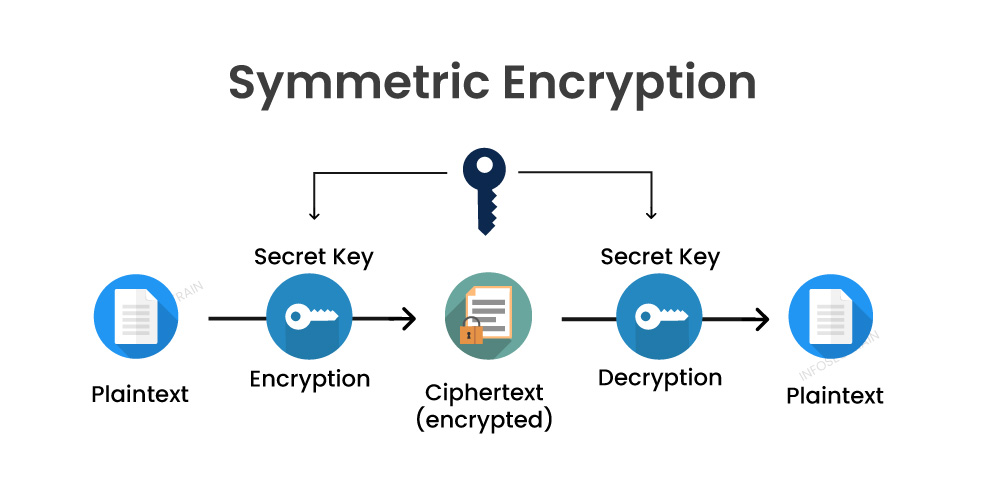
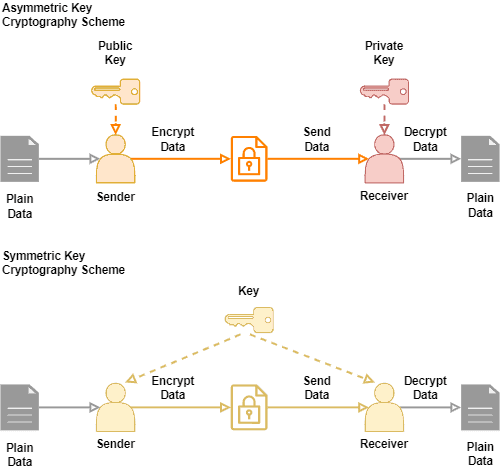
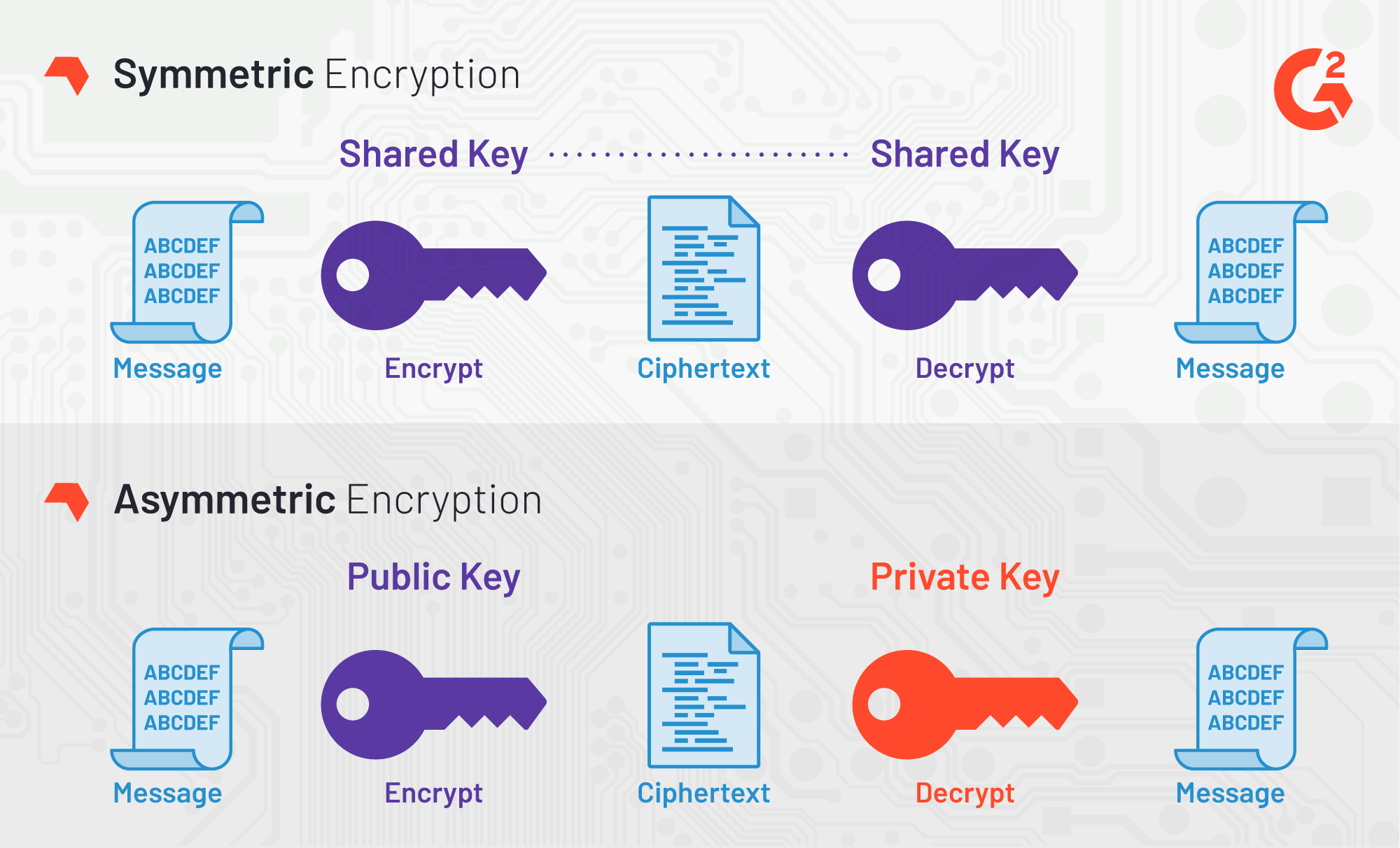
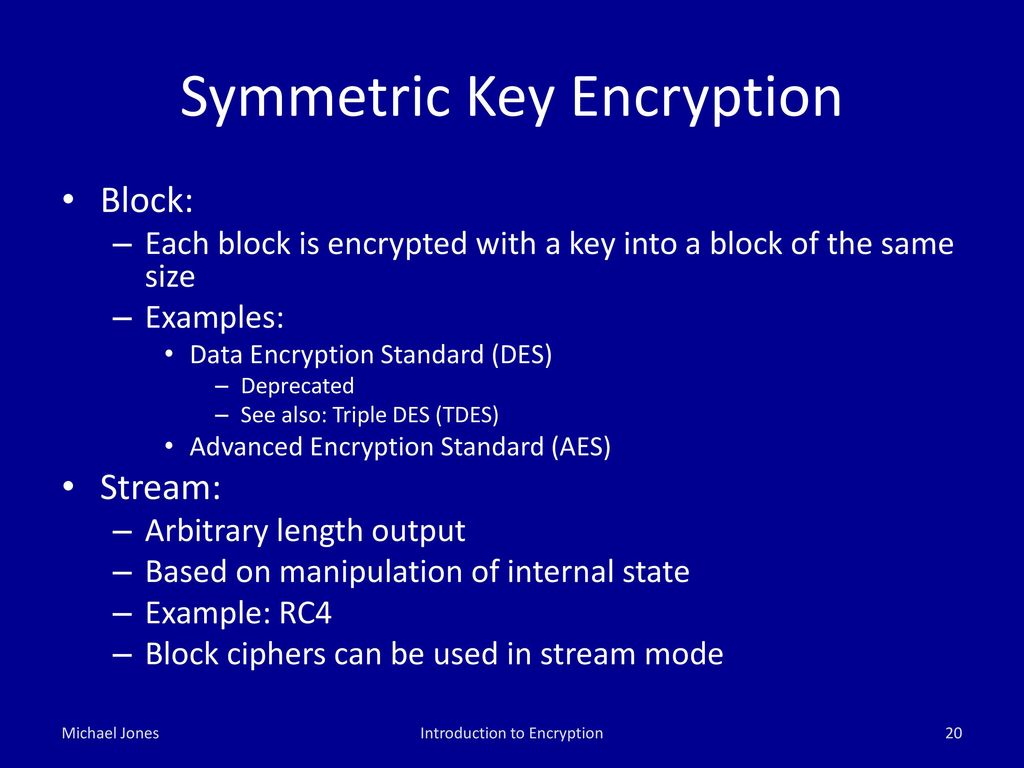
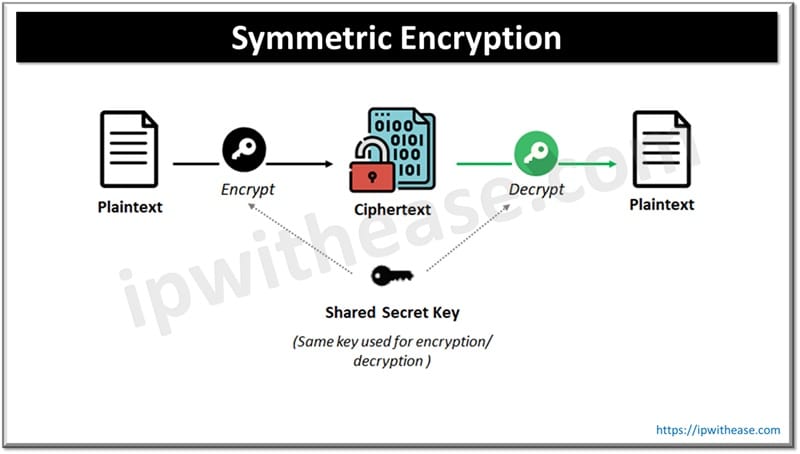
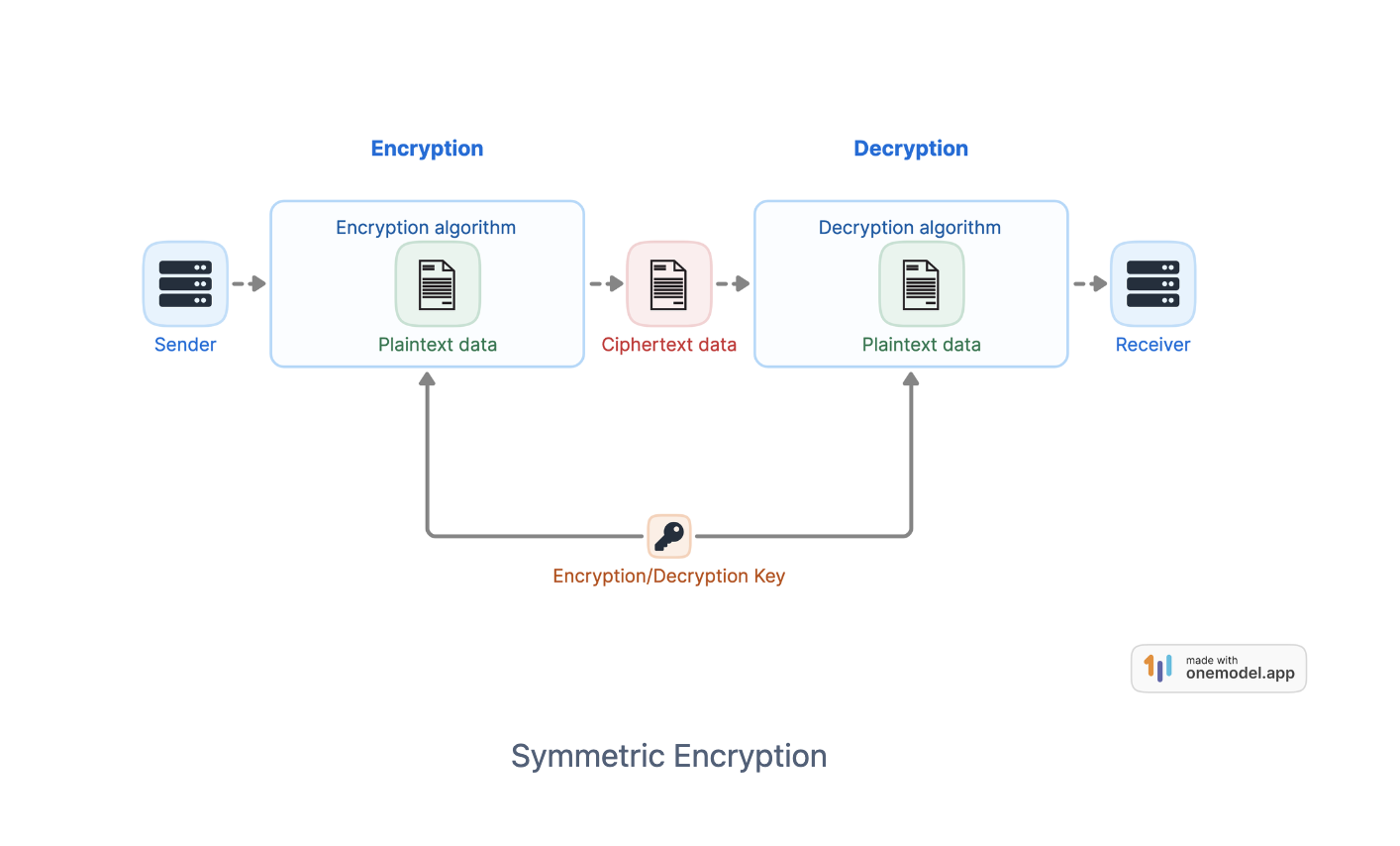
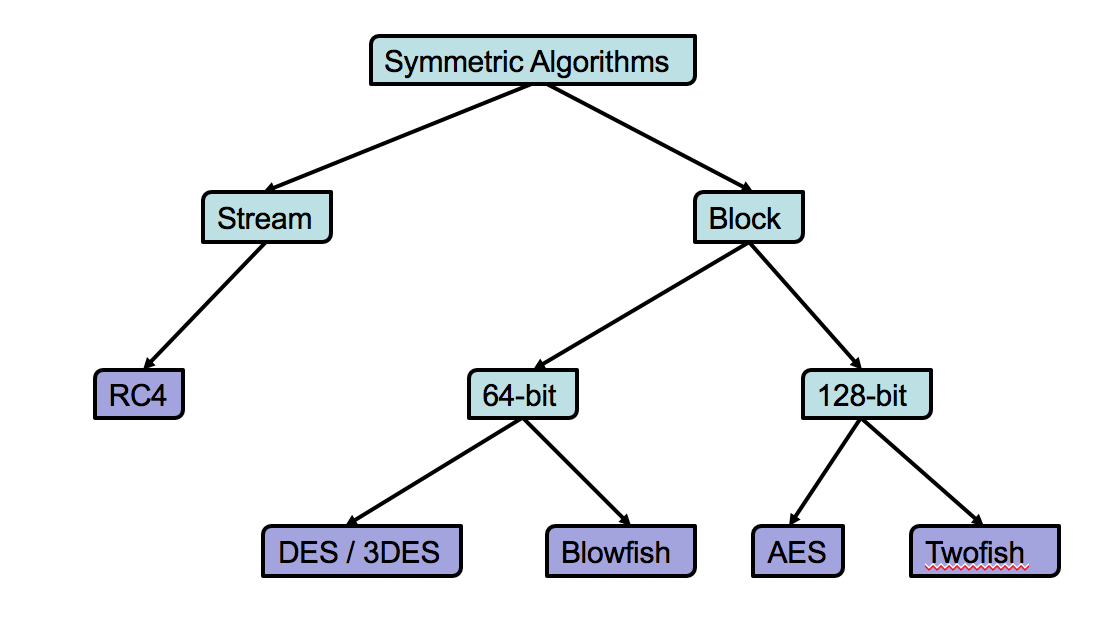
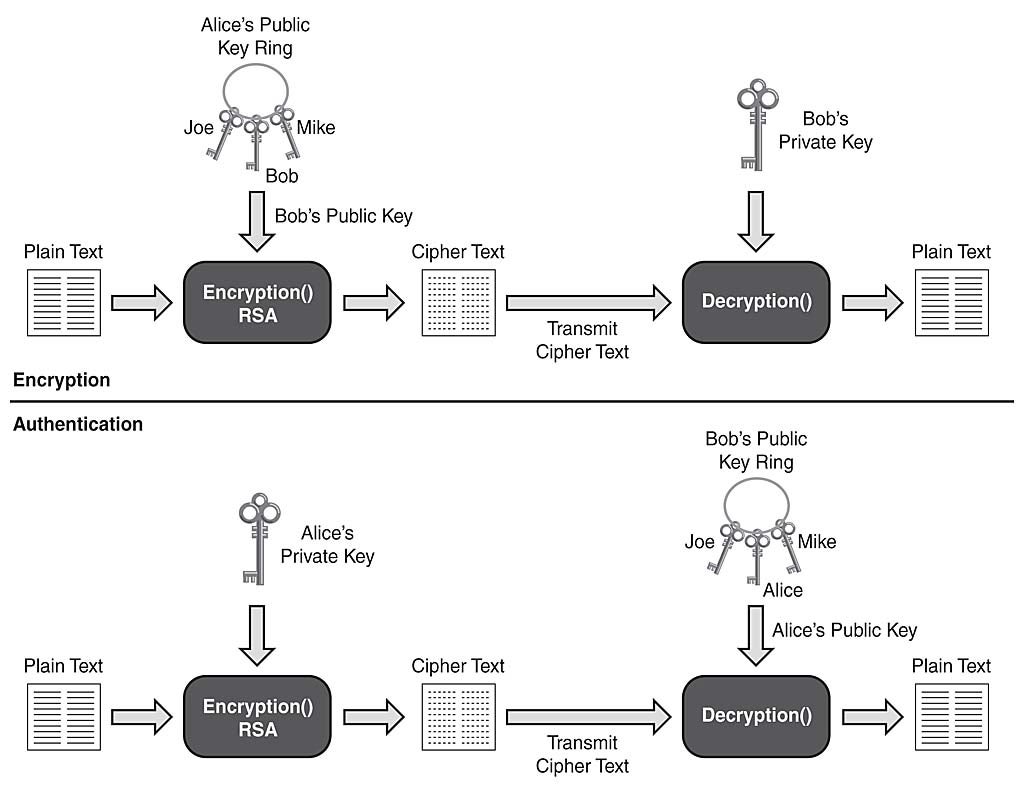
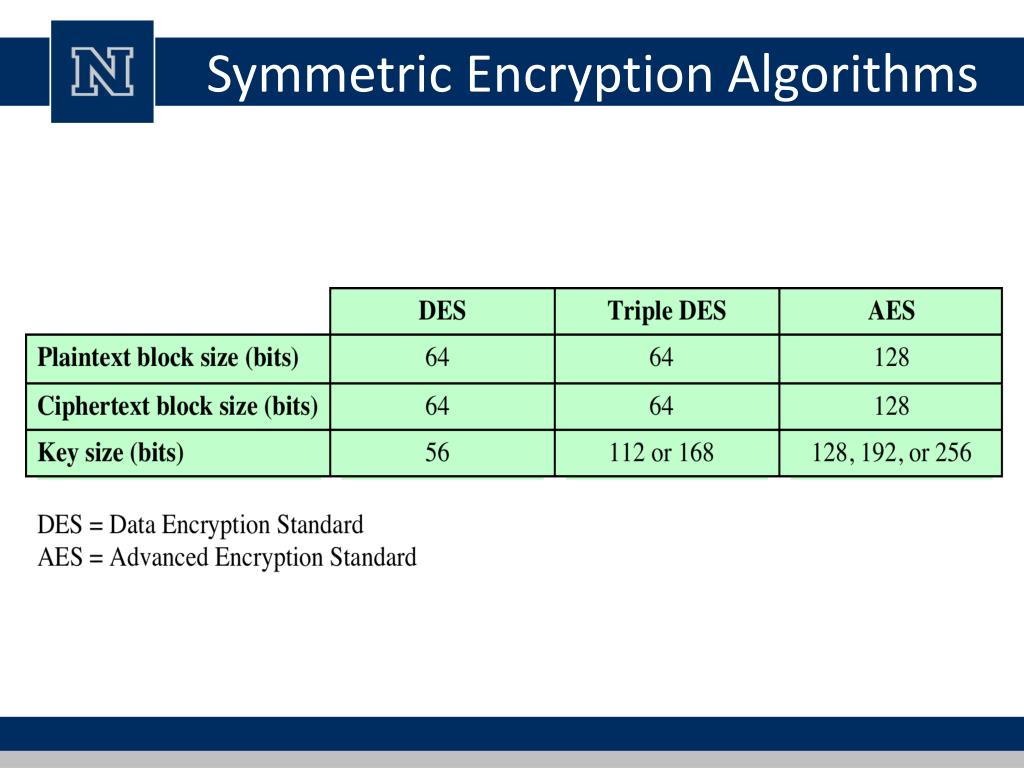
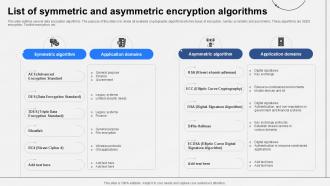
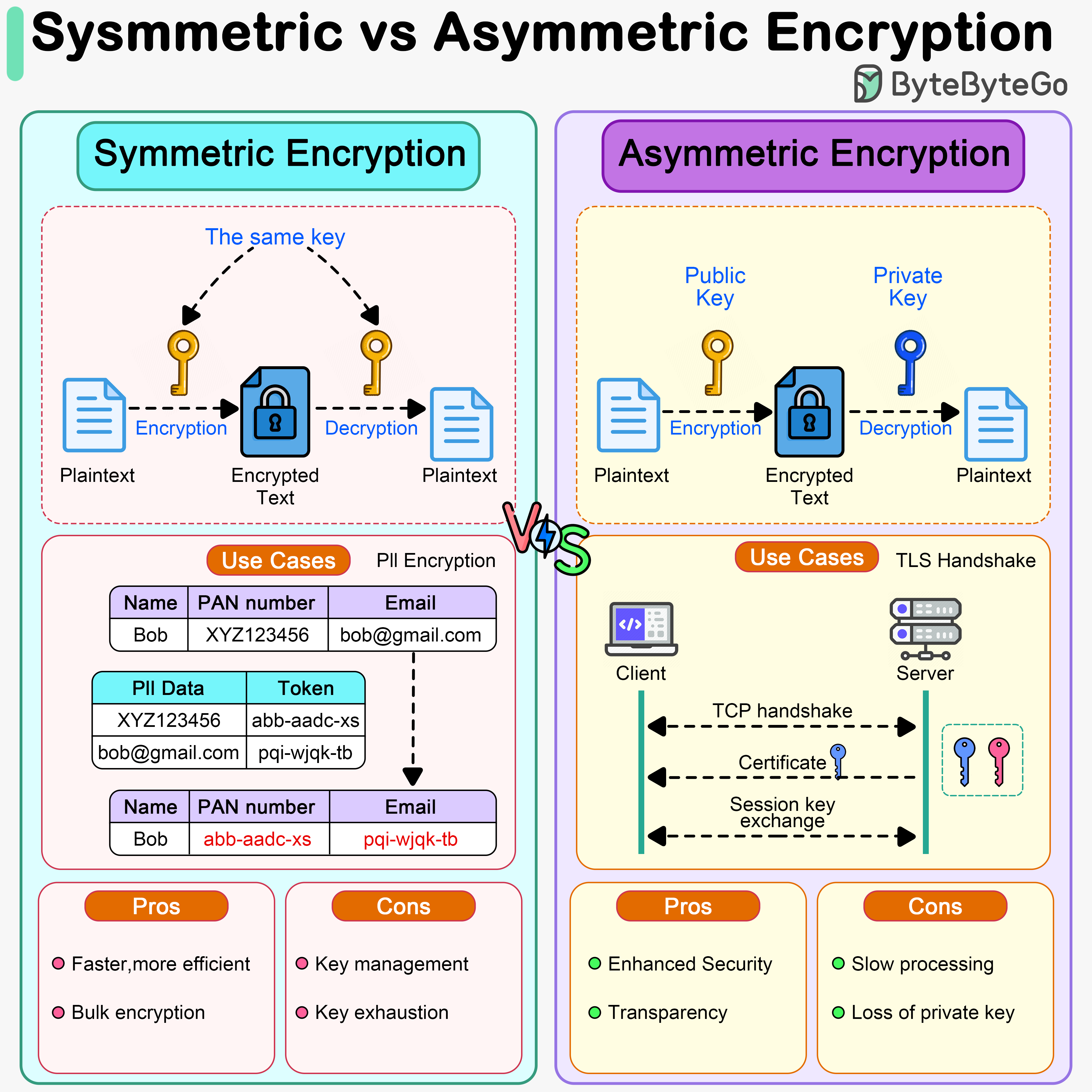
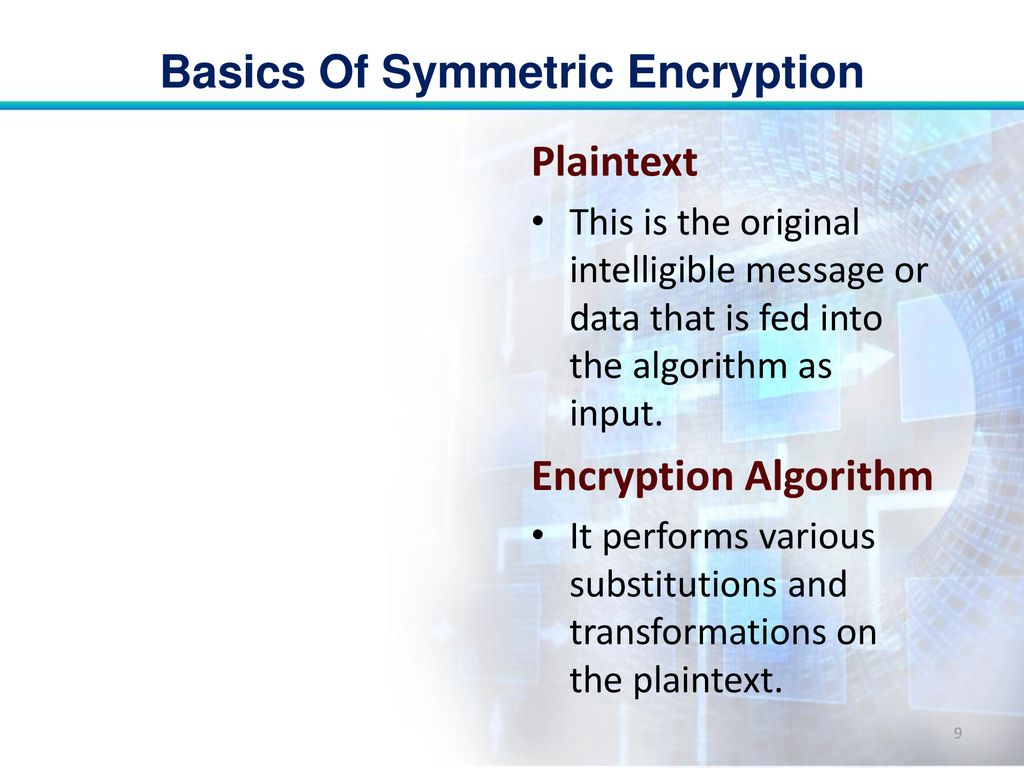
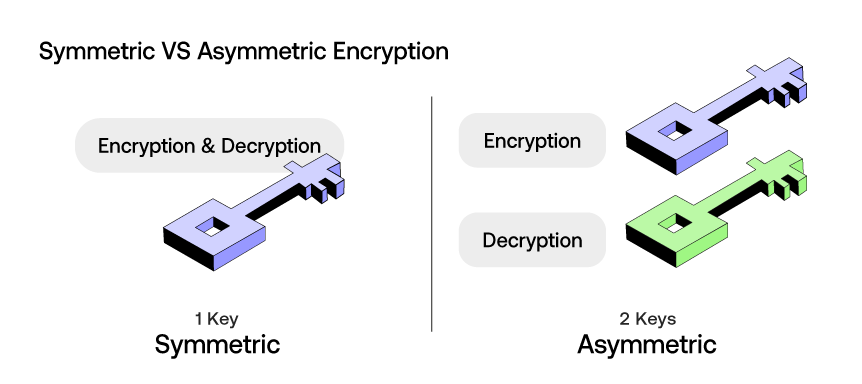
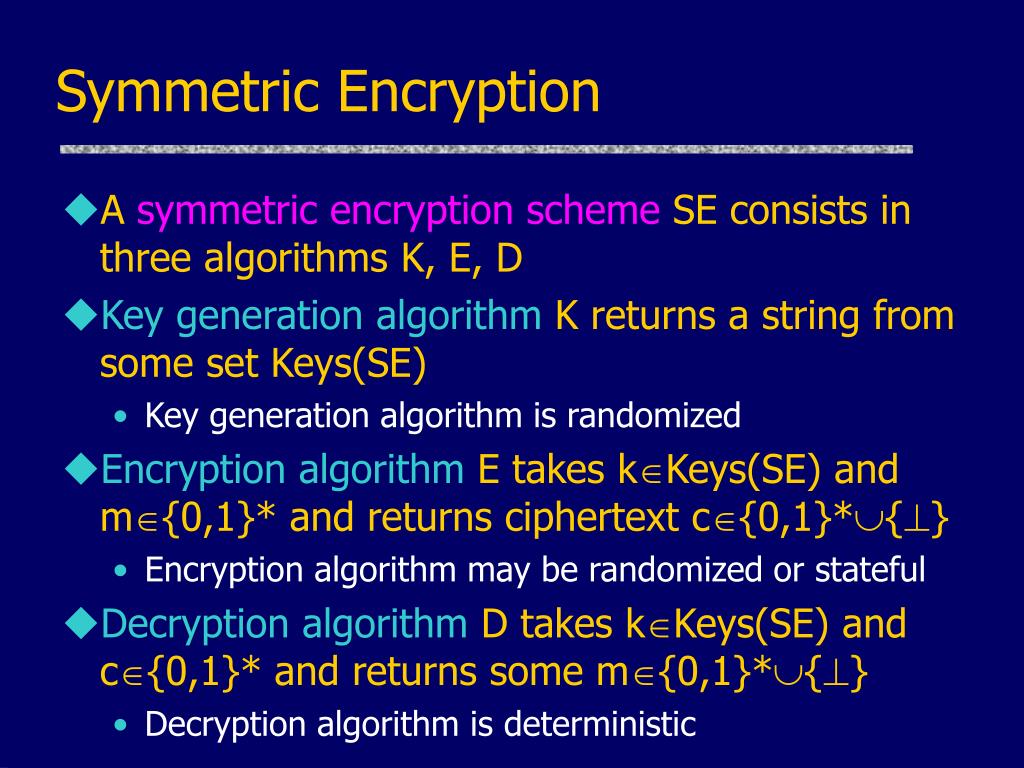
