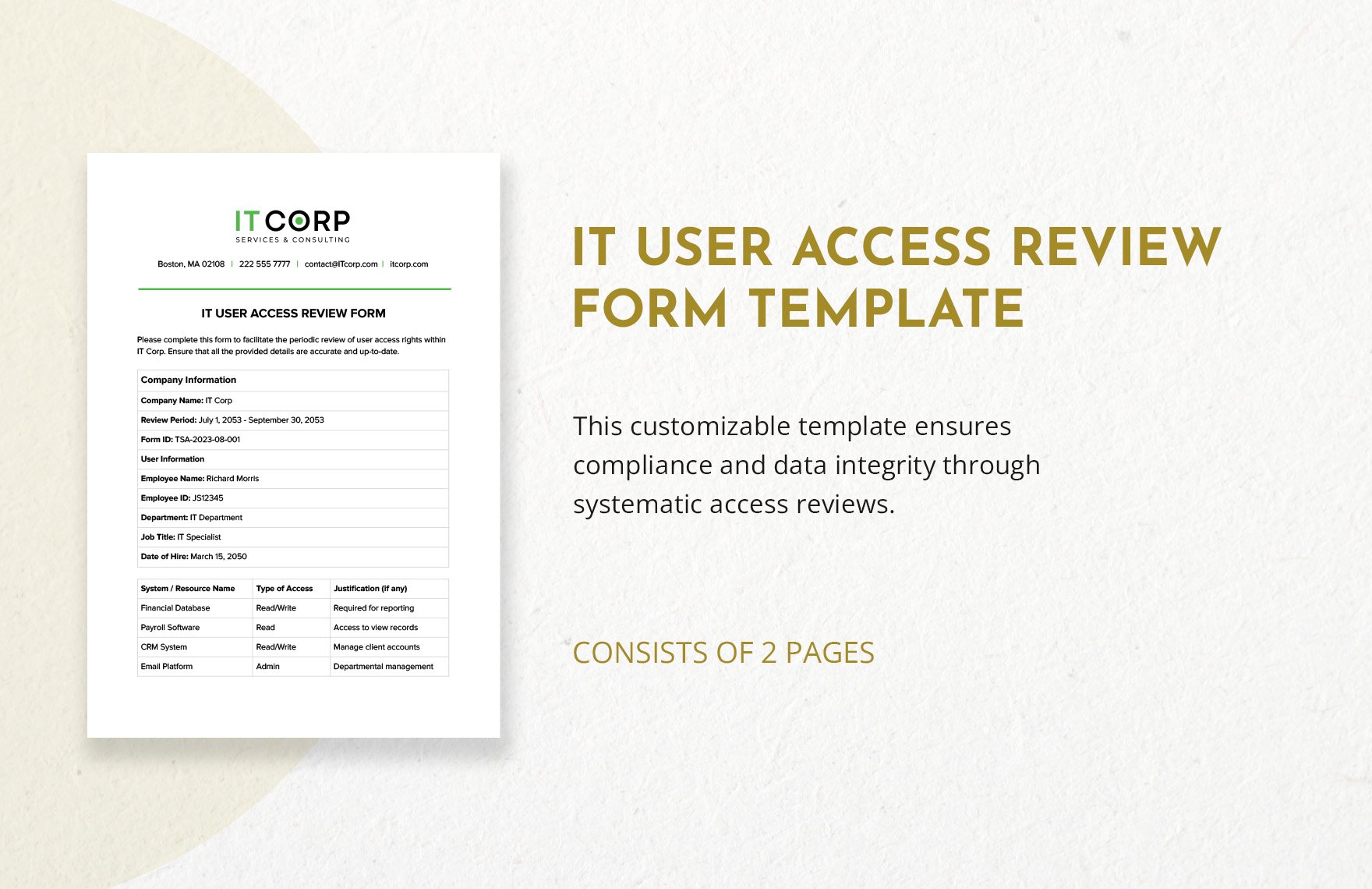
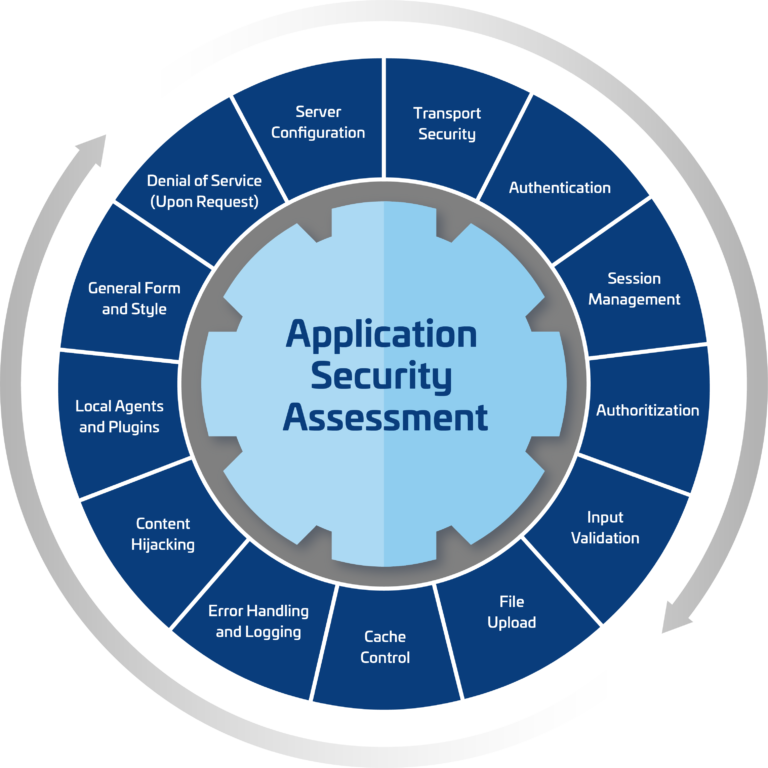
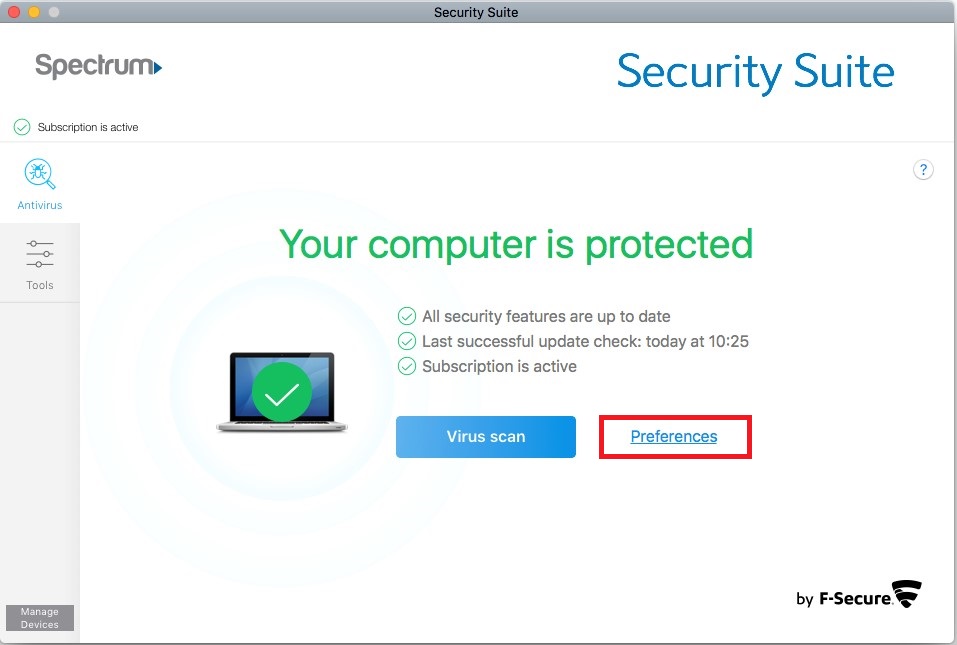
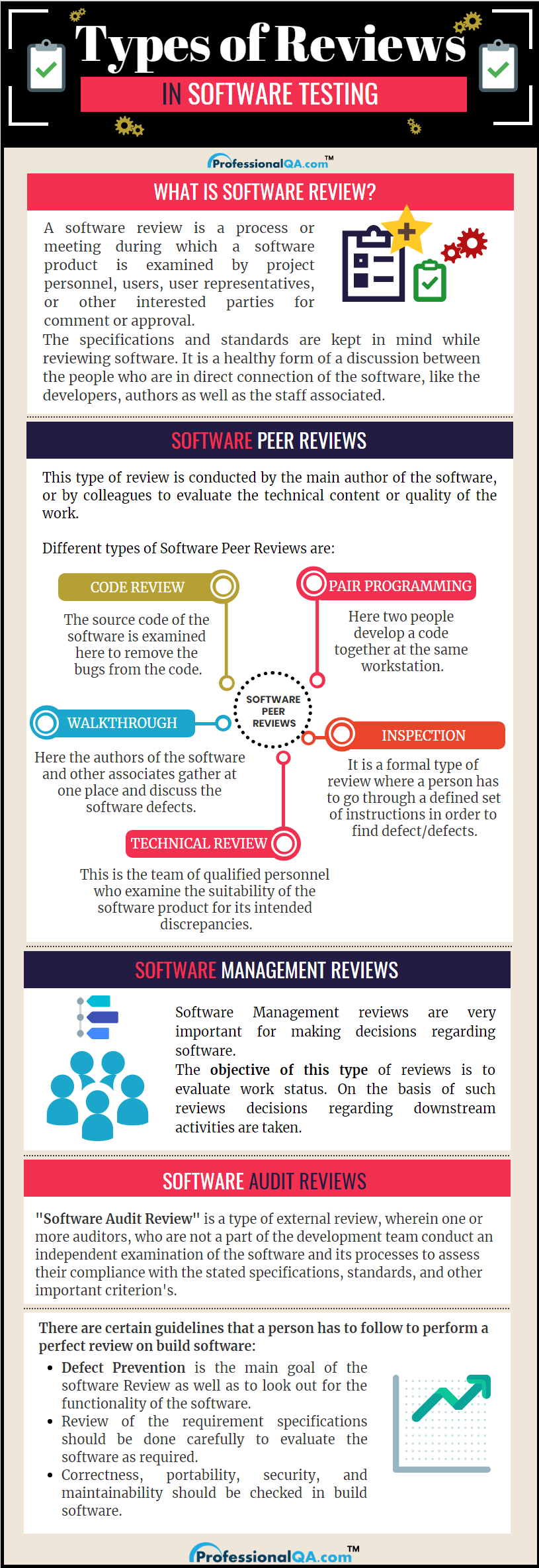
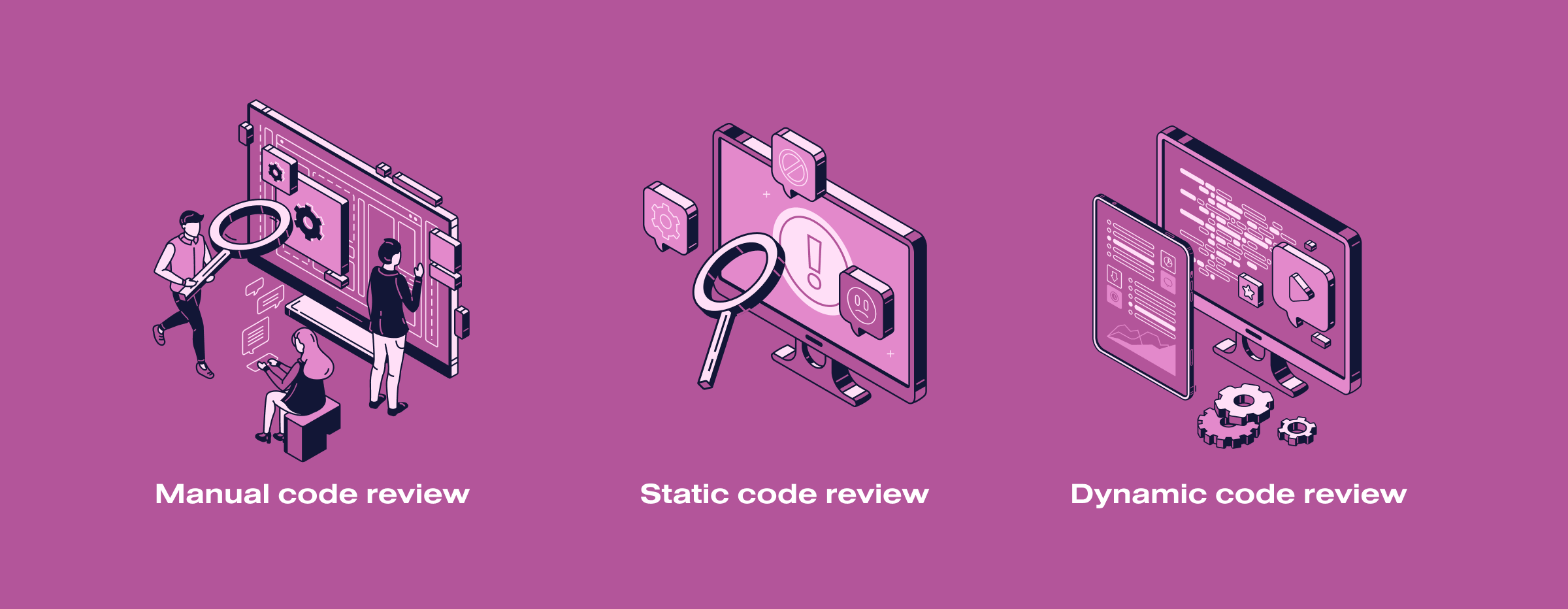
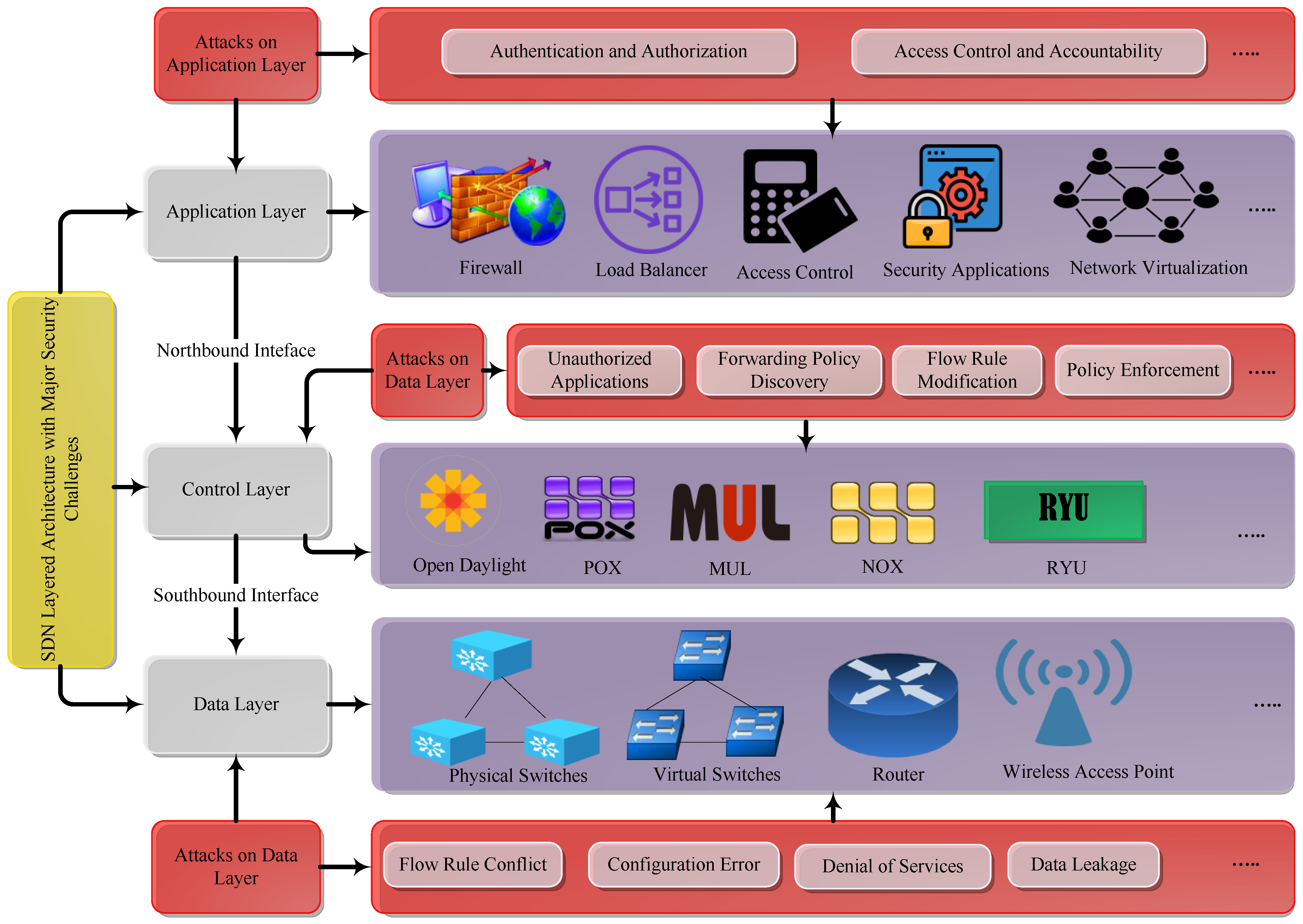
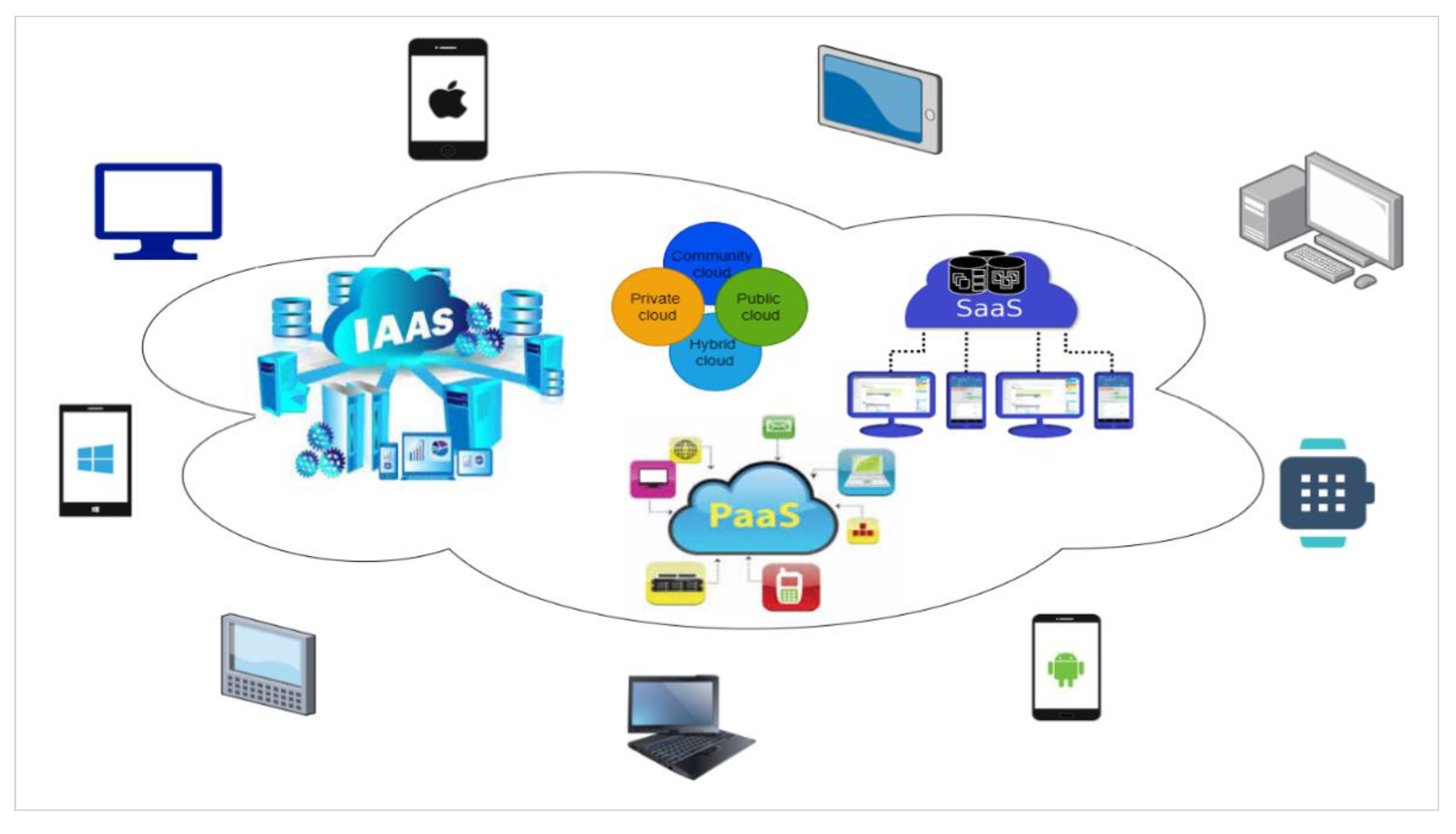
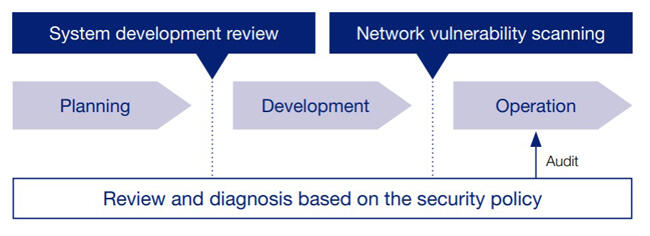
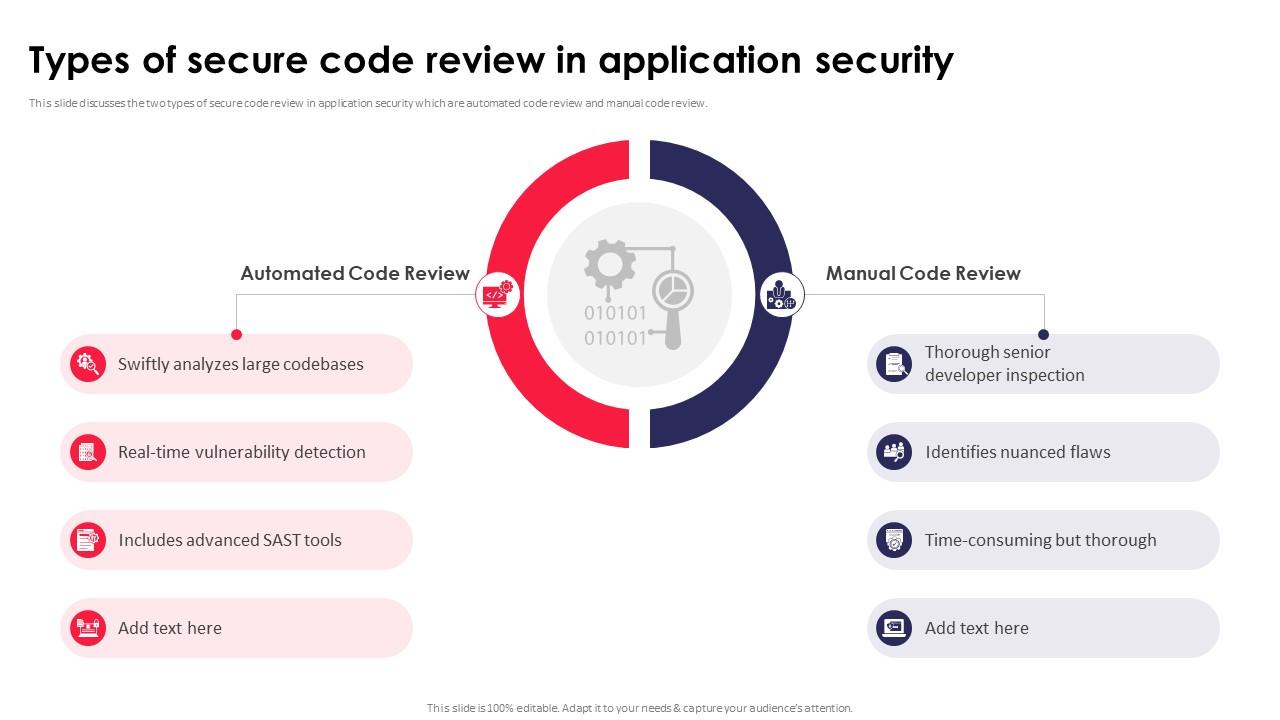
