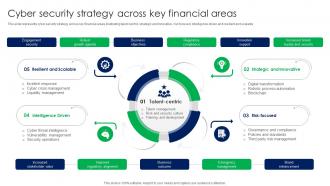
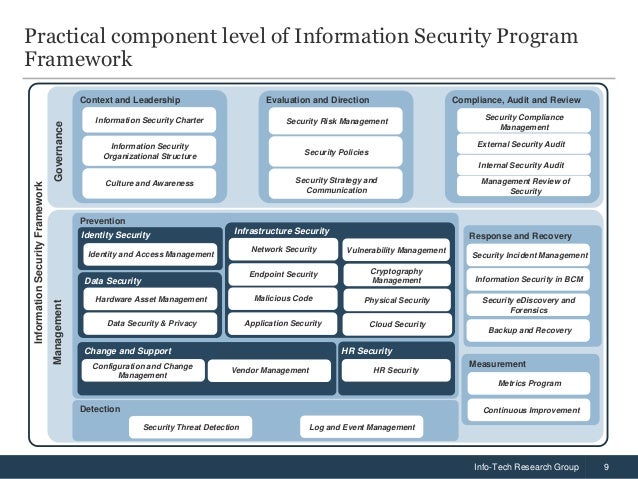
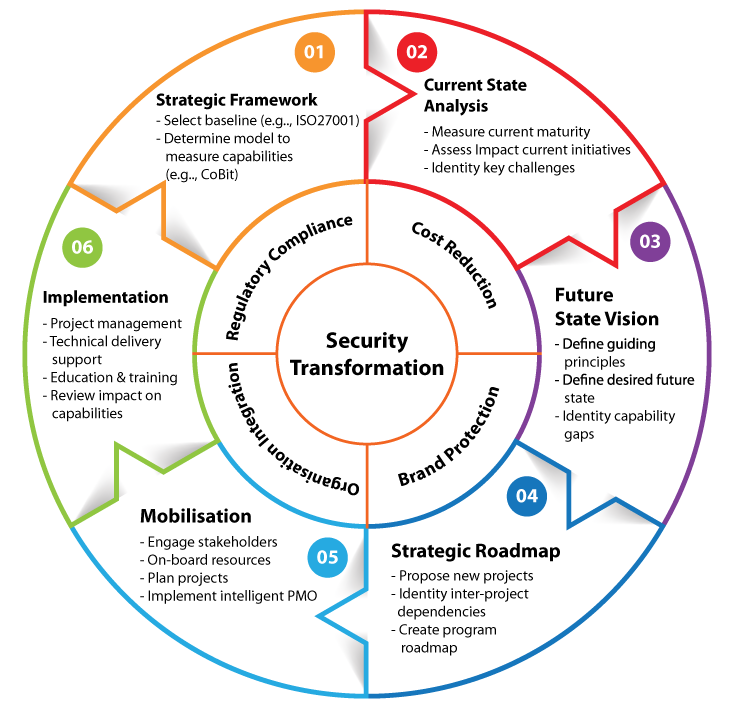
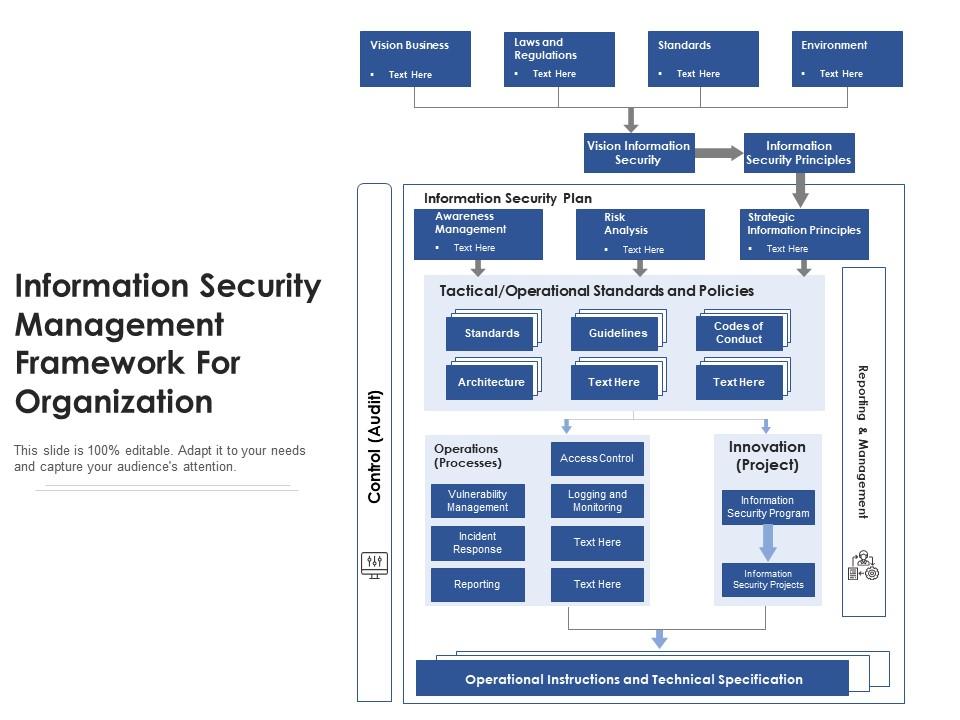
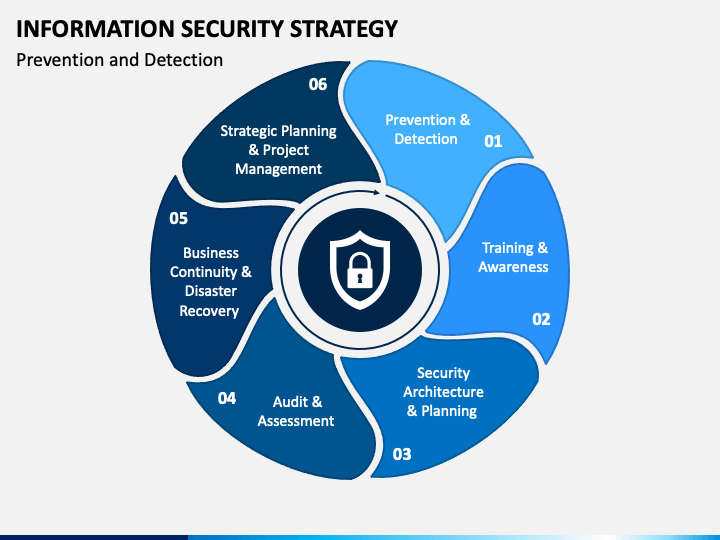
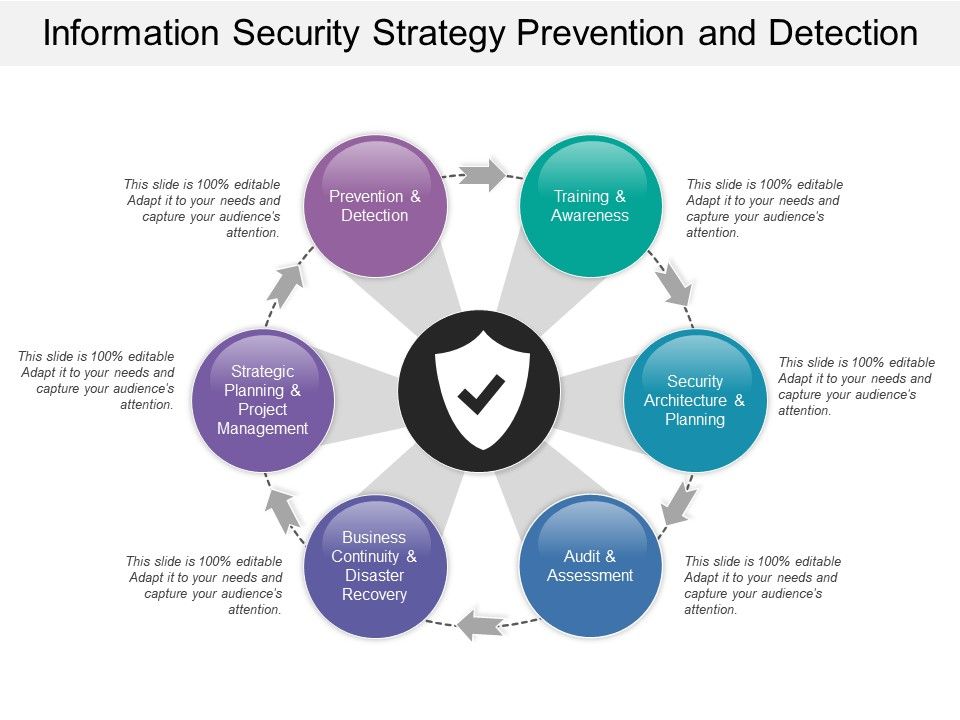
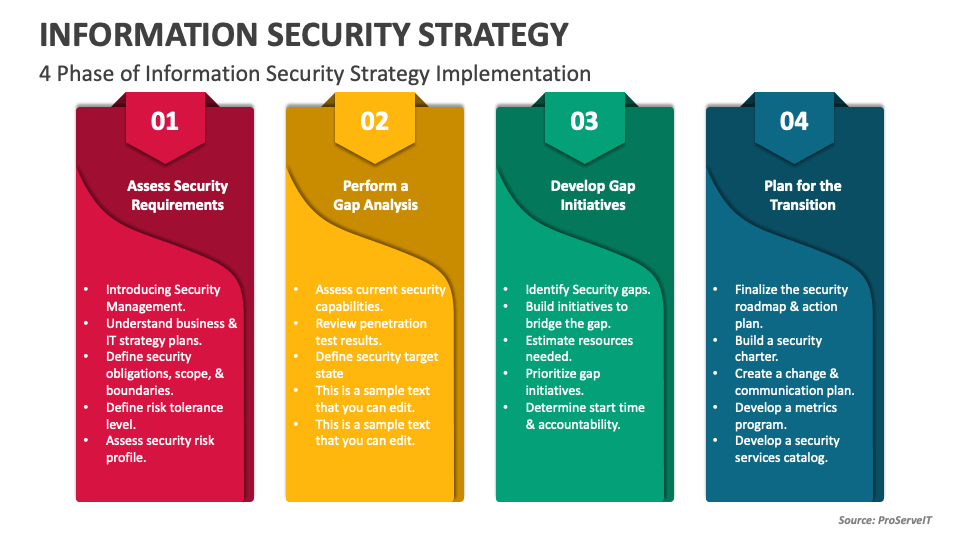
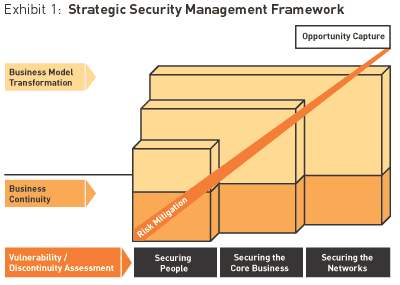
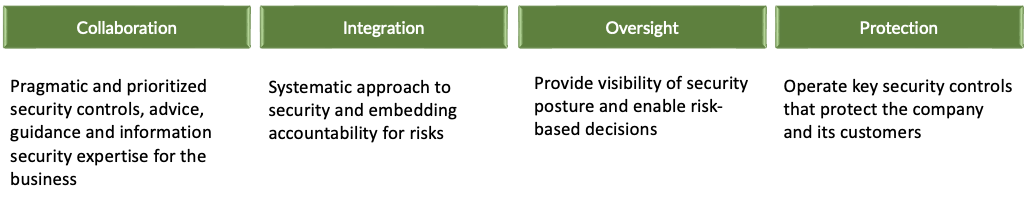
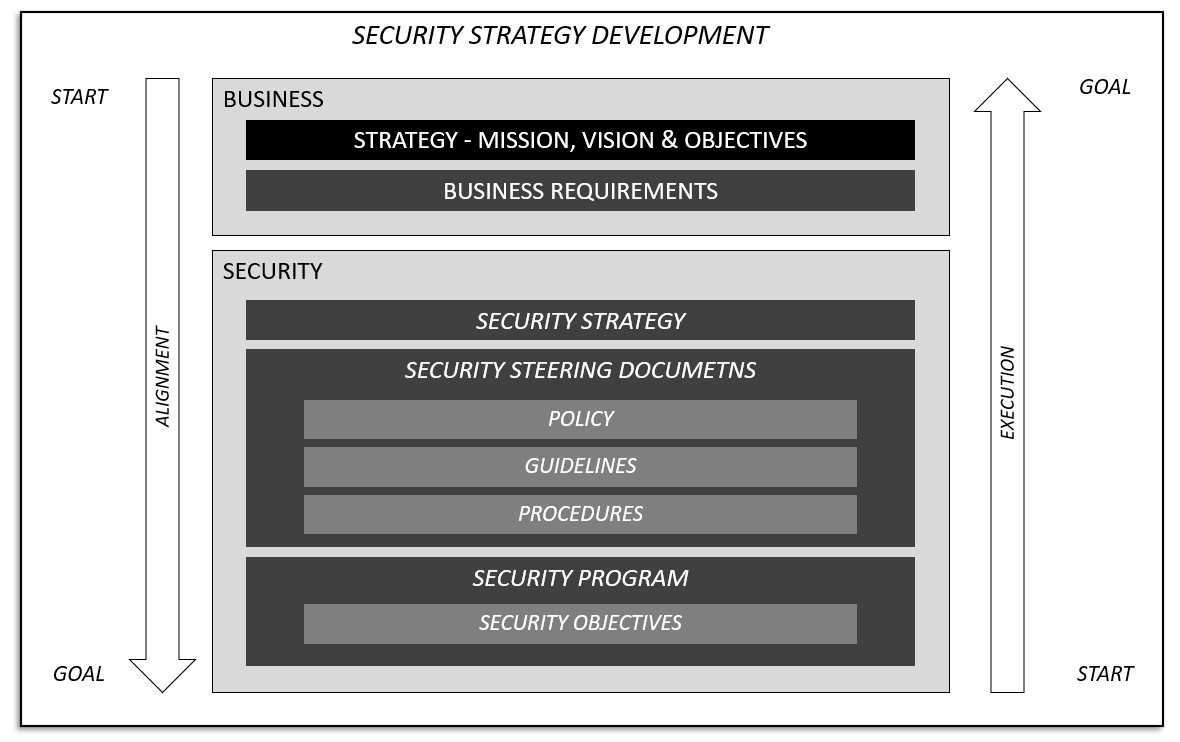
