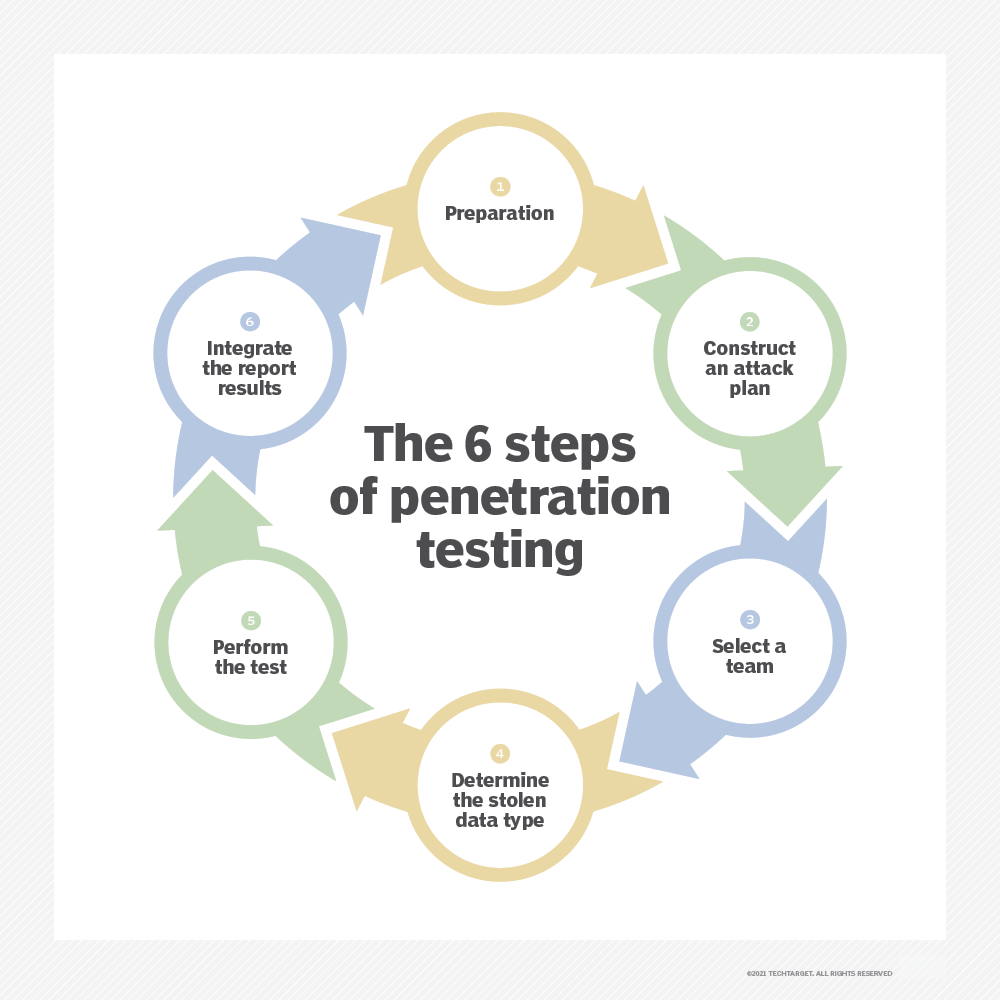
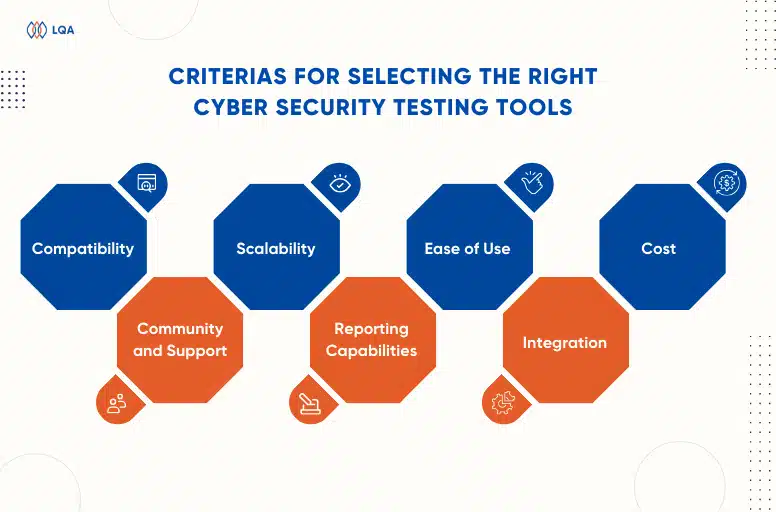
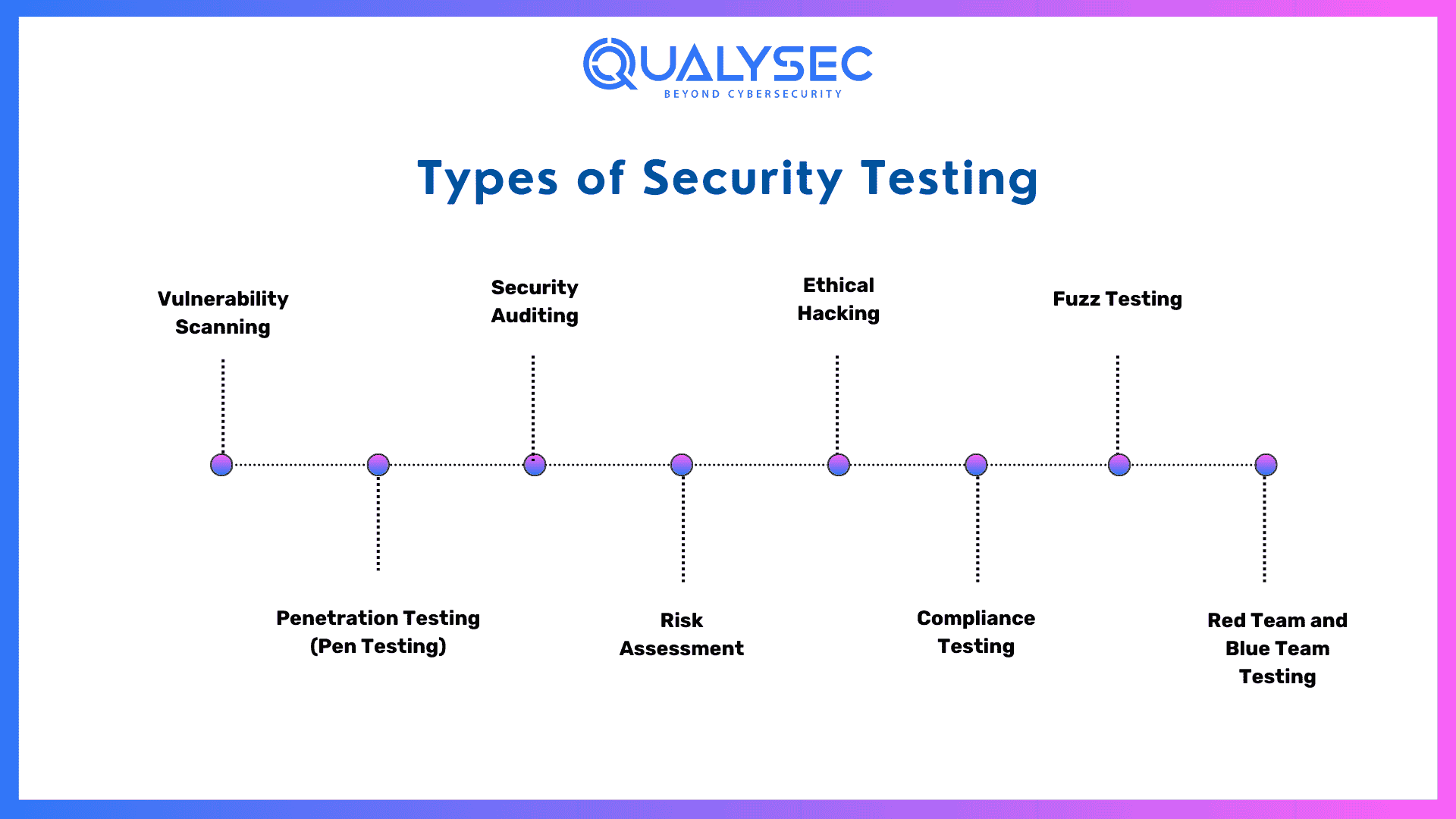
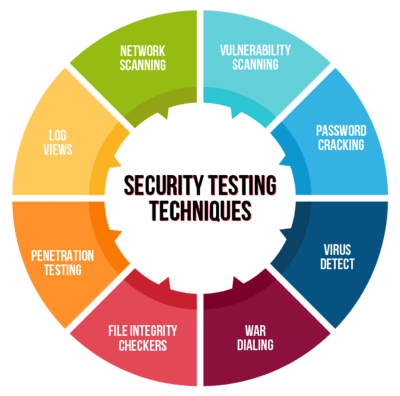
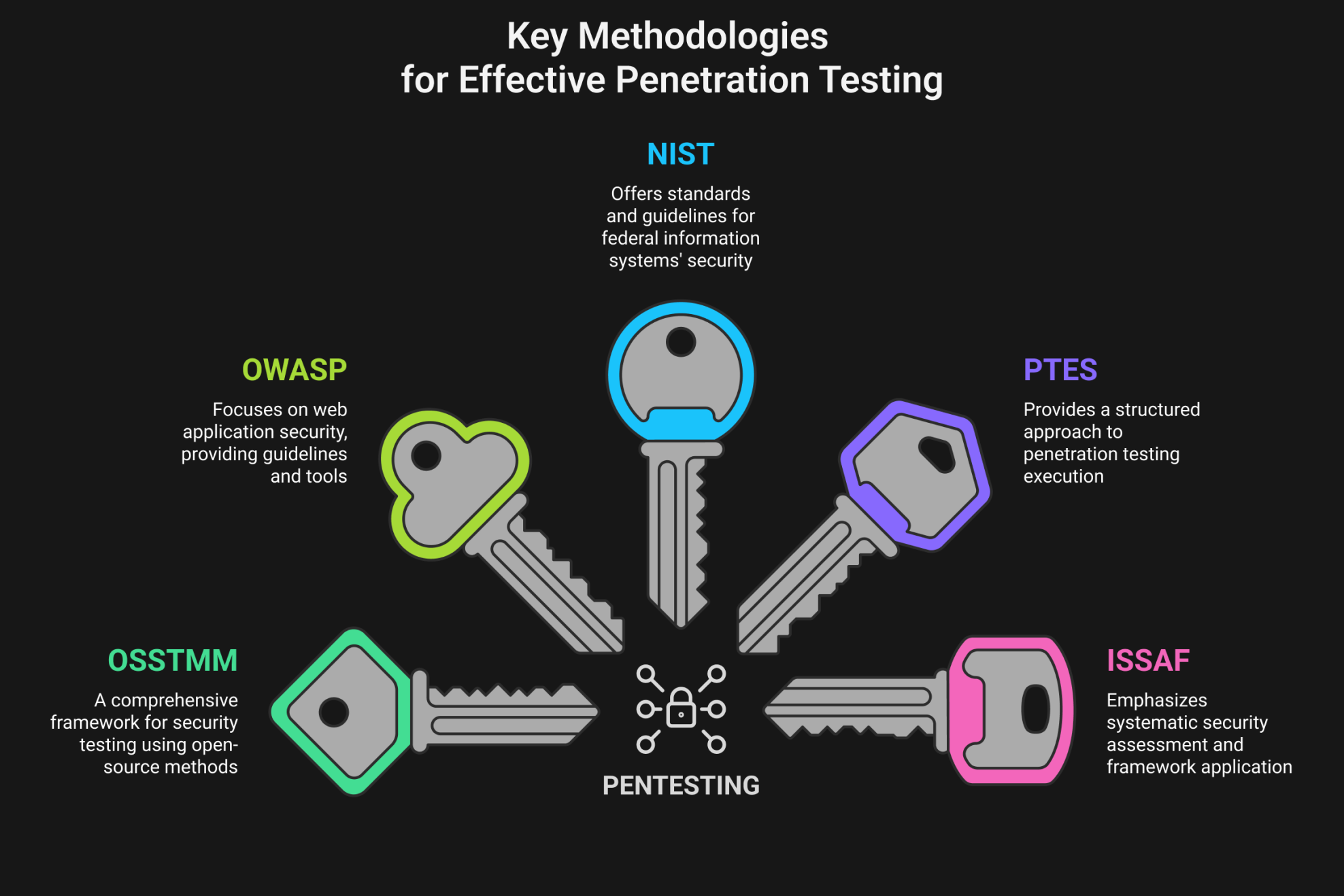
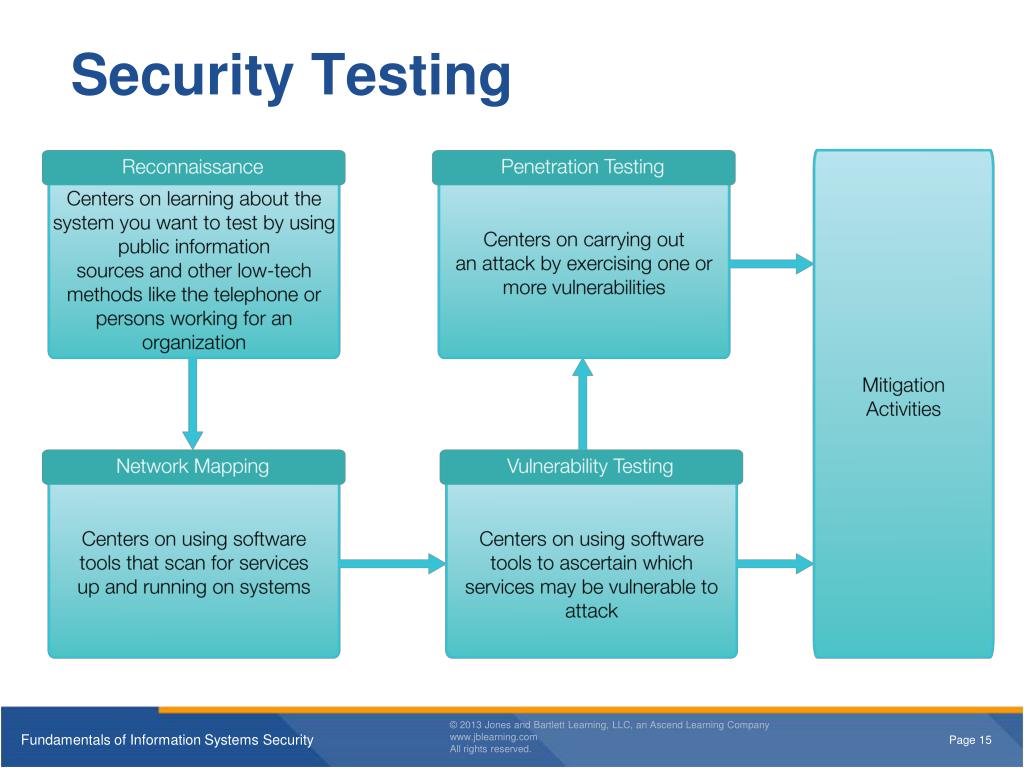
Security Testing Methodologies
Capture truth through substantial collections of documentary-style Security Testing Methodologies photographs. authentically documenting photography, images, and pictures. ideal for historical documentation and archives. Our Security Testing Methodologies collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All Security Testing Methodologies images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Security Testing Methodologies collection for various creative and professional projects. Each image in our Security Testing Methodologies gallery undergoes rigorous quality assessment before inclusion. Comprehensive tagging systems facilitate quick discovery of relevant Security Testing Methodologies content. Reliable customer support ensures smooth experience throughout the Security Testing Methodologies selection process. Instant download capabilities enable immediate access to chosen Security Testing Methodologies images. The Security Testing Methodologies collection represents years of careful curation and professional standards. Professional licensing options accommodate both commercial and educational usage requirements. Regular updates keep the Security Testing Methodologies collection current with contemporary trends and styles. Our Security Testing Methodologies database continuously expands with fresh, relevant content from skilled photographers. Advanced search capabilities make finding the perfect Security Testing Methodologies image effortless and efficient.