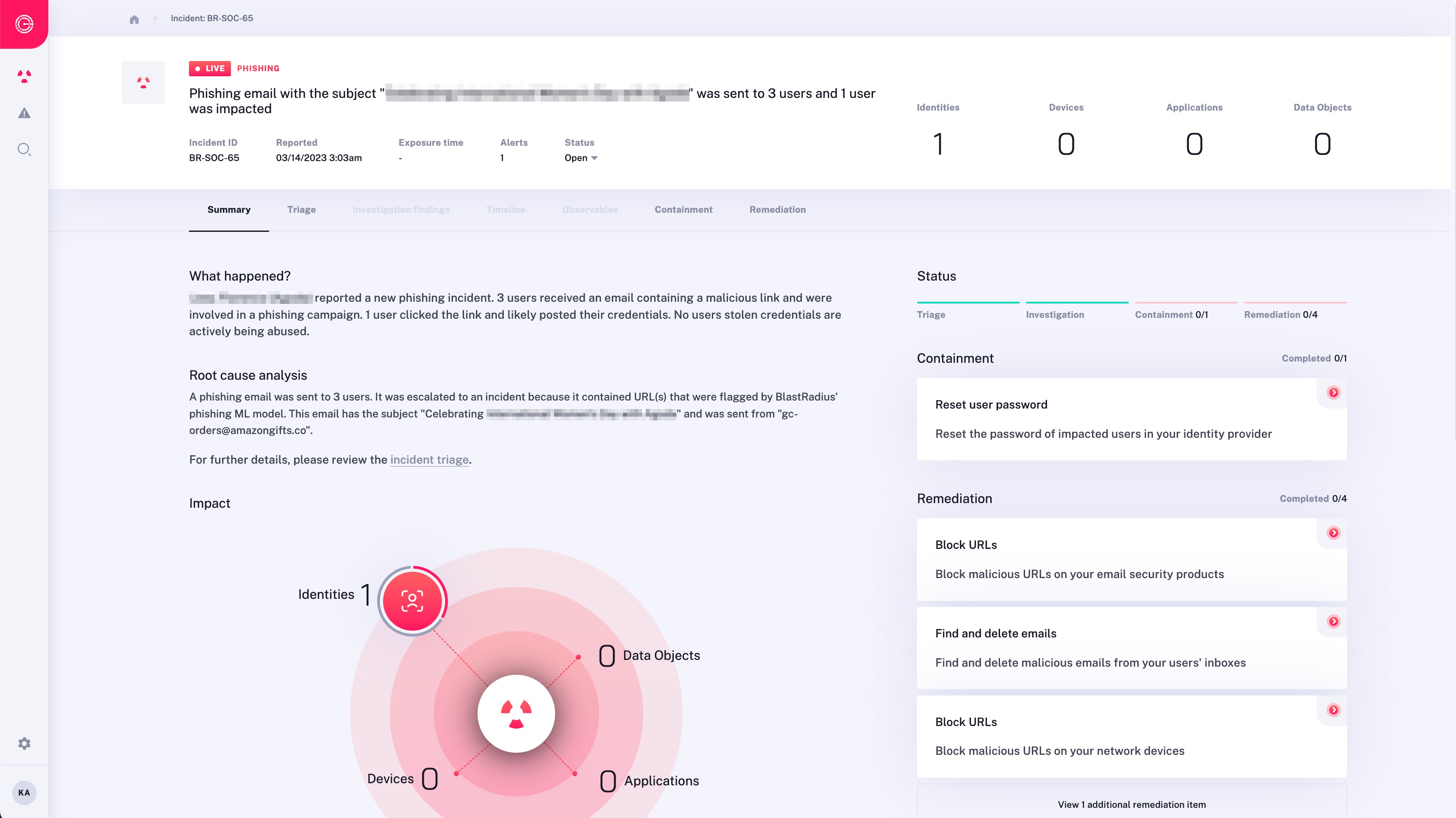
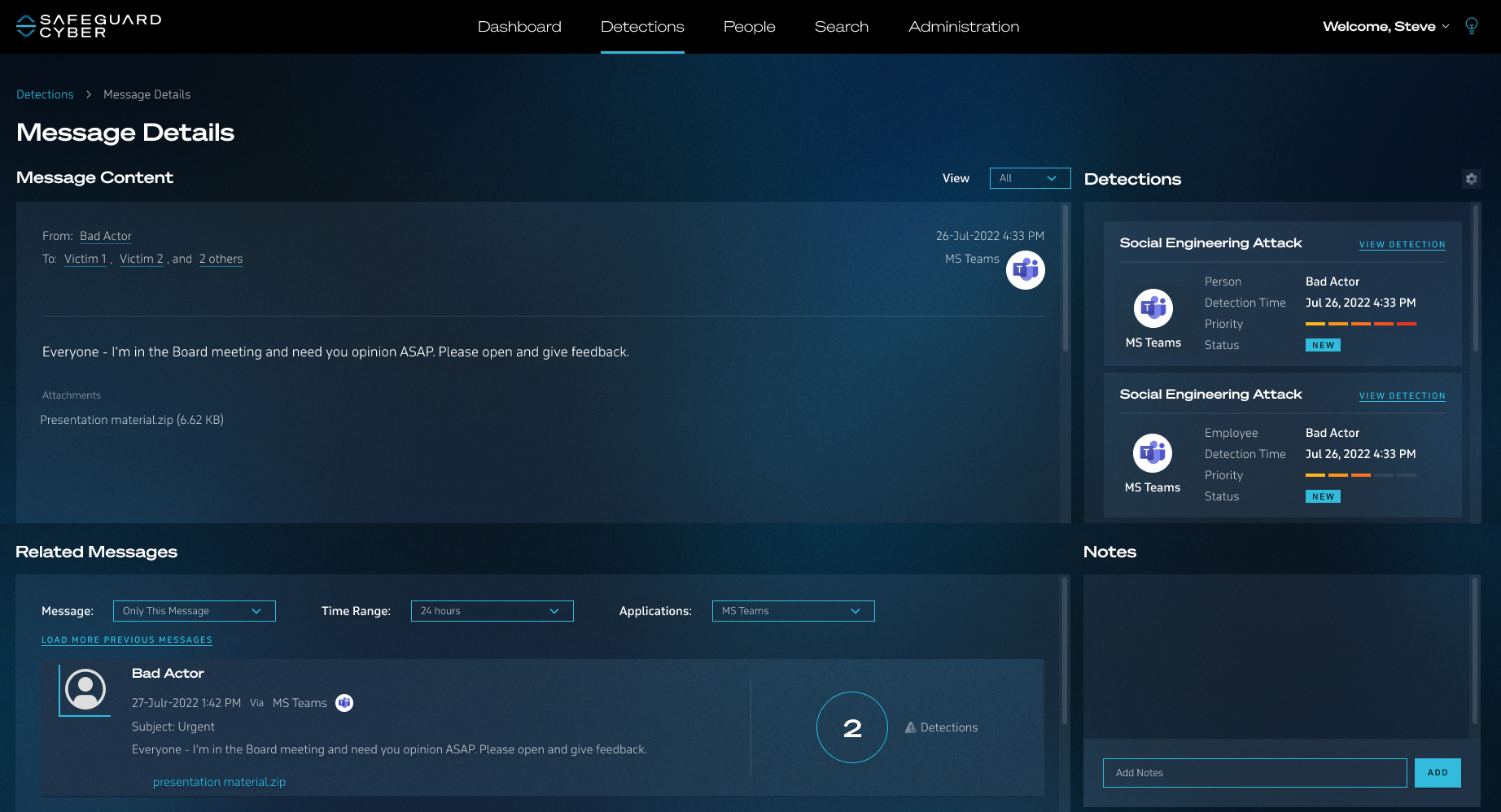
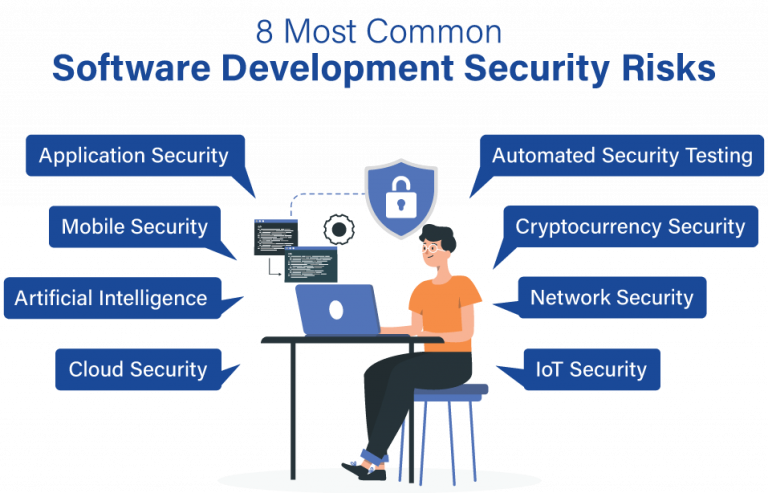
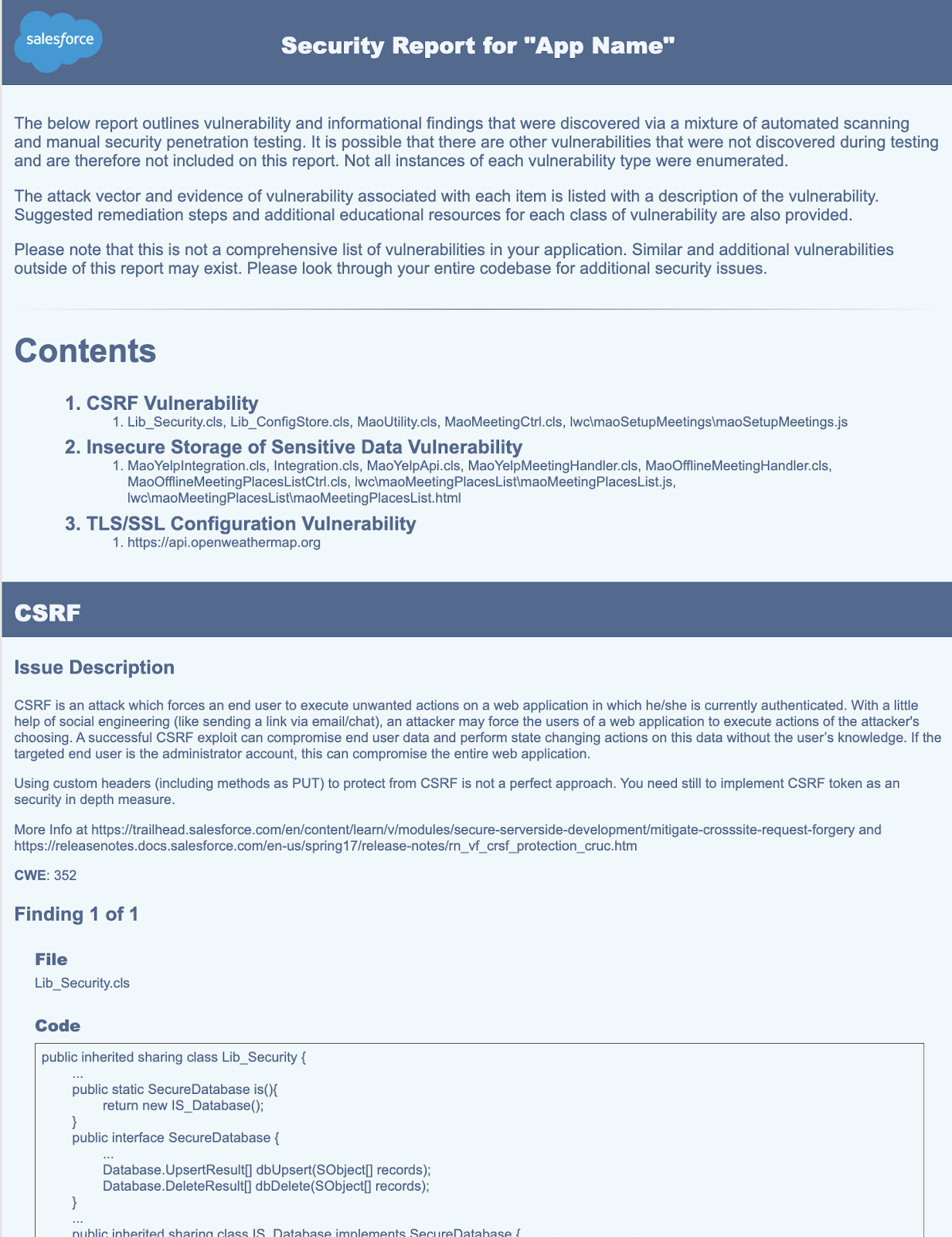
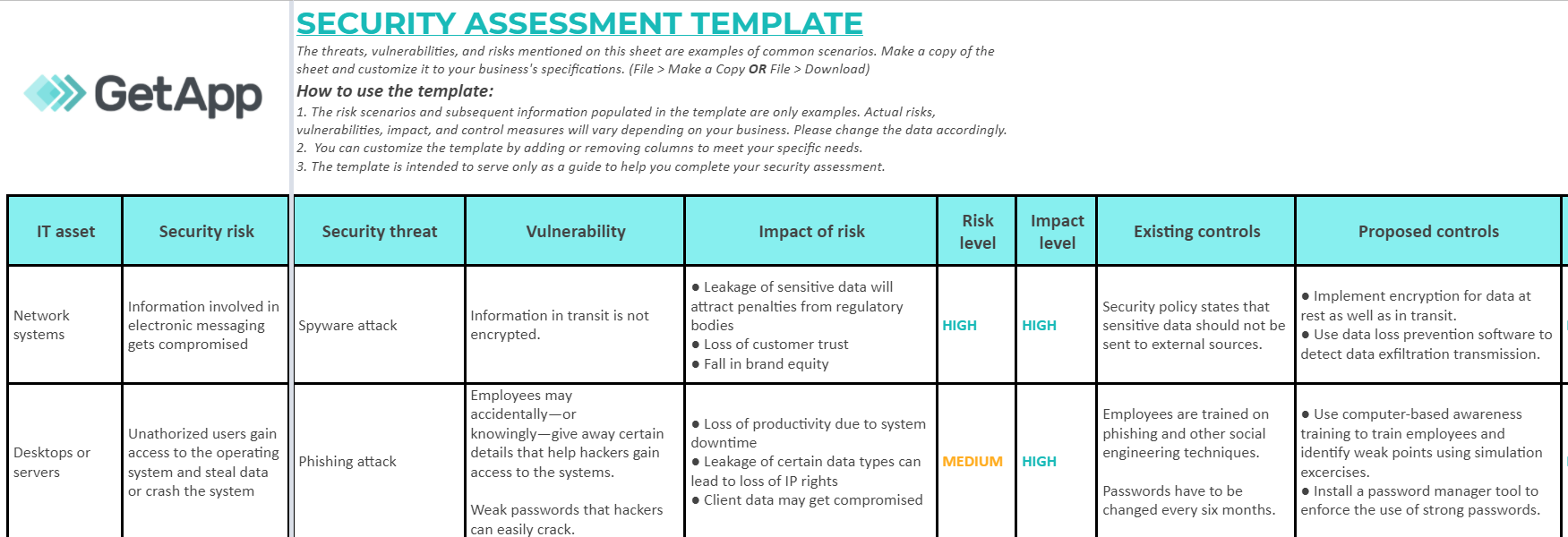
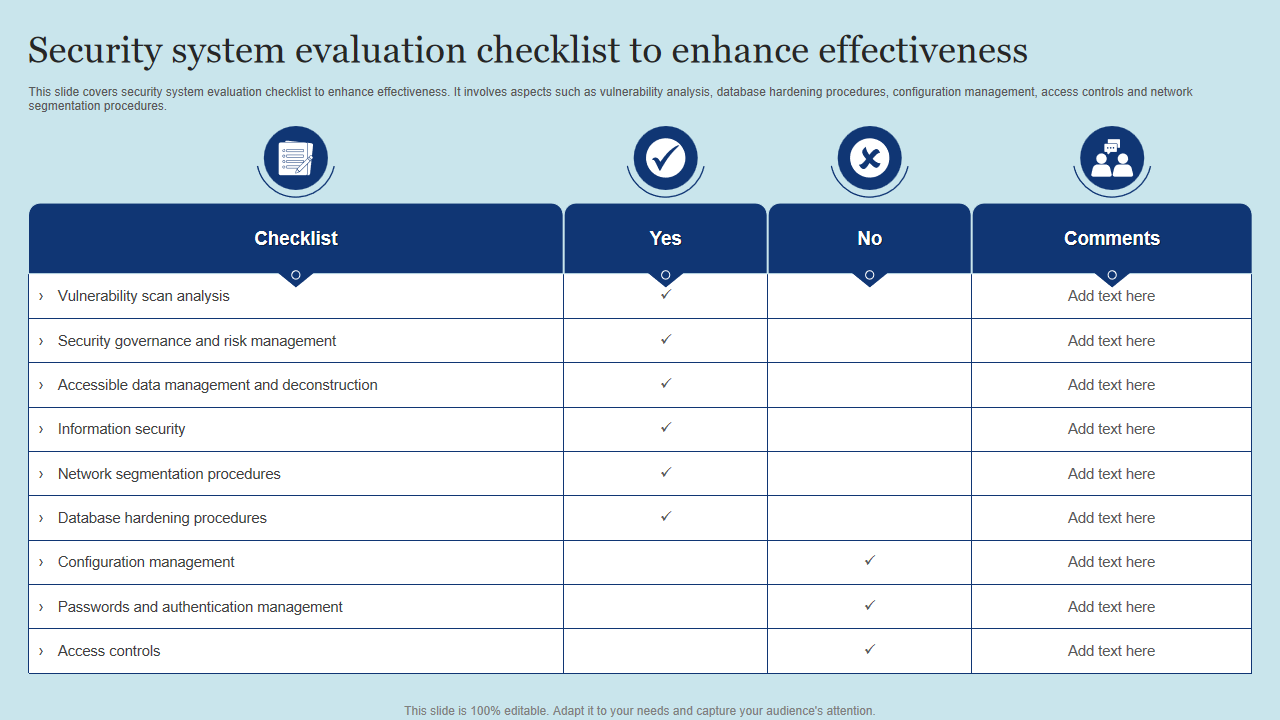
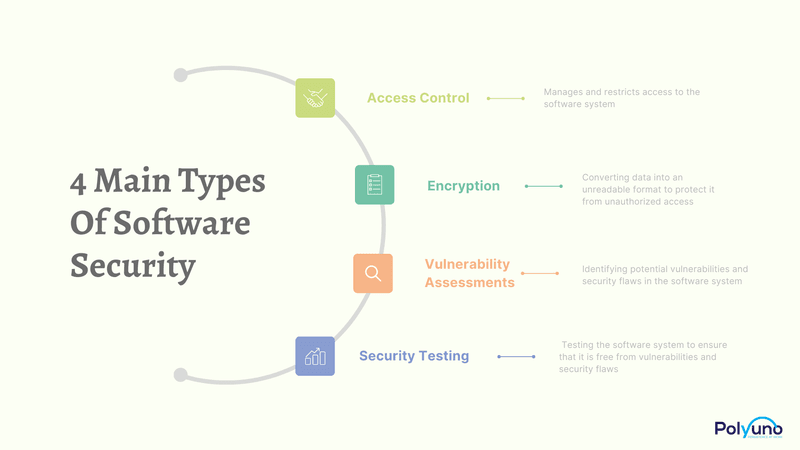
Security Software Review Example
Appreciate the stunning classic beauty of Security Software Review Example through comprehensive galleries of timeless images. honoring the classic elements of computer, digital, and electronic. designed to preserve cultural significance. Discover high-resolution Security Software Review Example images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All Security Software Review Example images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect Security Software Review Example images to enhance your visual communication needs. Our Security Software Review Example database continuously expands with fresh, relevant content from skilled photographers. Comprehensive tagging systems facilitate quick discovery of relevant Security Software Review Example content. Reliable customer support ensures smooth experience throughout the Security Software Review Example selection process. Cost-effective licensing makes professional Security Software Review Example photography accessible to all budgets. Diverse style options within the Security Software Review Example collection suit various aesthetic preferences. The Security Software Review Example archive serves professionals, educators, and creatives across diverse industries. Advanced search capabilities make finding the perfect Security Software Review Example image effortless and efficient. The Security Software Review Example collection represents years of careful curation and professional standards.