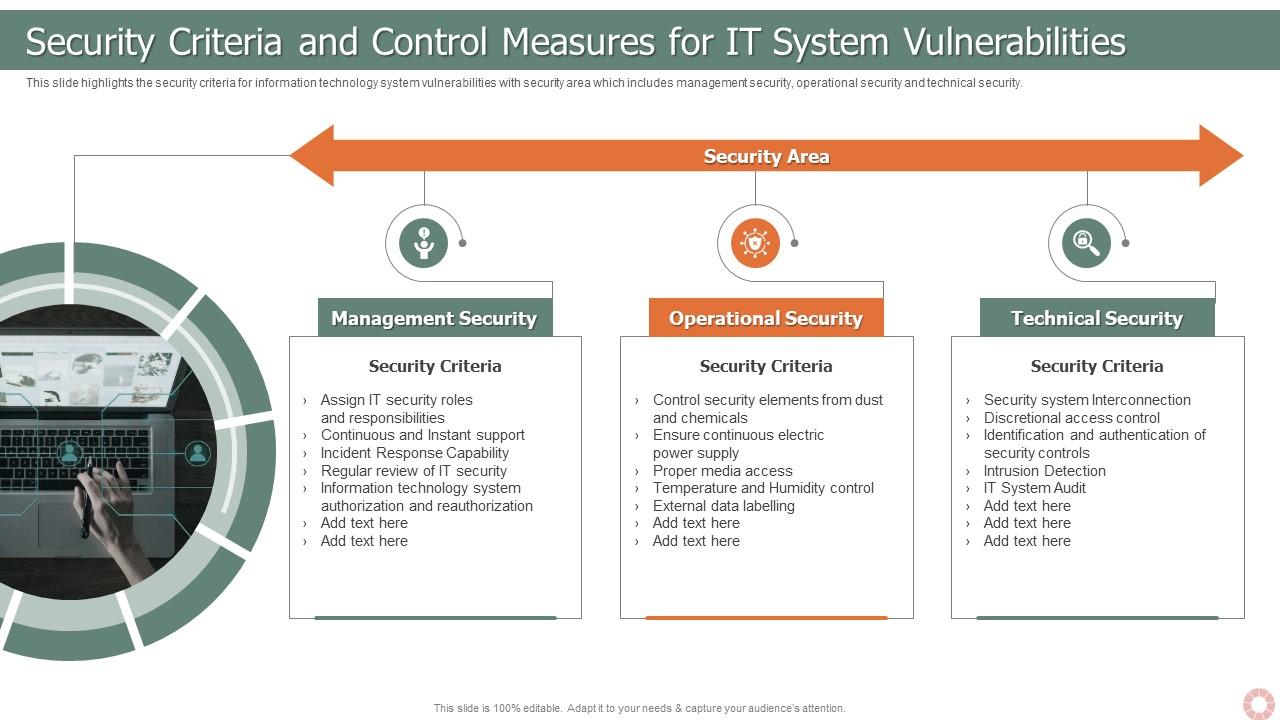
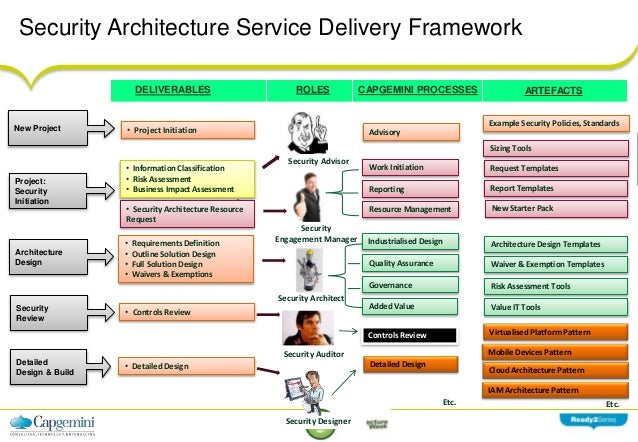
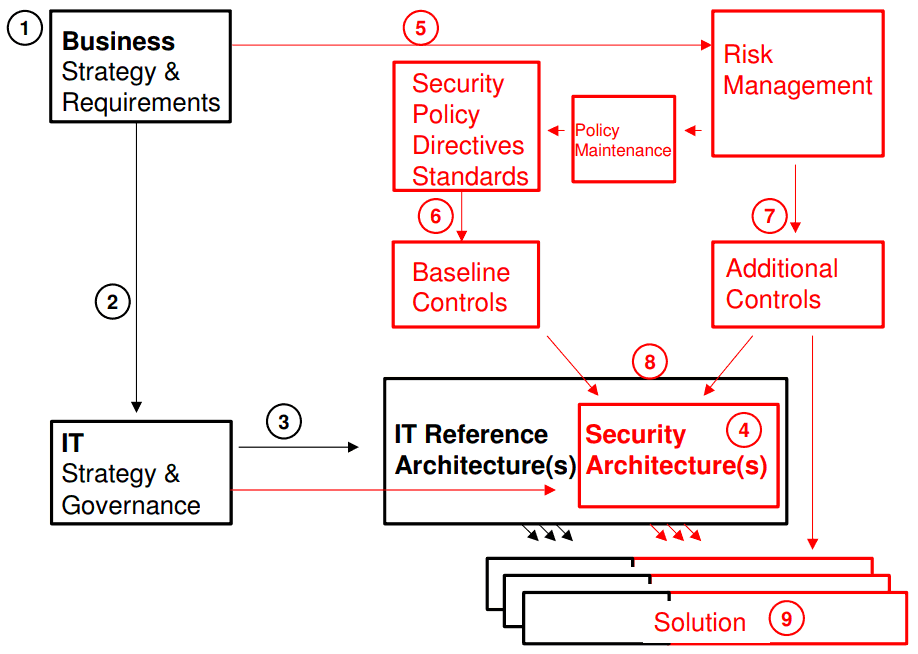
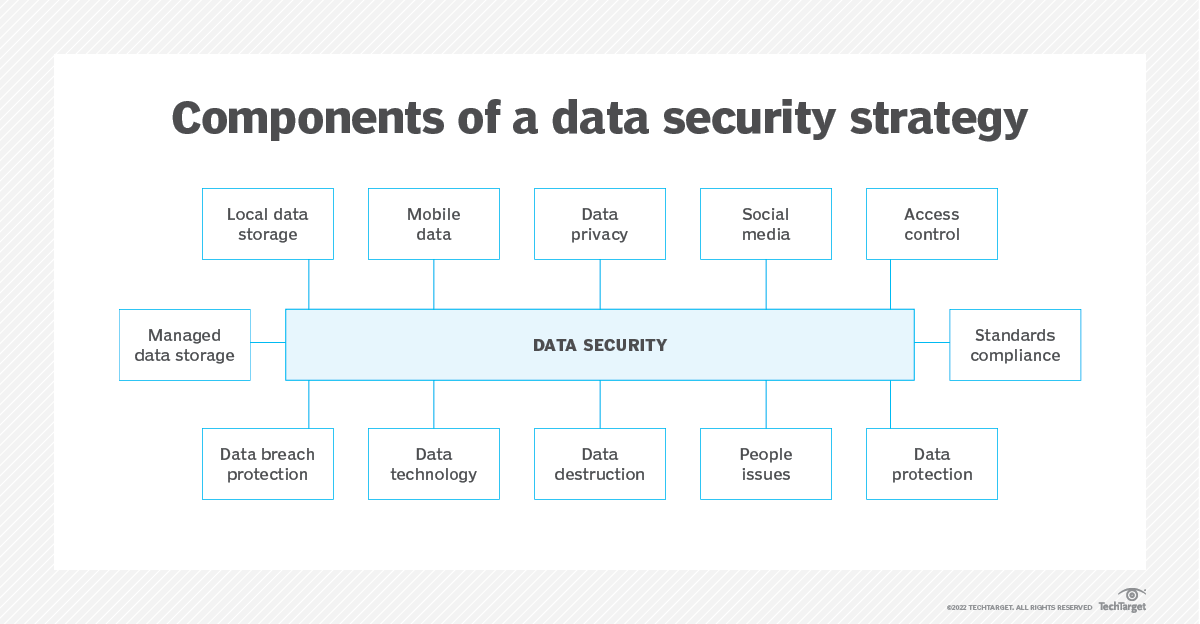
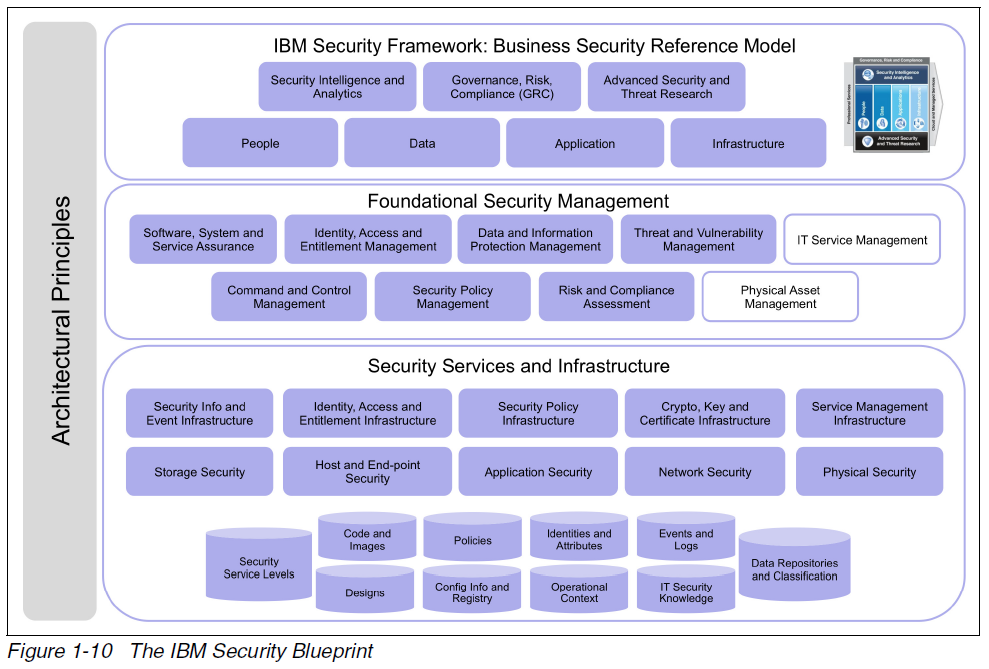
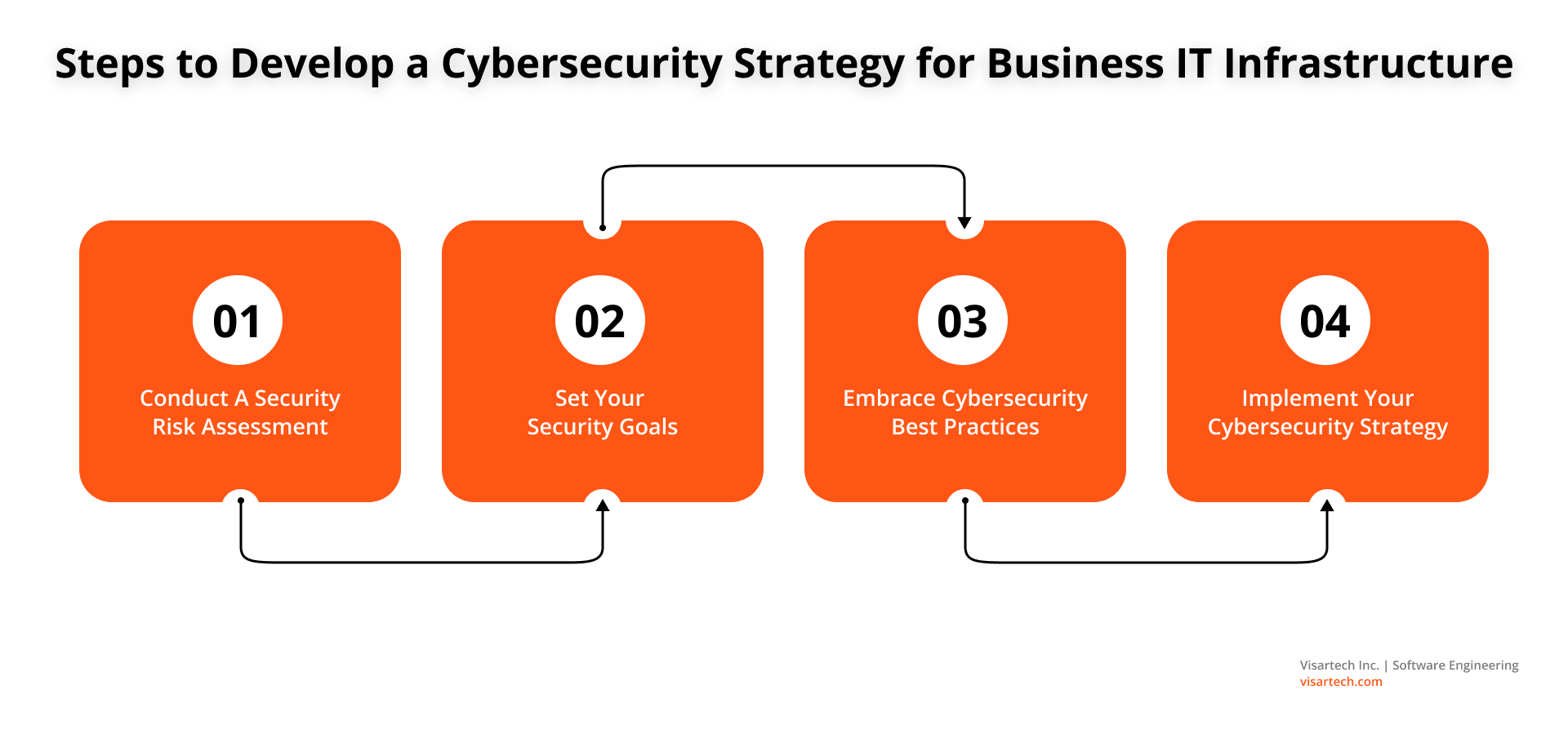
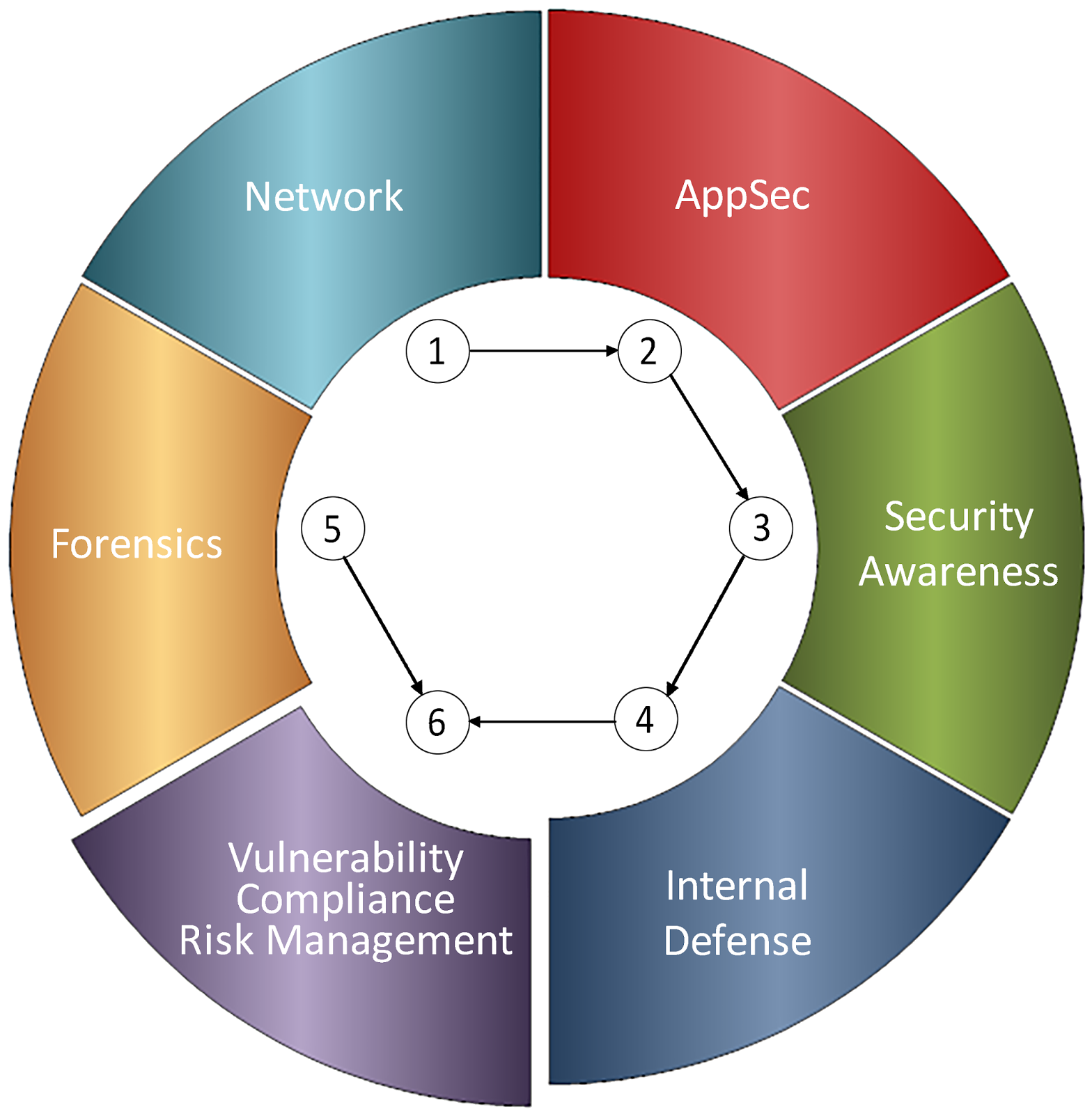
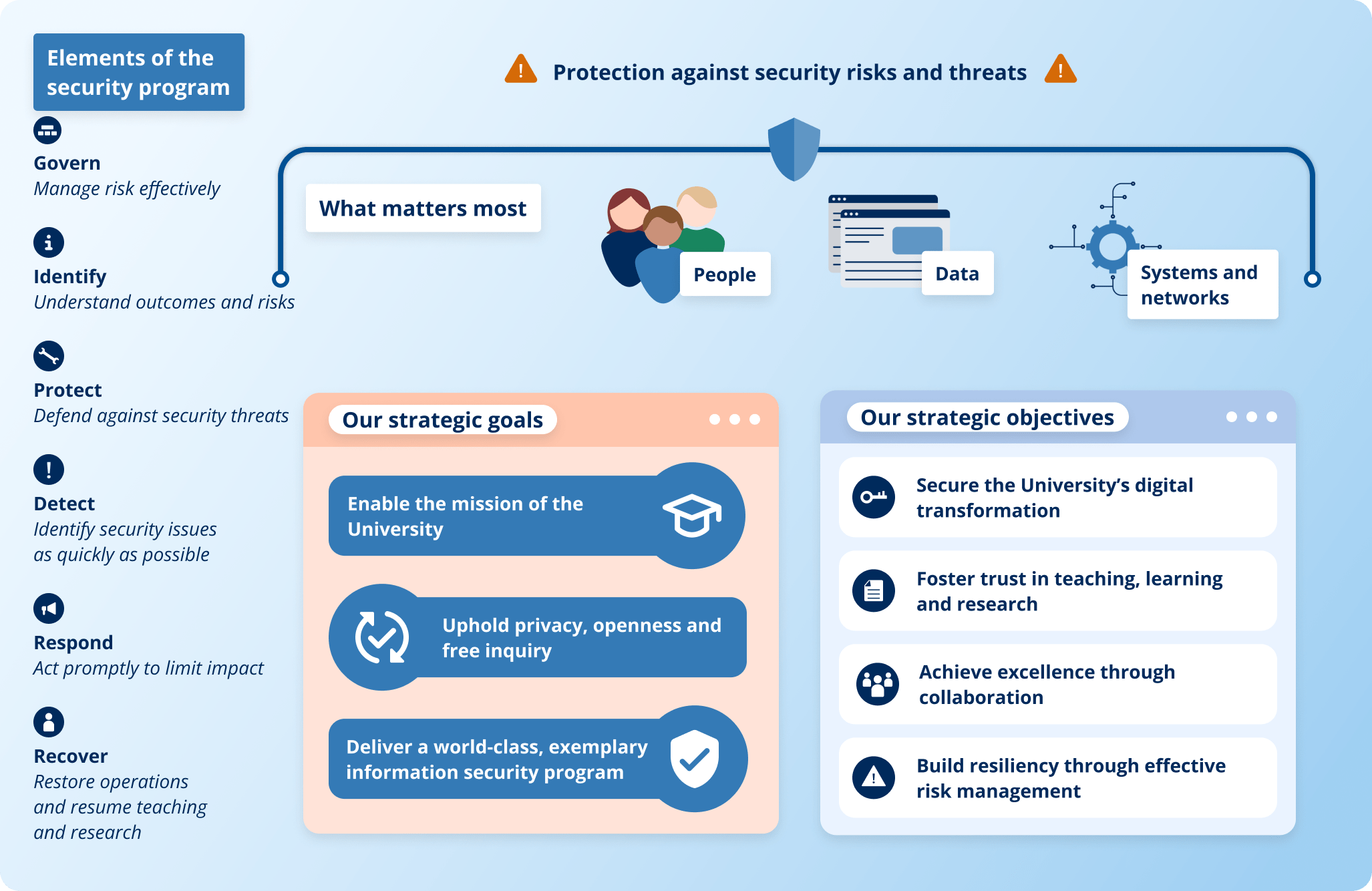
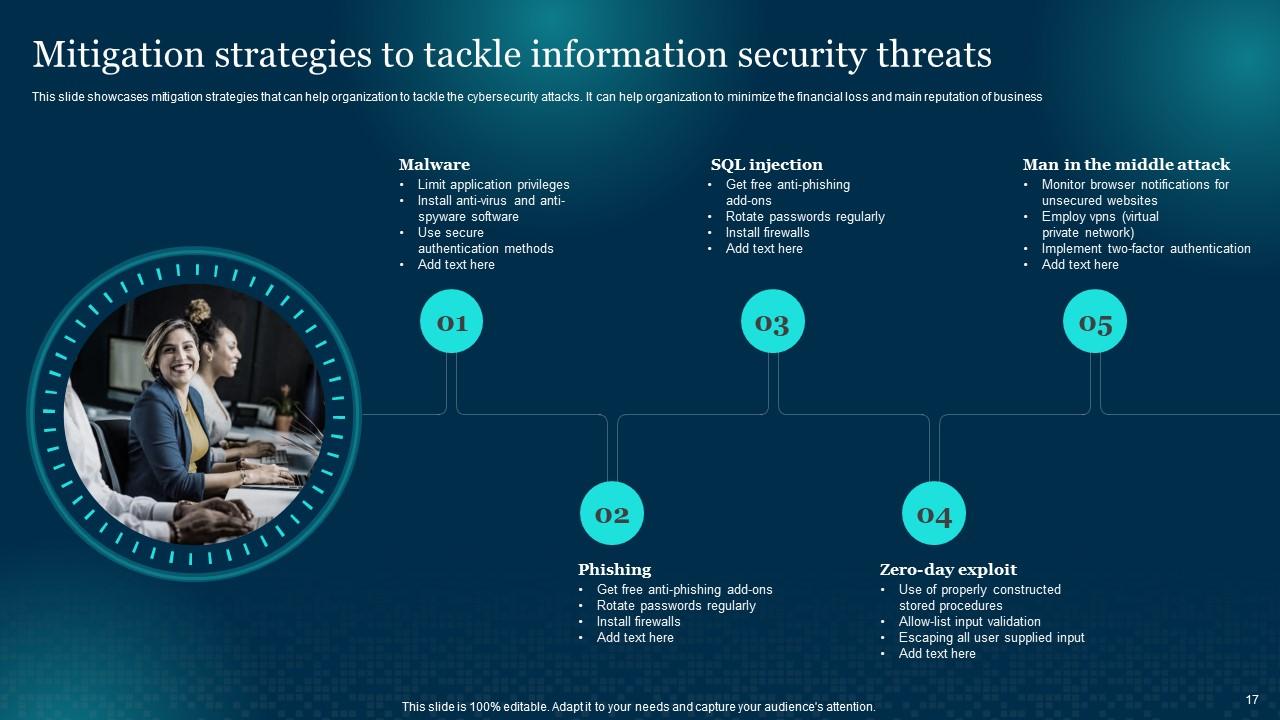
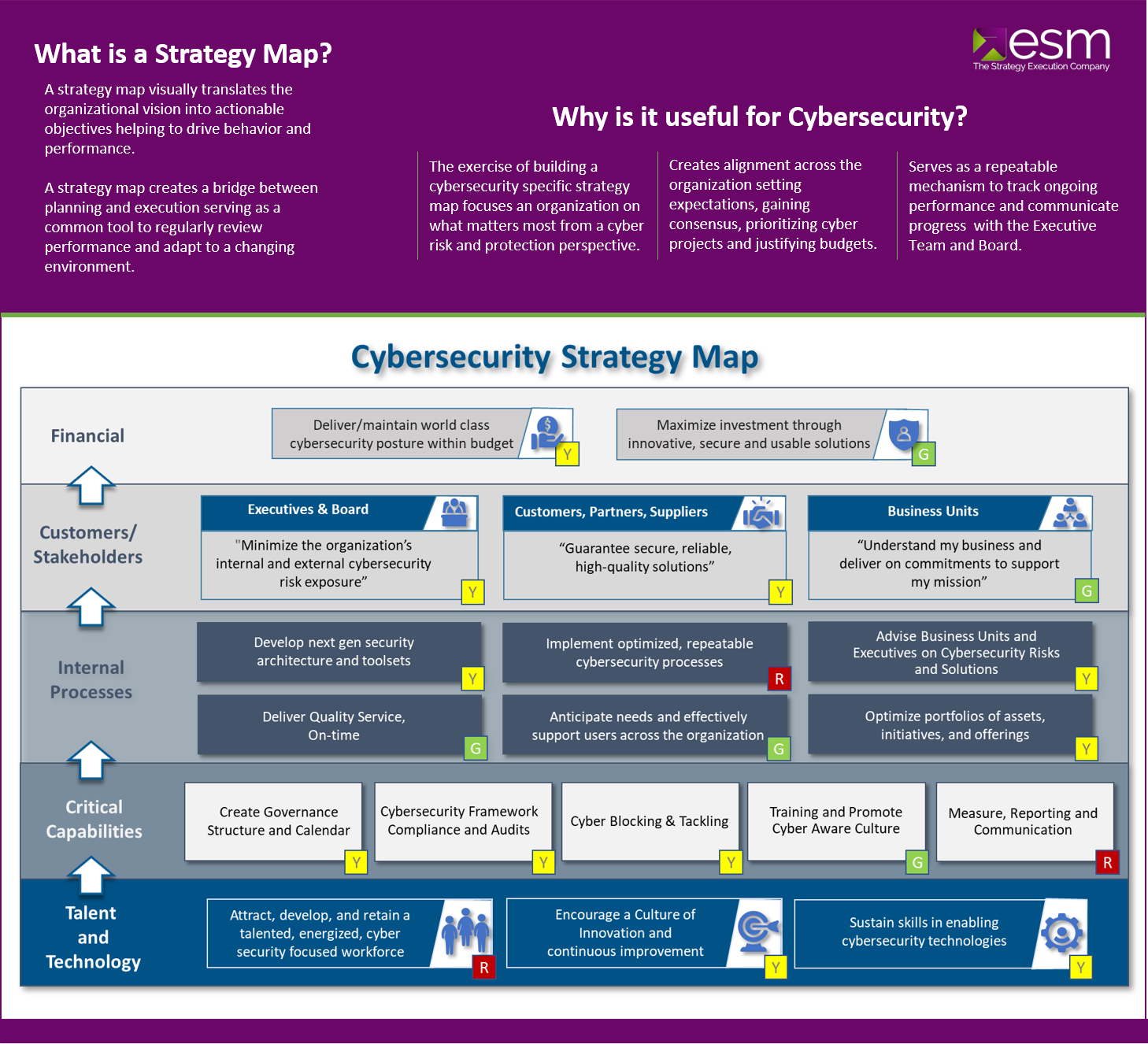
