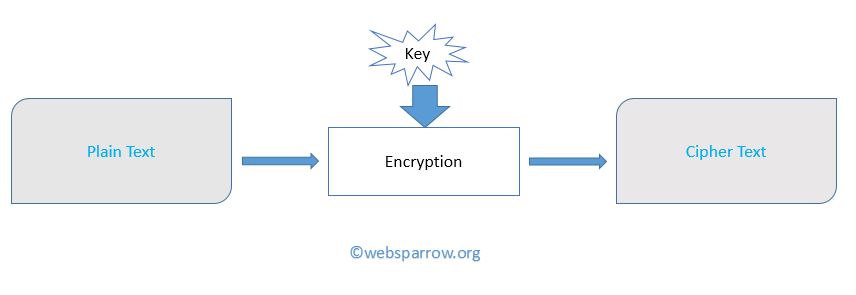
Design the future through hundreds of architecture-focused java cryptography (blowfish encryption & decryption tutorial) | by arie photographs. spatially documenting photography, images, and pictures. designed to inspire architectural innovation. Our java cryptography (blowfish encryption & decryption tutorial) | by arie collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All java cryptography (blowfish encryption & decryption tutorial) | by arie images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our java cryptography (blowfish encryption & decryption tutorial) | by arie gallery offers diverse visual resources to bring your ideas to life. Reliable customer support ensures smooth experience throughout the java cryptography (blowfish encryption & decryption tutorial) | by arie selection process. Advanced search capabilities make finding the perfect java cryptography (blowfish encryption & decryption tutorial) | by arie image effortless and efficient. Cost-effective licensing makes professional java cryptography (blowfish encryption & decryption tutorial) | by arie photography accessible to all budgets. The java cryptography (blowfish encryption & decryption tutorial) | by arie collection represents years of careful curation and professional standards. Diverse style options within the java cryptography (blowfish encryption & decryption tutorial) | by arie collection suit various aesthetic preferences.







































![[TUTORIAL] How to encrypt/decrypt data using C# (Source Code Free ...](https://i.ytimg.com/vi/nTiBQ7nNdDo/maxresdefault.jpg)












![Blowfish encryption algorithm [12–15, 17, 21]. | Download Scientific ...](https://www.researchgate.net/publication/350655579/figure/fig12/AS:1080288960610396@1634572367573/Blowfish-encryption-algorithm-12-15-17-21.jpg)