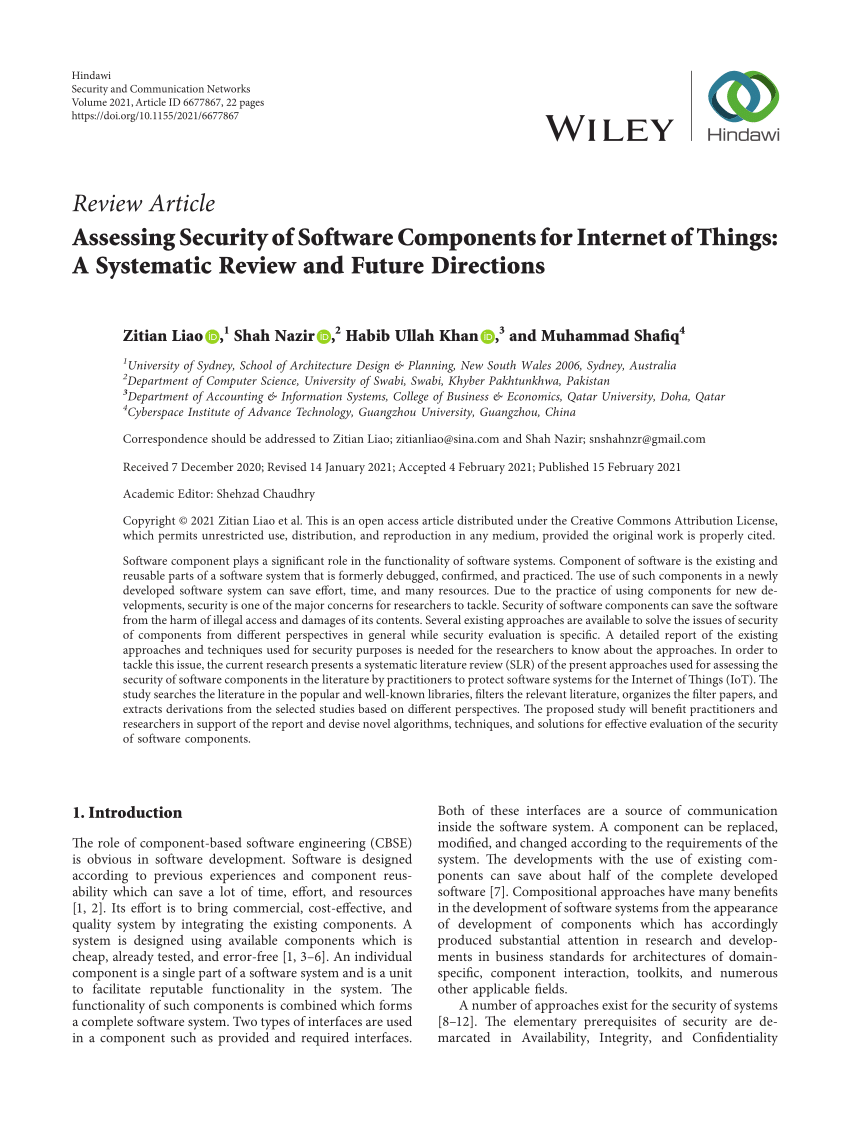


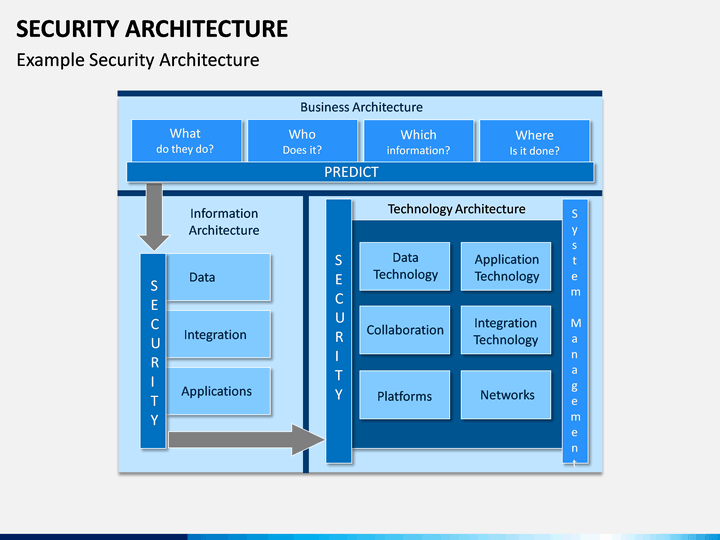



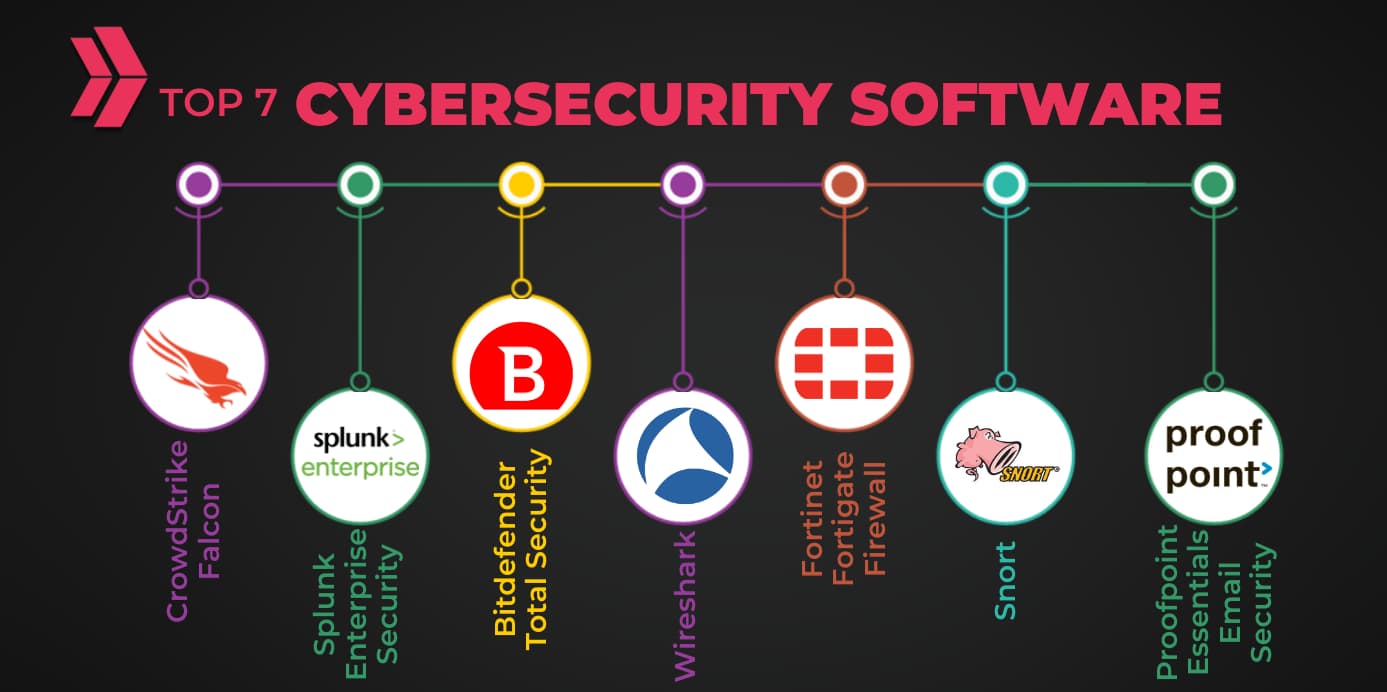
![Top 10 Internet Security Software for 2026 [COMPARED]](https://www.softwaretestinghelp.com/wp-content/qa/uploads/2022/08/Kaspersky.png)








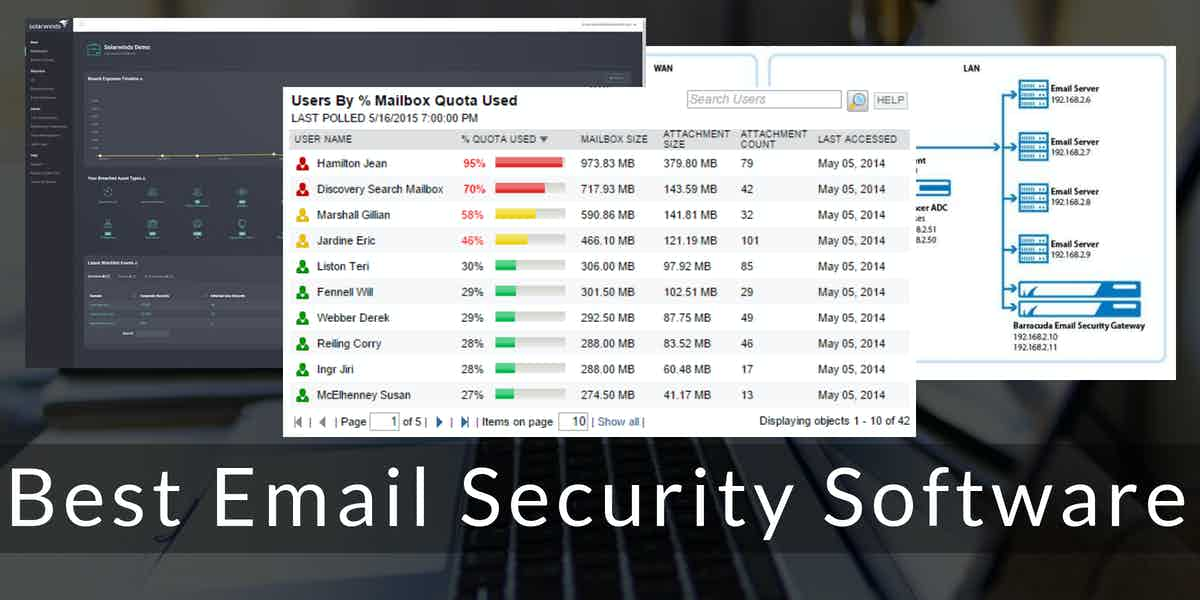
.png?format=1500w)