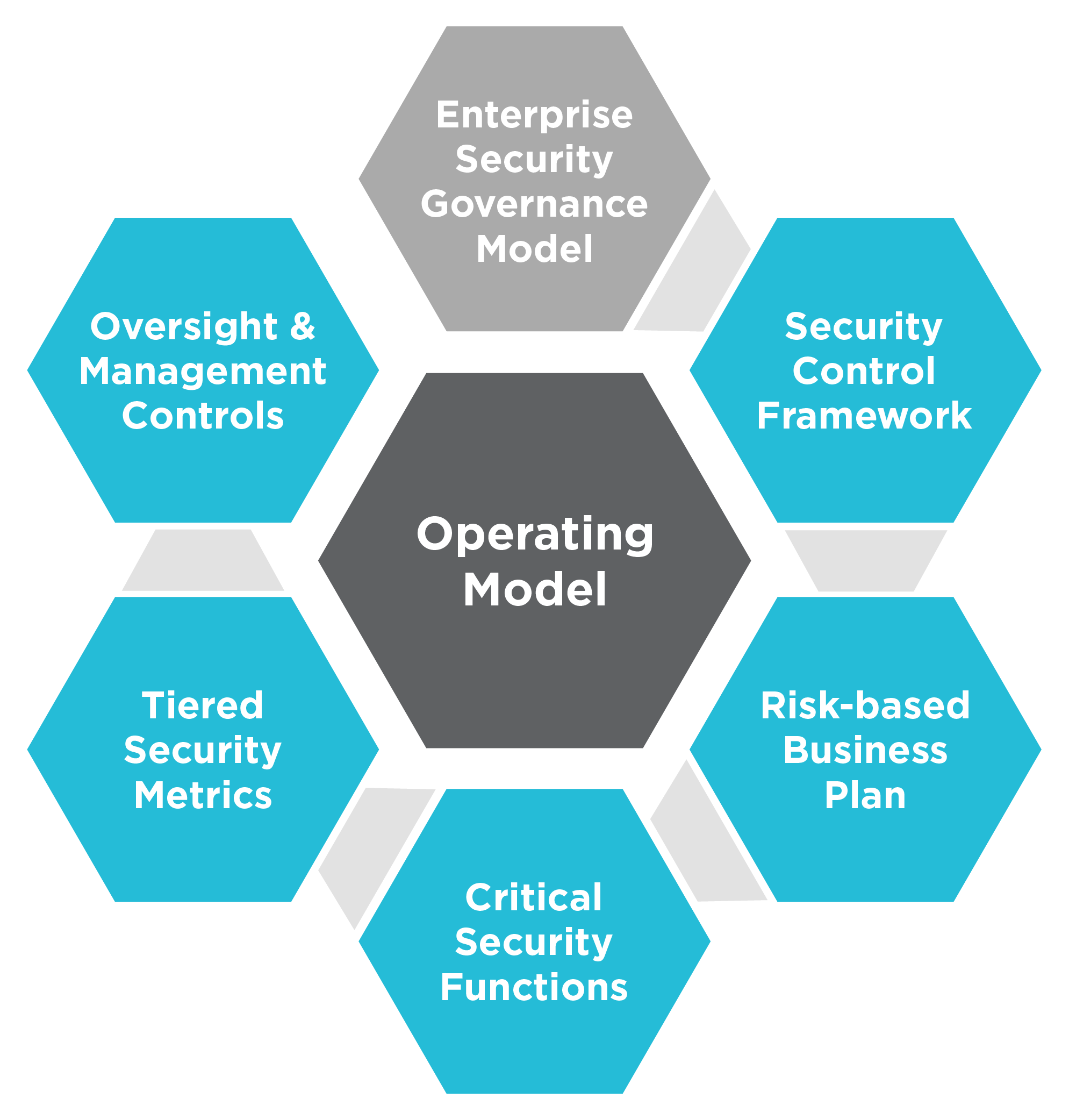
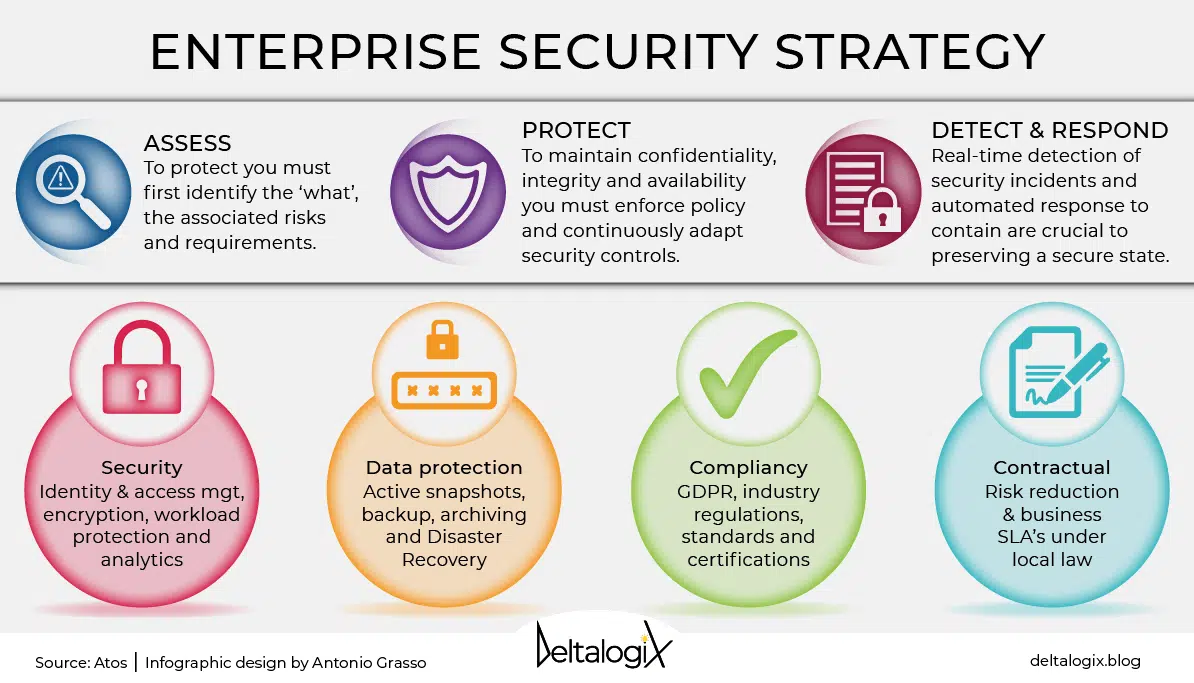
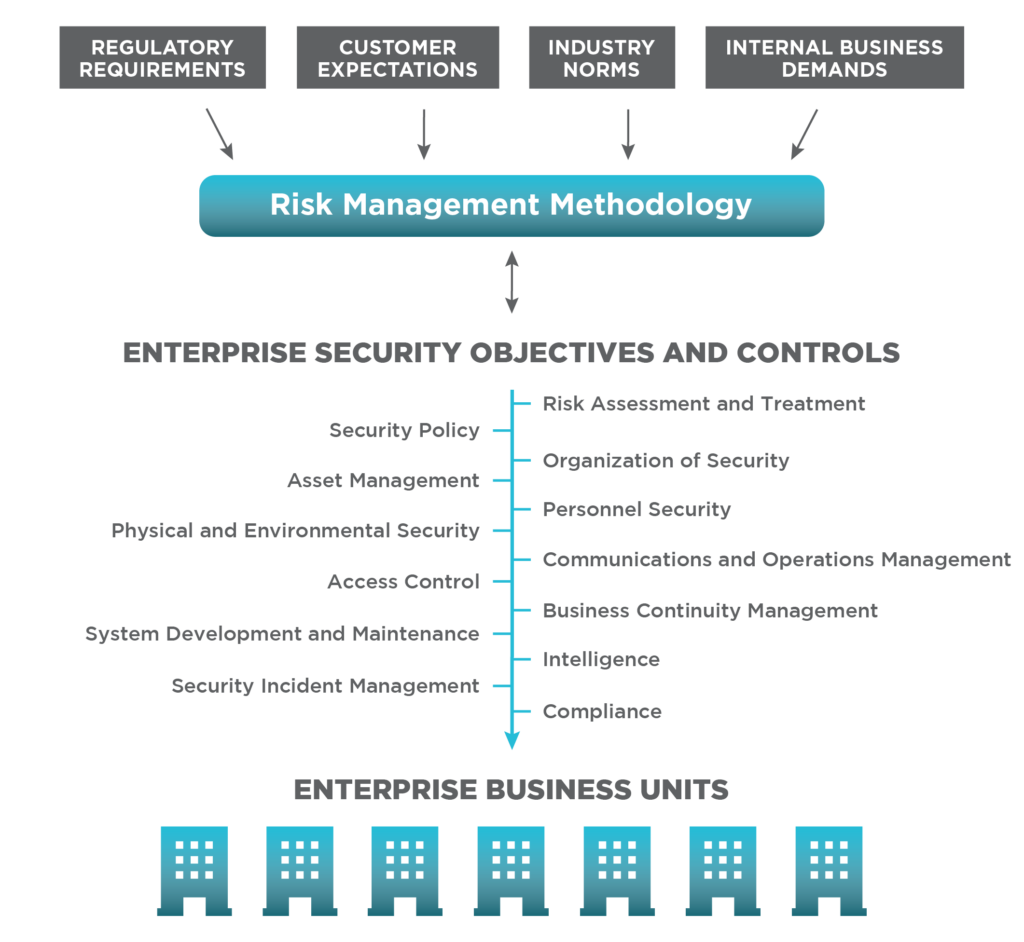
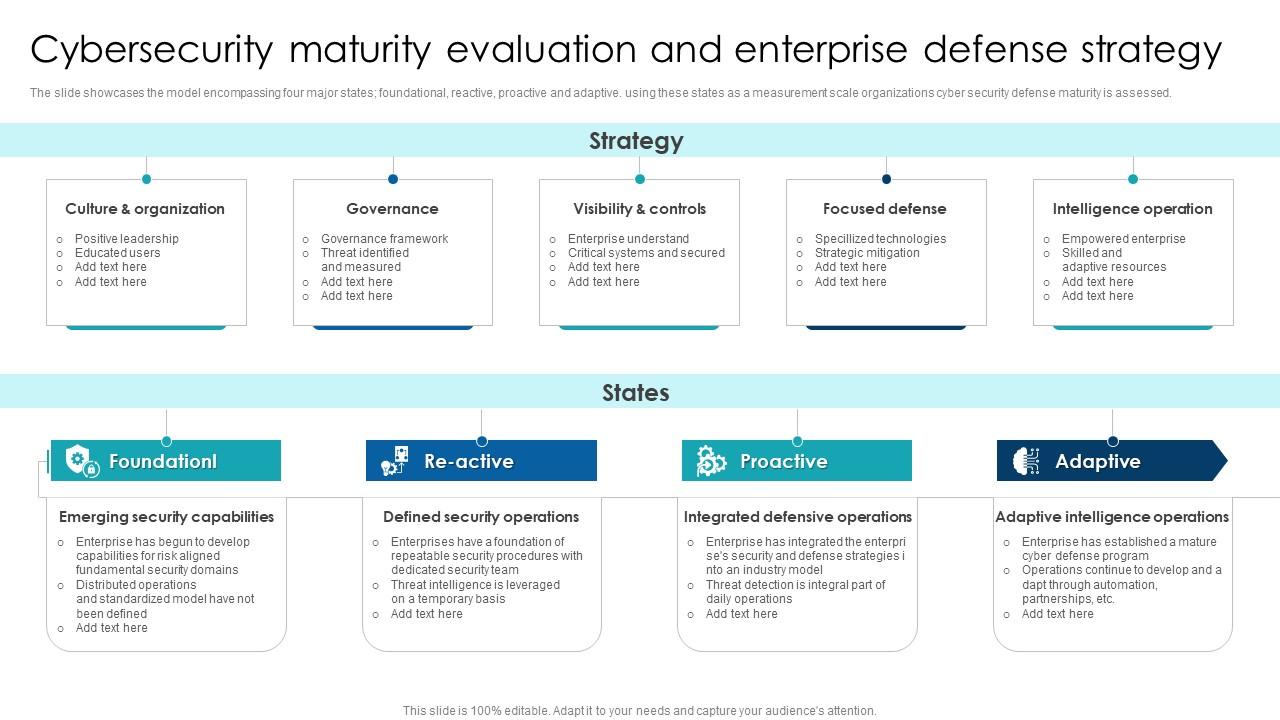
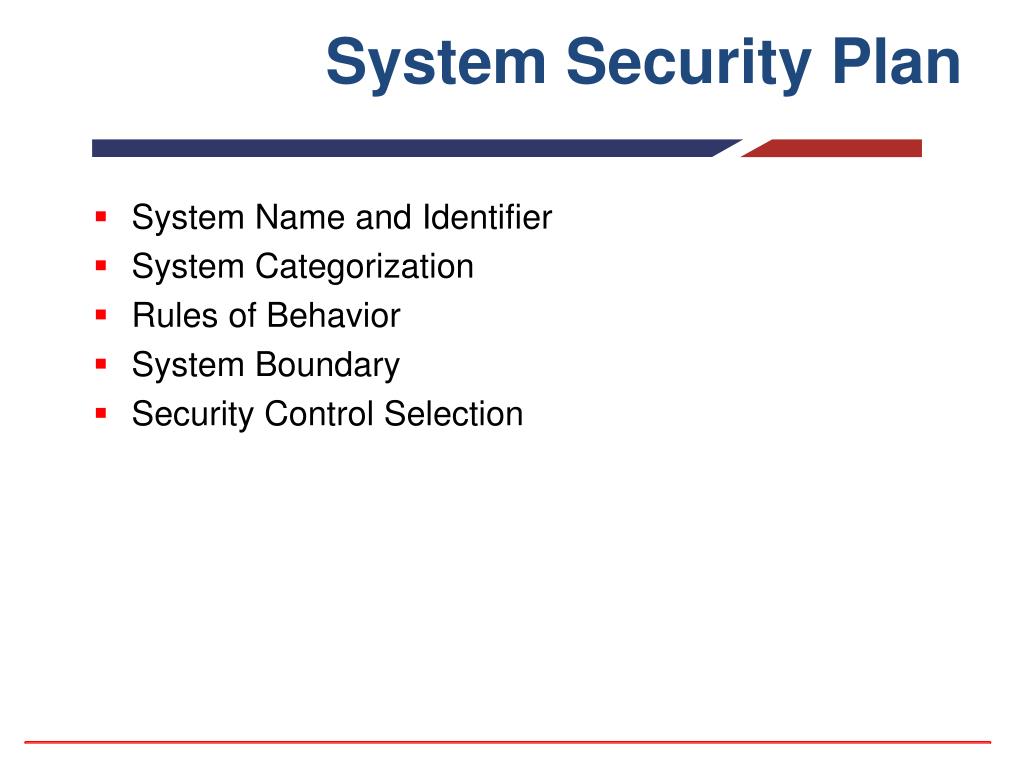
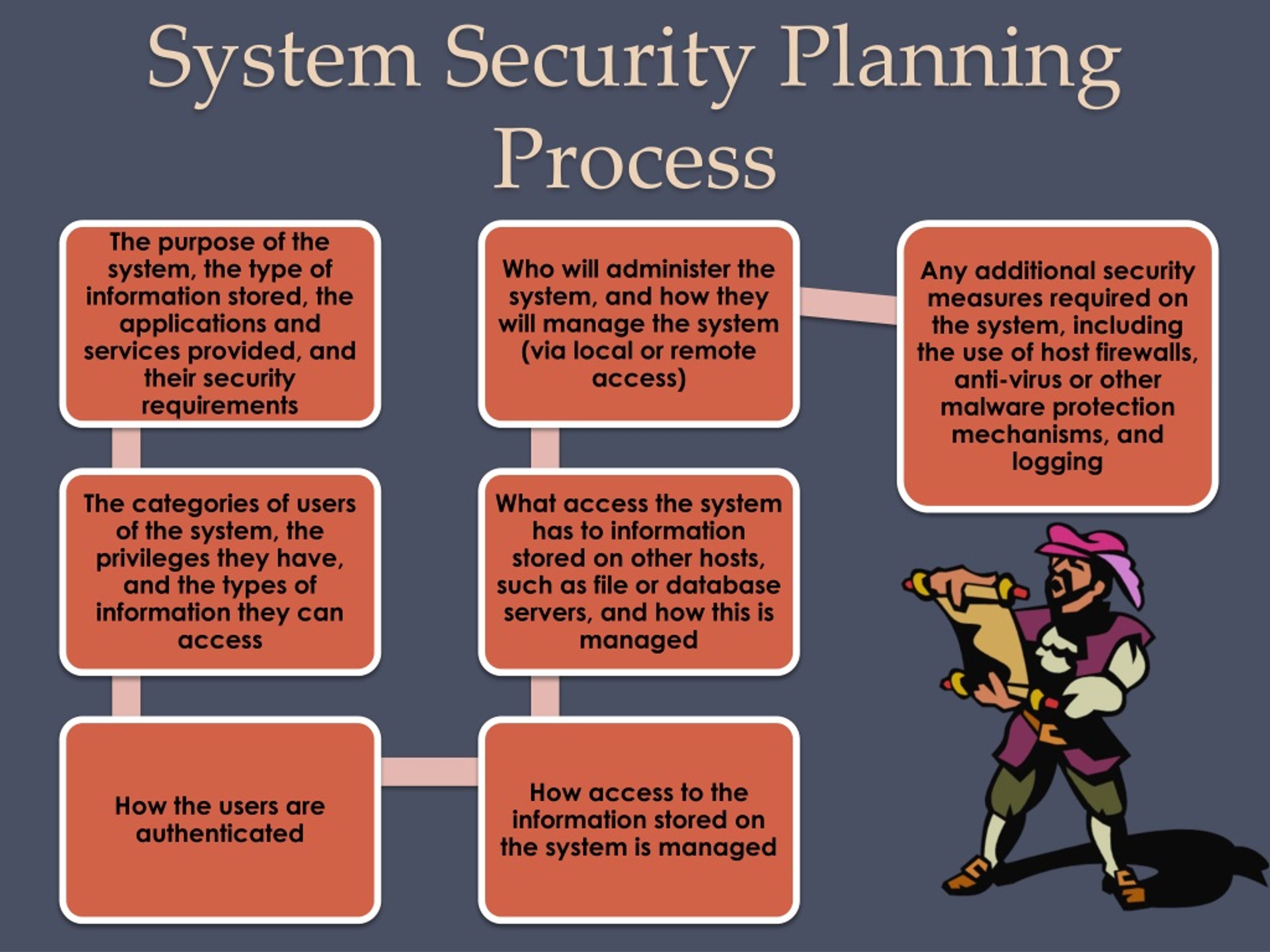
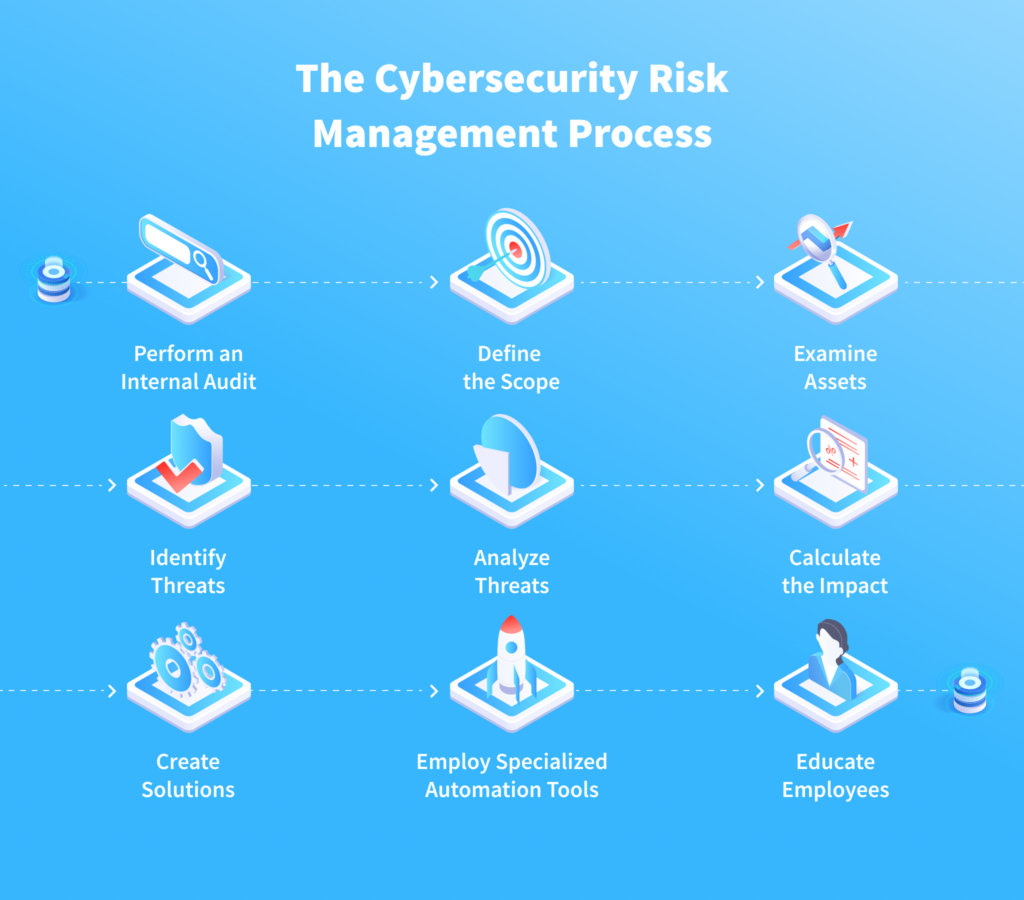
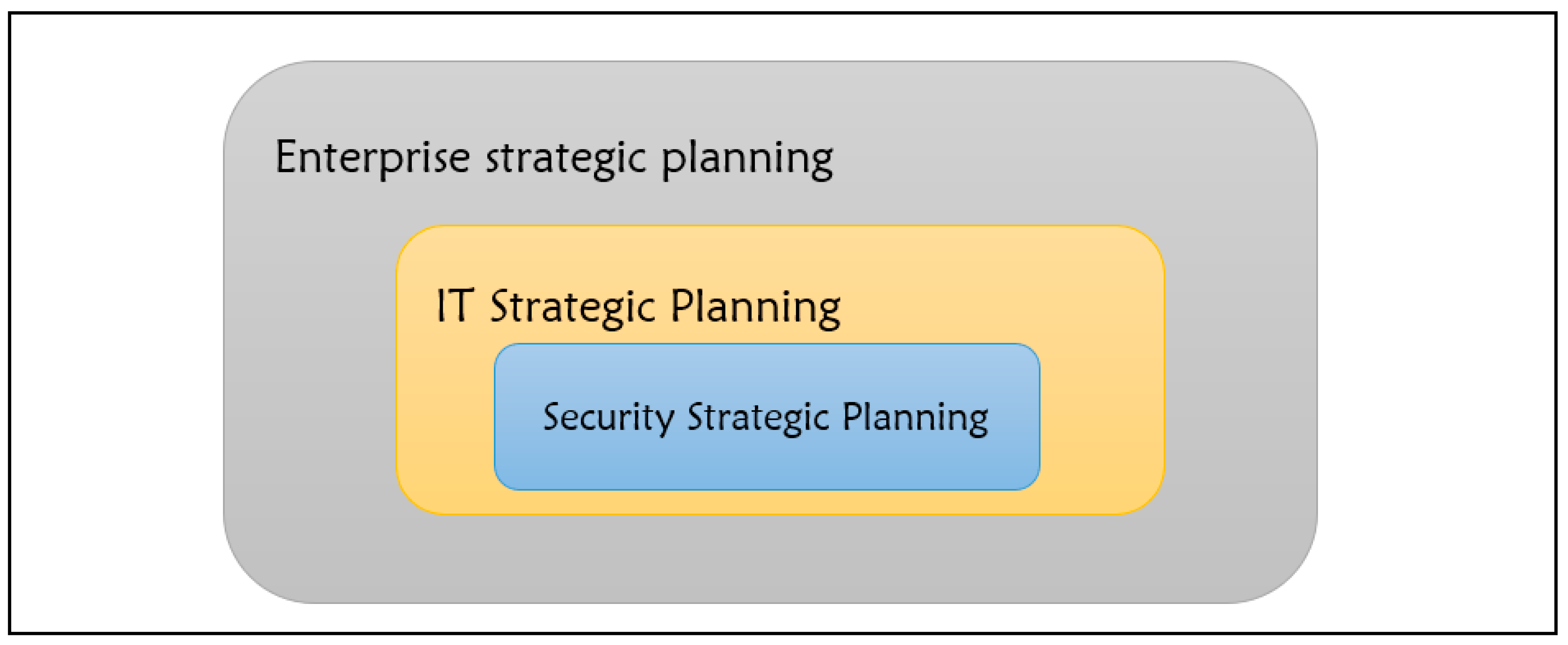
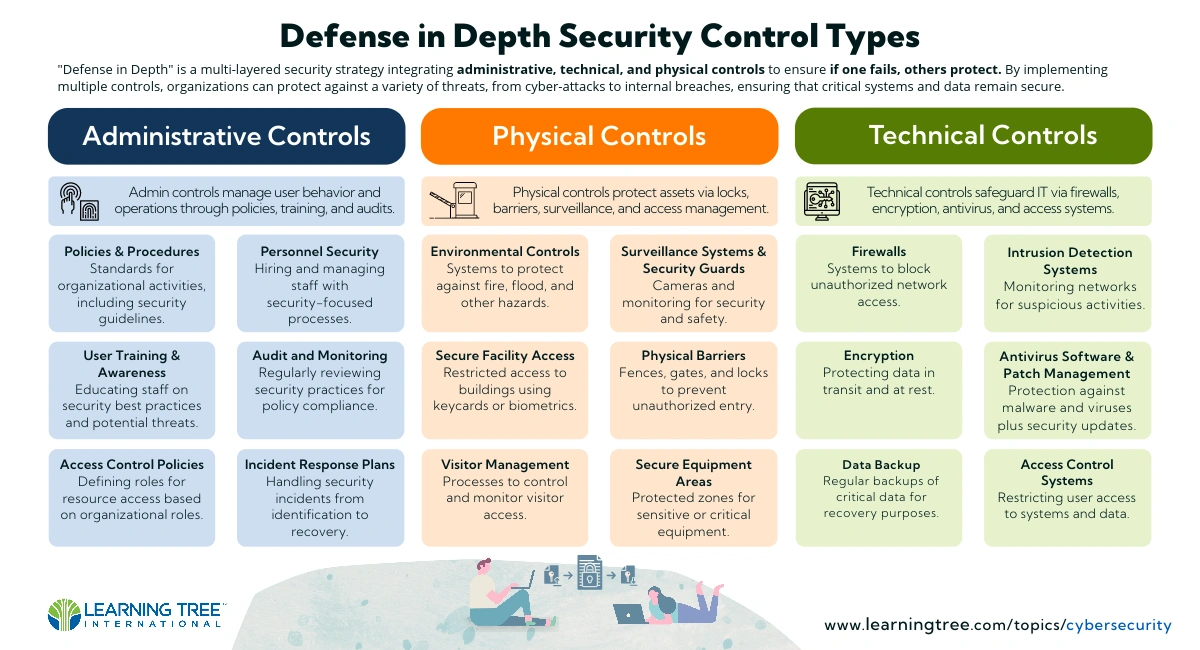
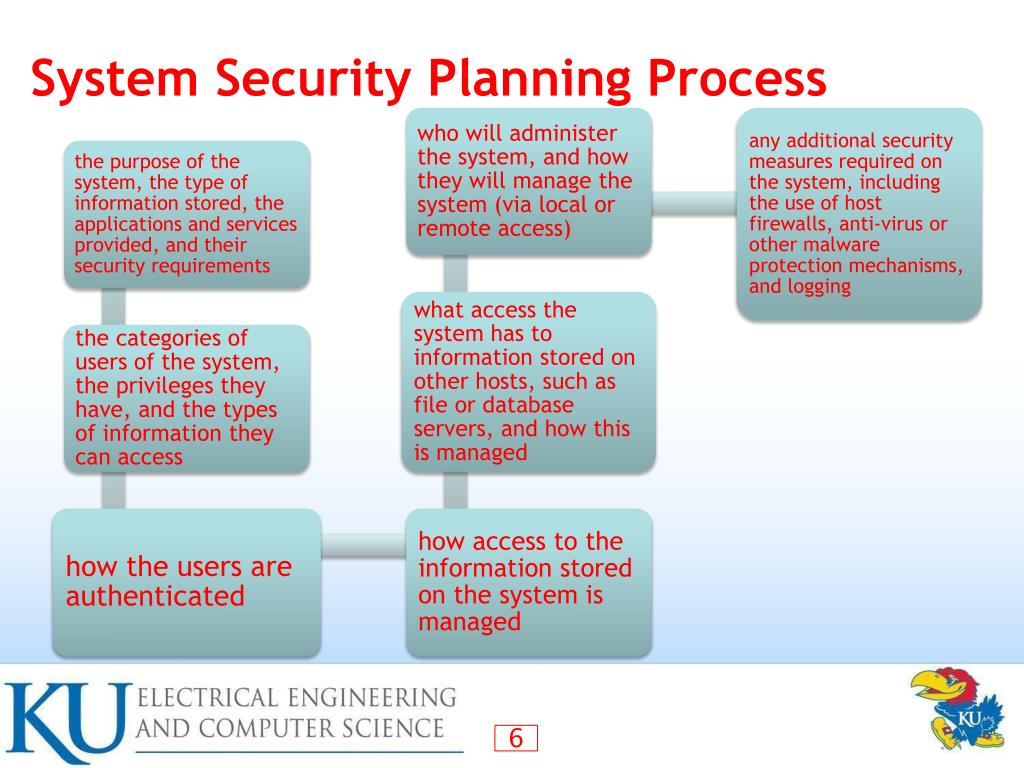
