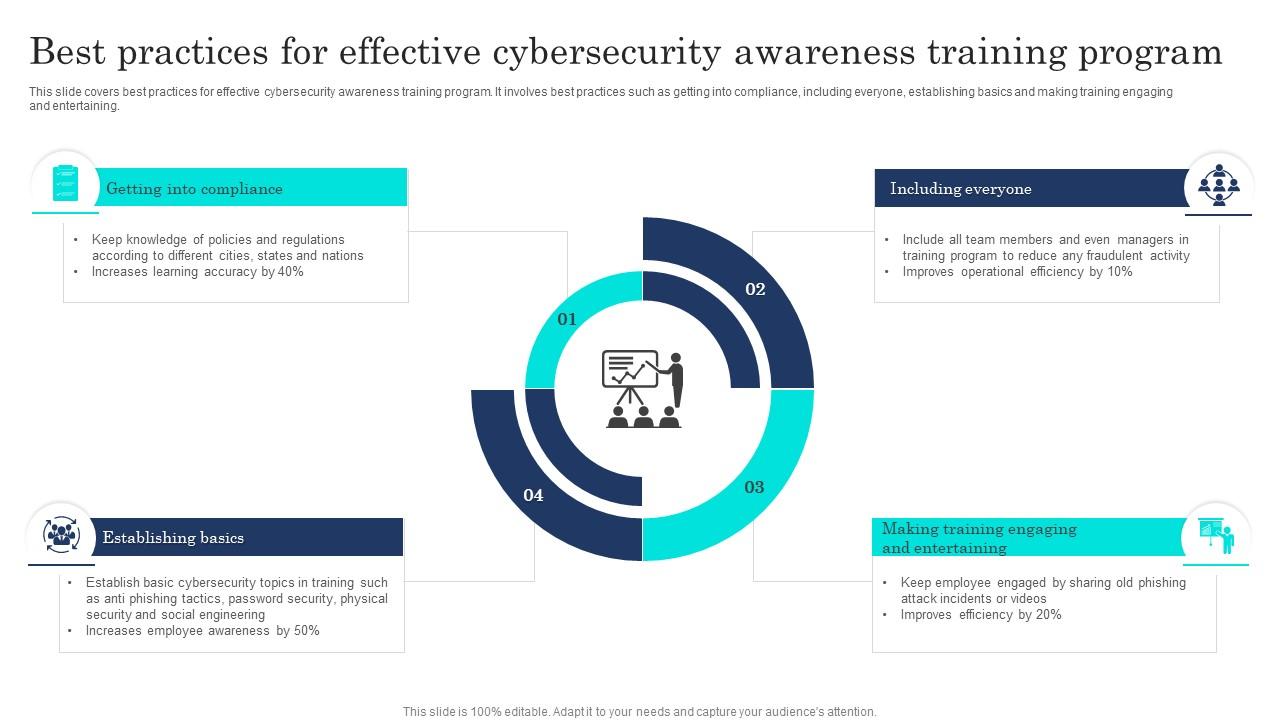
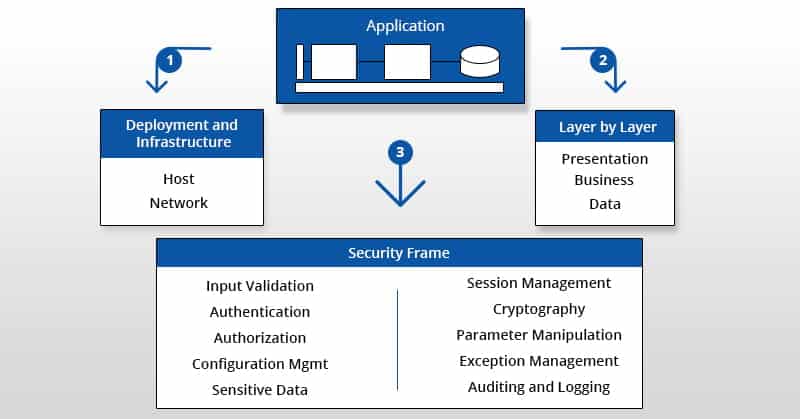




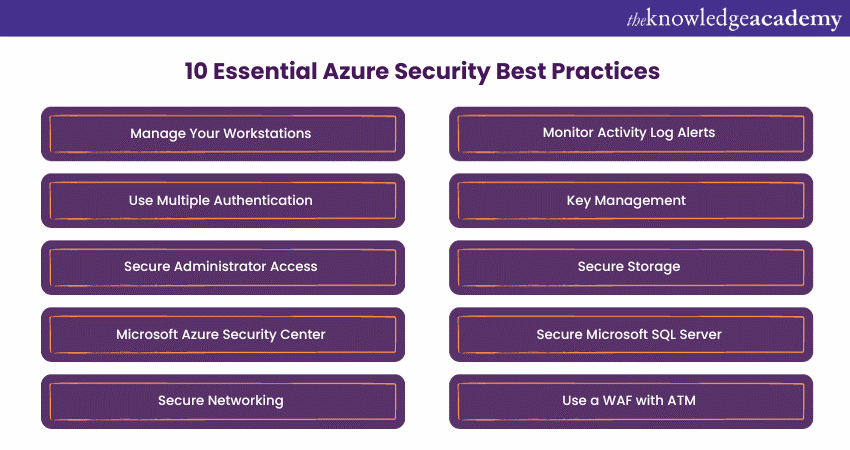
![Azure Security Best Practices [Cheat Sheet] | Wiz](https://www.datocms-assets.com/75231/1701803157-azure-security-best-practices-cheat-sheet-cover.png)