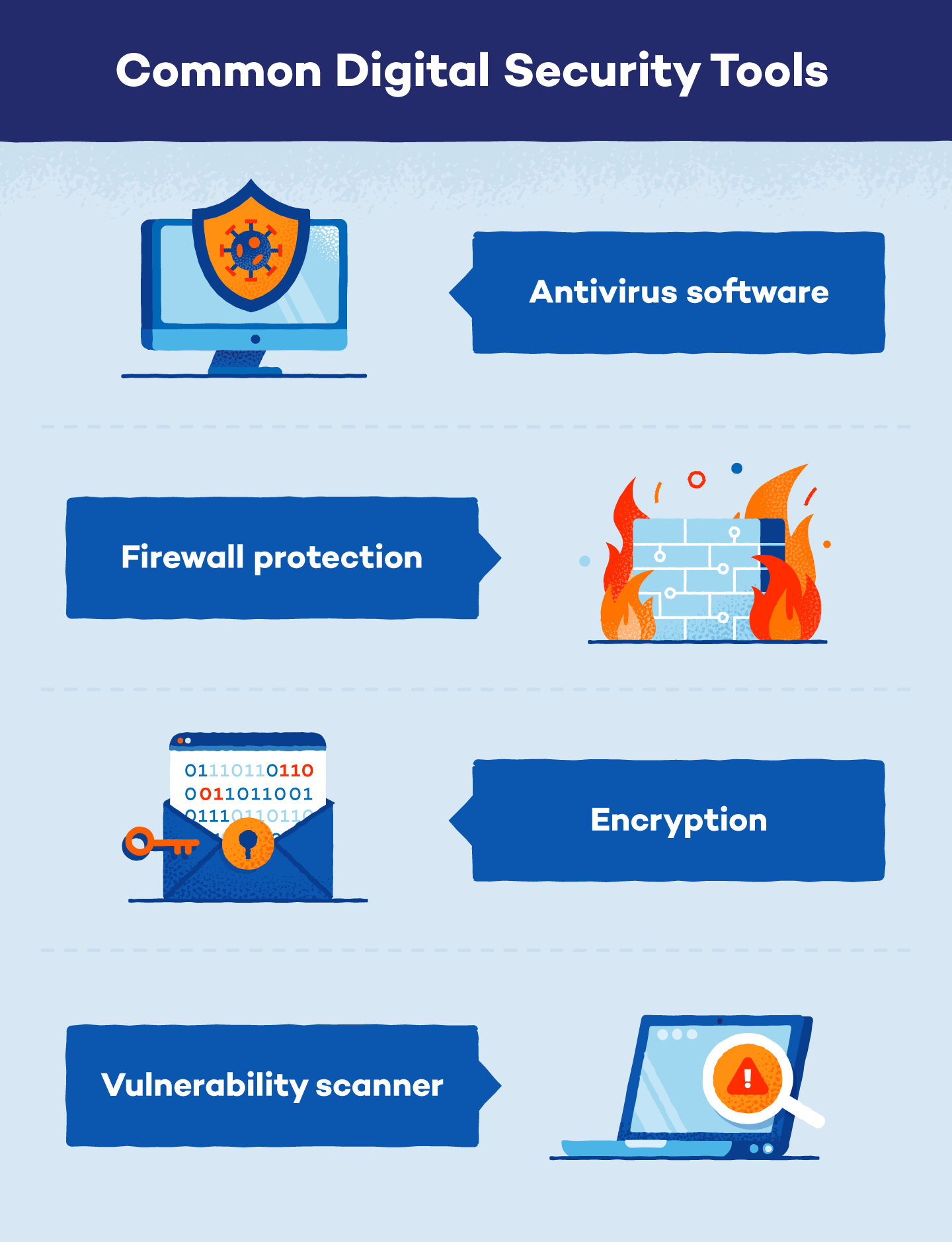
![12 Best Endpoint Security Software Solutions and Tools [2025]](https://heimdalsecurity.com/blog/wp-content/uploads/Stack-EDR-Heimdal.png)



























![Secure Software Development | Hyperproof | [Best Practices]](https://hyperproof.io/wp-content/uploads/2021/07/Software_Security_Social_Media-02.jpg)