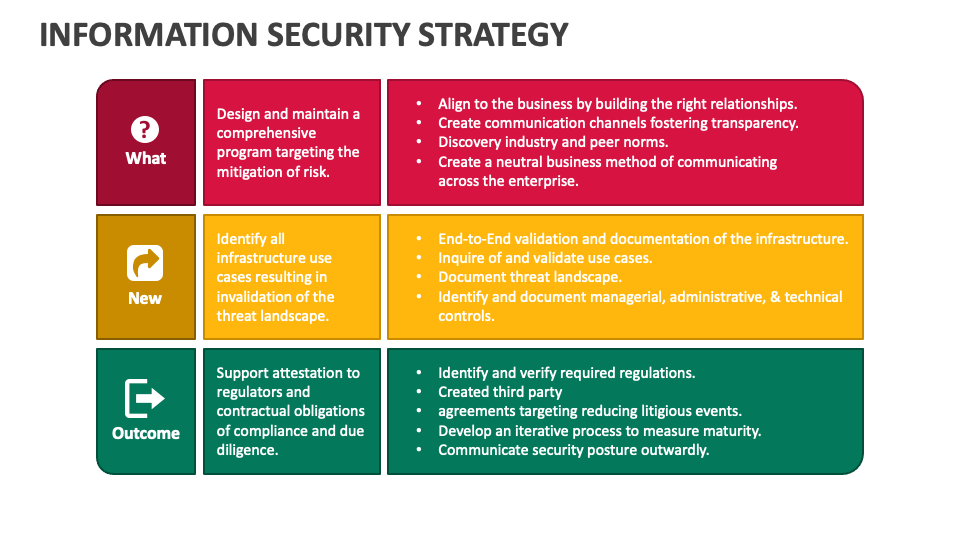
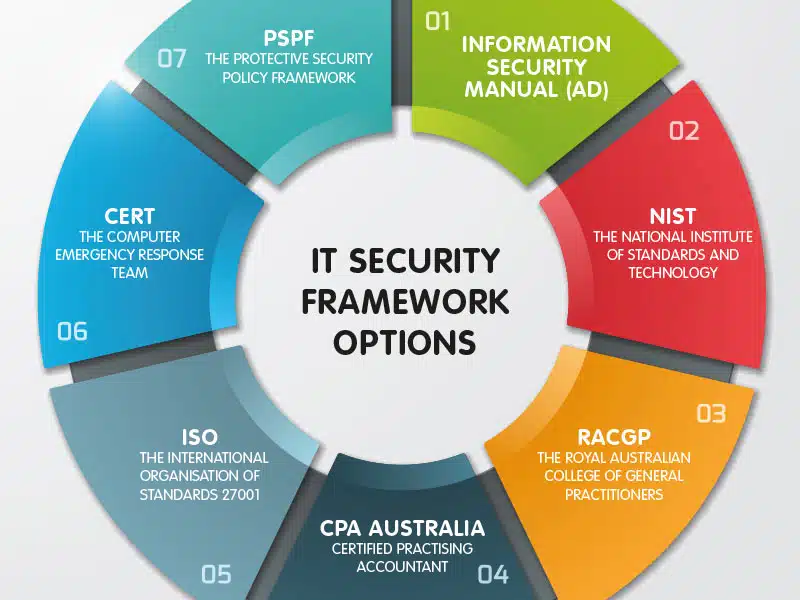
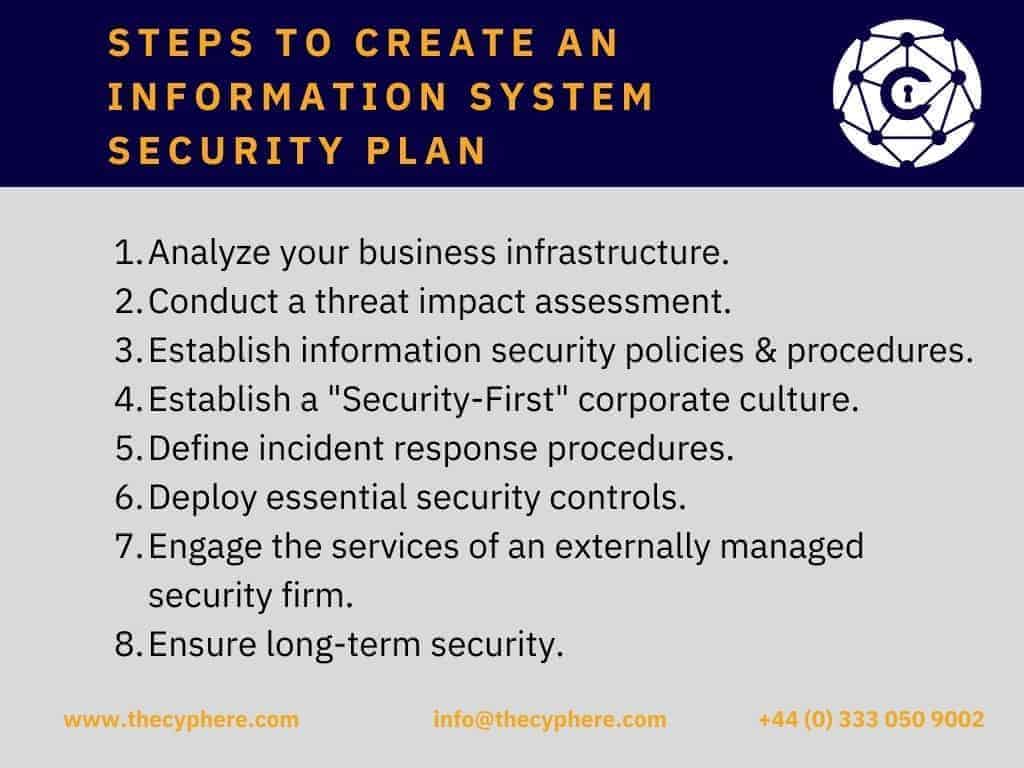
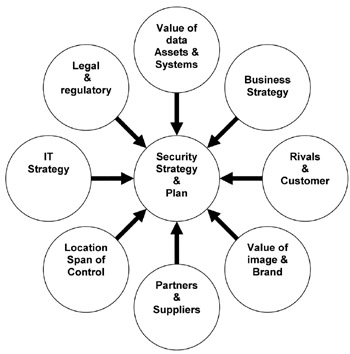
System Security Strategy Example
Appreciate the stunning classic beauty of System Security Strategy Example through countless timeless images. preserving the heritage of photography, images, and pictures. ideal for traditional