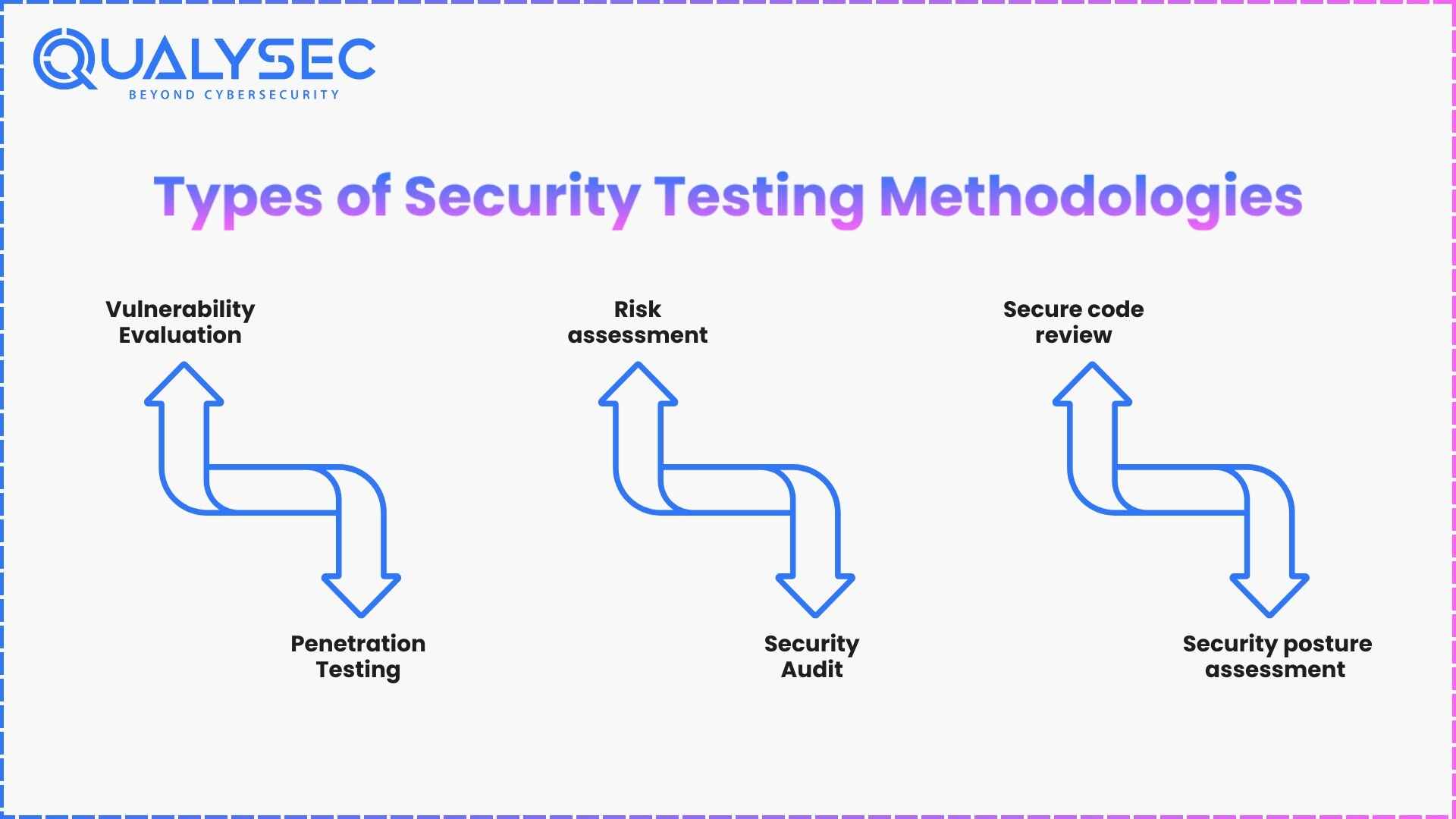



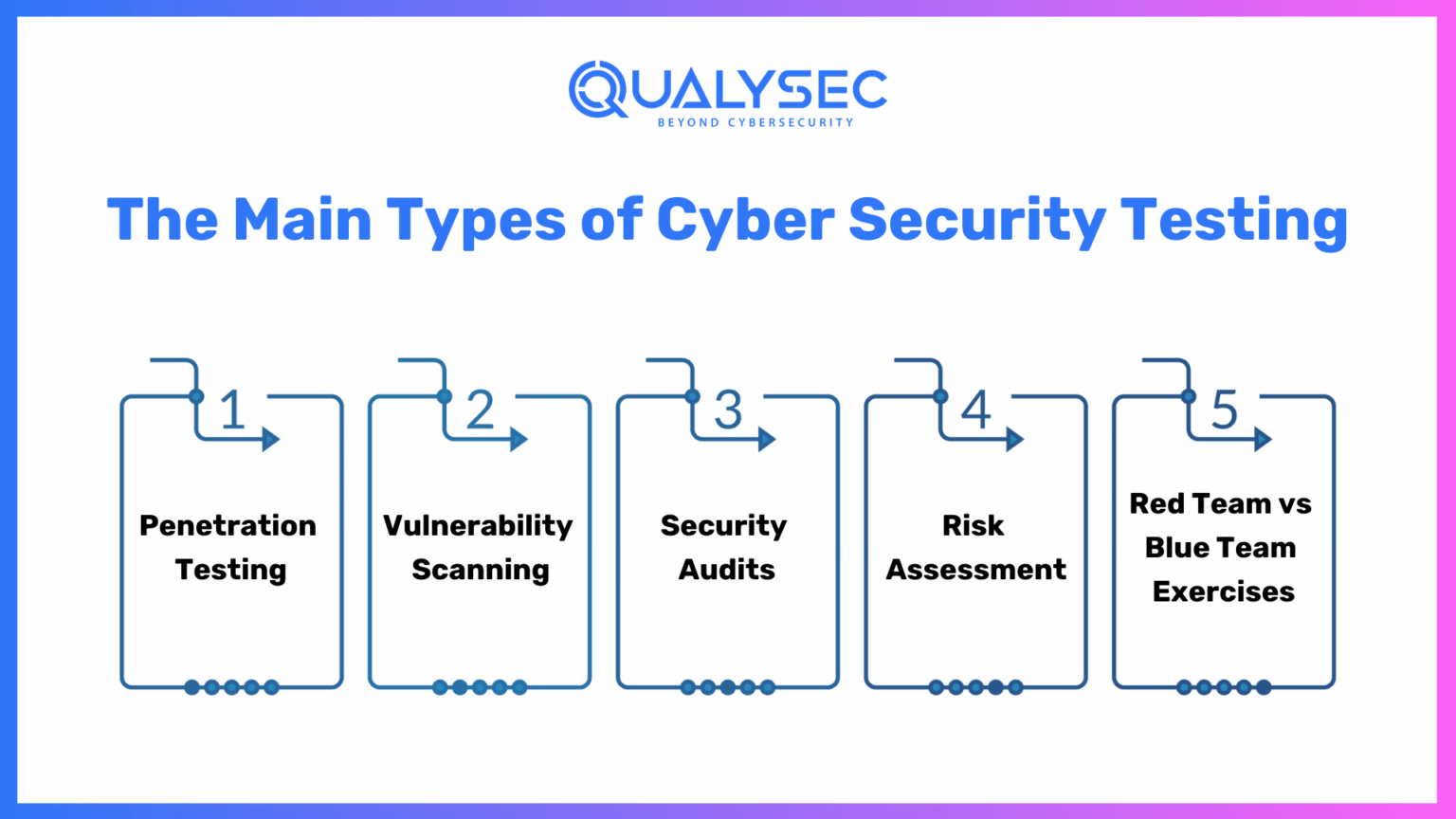
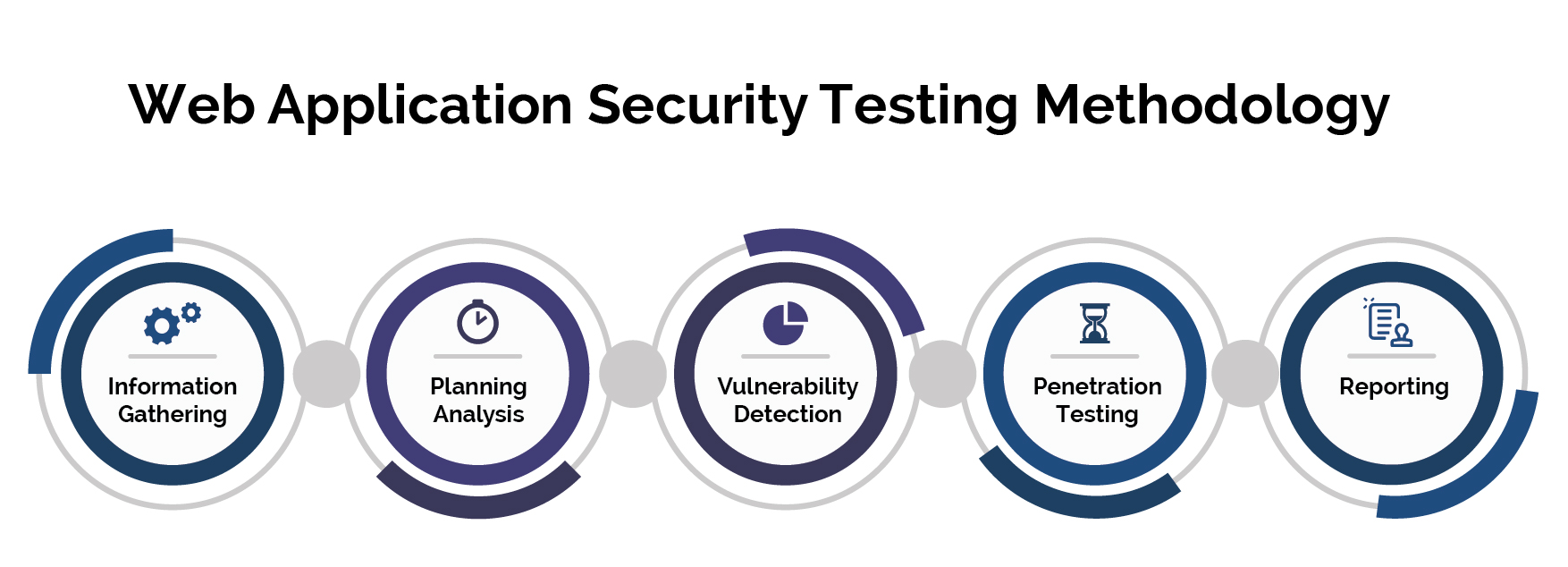

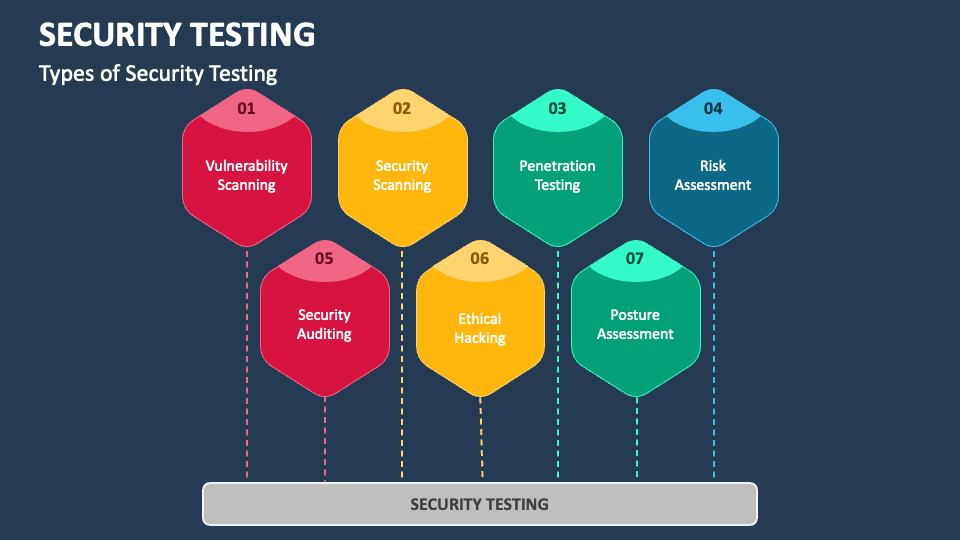