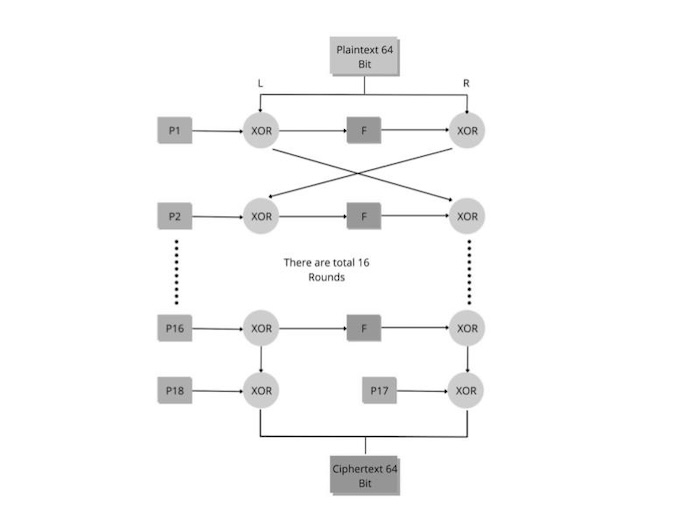



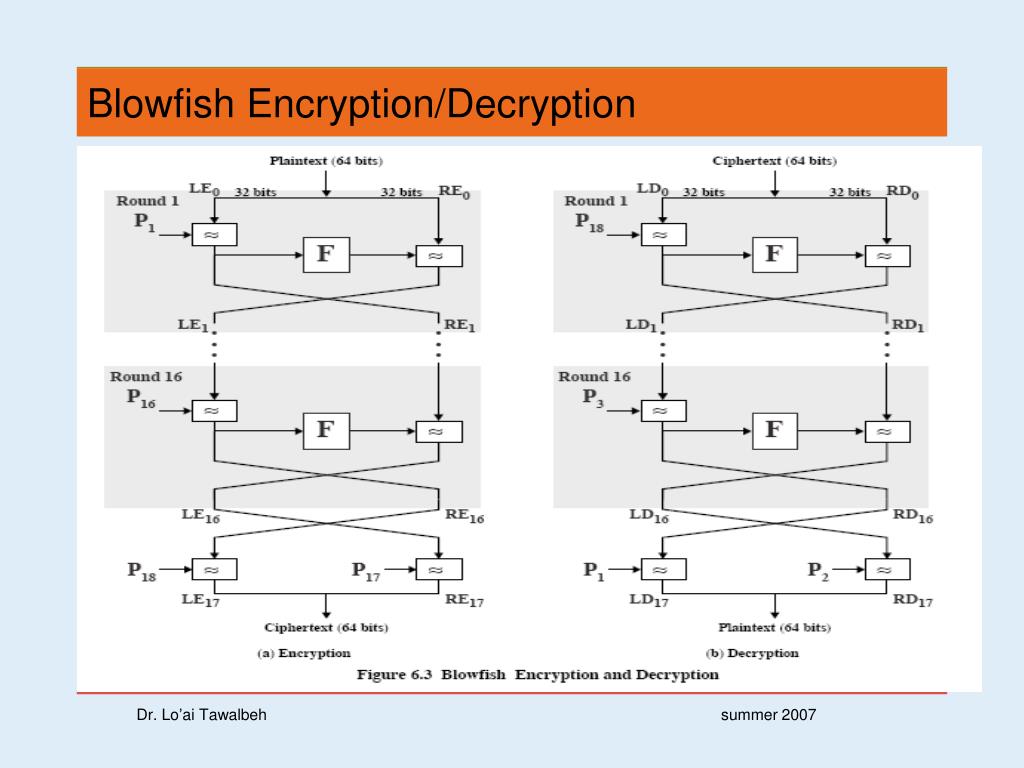













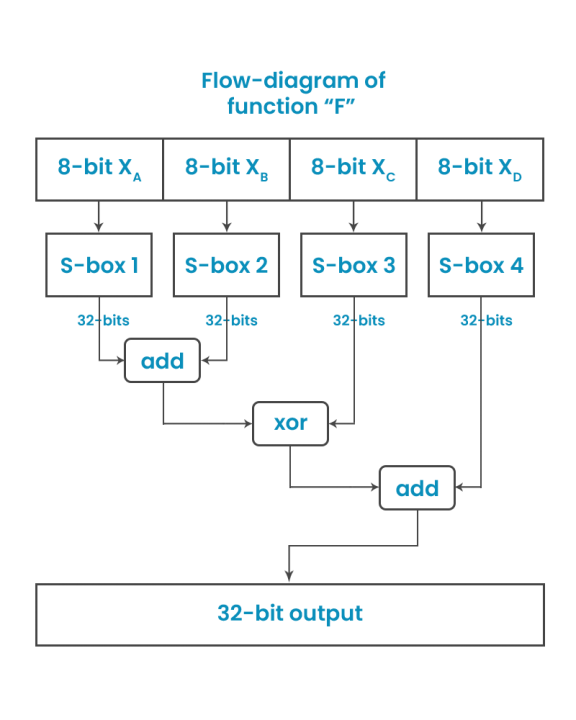
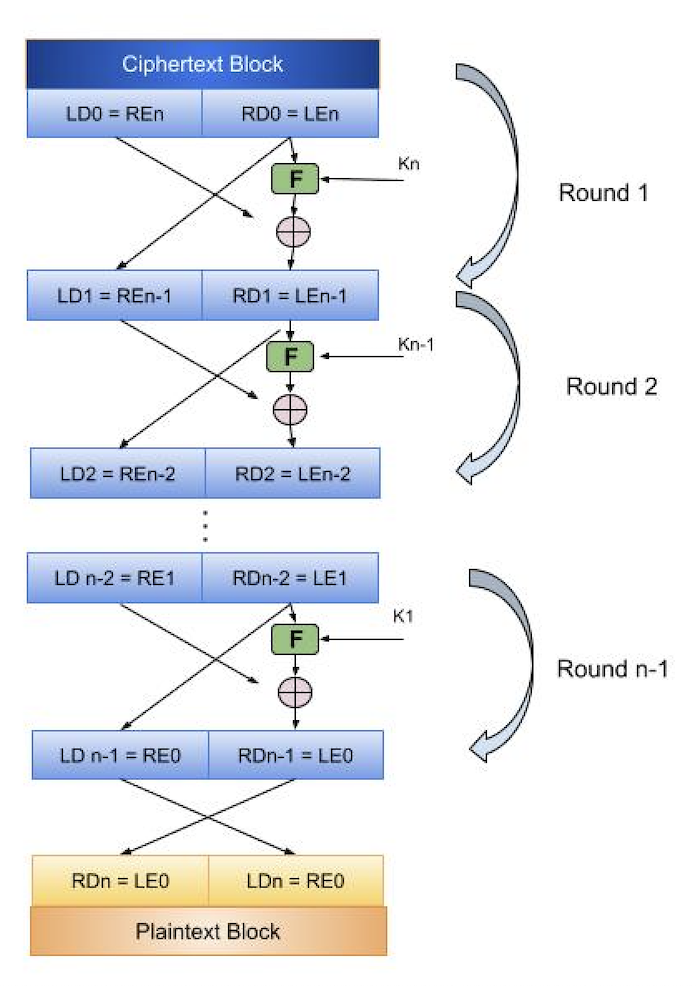





![Encryption in blowfish algorithm[7]. | Download Scientific Diagram](https://www.researchgate.net/profile/Ali-Bermani/publication/350417078/figure/fig3/AS:1043773178007554@1625866326973/Encryption-in-blowfish-algorithm7.png)