publications and documentation. The System Security Strategy Example collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All System Security Strategy Example images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our System Security Strategy Example gallery offers diverse visual resources to bring your ideas to life. The System Security Strategy Example collection represents years of careful curation and professional standards. The System Security Strategy Example archive serves professionals, educators, and creatives across diverse industries. Cost-effective licensing makes professional System Security Strategy Example photography accessible to all budgets. Professional licensing options accommodate both commercial and educational usage requirements. Advanced search capabilities make finding the perfect System Security Strategy Example image effortless and efficient. Our System Security Strategy Example database continuously expands with fresh, relevant content from skilled photographers. Diverse style options within the System Security Strategy Example collection suit various aesthetic preferences. Instant download capabilities enable immediate access to chosen System Security Strategy Example images.



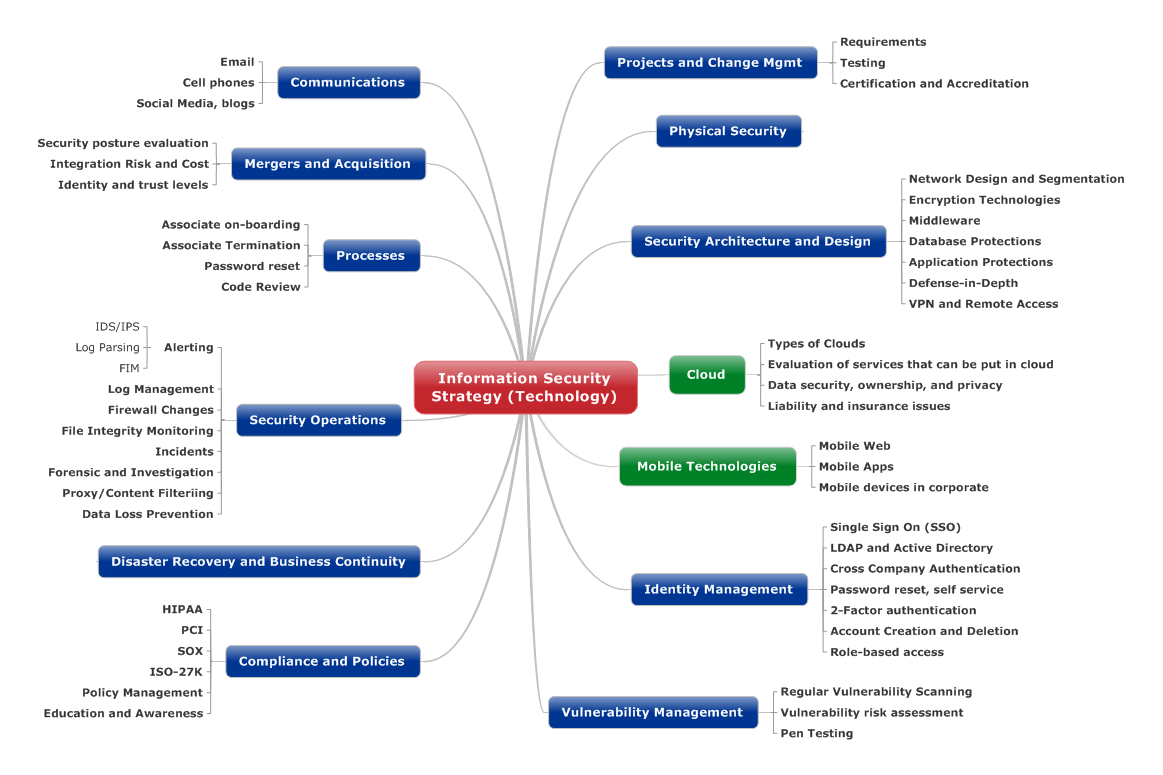
![Top-level view of NIST System Security Framework [22]. The framework in ...](https://www.researchgate.net/publication/367438251/figure/fig2/AS:11431281115027704@1674748316213/Top-level-view-of-NIST-System-Security-Framework-22-The-framework-in-Figure-1-is-one.png)


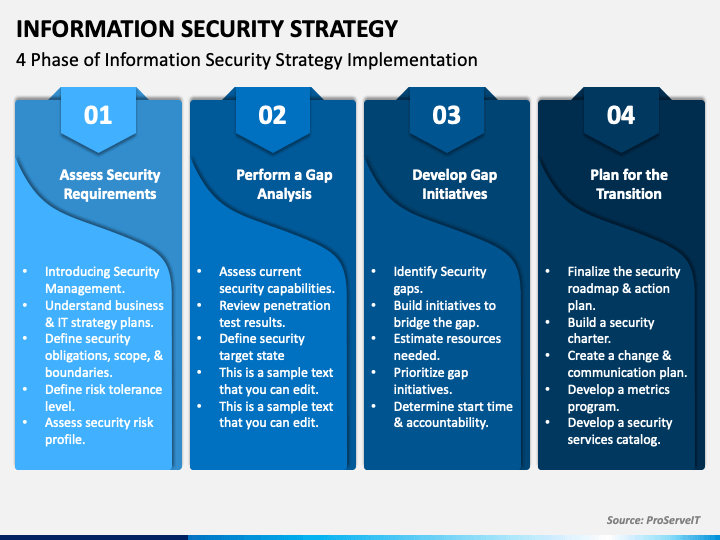

_-_16x9_-_HiRes_distro.jpg?1710356443)