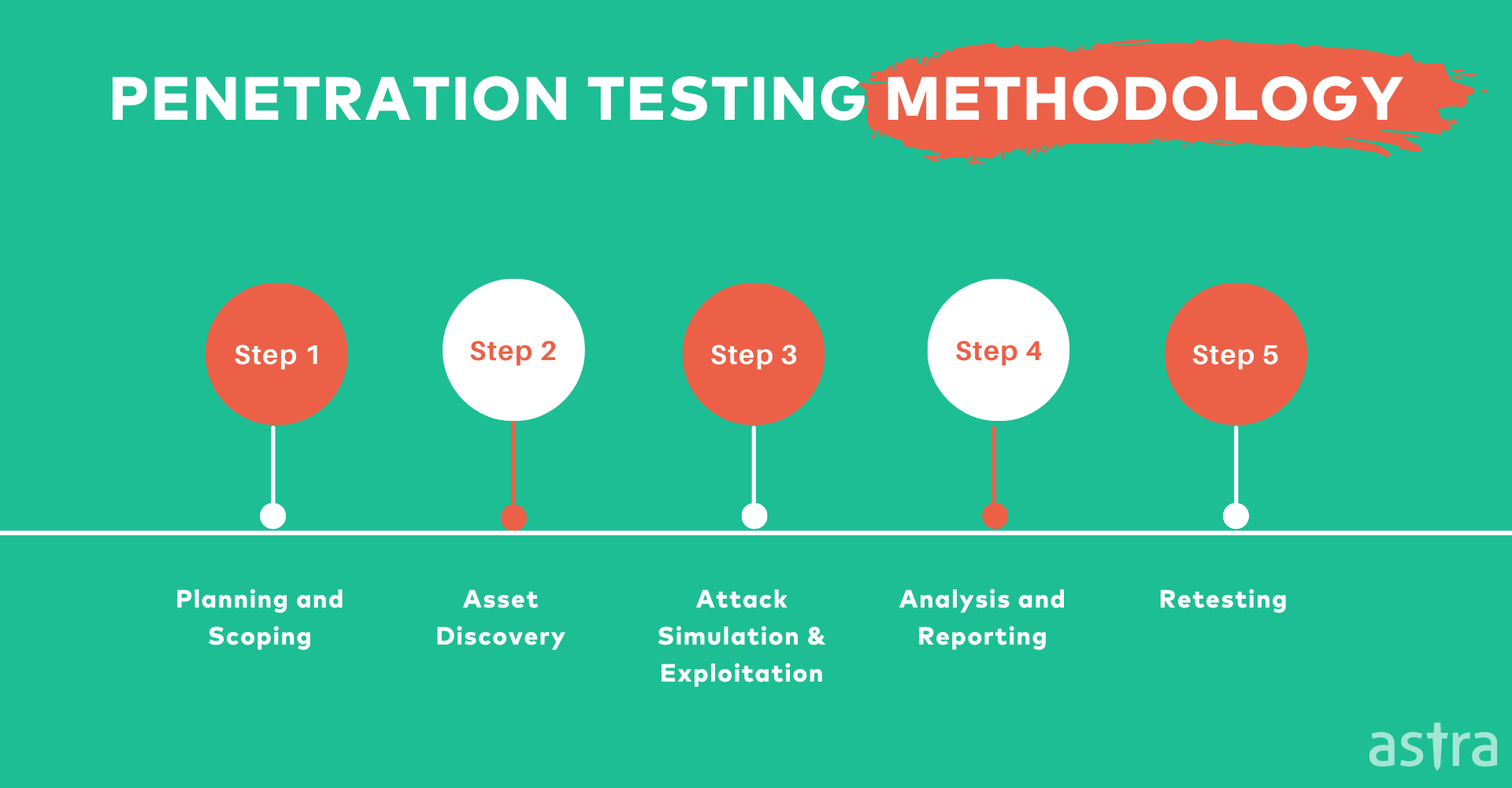
![Steps to use the Security Testing Methodology [4]. | Download ...](https://www.researchgate.net/publication/260194199/figure/fig7/AS:297219380006918@1447874030362