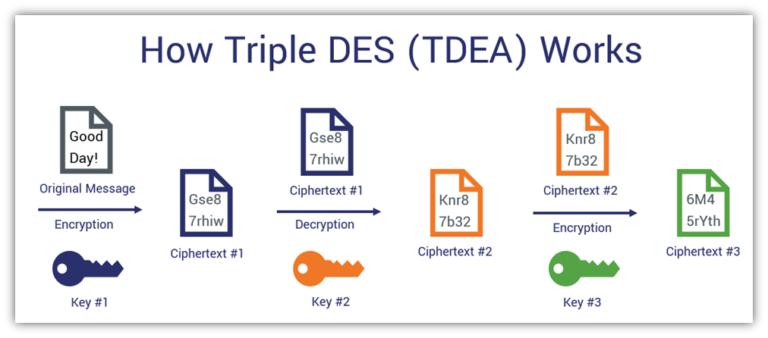
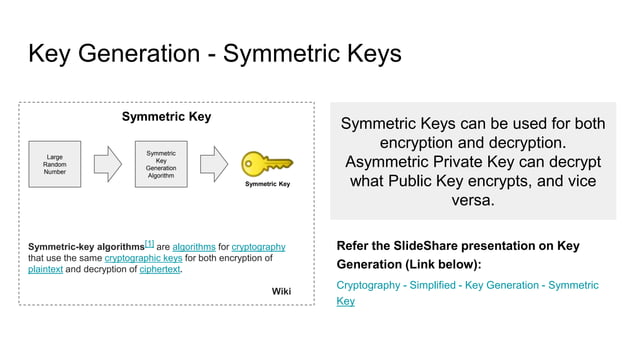
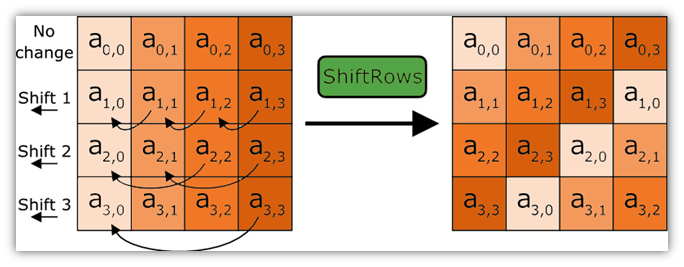
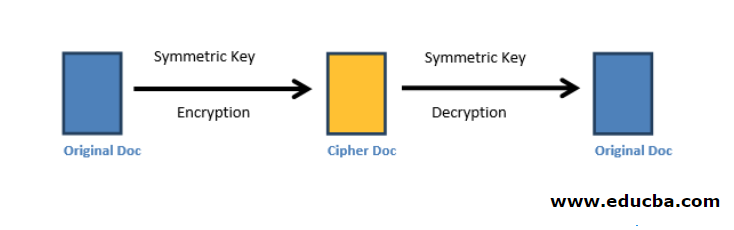
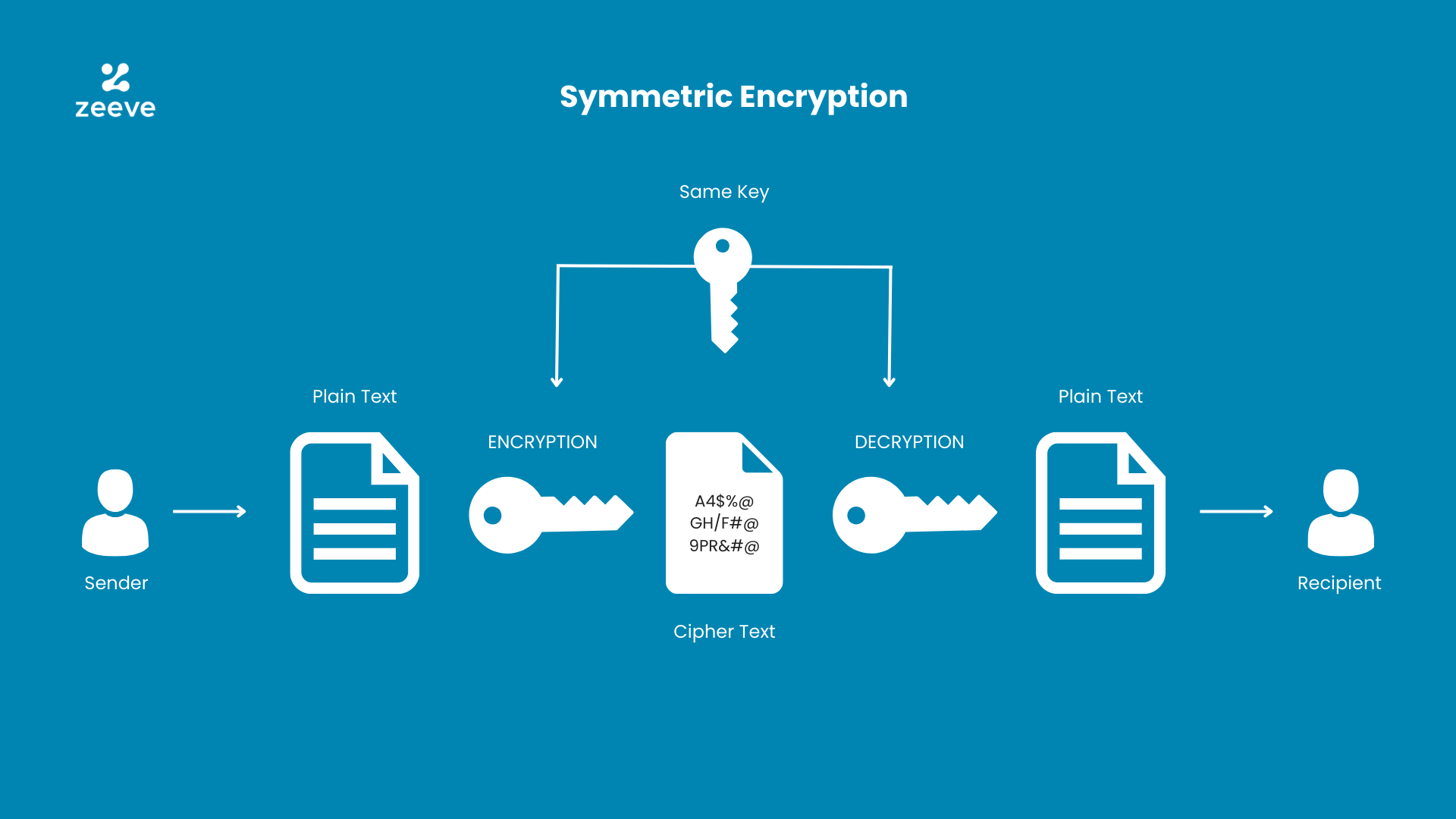
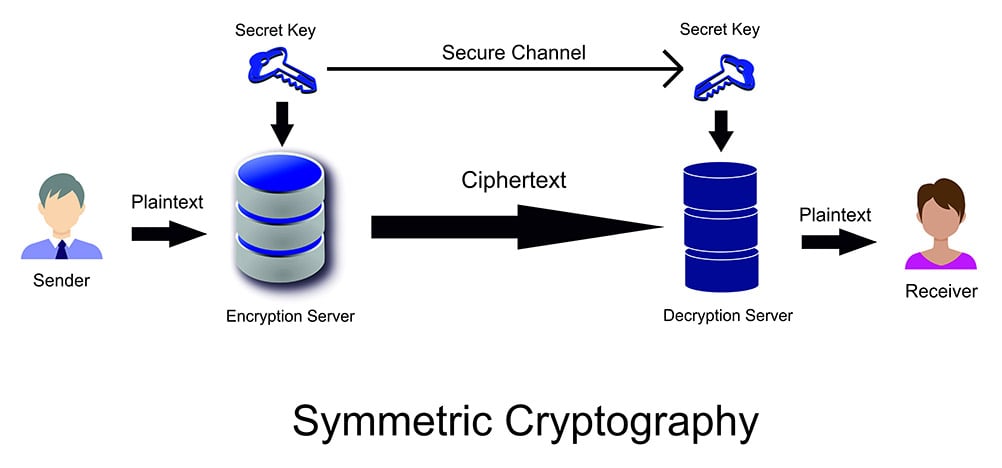
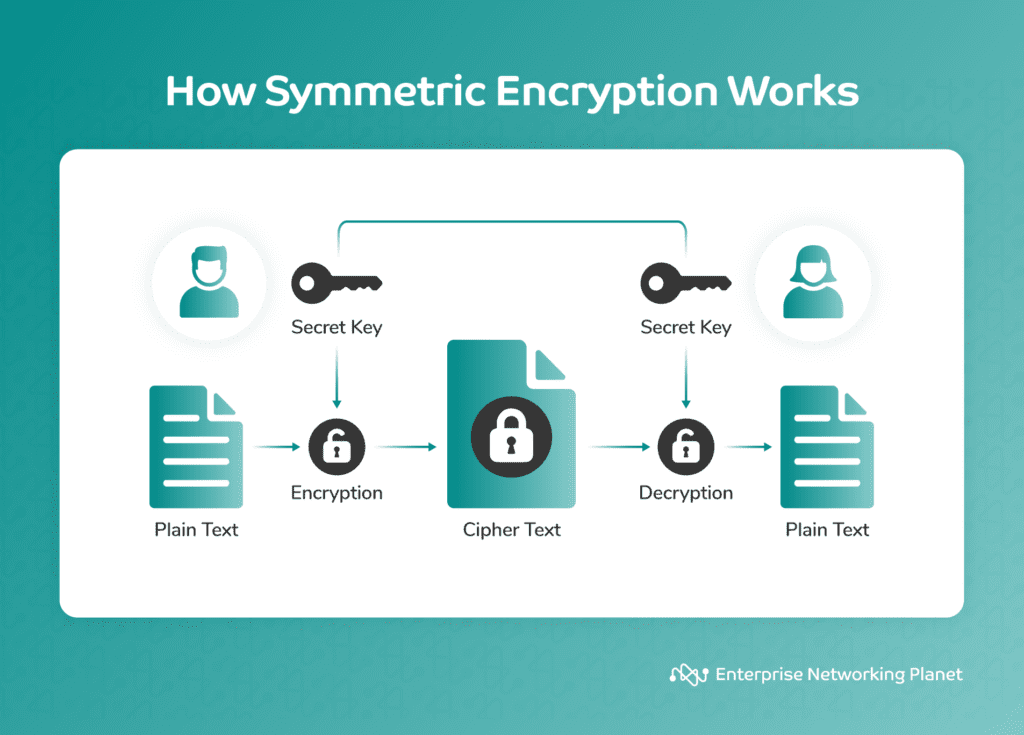
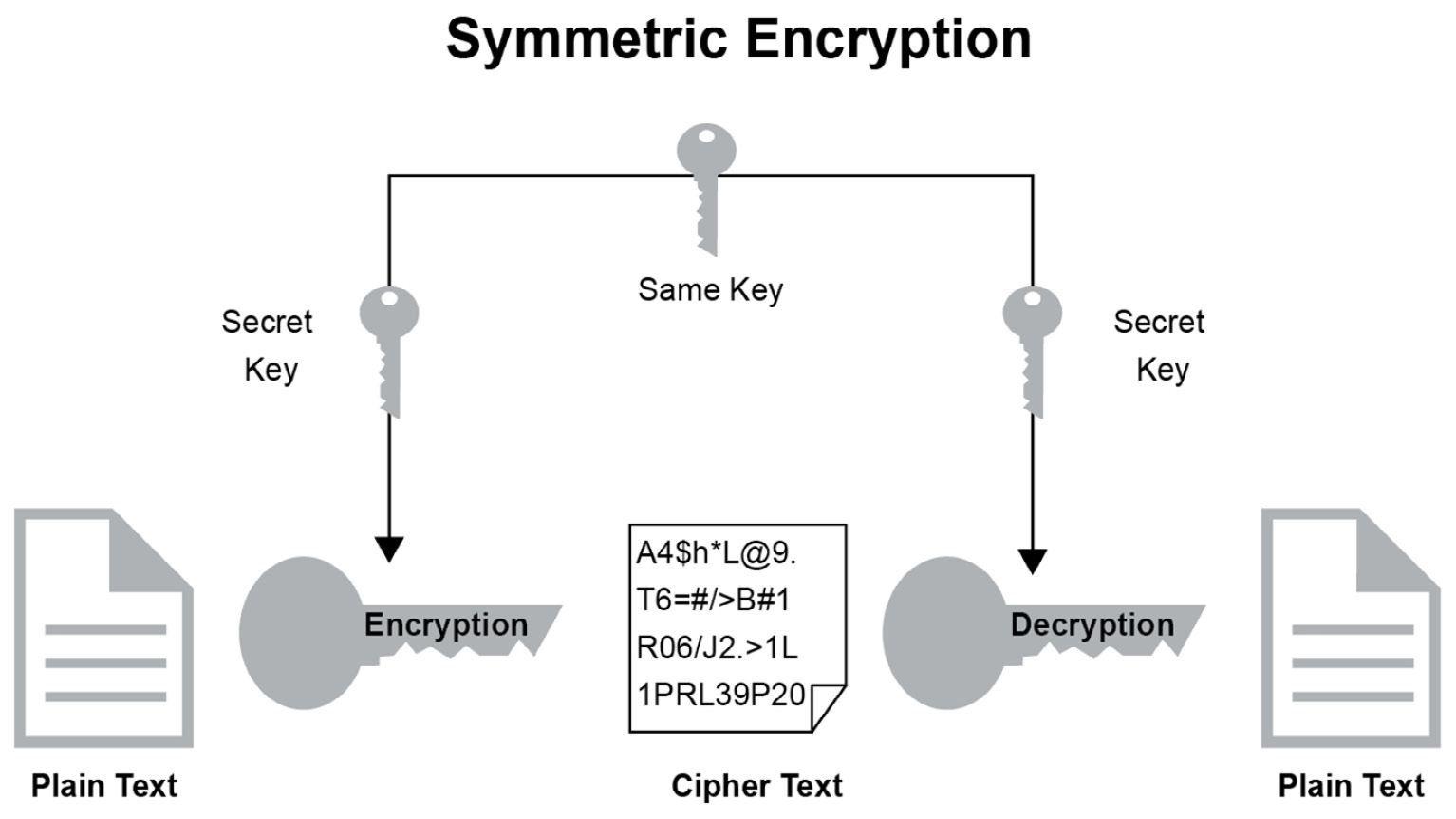
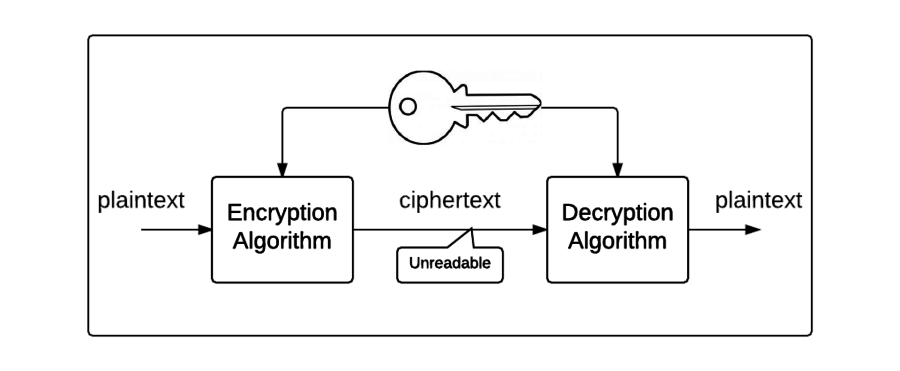
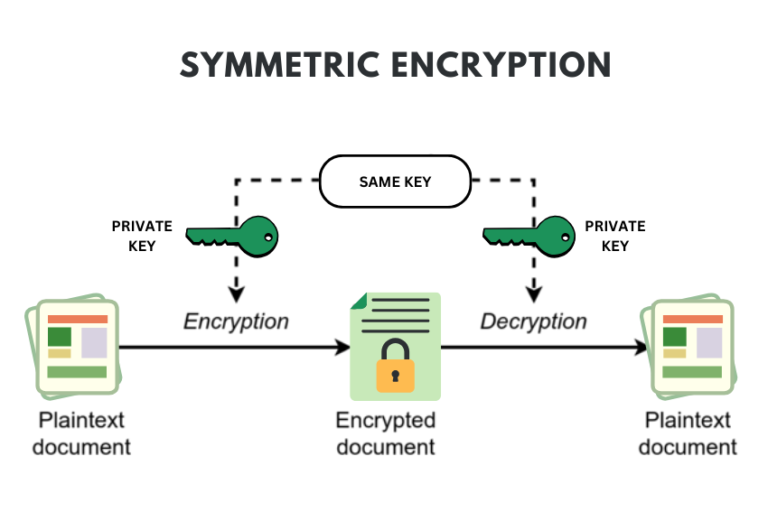
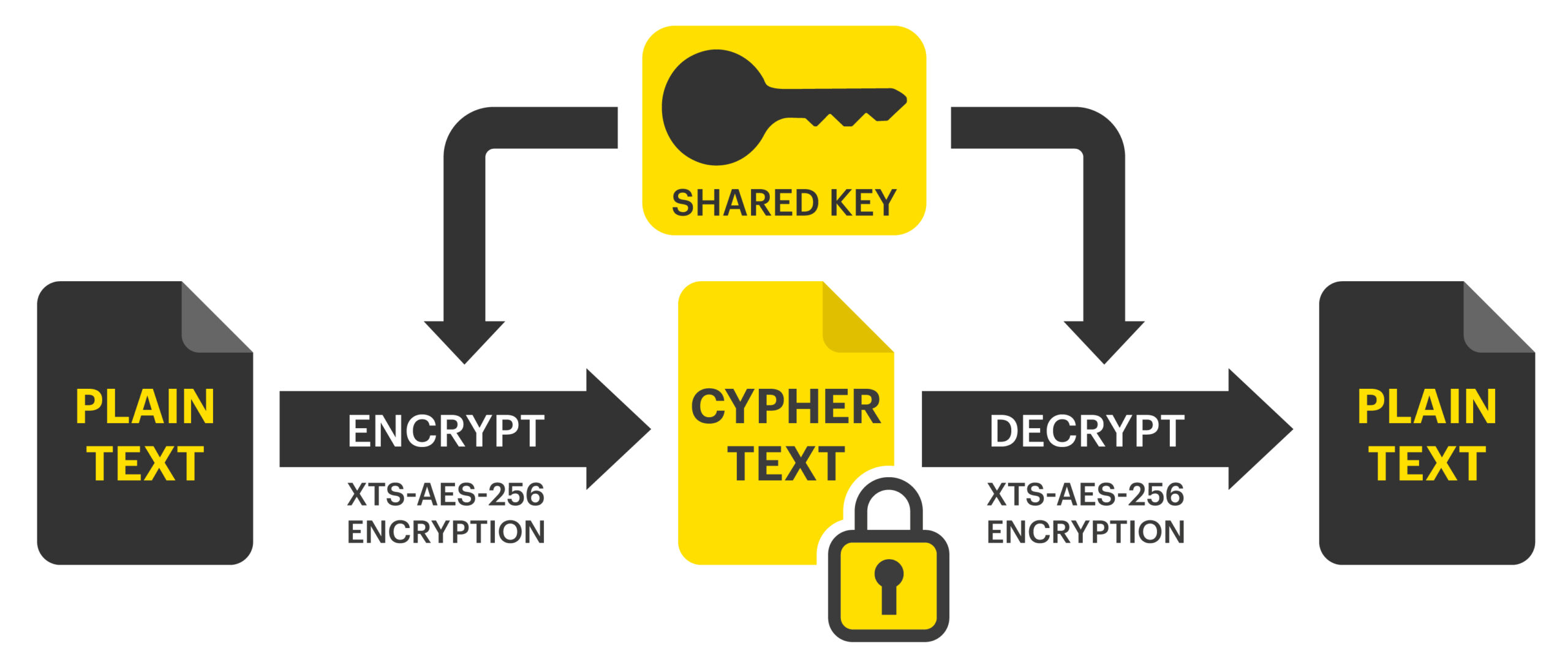
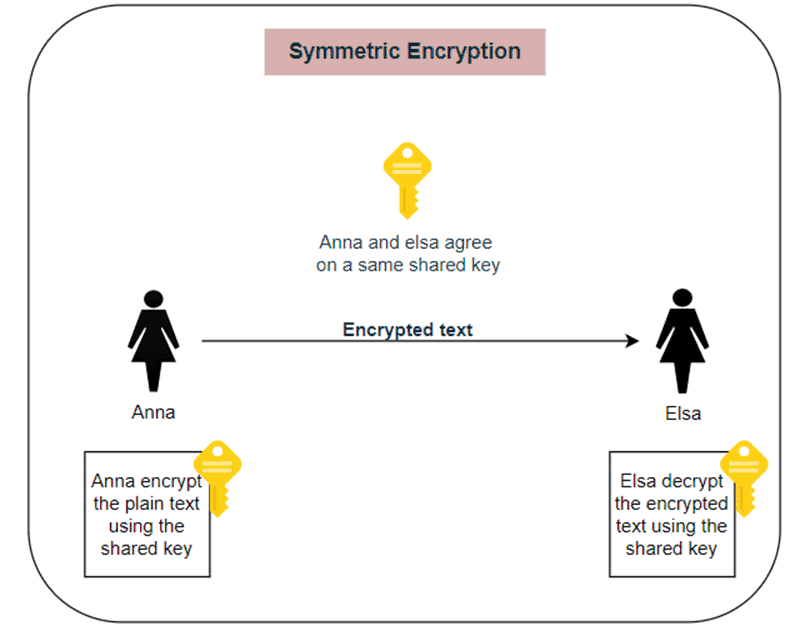
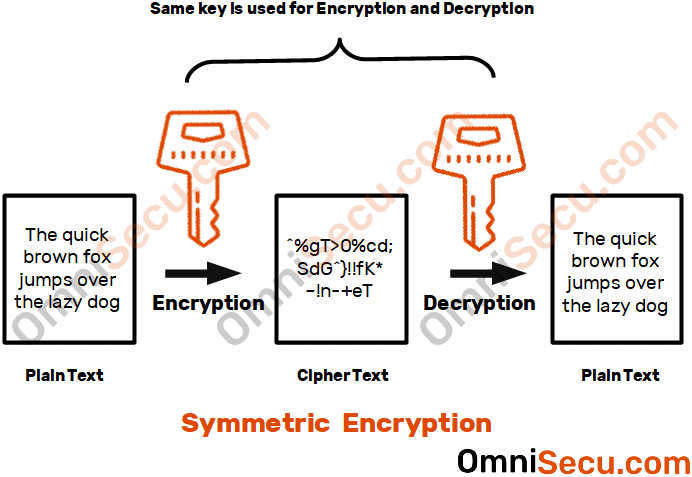
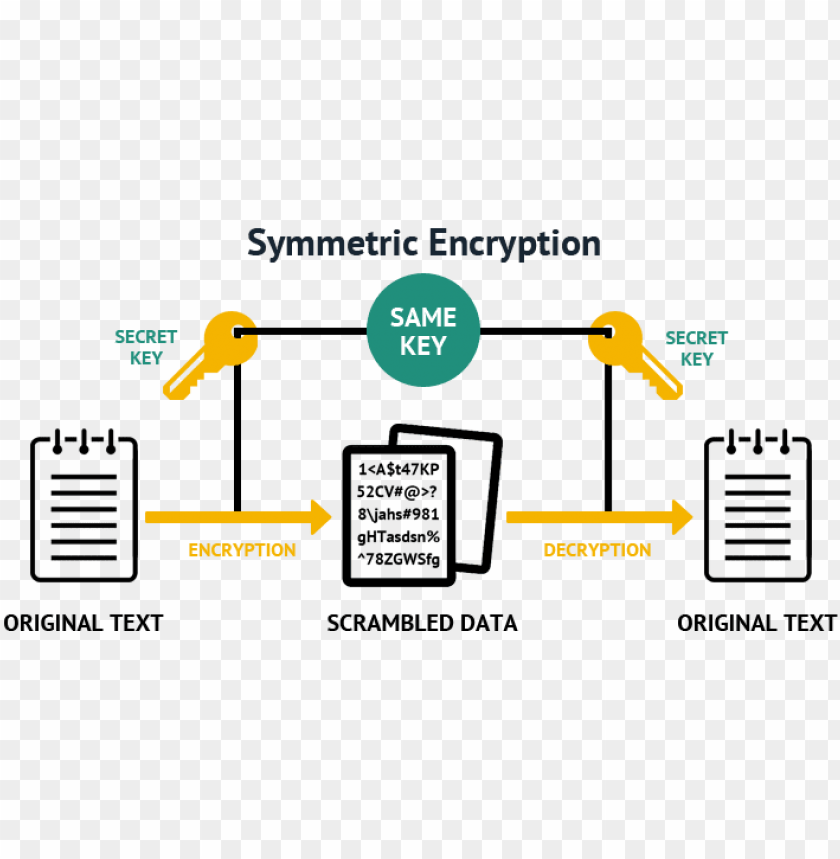