/Steps-to-use-the-Security-Testing-Methodology-4.png)


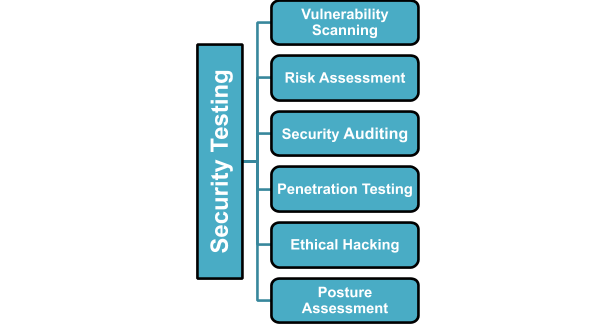






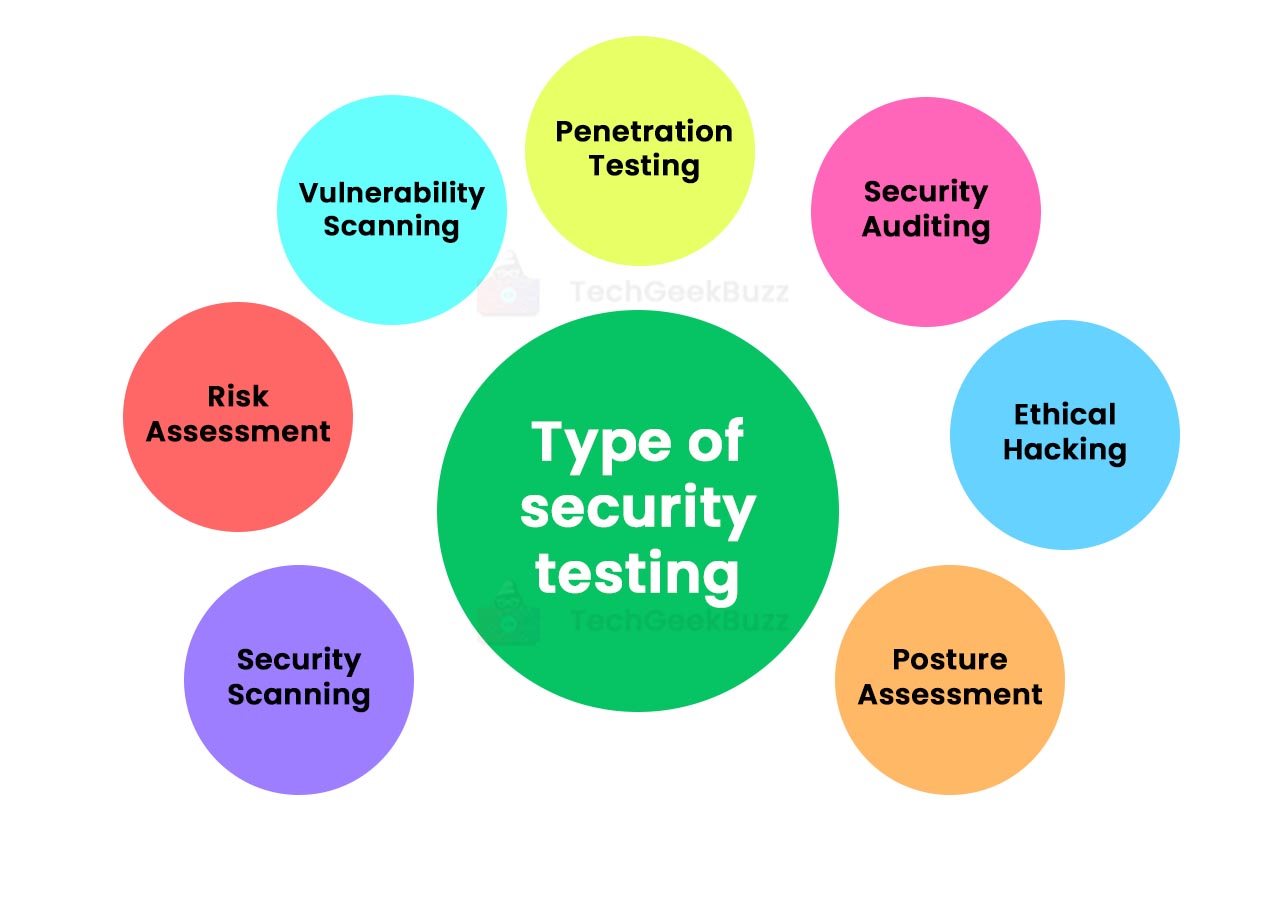


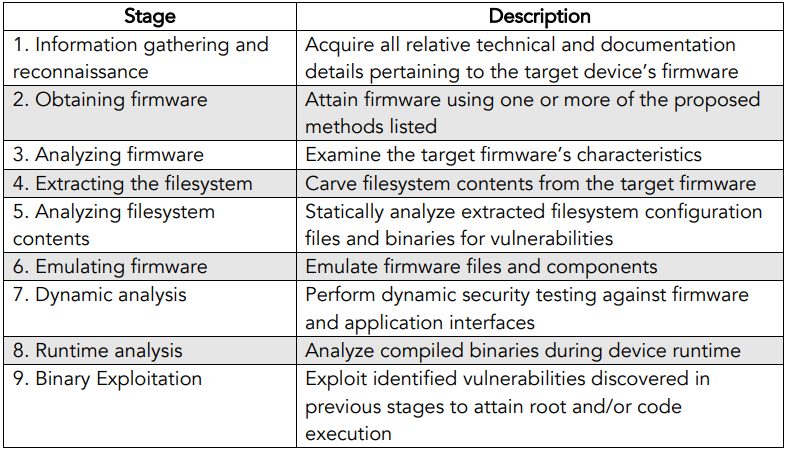