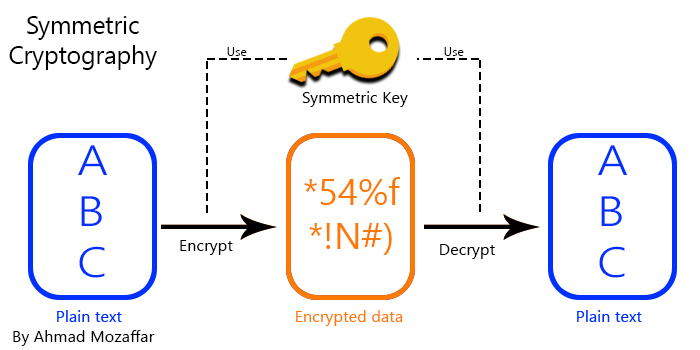
Symmetric Encryption Algorithm
Advance healthcare with our stunning medical Symmetric Encryption Algorithm collection of comprehensive galleries of clinical images. medically documenting photography, images, and pictures. ideal for healthcare communications and materials. Discover high-resolution Symmetric Encryption Algorithm images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All Symmetric Encryption Algorithm images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Symmetric Encryption Algorithm collection for various creative and professional projects. Advanced search capabilities make finding the perfect Symmetric Encryption Algorithm image effortless and efficient. Professional licensing options accommodate both commercial and educational usage requirements. The Symmetric Encryption Algorithm archive serves professionals, educators, and creatives across diverse industries. Comprehensive tagging systems facilitate quick discovery of relevant Symmetric Encryption Algorithm content. Each image in our Symmetric Encryption Algorithm gallery undergoes rigorous quality assessment before inclusion. Our Symmetric Encryption Algorithm database continuously expands with fresh, relevant content from skilled photographers. Regular updates keep the Symmetric Encryption Algorithm collection current with contemporary trends and styles. Cost-effective licensing makes professional Symmetric Encryption Algorithm photography accessible to all budgets.







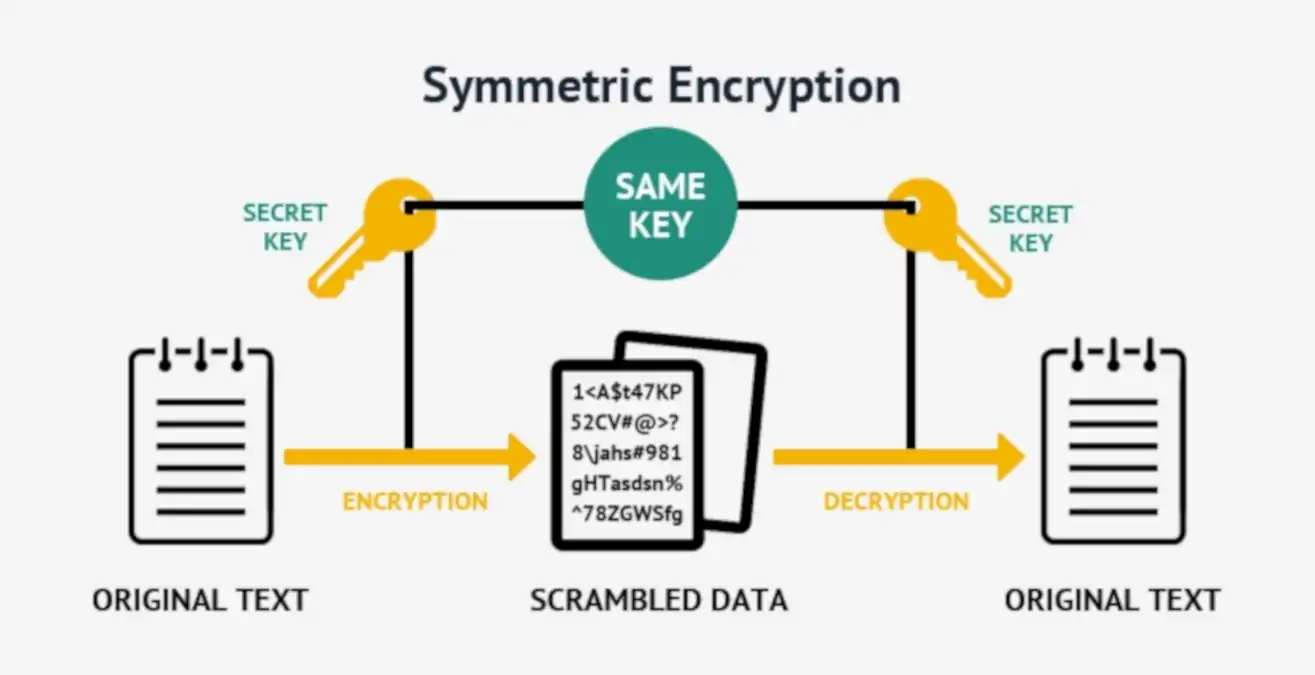





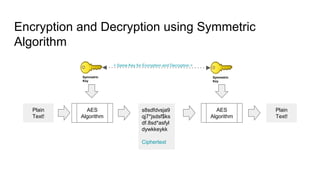
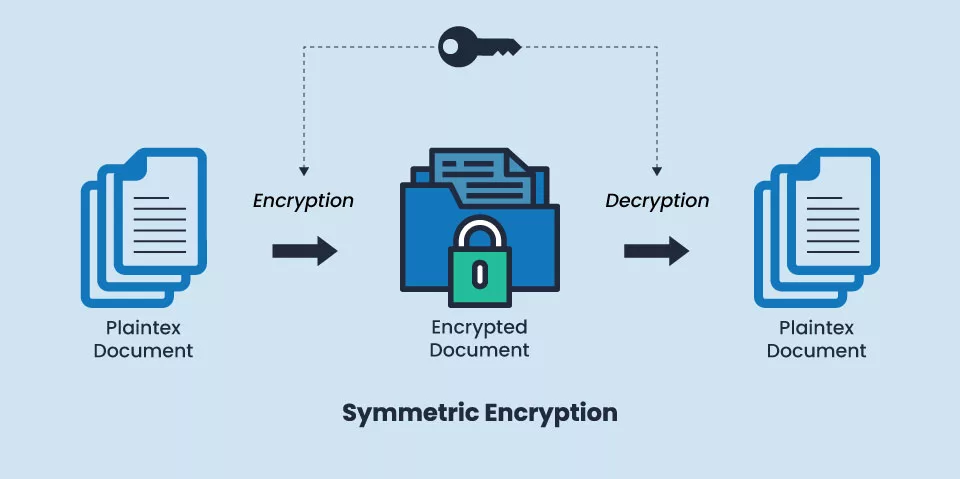

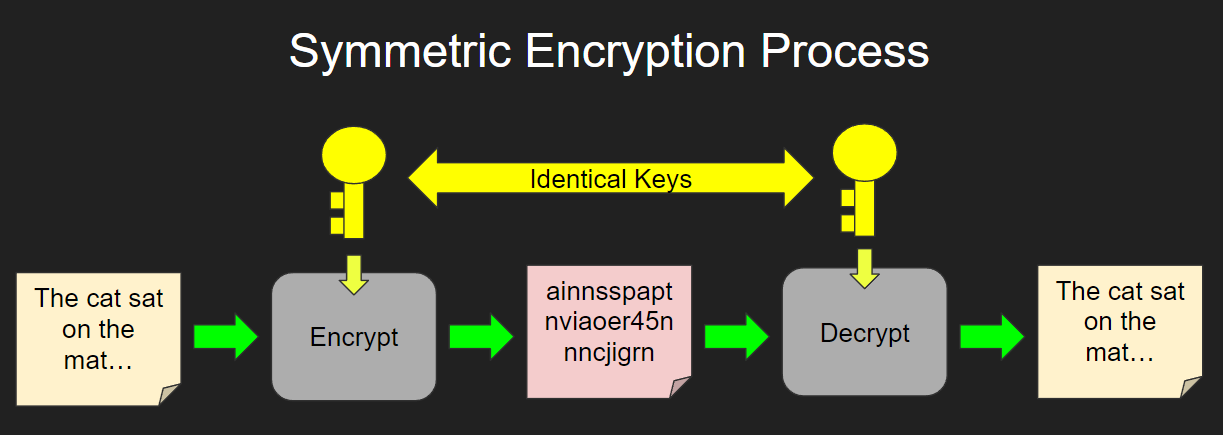