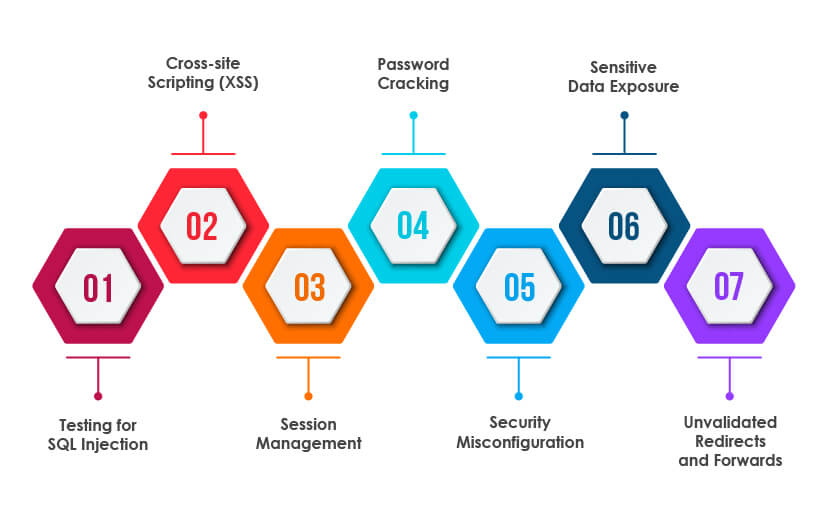



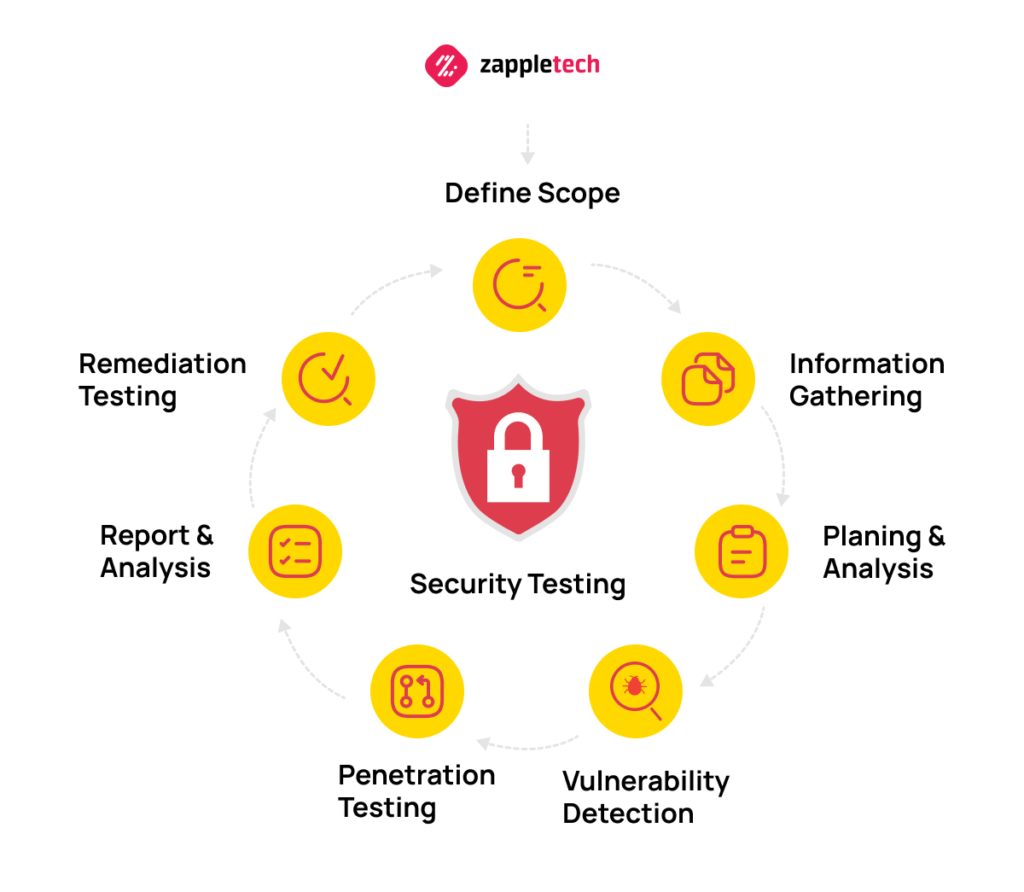
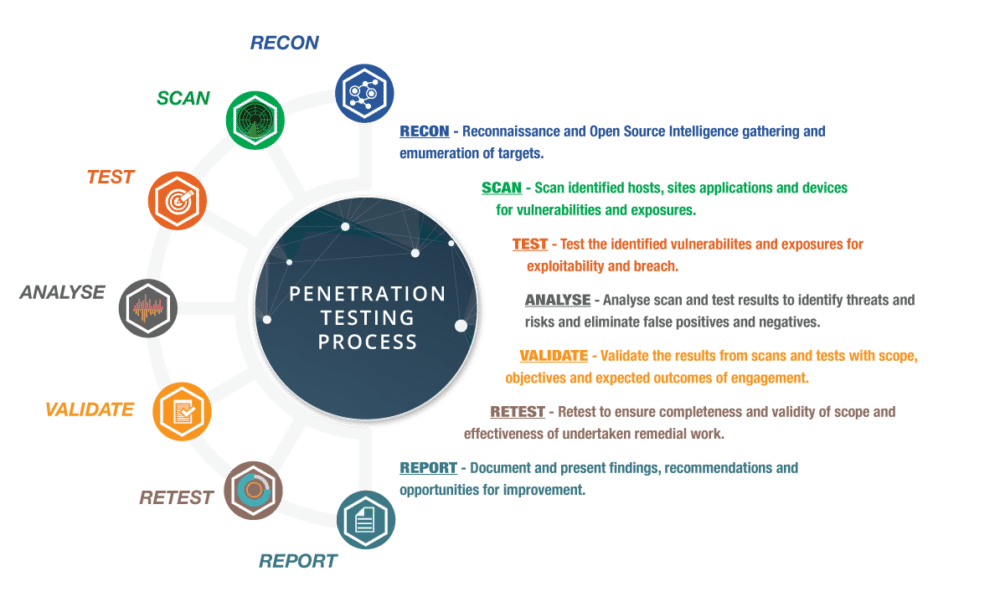
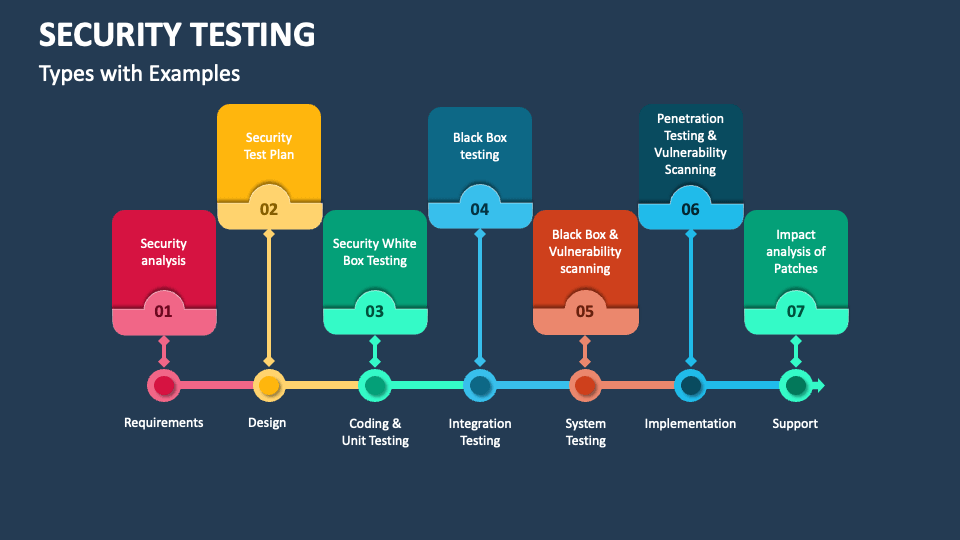

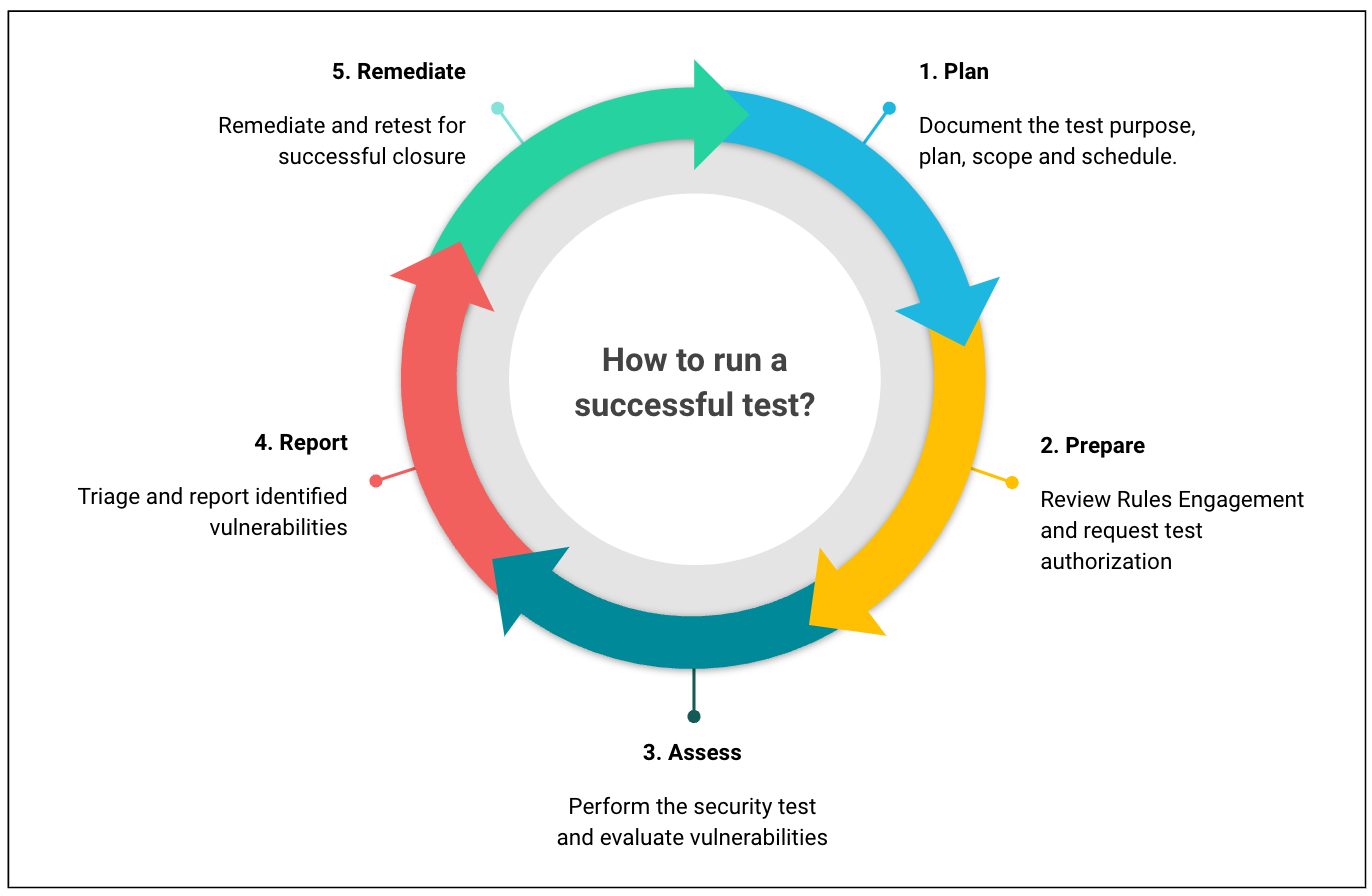