![Simplified Model of Symmetric Encryption [16] | Download Scientific Diagram](https://www.researchgate.net/publication/322252617/figure/fig1/AS:663003187916801@1535083686609/Simplified-Model-of-Symmetric-Encryption-16.png)

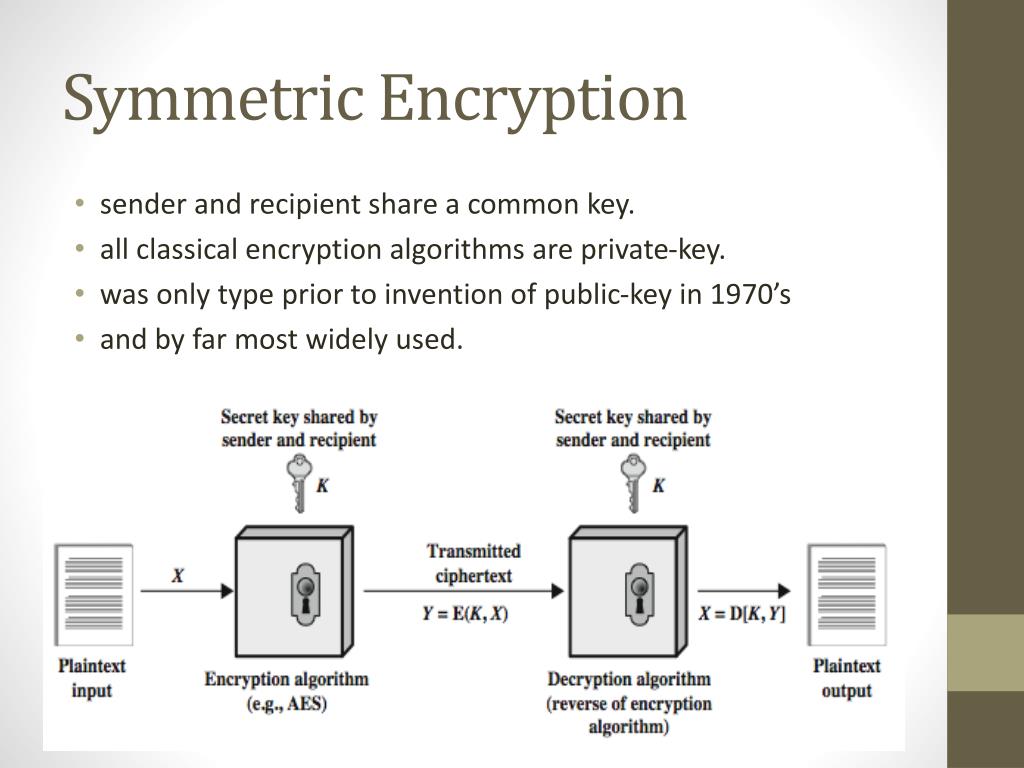
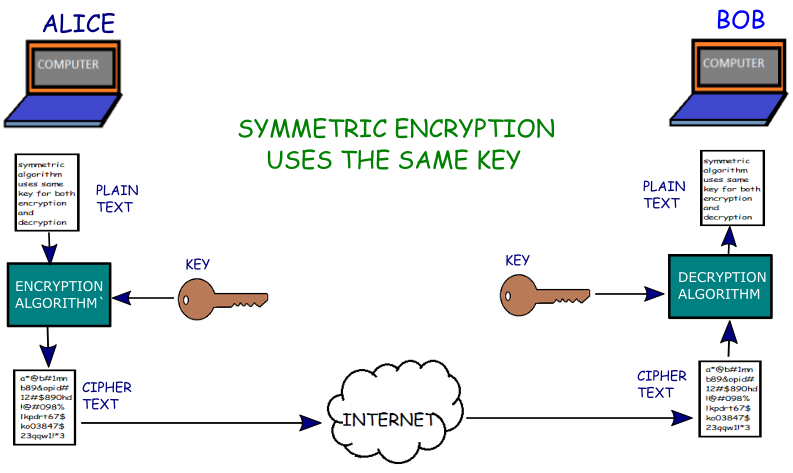








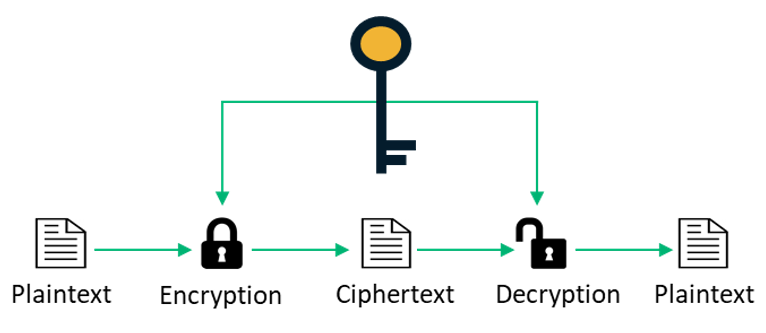



![Simplified Model of Symmetric Encryption [16] | Download Scientific Diagram](https://www.researchgate.net/profile/Murtala-Aminu-Baba/publication/322252617/figure/fig1/AS:663003187916801@1535083686609/Simplified-Model-of-Symmetric-Encryption-16_Q640.jpg)
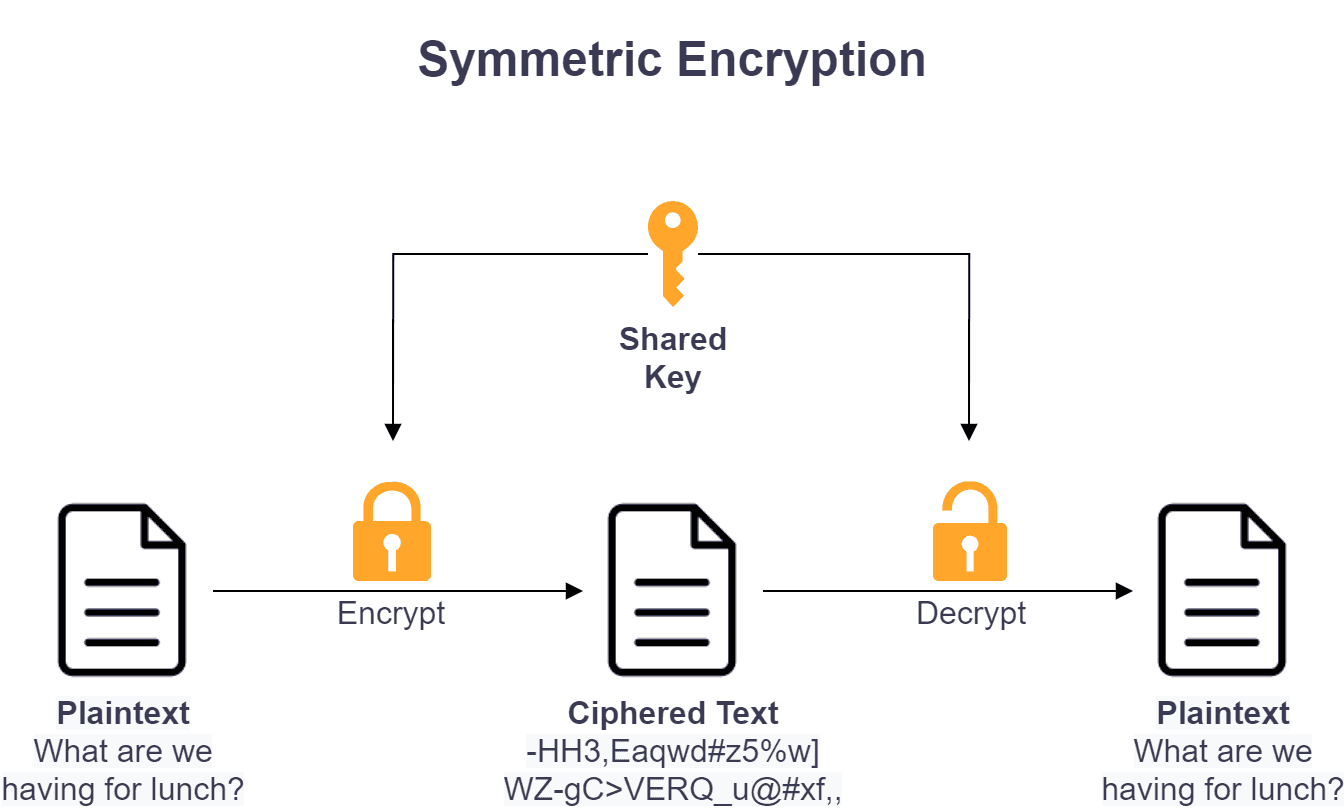
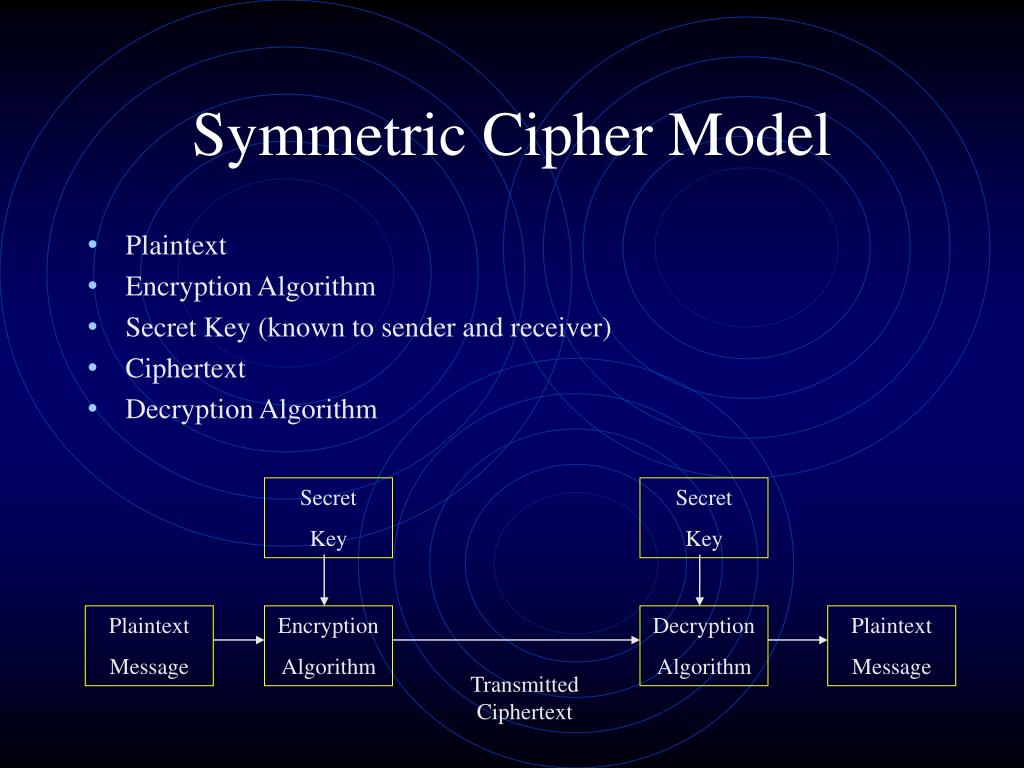

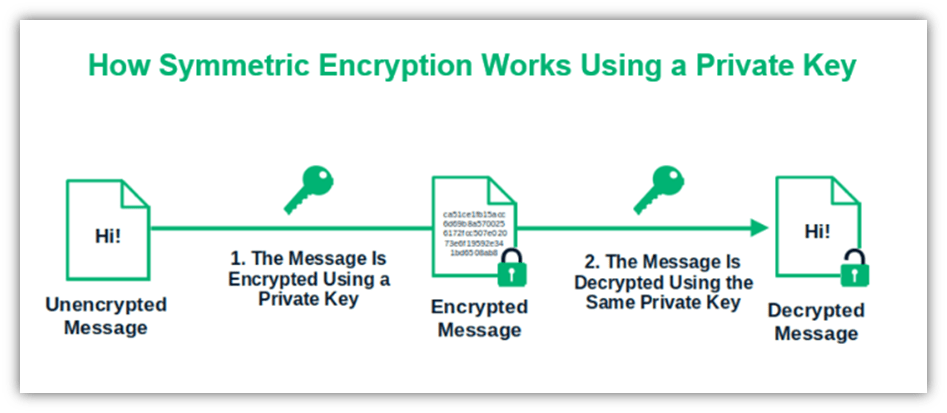

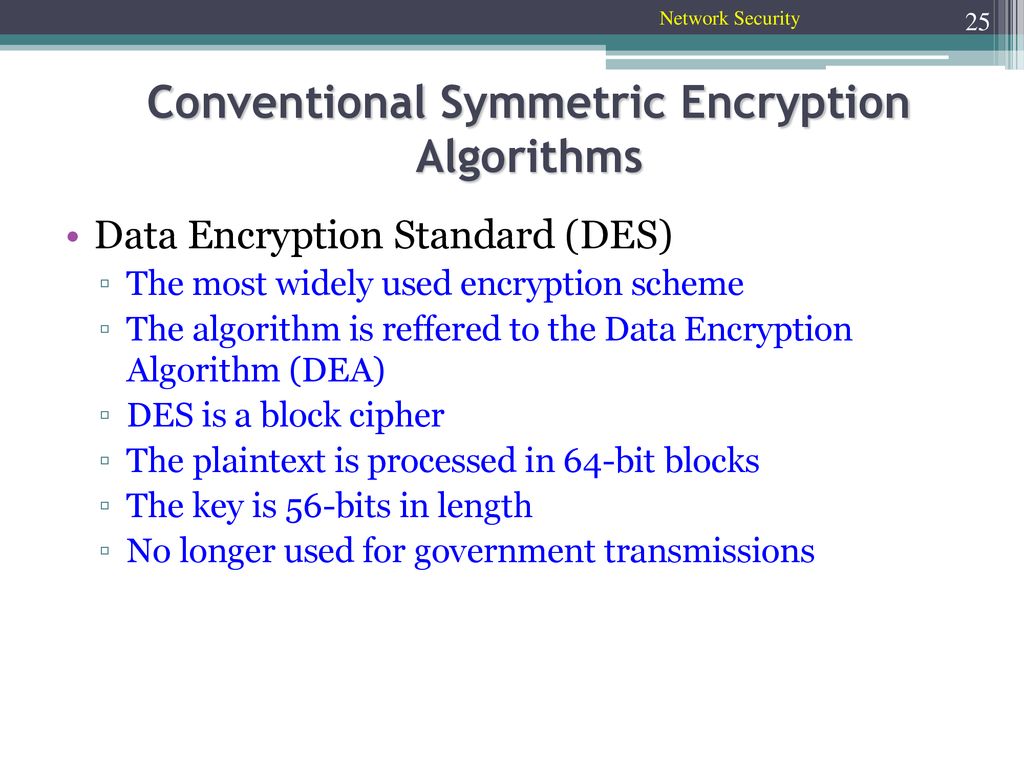



![Simplified Model of Symmetric Encryption [24] | Download Scientific Diagram](https://www.researchgate.net/profile/Ghassan_Majeed/publication/319402655/figure/download/fig2/AS:568656905150464@1512589779176/Simplified-Model-of-Symmetric-Encryption-24.png)

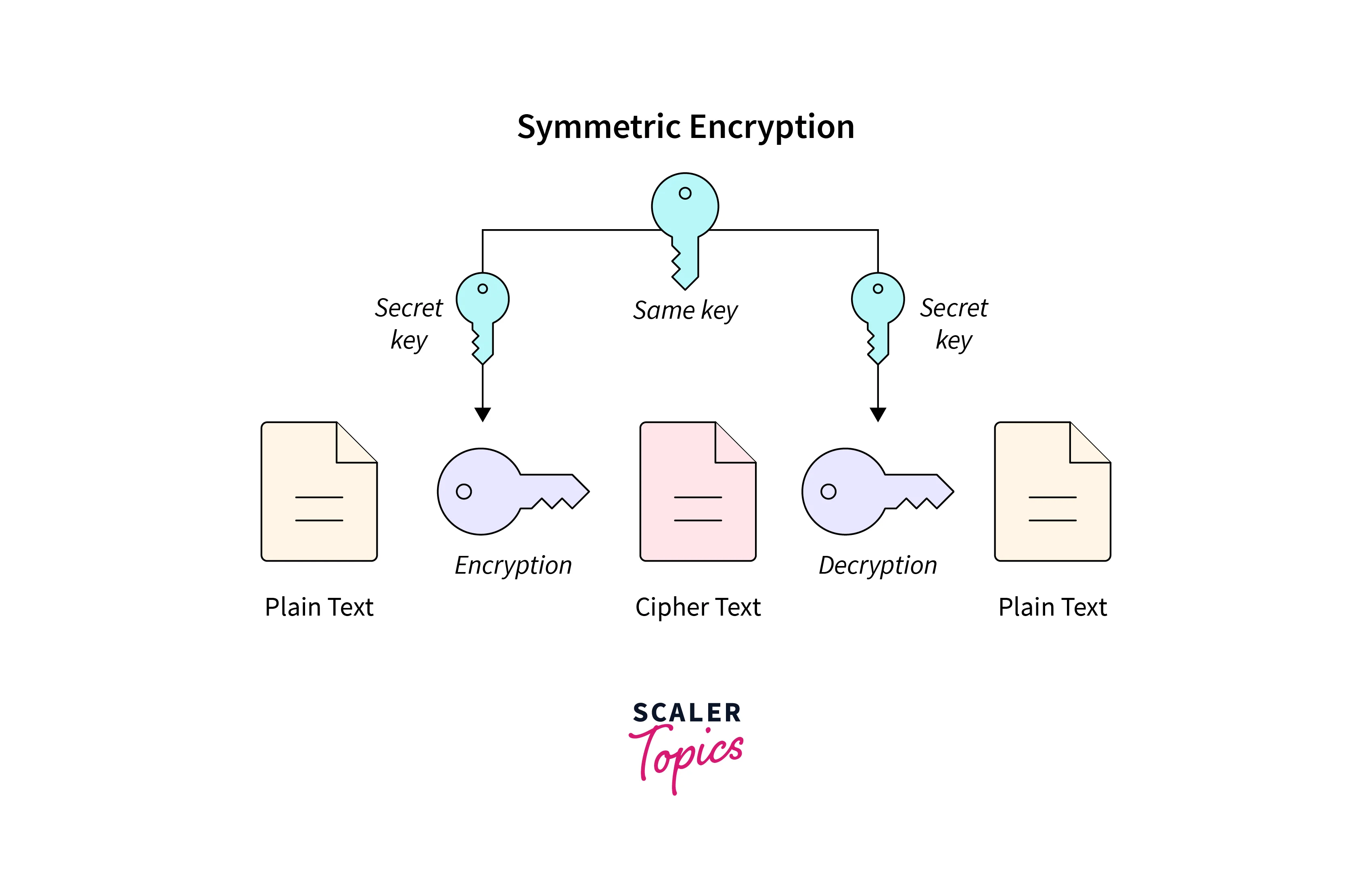
![Symmetric encryption [17] | Download Scientific Diagram](https://www.researchgate.net/publication/343025050/figure/fig1/AS:914594046423042@1595067621685/Symmetric-encryption-17.png)


![Symmetric Encryption [5] | Download Scientific Diagram](https://www.researchgate.net/publication/341738673/figure/fig1/AS:11431281127319798@1678997683334/Symmetric-Encryption-5_Q640.jpg)



![Symmetric encryption [17] | Download Scientific Diagram](https://www.researchgate.net/publication/343025050/figure/fig1/AS:914594046423042@1595067621685/Symmetric-encryption-17_Q320.jpg)



















+Encryption+algorithms.jpg)