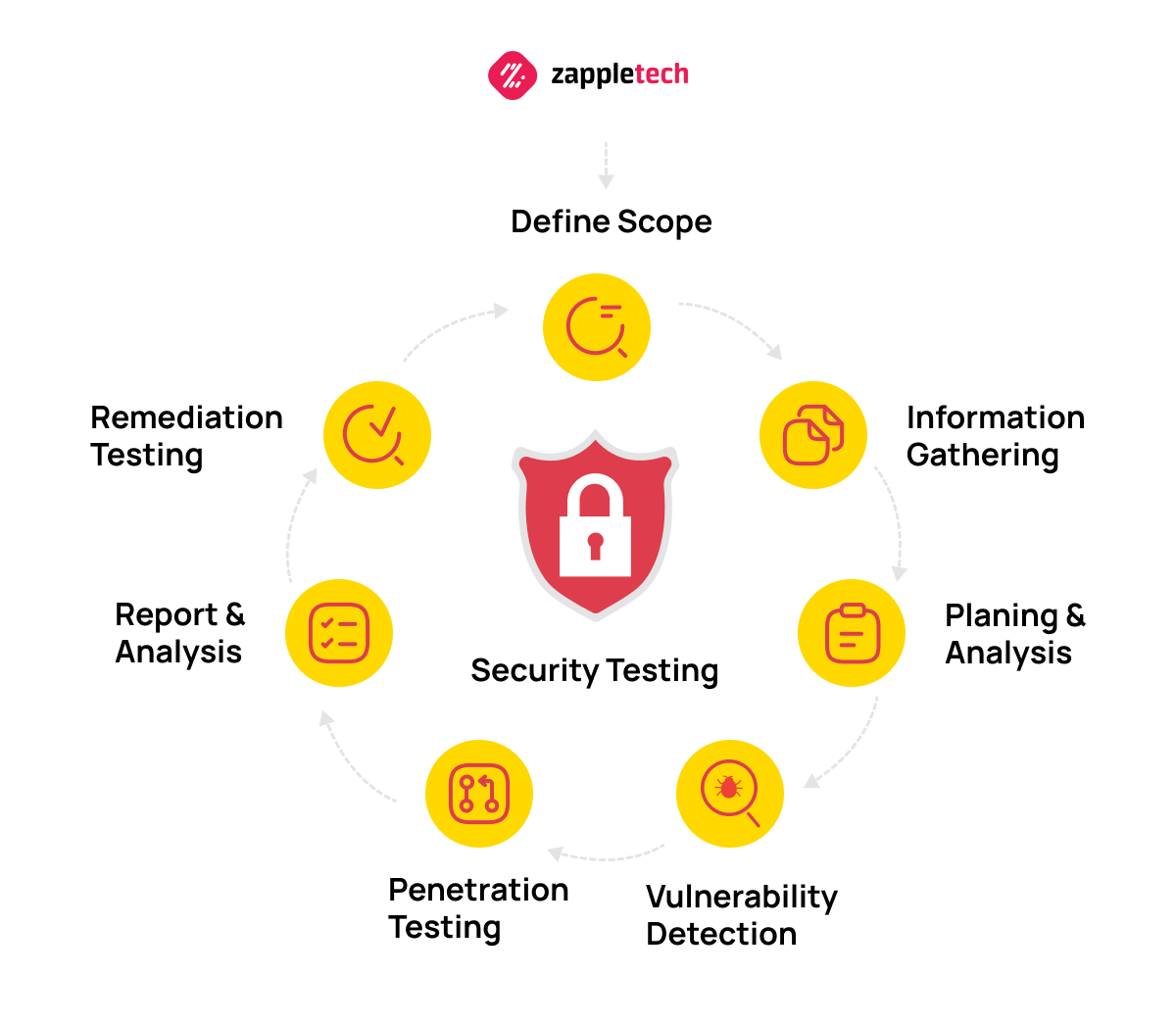

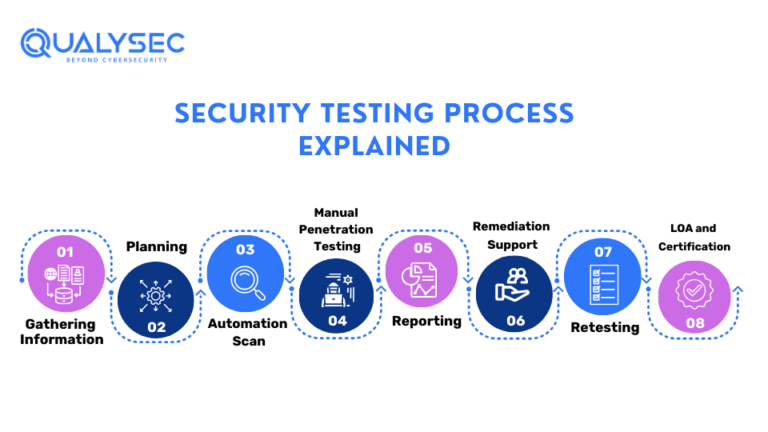

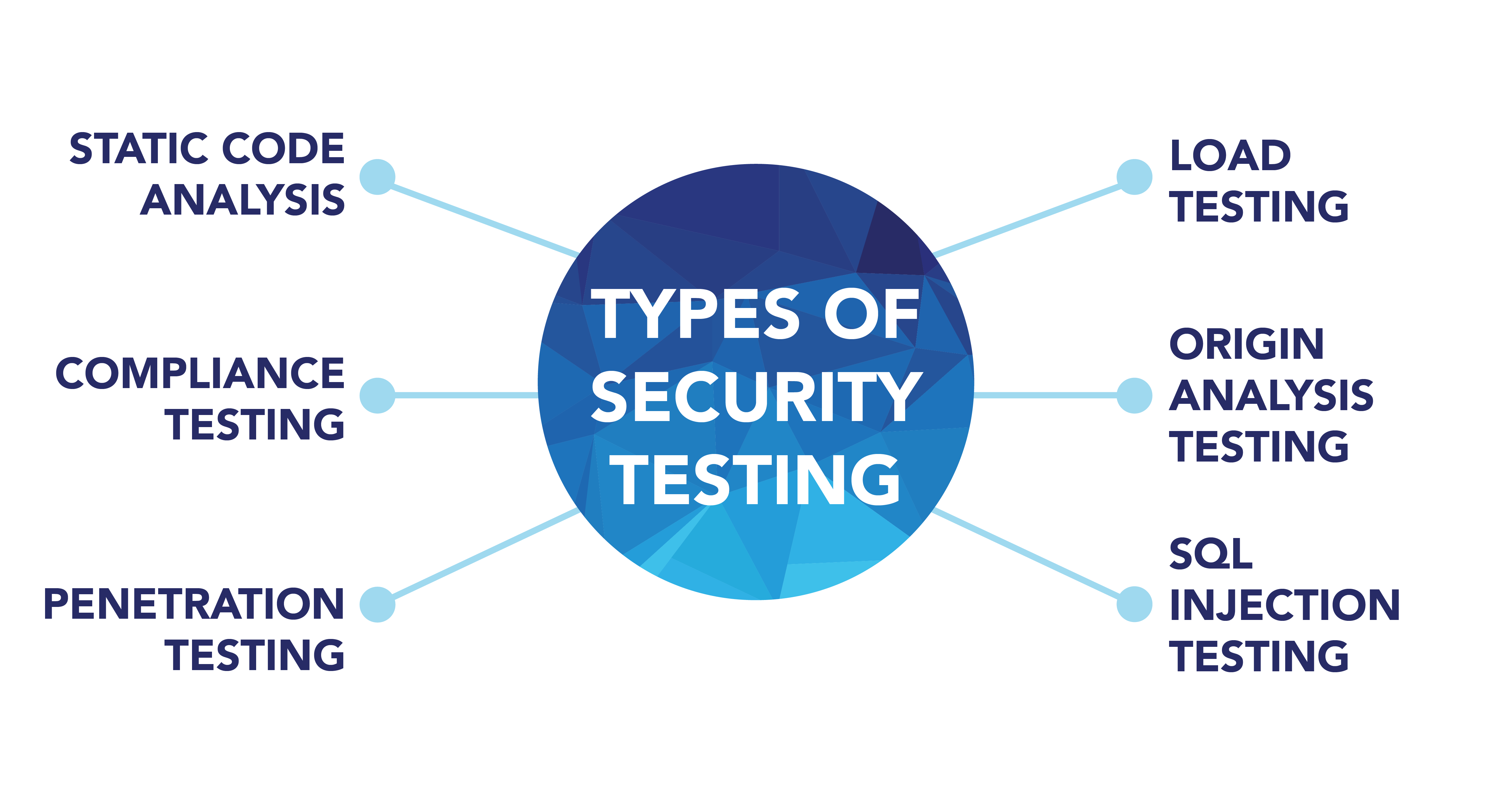

















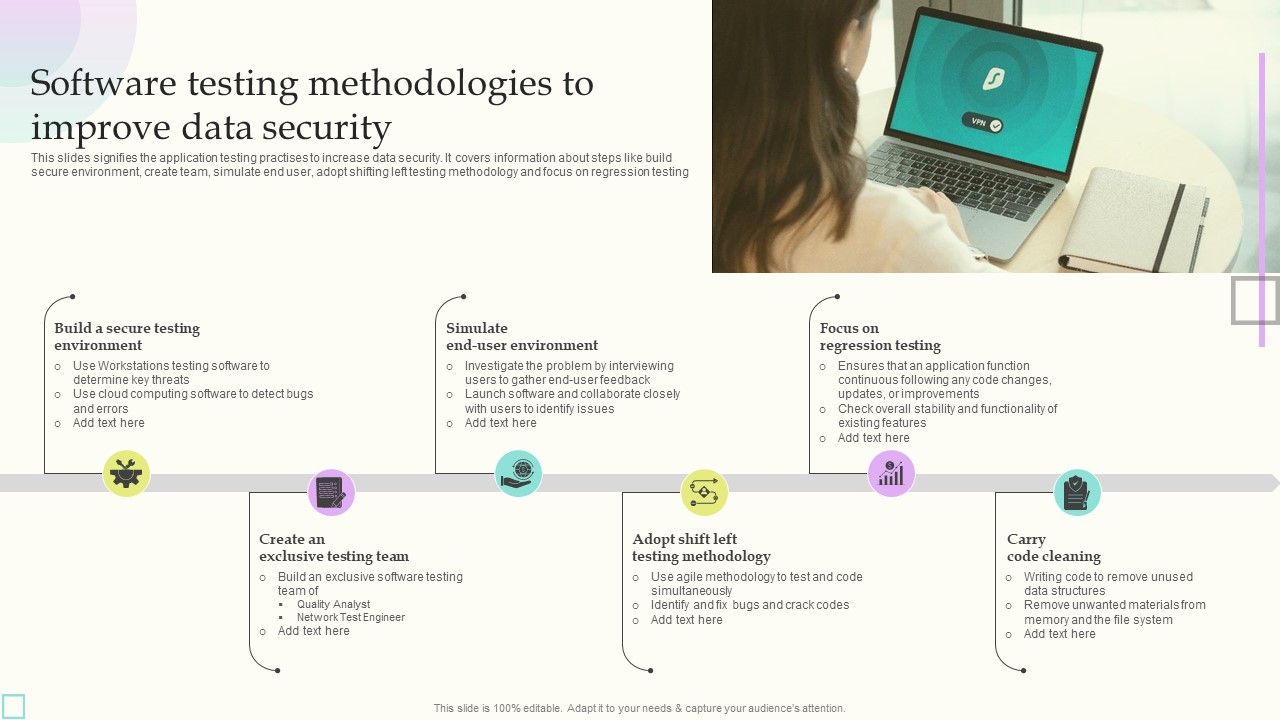
![Top 8 Cybersecurity Audit Companies in 2025 [Updated]](https://qualysec.com/wp-content/uploads/2025/07/Security-Testing-Methodologies-Definitions-Processes-Checklist-1024x576.jpg)